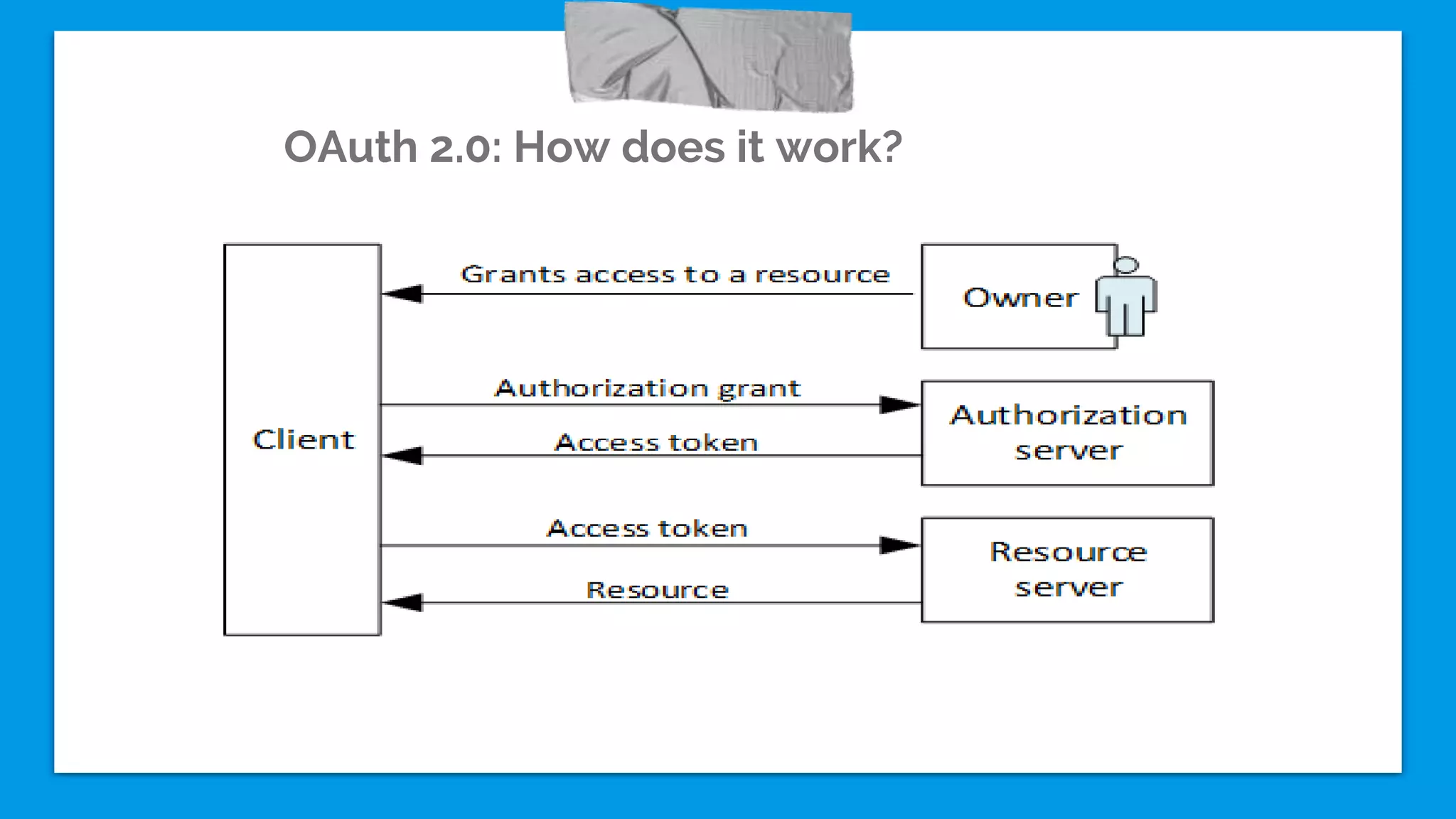
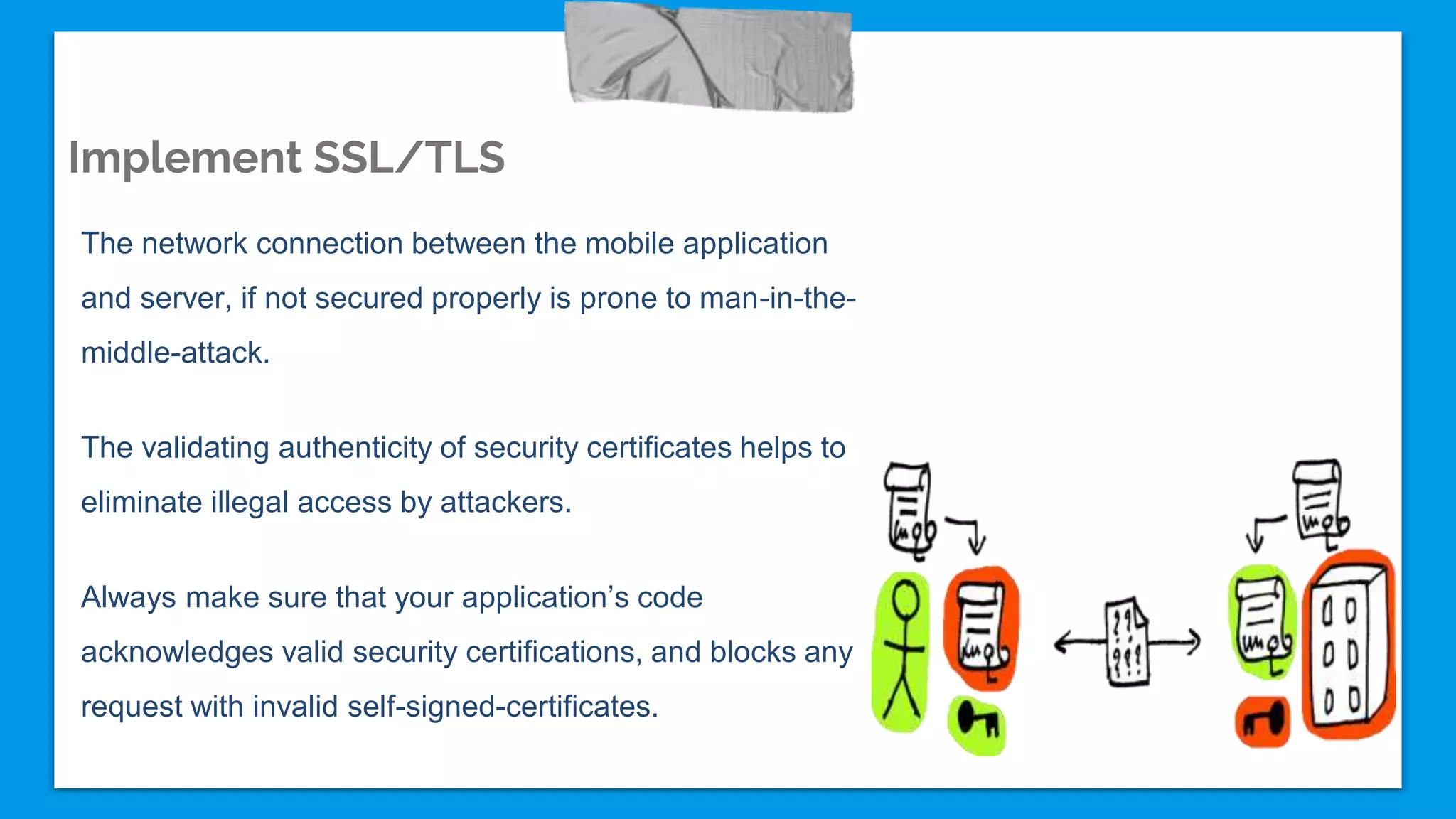
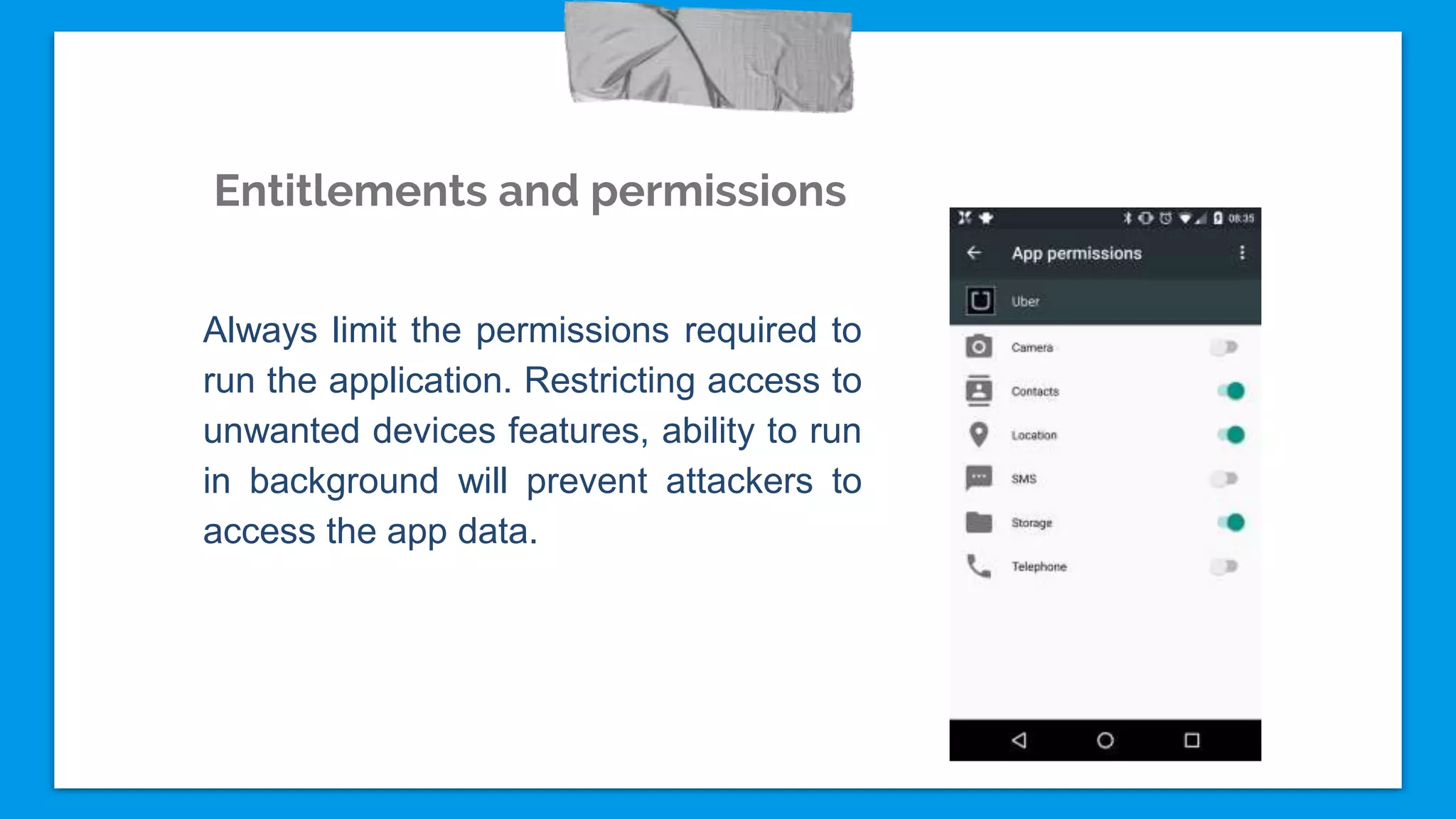
The document discusses mobile application security vulnerabilities, highlighting risks faced by enterprises using both iOS and Android platforms. It provides a comprehensive checklist aimed at enhancing security, including recommendations for using OAuth 2.0, preventing client-side injections, and implementing secure data storage practices. Key strategies include disabling debugging before app release, enabling remote data wipe capabilities, and implementing SSL/TLS for network connections.