Downloaded 31 times



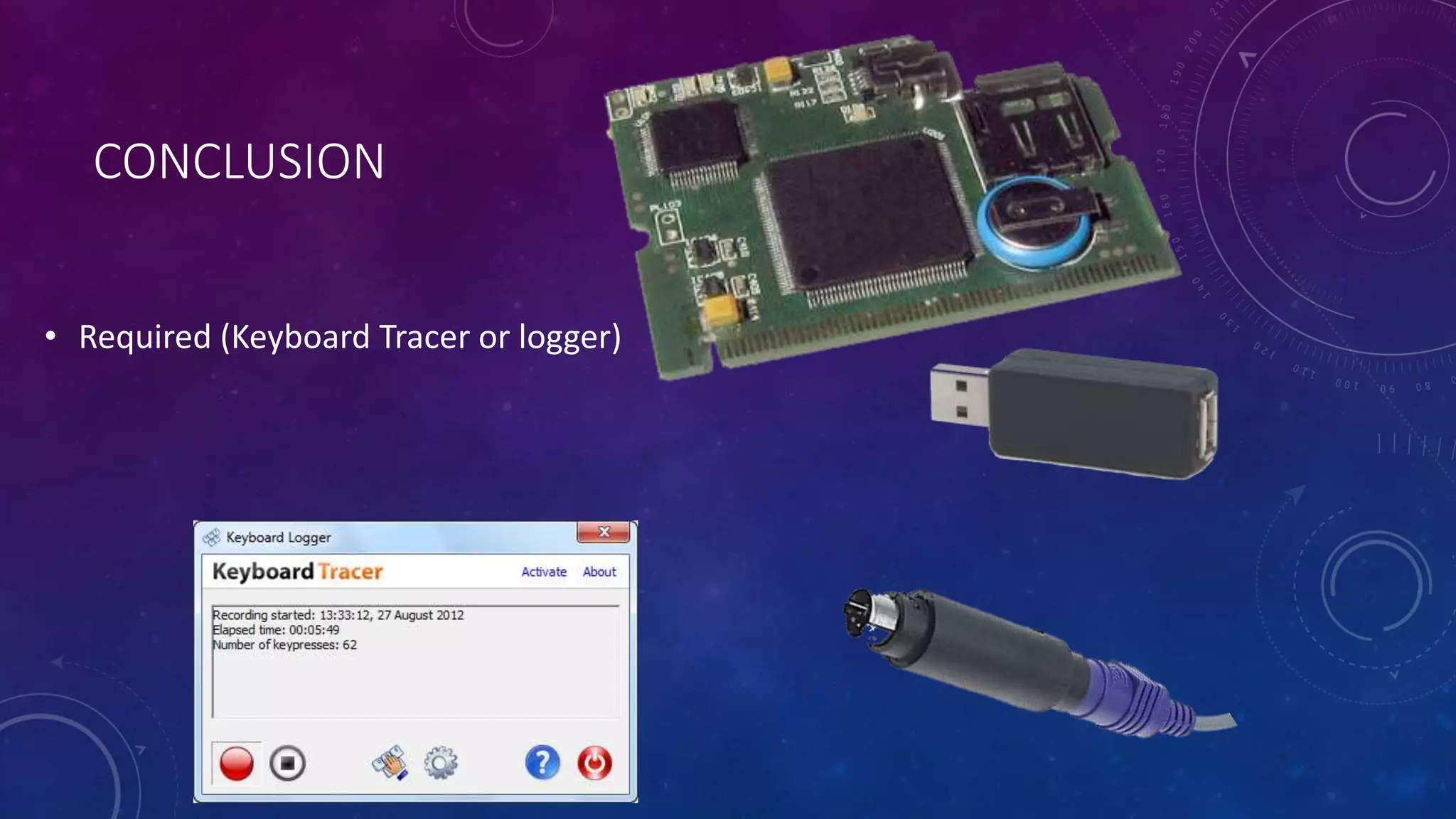


The document provides an overview of computer hacking, including its history from the 1960s to significant attacks in the 2000s. It differentiates between hackers and crackers, lists famous hackers, and outlines various types of hacking such as website, email, and network hacking. Additionally, it discusses essential security measures and concludes with a mention of tools like keyboard tracers.








