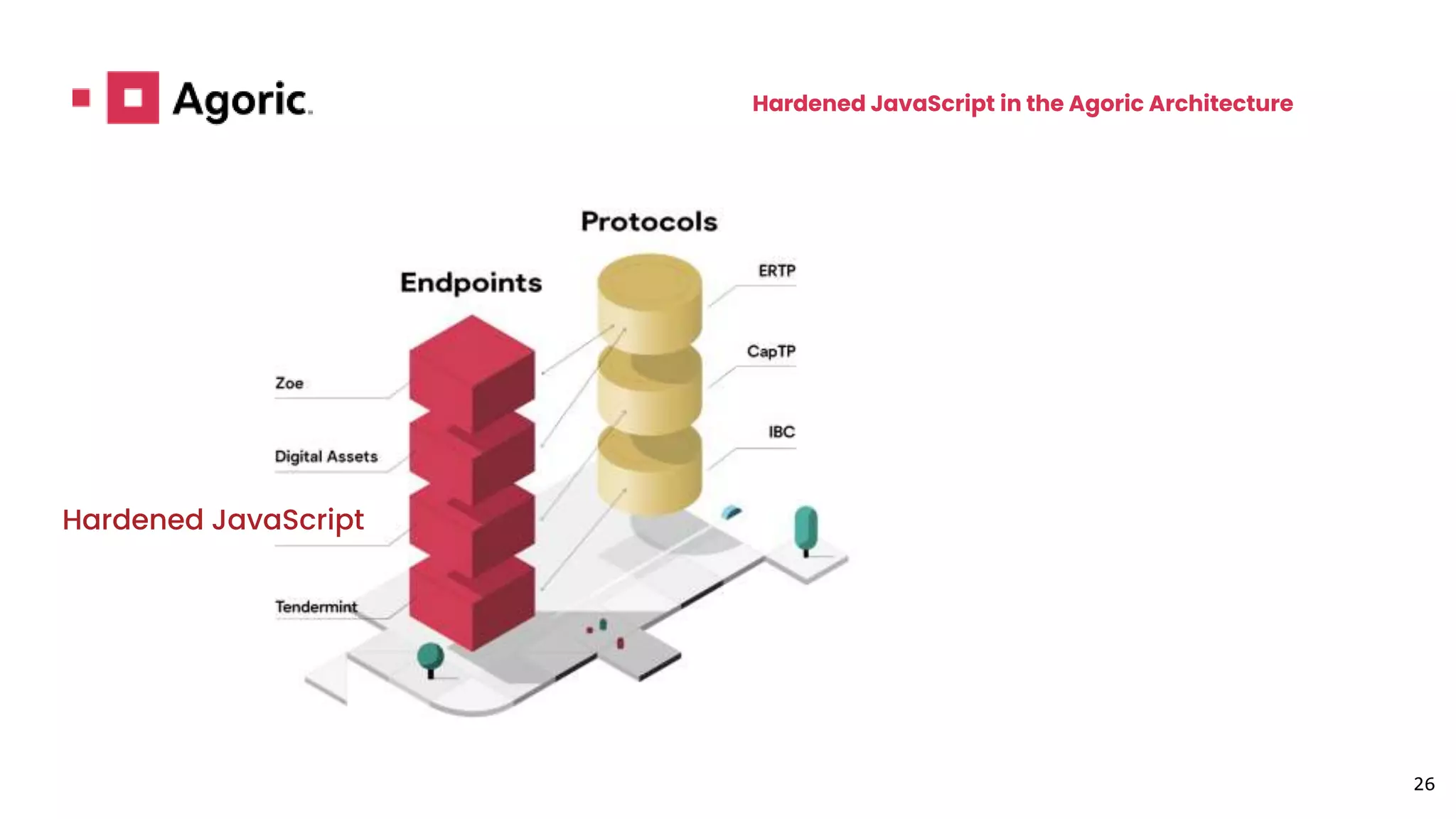
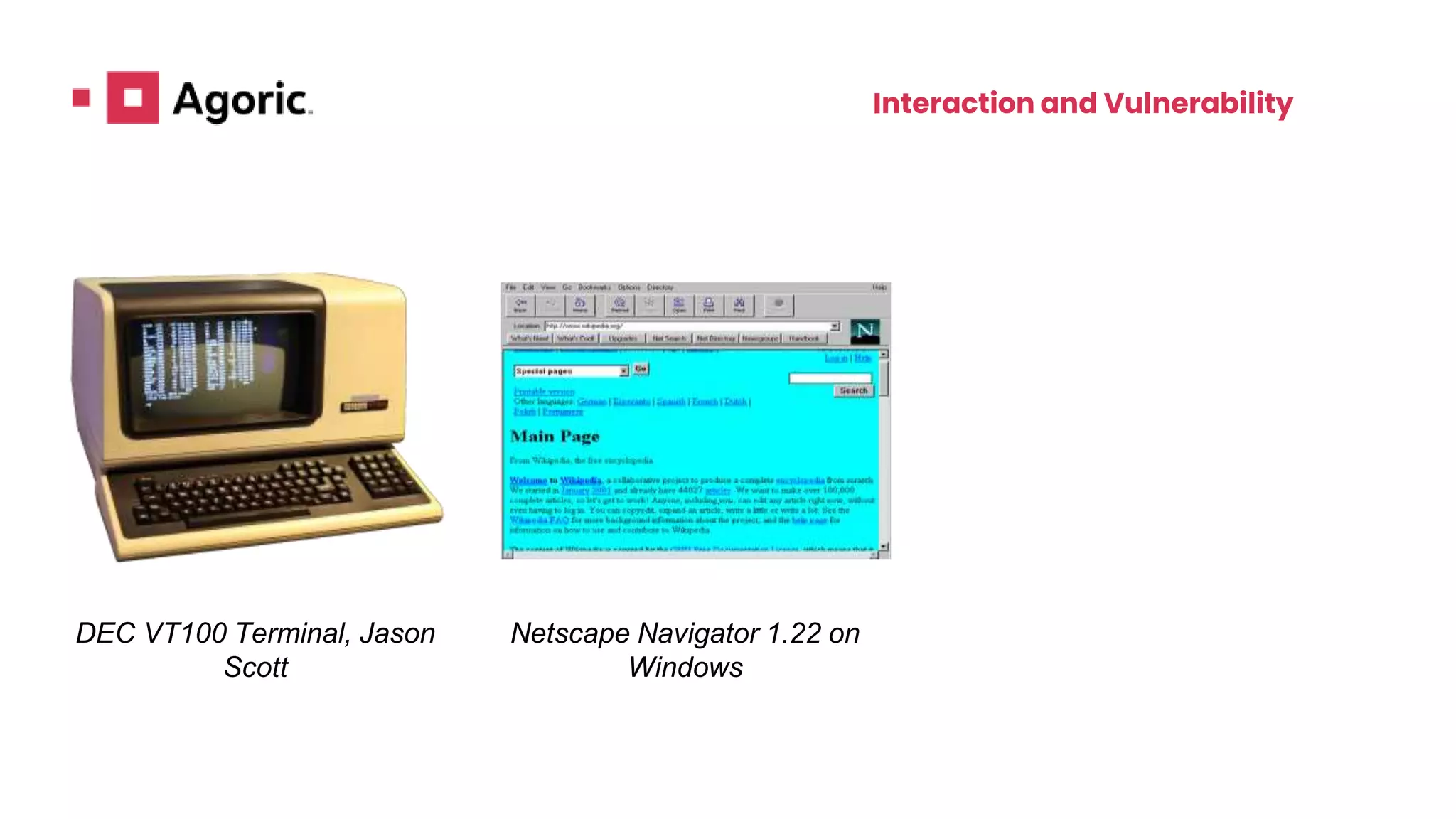
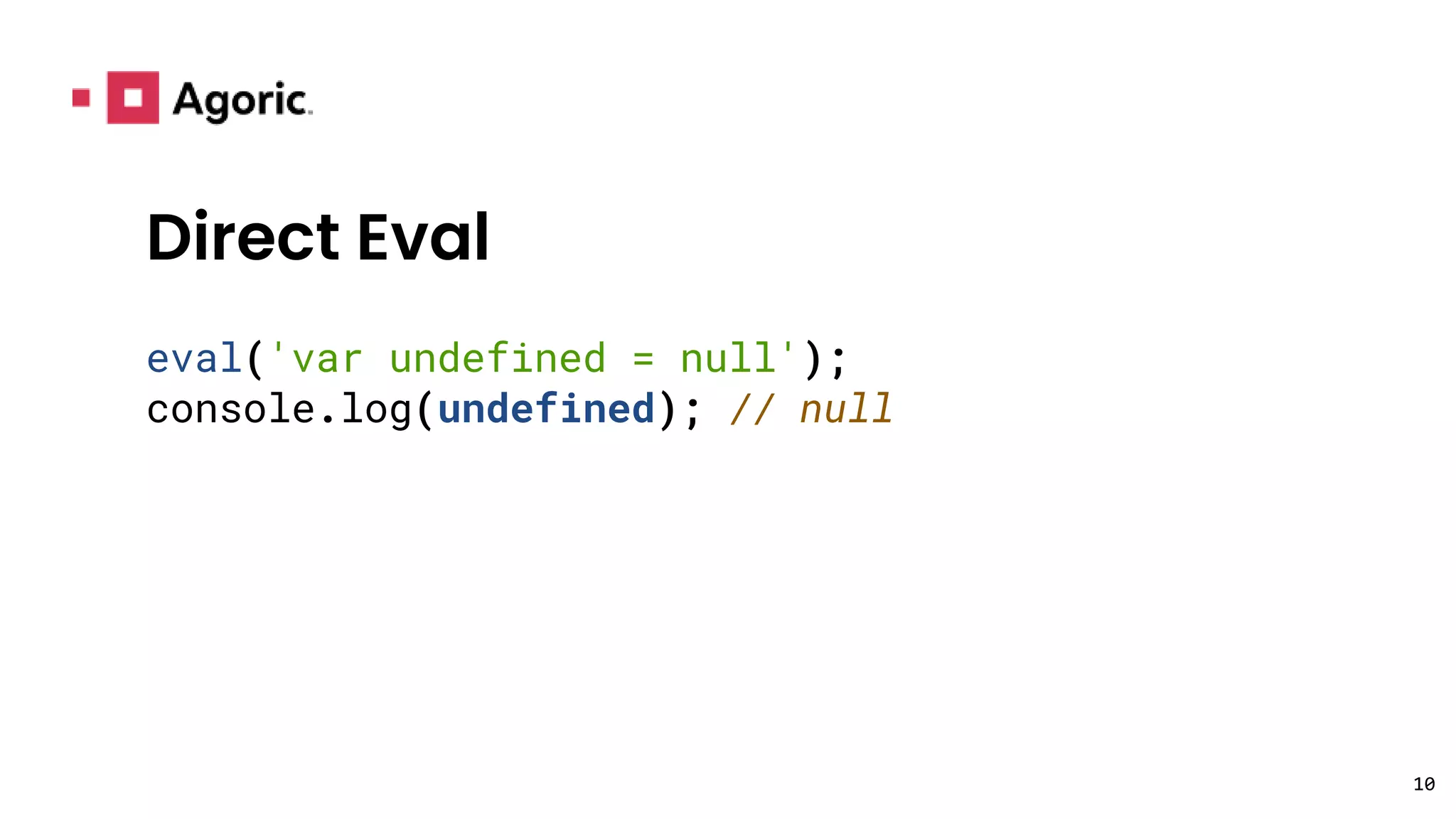
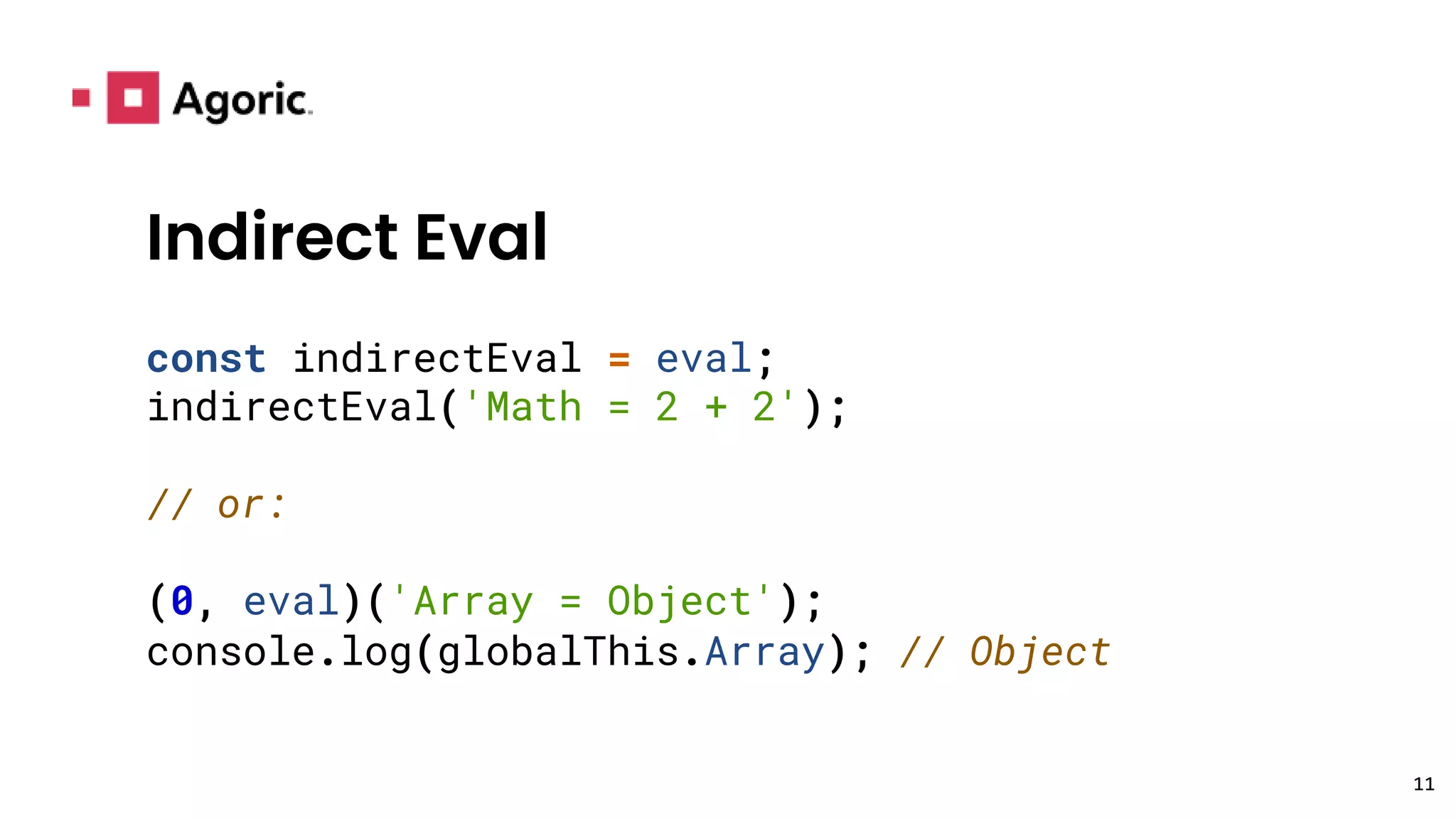
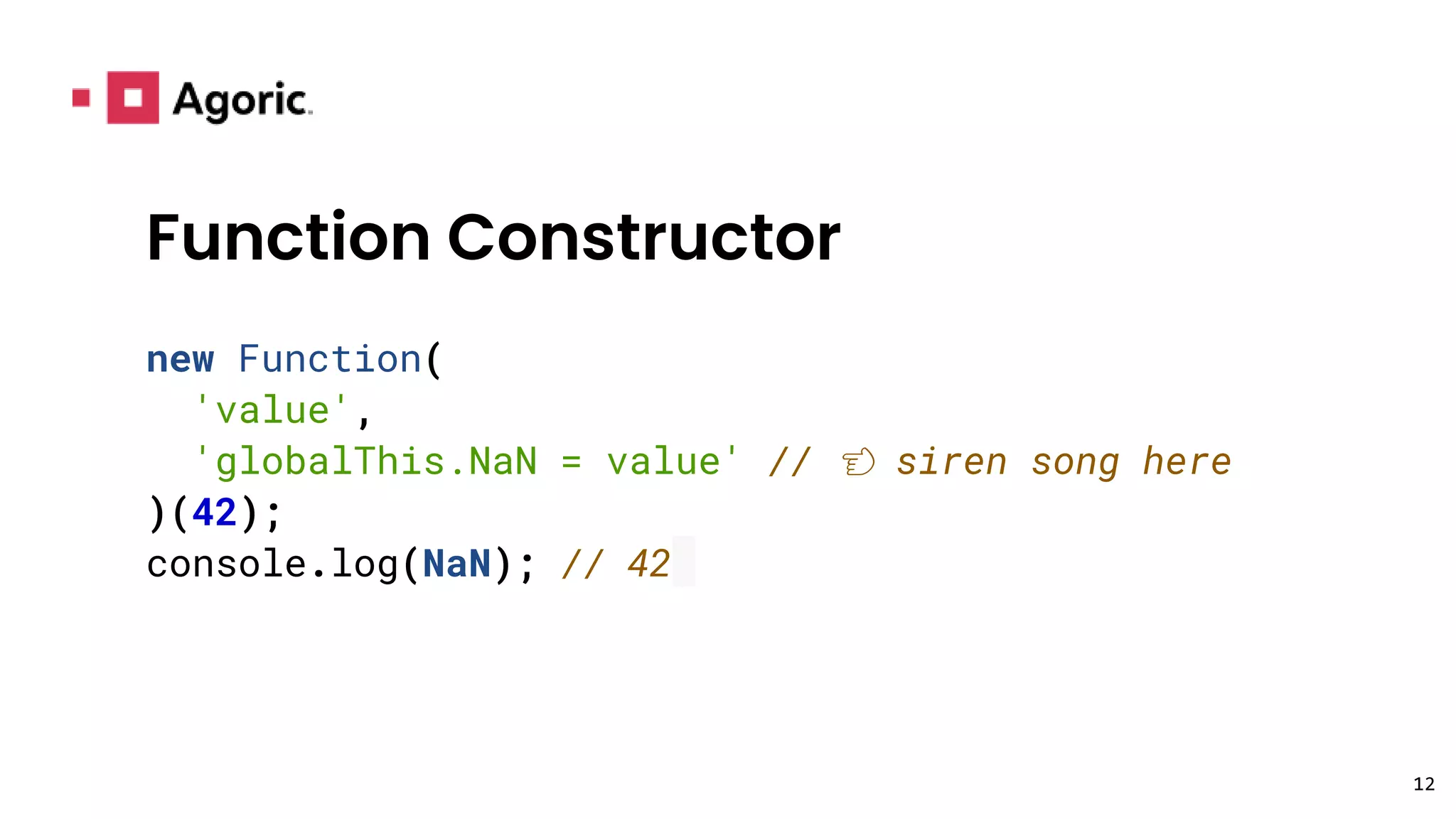
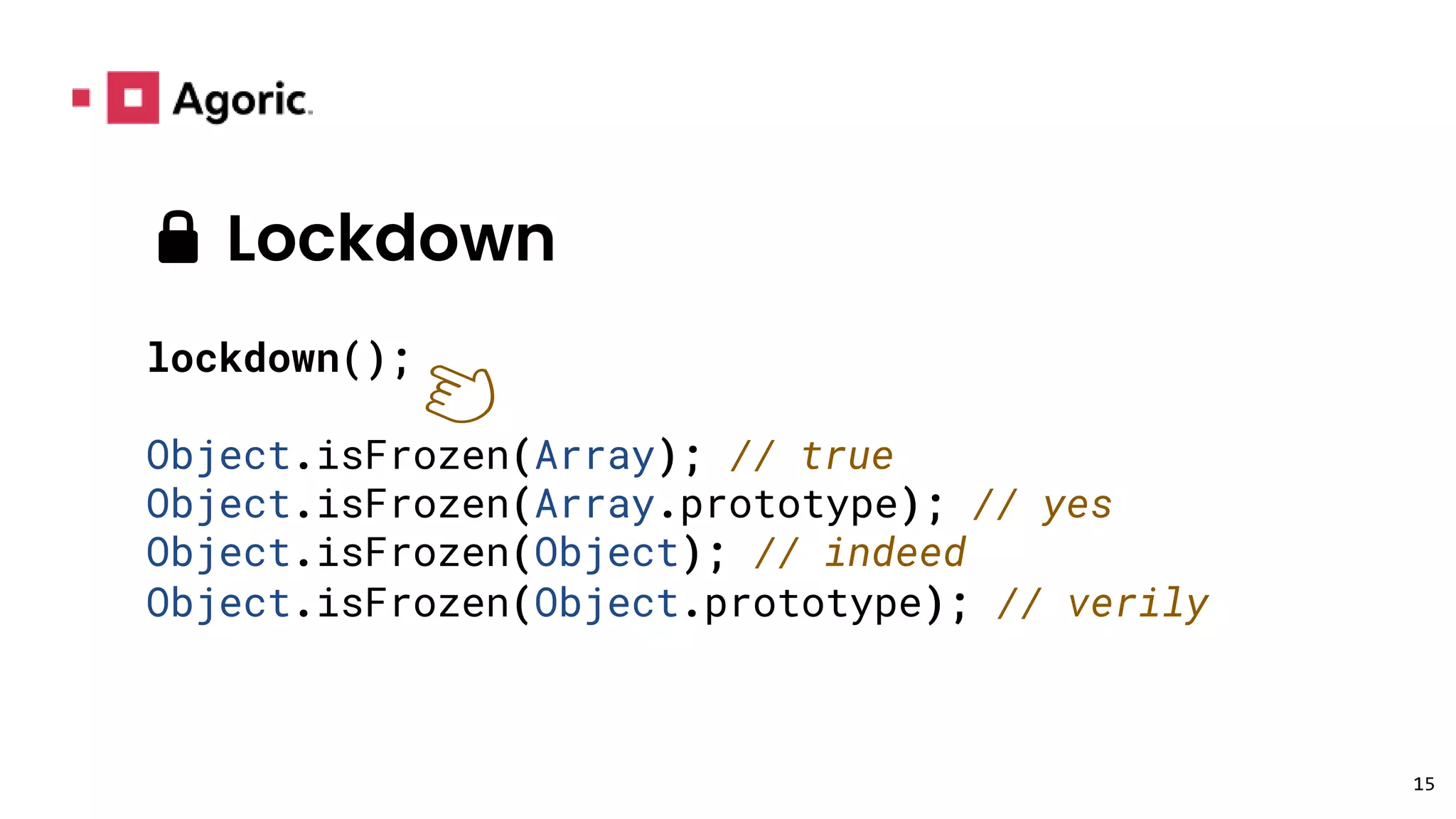
This document discusses hardened JavaScript and how it can be used to safely run untrusted code. It describes how JavaScript environments like browsers allow arbitrary programs to run but mediate their interactions. It then explains how techniques like freezing objects, compartmentalization, and avoiding direct eval can "harden" JavaScript to prevent malicious code from harming the system or accessing private data. The goal is to allow safe interaction between mutually untrusting code while preventing attacks.





![Queries are
Hobbled
Programs
Consider the case of a data
service provider that accepts
arbitrary programs instead of a
weakened query language.
8
const search = query => {
const matches = [];
for (const item of database.items()) {
if (eval(query)) {
matches.push(item);
};
}
return matches;
};
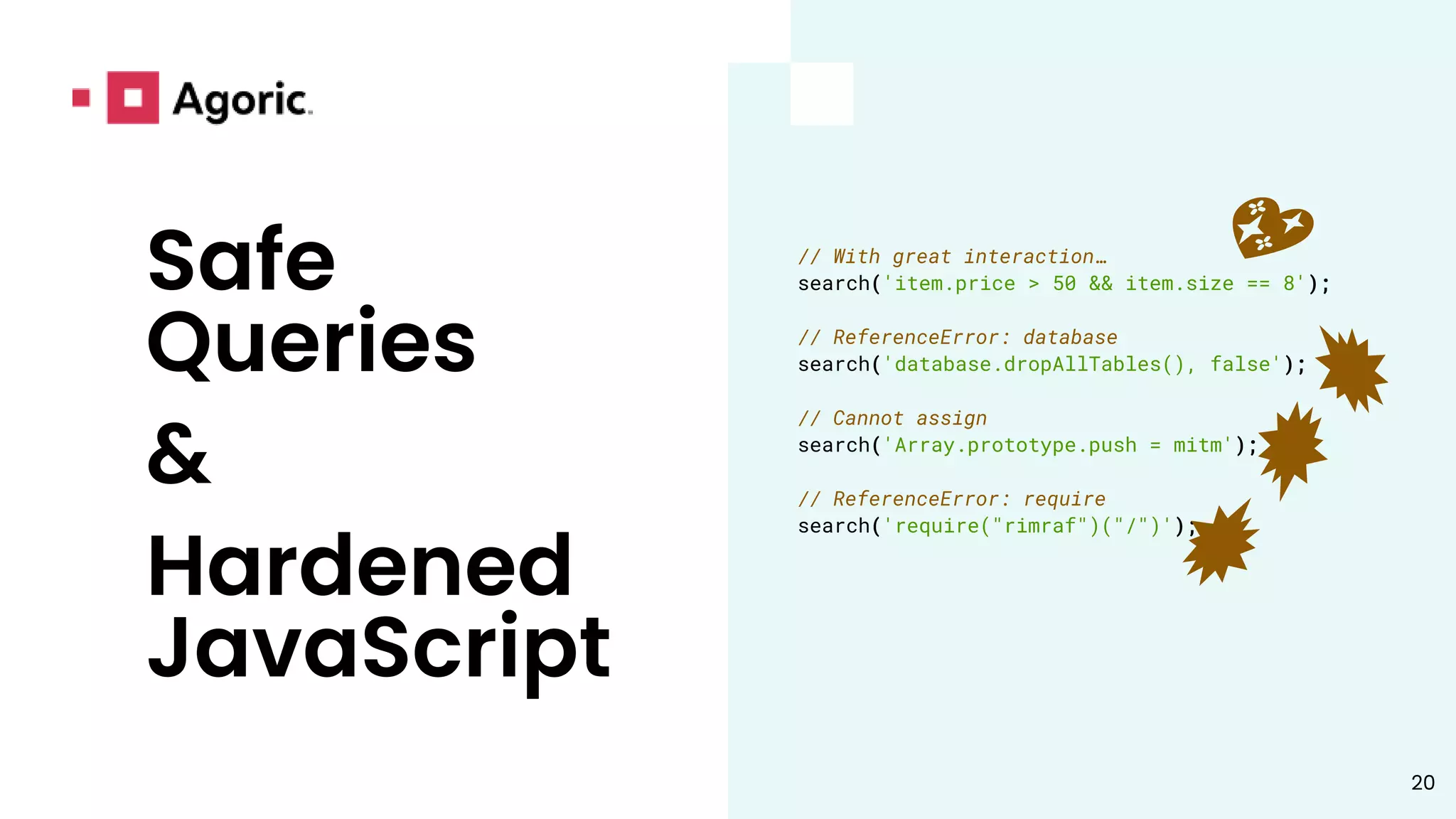
// With great interaction…
search('item.price > 50 && item.size == 8');
// …comes great vulnerability.
search('database.dropAllTables(), false');](https://image.slidesharecdn.com/hardenedjavascript20213-220131060233/75/Hardened-JavaScript-8-2048.jpg)




![17
📦 Compartment
lockdown();
const compartment = new Compartment({ console });
harden(compartment.globalThis);
compartment.evaluate('console.log("Hello, World!");');
compartment.evaluate(`eval("console.log('Hi');")`);
compartment.evaluate('[]') instanceof Array; // totally
compartment.evaluate('{}') instanceof Object; // exactly
compartment.evaluate('globalThis') !== globalThis; // unique!
compartment.evaluate('Date.now()'); // NaN
compartment.evaluate('new Date()'); // Invalid Date
compartment.evaluate('Math.random'); // undefined](https://image.slidesharecdn.com/hardenedjavascript20213-220131060233/75/Hardened-JavaScript-17-2048.jpg)

![19
lockdown();
const compartment = new Compartment();
harden(compartment.globalThis);
const SafeFunction = compartment.globalThis.Function;
const search = harden(query => {
const match = new SafeFunction('item', query);
const matches = [];
for (const item of database.items()) {
if (match(harden(item))) {
matches.push(item);
};
}
return harden(matches);
});
Safe
Queries
&
Hardened
JavaScript](https://image.slidesharecdn.com/hardenedjavascript20213-220131060233/75/Hardened-JavaScript-19-2048.jpg)