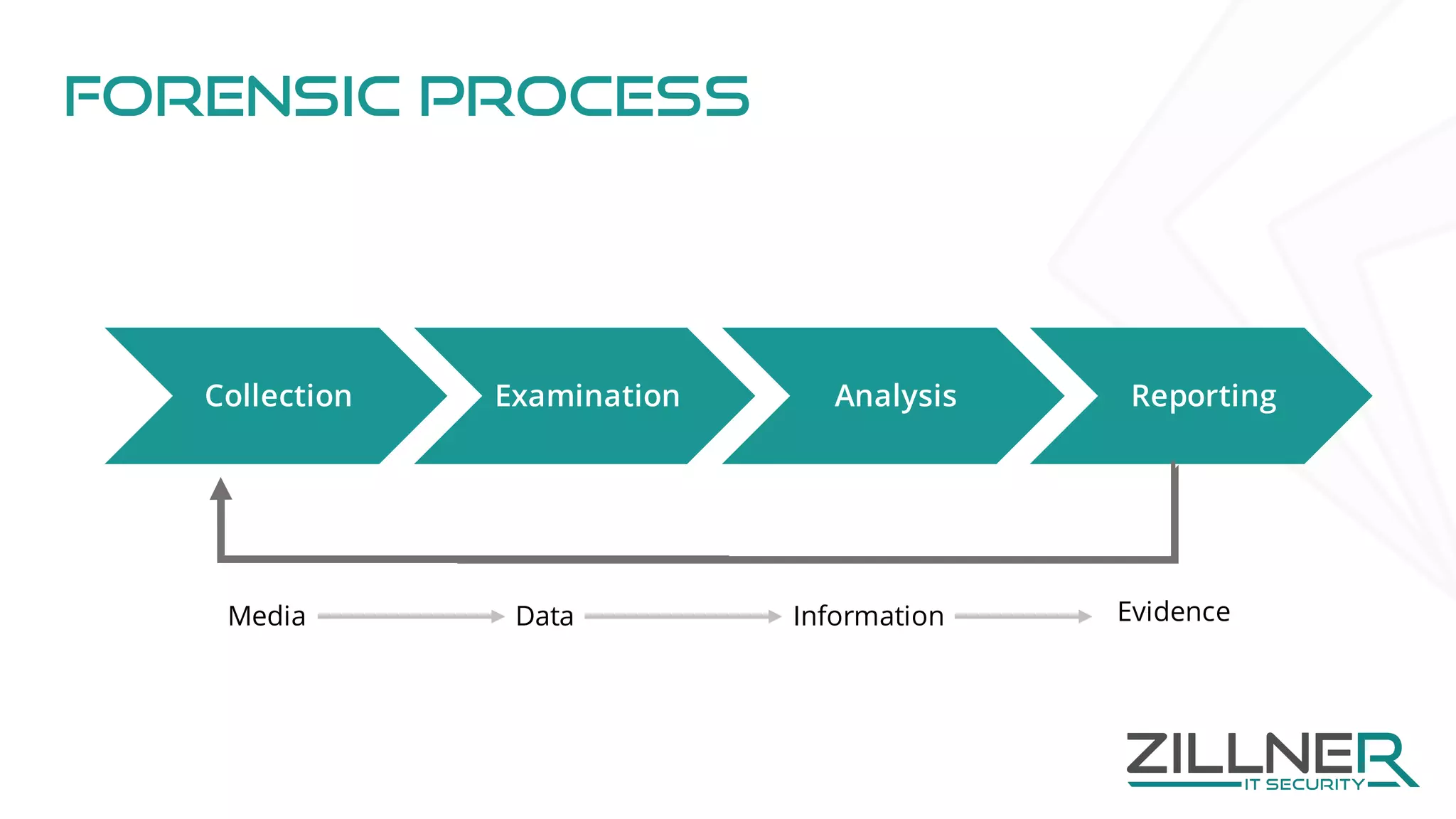
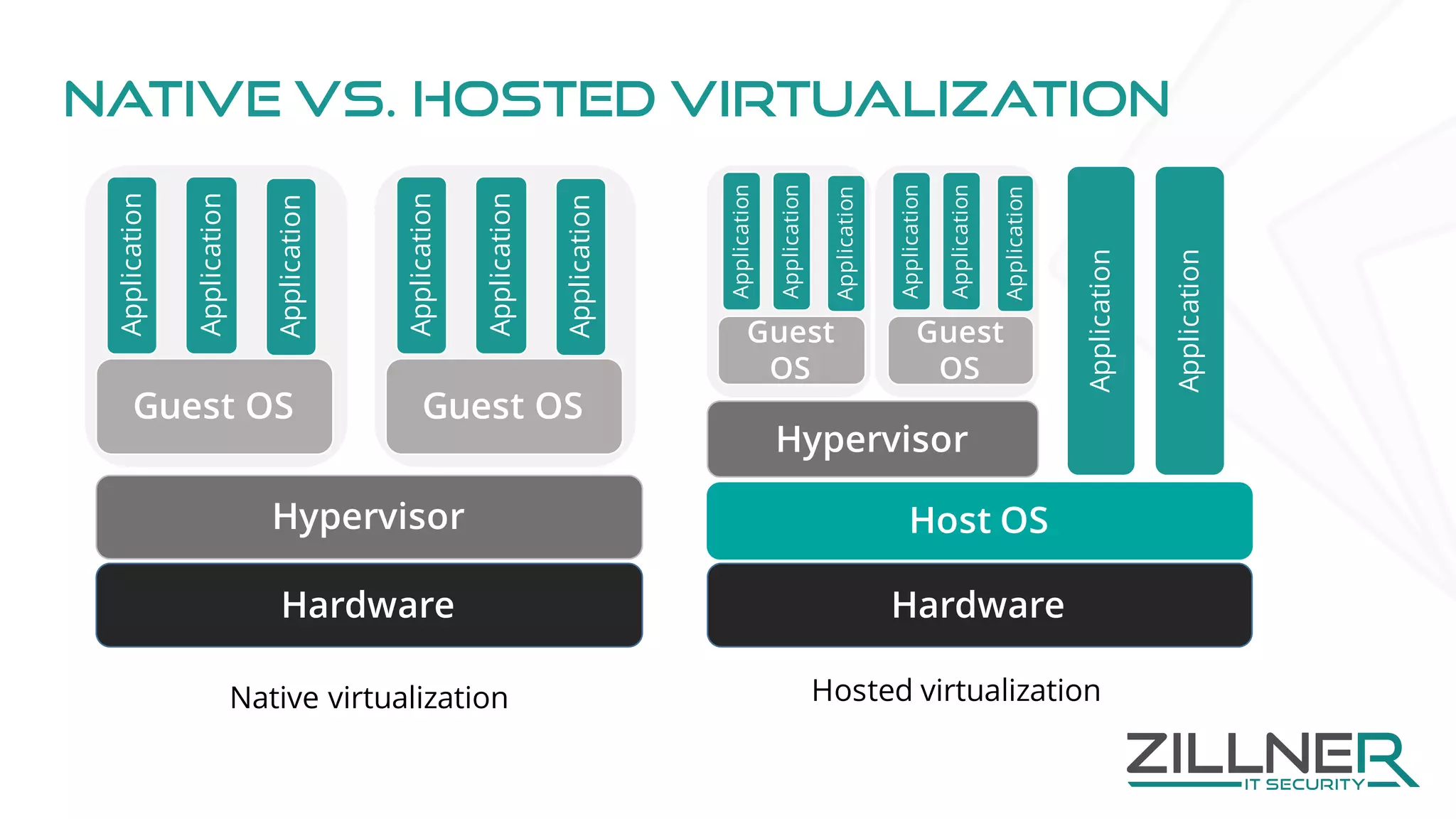
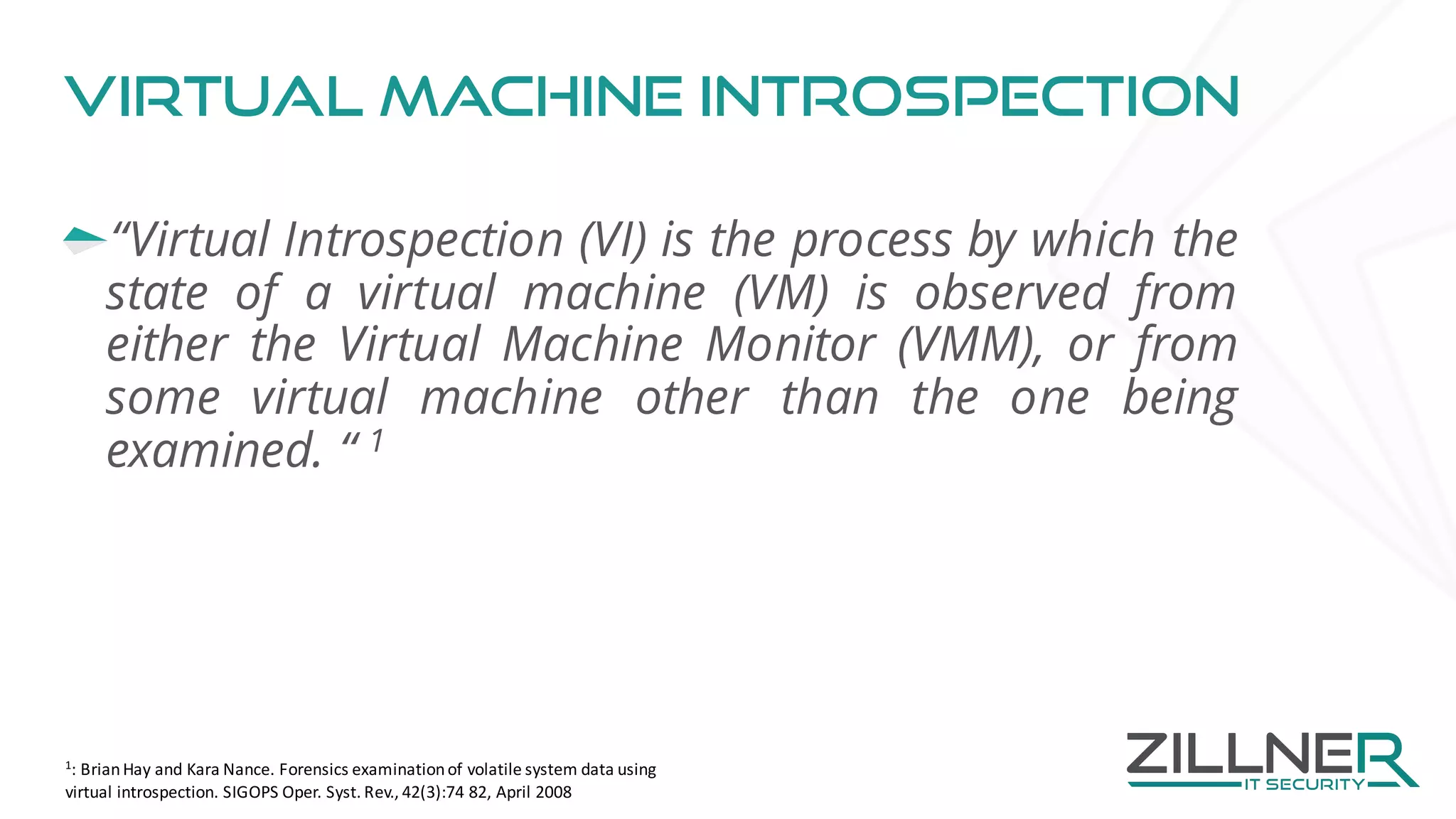
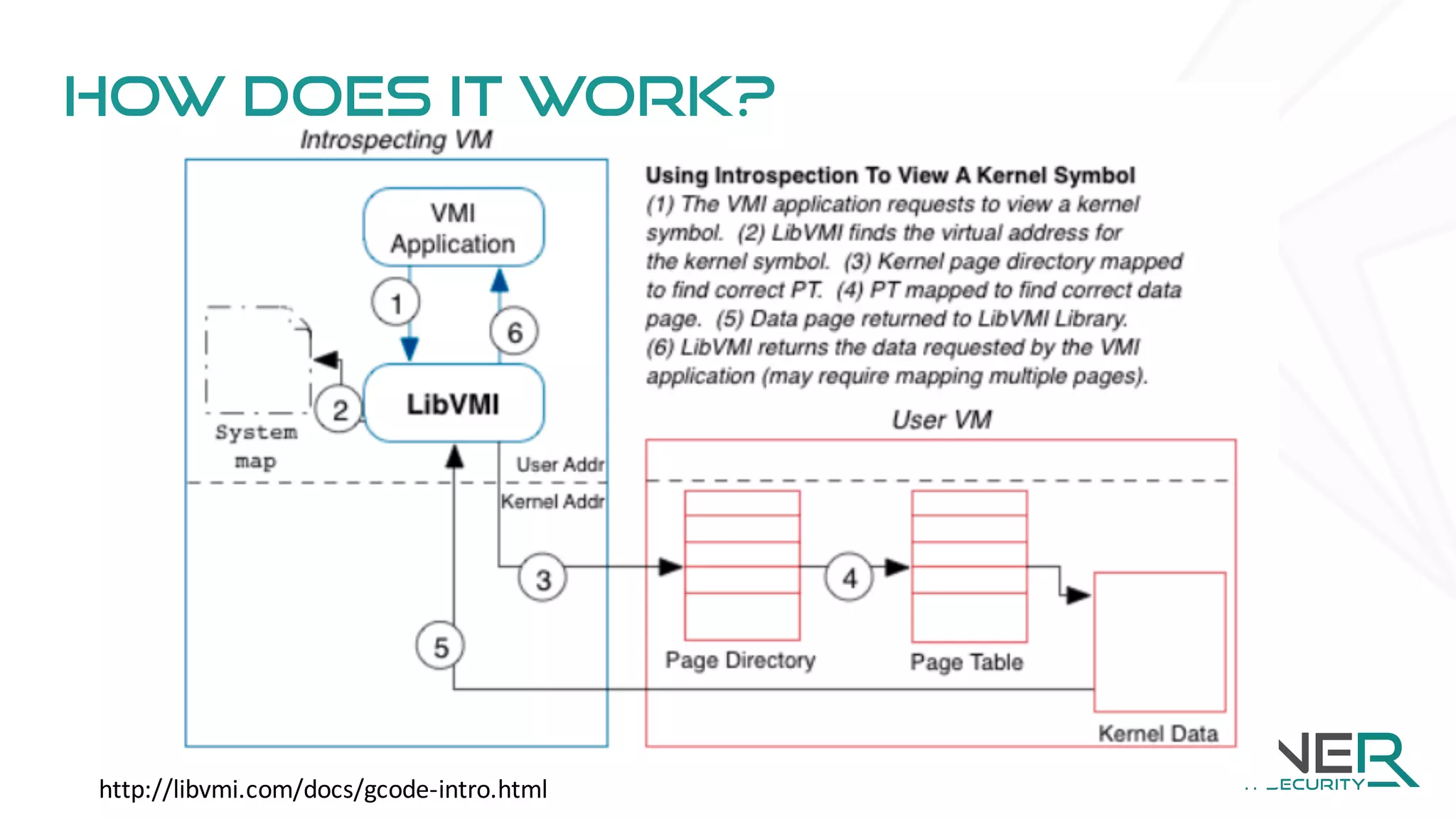
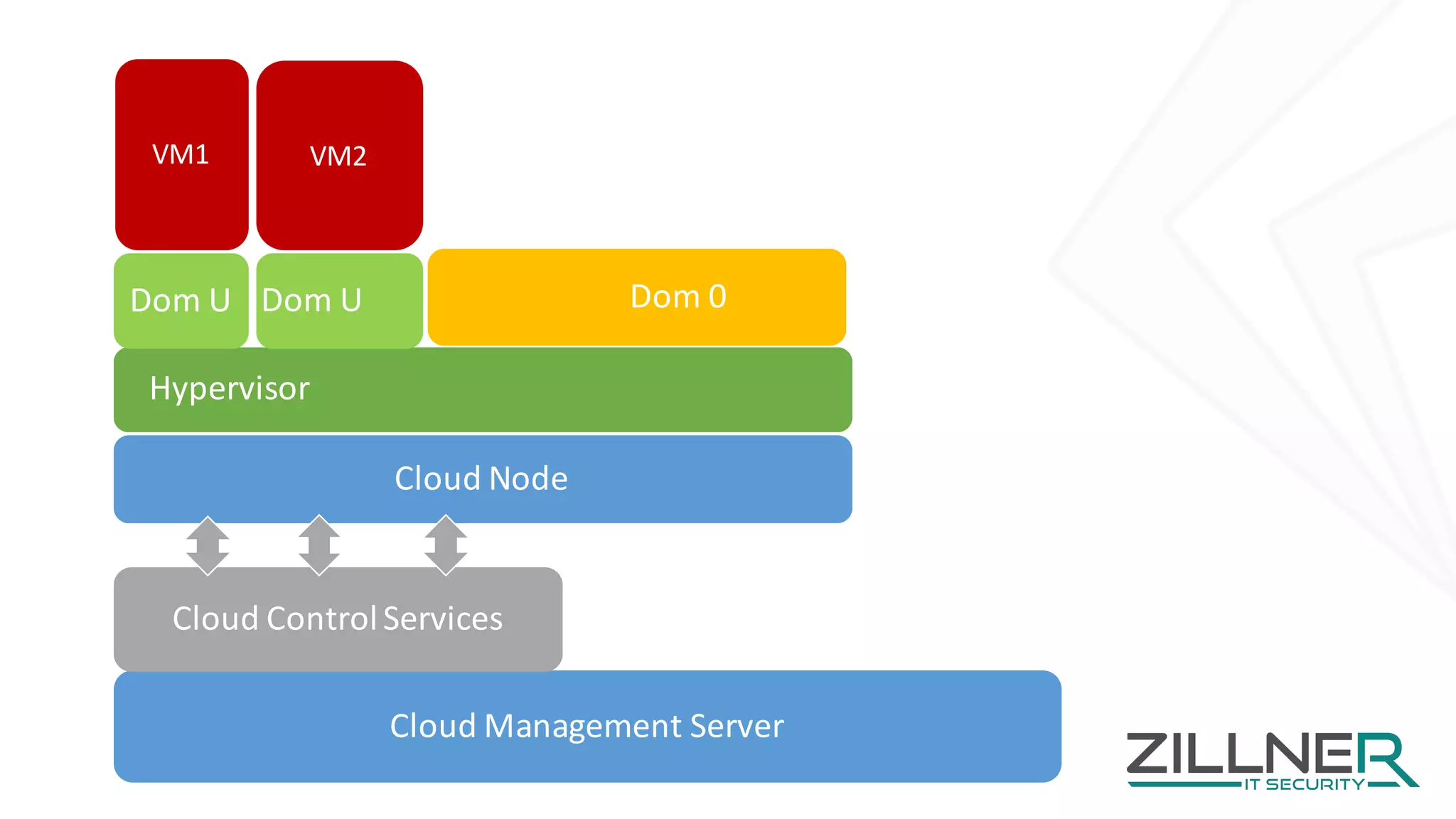
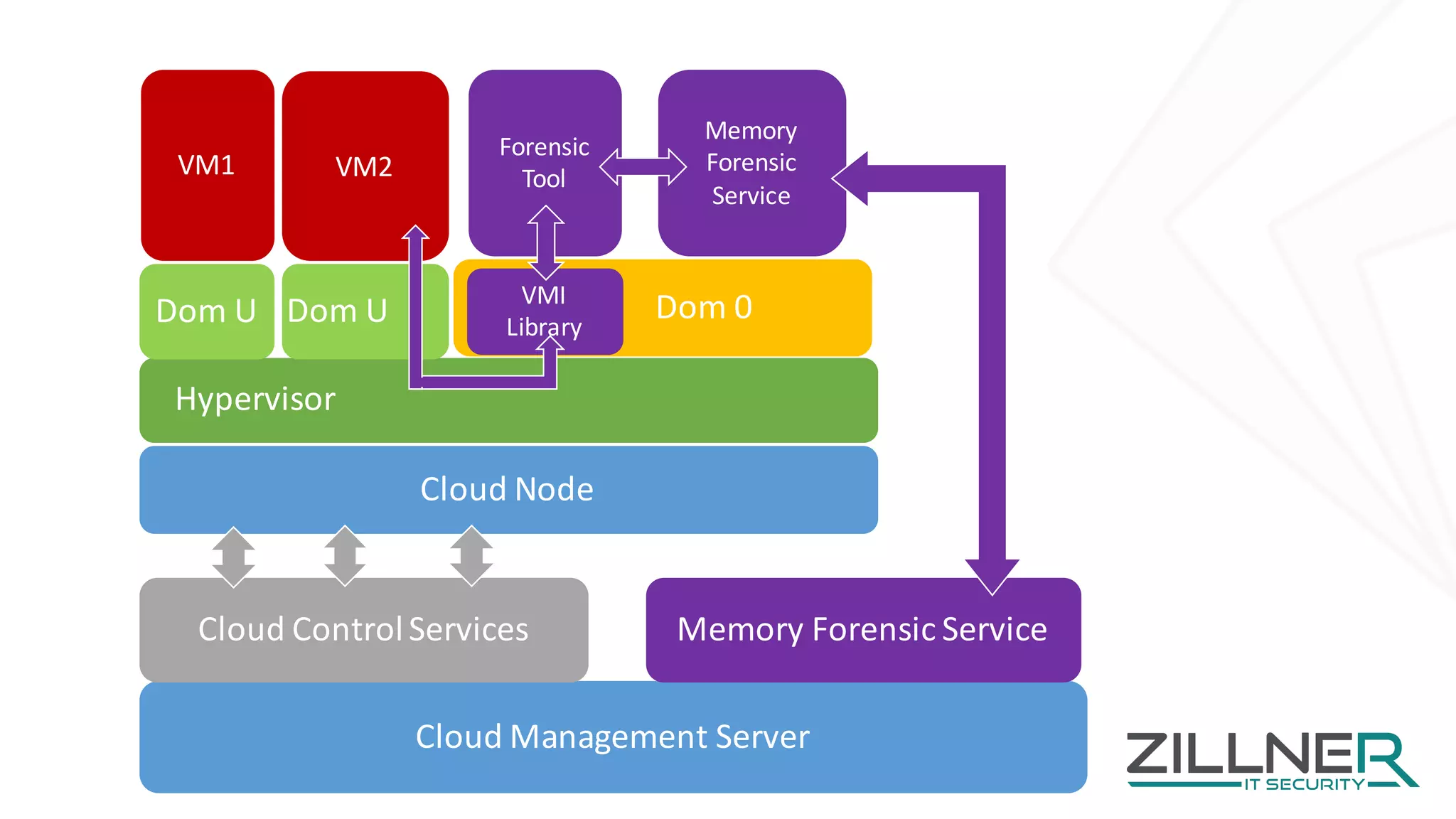
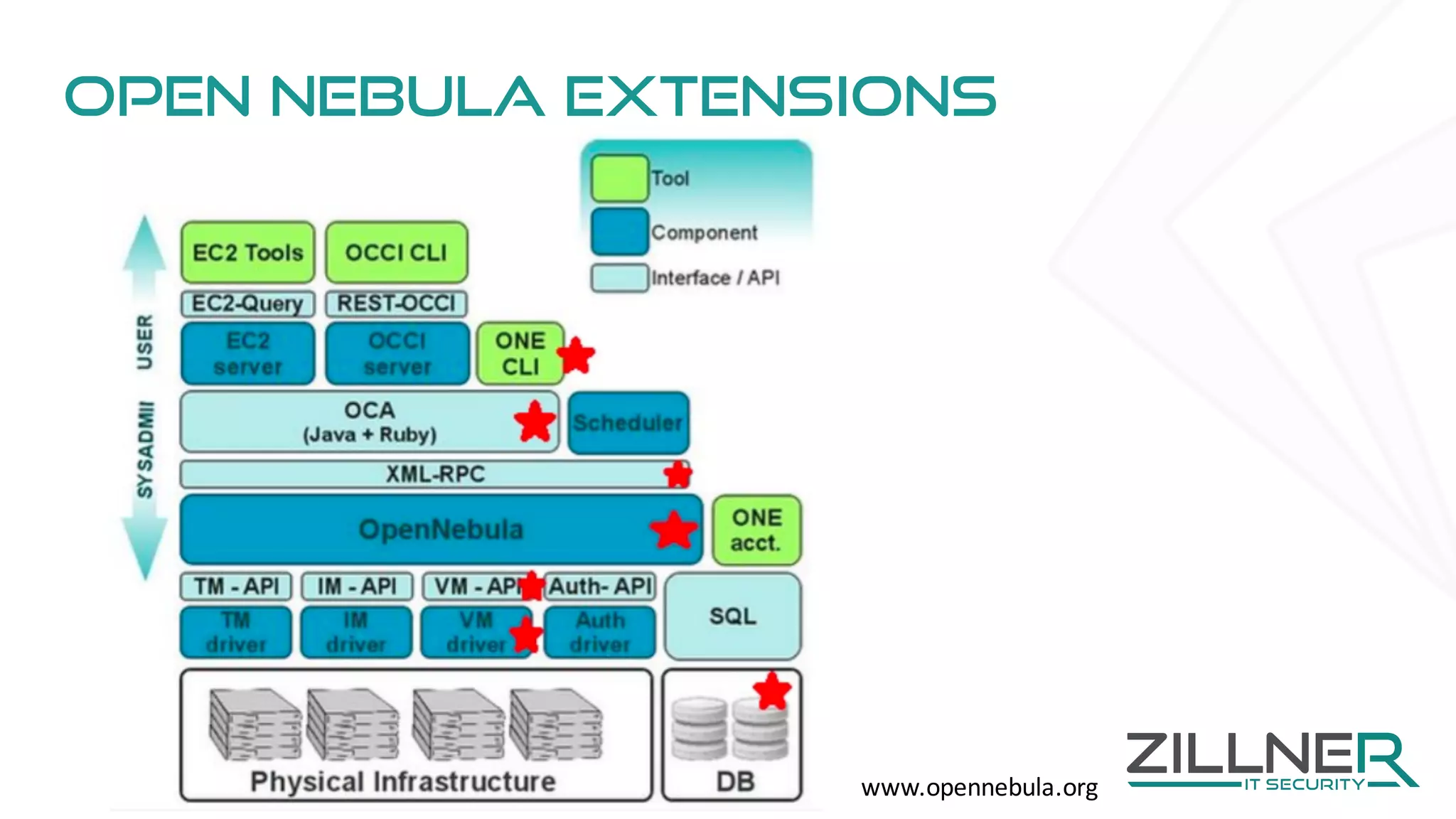
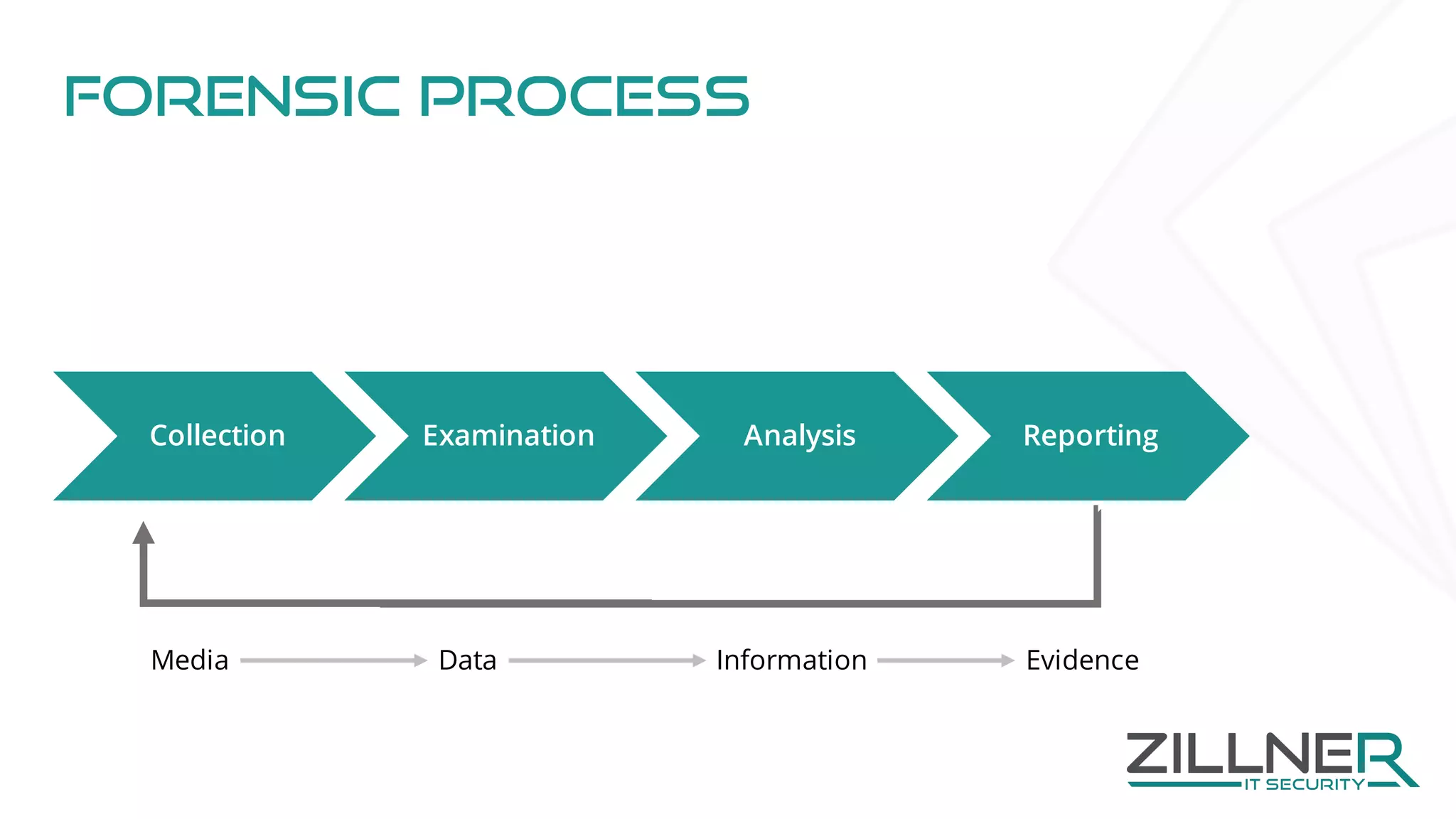
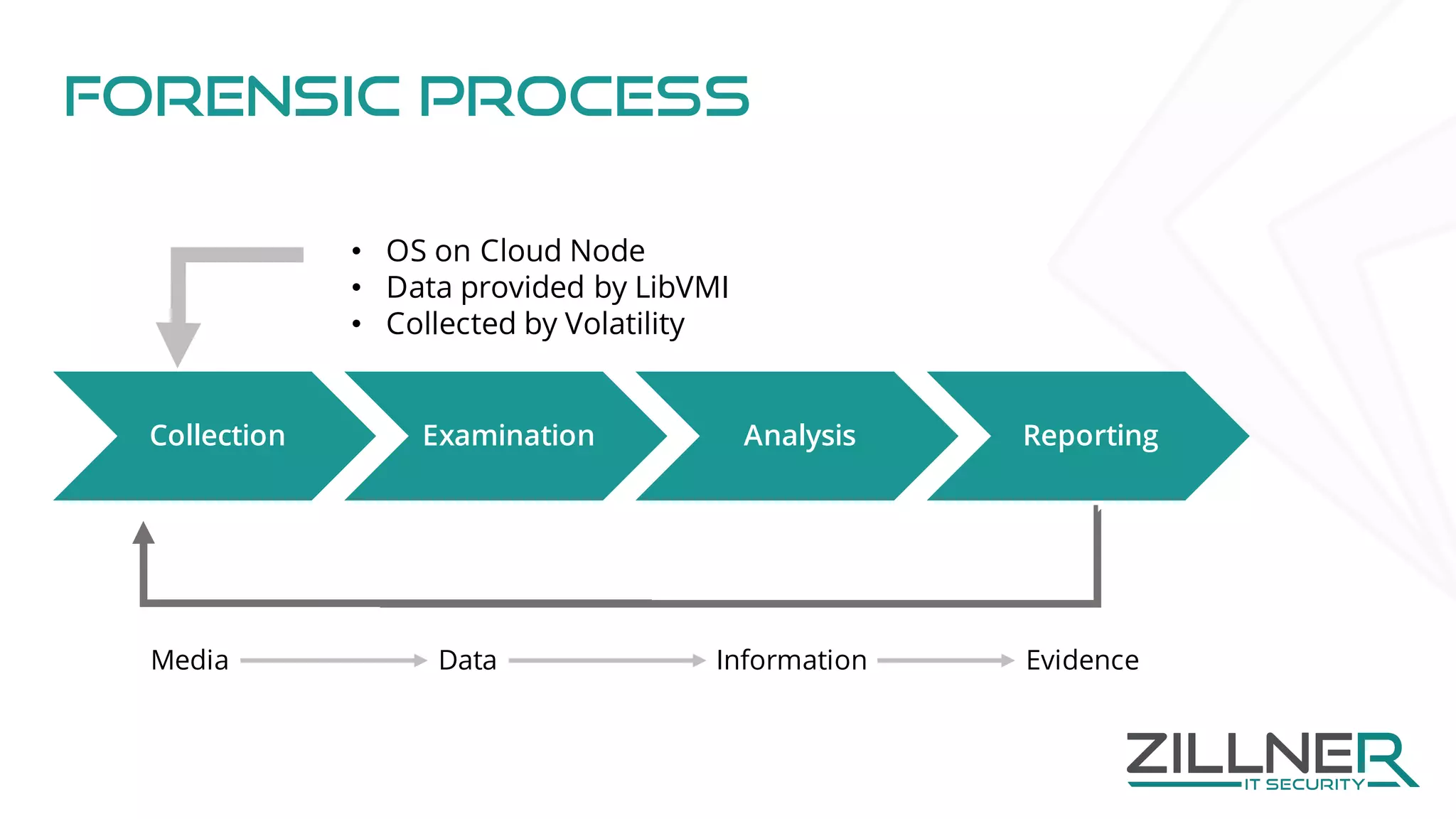
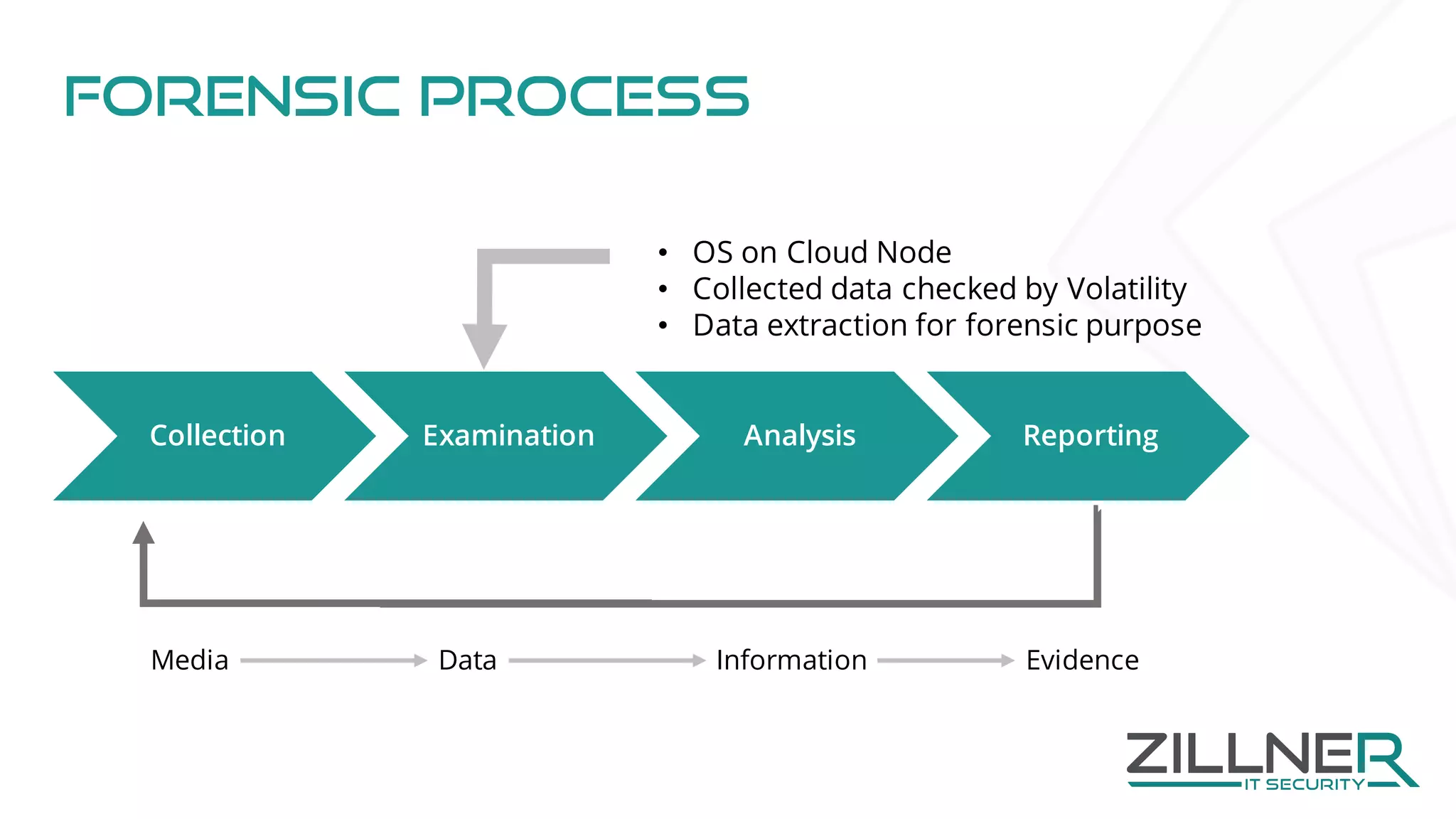
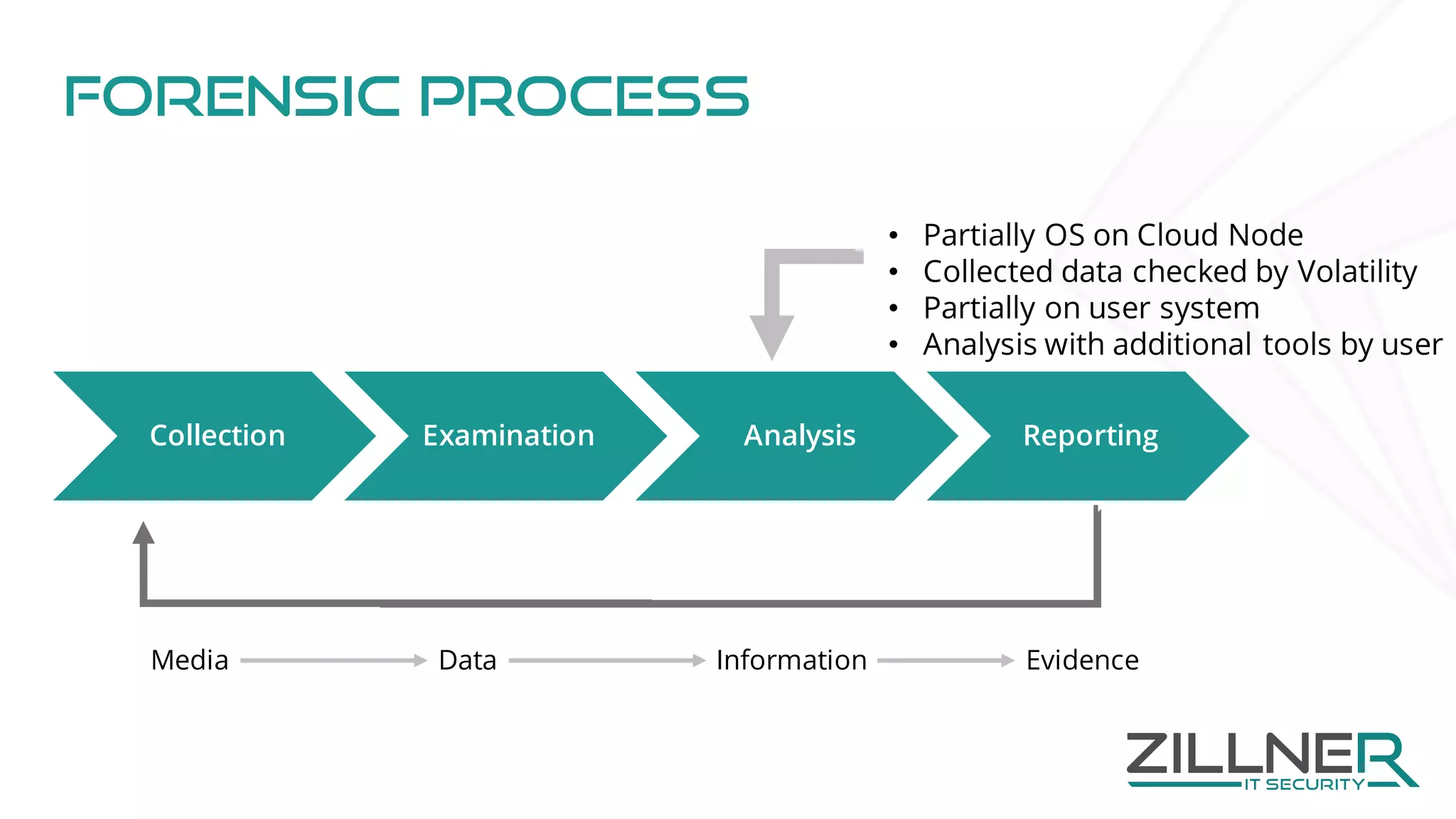
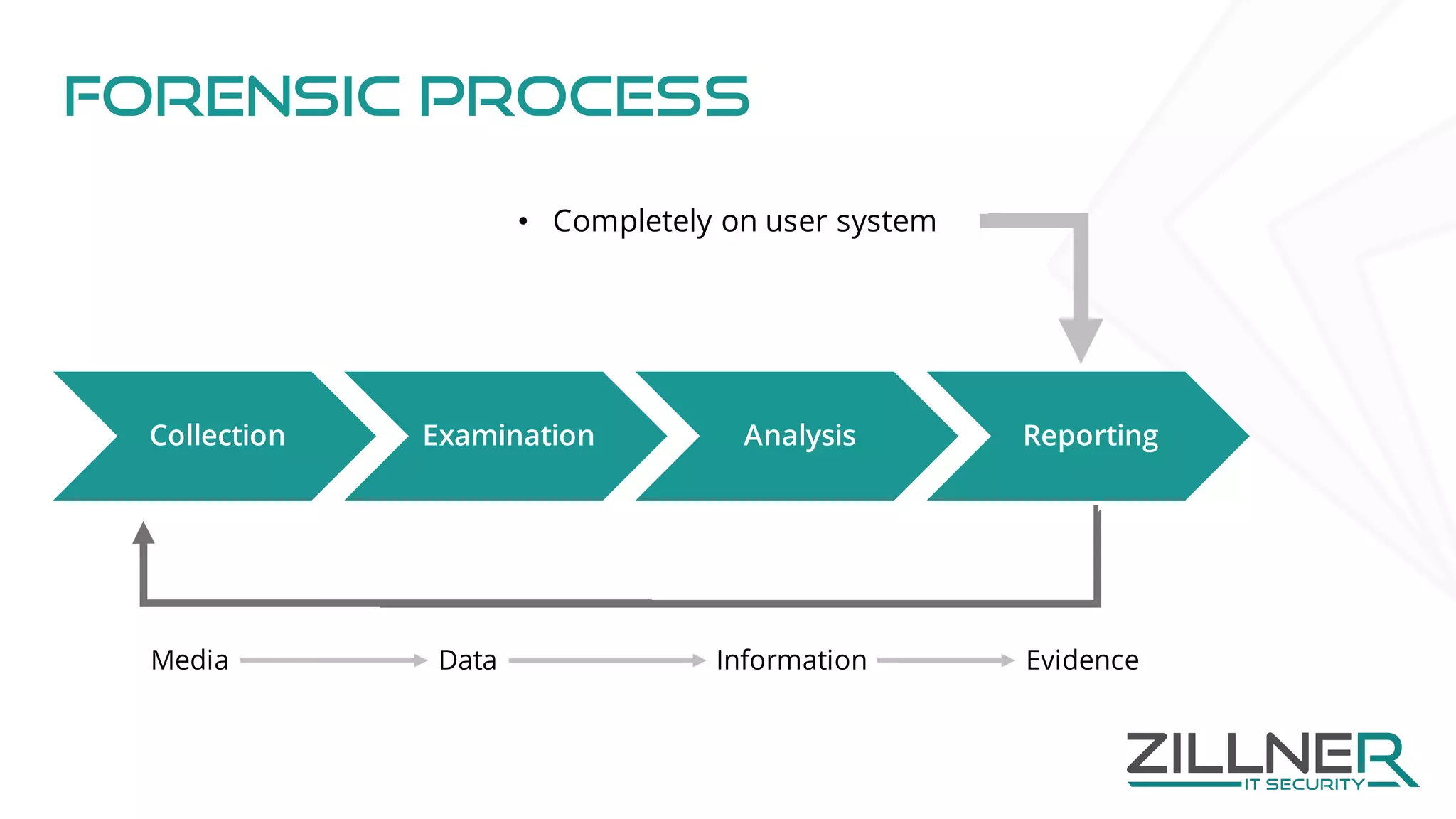
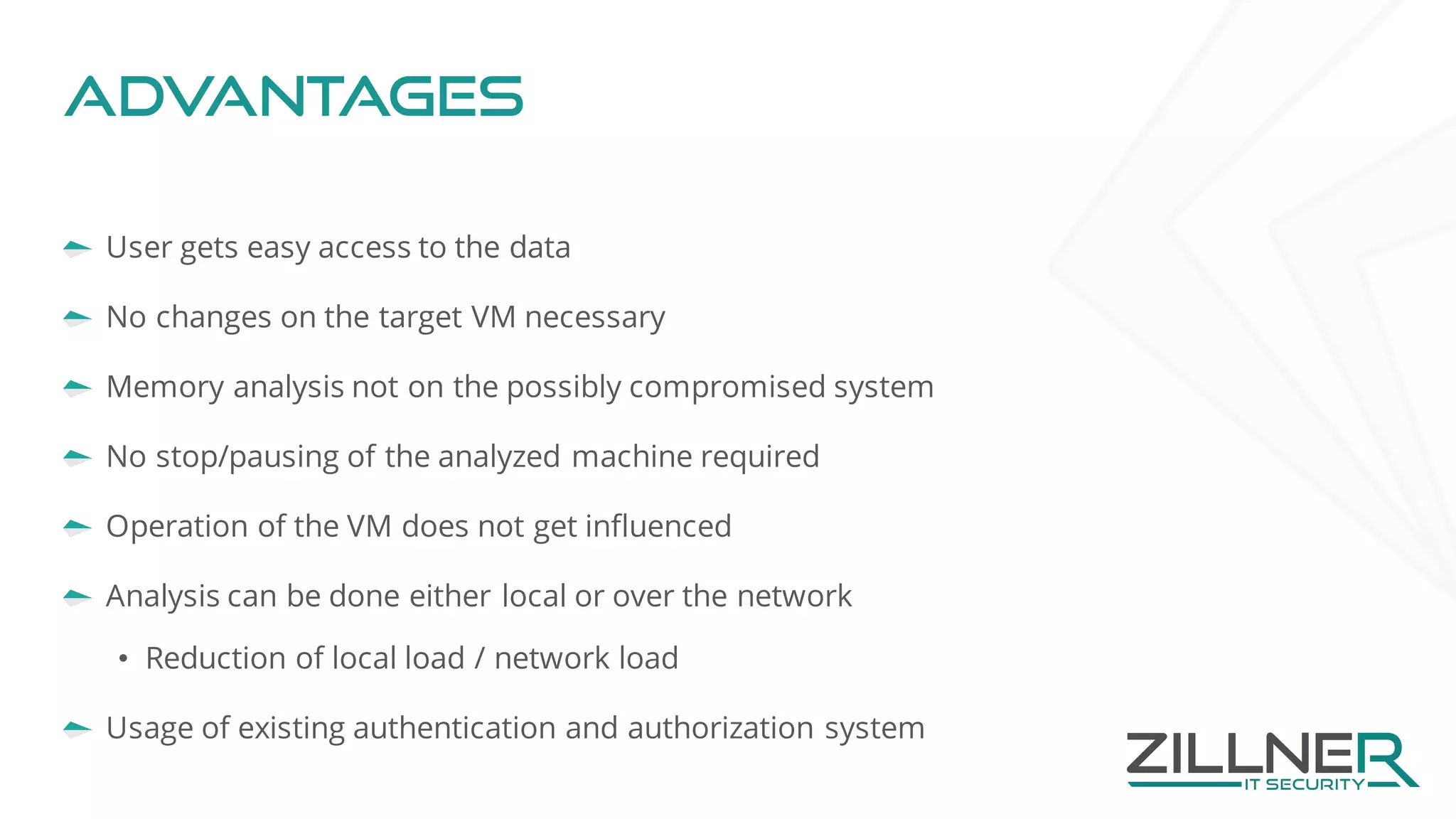
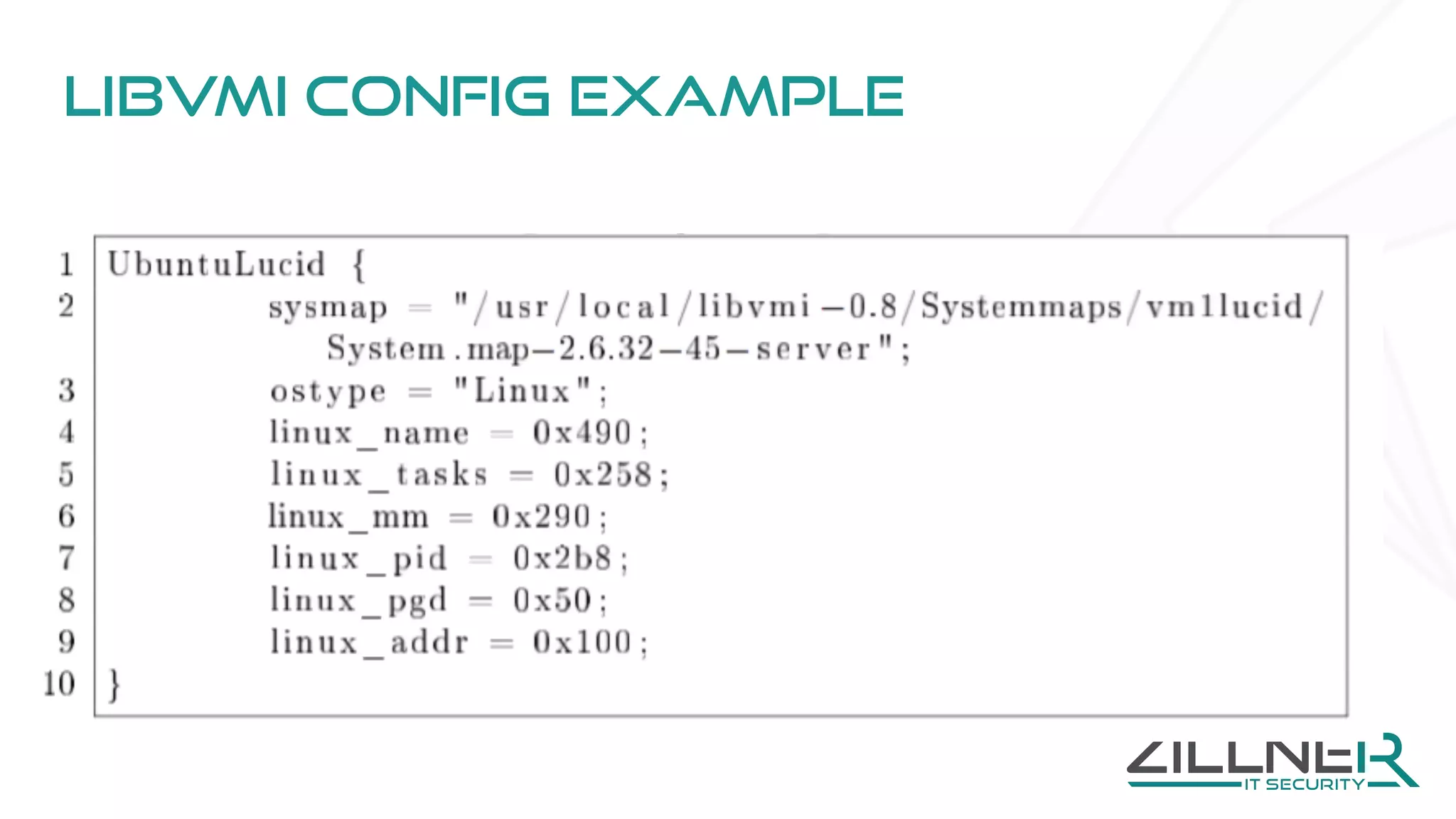
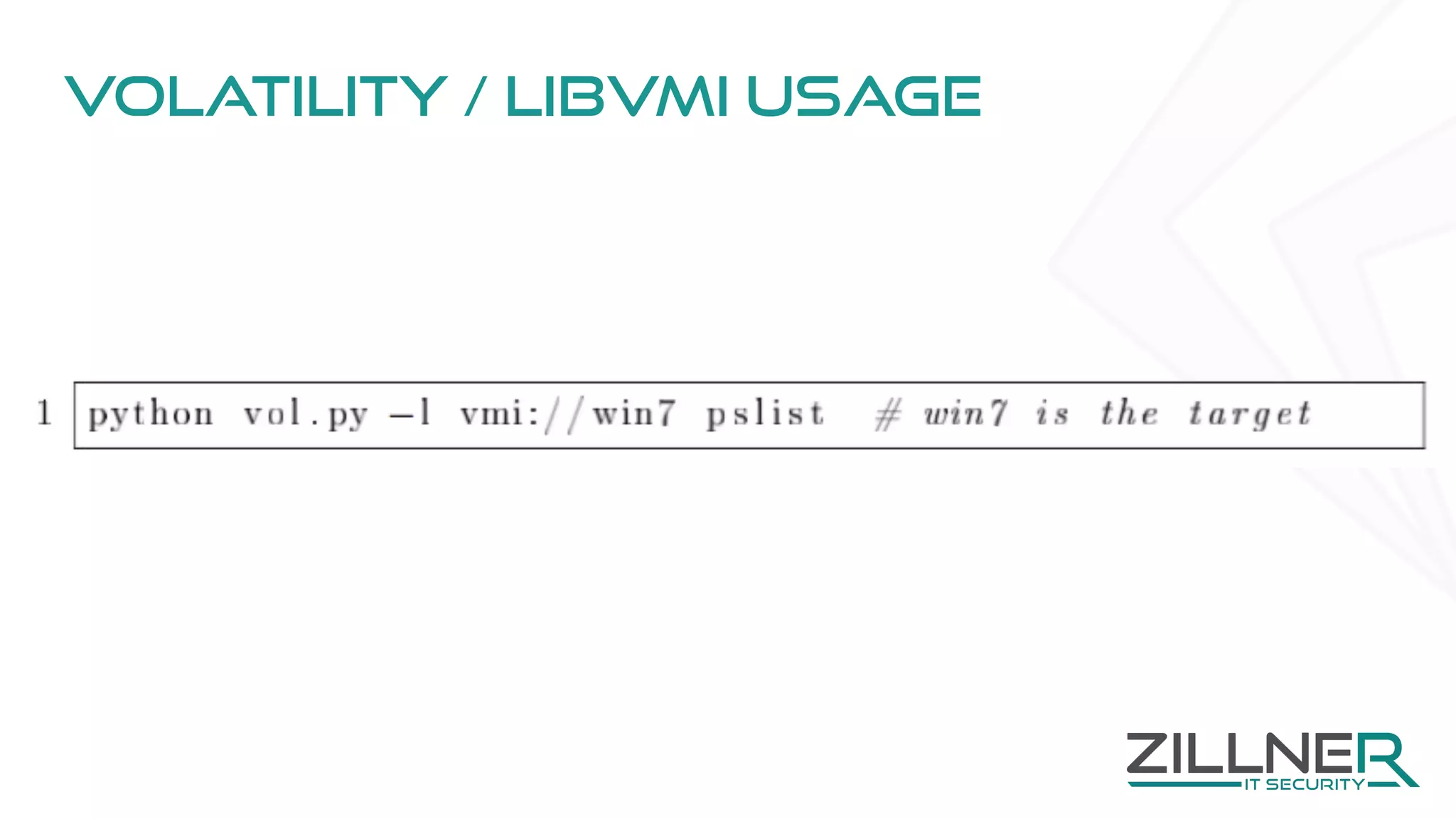
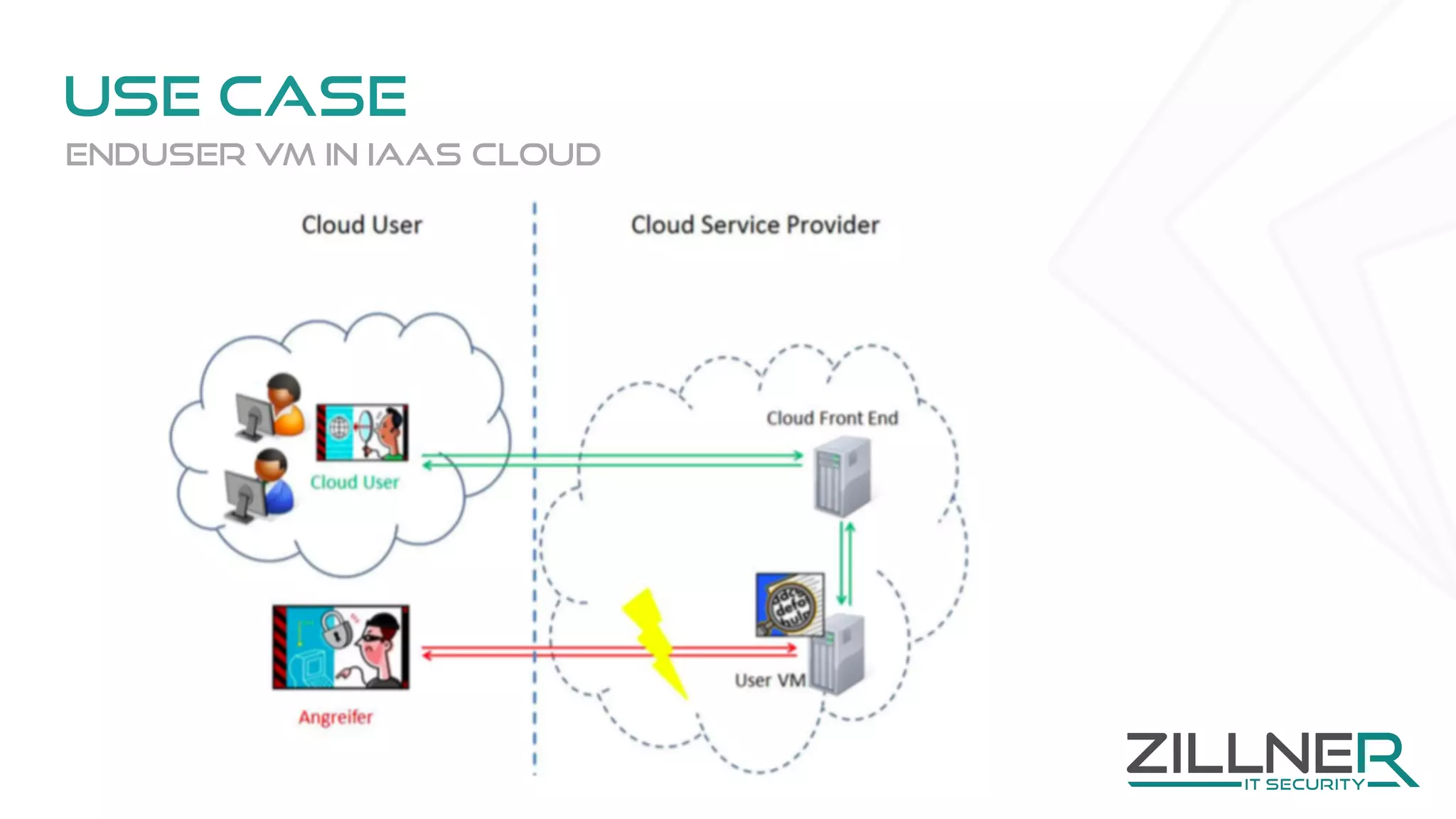
The document discusses memory forensics using virtual machine introspection (VMI) in cloud computing, highlighting its importance due to the limited forensic capabilities in cloud environments. VMI enables users to conduct their own forensic investigations while maintaining minimal impact on the target systems and enhancing the detection of advanced malware. The prototype solution presented utilizes open-source tools to facilitate efficient forensic processes in both local and networked scenarios.