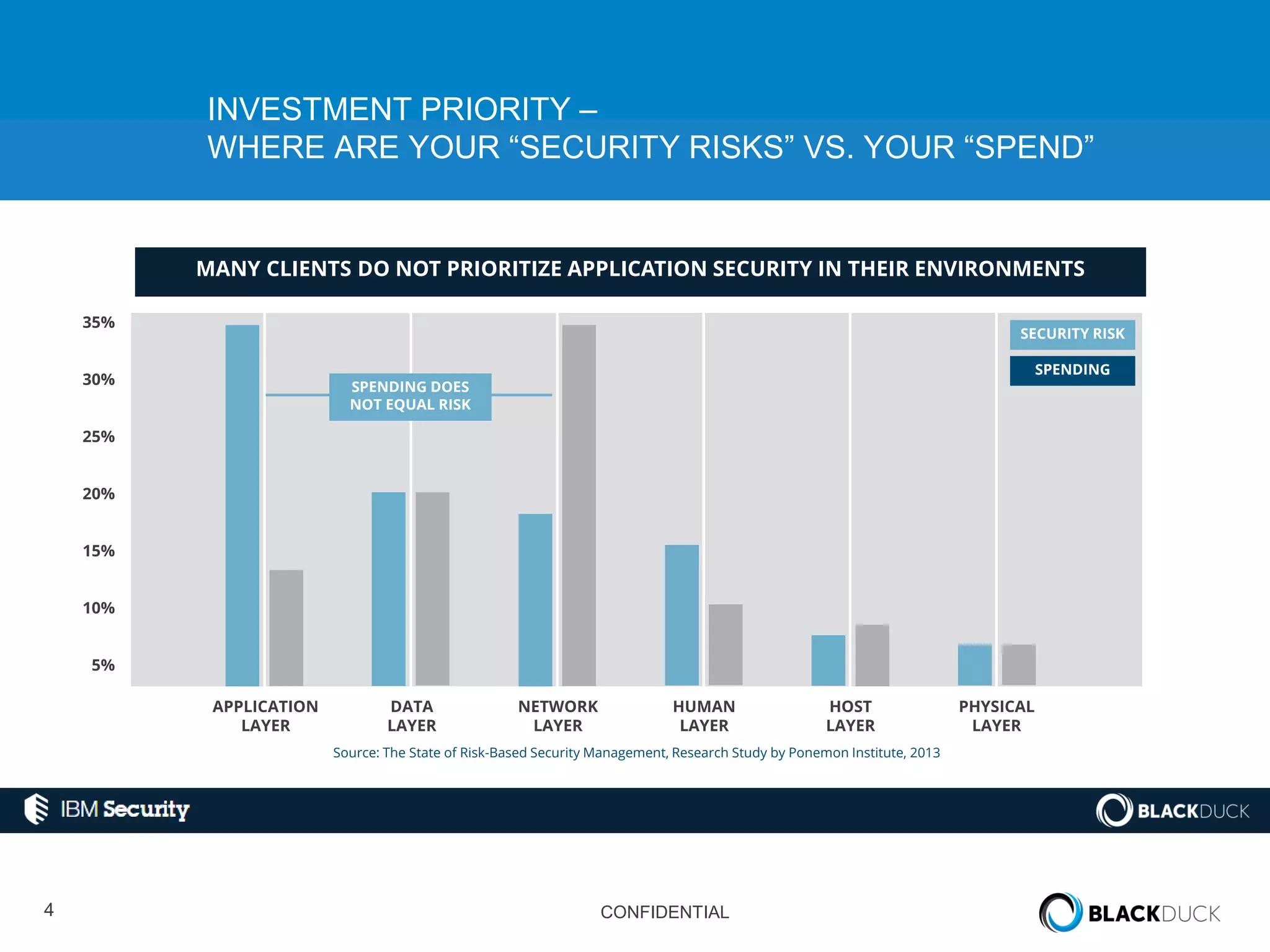
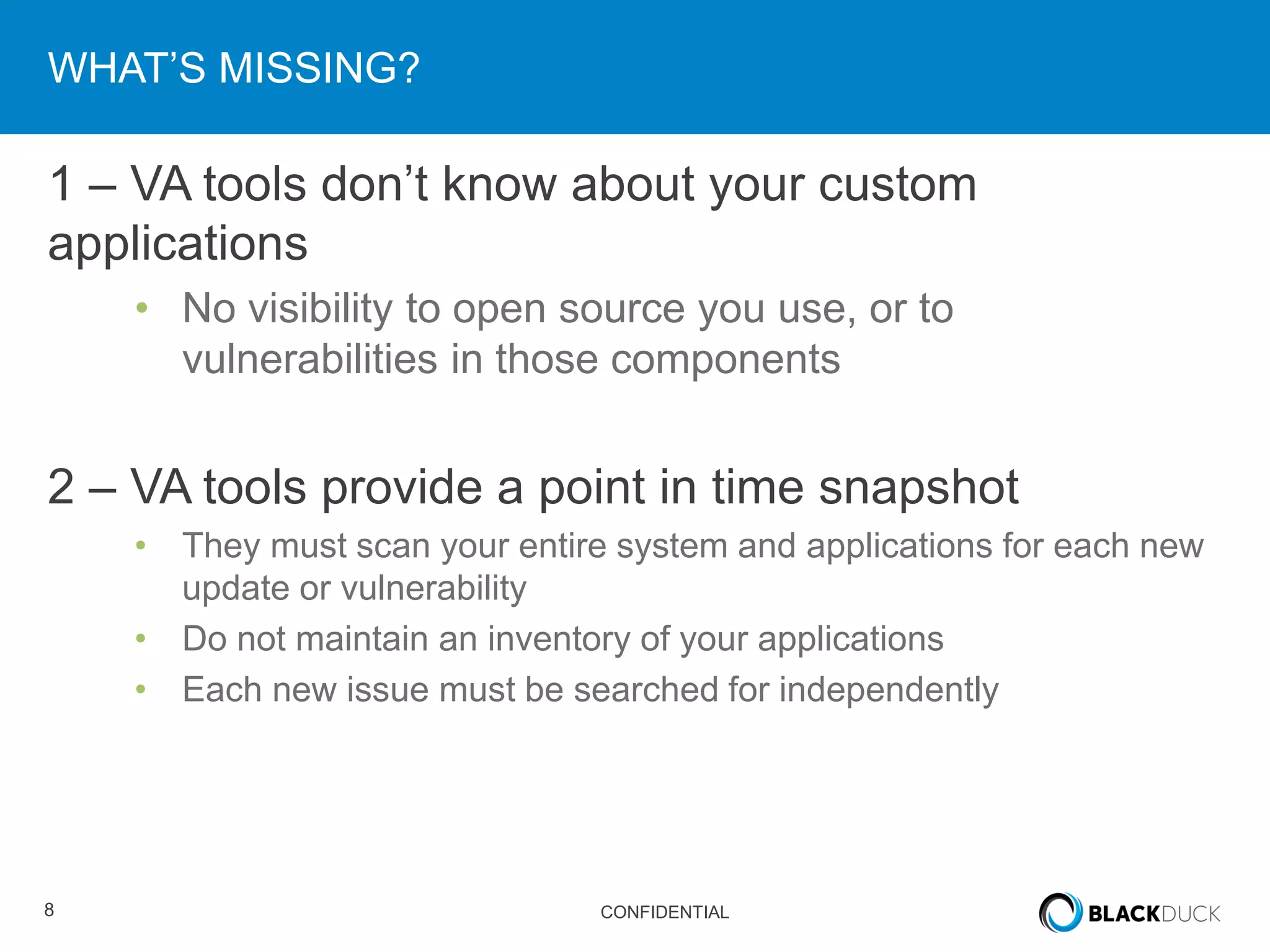
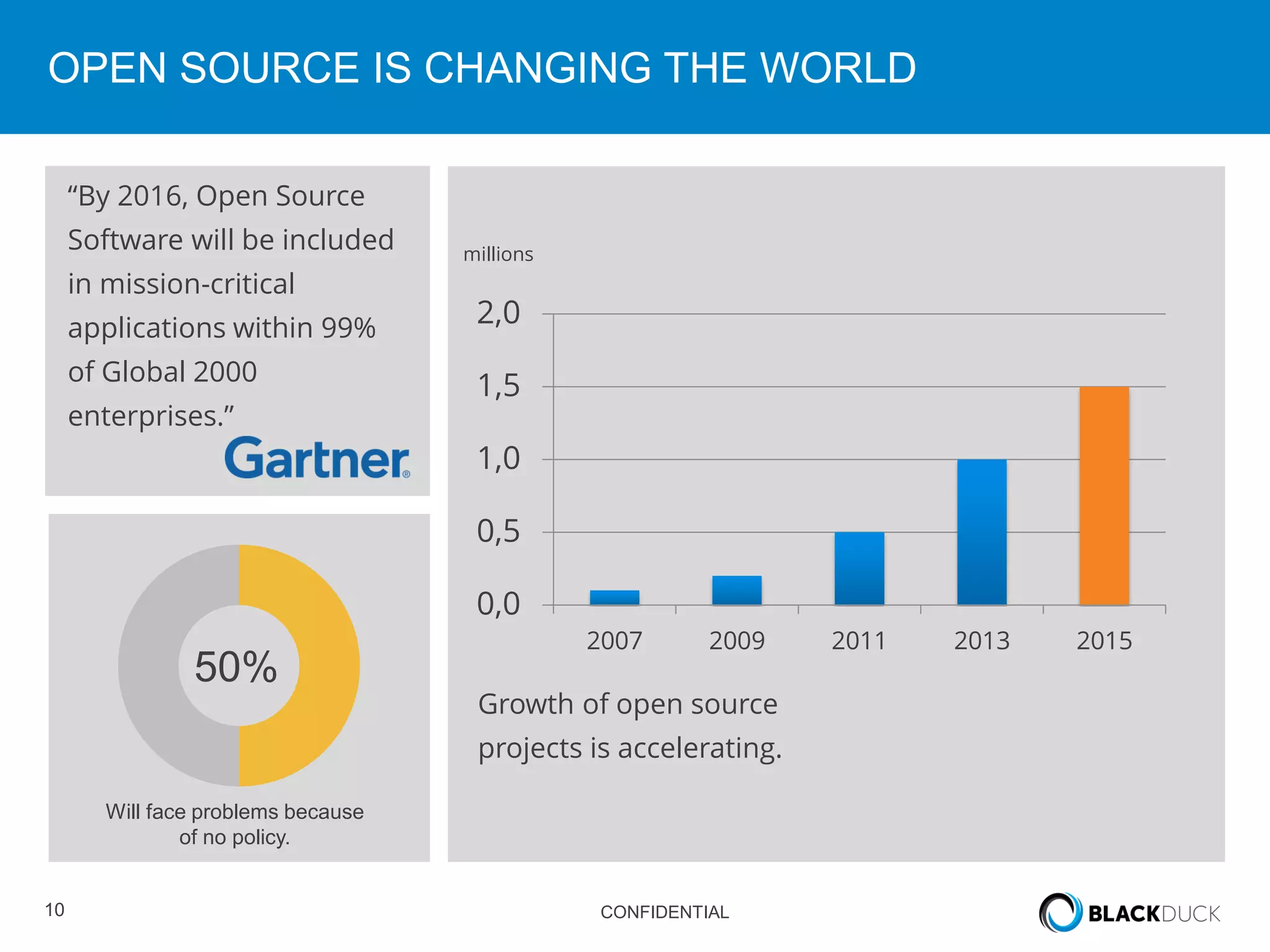
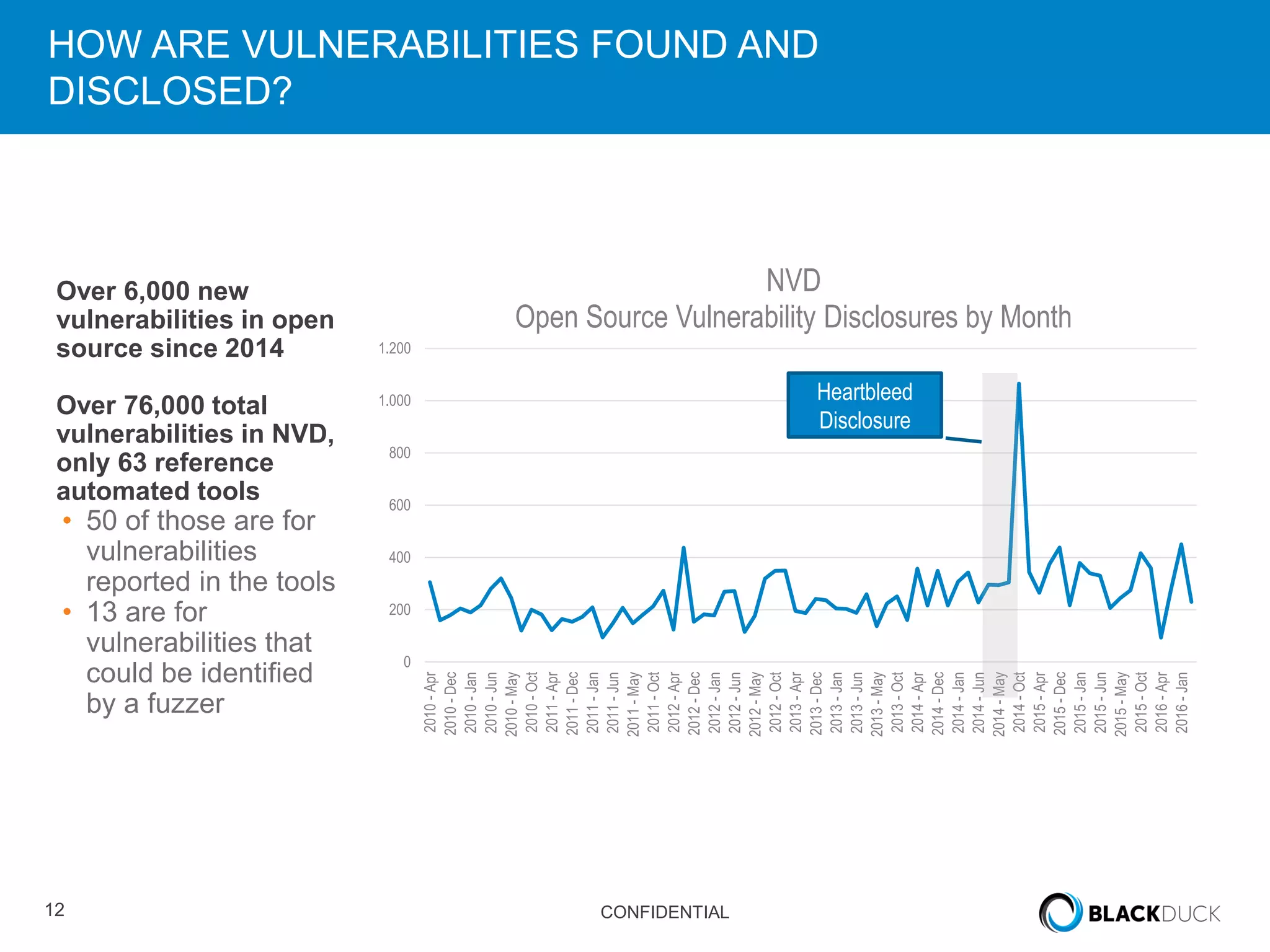
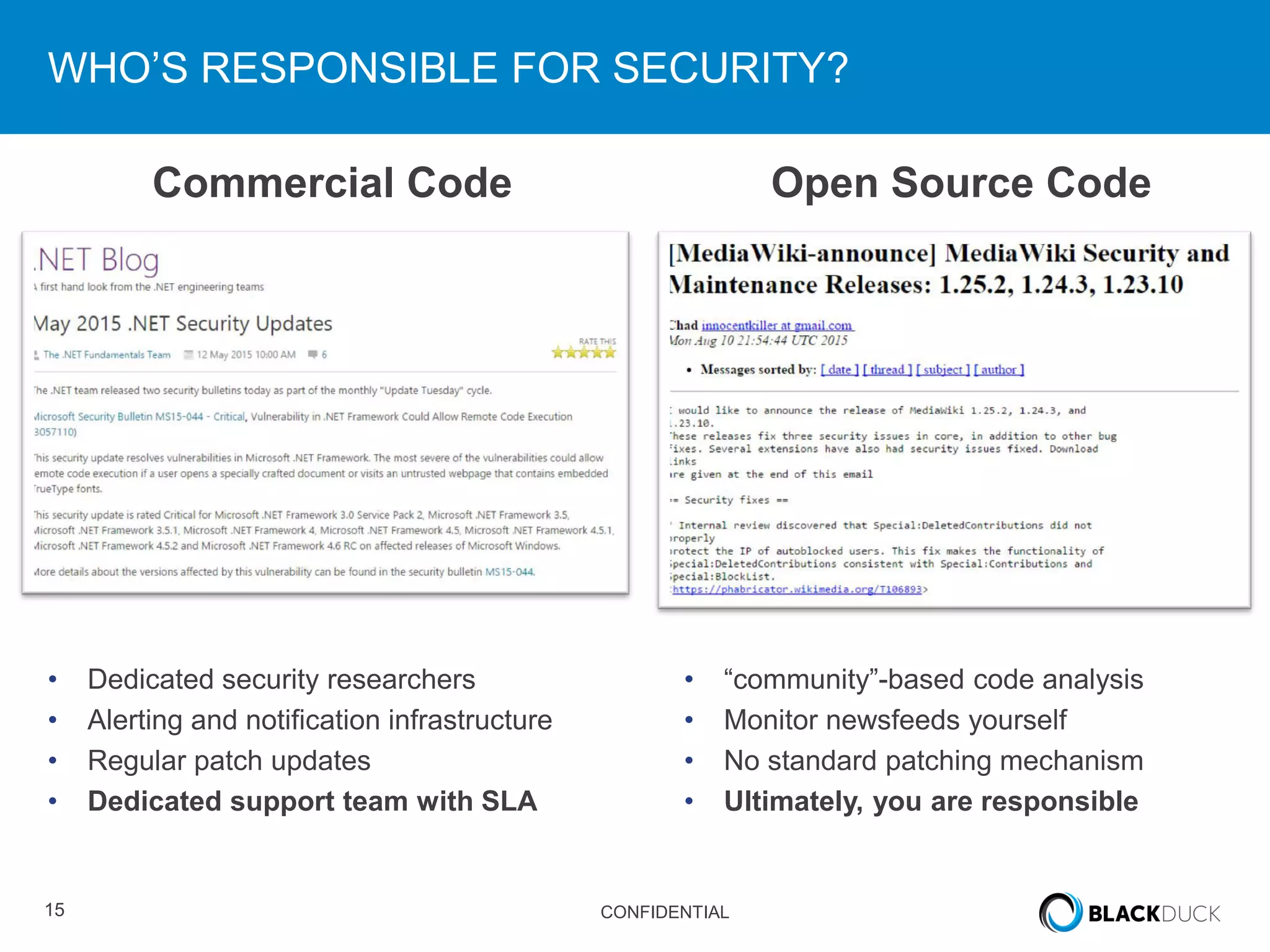
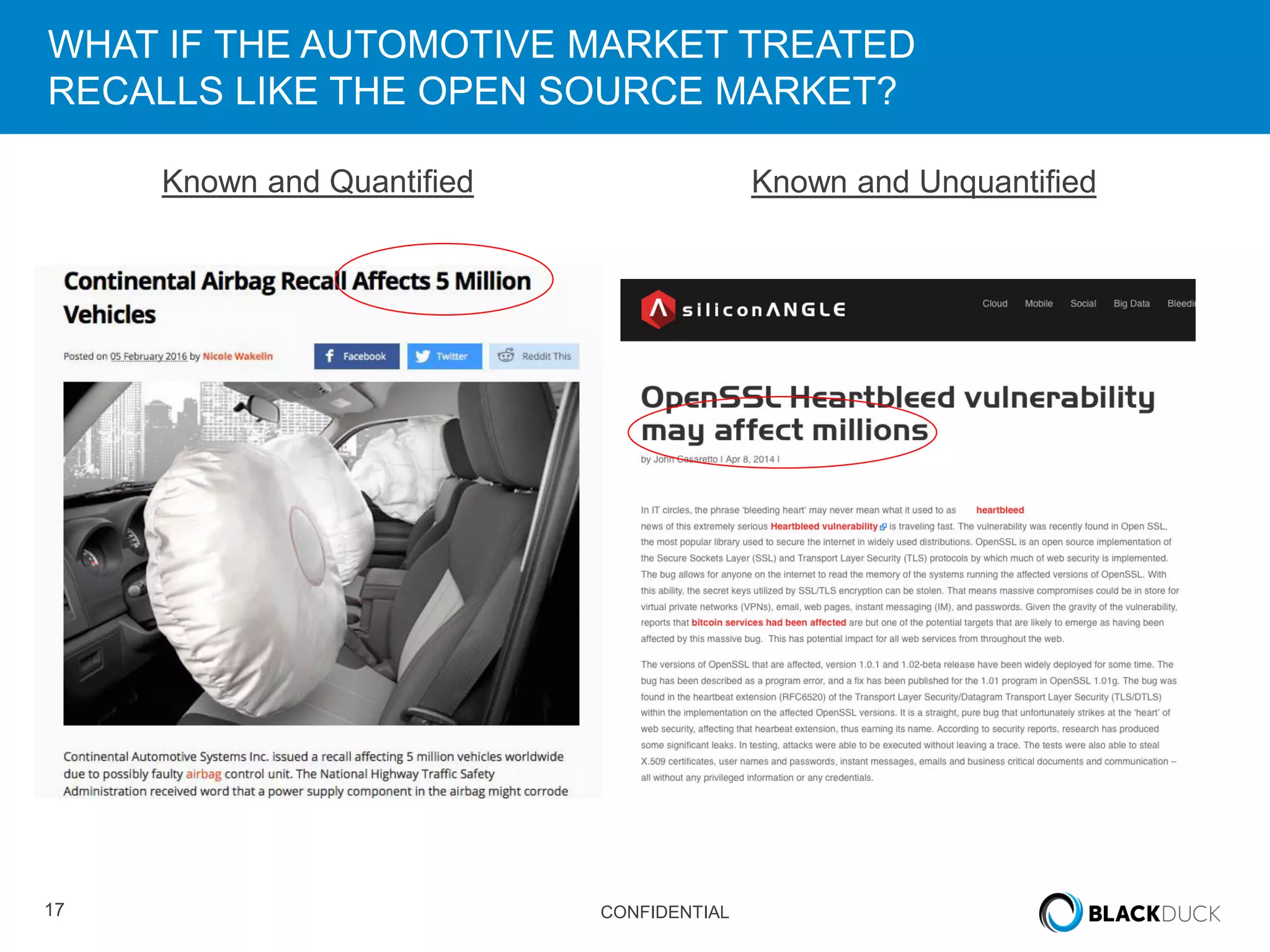
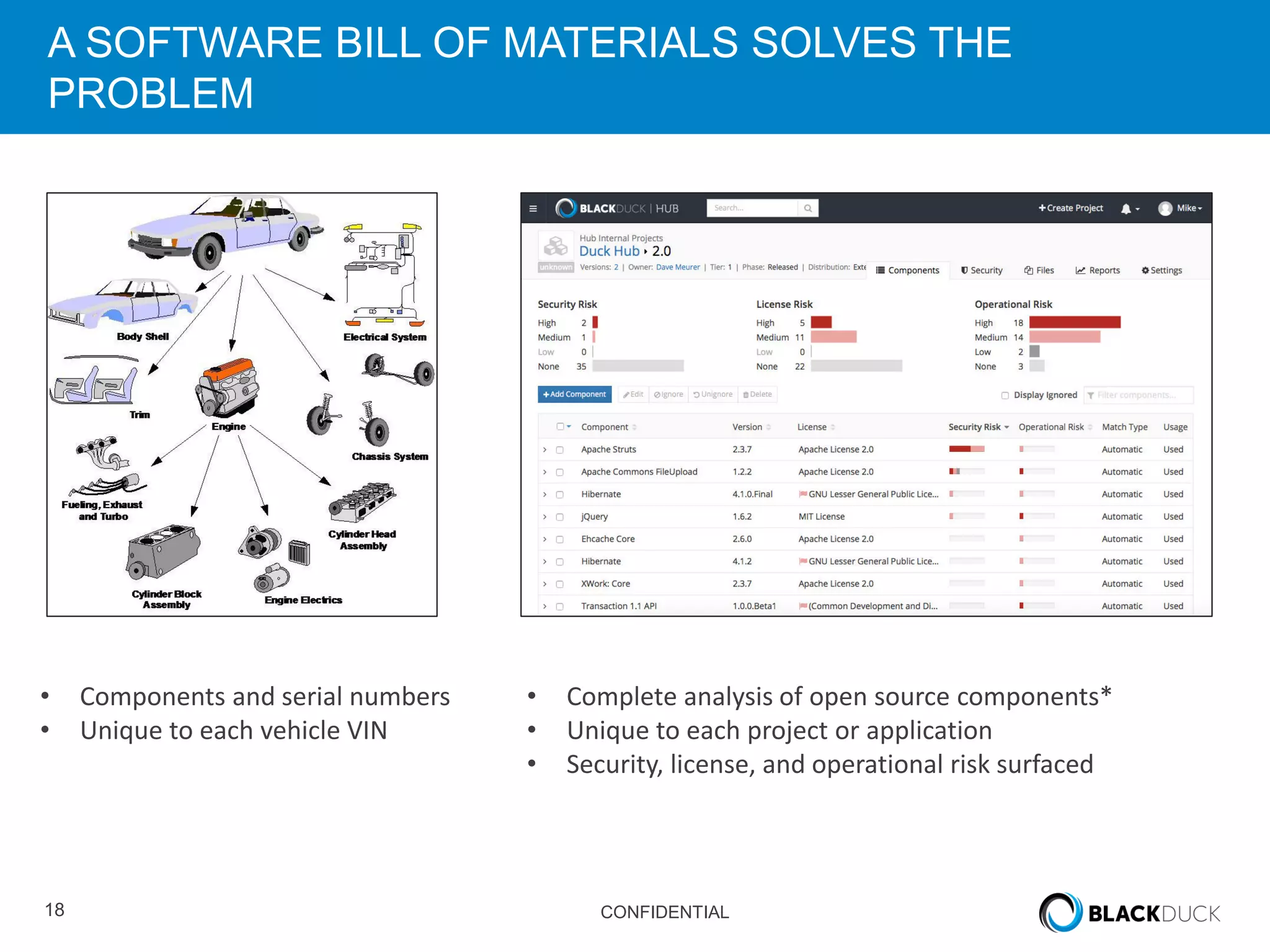
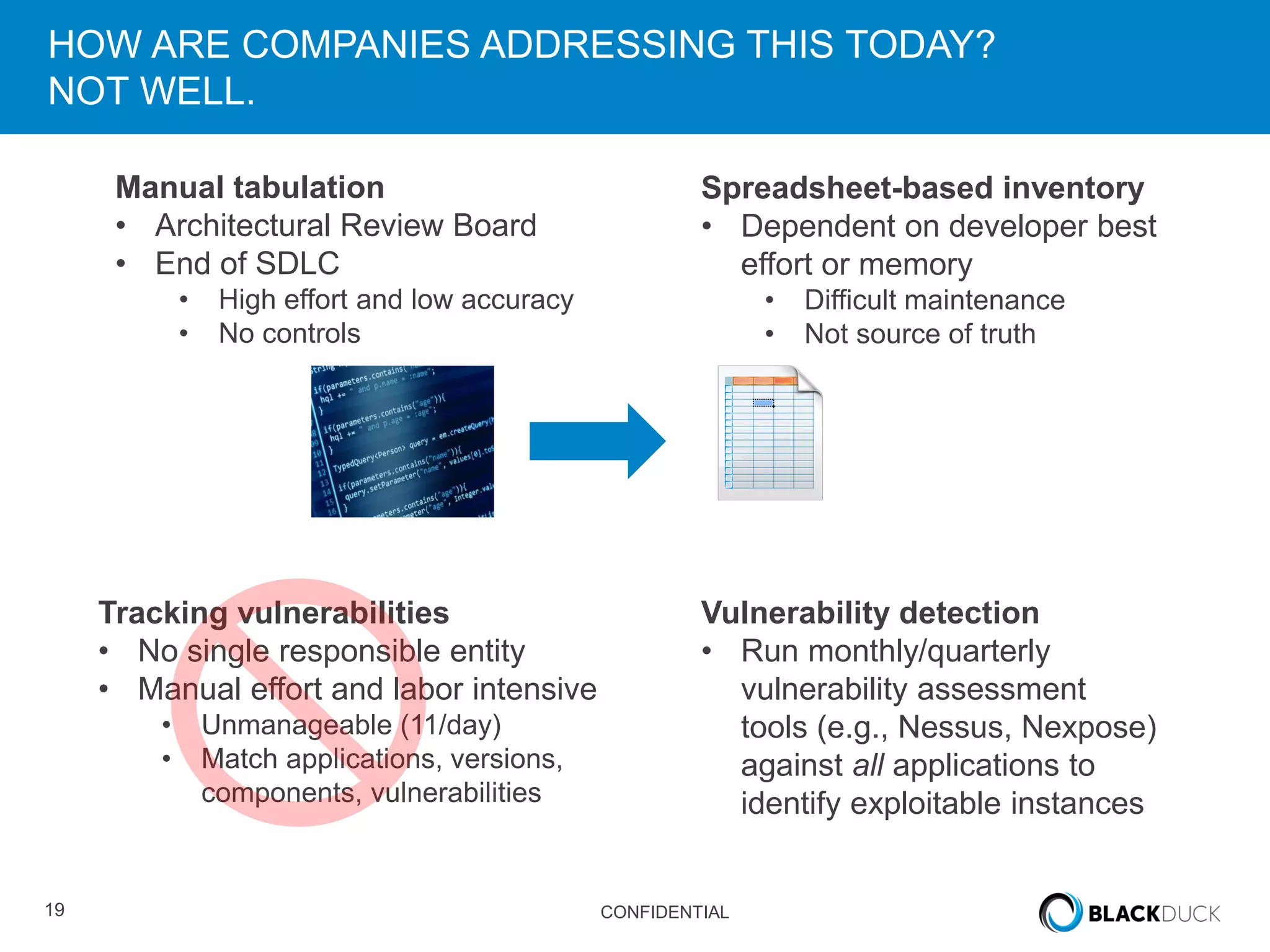
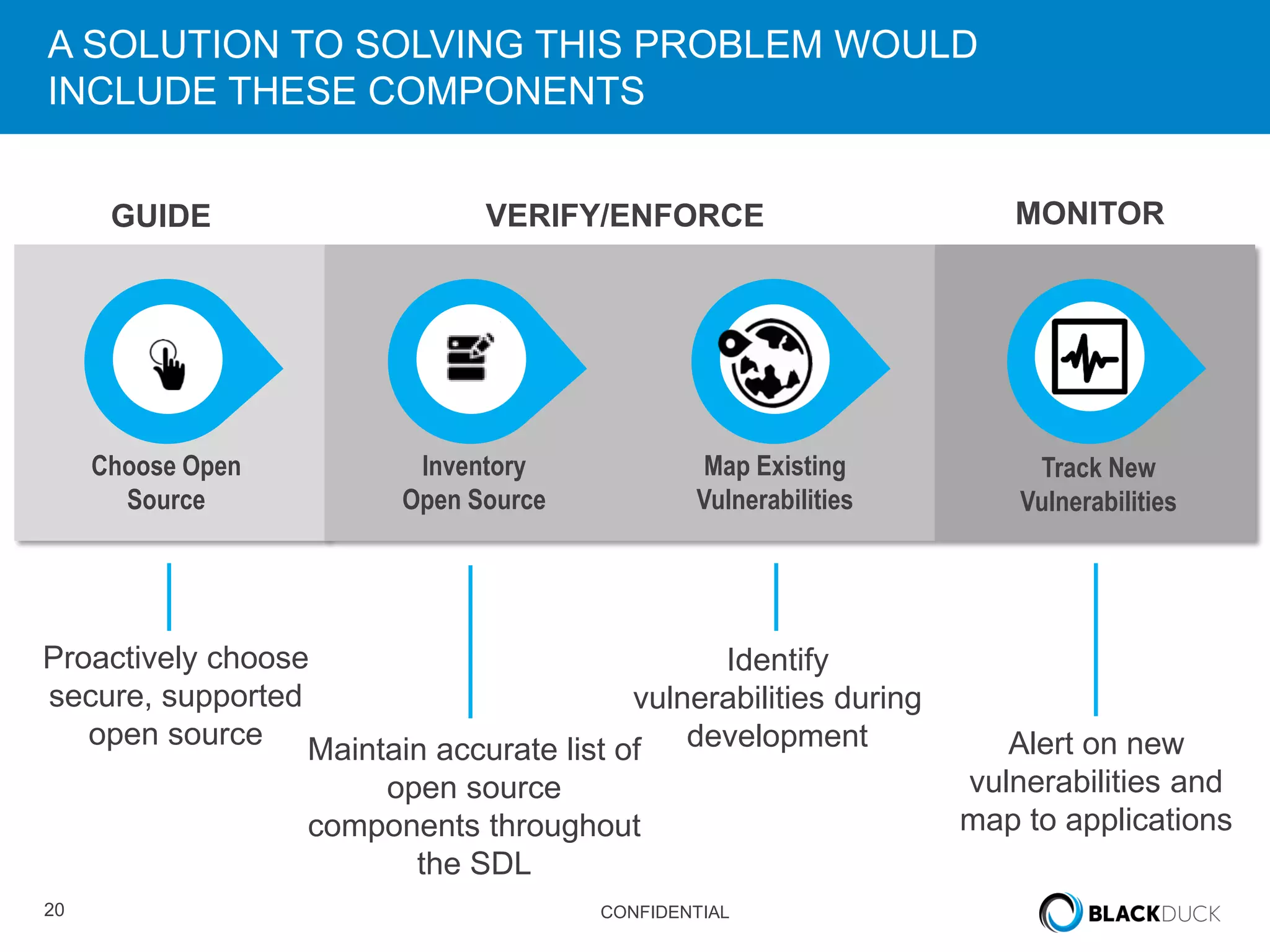
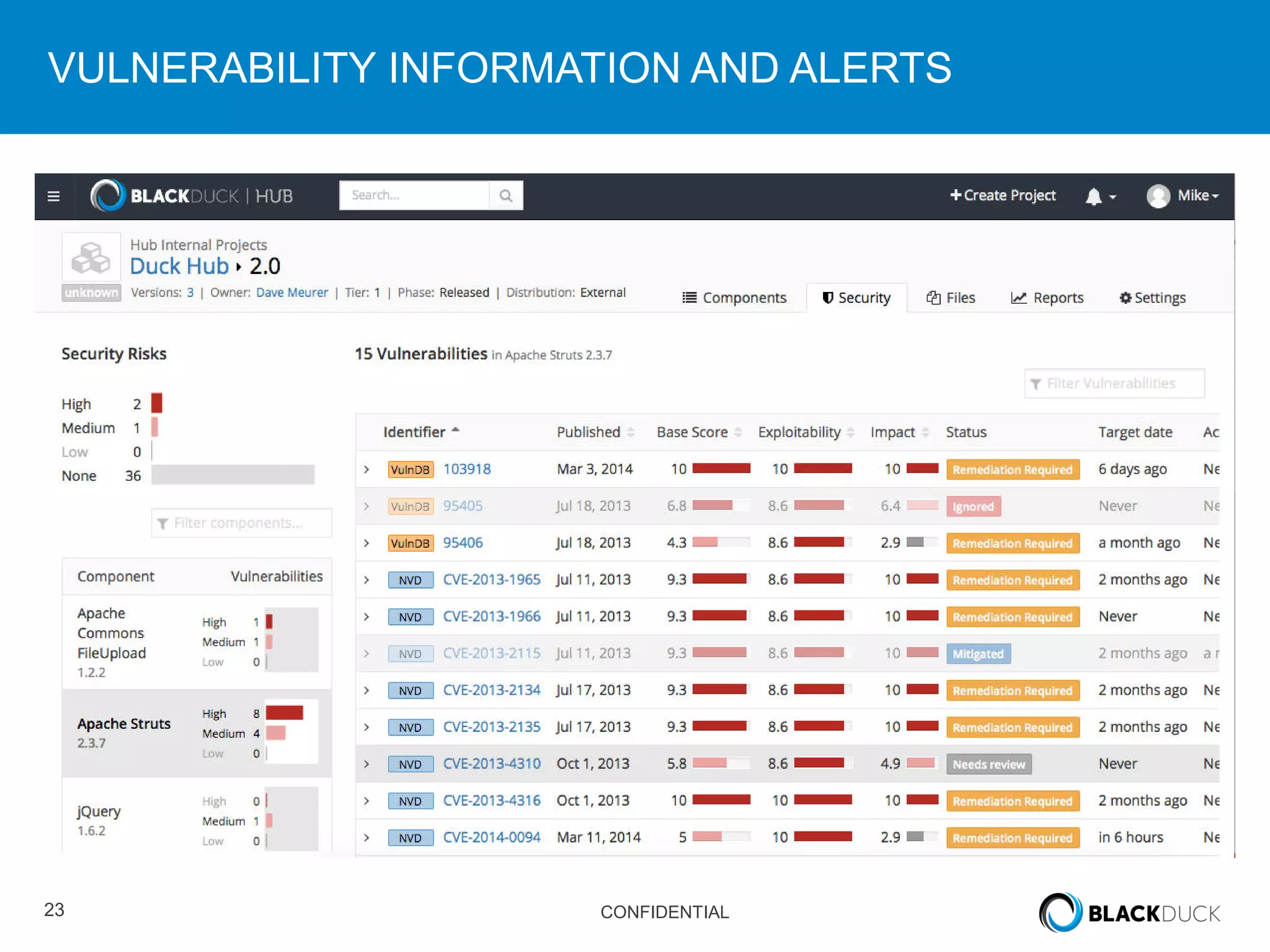
This document discusses regulatory requirements for vulnerability assessments and the challenges of managing open source software vulnerabilities. It notes that regulatory requirements from standards like PCI-DSS require vulnerability monitoring and patching, but traditional vulnerability assessment tools do not provide visibility into custom code or track vulnerabilities over time in open source components. The document argues that organizations need software bills of materials and proactive vulnerability management programs that can map vulnerabilities to applications to effectively manage risks from open source.