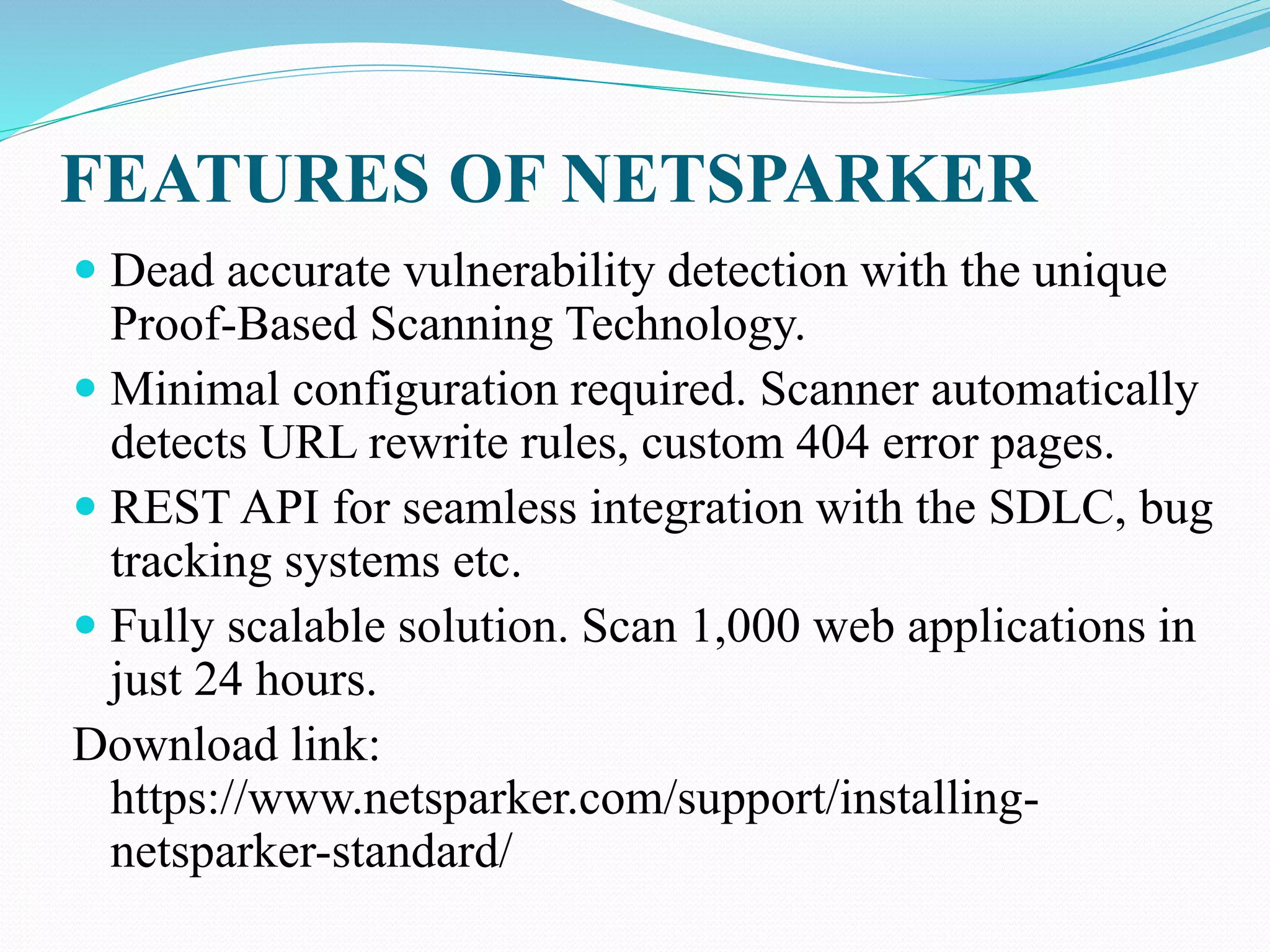
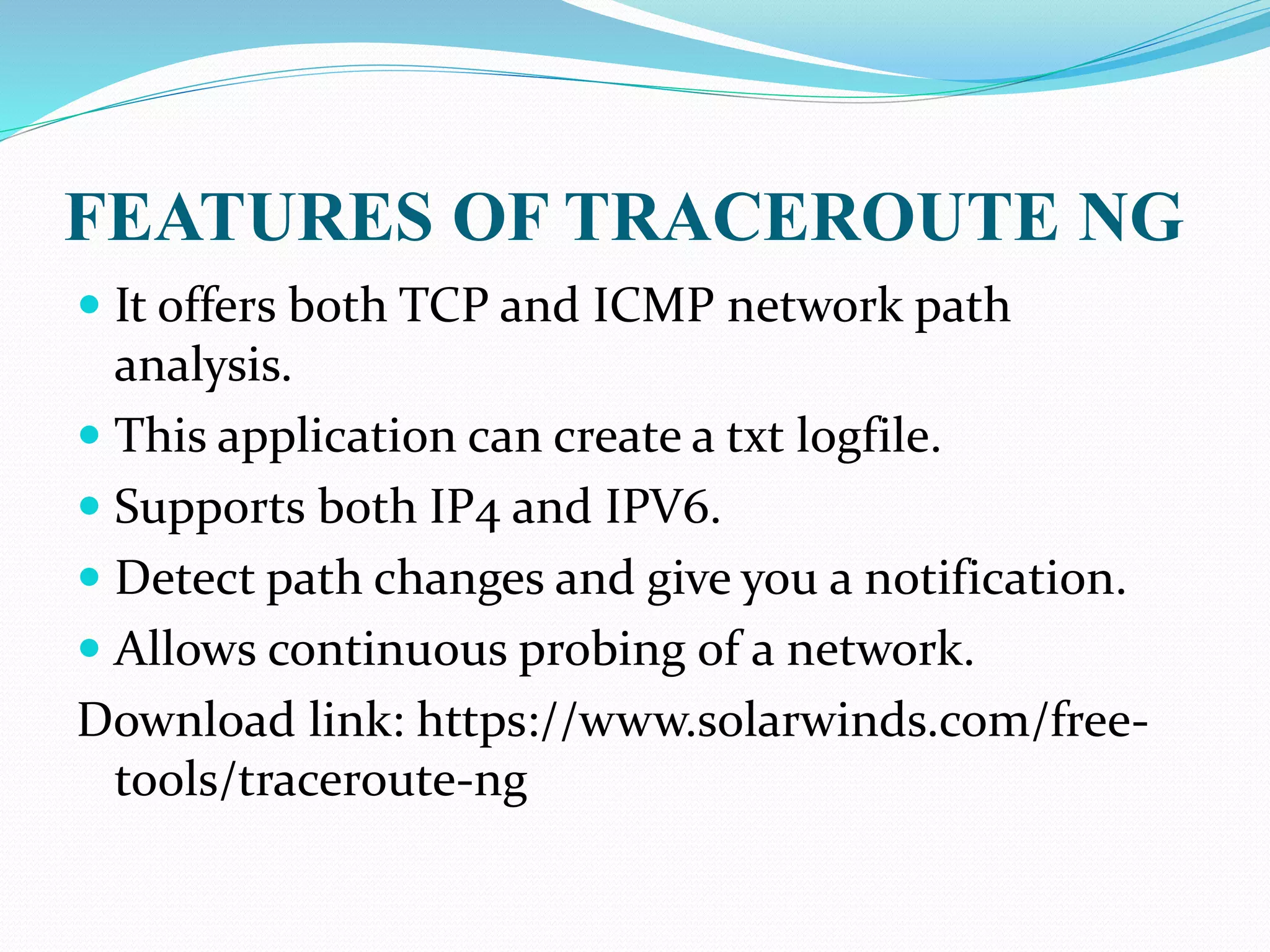
The document discusses hacking tools, including what they are, their types, and some examples. Hacking tools help find weaknesses in computer systems and networks to test security. The document provides details on three hacking tools: Netsparker scans for vulnerabilities in web applications, Traceroute NG analyzes network paths, and Aircrack-NG cracks wireless encryption keys. While these tools can strengthen security, they can also enable privacy violations and security breaches if misused.