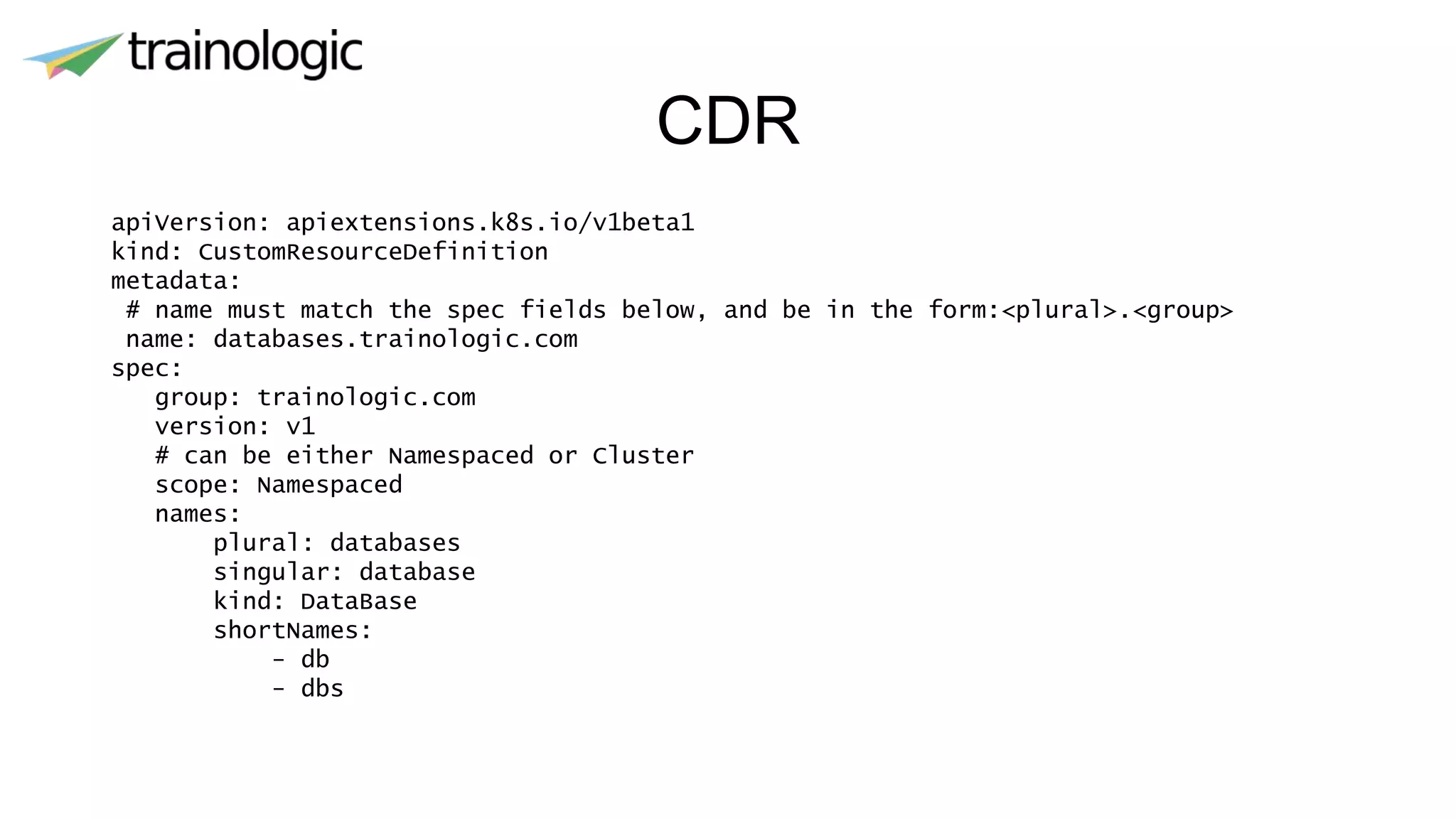
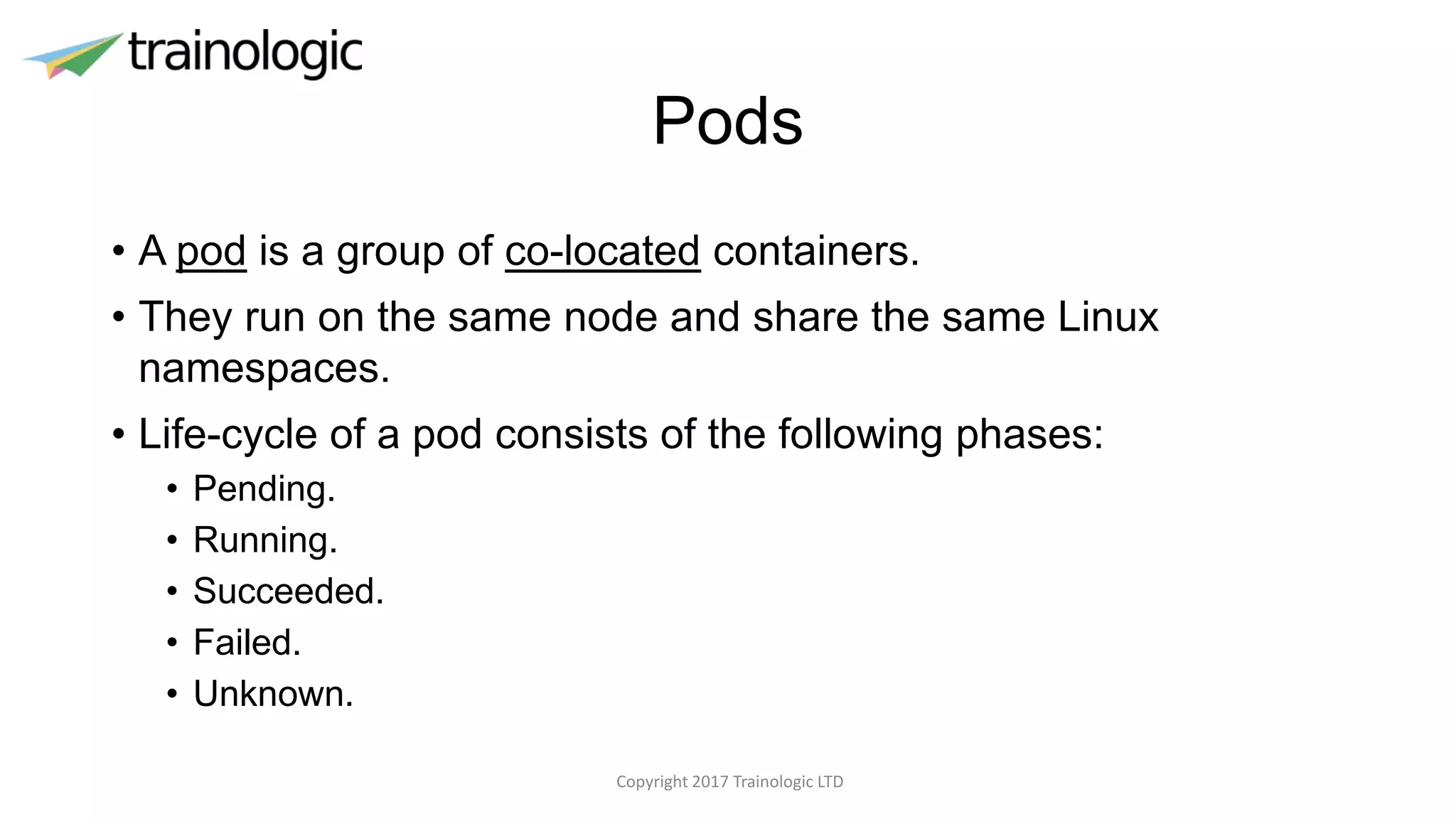
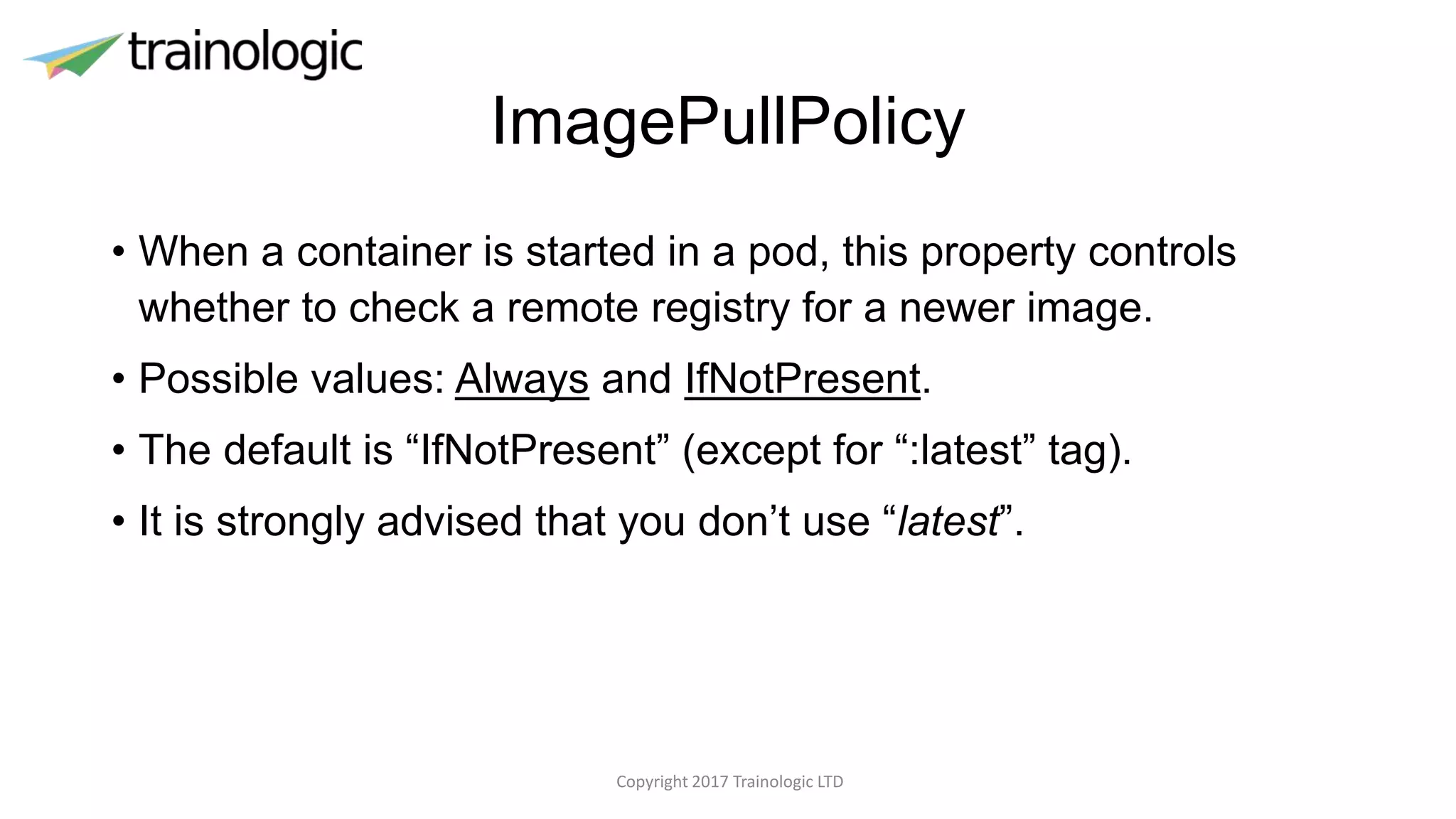
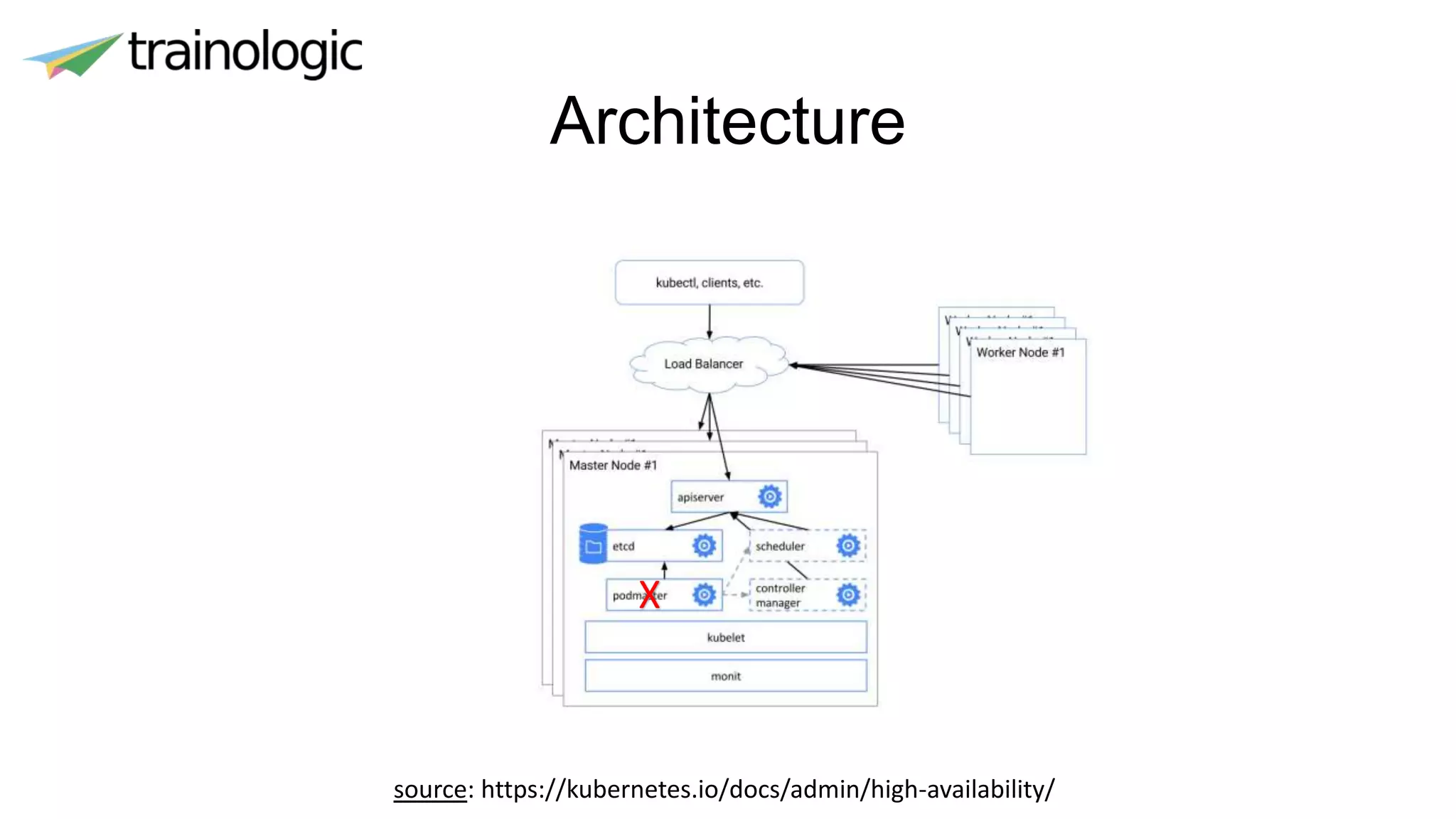
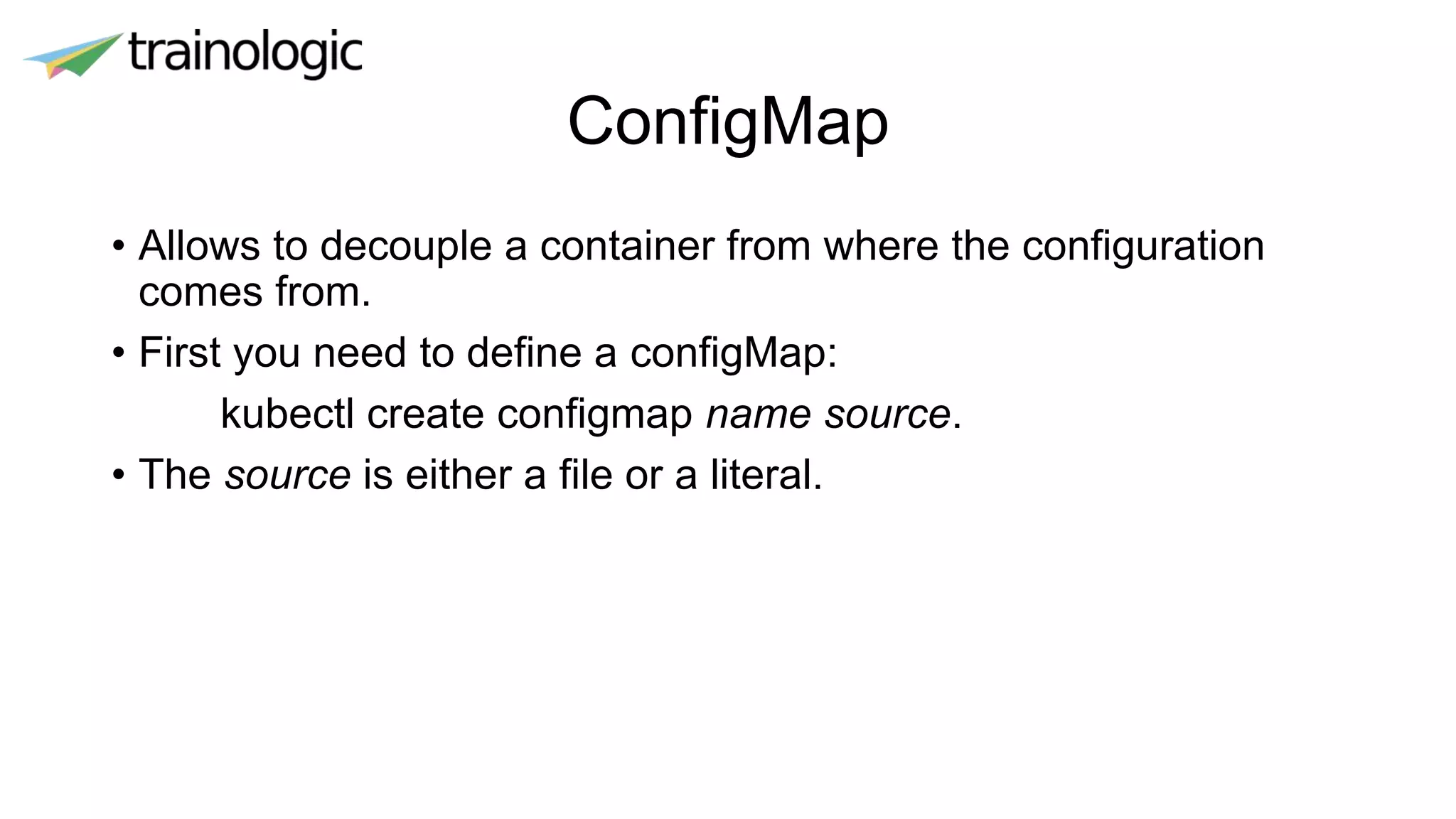
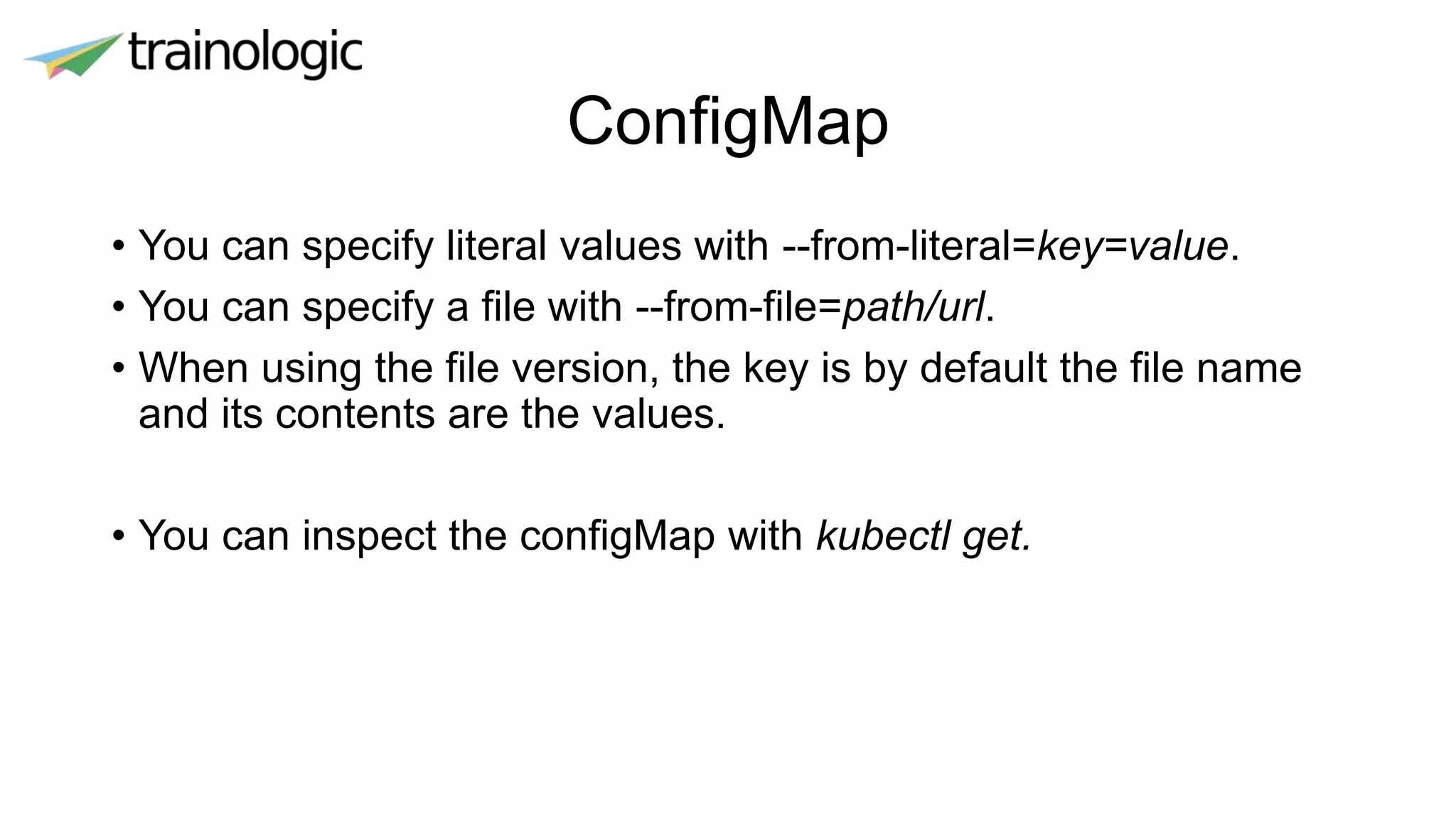
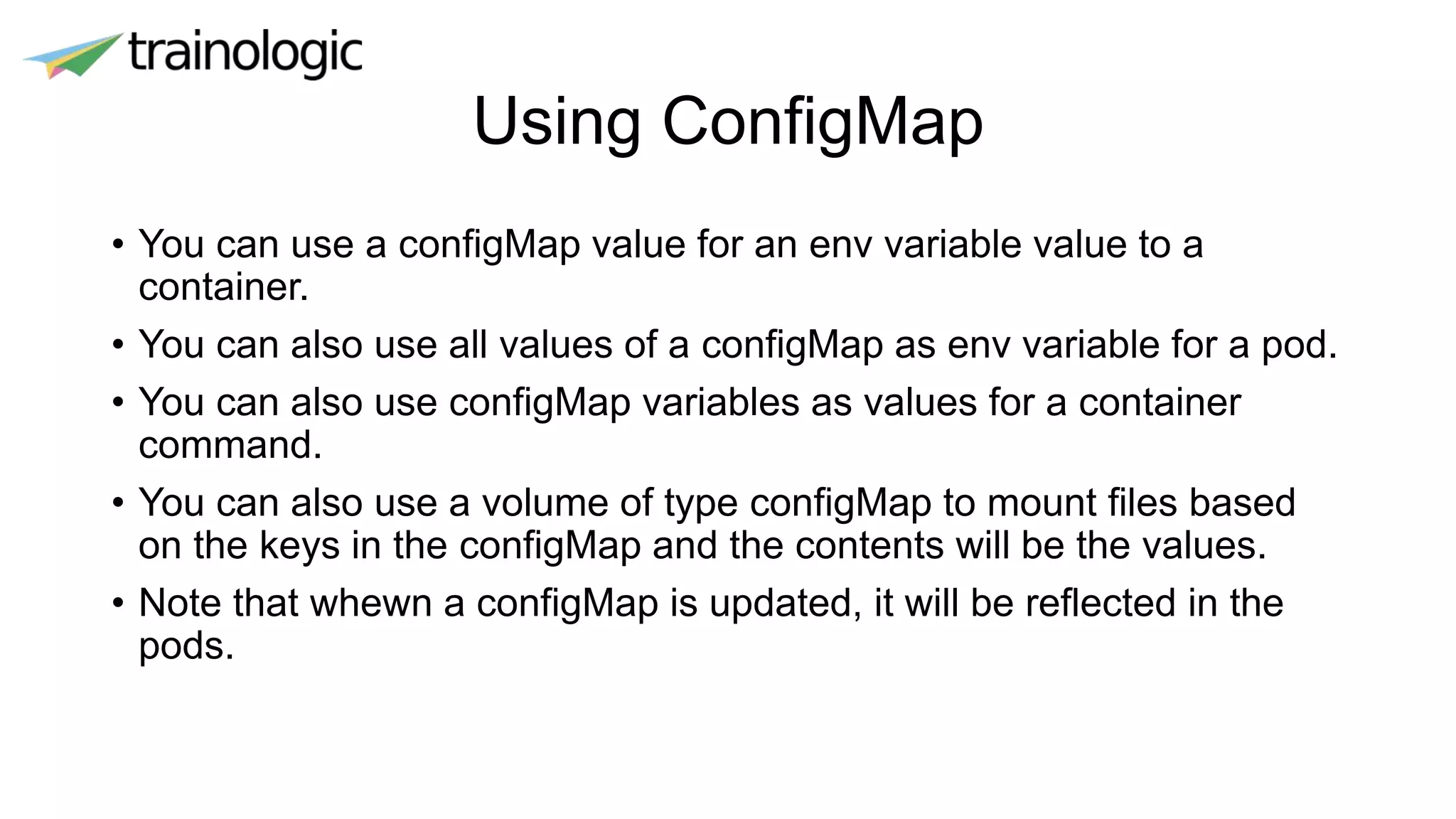
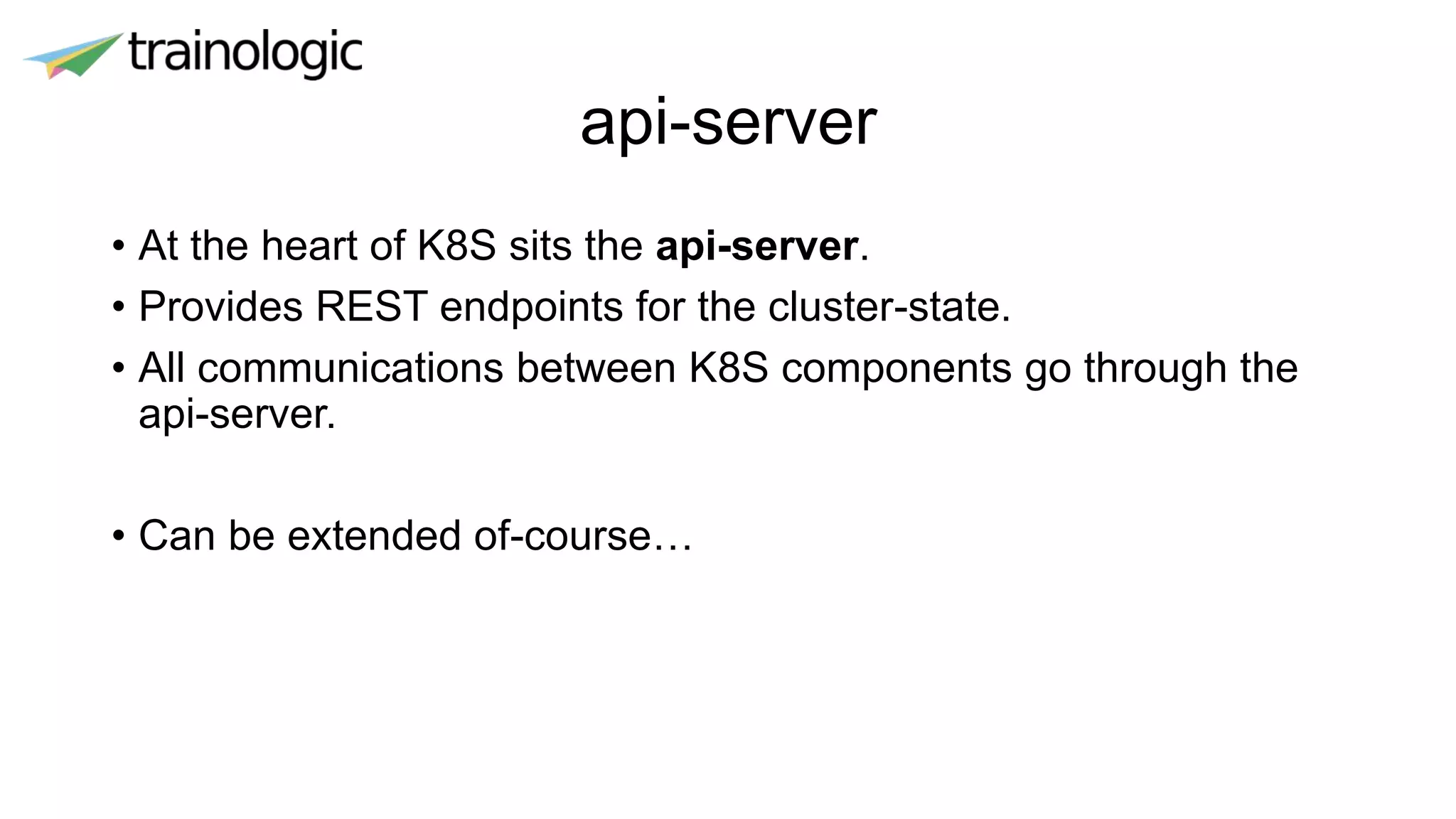
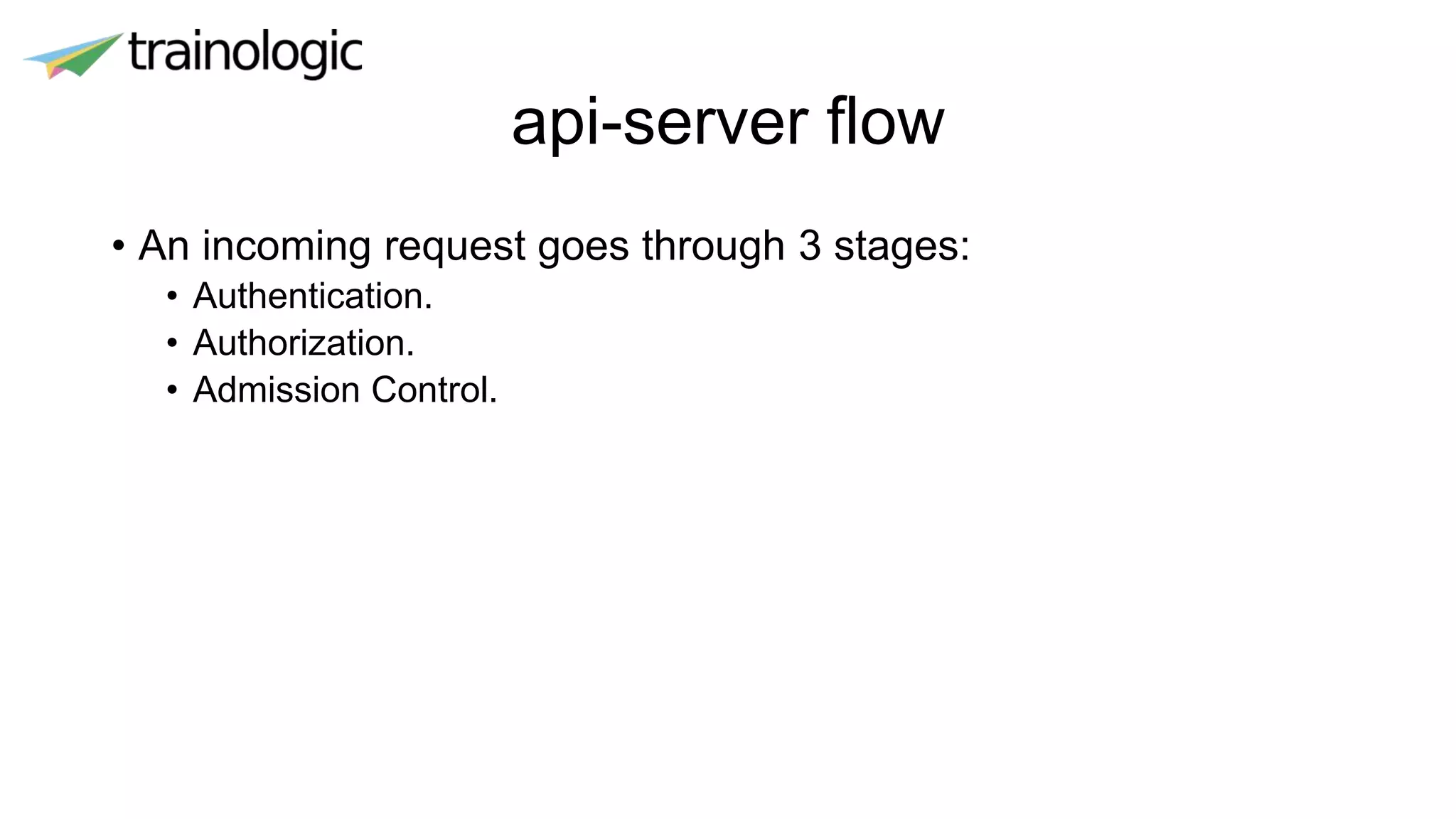
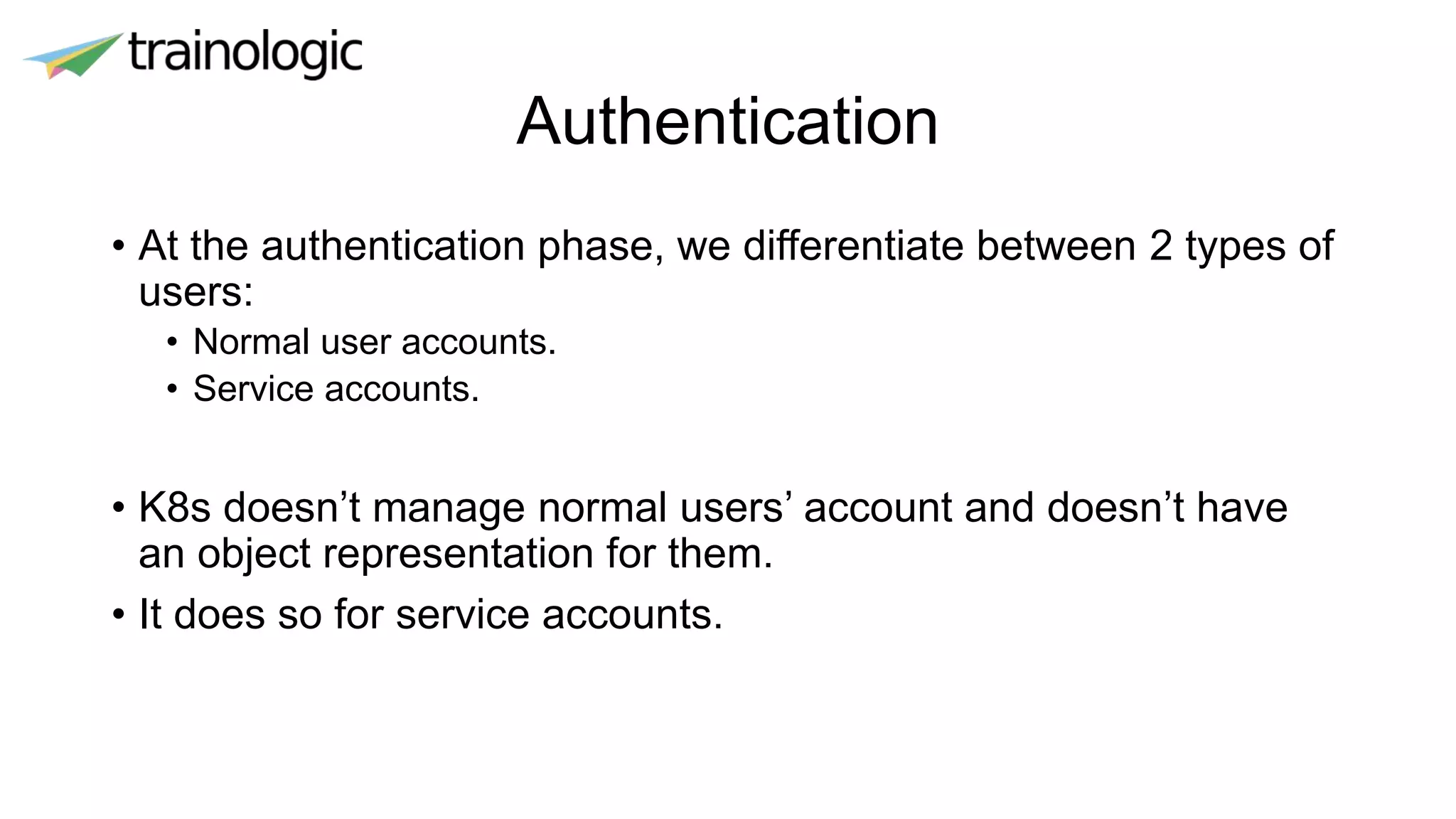
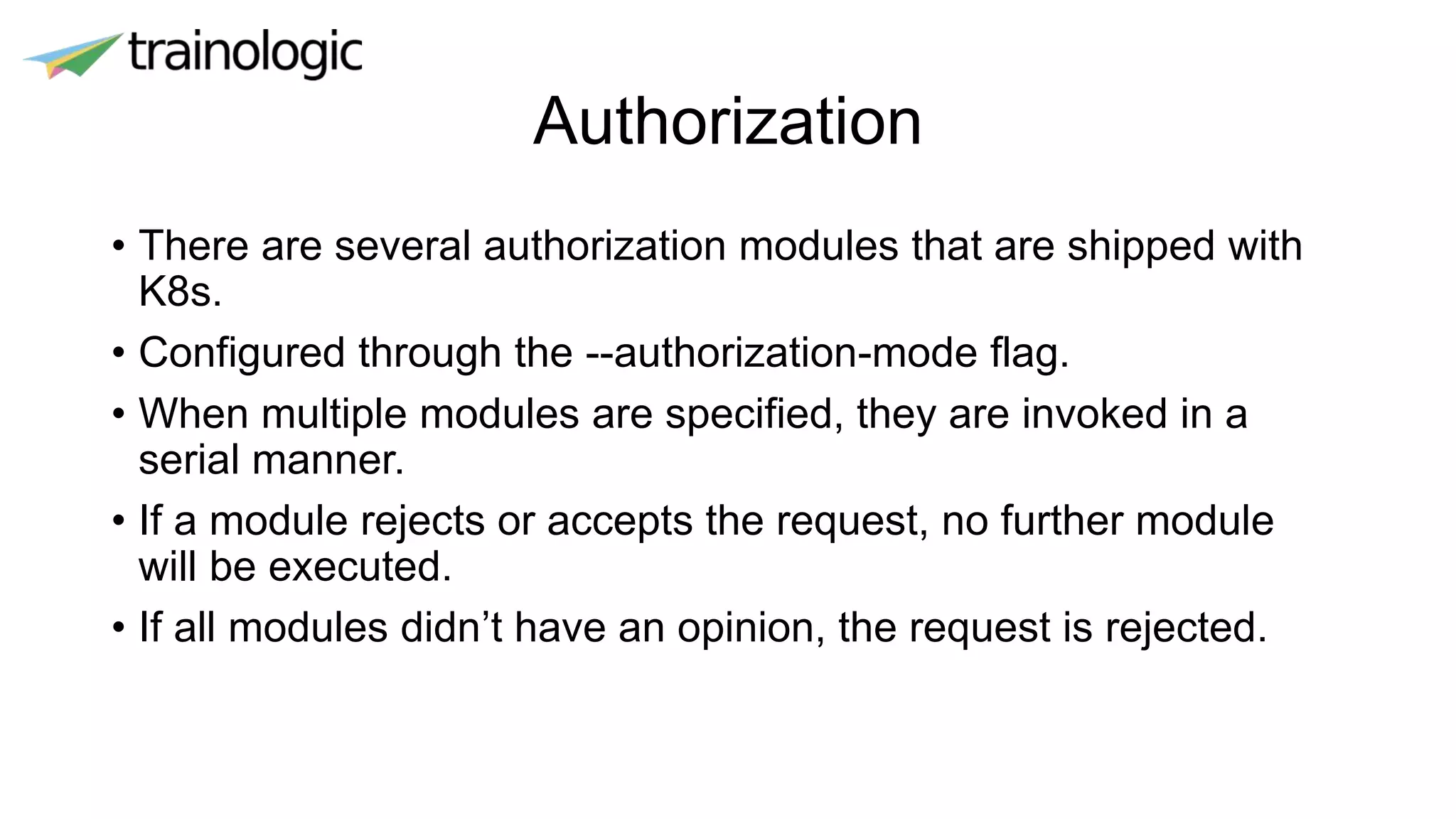
Kubernetes provides logical abstractions for deploying and managing containerized applications across a cluster. The main concepts include pods (groups of containers), controllers that ensure desired pod states are maintained, services for exposing pods, and deployments for updating replicated pods. Kubernetes allows defining pod specifications that include containers, volumes, probes, restart policies, and more. Controllers like replica sets ensure the desired number of pod replicas are running. Services provide discovery of pods through labels and load balancing. Deployments are used to declaratively define and rollout updates to replicated applications.

































![Roles & ClusterRoles
• Role objects specify permissions to a single namespace.
• ClusterRole objects specify permissions cluster-wide (across all
namespaces).
• Example:
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: app1
name: default-deployment
rules:
- apiGroups: [”apps"] # "" indicates the core API group
resources: [”deployments"]
verbs: ["get","watch","list”, “create”]](https://image.slidesharecdn.com/k8s-180523062758/75/Kubernetes-Internals-58-2048.jpg)