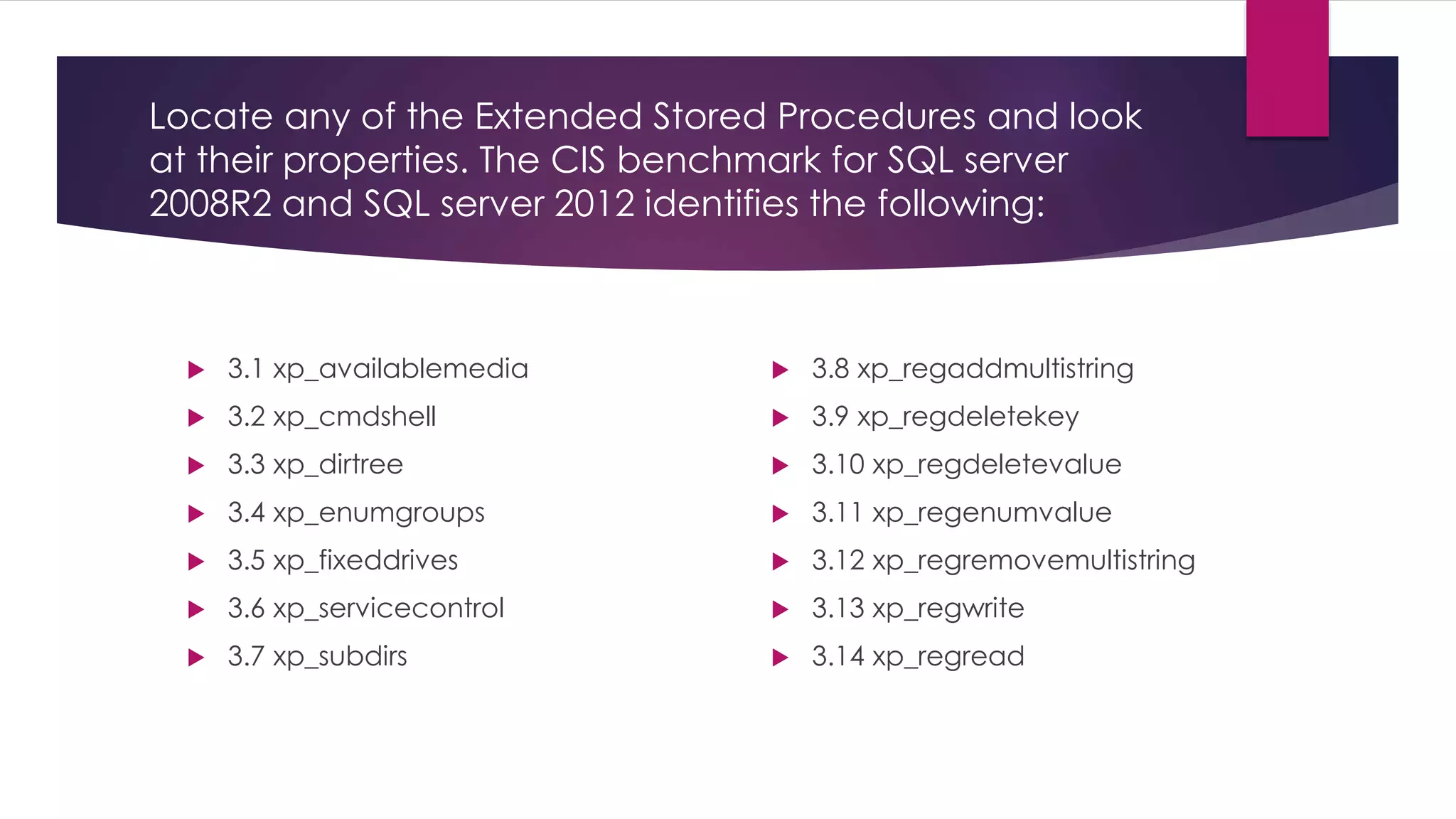
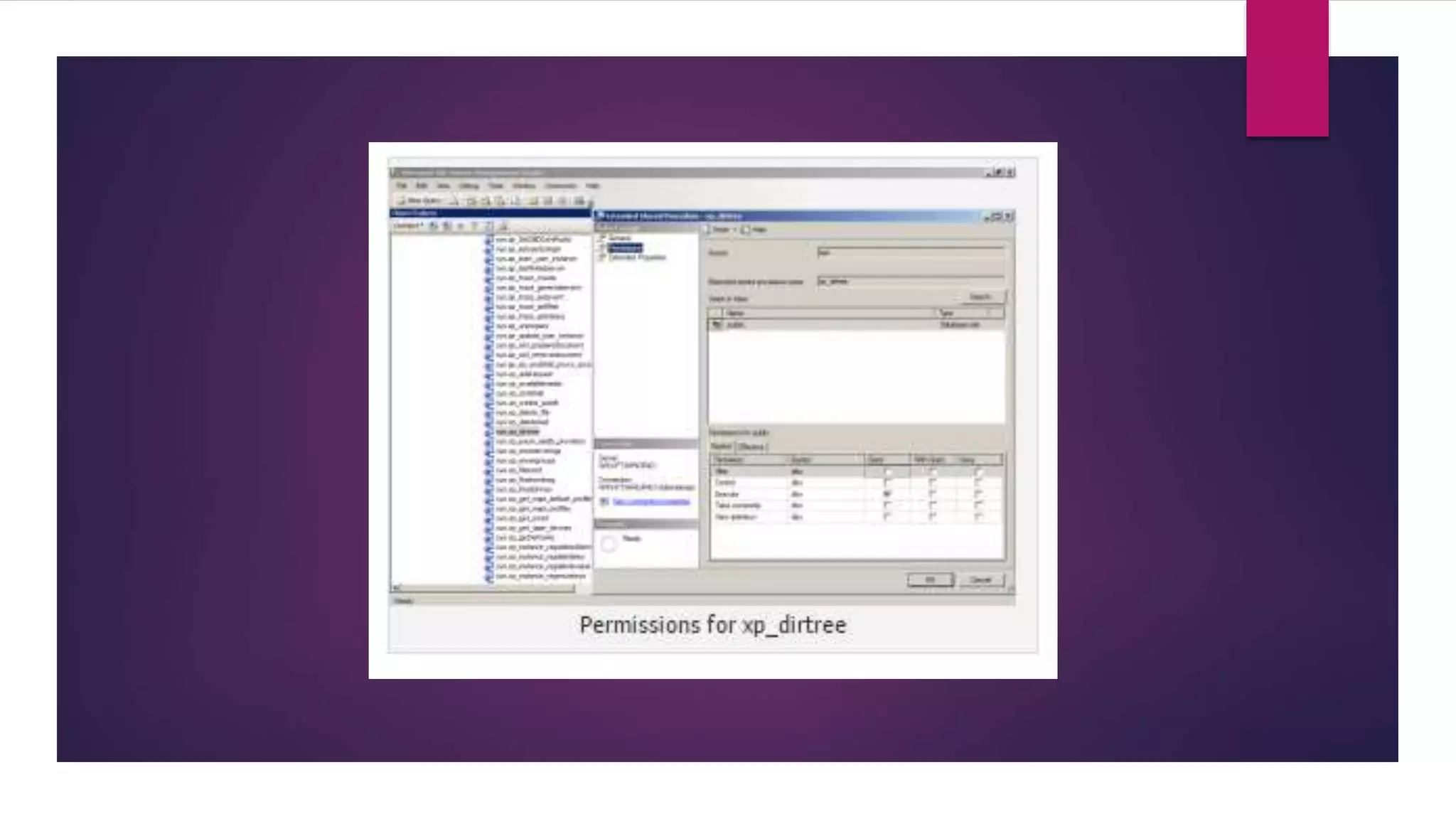
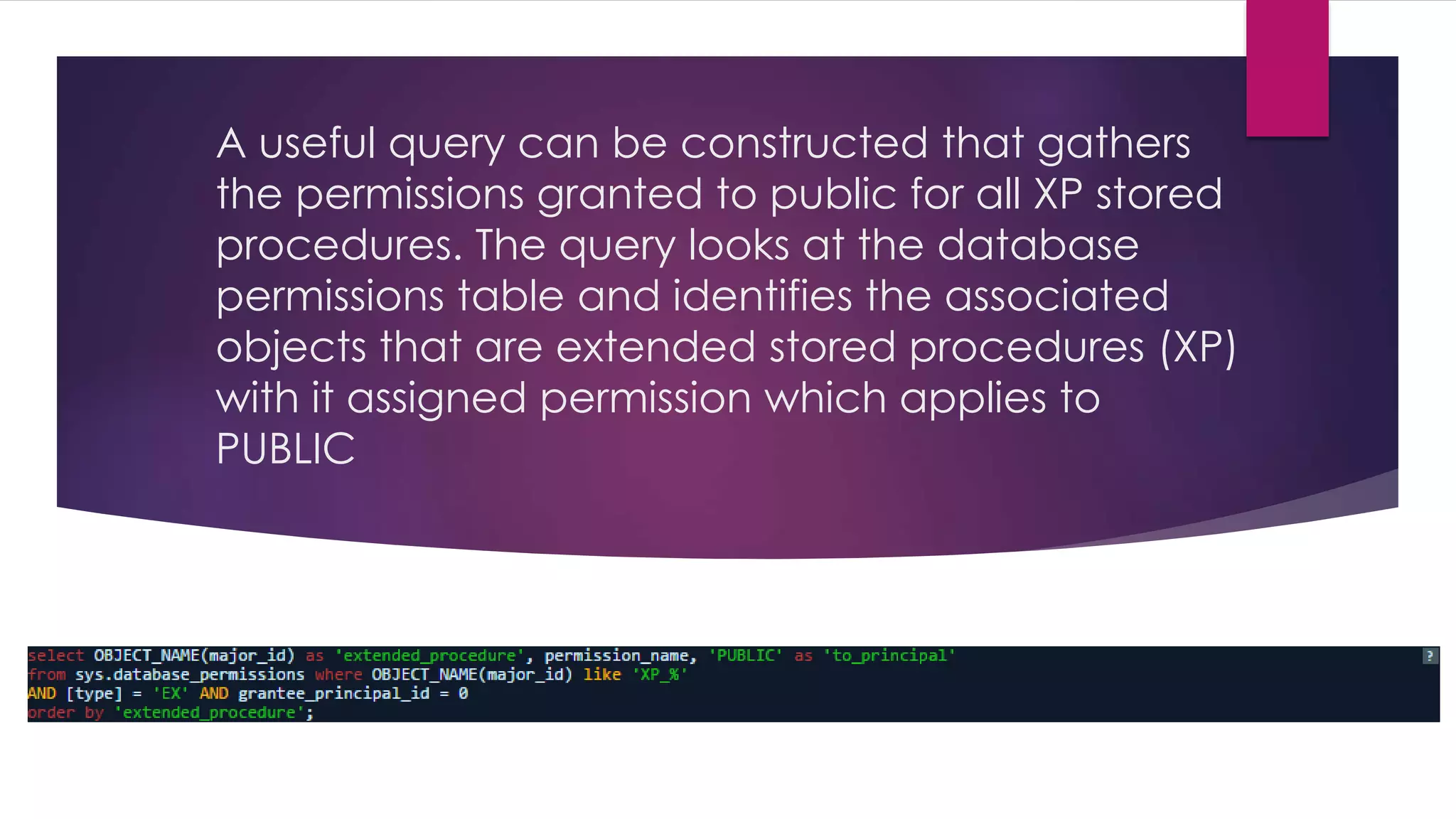
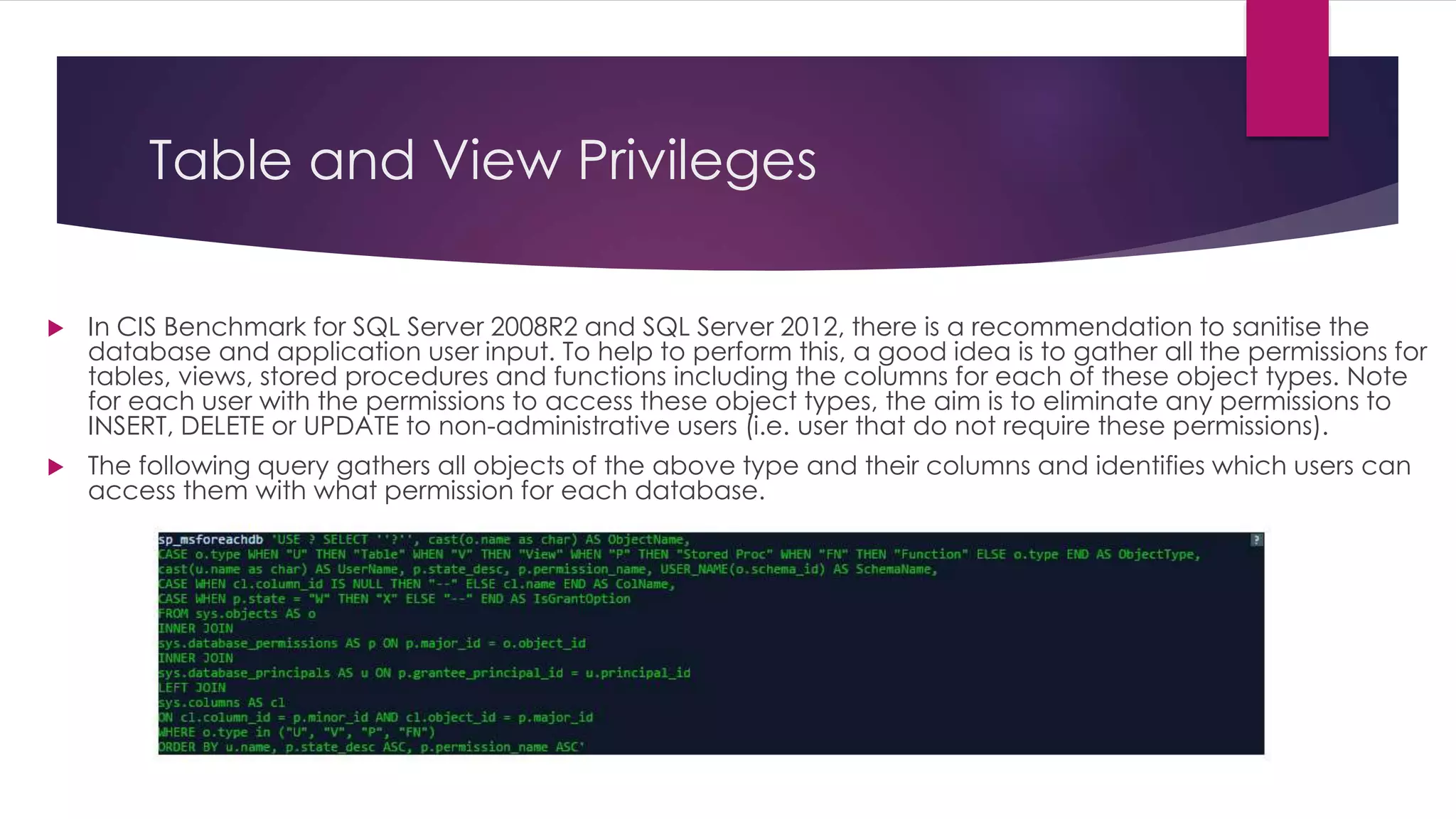
The document provides an overview of extended stored procedures in SQL Server, highlighting that they call functions from dynamic-link library (DLL) files but are deprecated in SQL Server 2012. It emphasizes the importance of disabling these procedures and understanding table privileges to prevent unauthorized data modification, following guidelines from the Centre for Internet Security (CIS). Additionally, it includes methods for identifying and assessing permissions on extended stored procedures and other database objects.