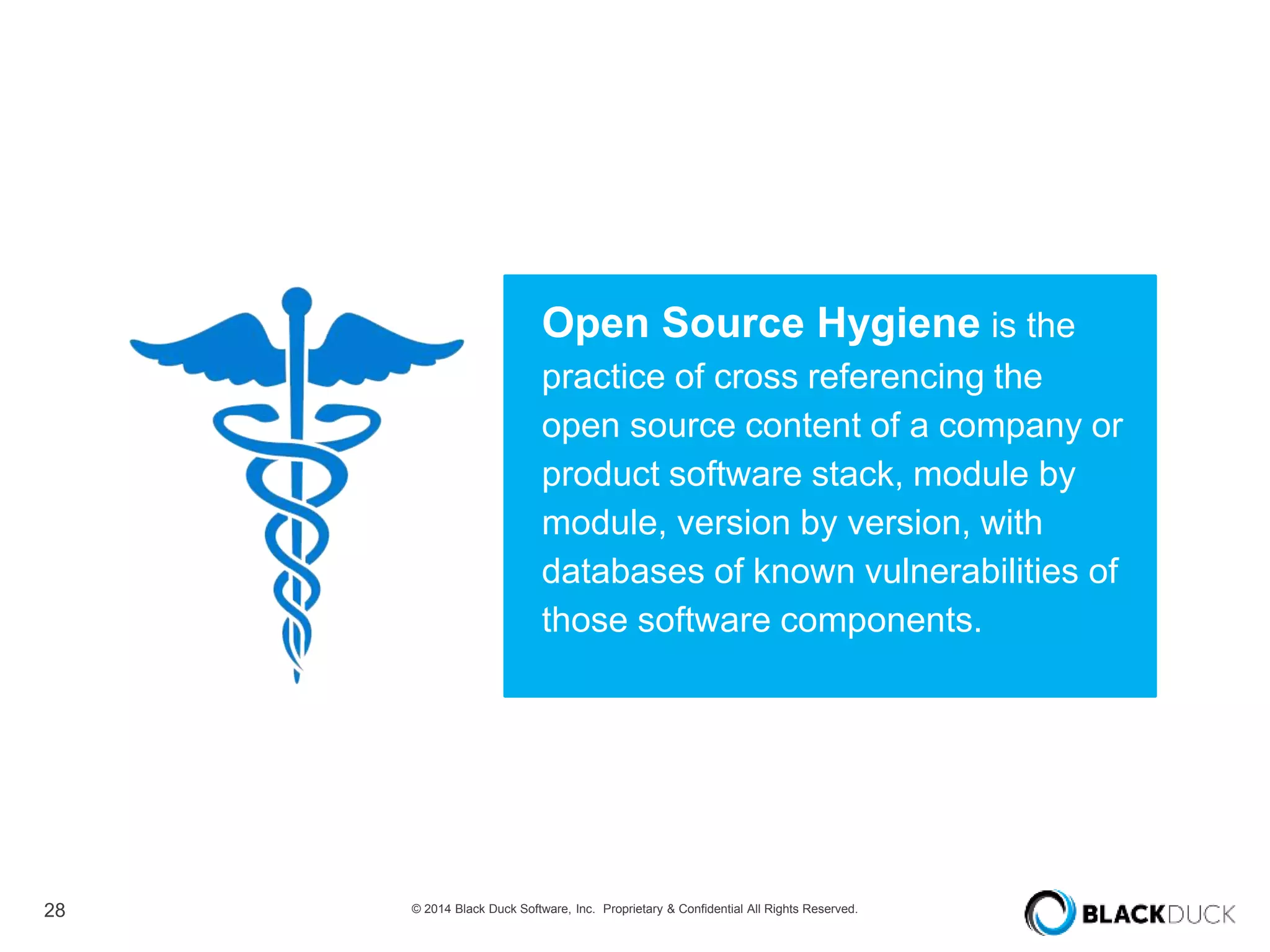
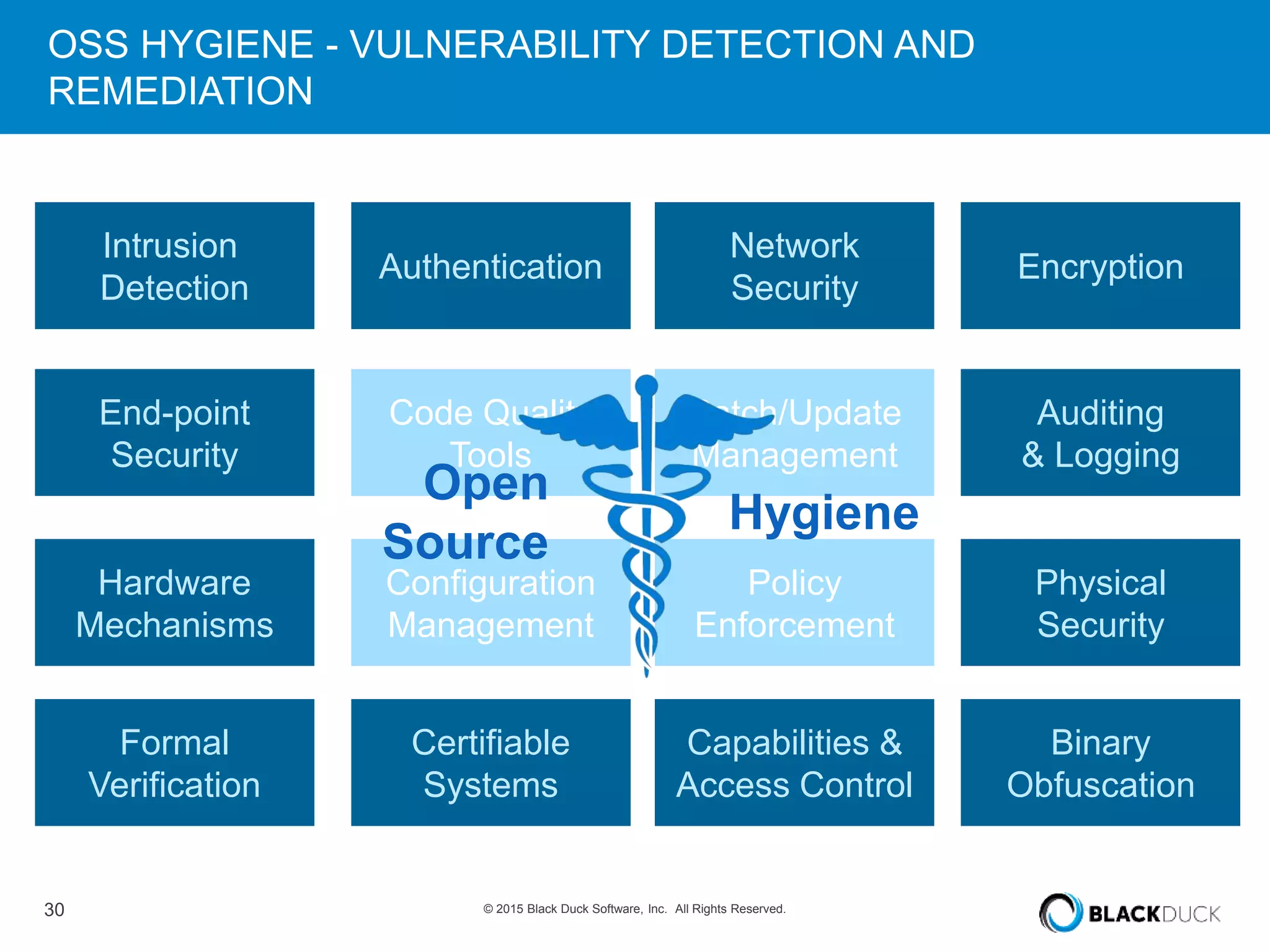
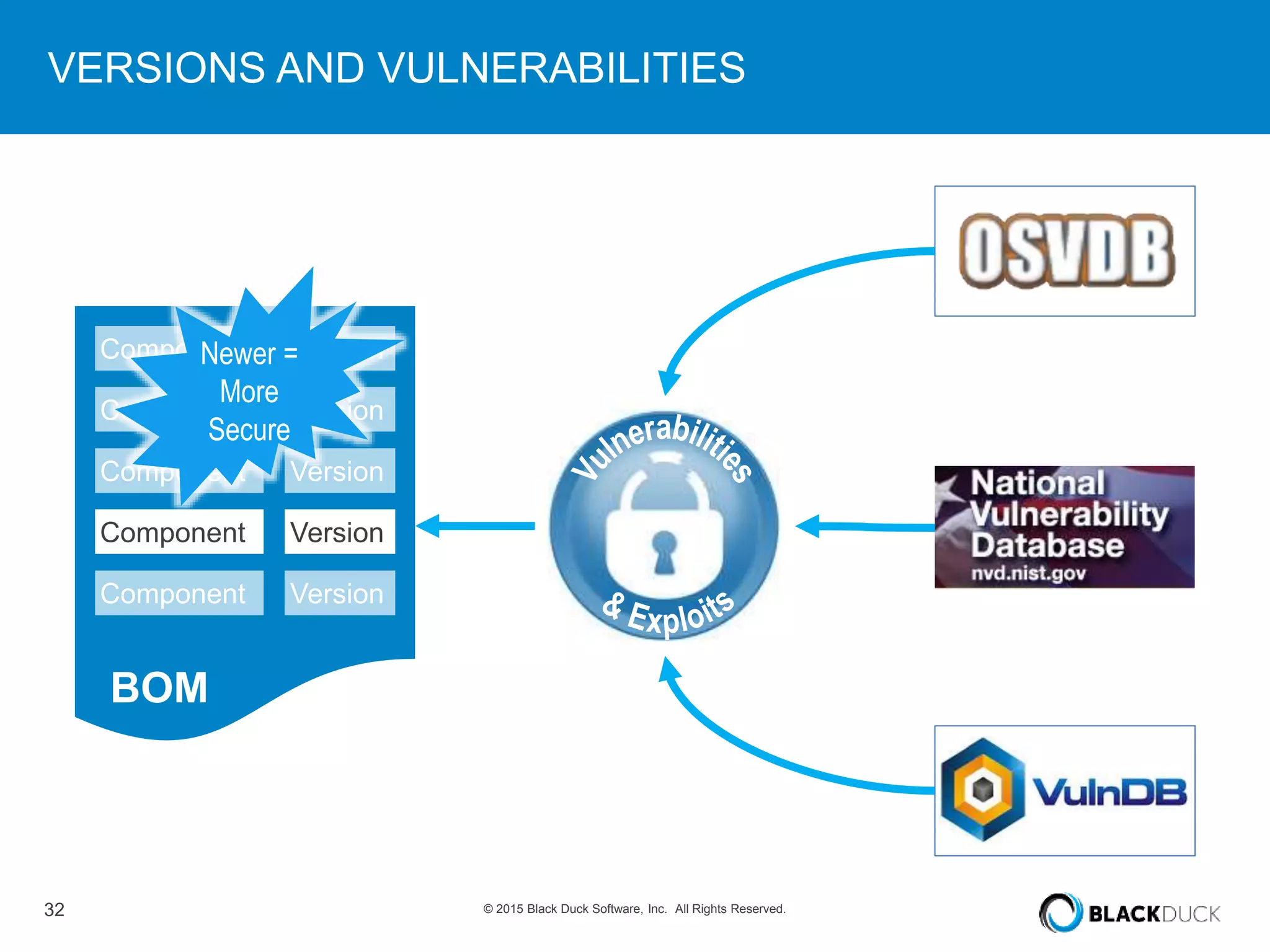
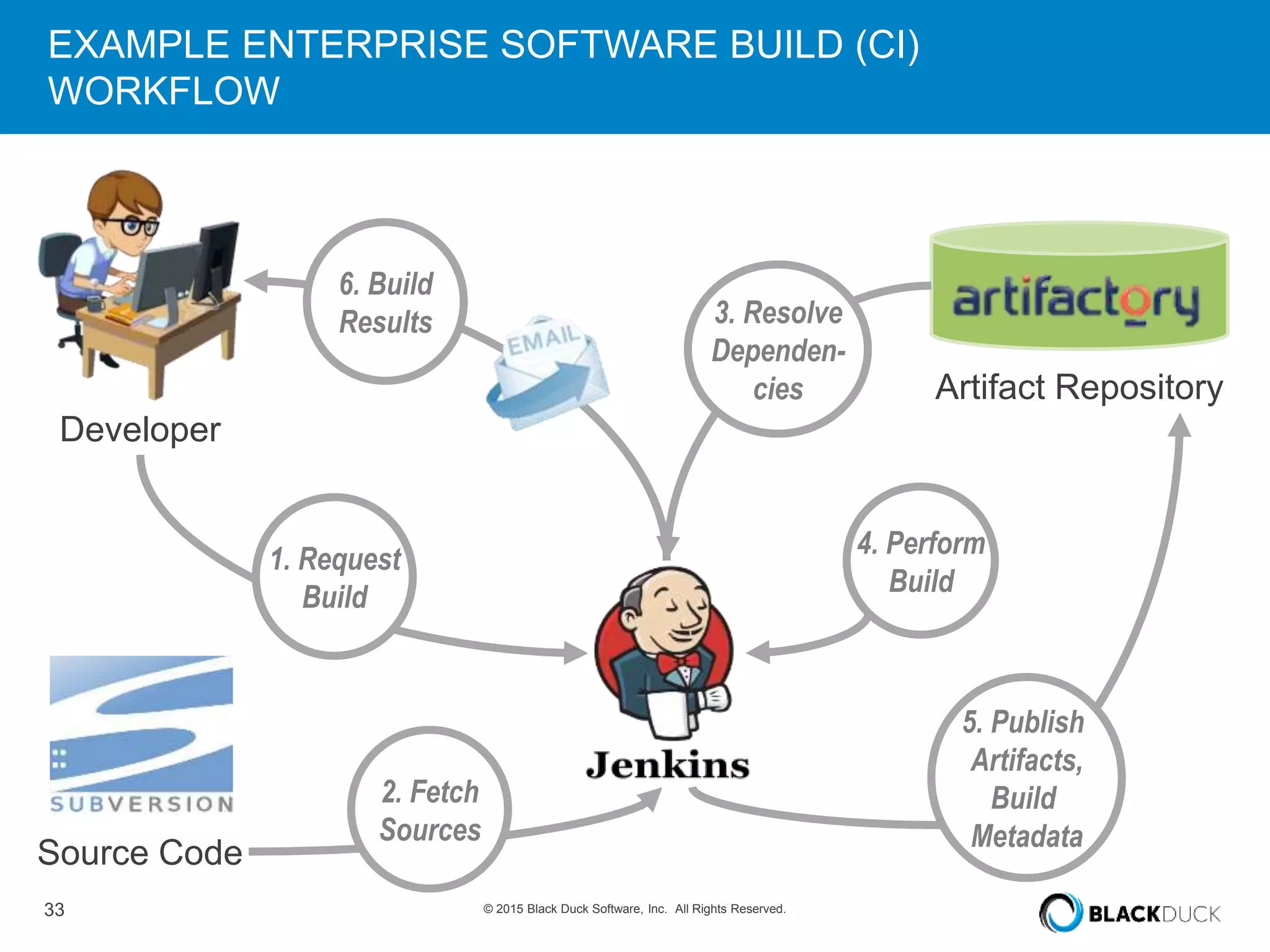
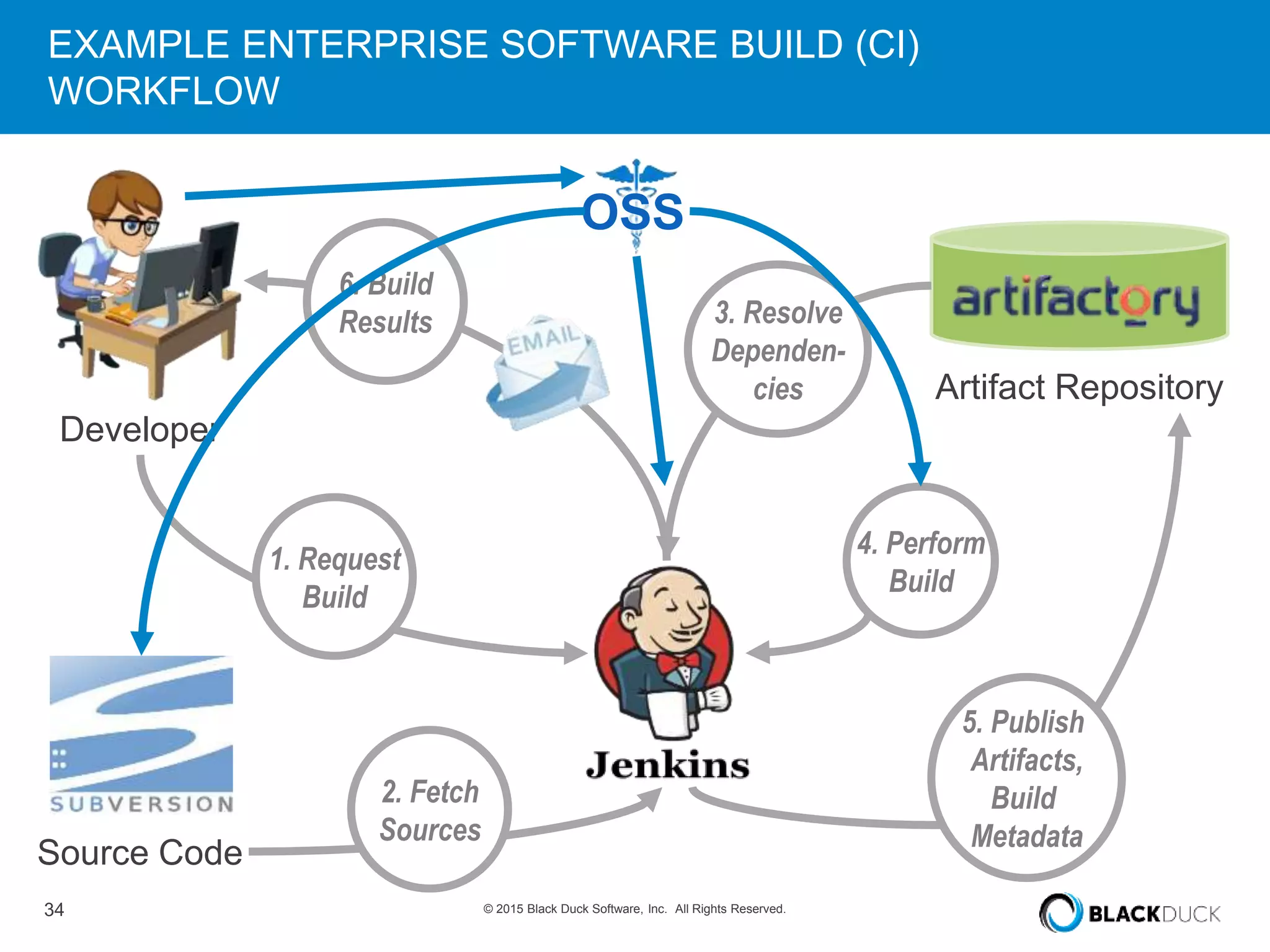
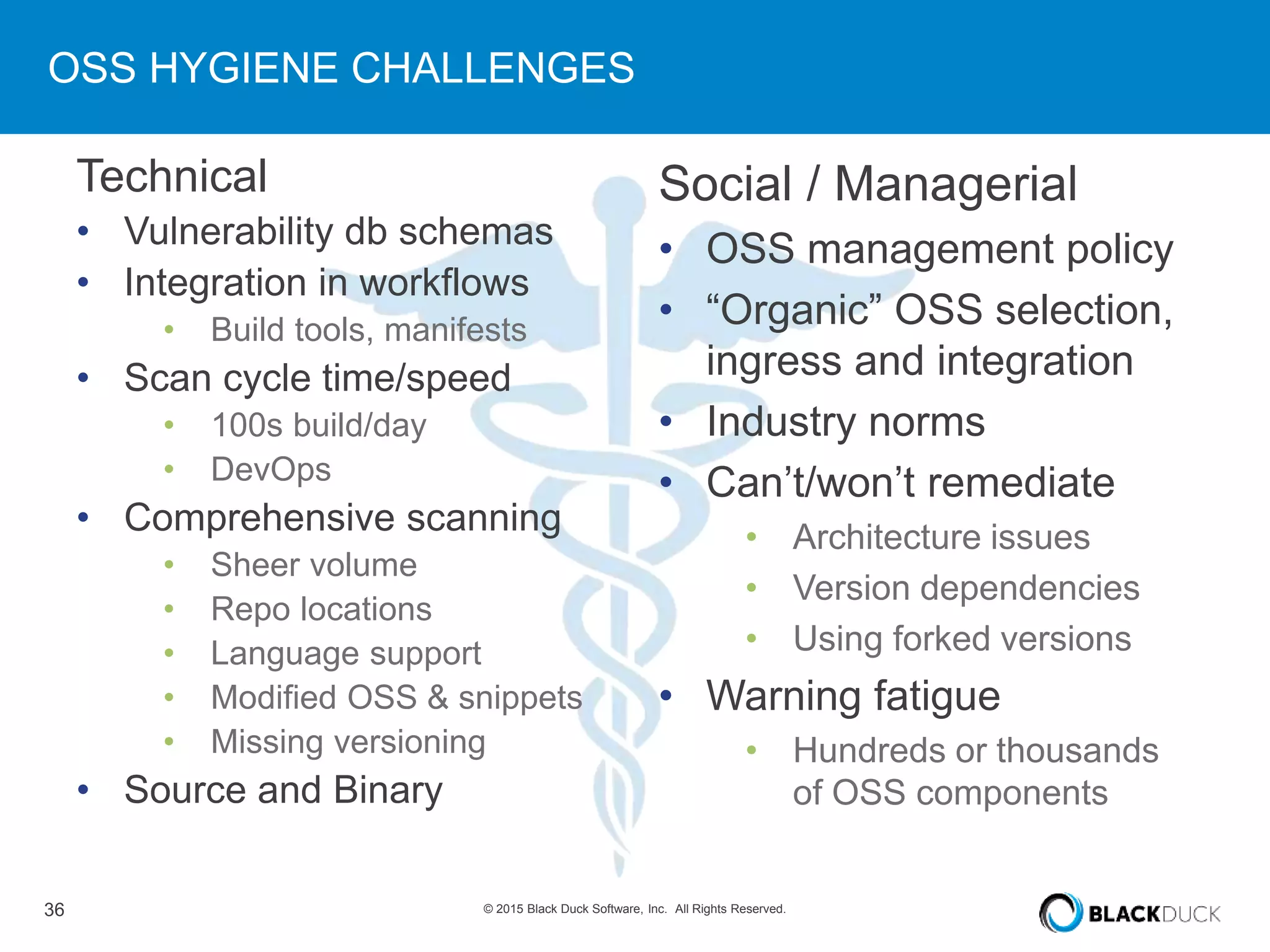
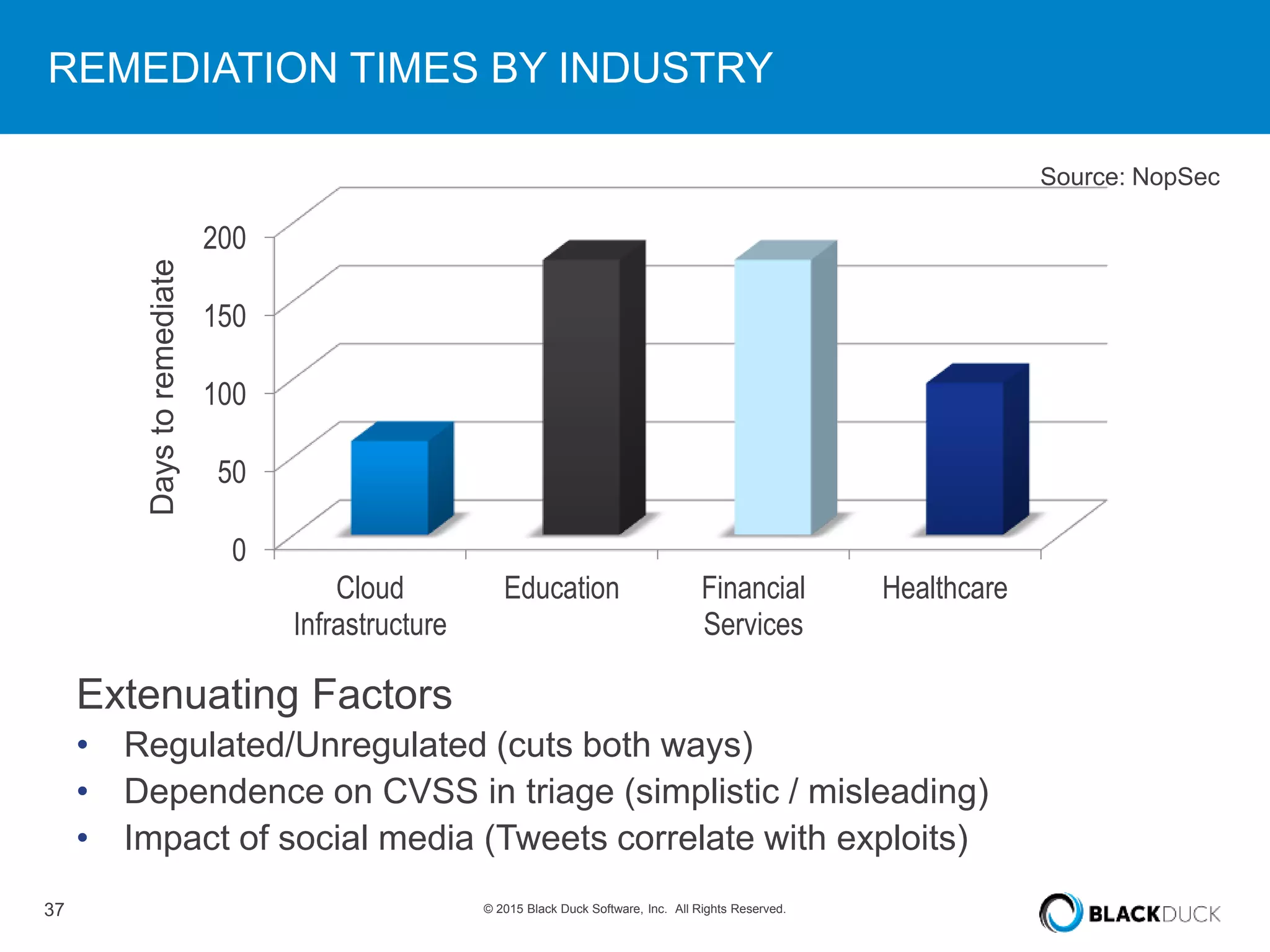
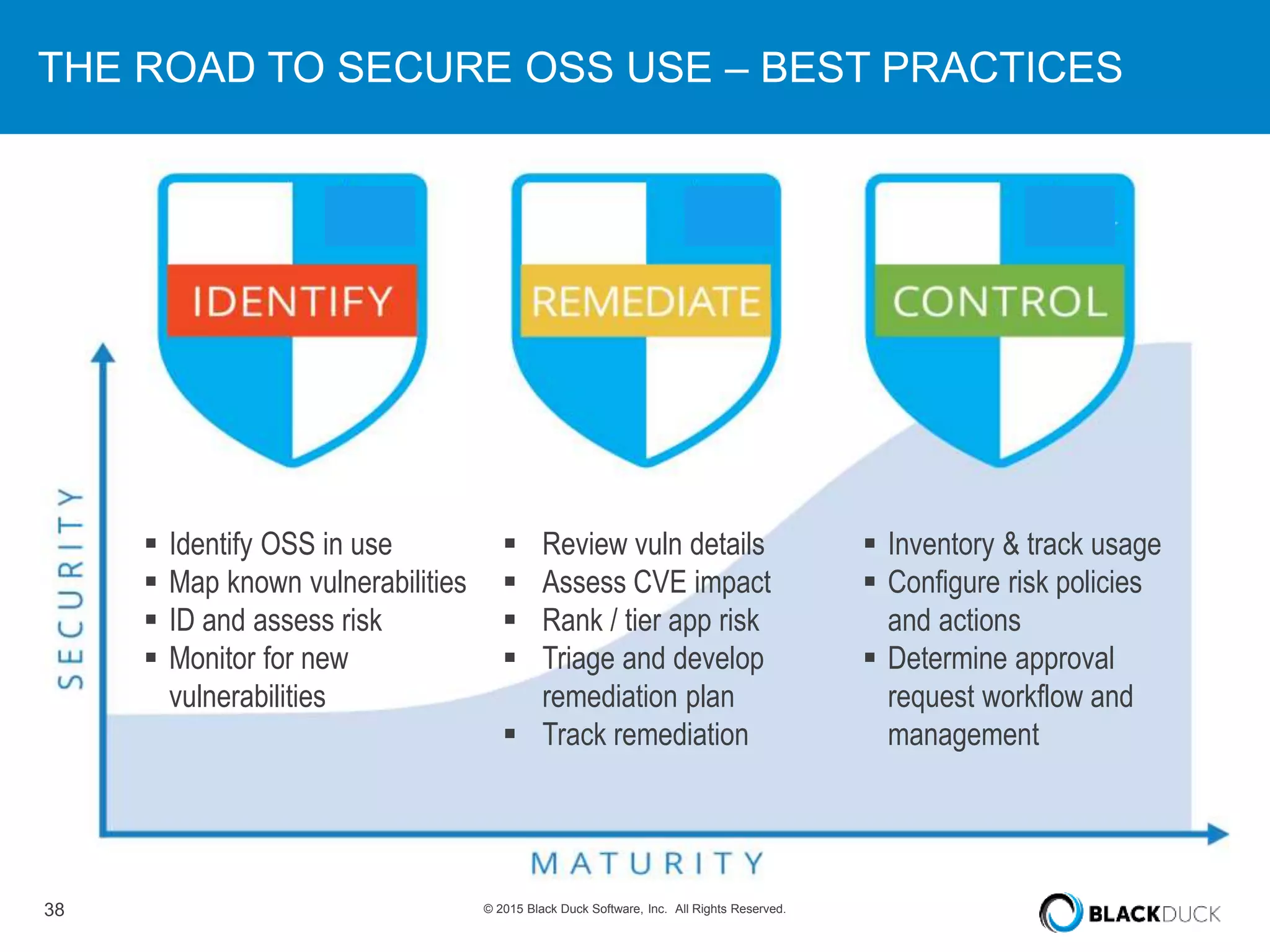
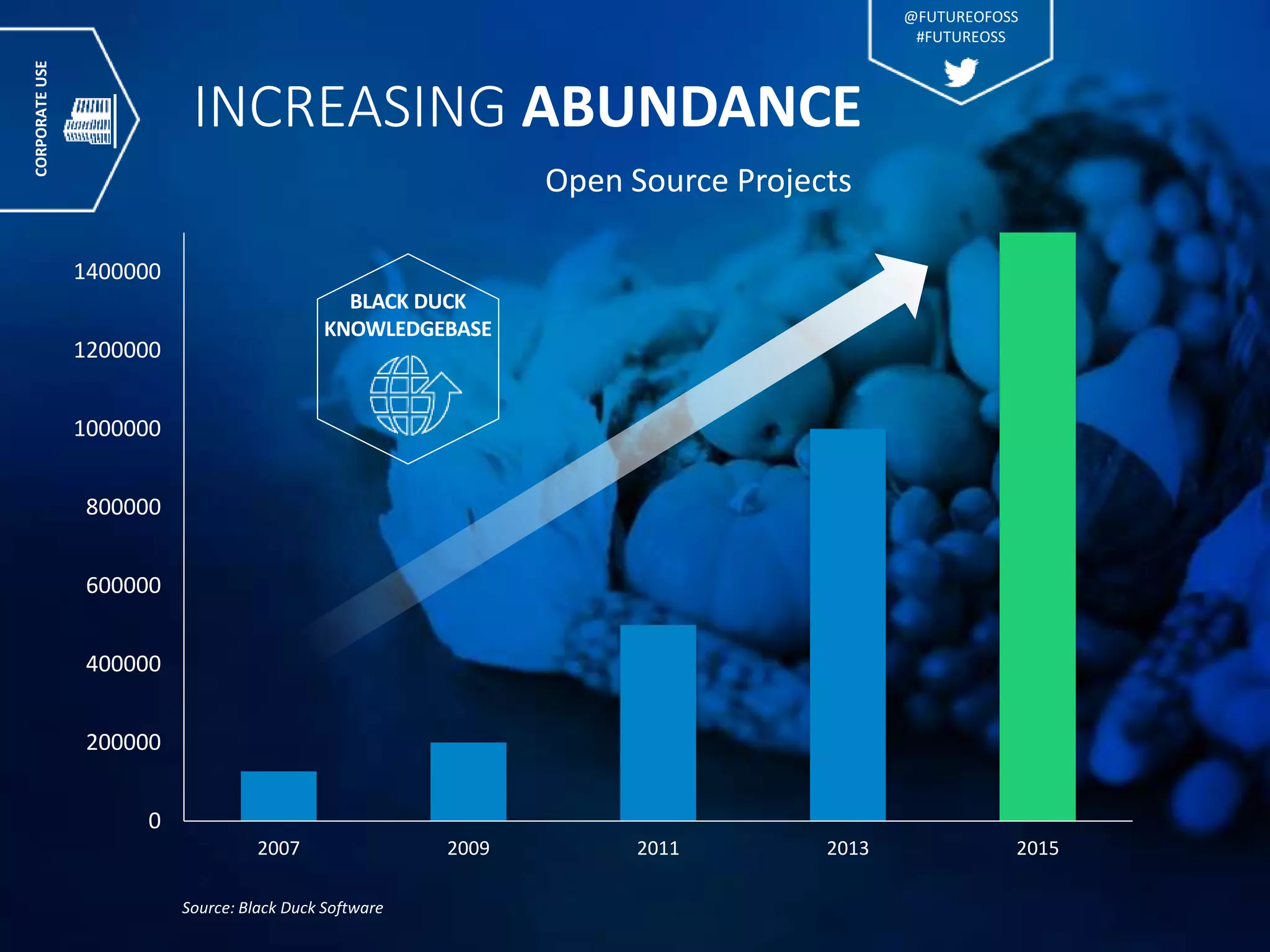
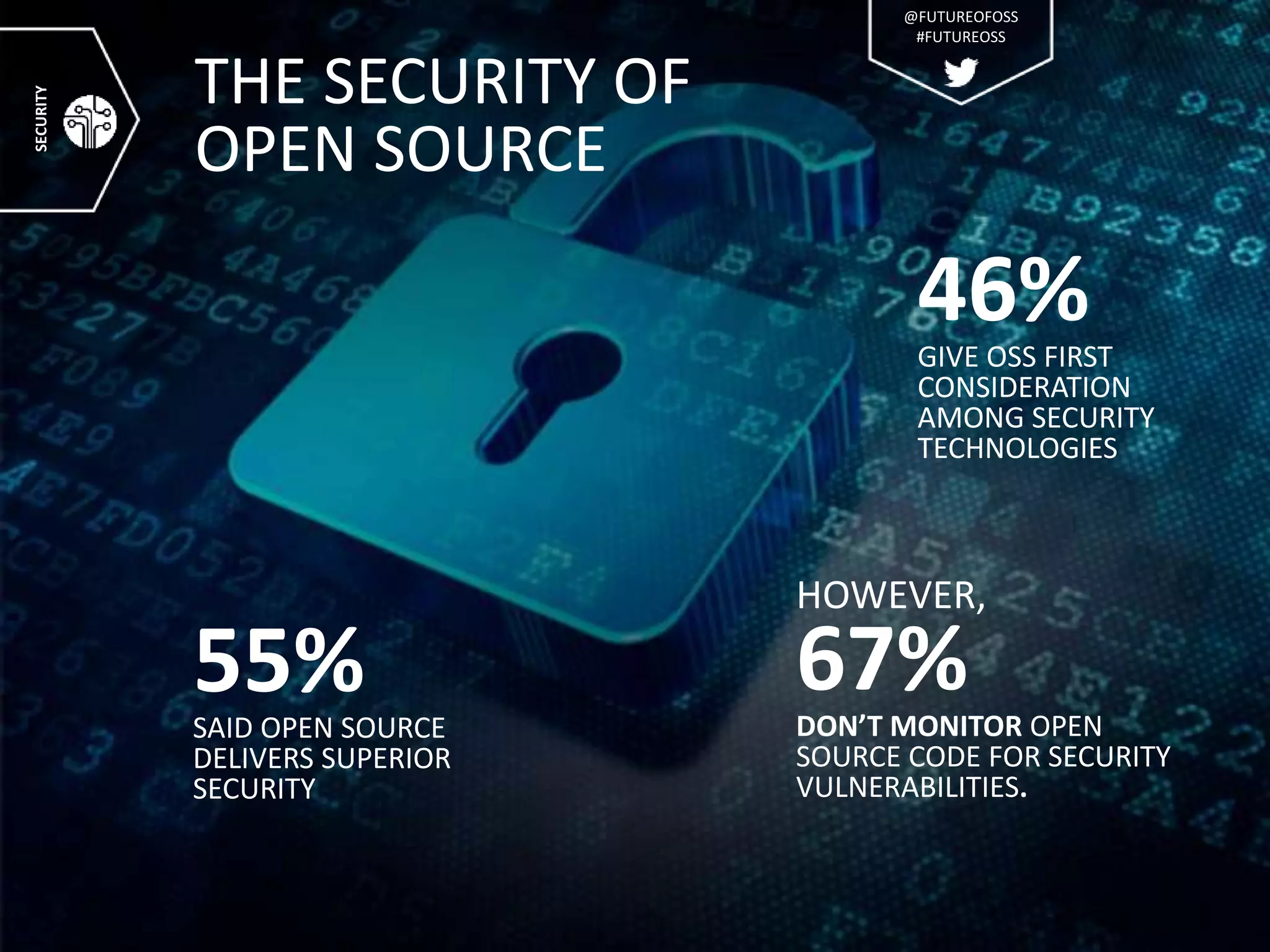
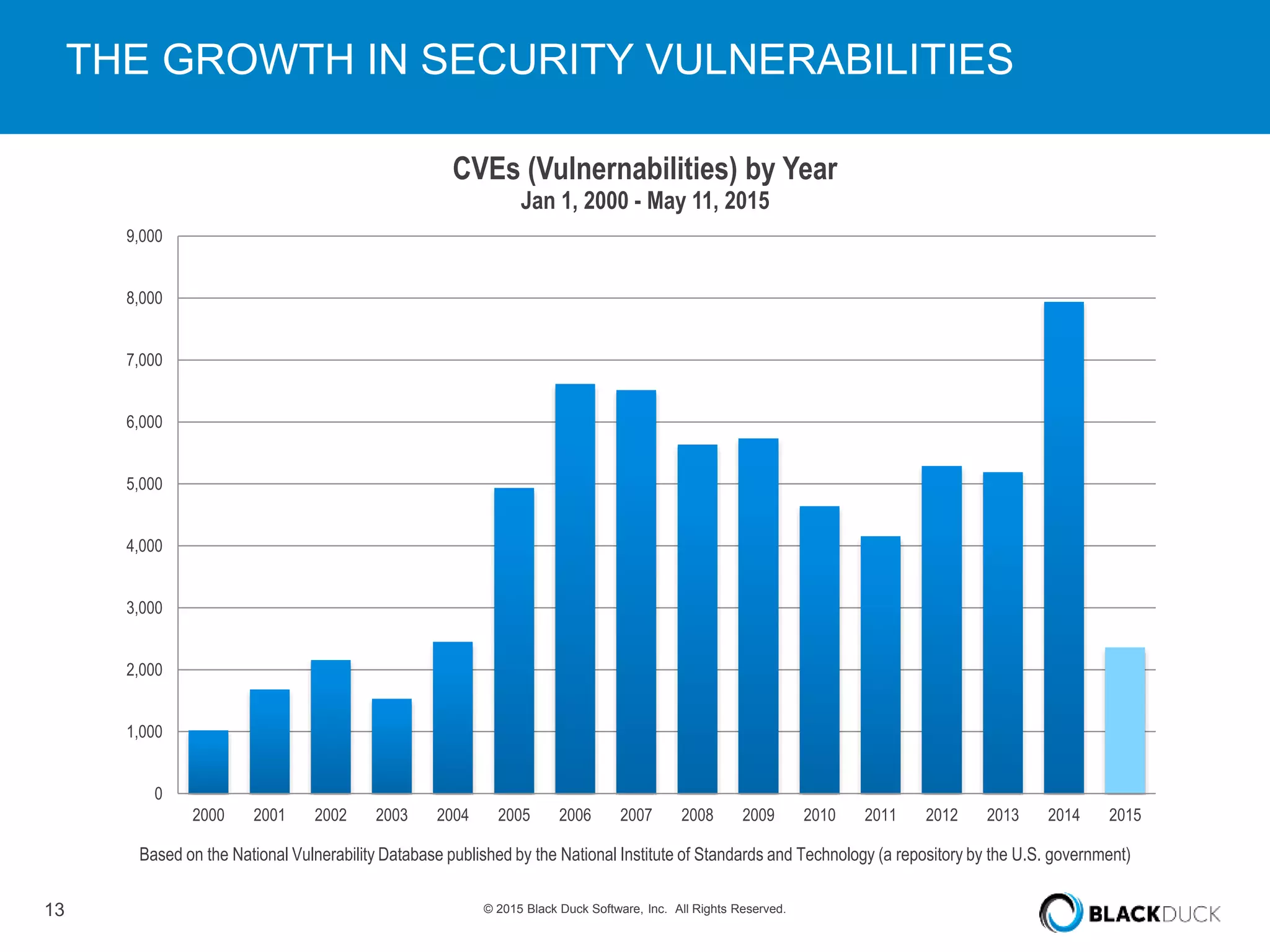
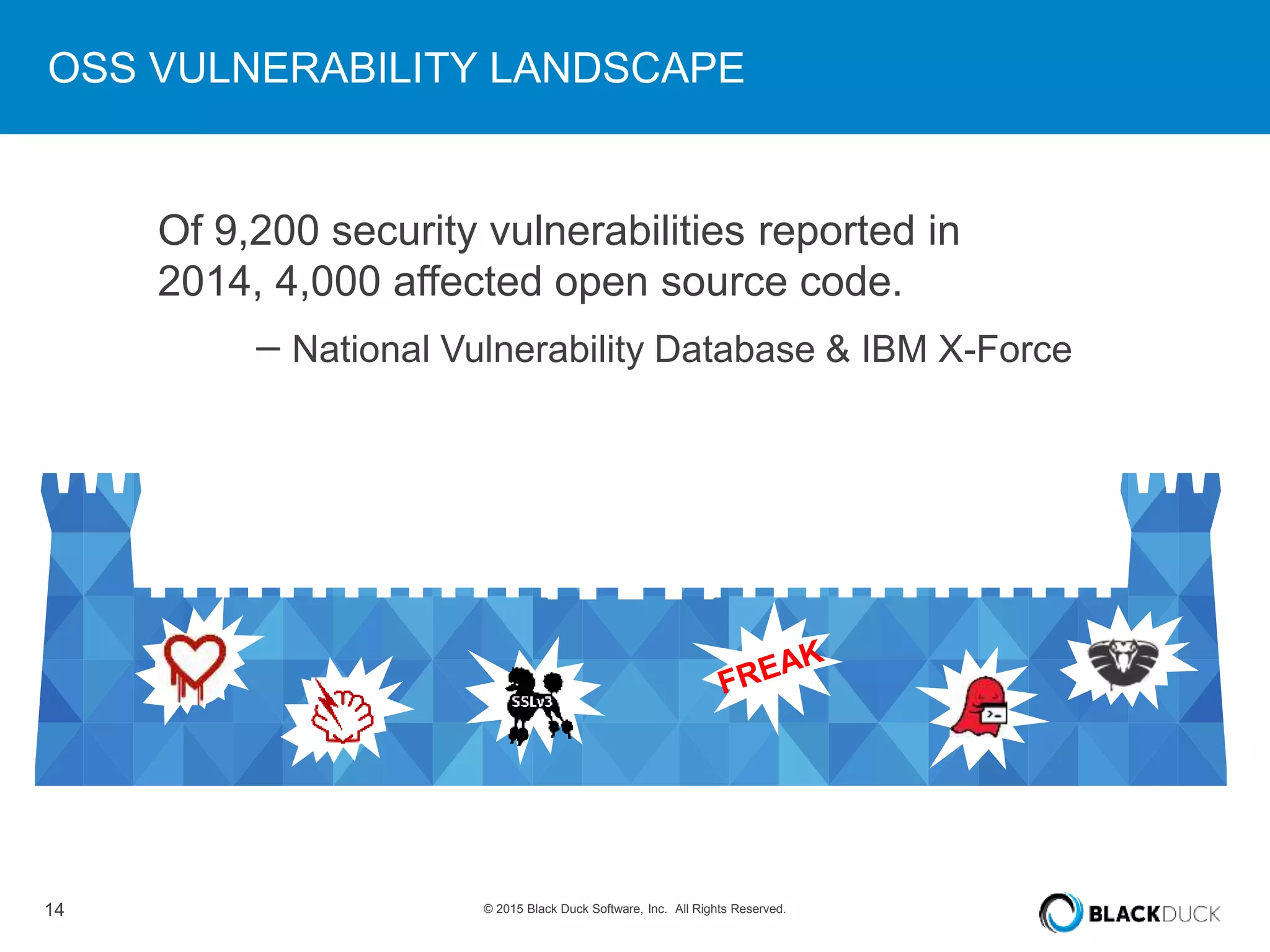
The presentation discusses the pervasive use of open source software (OSS) and the associated security, operational, and legal risks that arise from its development and deployment. It emphasizes the importance of 'open source hygiene'—practices for cross-referencing OSS components against known vulnerabilities to mitigate risks. Additionally, it highlights the growing need for automation in managing OSS security as vulnerabilities continue to increase.













![26 © 2015 Black Duck Software, Inc. All Rights Reserved.
HYGIENE?
hy·giene /ˈhīˌjēn/ [‘hai dji:n]
conditions or practices conducive to maintaining health and
preventing disease, especially through cleanliness.
synonyms: cleanliness, sanitation, sterility, purity,
disinfection](https://image.slidesharecdn.com/rv4secbillweinbergopensourcehygienepresentation-150714171904-lva1-app6891/75/RVAsec-Bill-Weinberg-Open-Source-Hygiene-Presentation-26-2048.jpg)