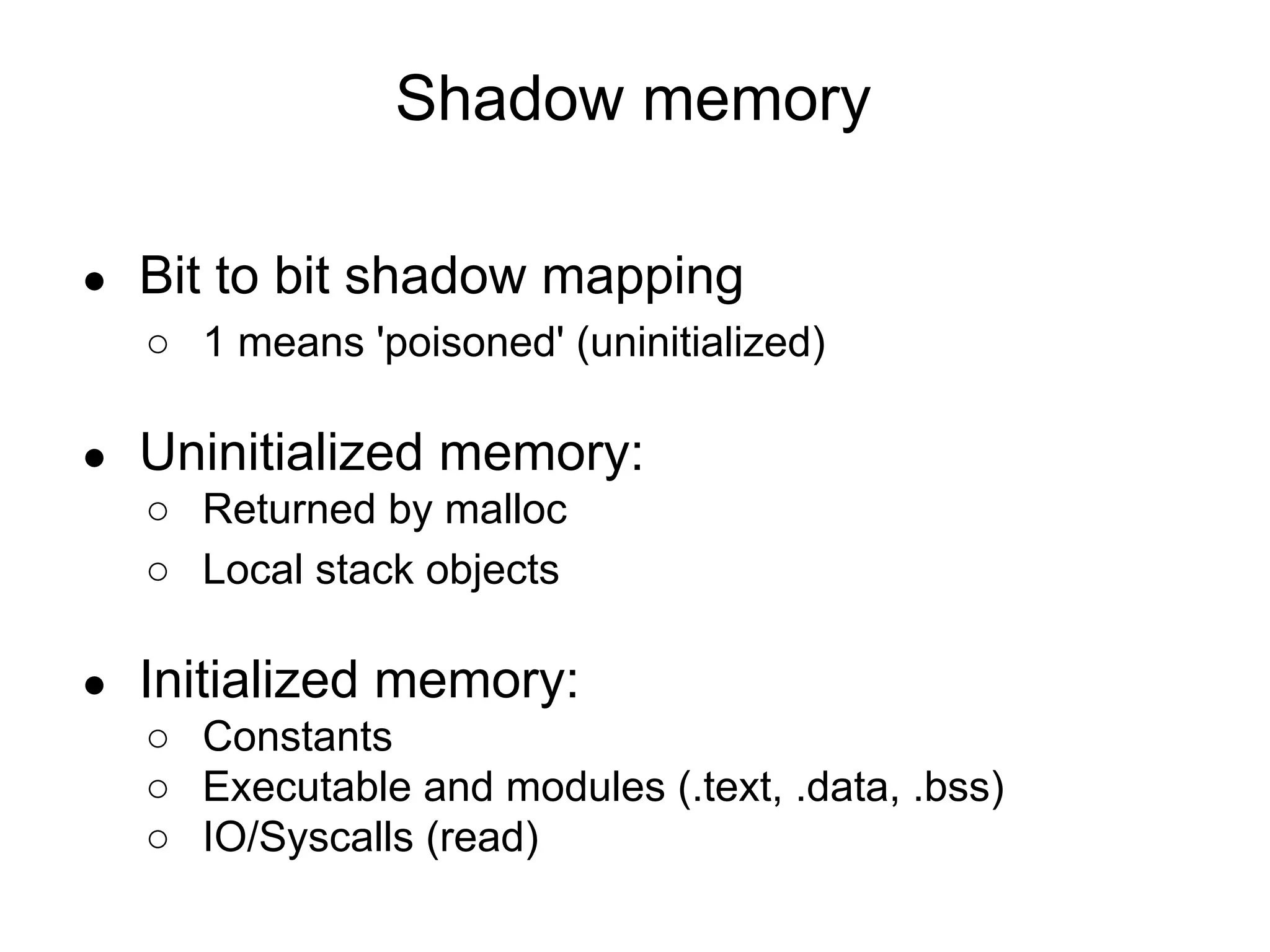
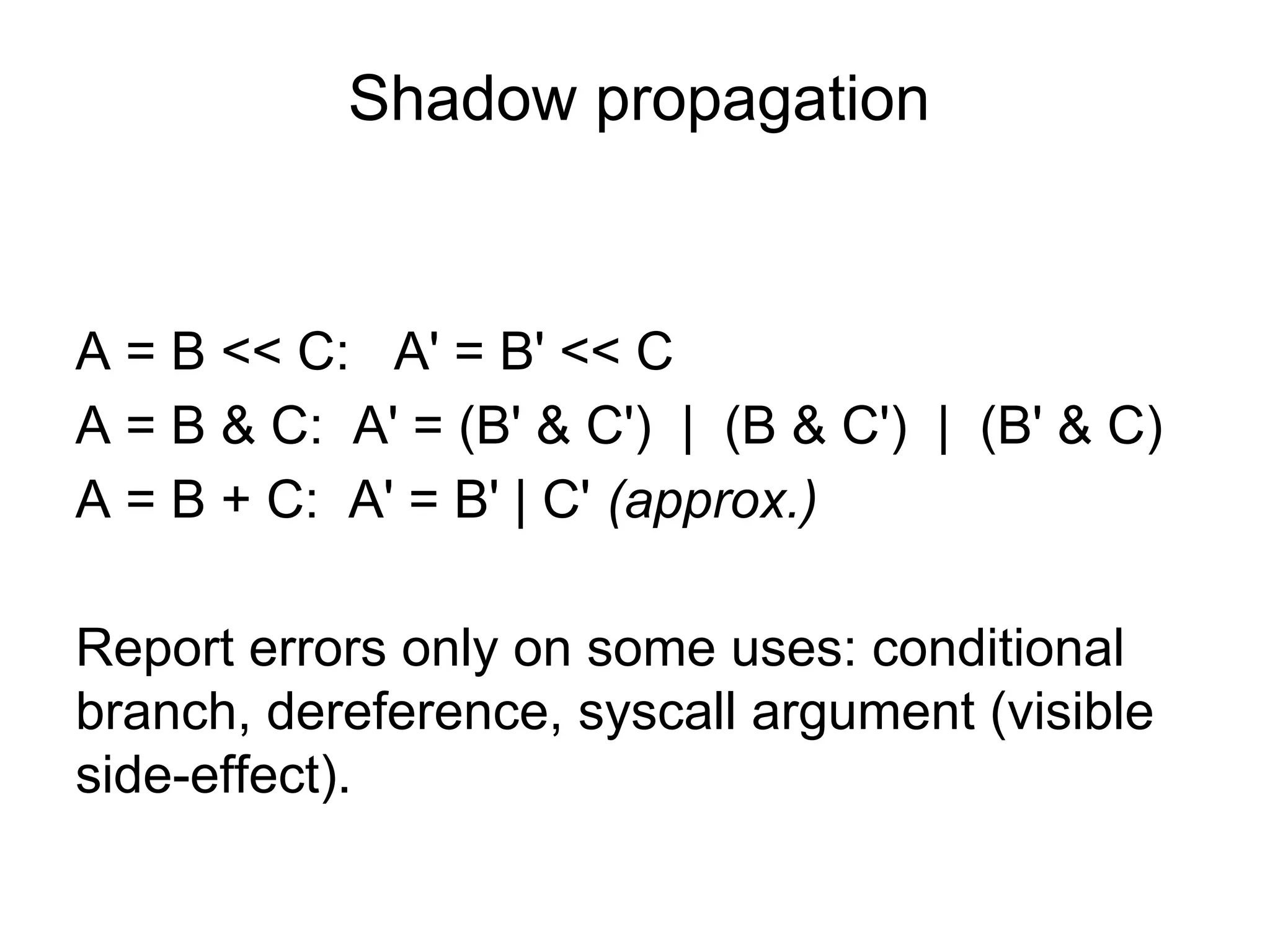
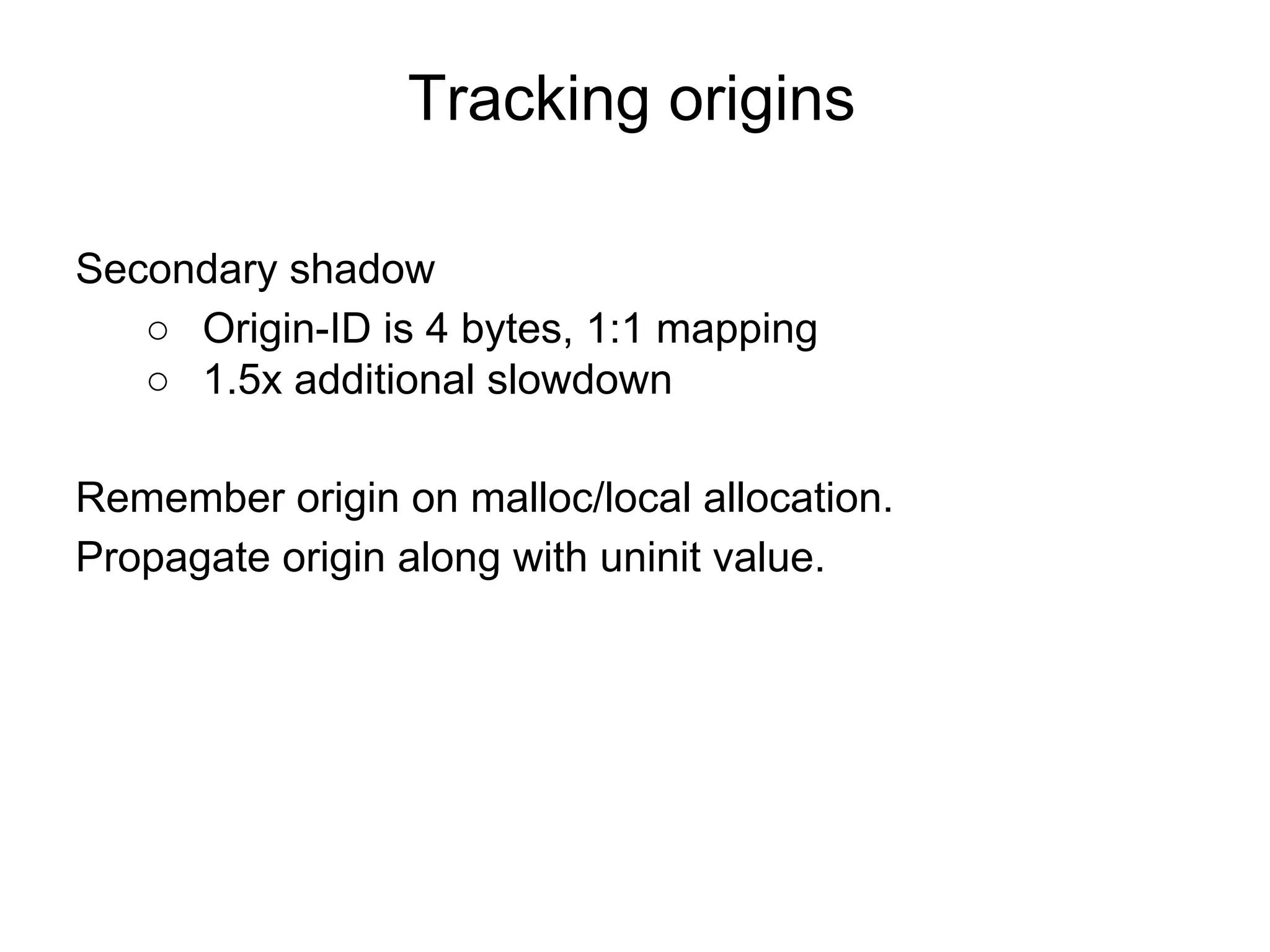
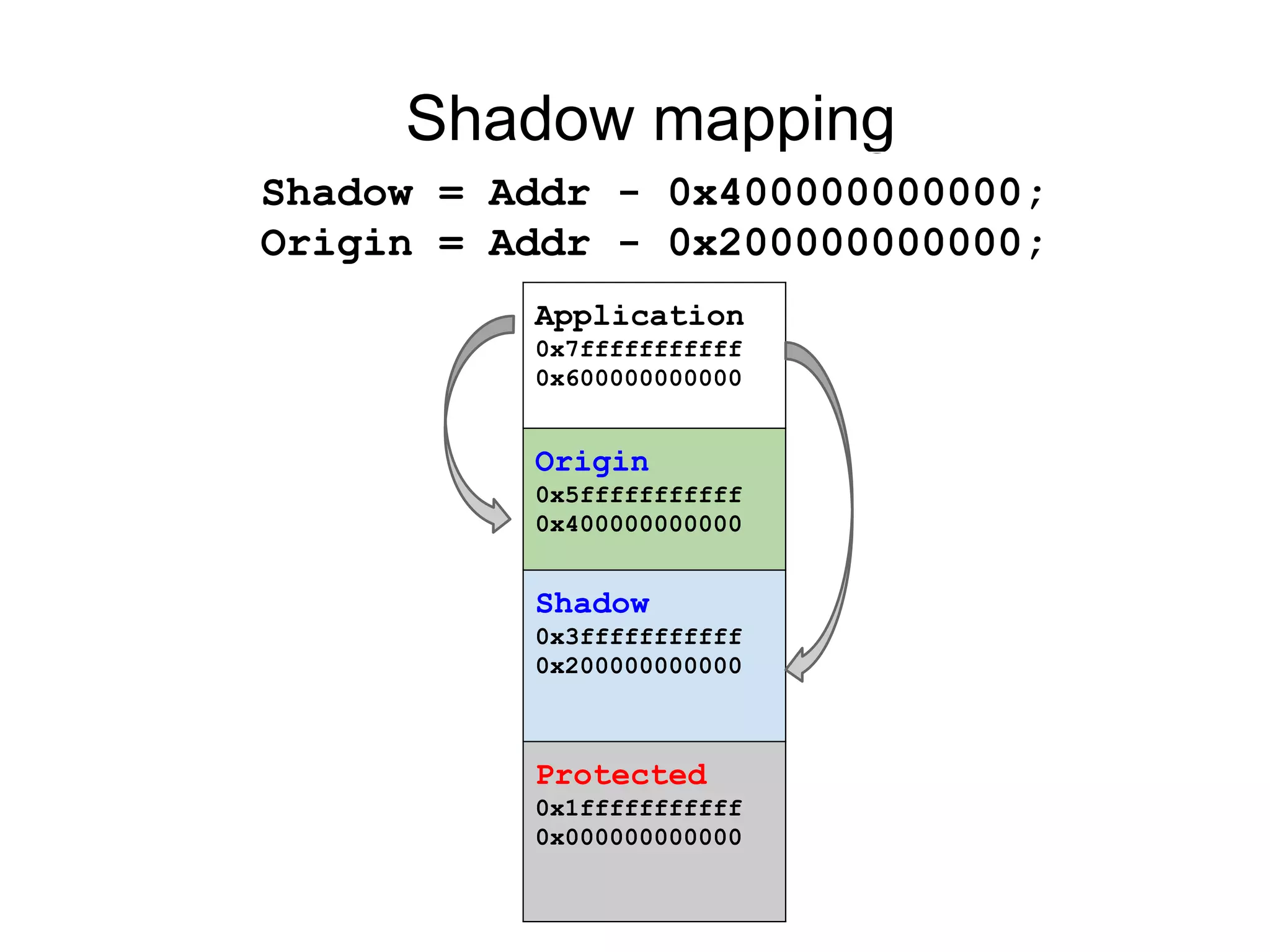
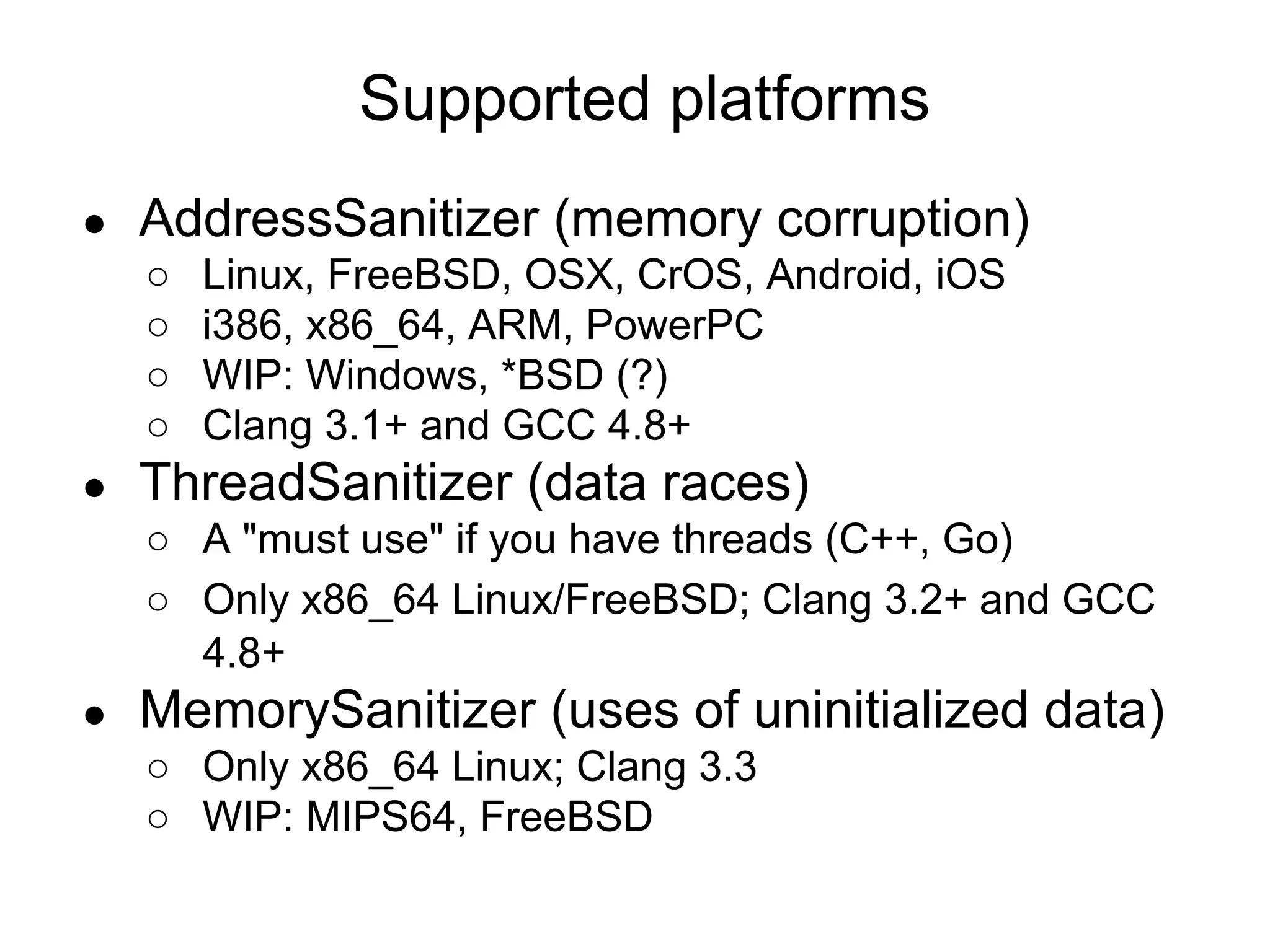
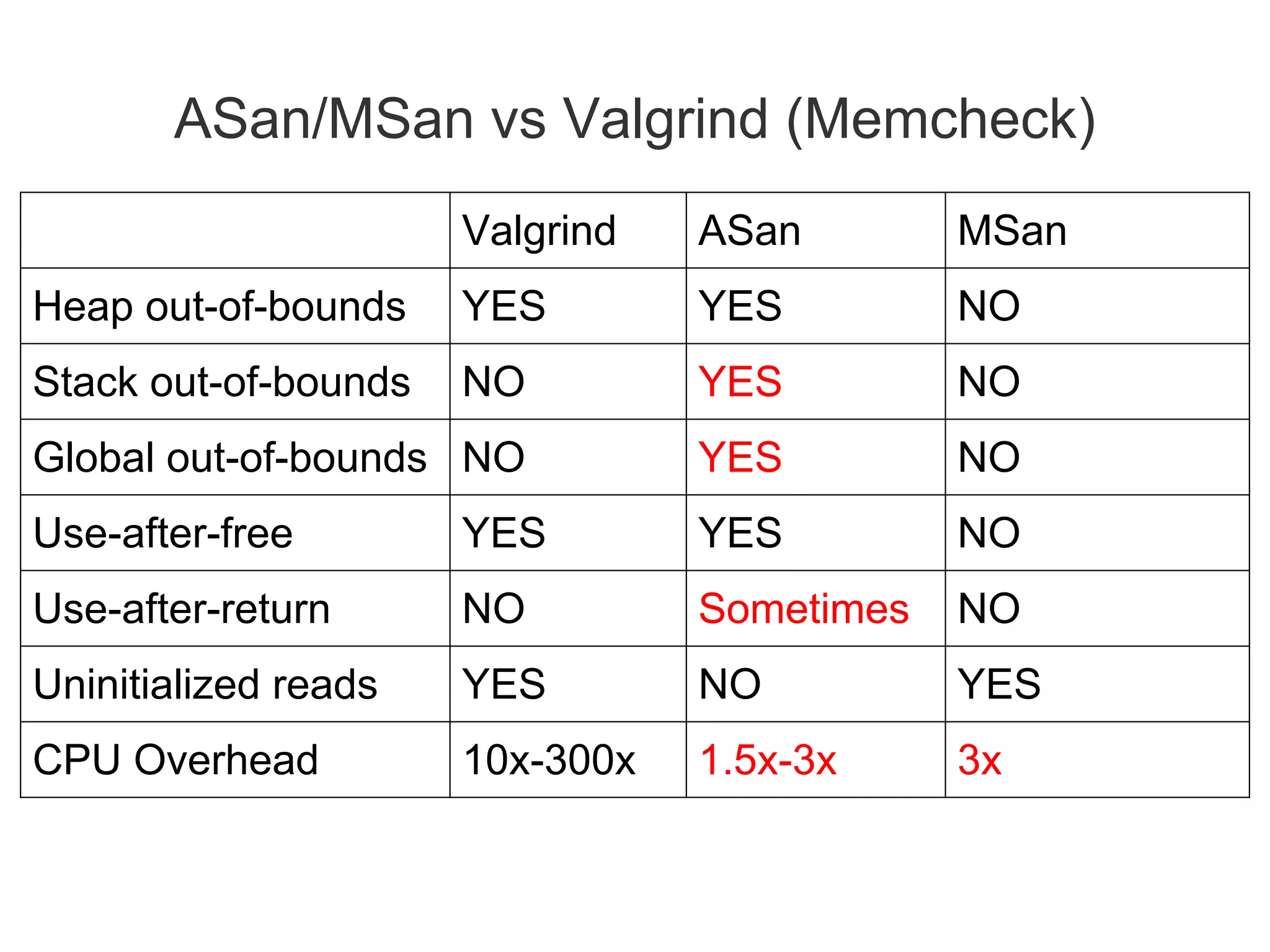
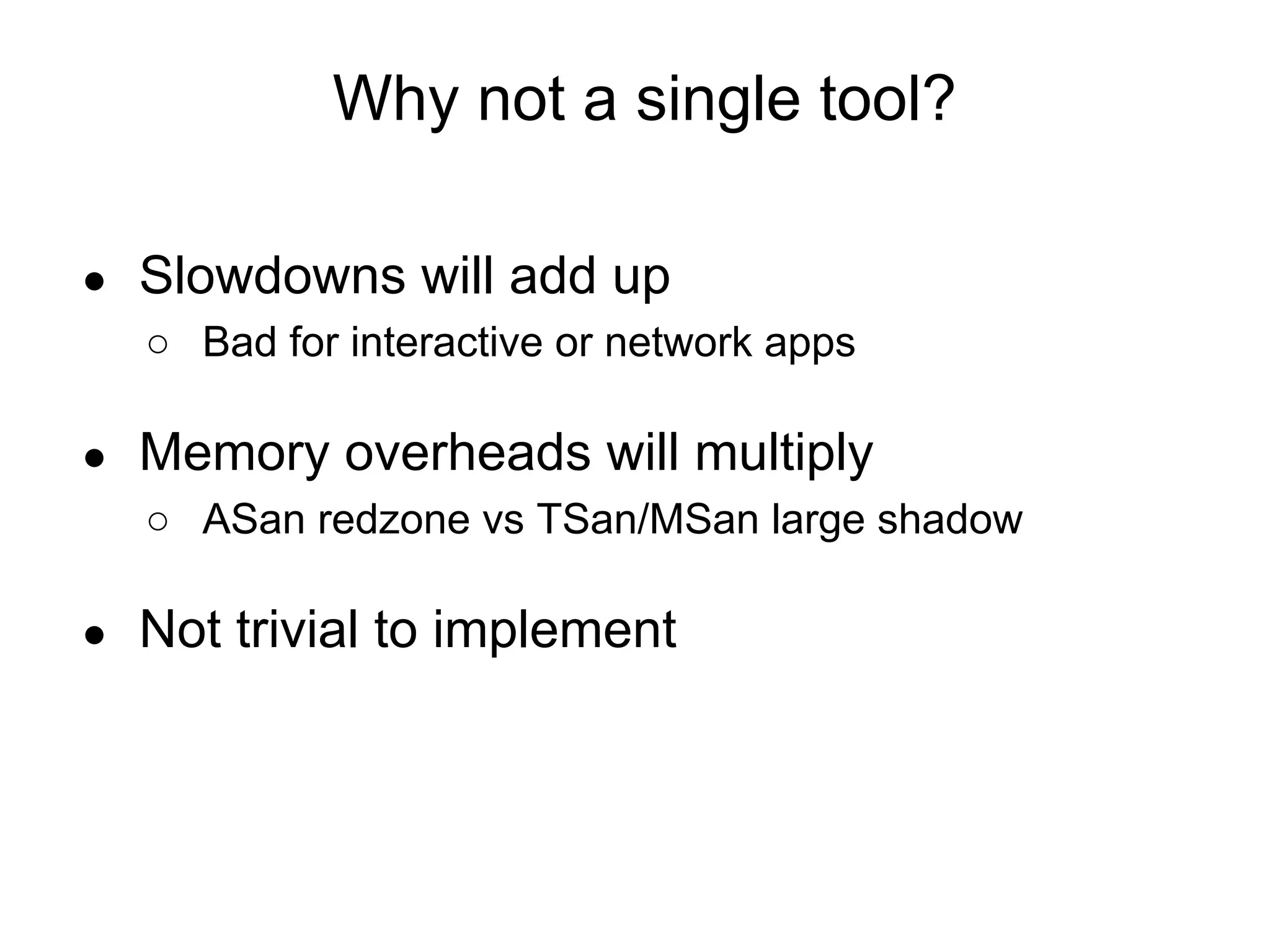
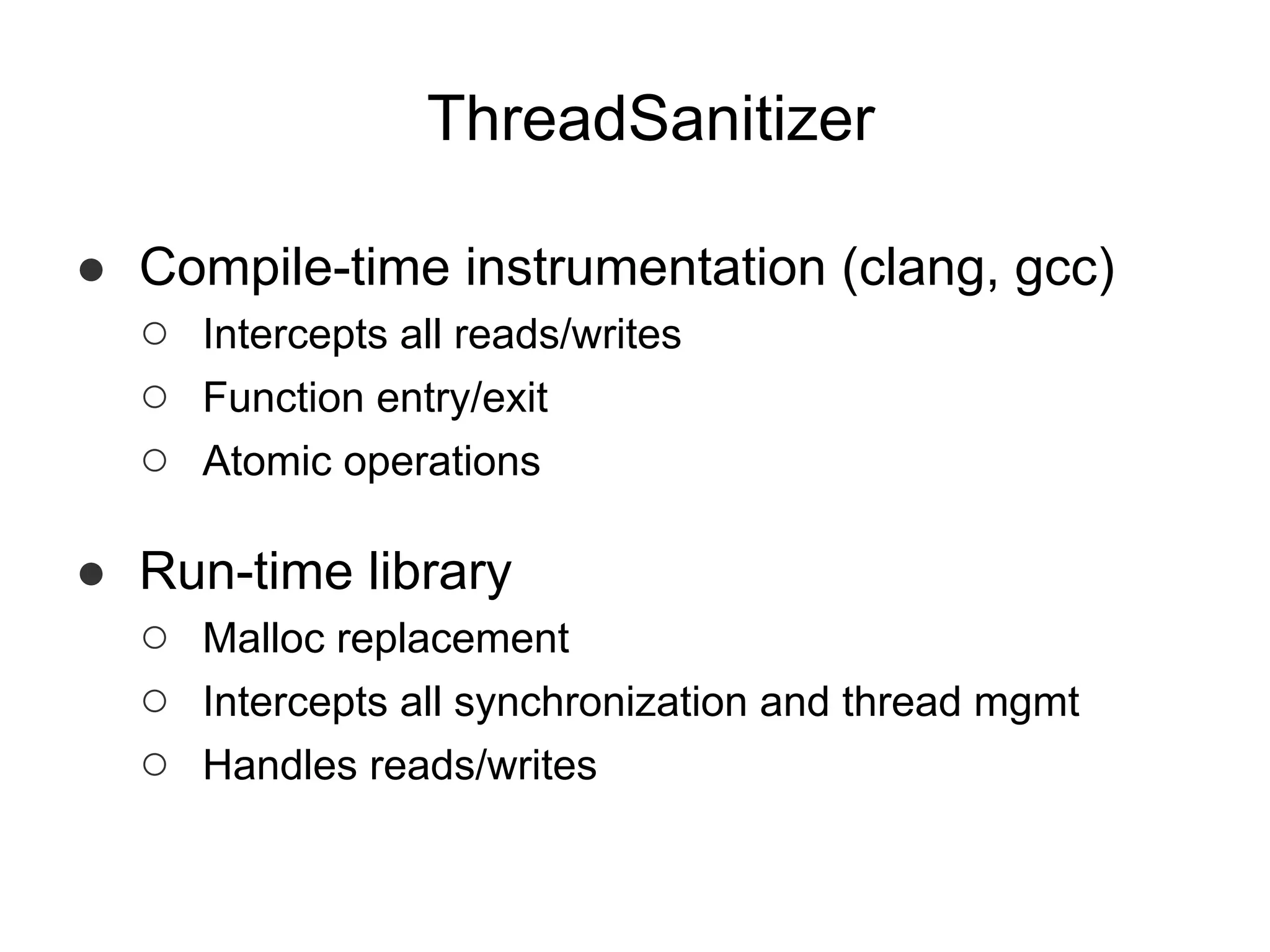
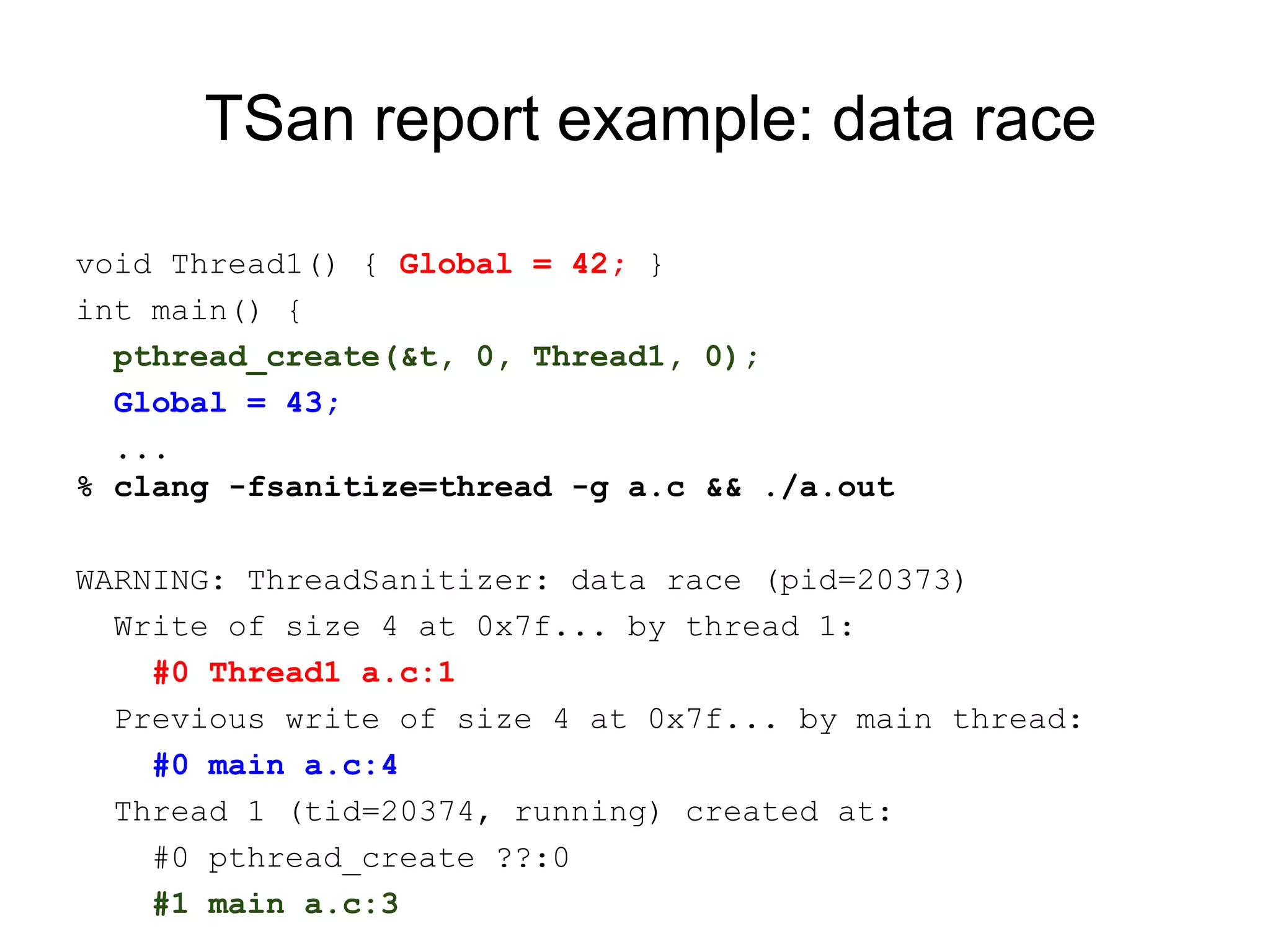
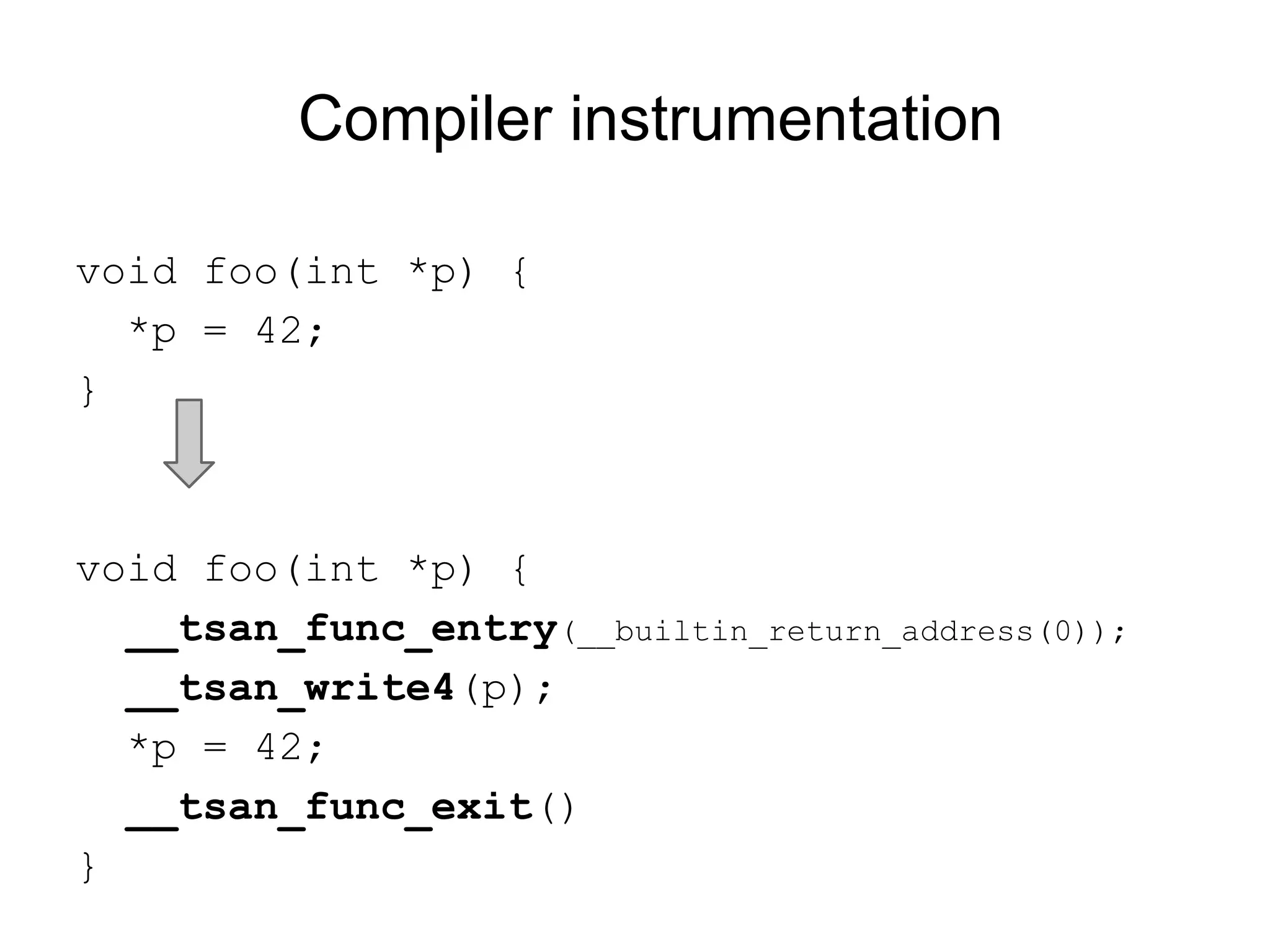
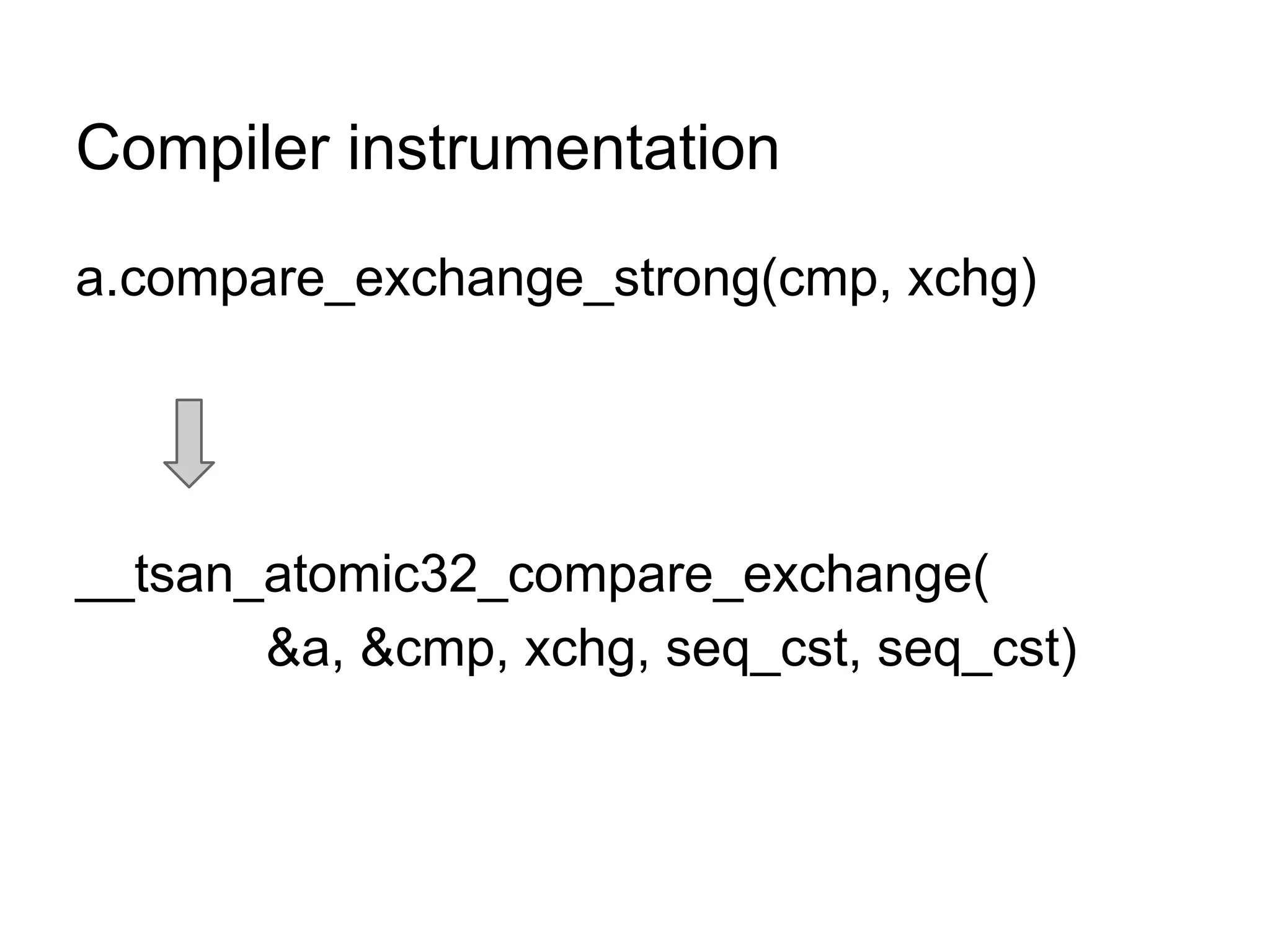
The document discusses three sanitizers - AddressSanitizer, ThreadSanitizer, and MemorySanitizer - that detect bugs in C/C++ programs. AddressSanitizer detects memory errors like buffer overflows and use-after-frees. ThreadSanitizer finds data races between threads. MemorySanitizer identifies uses of uninitialized memory. The sanitizers work by instrumenting code at compile-time and providing a run-time library for error detection and reporting. They have found thousands of bugs in major software projects with reasonable overhead. Future work includes supporting more platforms and detecting additional classes of bugs.



![int main(int argc, char **argv) {
int stack_array[100];
stack_array[1] = 0;
return stack_array[argc + 100]; // BOOM
}
% clang++ -O1 -fsanitize=address a.cc; ./a.out
ERROR: AddressSanitizer stack-buffer-overflow
READ of size 4 at 0x7f5620d981b4 thread T0
#0 0x4024e8 in main a.cc:4
Address 0x7f5620d981b4 is located at offset 436 in frame
<main> of T0's stack:
This frame has 1 object(s):
[32, 432) 'stack_array'
ASan report example: stack-buffer-overflow](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-5-2048.jpg)
![int main(int argc, char **argv) {
int *array = new int[100];
int res = array[argc + 100]; // BOOM
delete [] array;
return res;
}
% clang++ -O1 -fsanitize=address a.cc; ./a.out
ERROR: AddressSanitizer heap-buffer-overflow
READ of size 4 at 0x7fe4b0c76214 thread T0
#0 0x40246f in main a.cc:3
0x7fe4b0c76214 is located 4 bytes to the right of 400-
byte region [0x7fe..., 0x7fe...)
allocated by thread T0 here:
#0 0x402c36 in operator new[](unsigned long)
#1 0x402422 in main a.cc:2
ASan report example: heap-buffer-overflow](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-6-2048.jpg)
![ASan report example: use-after-free
int main(int argc, char **argv) {
int *array = new int[100];
delete [] array;
return array[argc]; // BOOM
}
% clang++ -O1 -fsanitize=address a.cc && ./a.out
ERROR: AddressSanitizer heap-use-after-free
READ of size 4 at 0x7faa07fce084 thread T0
#0 0x40433c in main a.cc:4
0x7faa07fce084 is located 4 bytes inside of 400-byte region
freed by thread T0 here:
#0 0x4058fd in operator delete[](void*) _asan_rtl_
#1 0x404303 in main a.cc:3
previously allocated by thread T0 here:
#0 0x405579 in operator new[](unsigned long) _asan_rtl_
#1 0x4042f3 in main a.cc:2](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-7-2048.jpg)
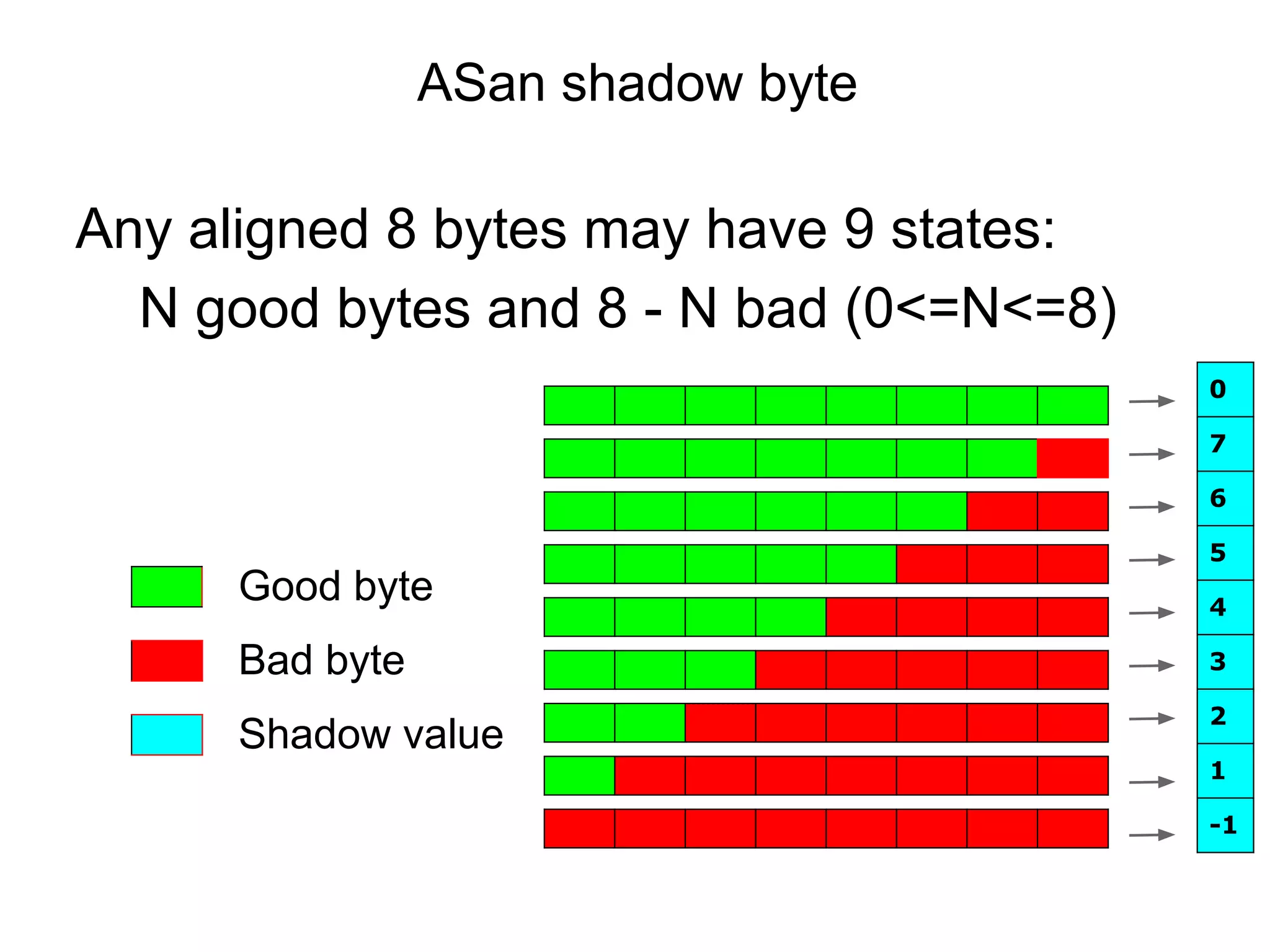
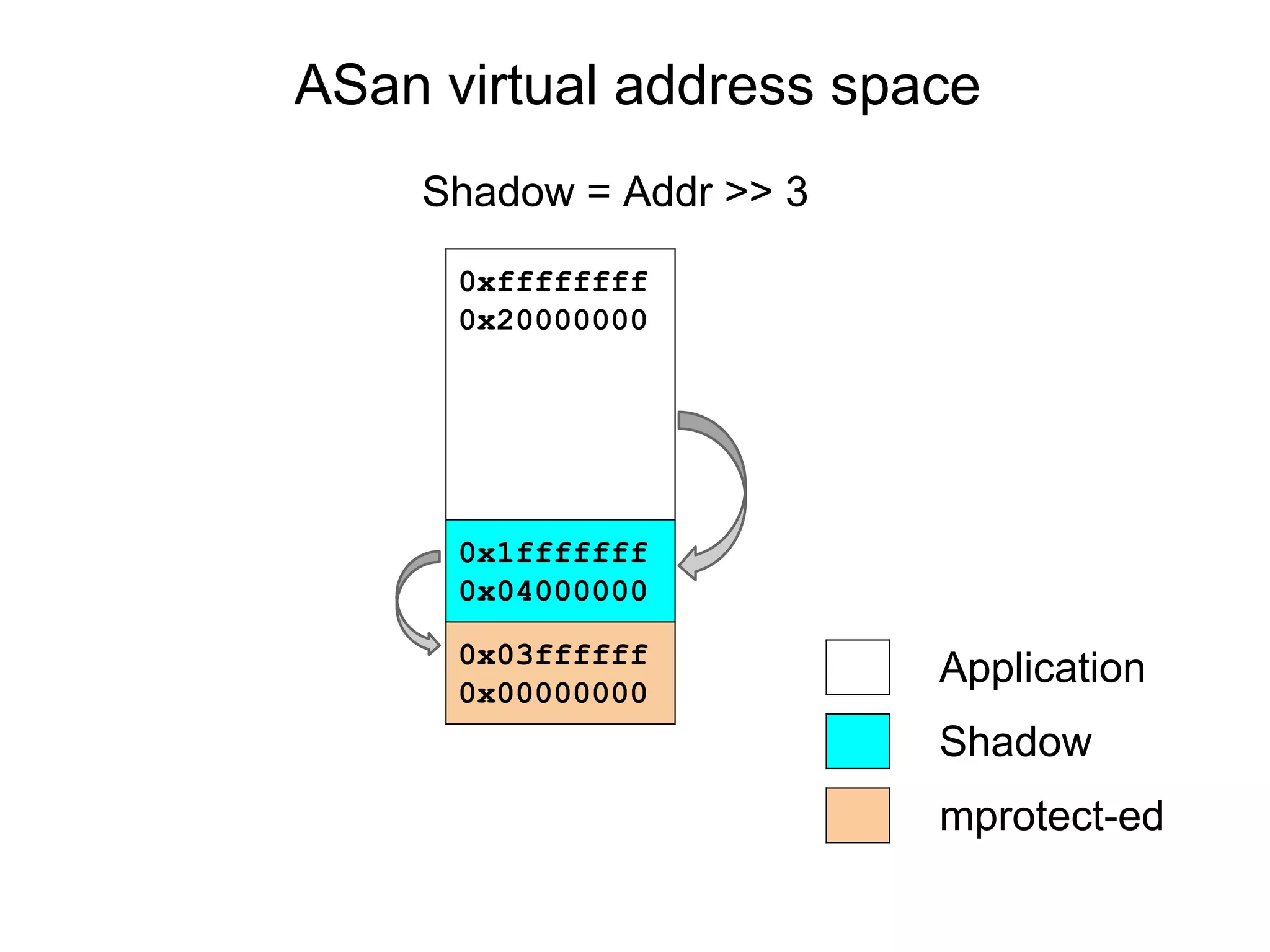
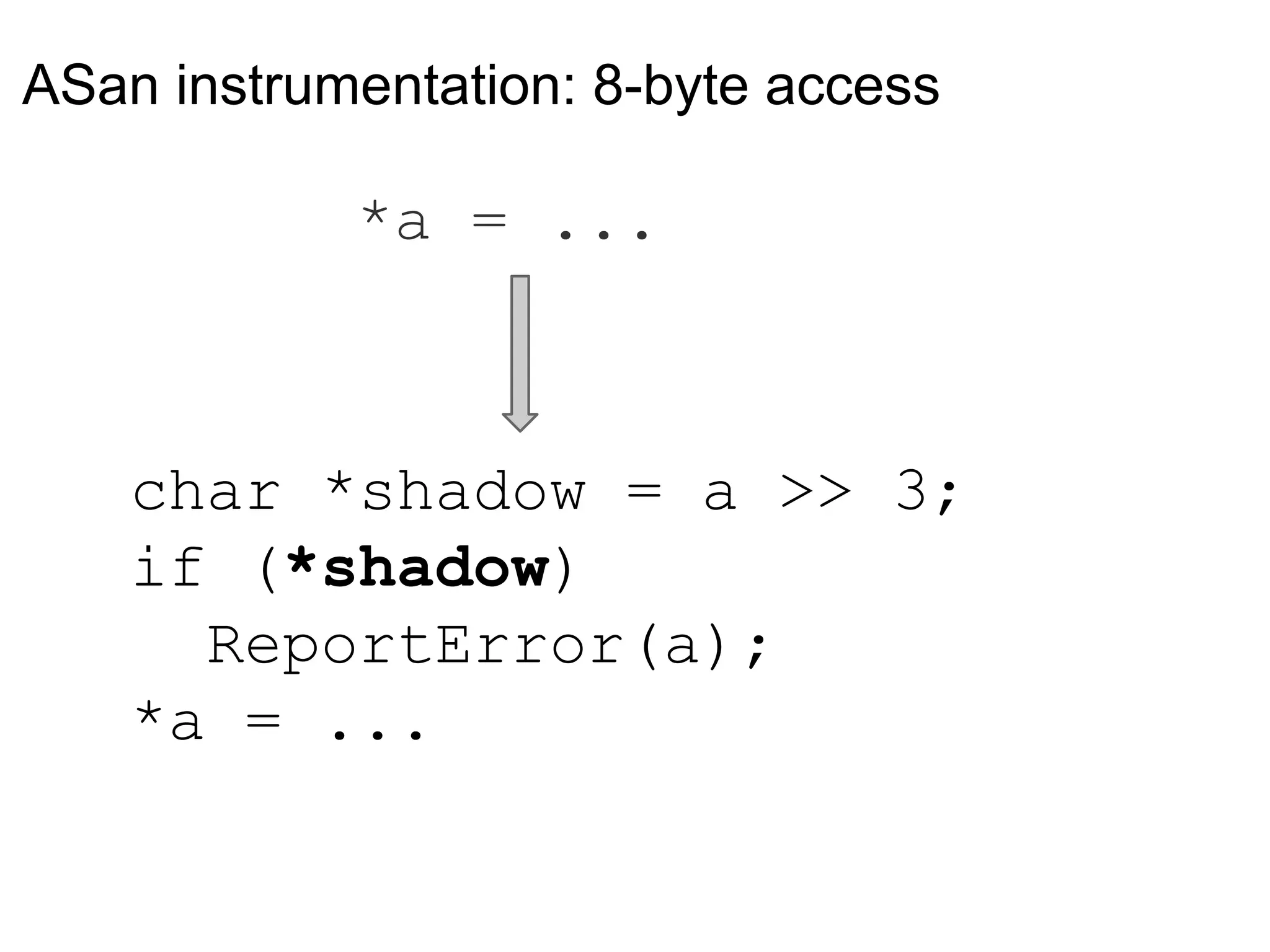
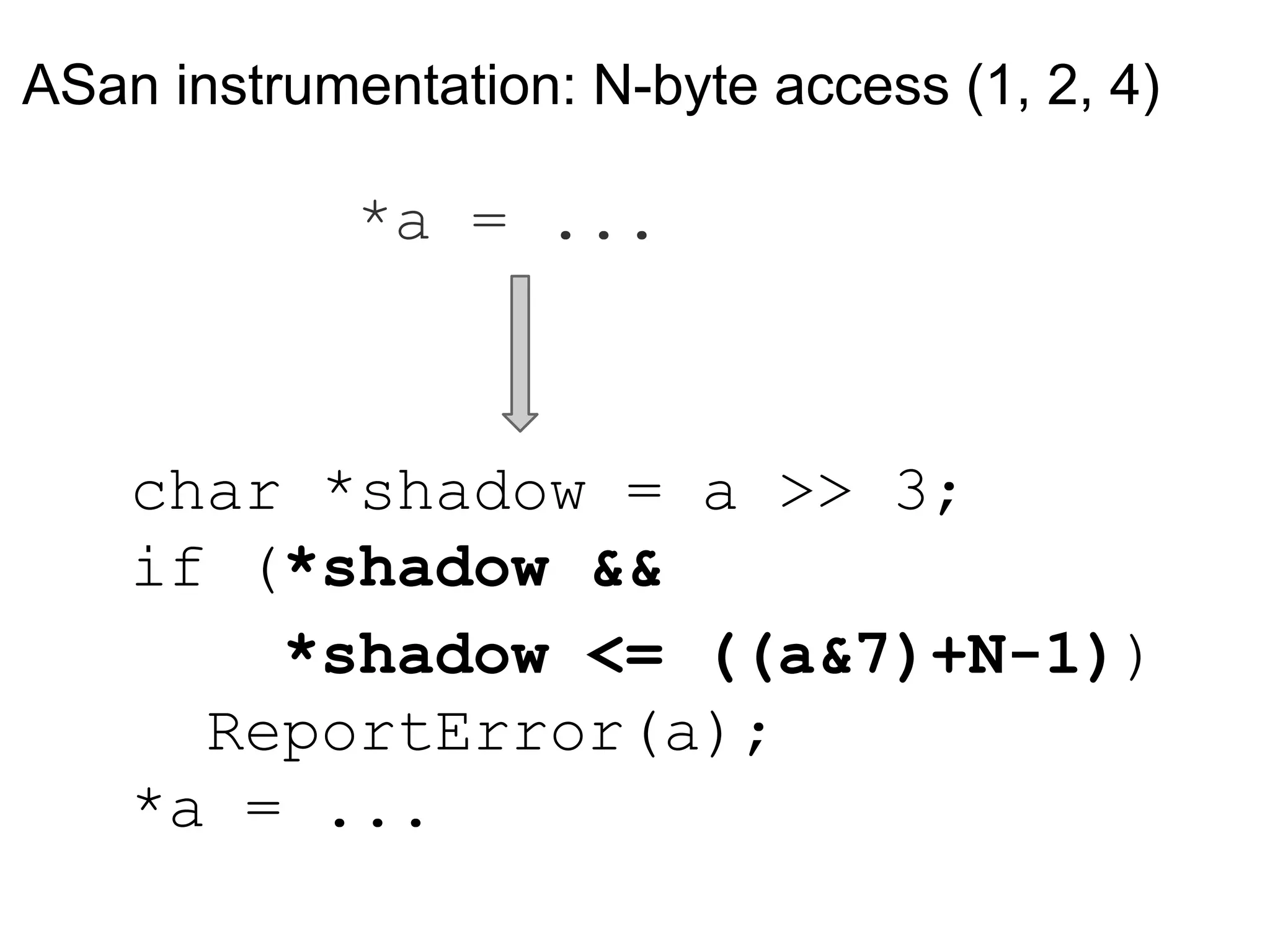
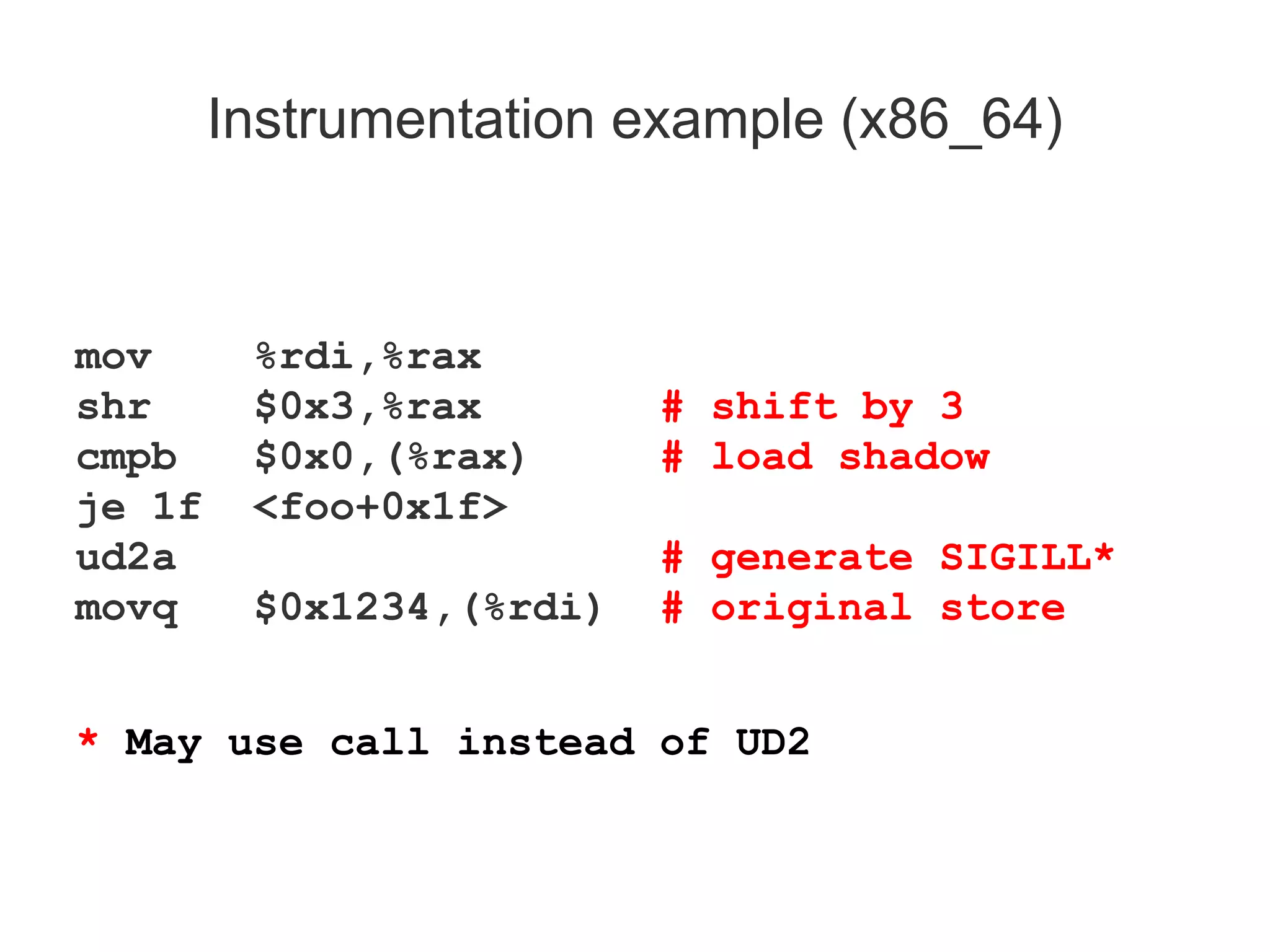
![Instrumenting stack frames
void foo() {
char a[328];
<------------- CODE ------------->
}](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-13-2048.jpg)
![Instrumenting stack frames
void foo() {
char rz1[32]; // 32-byte aligned
char a[328];
char rz2[24];
char rz3[32];
int *shadow = &rz1 >> 3;
shadow[0] = 0xffffffff; // poison rz1
shadow[11] = 0xffffff00; // poison rz2
shadow[12] = 0xffffffff; // poison rz3
<------------- CODE ------------->
shadow[0] = shadow[11] = shadow[12] = 0;
}](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-14-2048.jpg)
![Instrumenting globals
int a;
struct {
int original;
char redzone[60];
} a; // 32-aligned](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-15-2048.jpg)




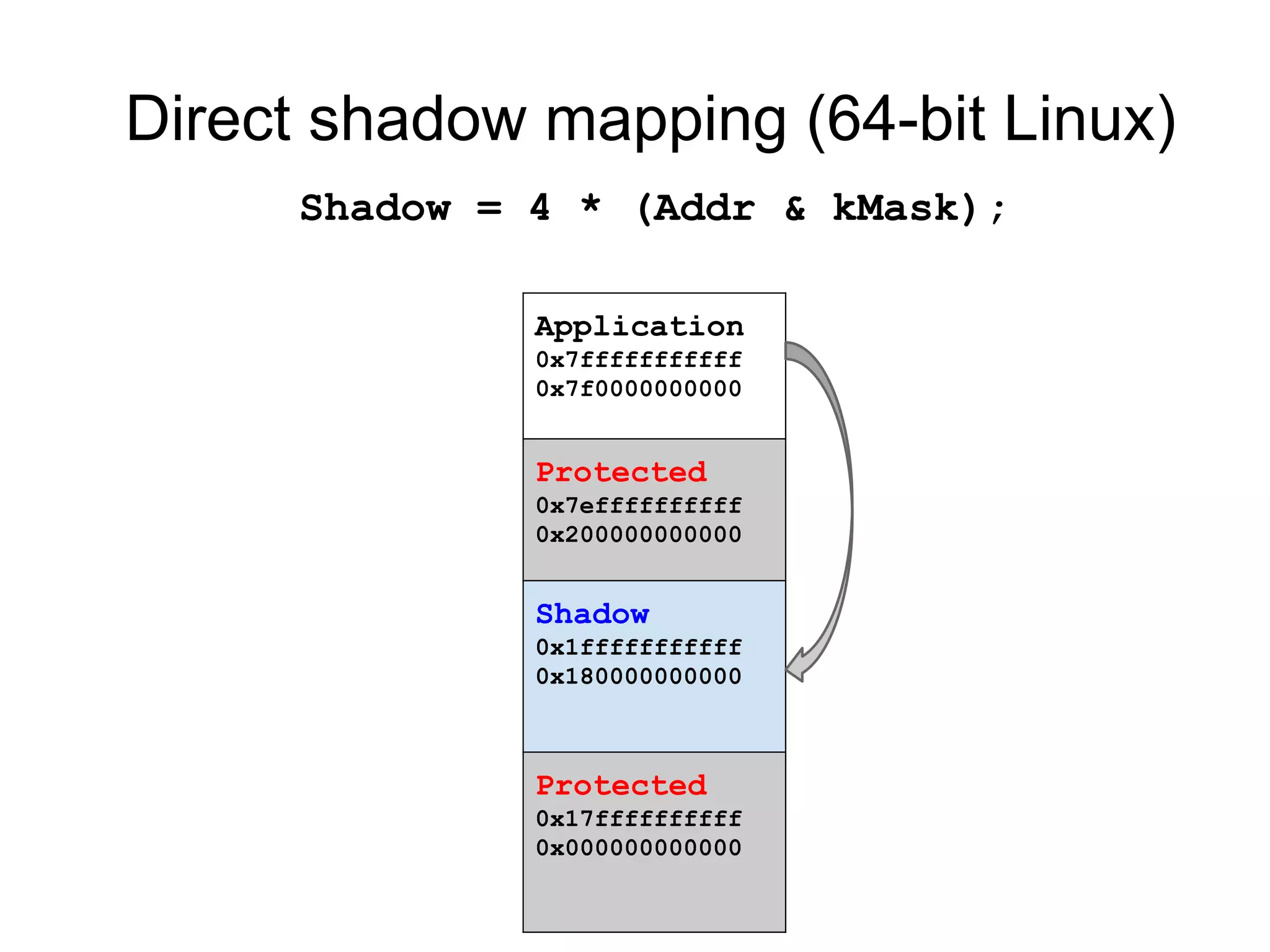
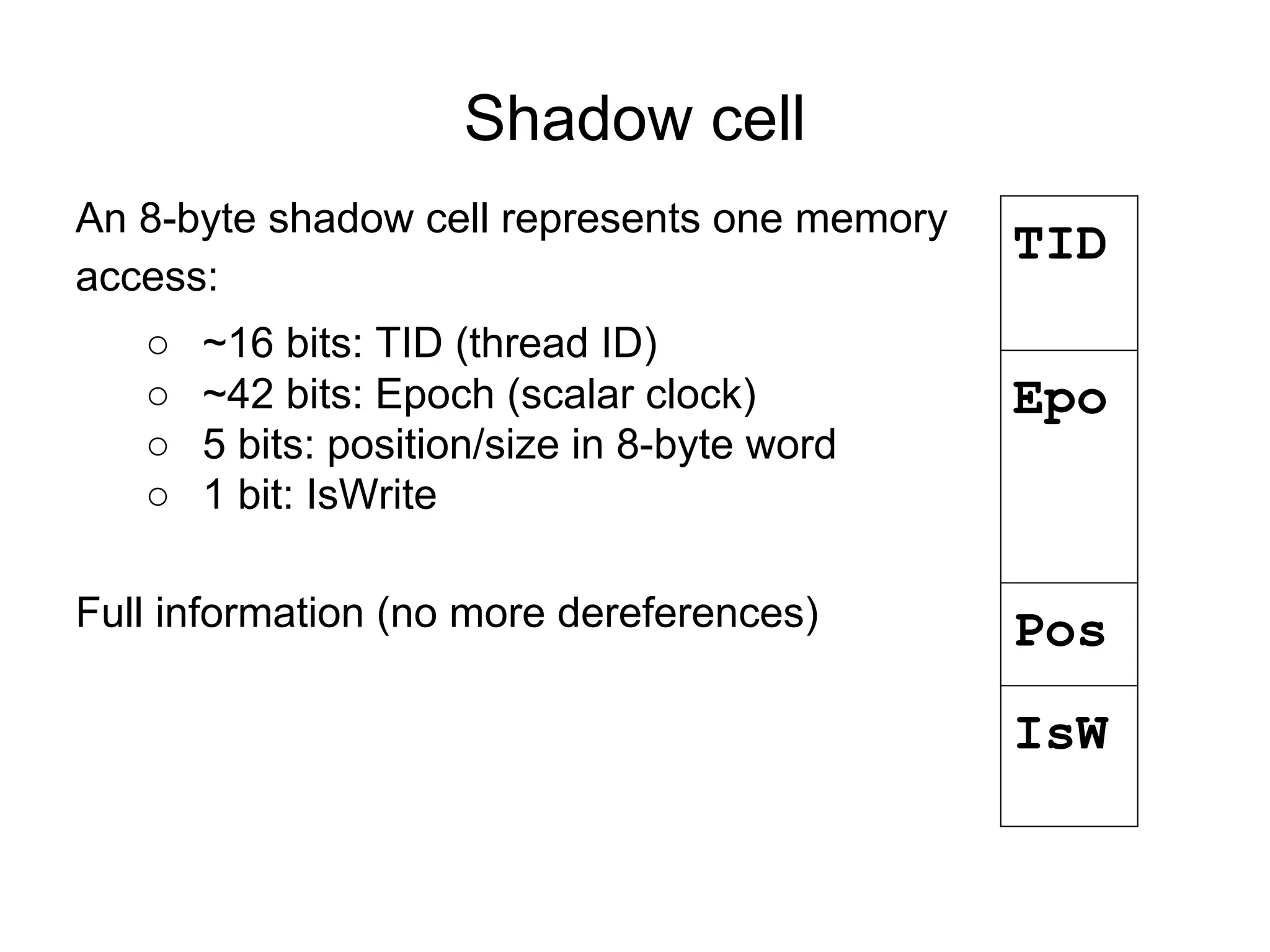
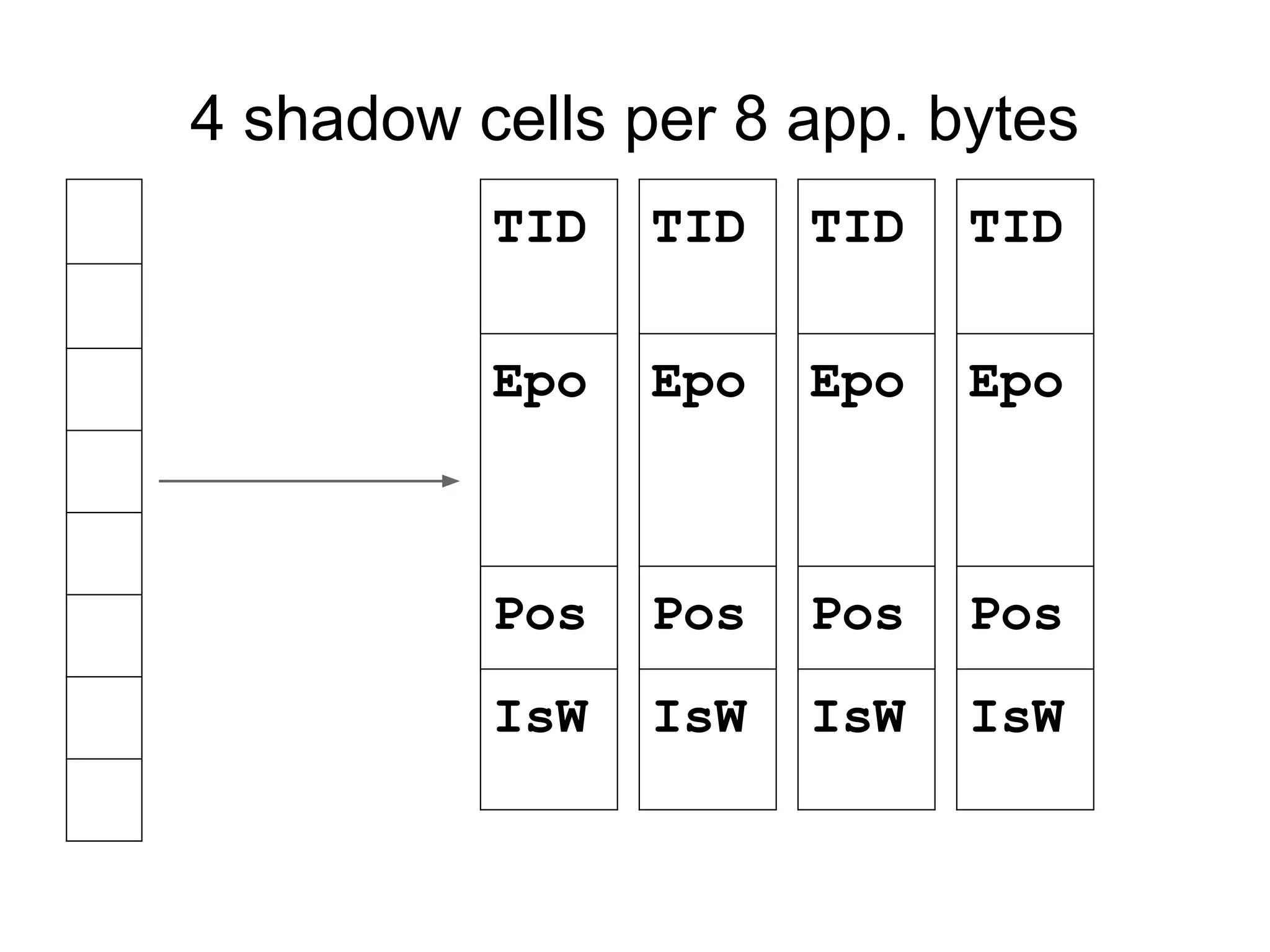
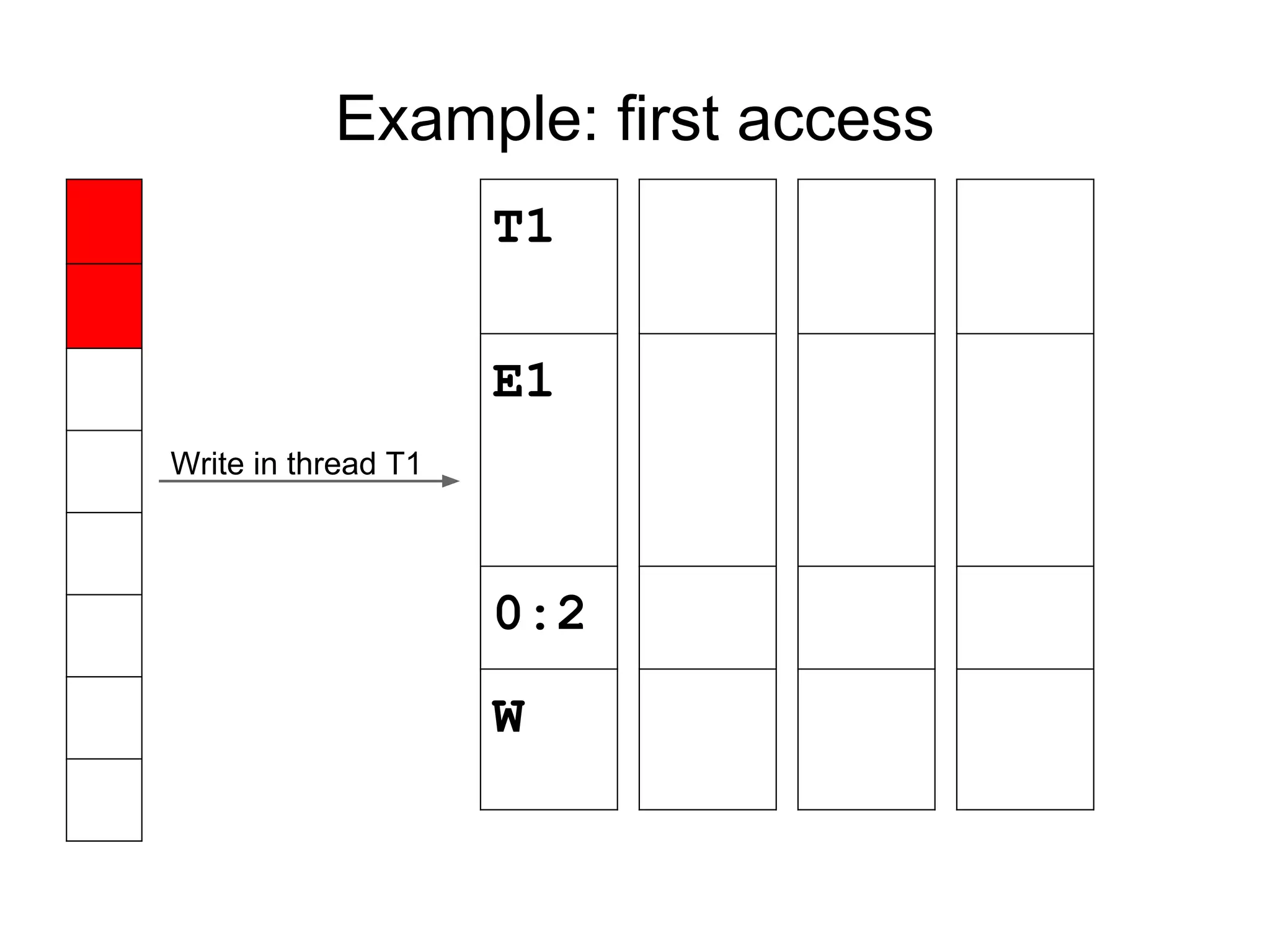
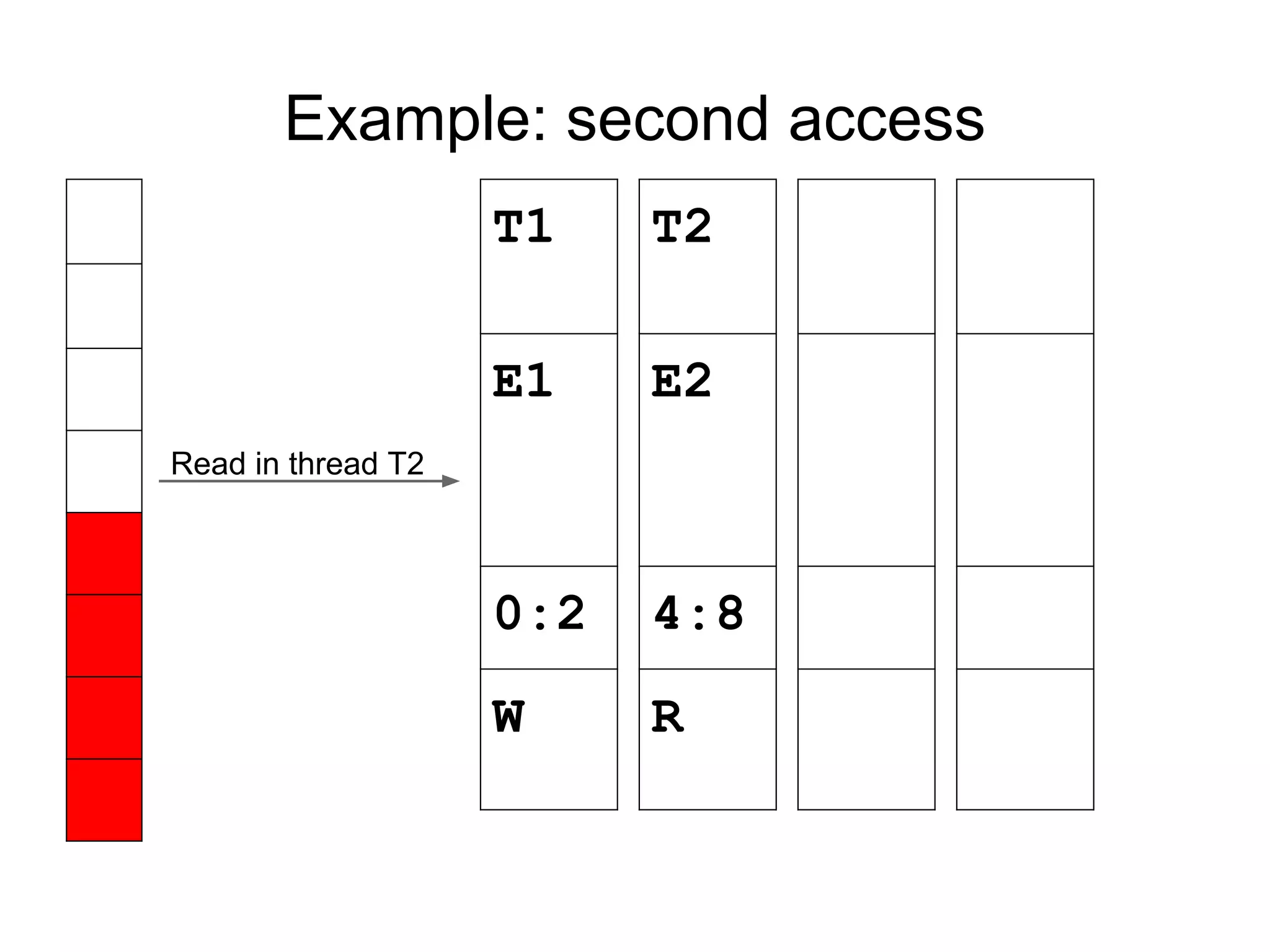
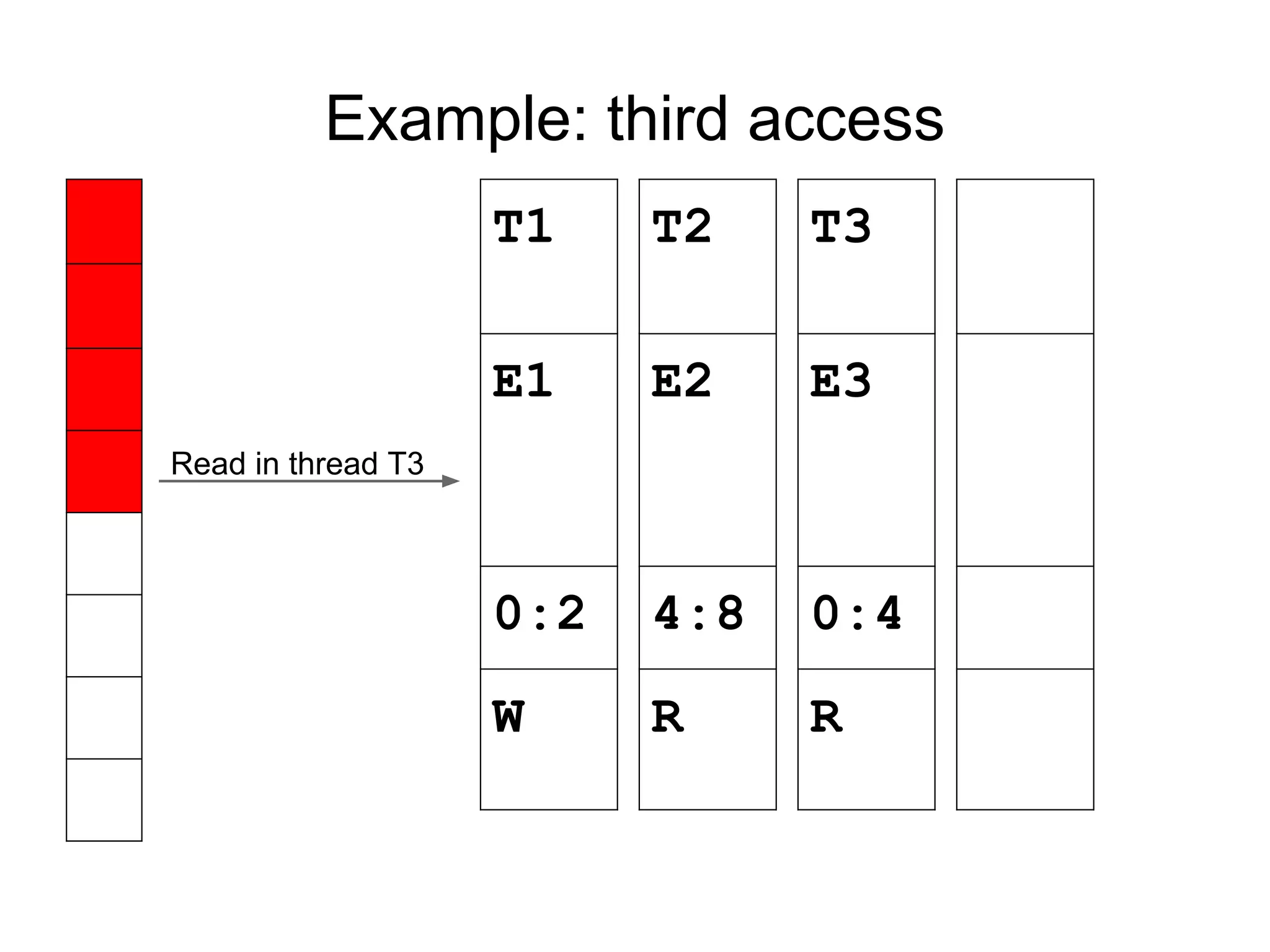
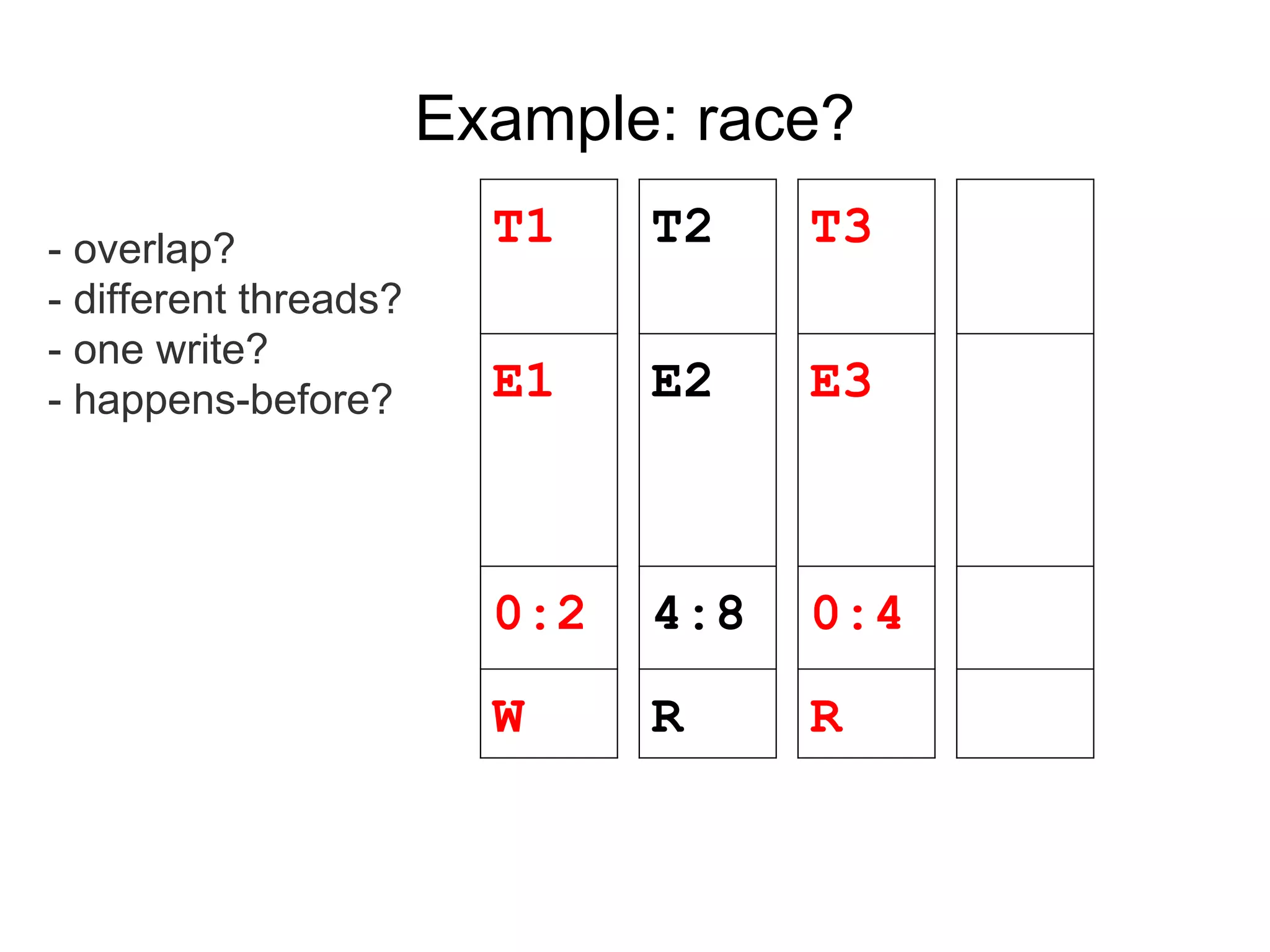
![Fast happens-before
Previous access by T1 at TS1 (from shadow).
Current access by T3.
T3->vclock[T1] > TS1 -> no race
T3->vclock[T1] < TS1 -> RACE
Constant-time operation: 1 local load + 1
comparison.](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-31-2048.jpg)




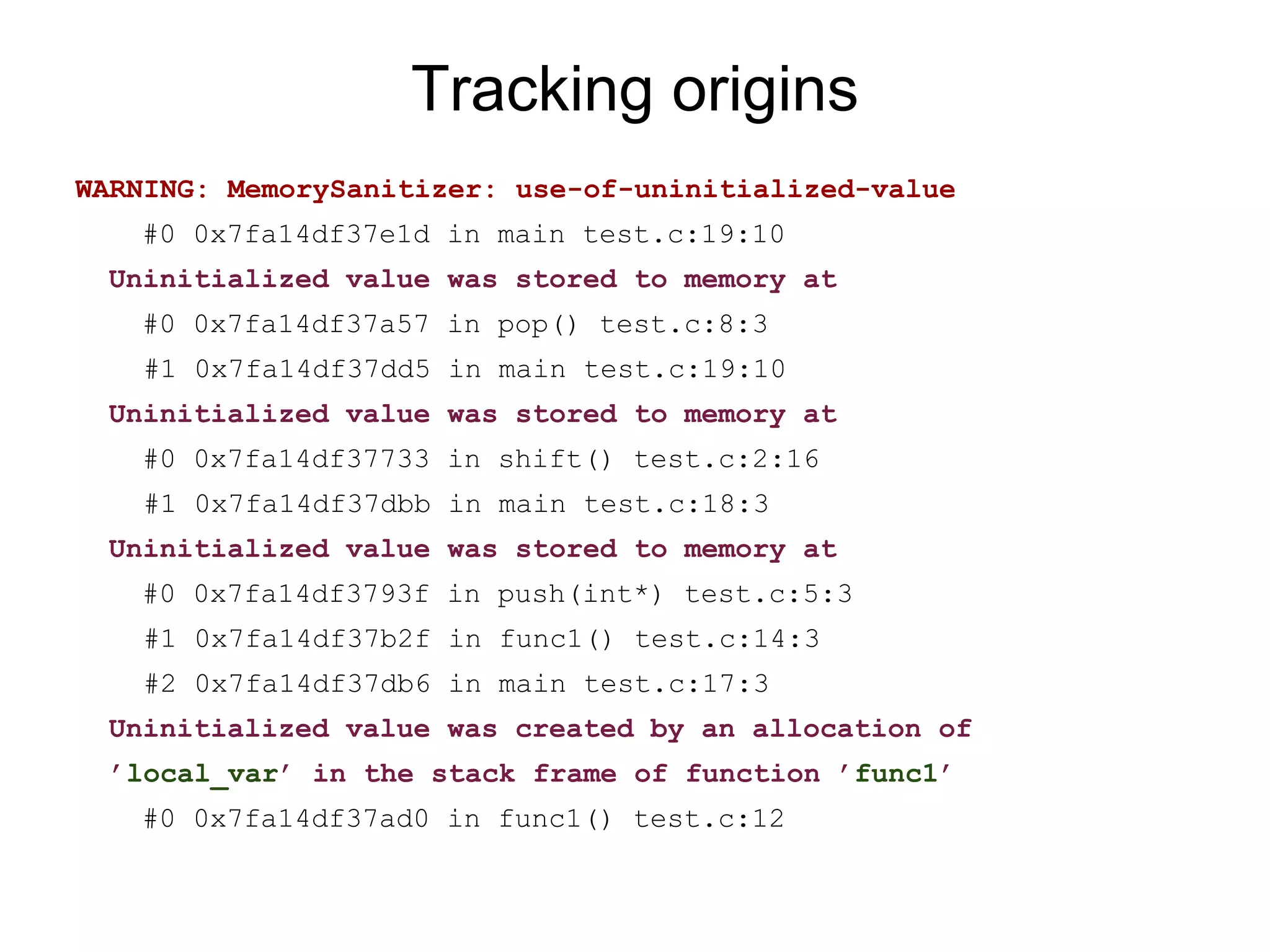
![MSan report example: UMR
int main(int argc, char **argv) {
int x[10];
x[0] = 1;
if (x[argc]) return 1;
...
% clang -fsanitize=memory -fPIE -pie a.c -g; ./a.out
WARNING: MemorySanitizer: UMR (uninitialized-memory-read)
#0 0x7ff6b05d9ca7 in main stack_umr.c:4
ORIGIN: stack allocation: x@main](https://image.slidesharecdn.com/sanitizercppconrussia-150306093216-conversion-gate01/75/Address-Thread-Memory-Sanitizer-37-2048.jpg)