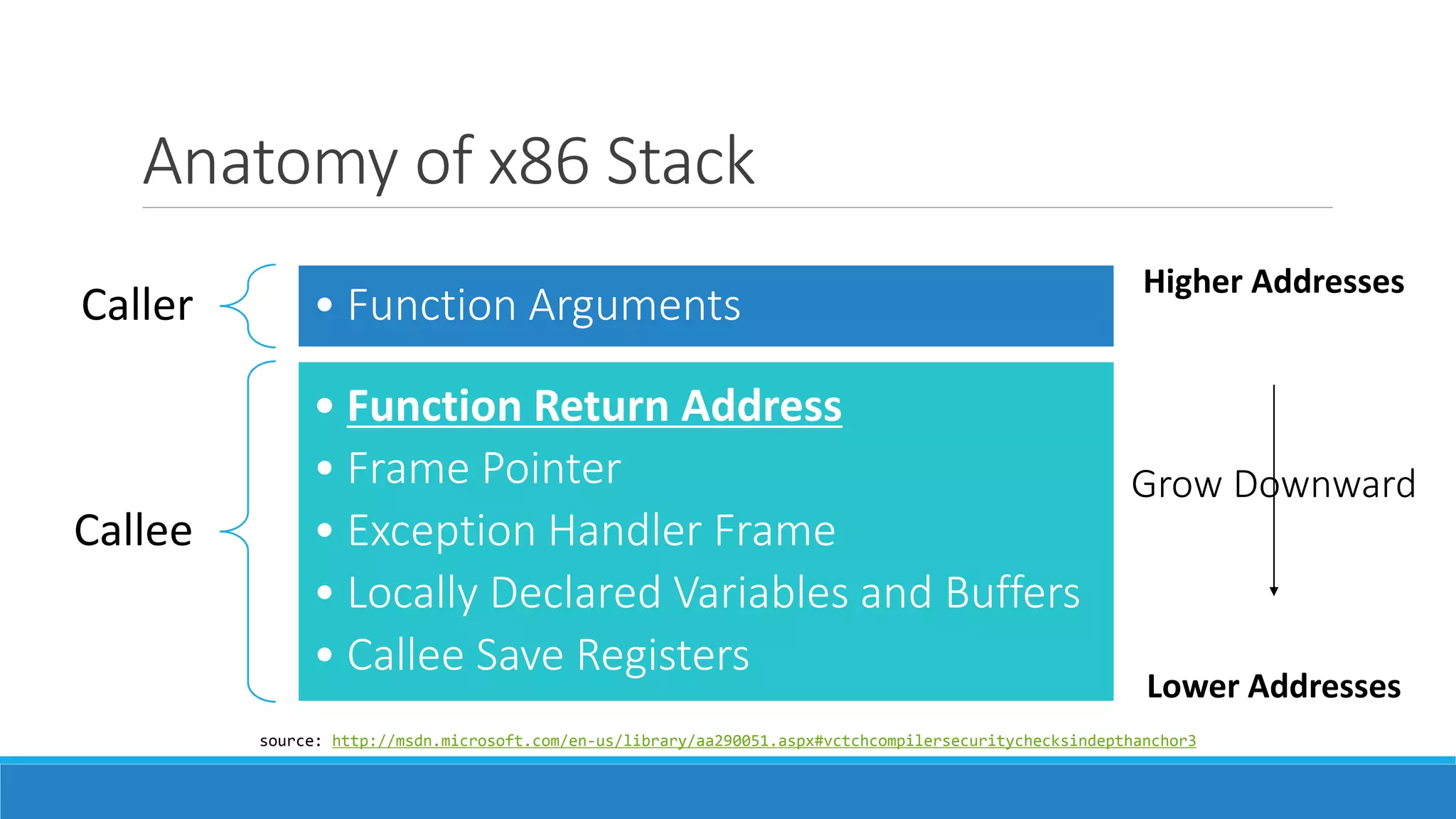
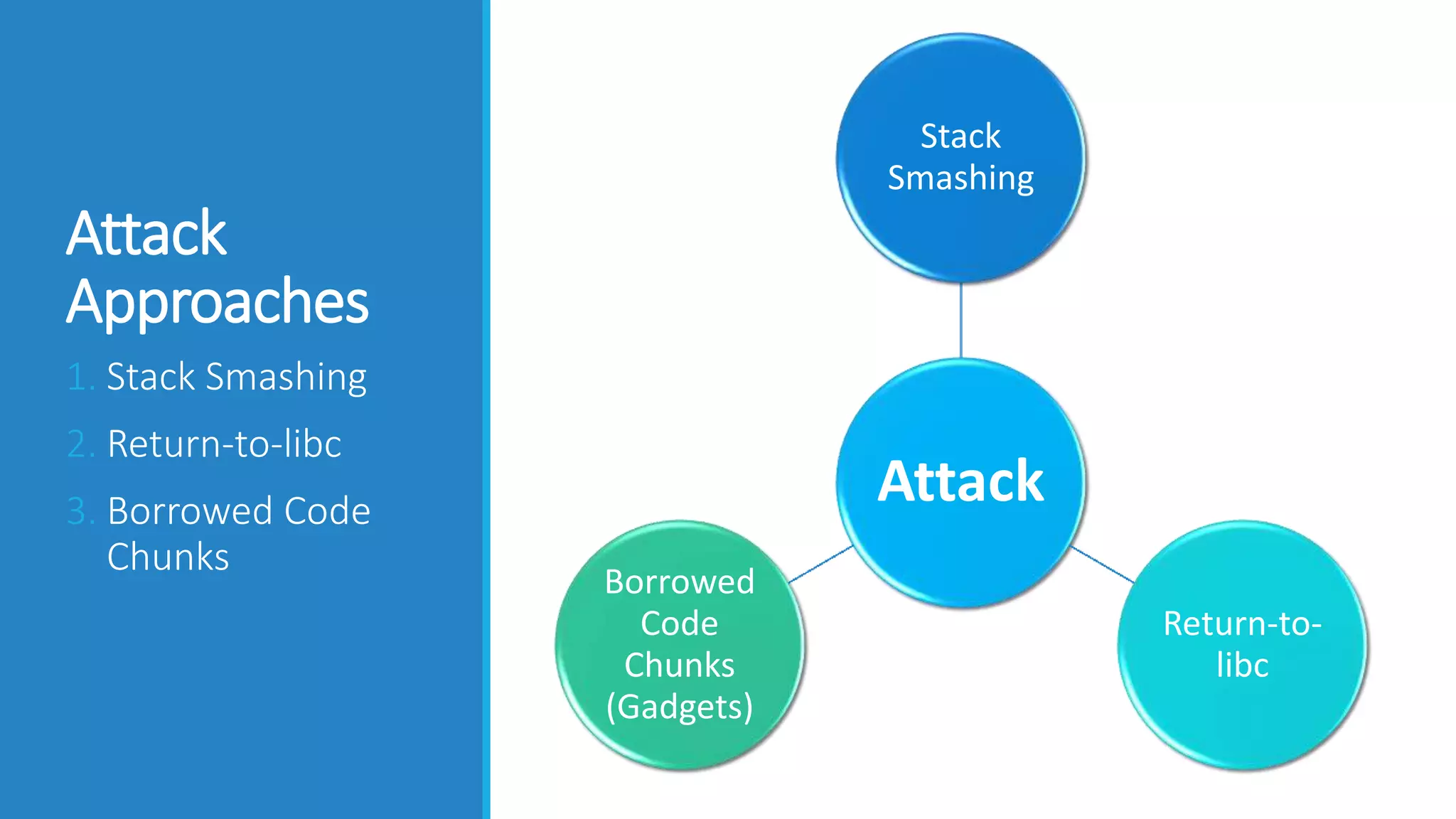
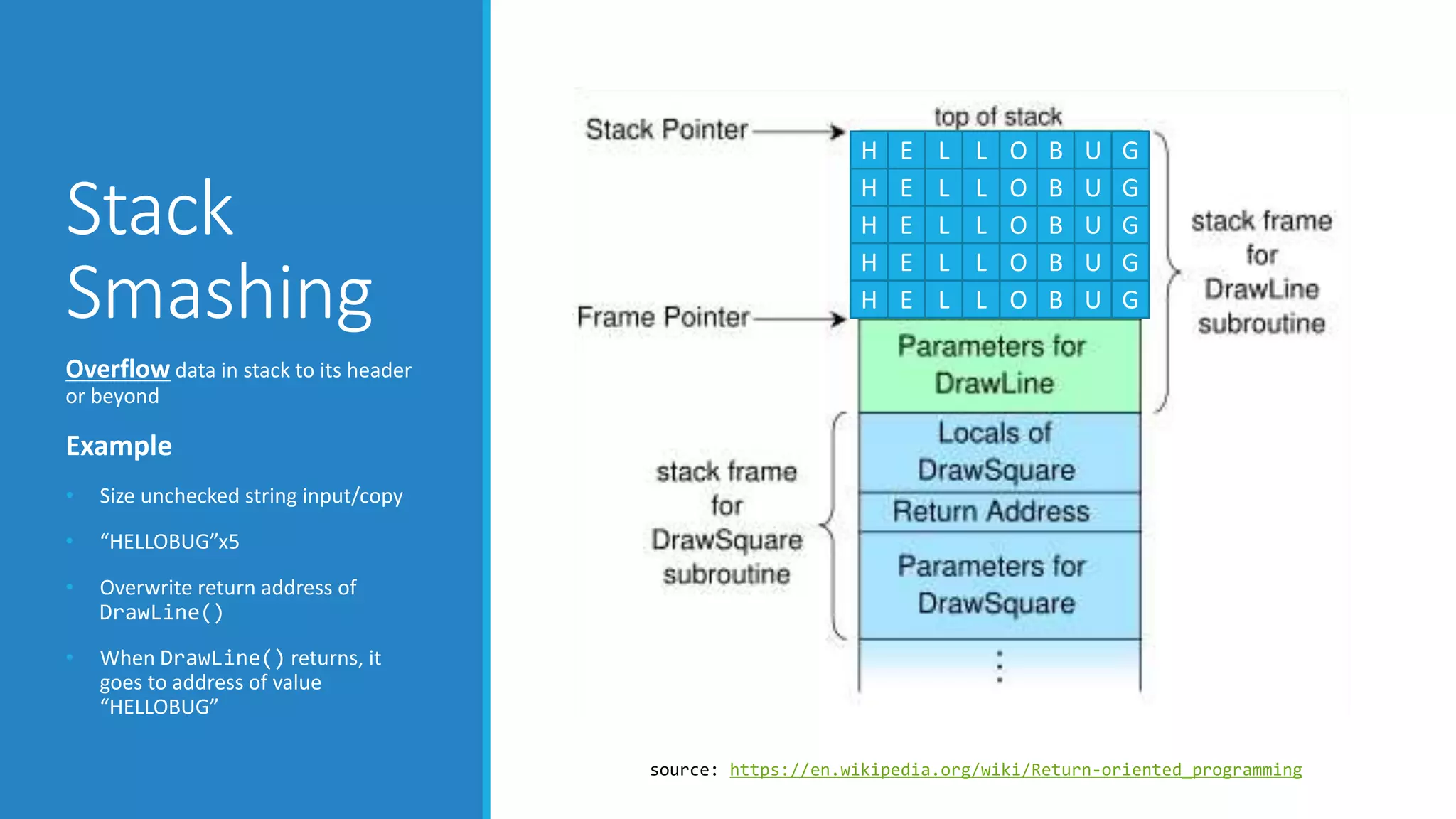
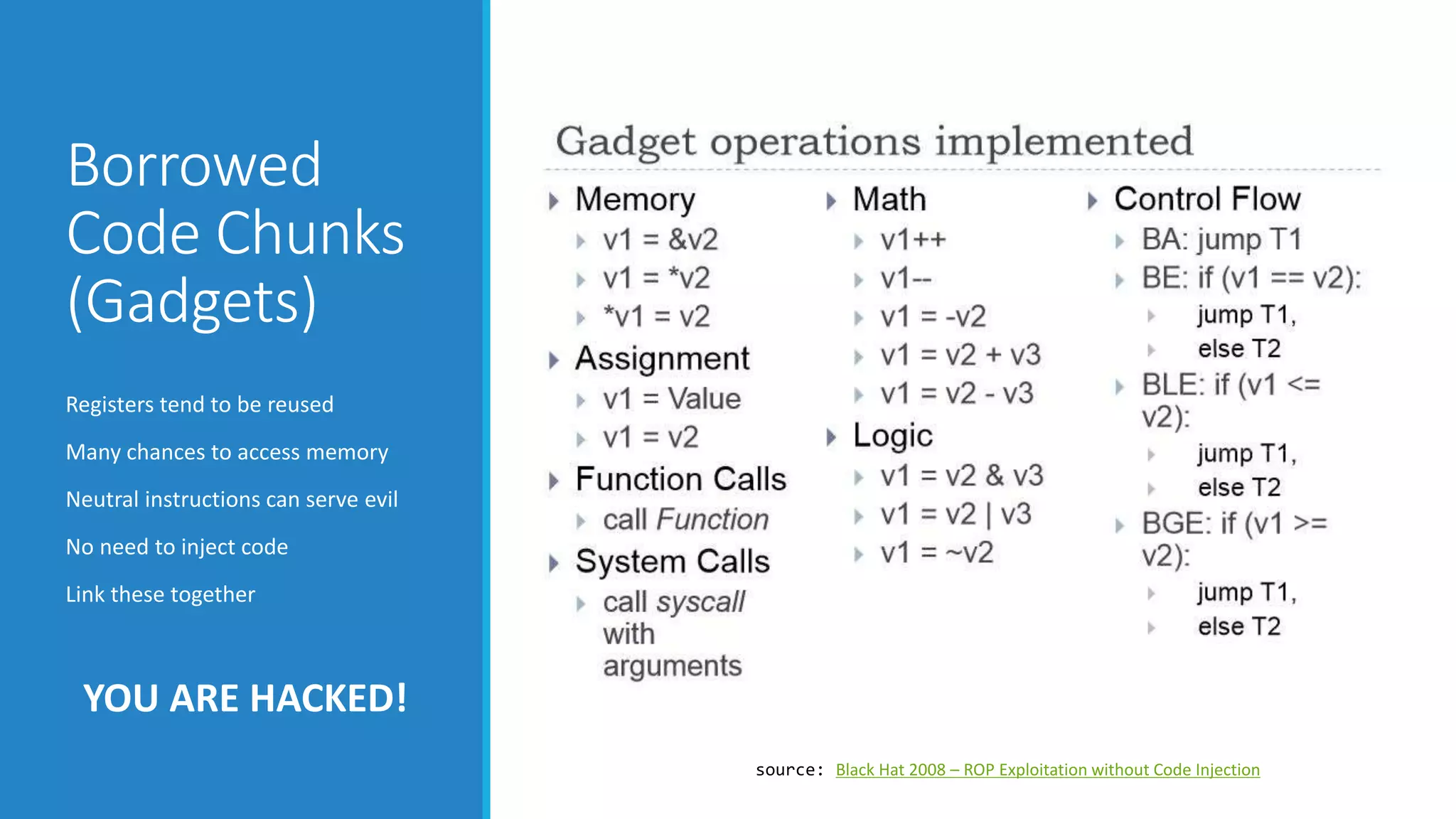
This document discusses Return Oriented Programming (ROP), which is a technique for exploiting software vulnerabilities to execute malicious code without injecting new code. It can be done by manipulating return addresses on the program stack to divert execution flow to existing code snippets ("gadgets") that perform the desired task when executed in sequence. The document covers the anatomy of the x86 stack, common ROP attack approaches like stack smashing and return-to-libc, how gadgets work by chaining neutral instructions, and various defenses such as stack canaries, non-executable memory, address space layout randomization, and position-independent executables.

![What is ROP?
A program composes of functions
◦ A lot of Calls and Returns
Manipulating return addresses
Go to other Address / Function / Program
Can be done without injecting new code
Example
◦ [Linux] Opening sh shell
◦ [Windows] Opening a calculator
source: https://en.wikipedia.org/wiki/Return-oriented_programming](https://image.slidesharecdn.com/returnorientedprogrammingrop-141104233413-conversion-gate02/75/Return-oriented-programming-ROP-2-2048.jpg)