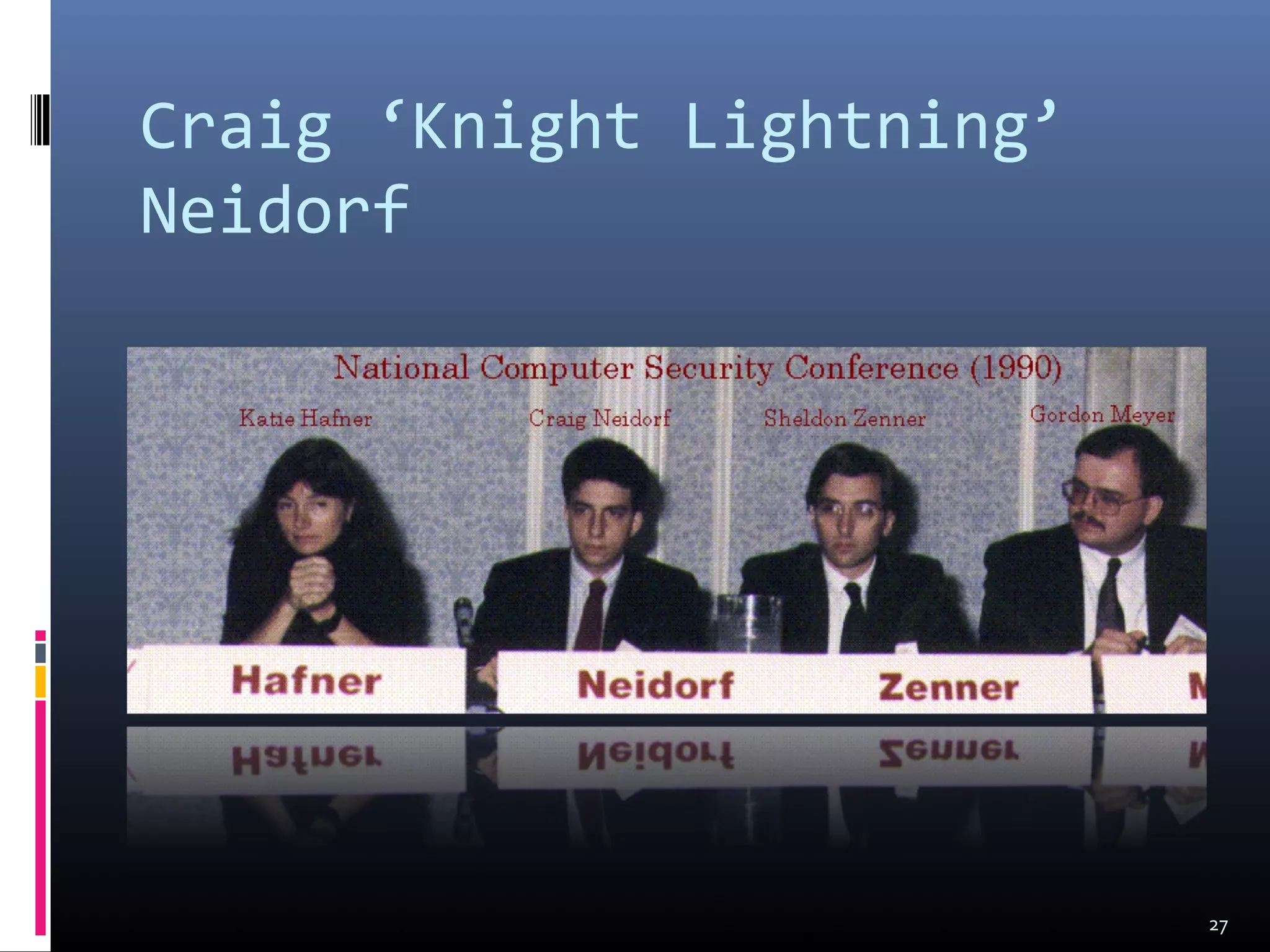
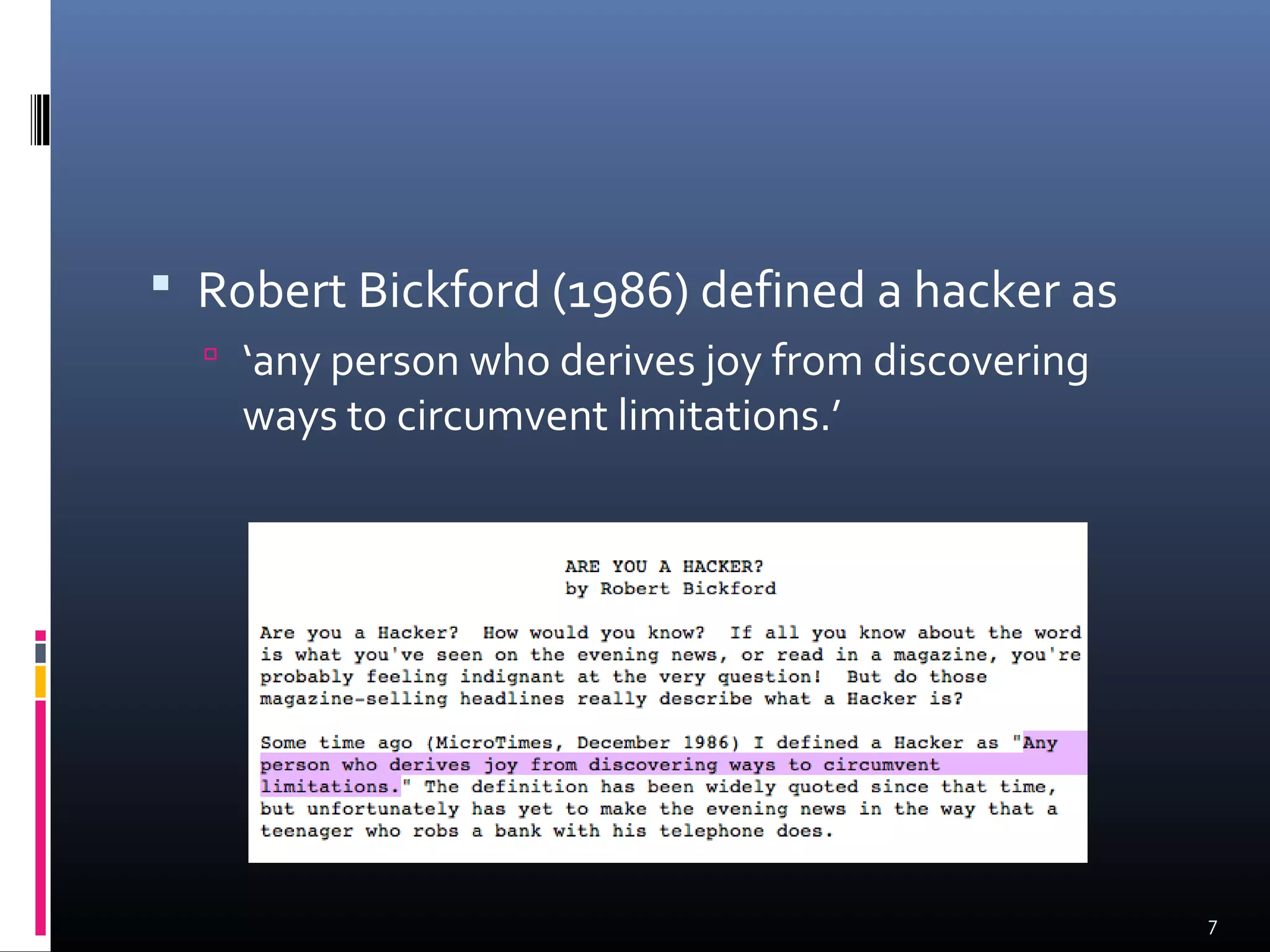
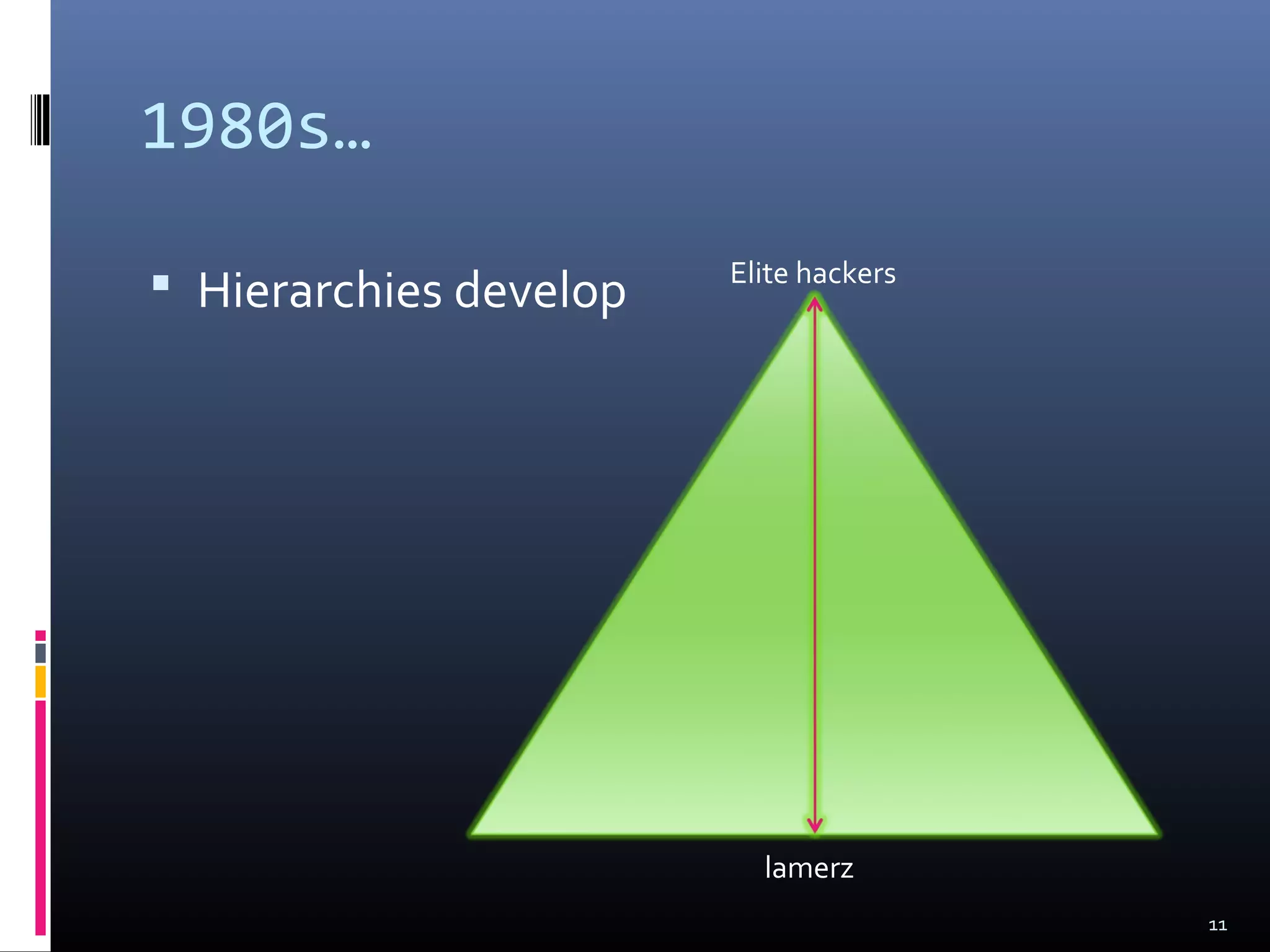
The document discusses the history and evolution of hacking from the 1940s to present day. It covers the origins of hacking at MIT, the "Golden Age of Hacking" from 1980-1990 which saw the rise of bulletin board systems and publications like Phrack, and the shift to viewing hacking as criminal as the media portrayed it as a "moral panic" and police raids increased. It also mentions the rise of hacktivism and how hackers today are involved in online protests and political causes.










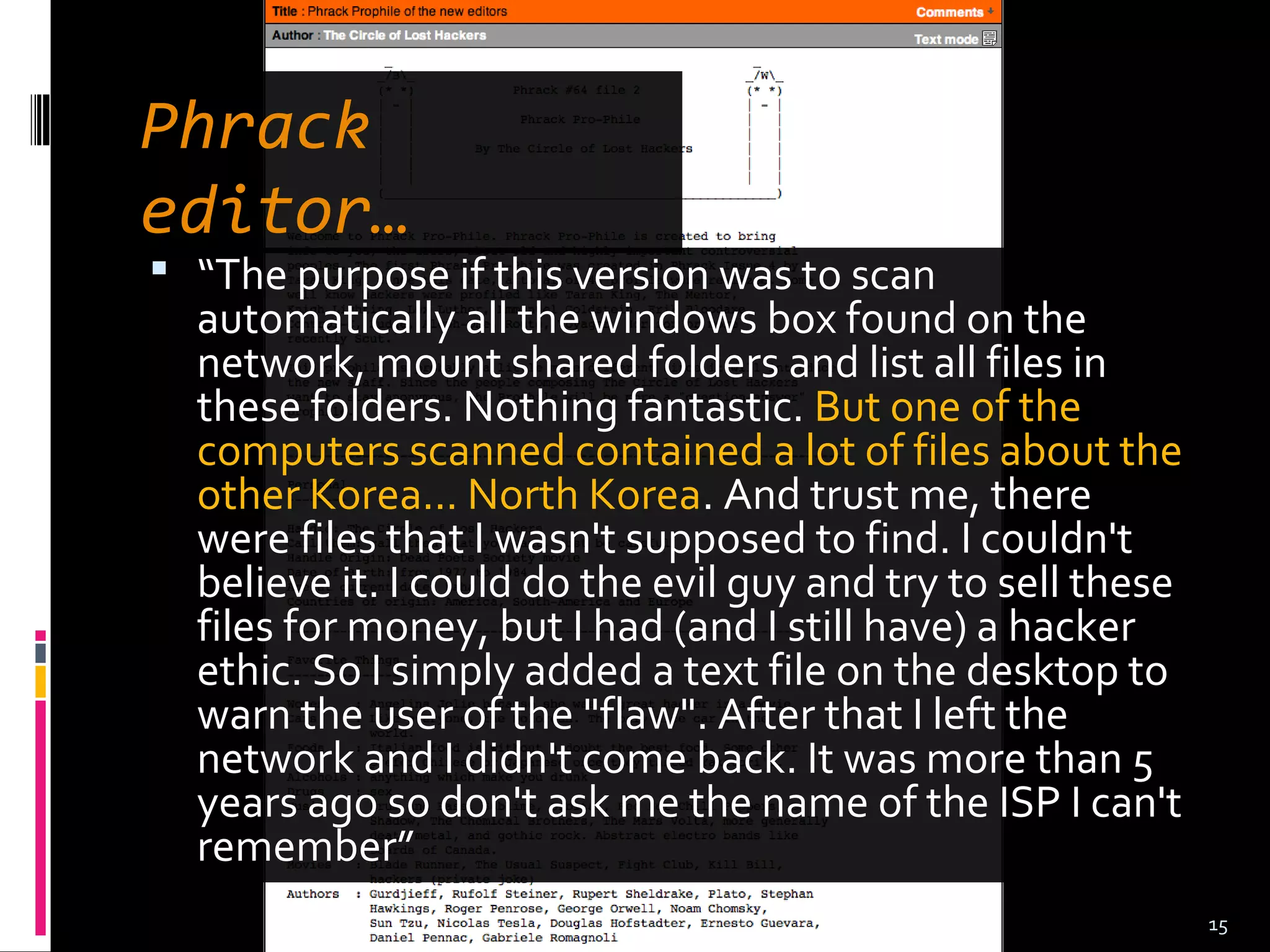
![ “A subtle modification about p0f [passive OS
fingerprinting] which [sic] made me finding
documents that I wasn't supposed to find. Some
years ago, I had a period when each month I tried to
focus on the security of one country. One of those
countries was South-Korea where I owned a big ISP
[Internet service provider]. After spending some
time to figure out how I could leave the DMZ [a
‘neutral’ network zone] and enter in the LAN [local
area network], I succeed thanks to a cisco
modification (I like default passwords). Once in the
LAN and after hiding my activity (userland >
kernelland), I installed a slightly modification of p0f.”
14
Phrack
editor…](https://image.slidesharecdn.com/med122hackerslecture-141009034533-conversion-gate02/75/Med122-hackers-lecture-14-2048.jpg)






![A noble pursuit?
It is a full time hobby, taking countless hours per week to learn,
experiment and execute the art of penetrating multi-user
computers: Why do hackers spend a good portion of their time
hacking? Some might say it is scientific curiosity, others that it is
for mental stimulation. But the true roots of hacker motives run
much deeper than that. In this file I will describe the underlying
motives of the aware hackers, make known the connections
between Hacking, Phreaking, Carding and Anarchy and make
known the ‘techno-revolution’ which is laying seeds in the mind
of every hacker . . . If you need a tutorial on how to perform any
of the above stated methods [of hacking], please read a [Phrack]
file on it. And whatever you do, continue the fight. Whether
you know it or not, if you are a hacker, you are a revolutionary.
[D]on’t worry, you’re on the right side.
(‘Doctor Crash’, 1986)
23](https://image.slidesharecdn.com/med122hackerslecture-141009034533-conversion-gate02/75/Med122-hackers-lecture-23-2048.jpg)