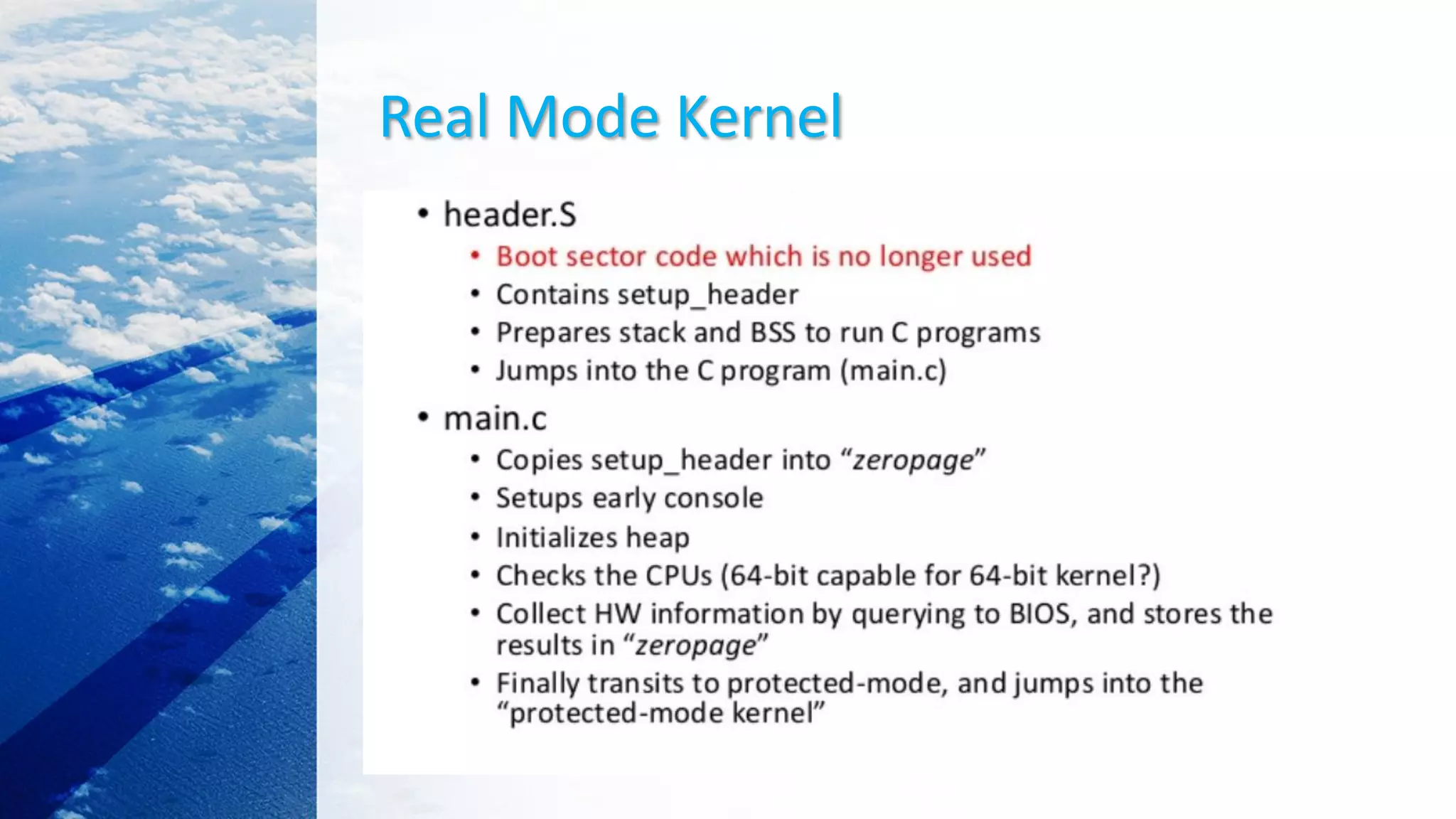
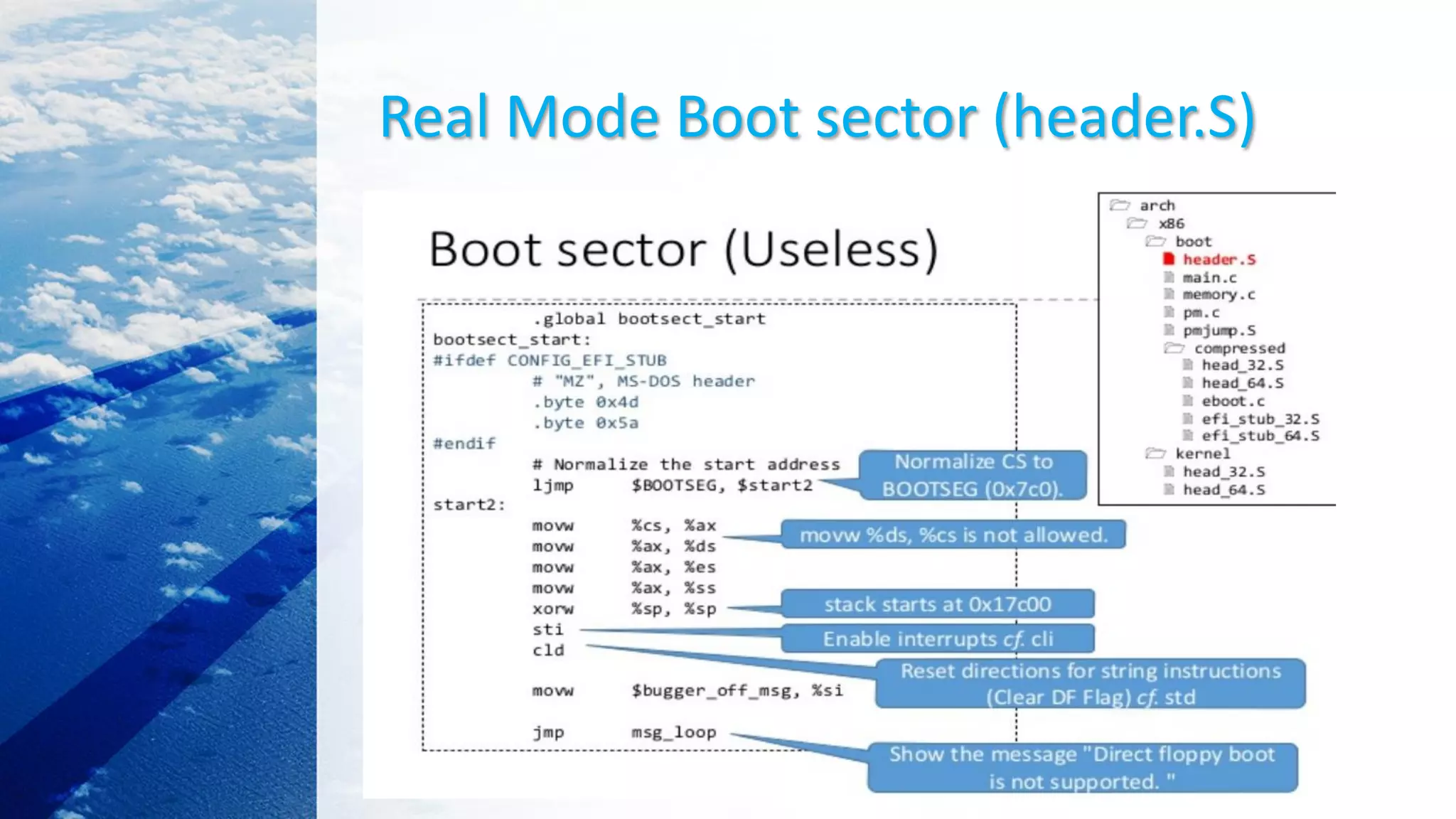
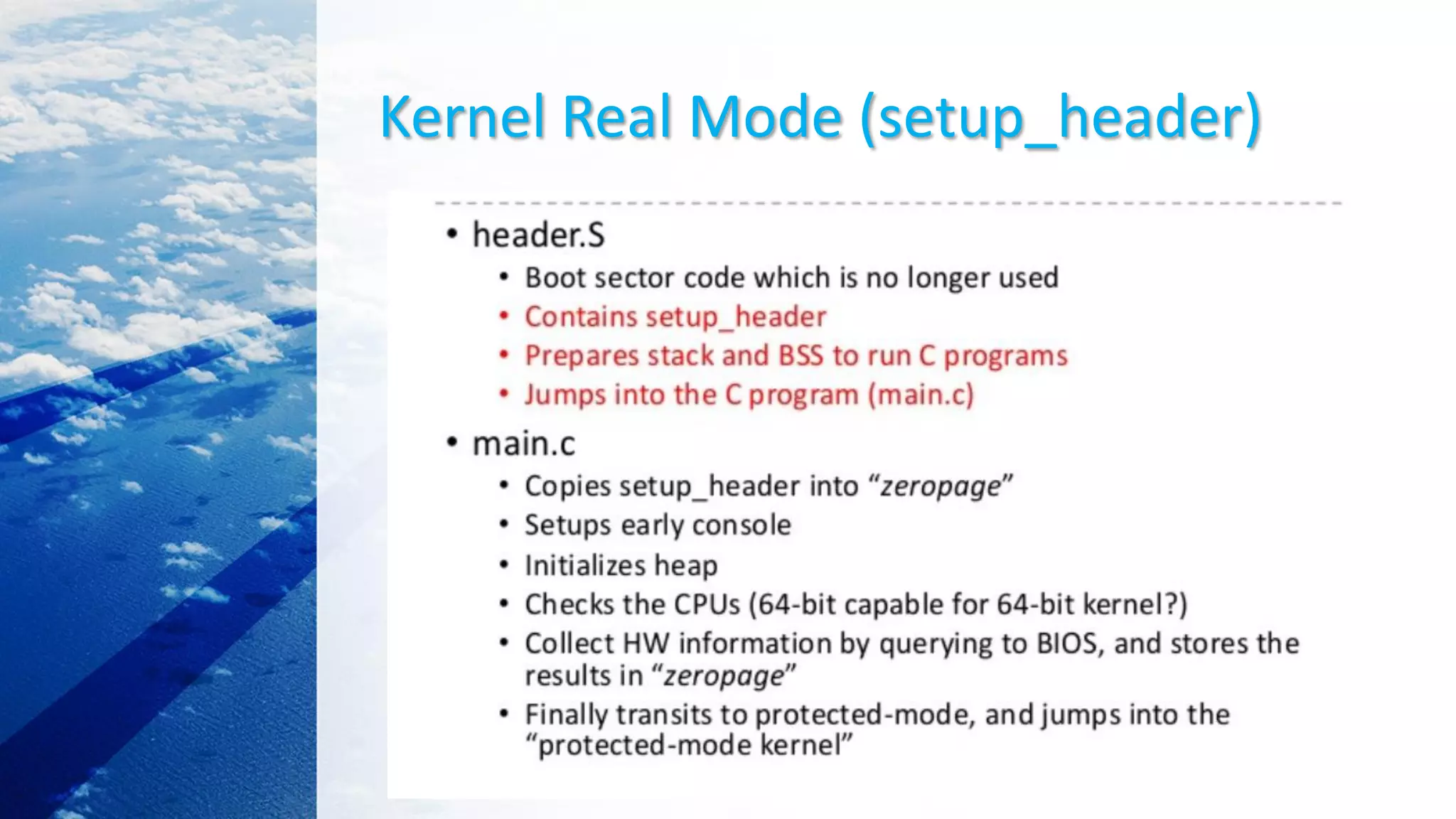
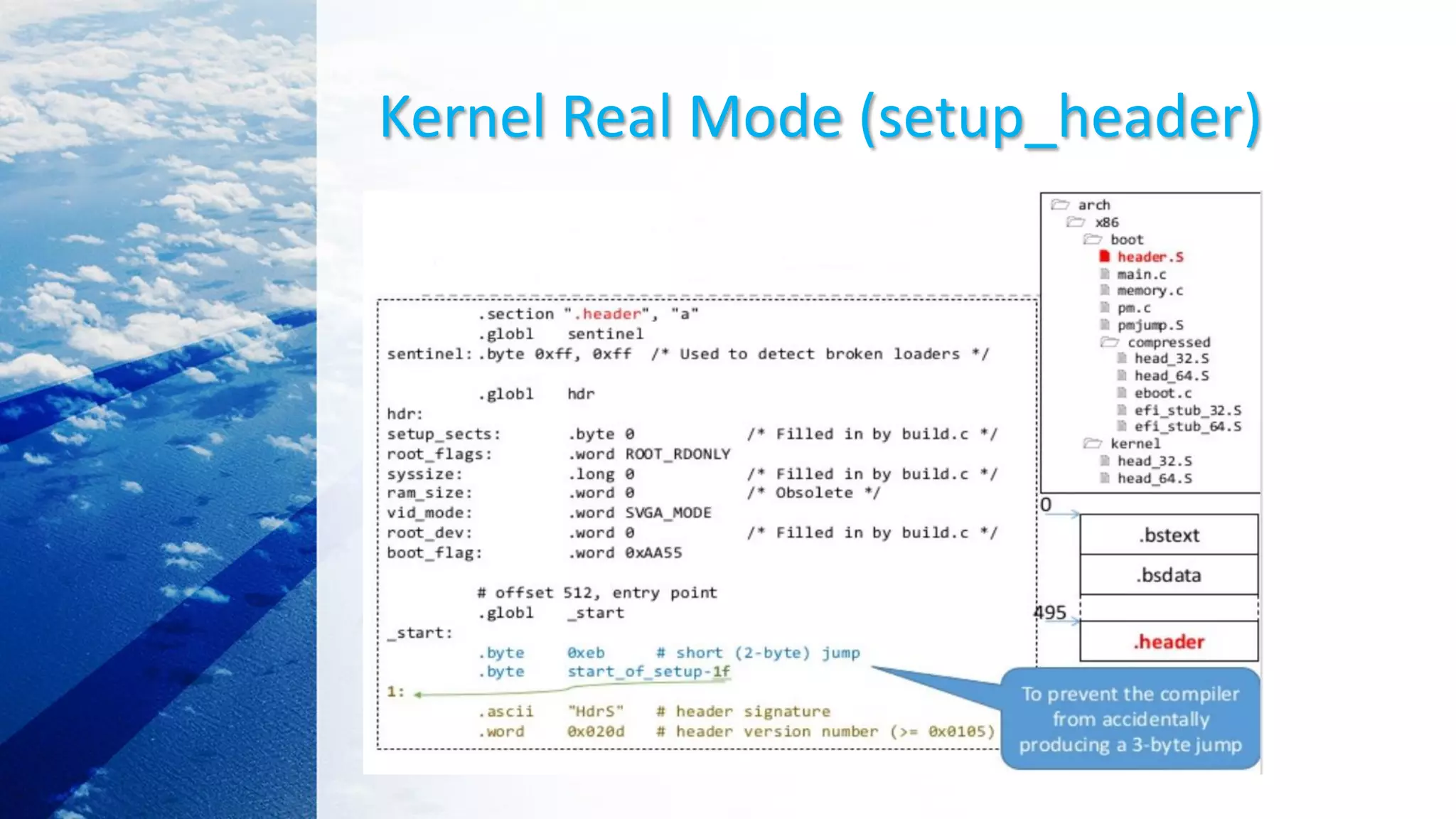
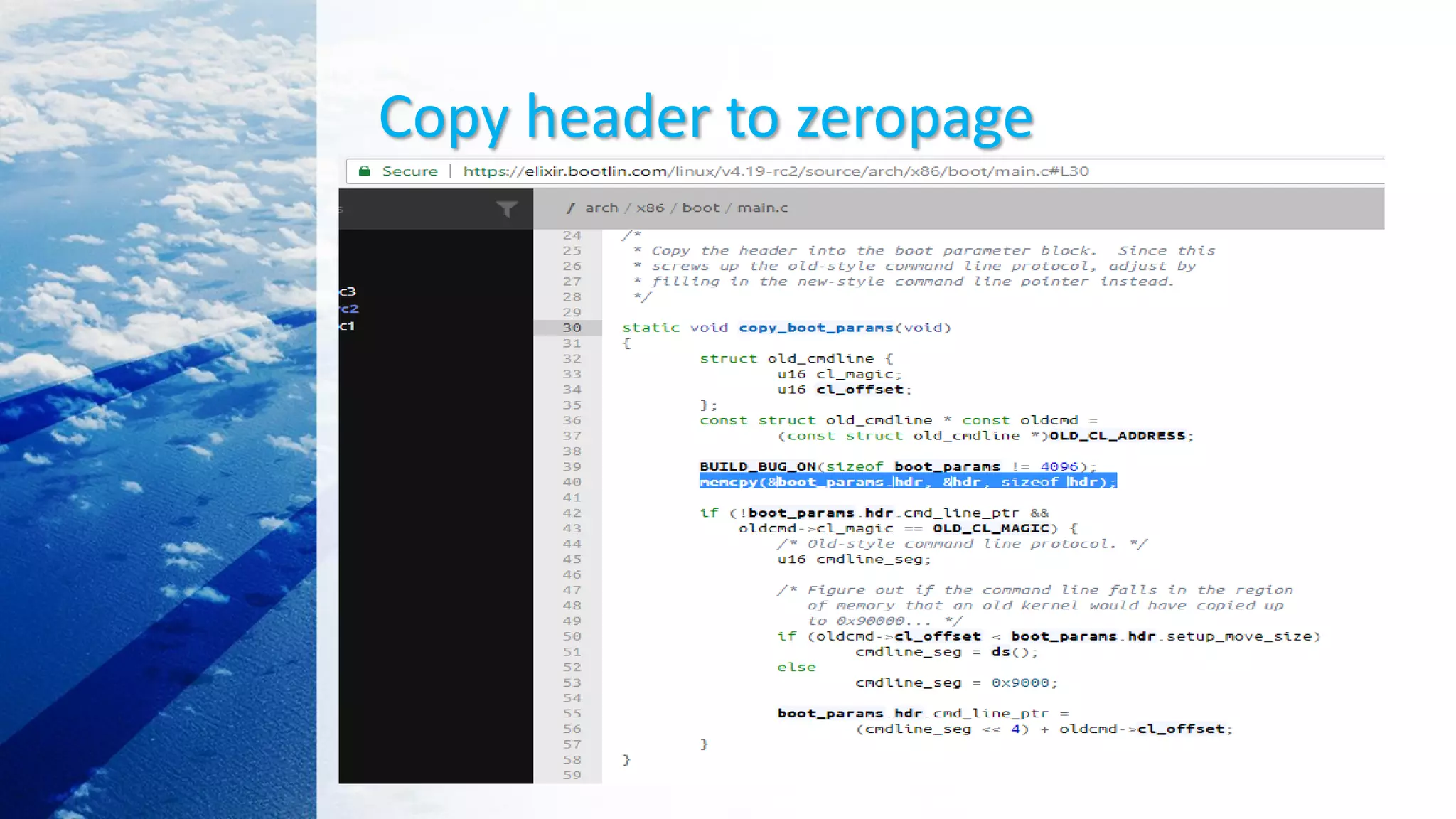
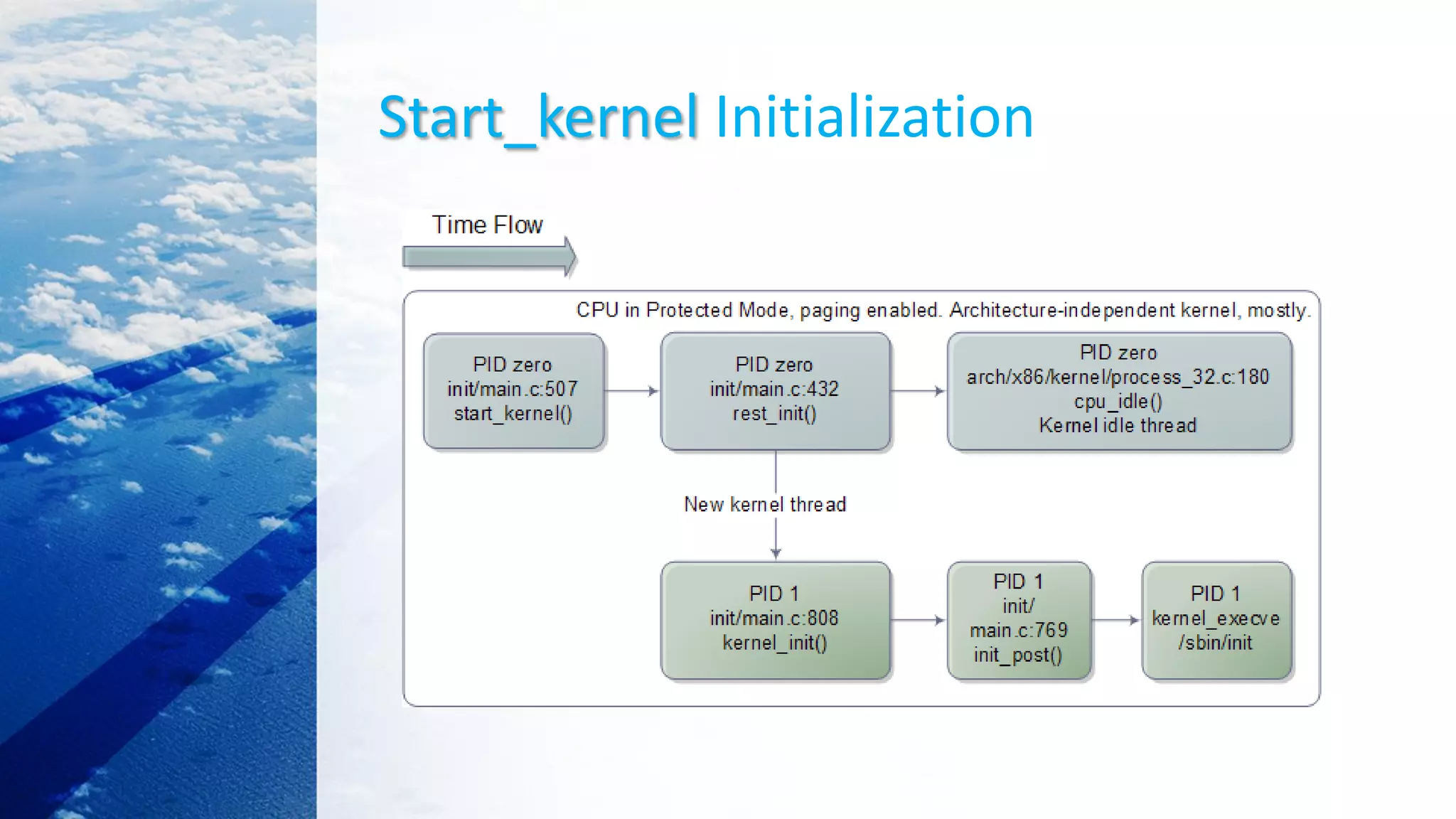
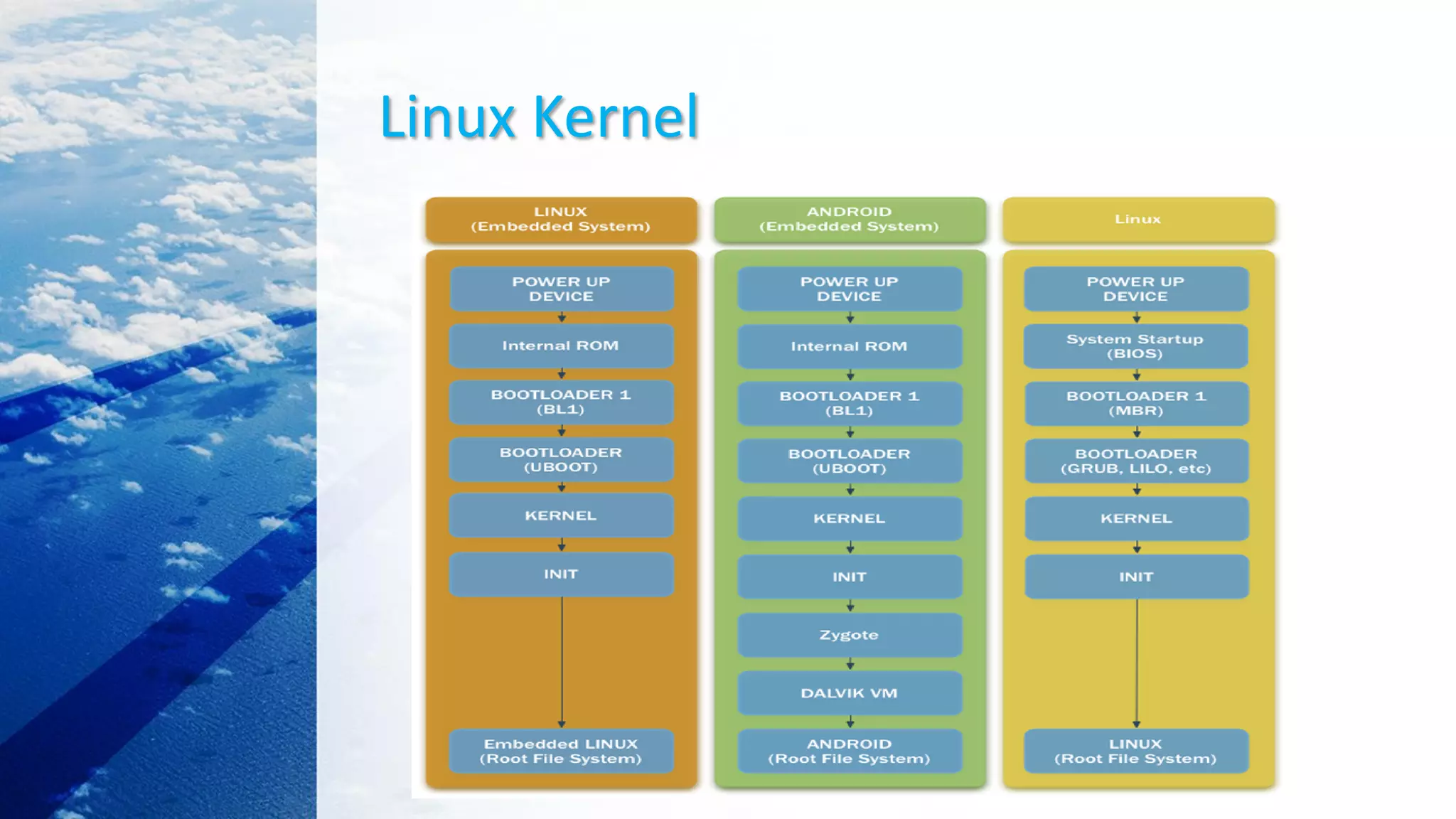
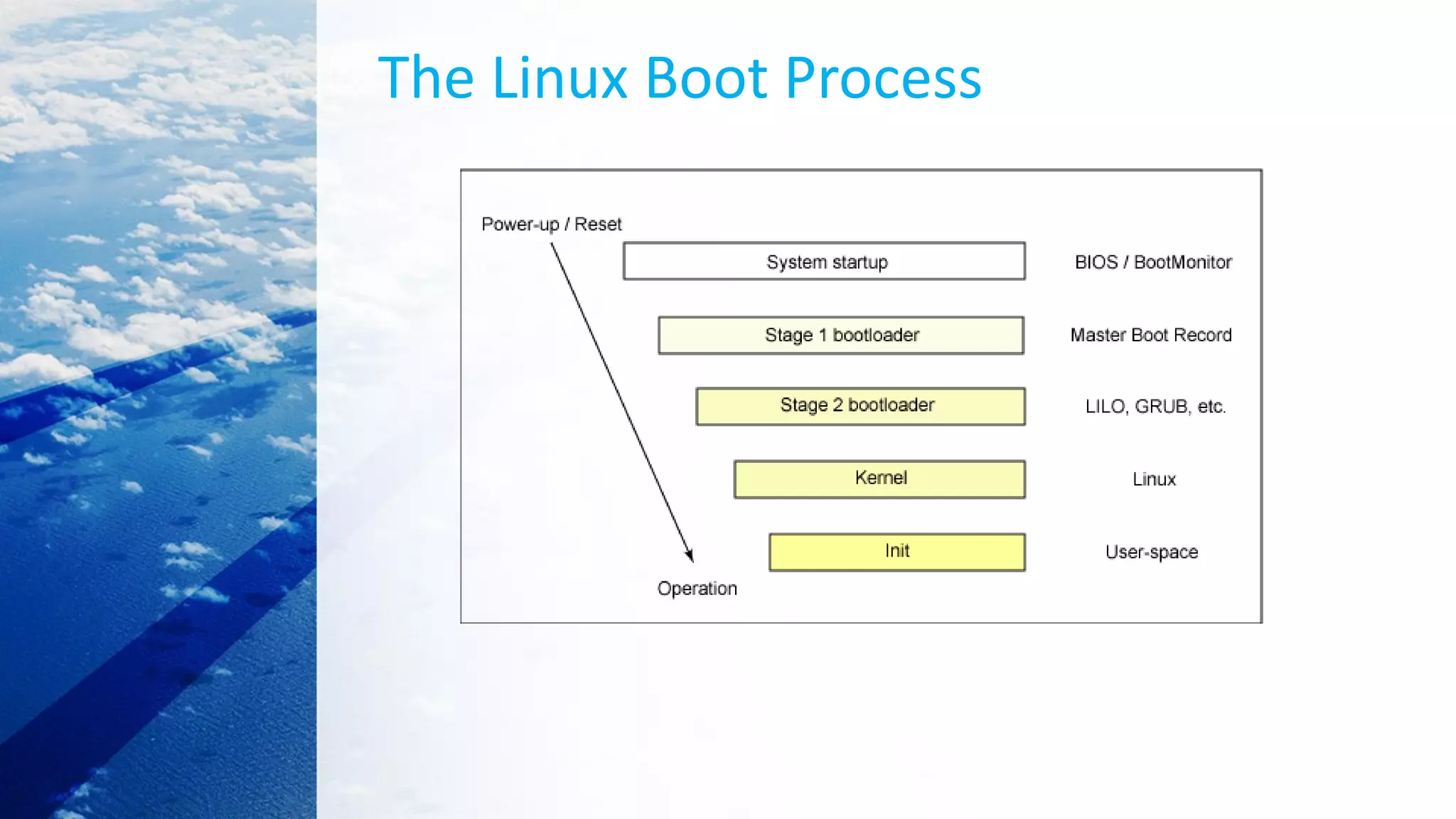
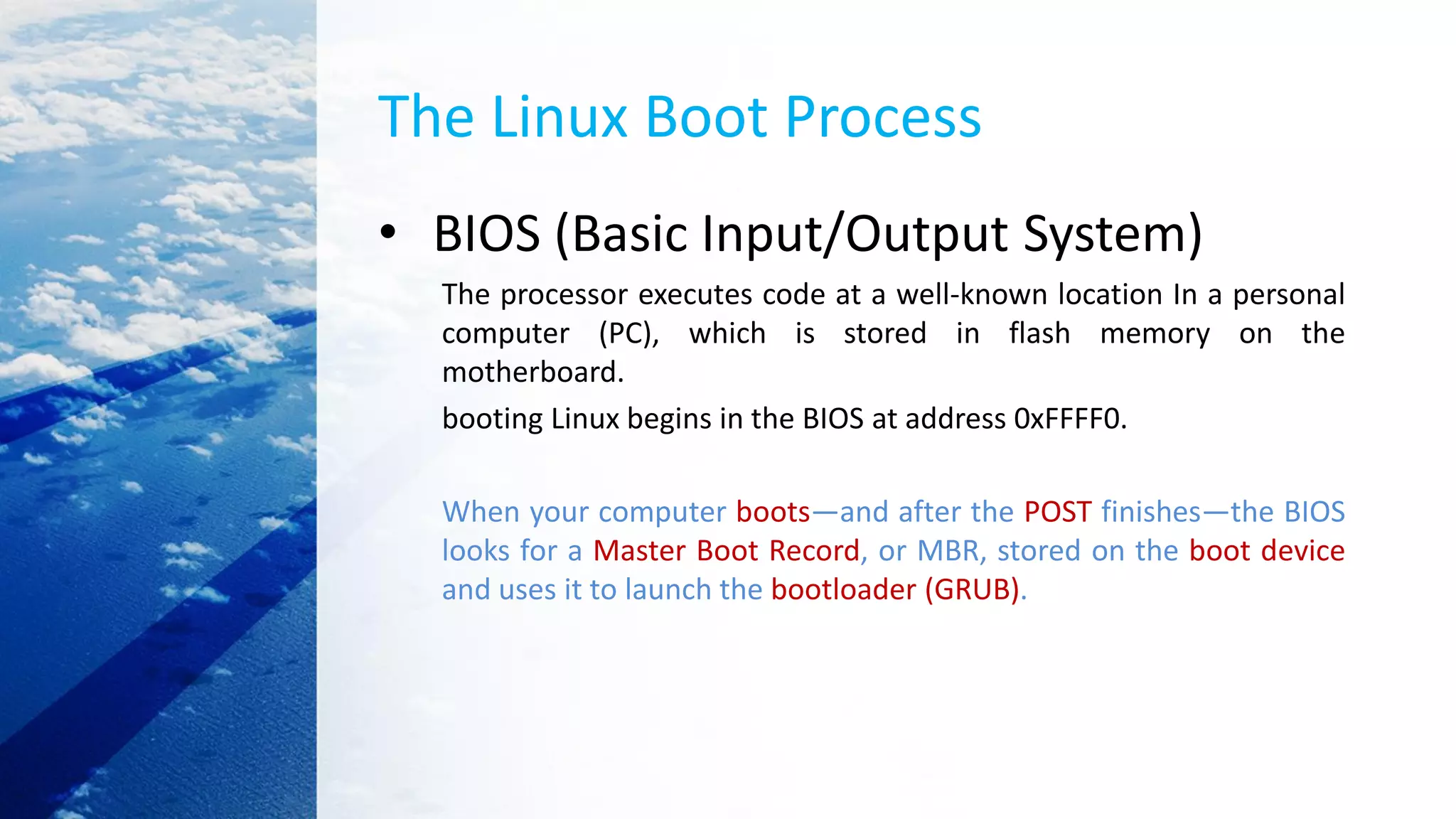
This document provides an overview of the Linux kernel boot process and kernel development. It discusses the BIOS boot process, the Master Boot Record (MBR), bootloaders like GRUB, how the kernel image gets loaded into memory, and the initial kernel initialization in real mode. It also covers kernel architecture, virtual memory initialization, and moving from real mode to protected mode. Additional topics include the Linux kernel source code tree, different kernel architectures, and kernel security issues.






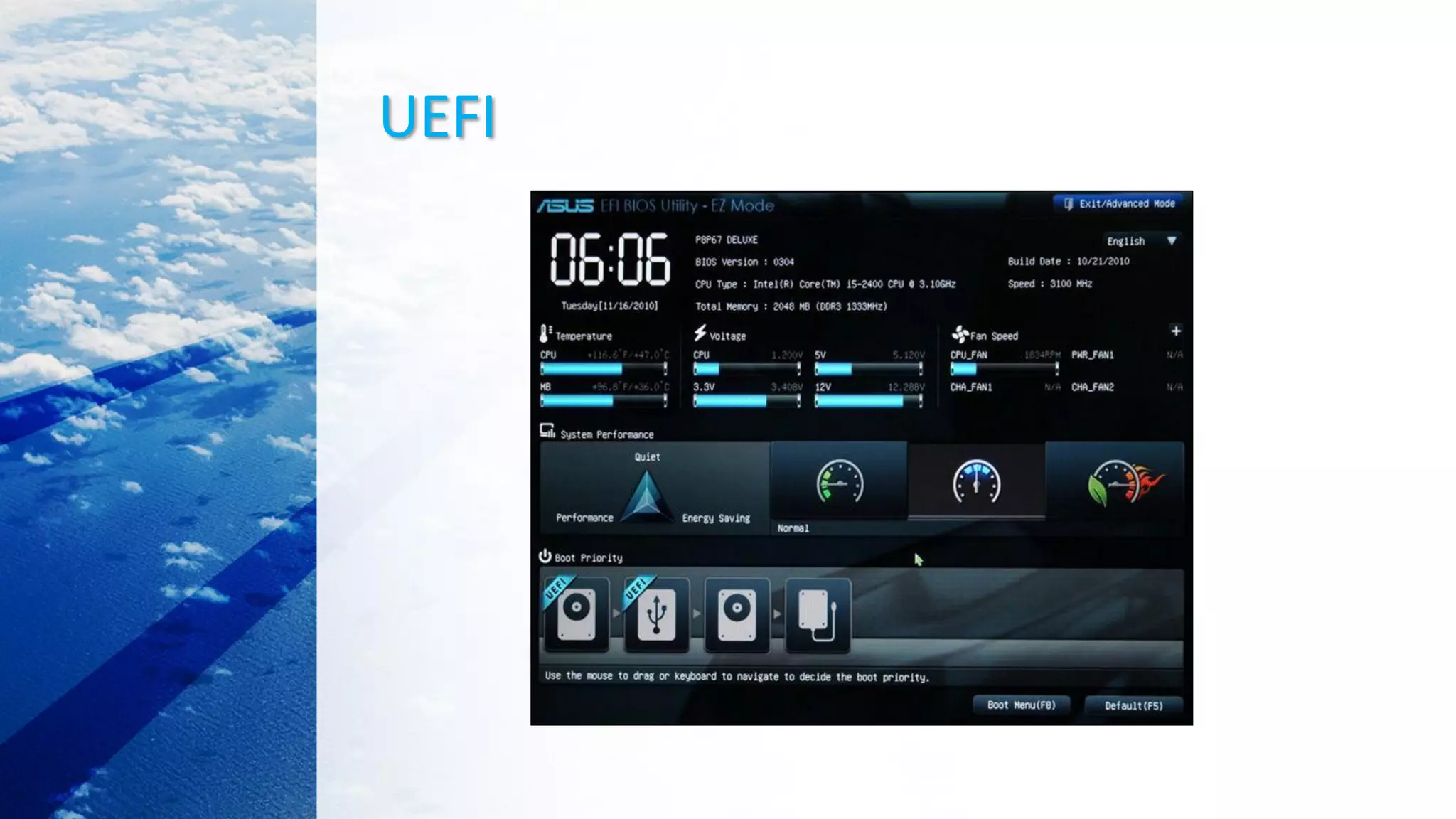
![What is UEFI?
• You need to buy new hardware that supports and includes UEFI.
• UEFI firmware can boot from drives of 2.2 TB or larger.
• UEFI can run in 32-bit or 64-bit mode.
• Your boot process is faster.
• UEFI screens can be slicker than BIOS settings screens, including graphics and
mouse cursor support.
• UEFI supports Secure Boot, which means the operating system can be checked
for validity to ensure no malware has tampered with the boot process.
• UEFI support networking features.
• UEFI is modular.
• Analyzing UEFI BIOSes from attacking [ BH 2014 ]
(https://youtu.be/CGBpil0S5NI)](https://image.slidesharecdn.com/linuxkernelbooting-201030123411/75/Linux-kernel-booting-15-2048.jpg)
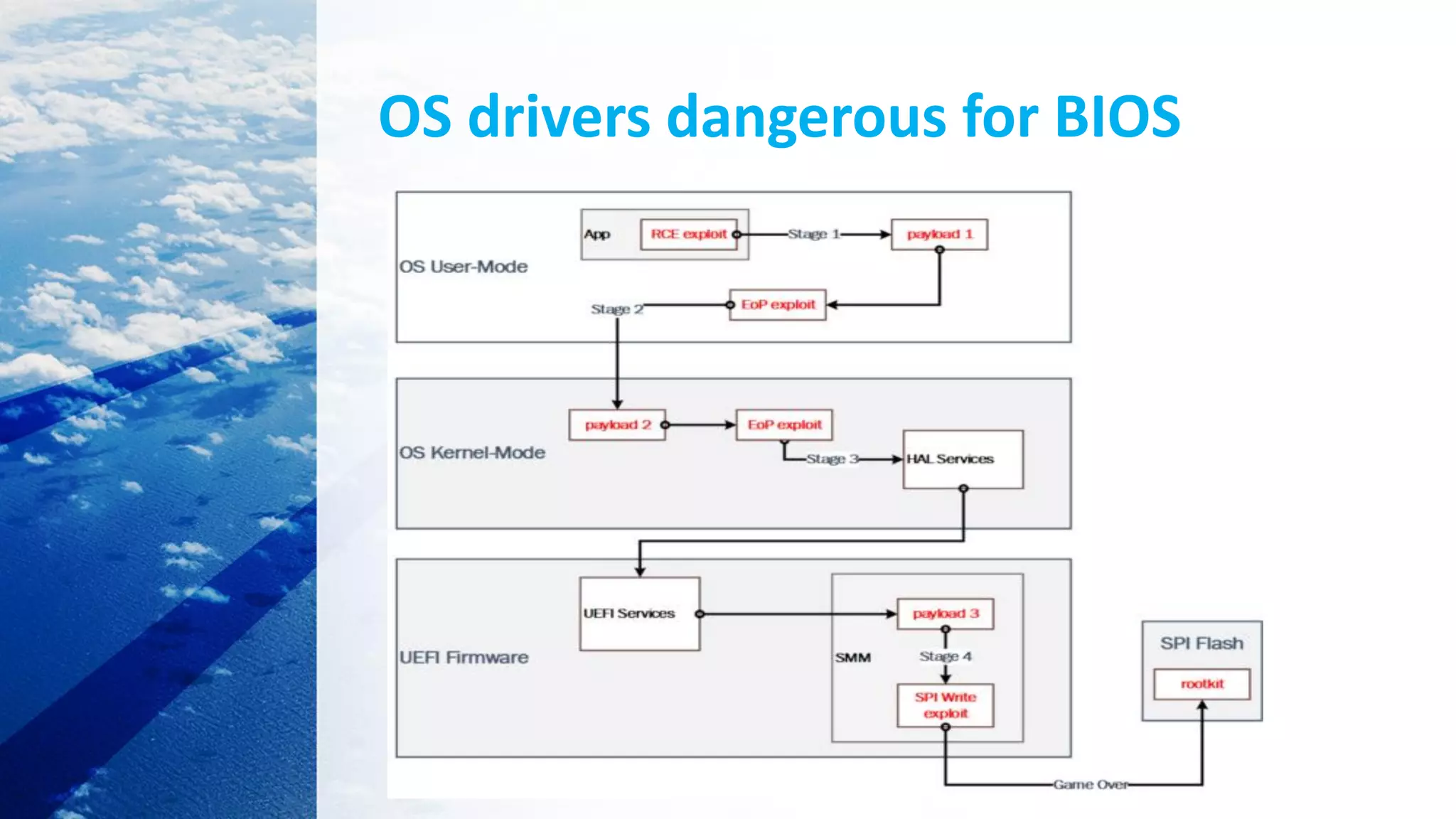
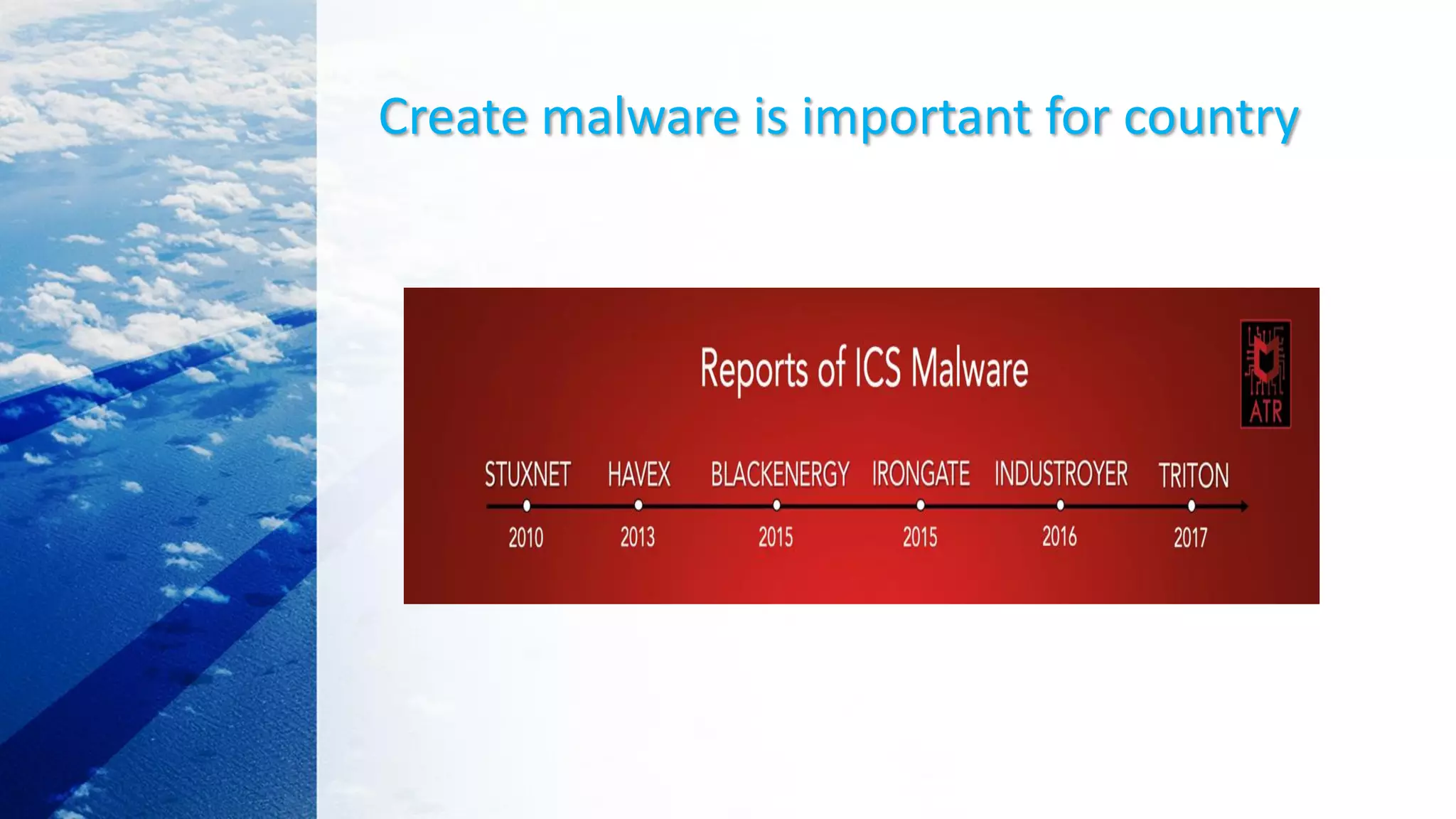

![What Is BootLoader?
• It is the part that starts the system up
and loads the operating system kernel
• Bootloader has two main jobs:
• [1] Initialize the system to a basic level
(MBR) and to [2] Load the kernel.](https://image.slidesharecdn.com/linuxkernelbooting-201030123411/75/Linux-kernel-booting-21-2048.jpg)
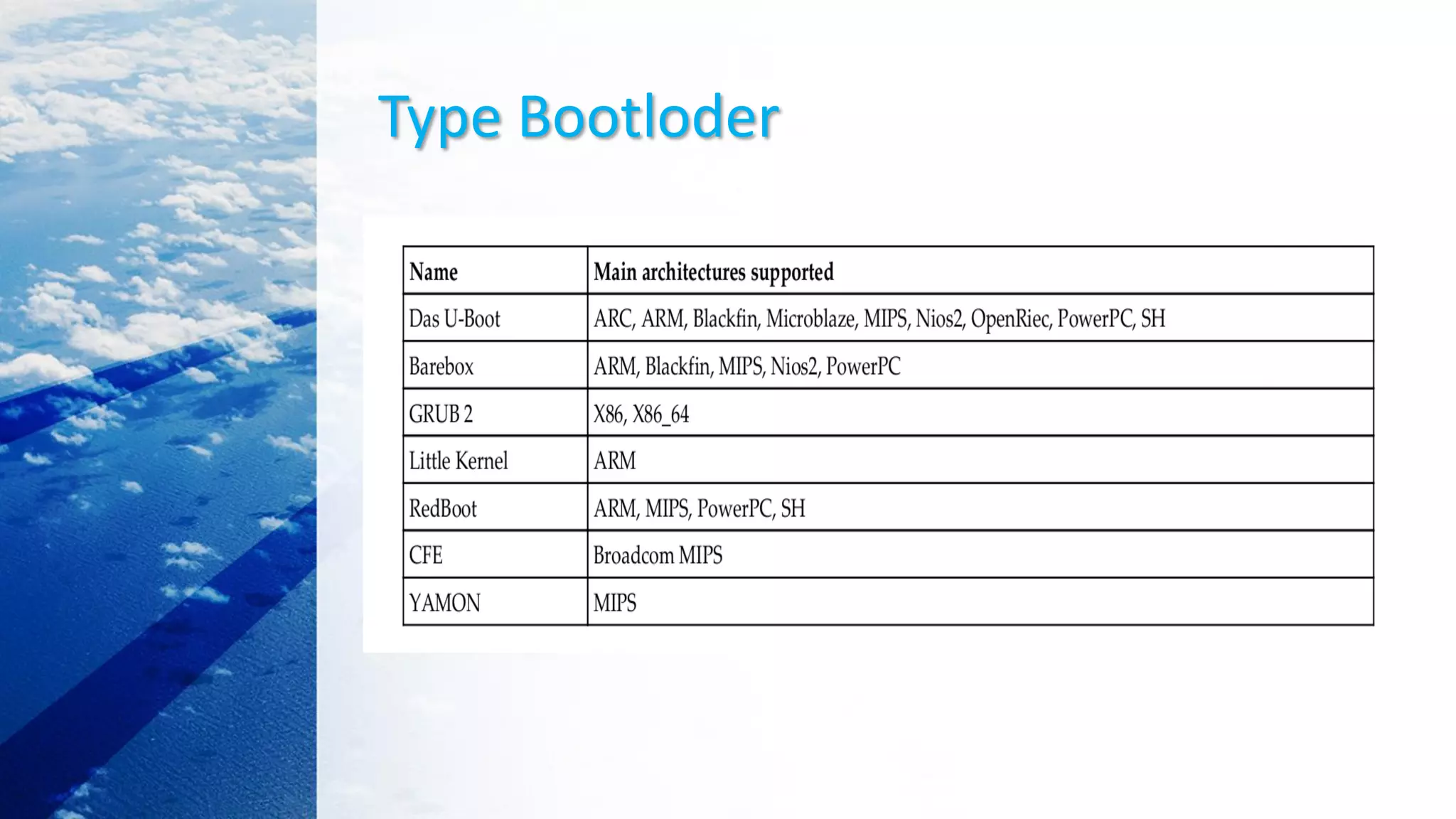


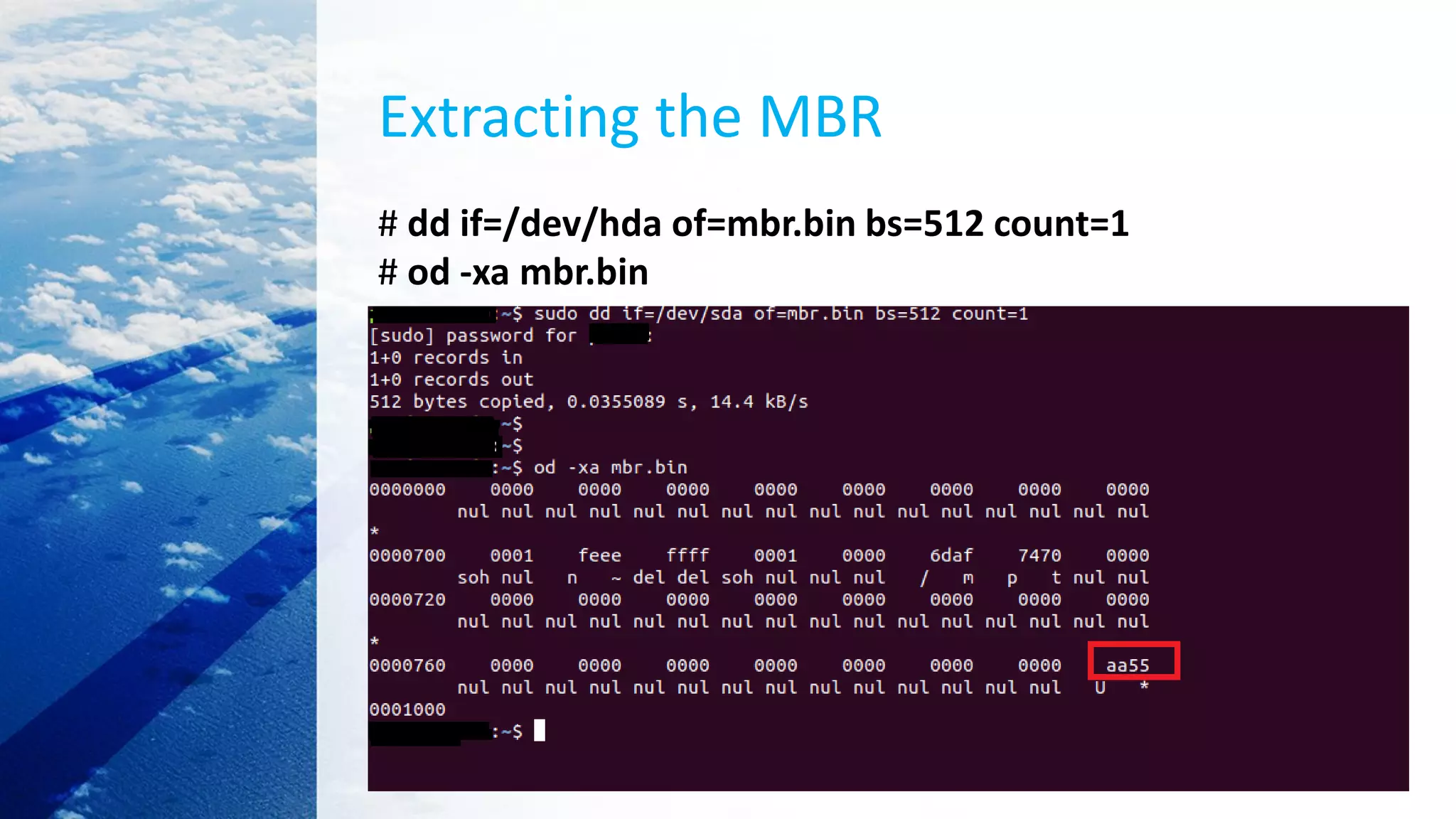


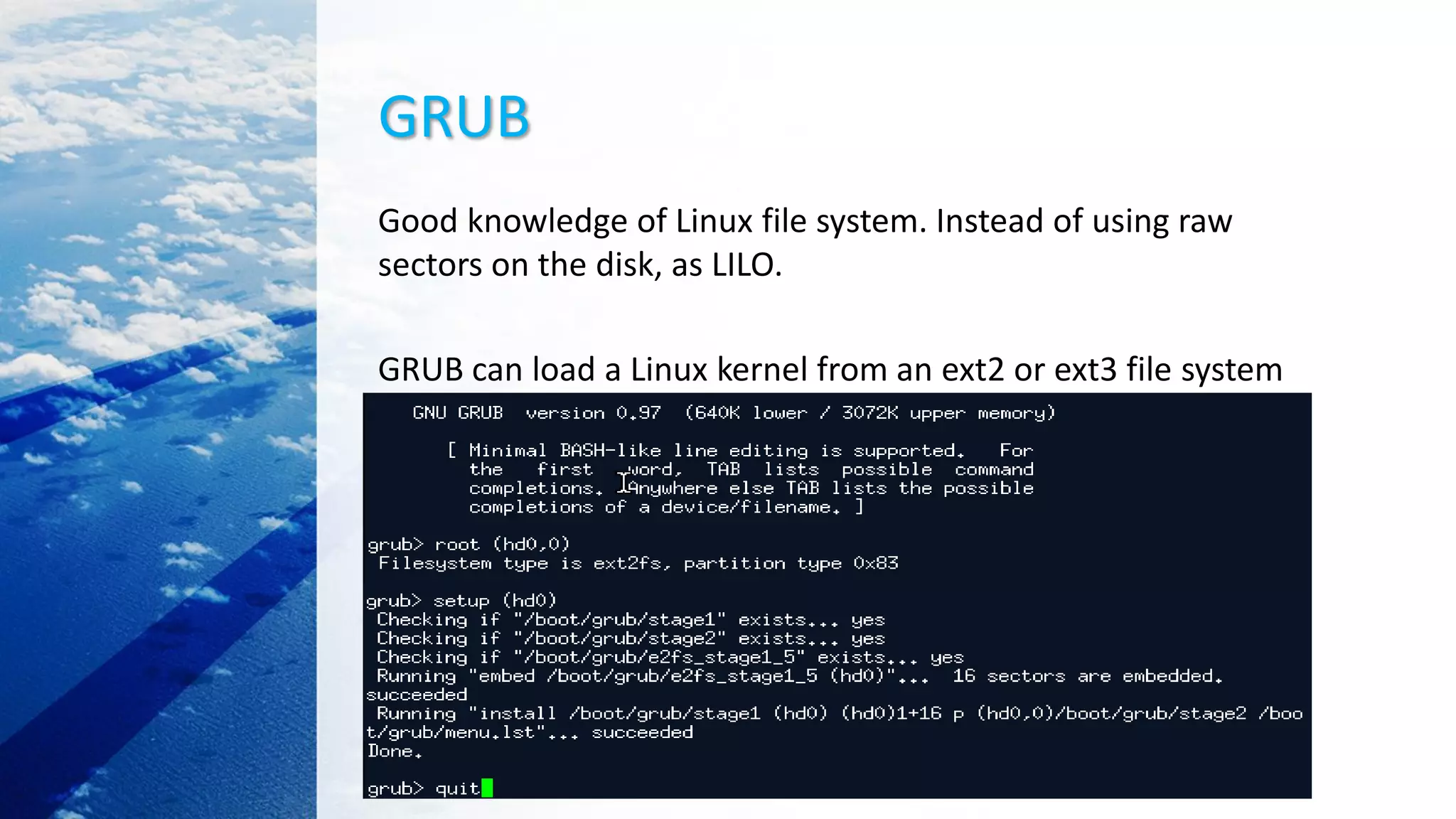
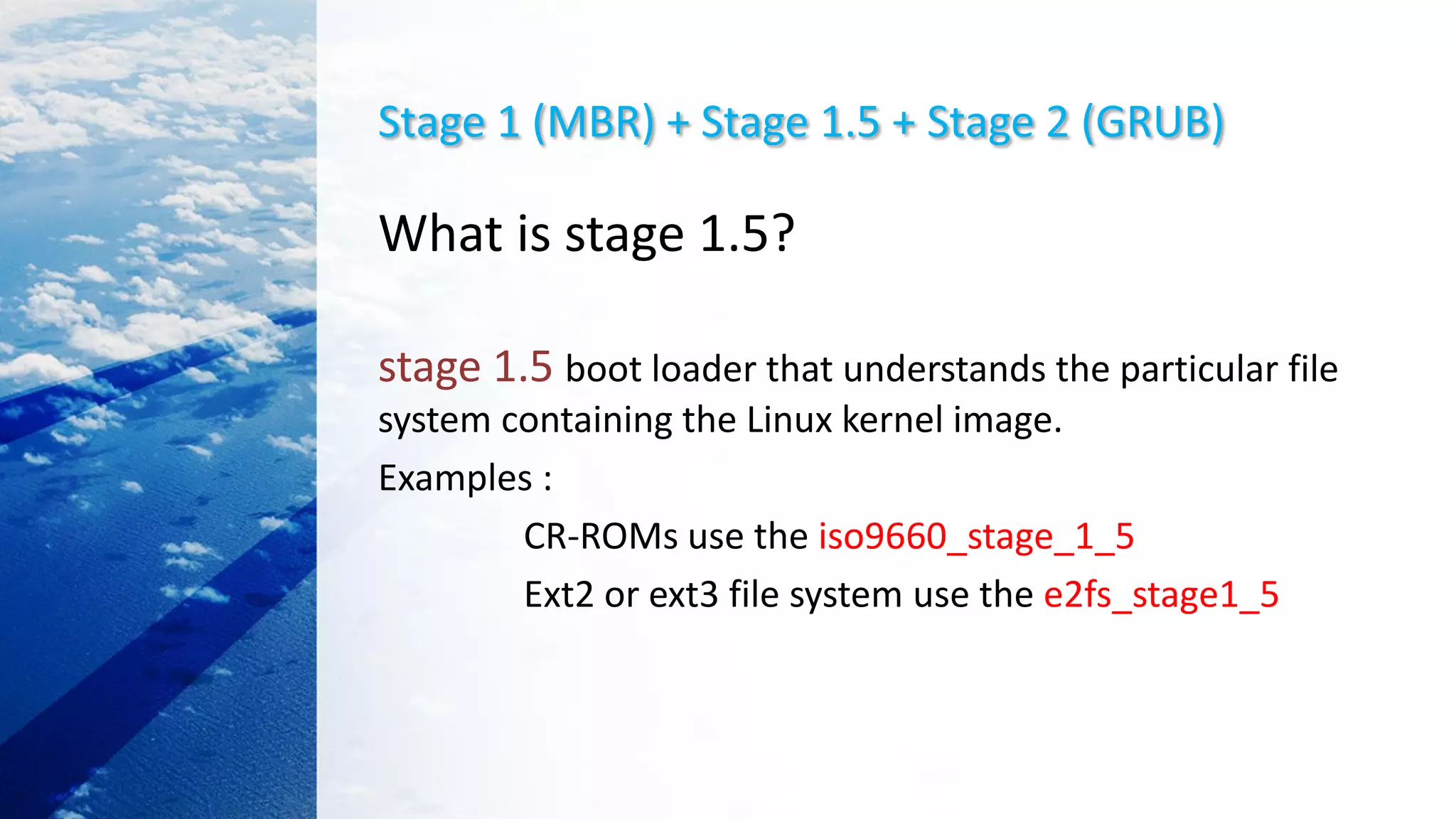
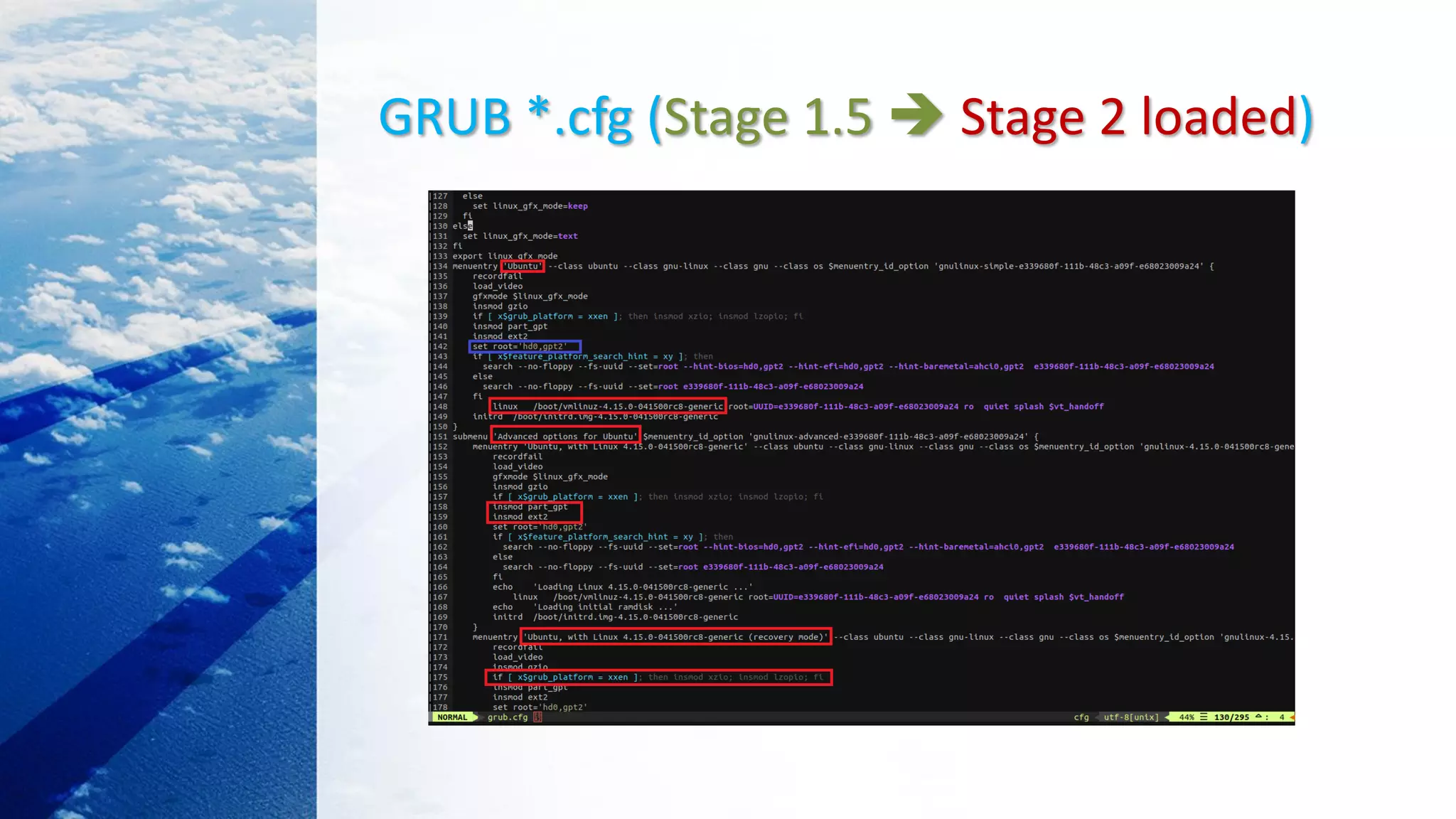

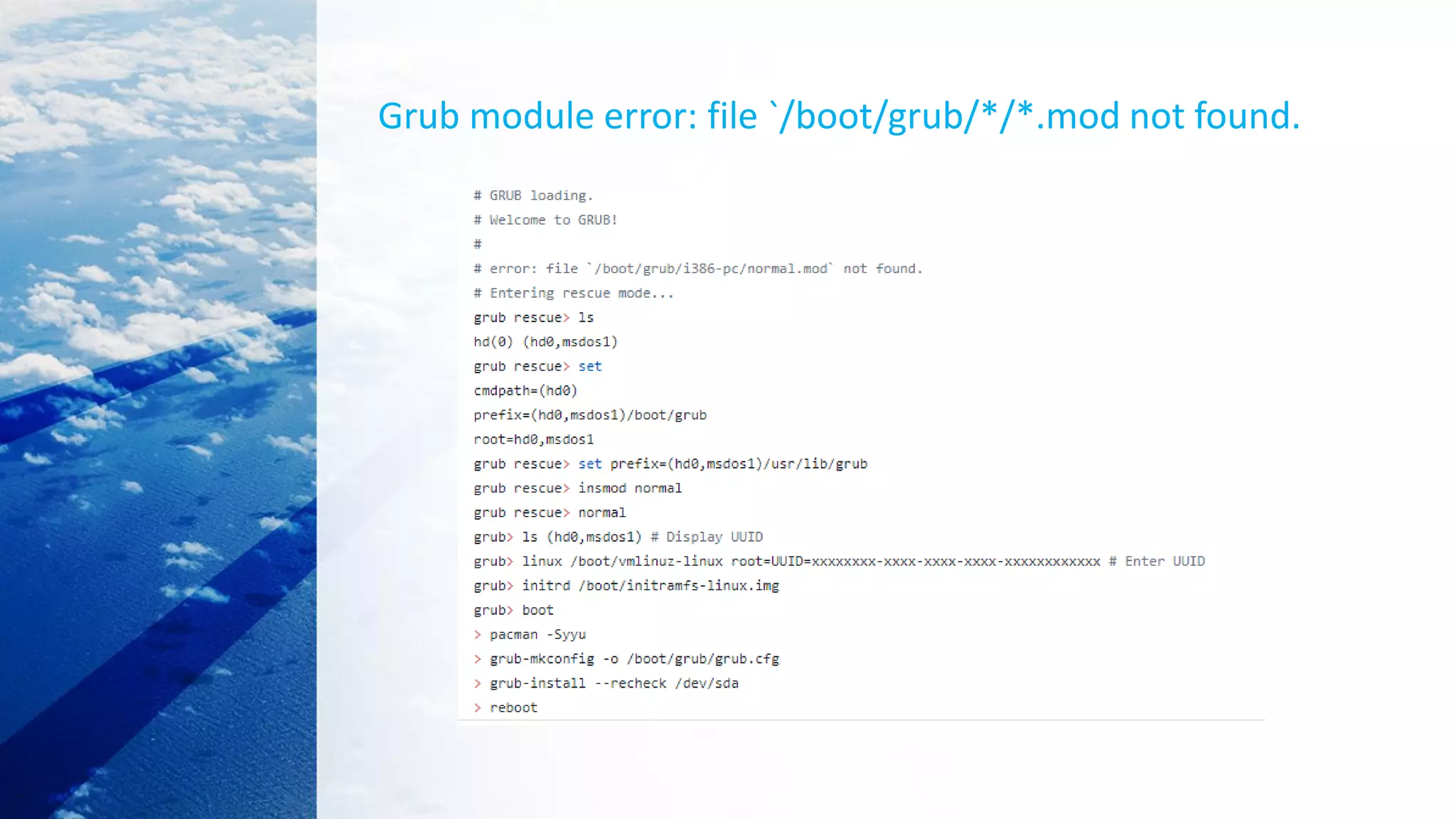
![Load kernel image with GRUB
grub> kernel /bzImage-<version>
[Linux-bzImage, setup=0x1400, size=0x29672e]
grub> initrd /initrd-<version>.img
[Linux-initrd @ 0x5f13000, 0xcc199 bytes]
grub> boot
Uncompressing Linux... Ok, booting the kernel.
Refs install manual : http://tinycorelinux.net/install_manual.html](https://image.slidesharecdn.com/linuxkernelbooting-201030123411/75/Linux-kernel-booting-35-2048.jpg)