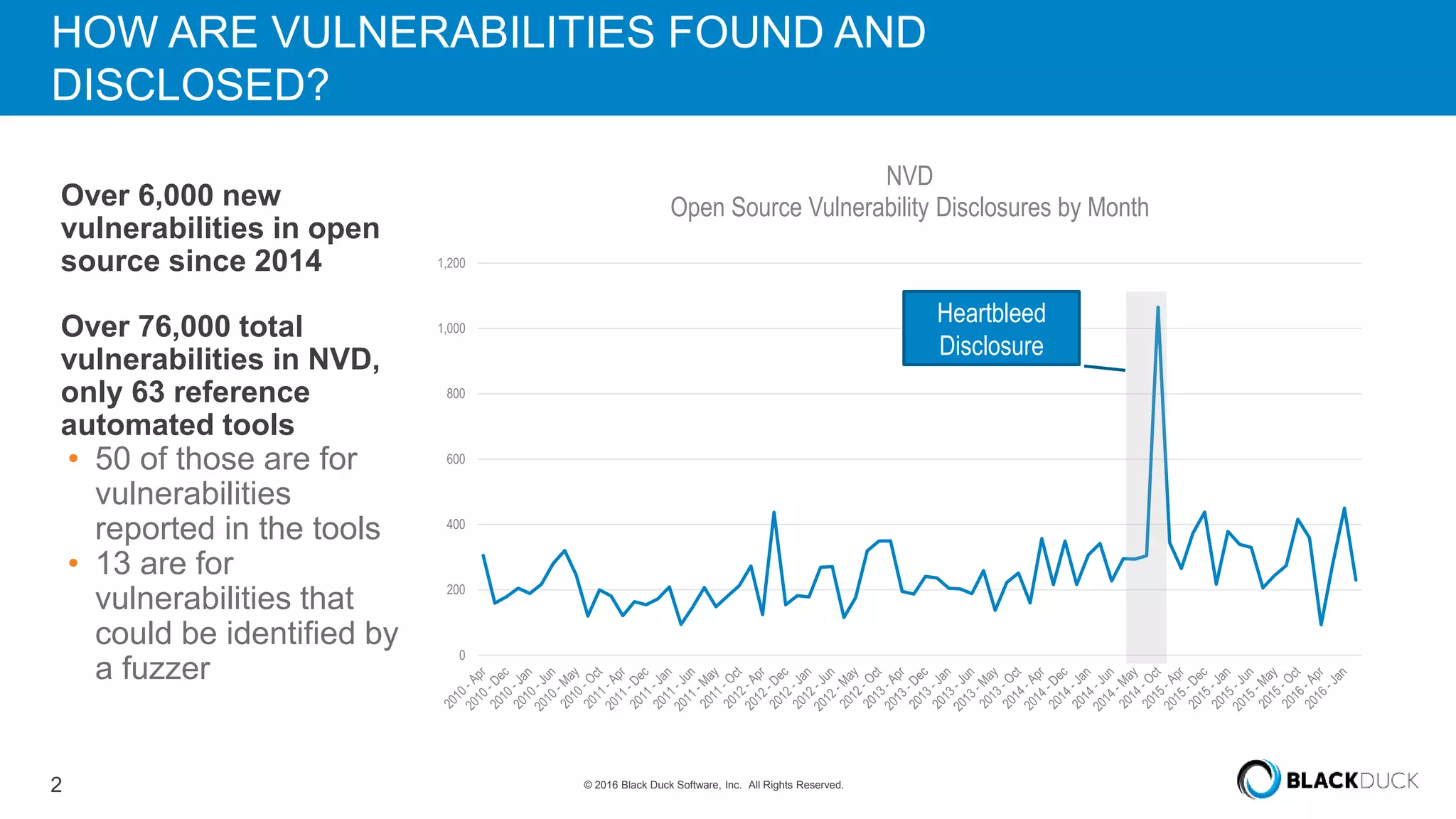
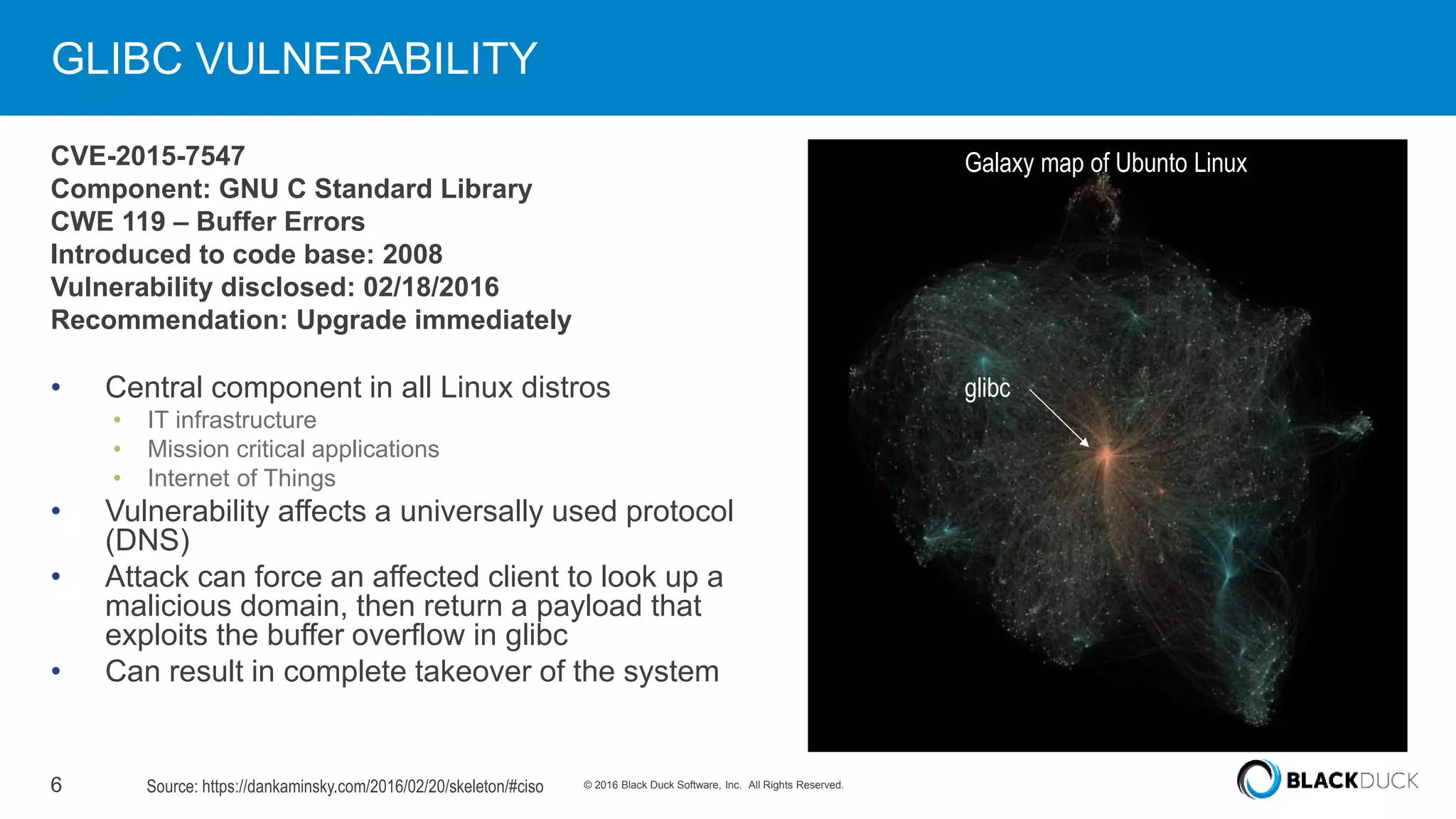
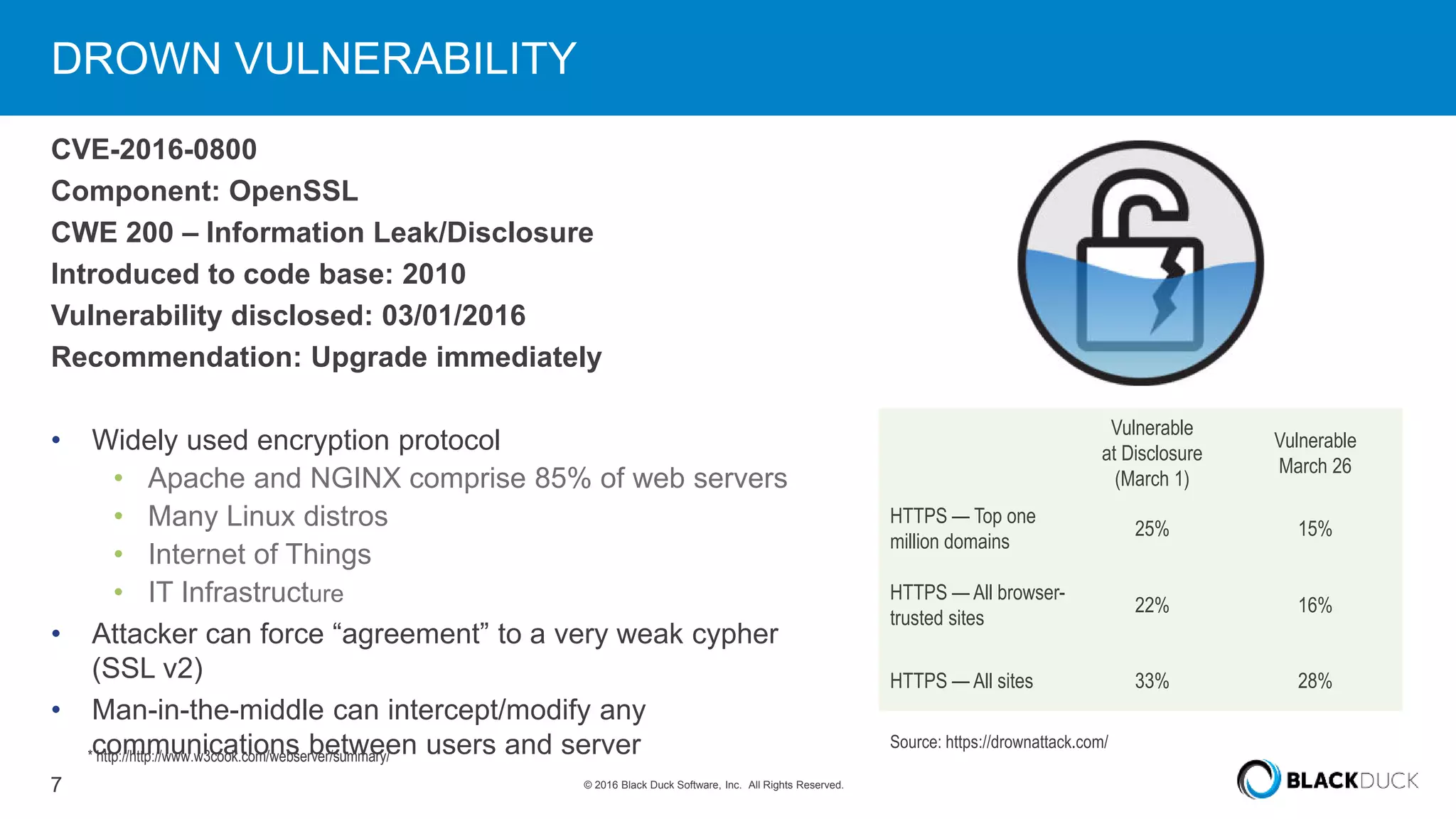
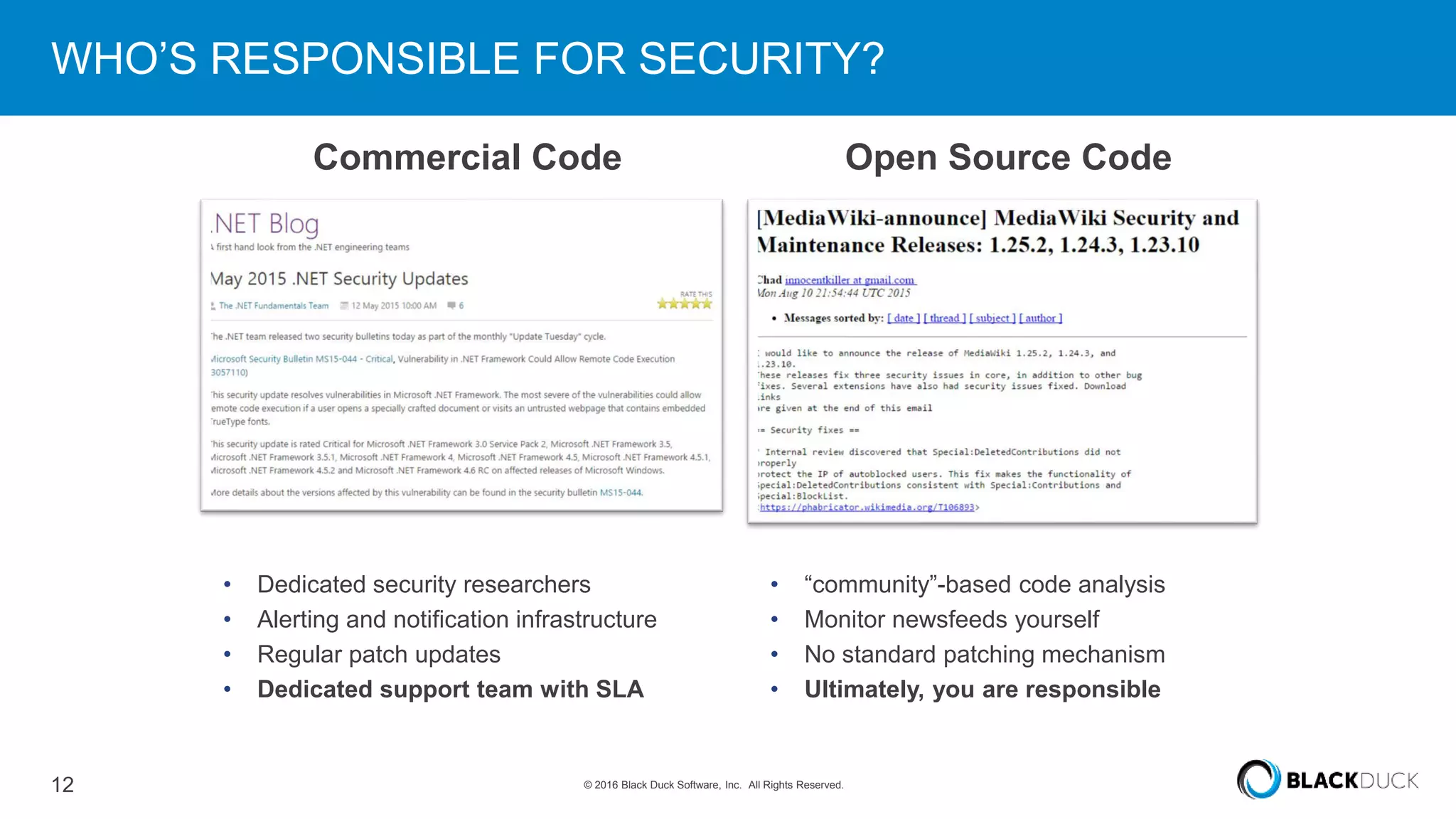
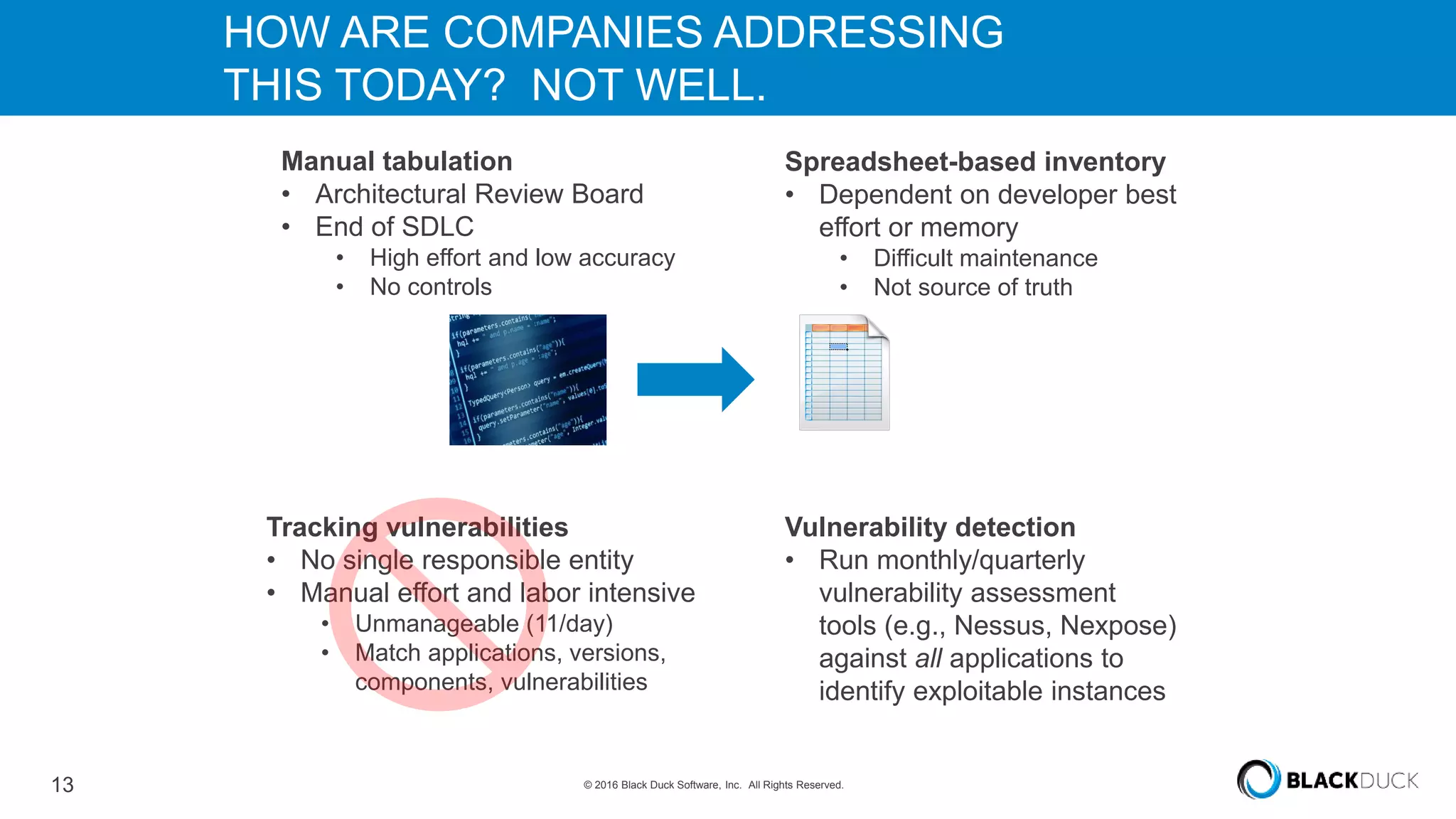
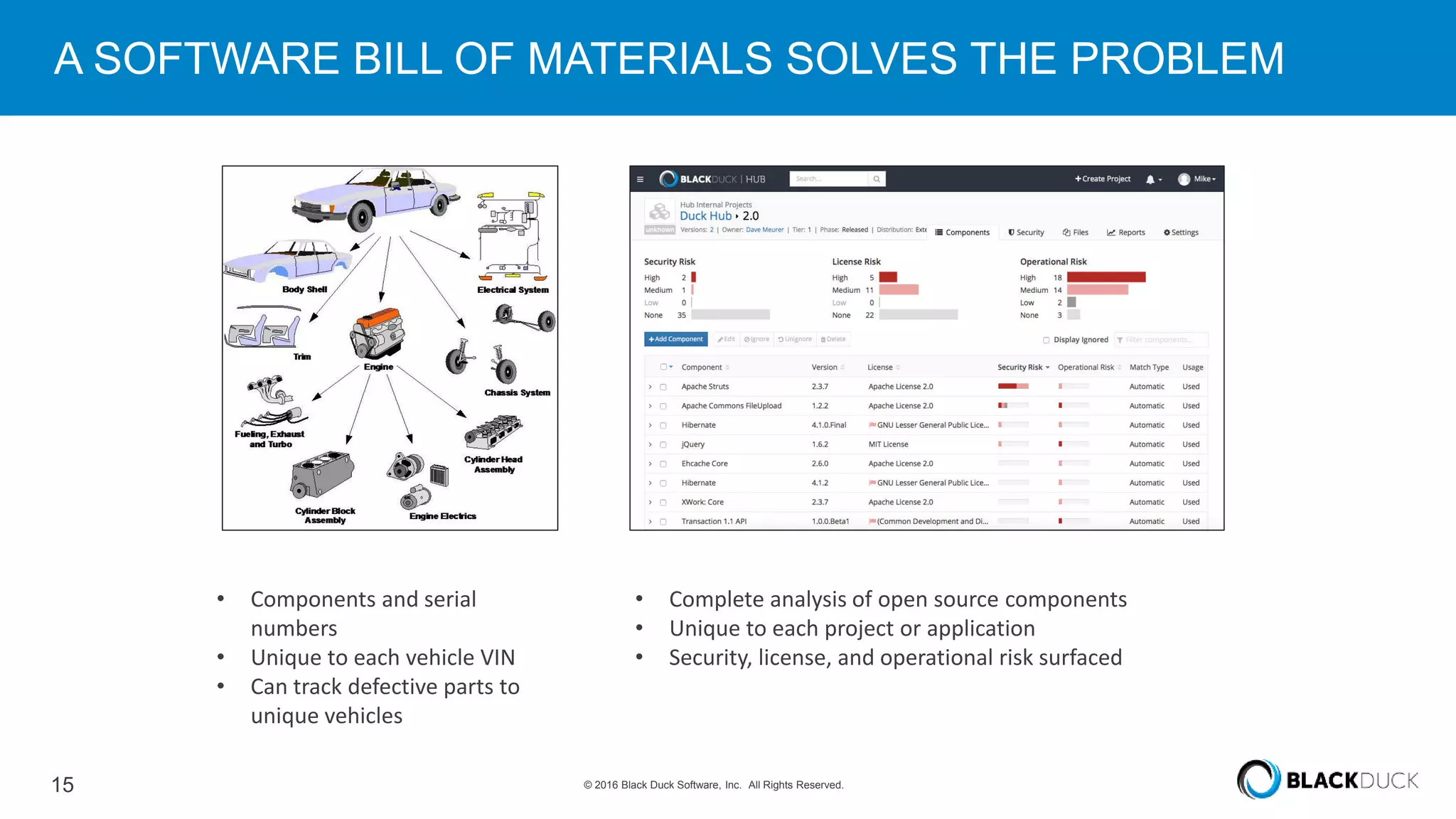
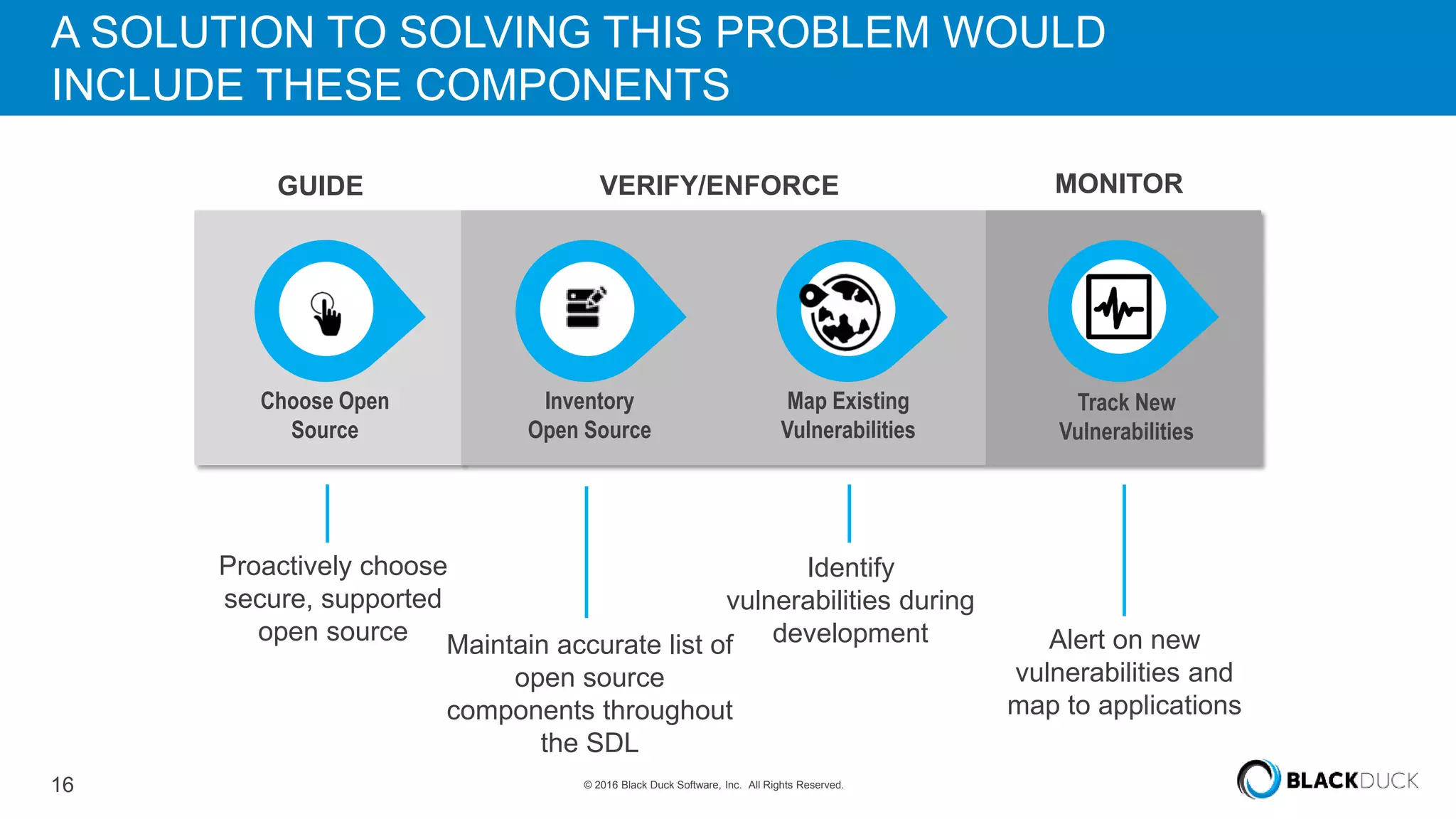
Over 6,000 new open source vulnerabilities have been discovered since 2014. In Q1 2016, 960 new vulnerabilities were found, a 20% increase over Q1 2015. Common vulnerability types include buffer errors and input validation issues. Notable vulnerabilities included issues in glibc and OpenSSL (DROWN). It can be difficult for companies to manage open source security due to a lack of centralized responsibility and patching. A software bill of materials that tracks components and vulnerabilities is recommended to address this problem.