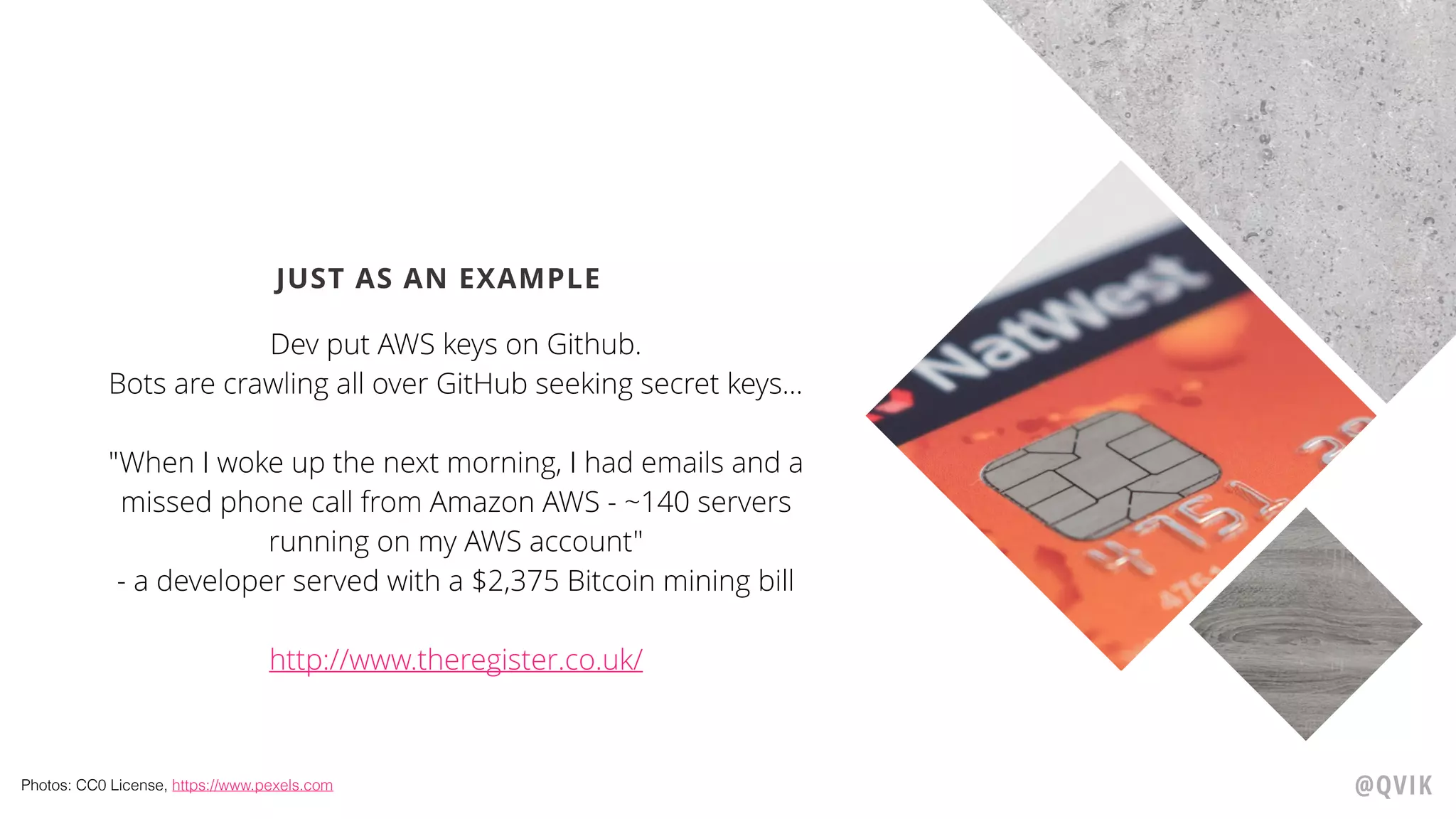
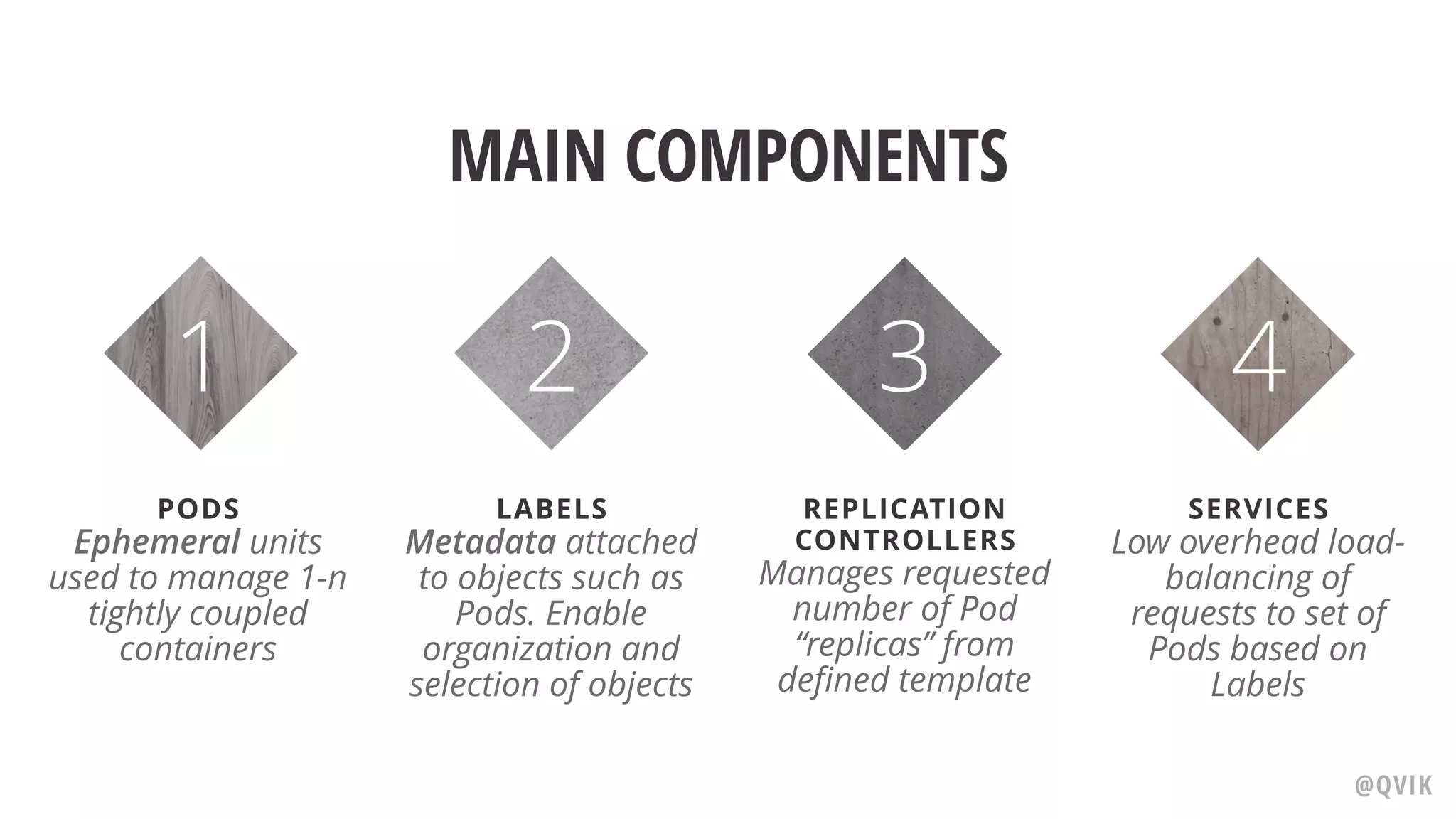
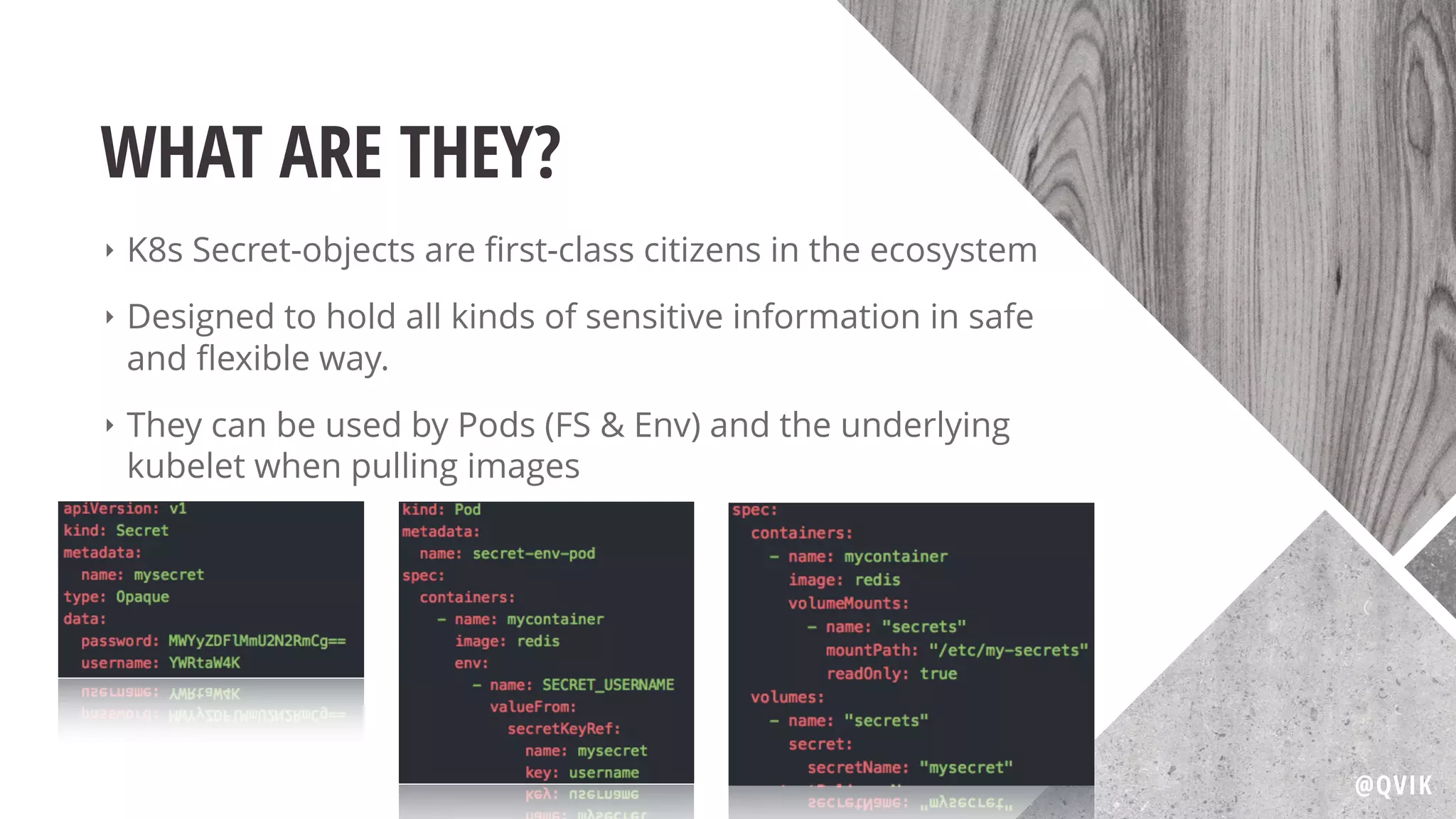
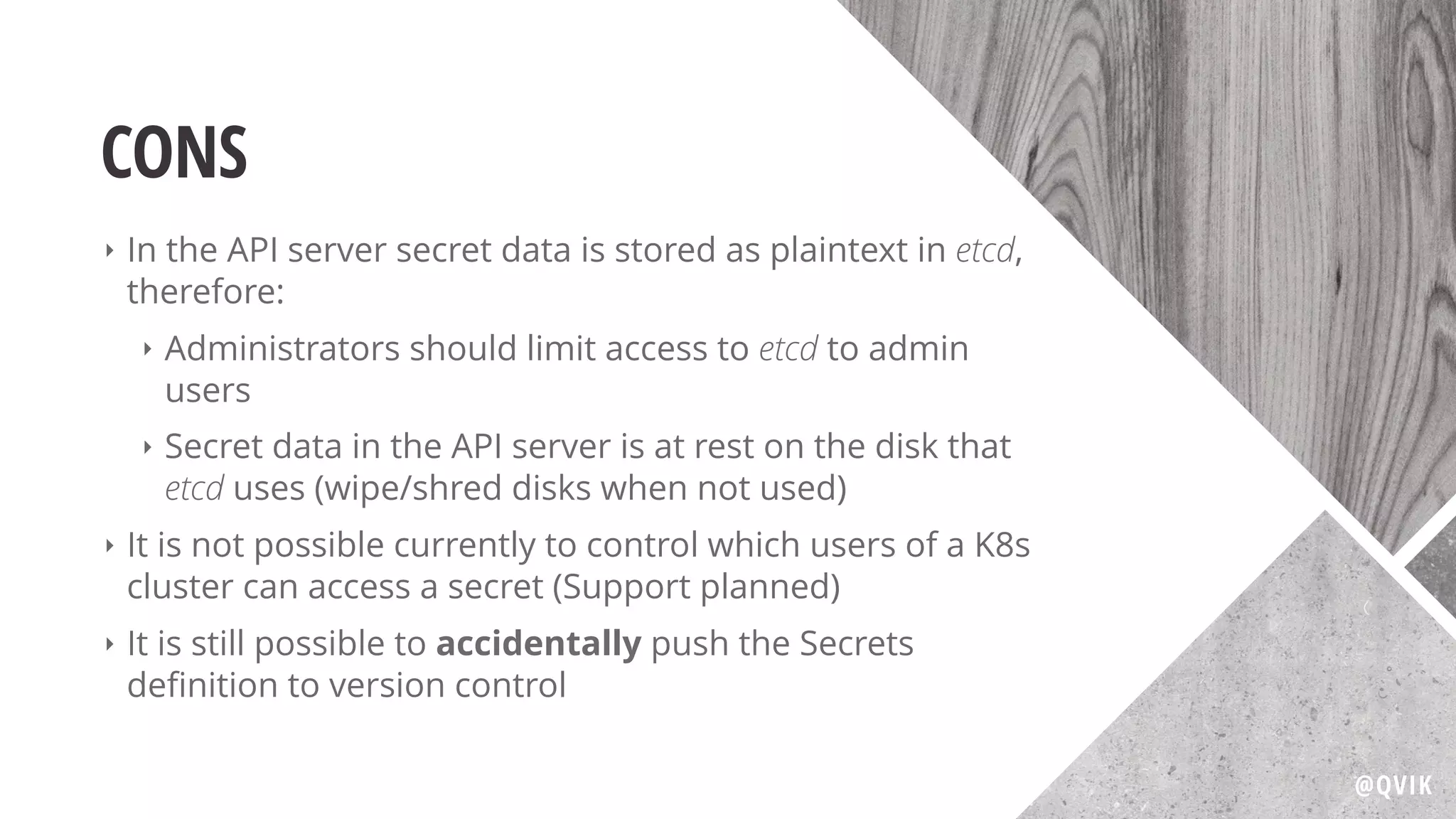
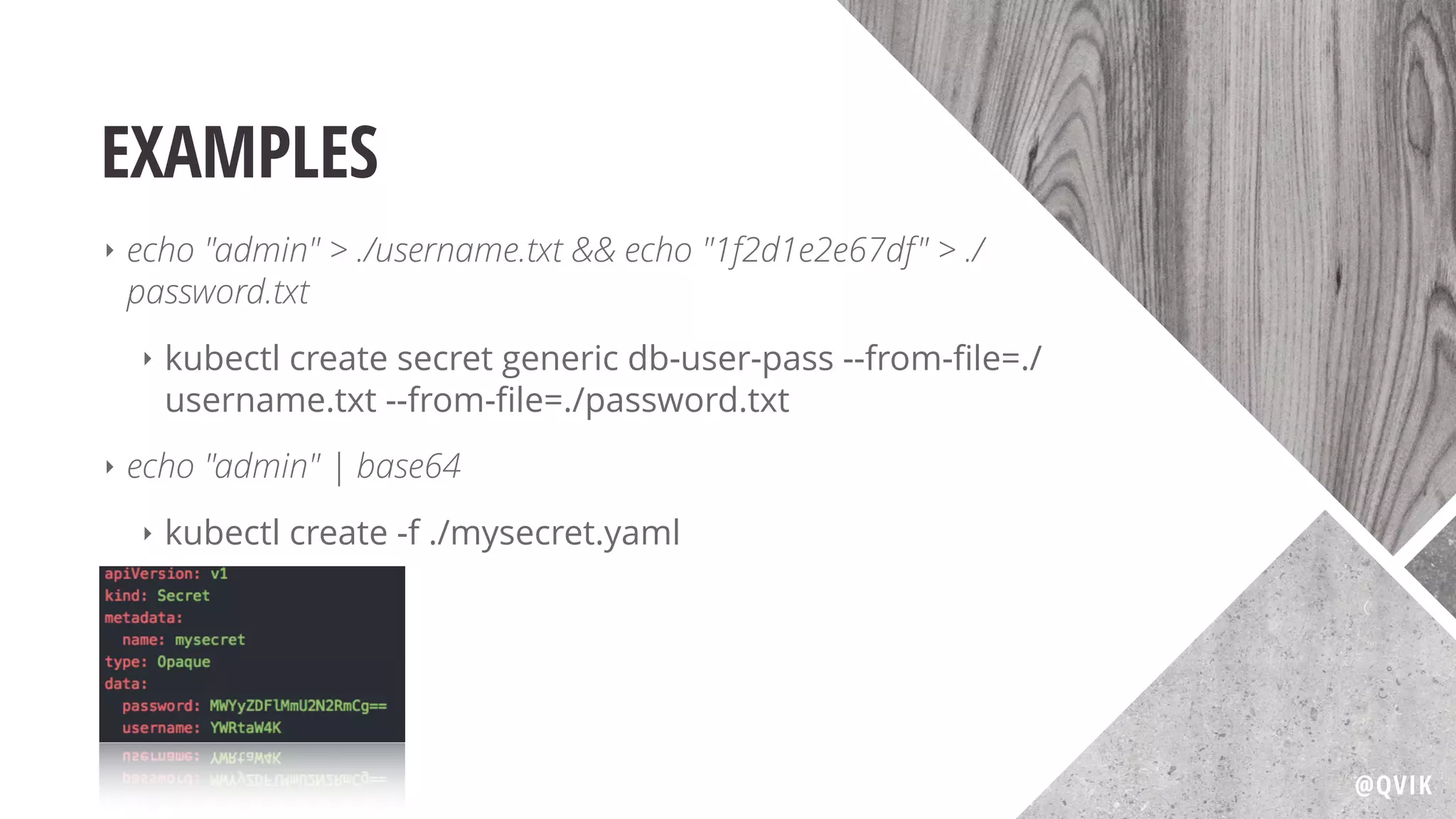
Jerry Jalava discusses the importance of managing sensitive information in applications, particularly in the context of Kubernetes and Docker. He highlights the risks of exposing secrets like database or API credentials, sharing cautionary anecdotes of developers facing significant consequences. The document also explains Kubernetes secrets and config maps, their functionalities, and best practices for secure usage.