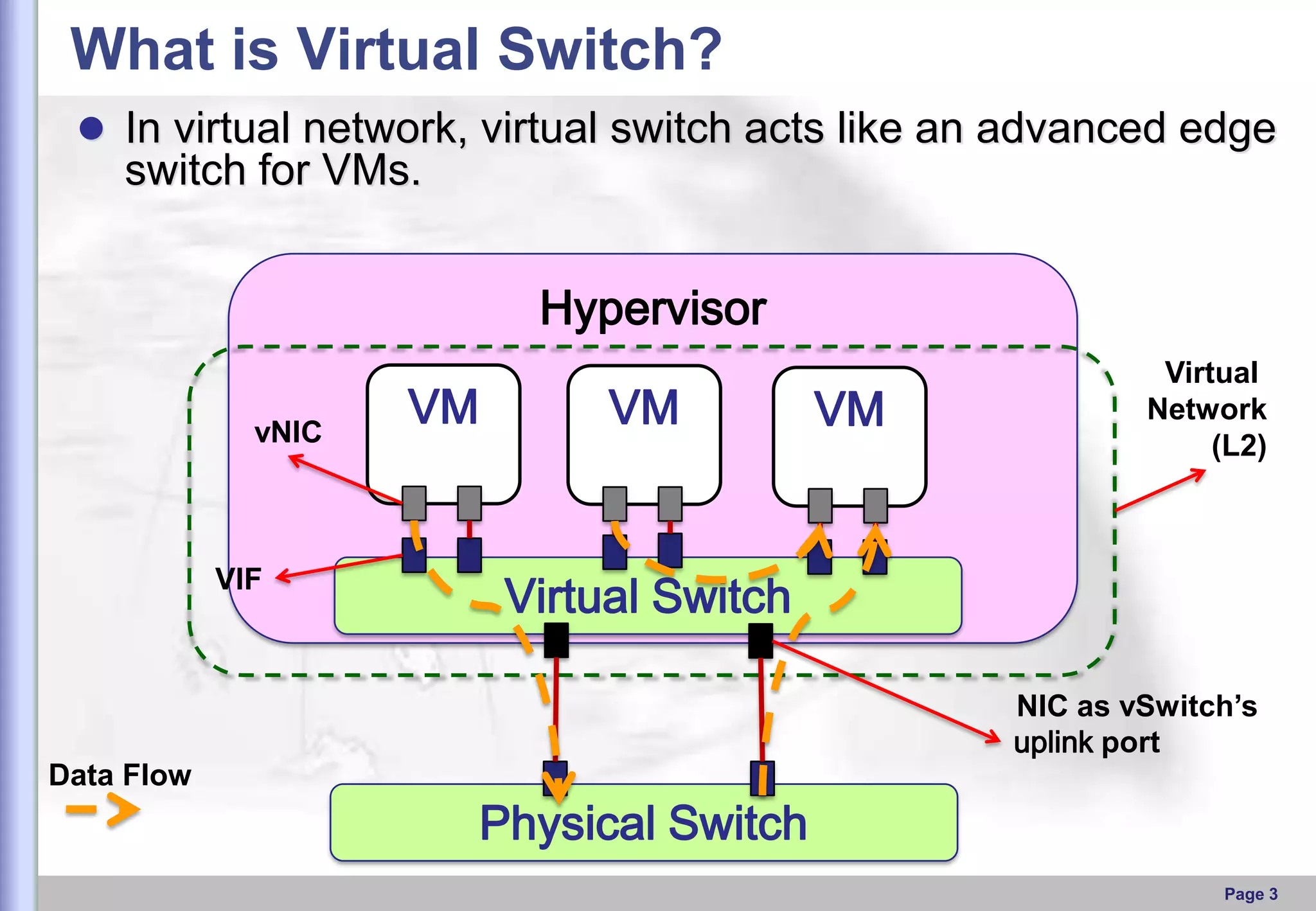
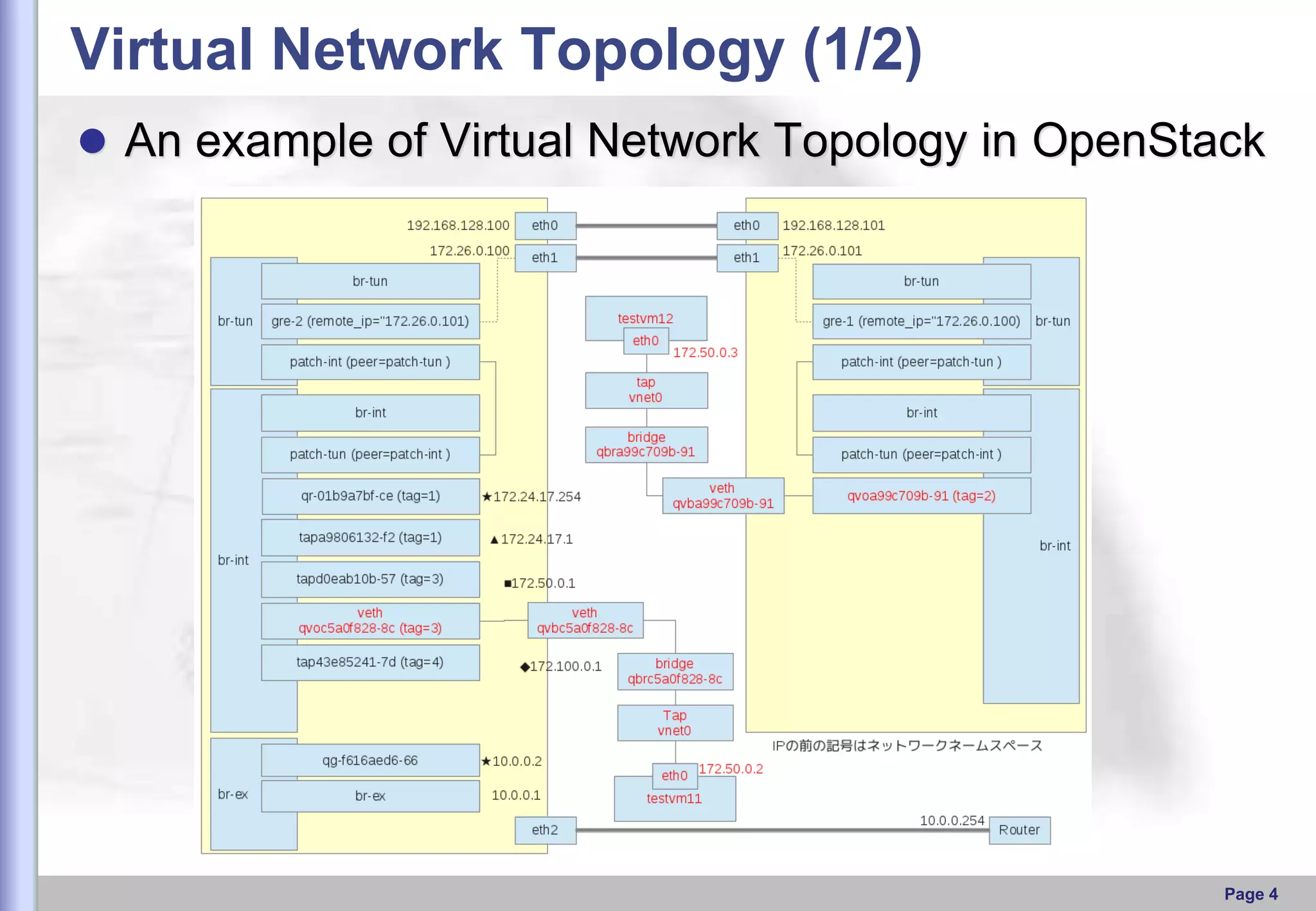
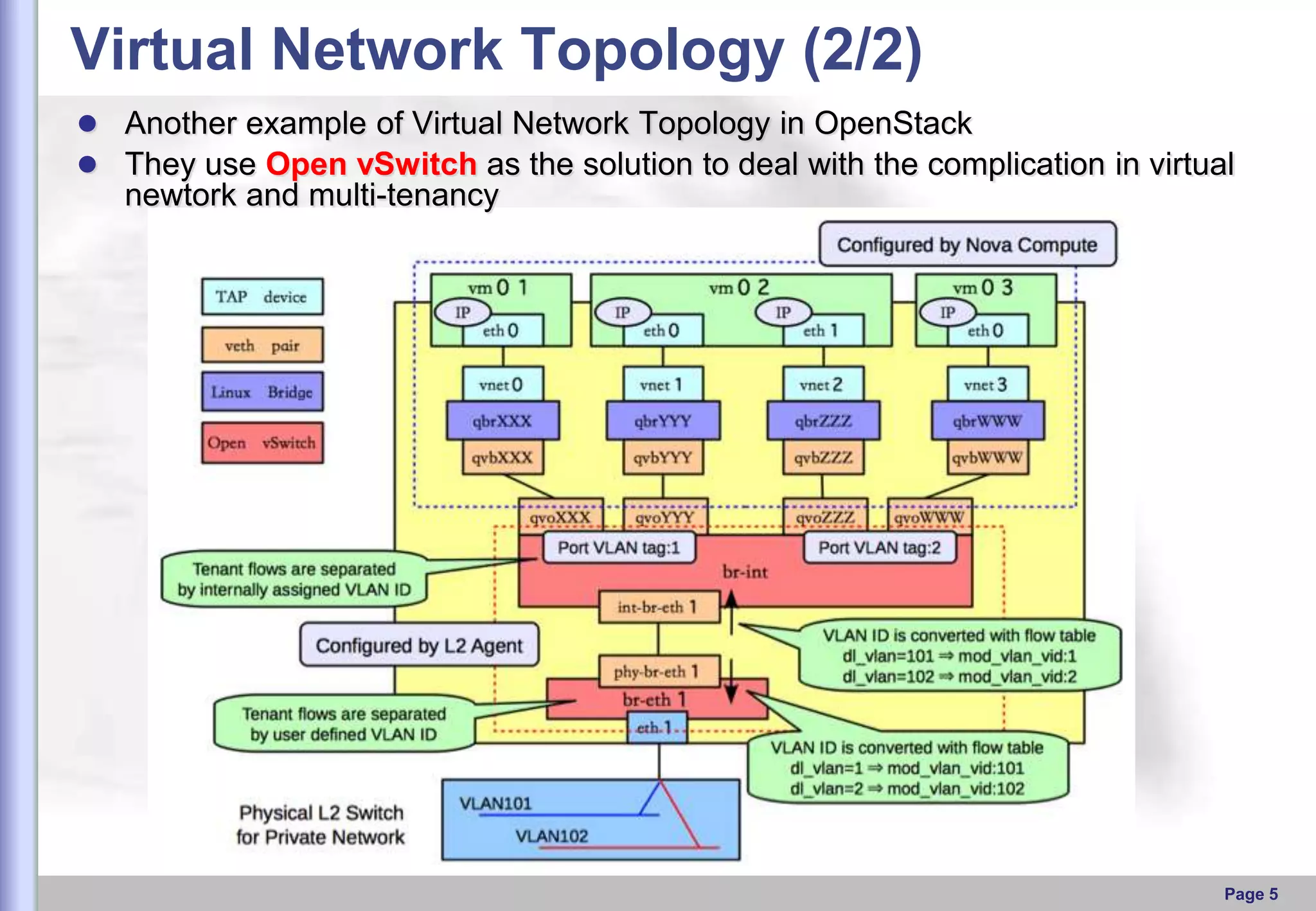
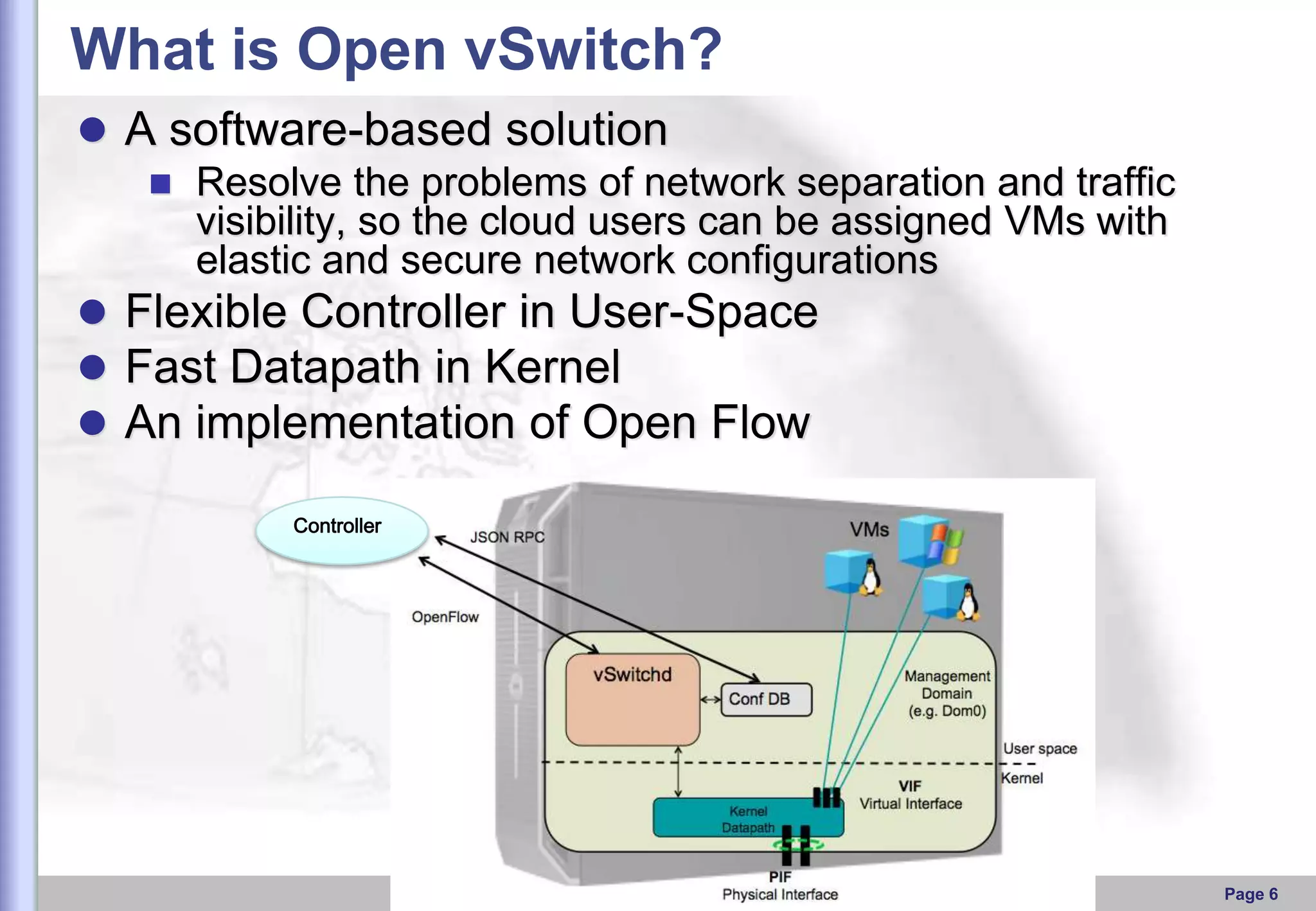
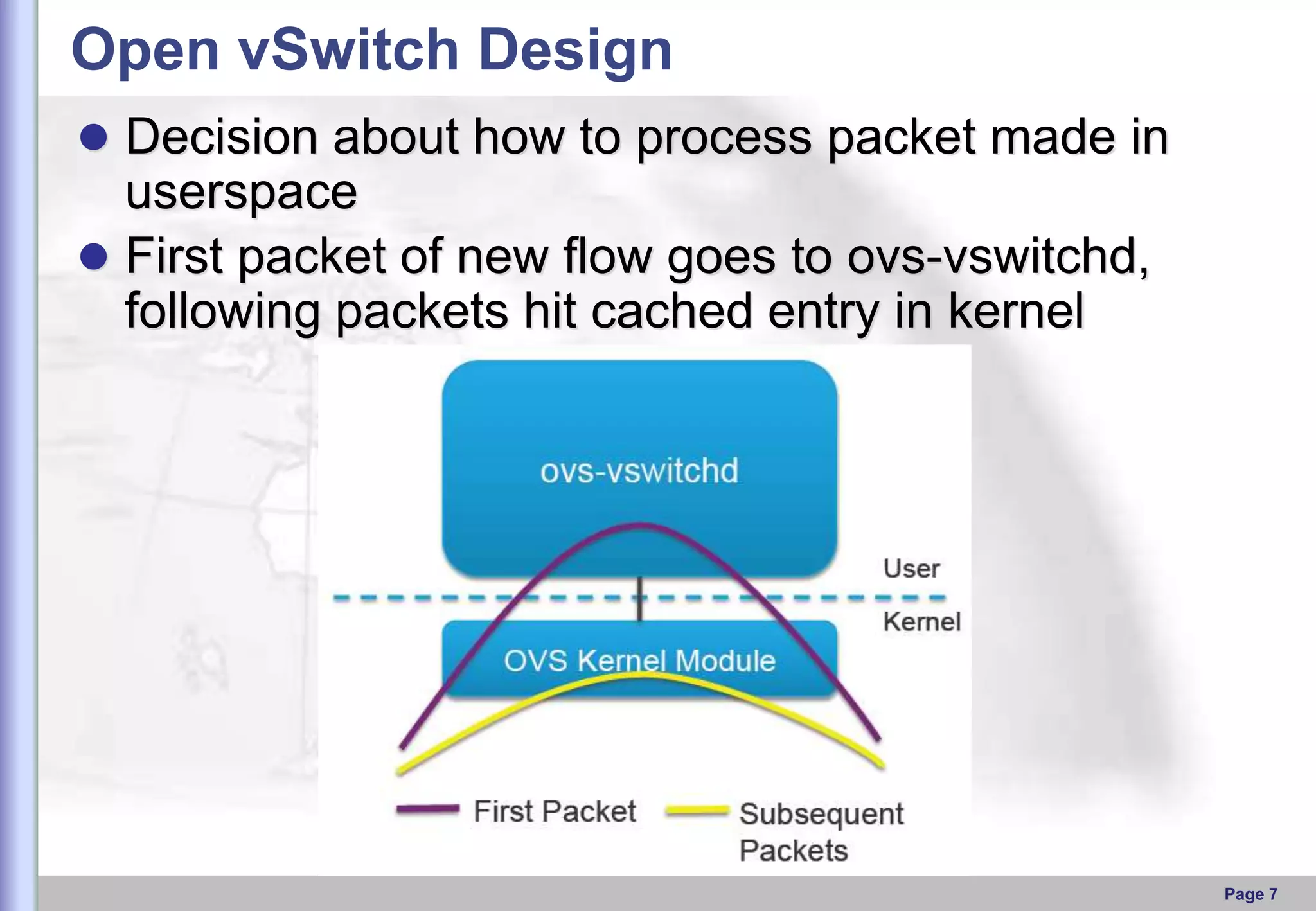
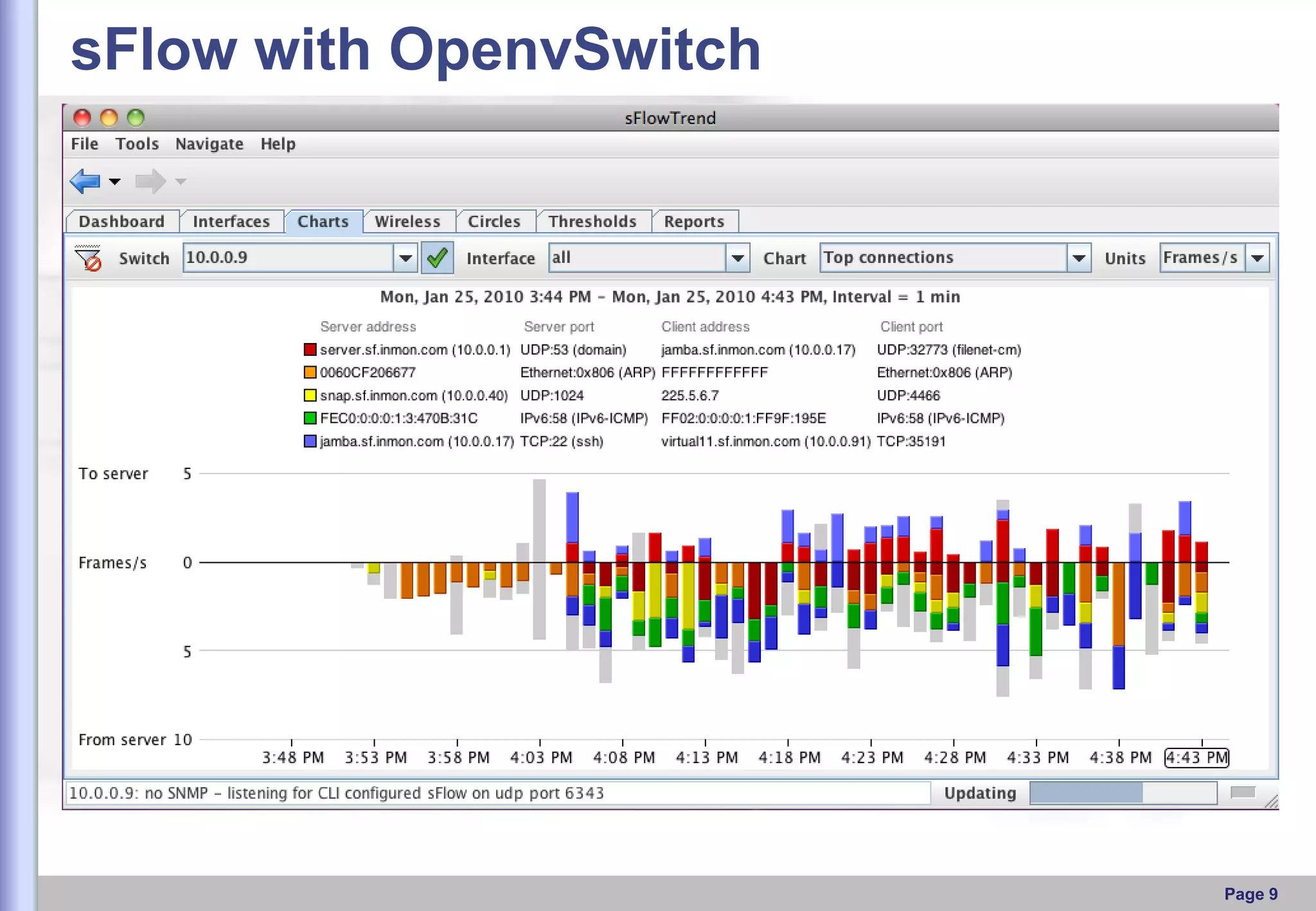
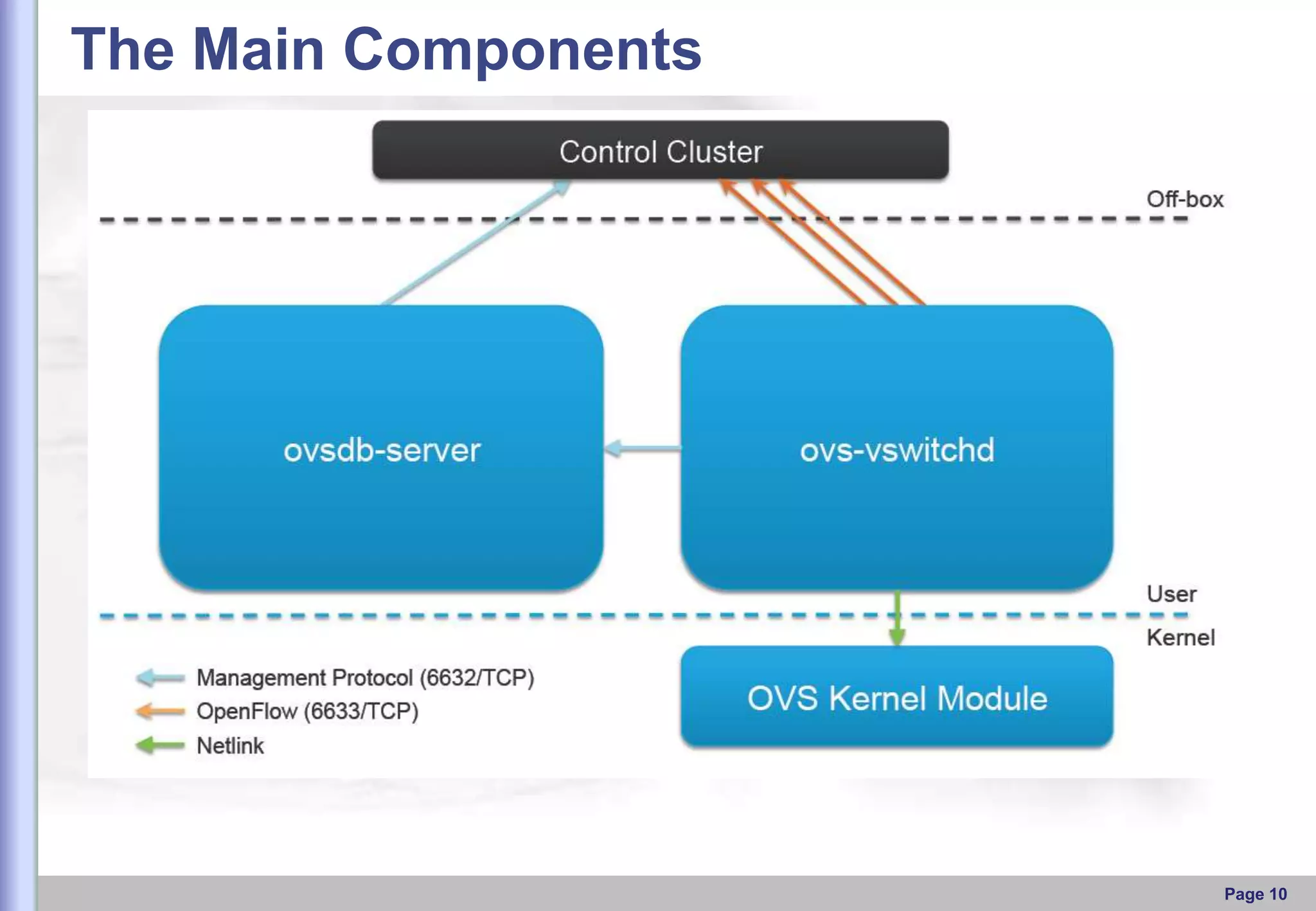
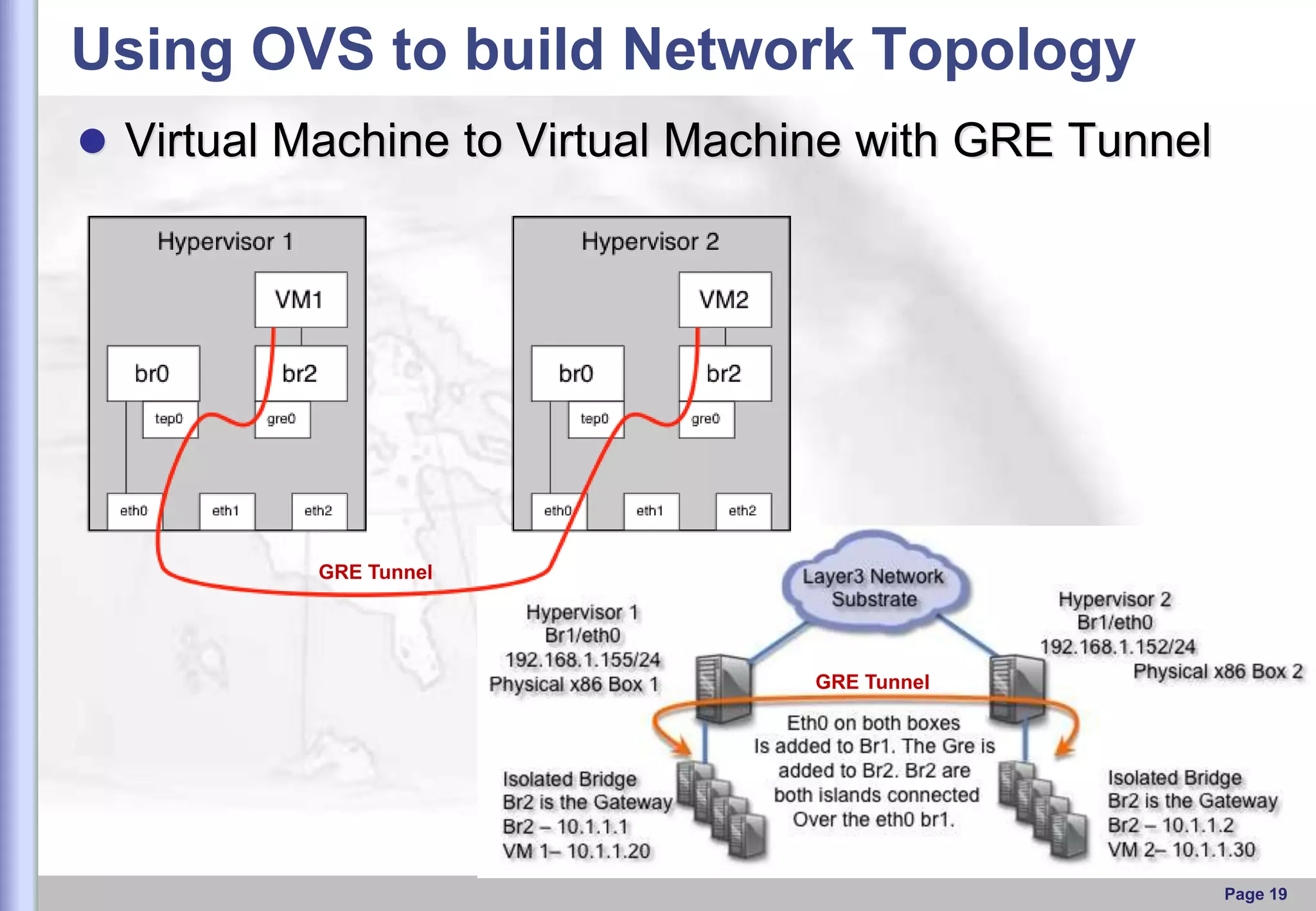
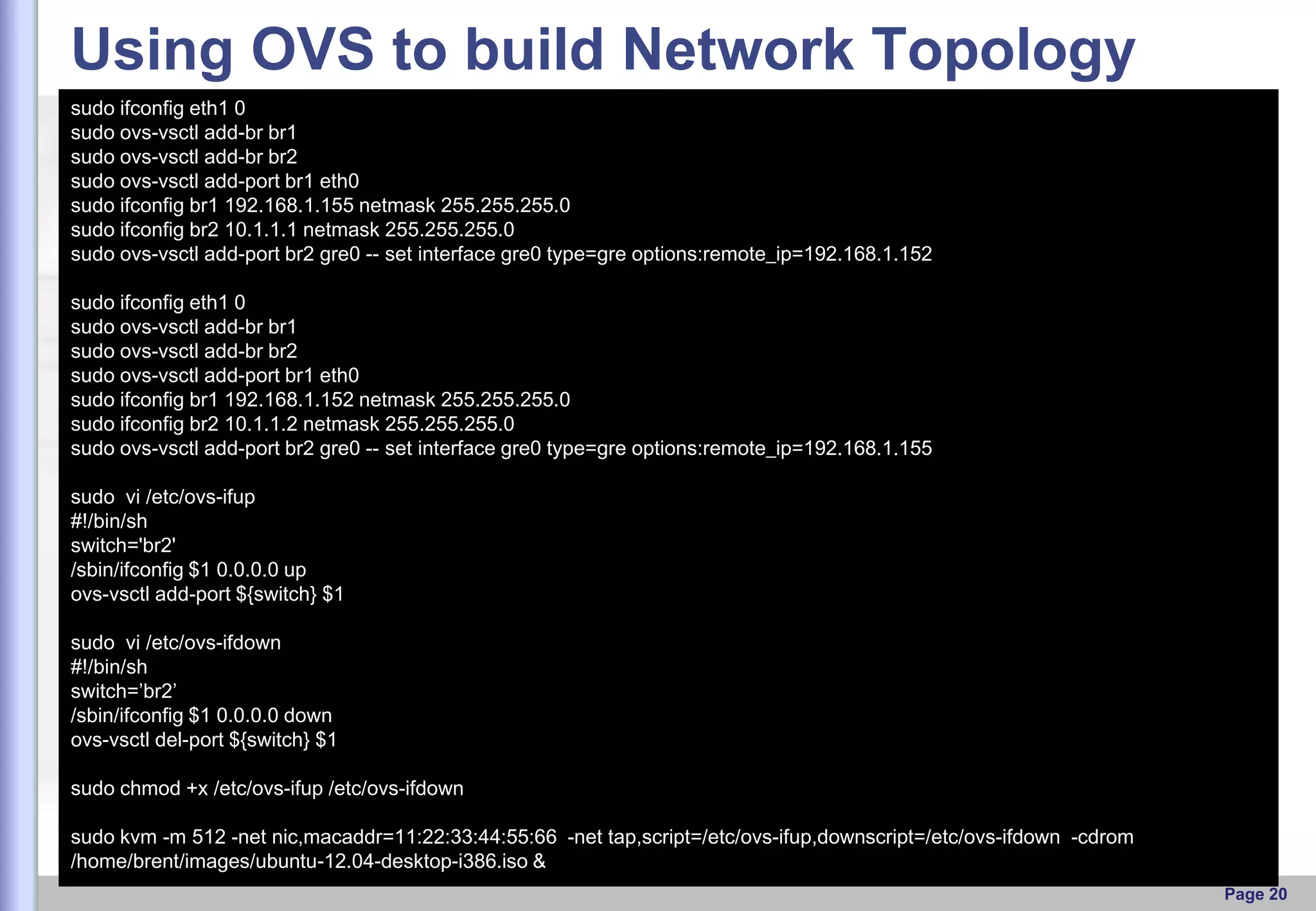
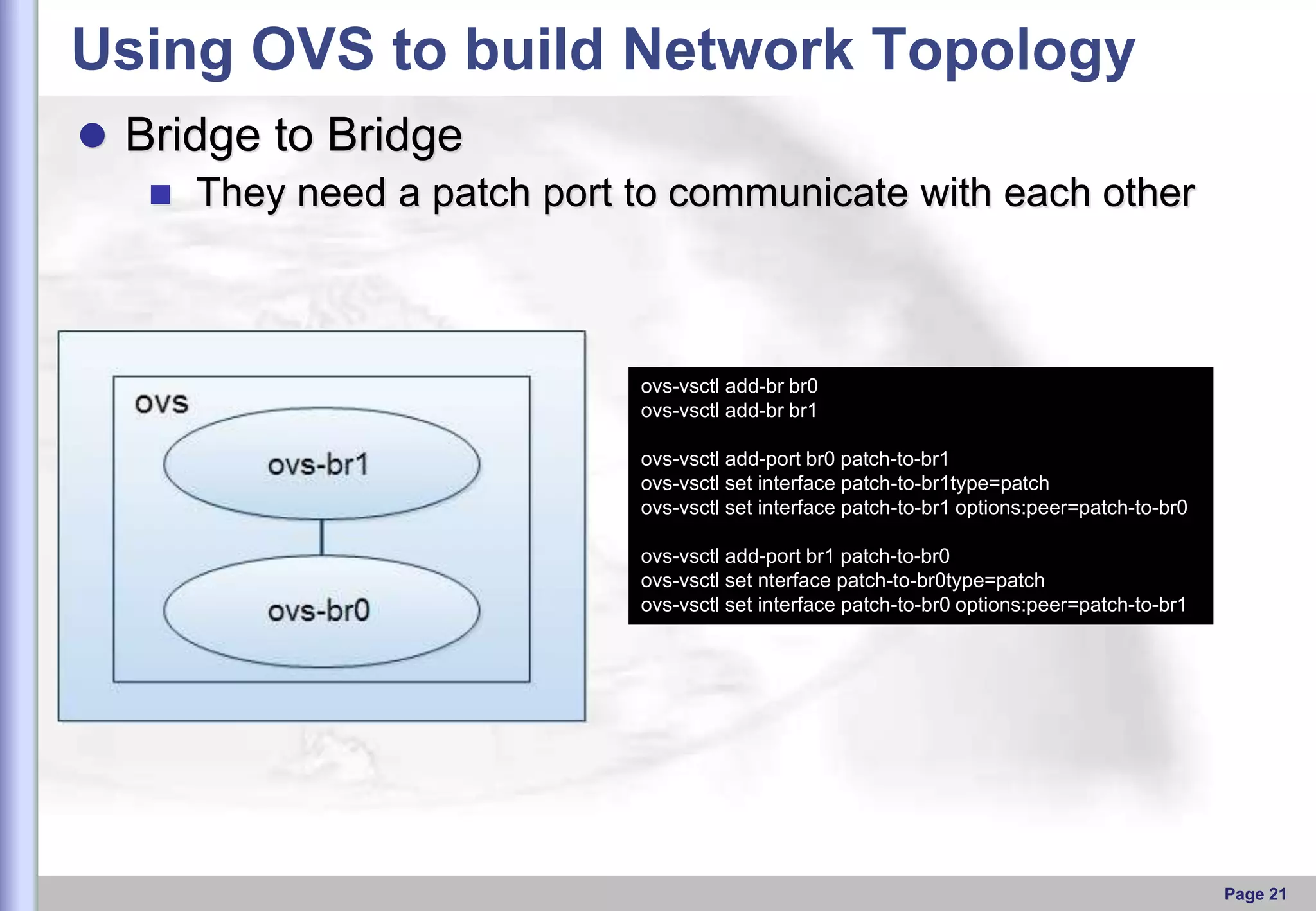
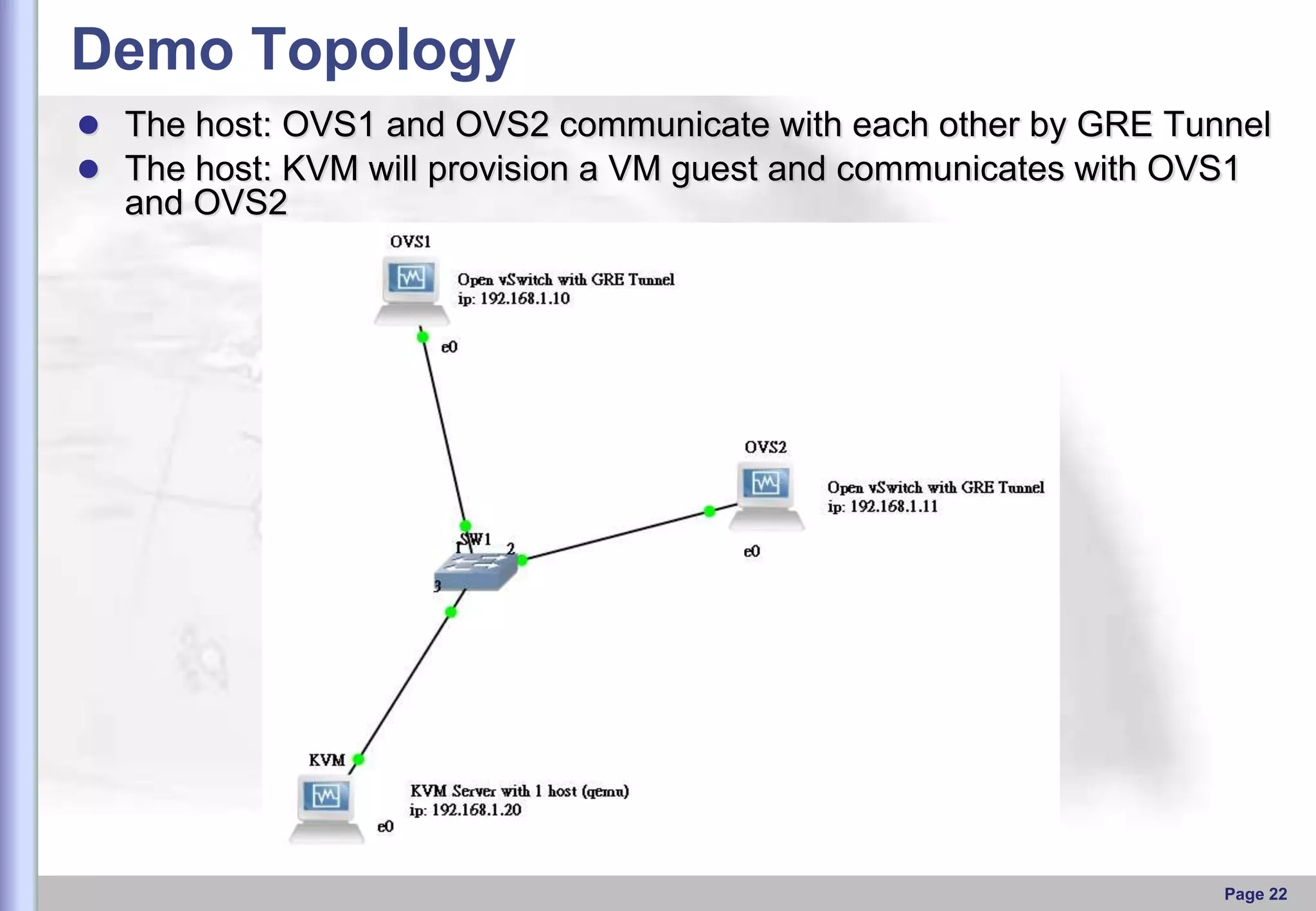
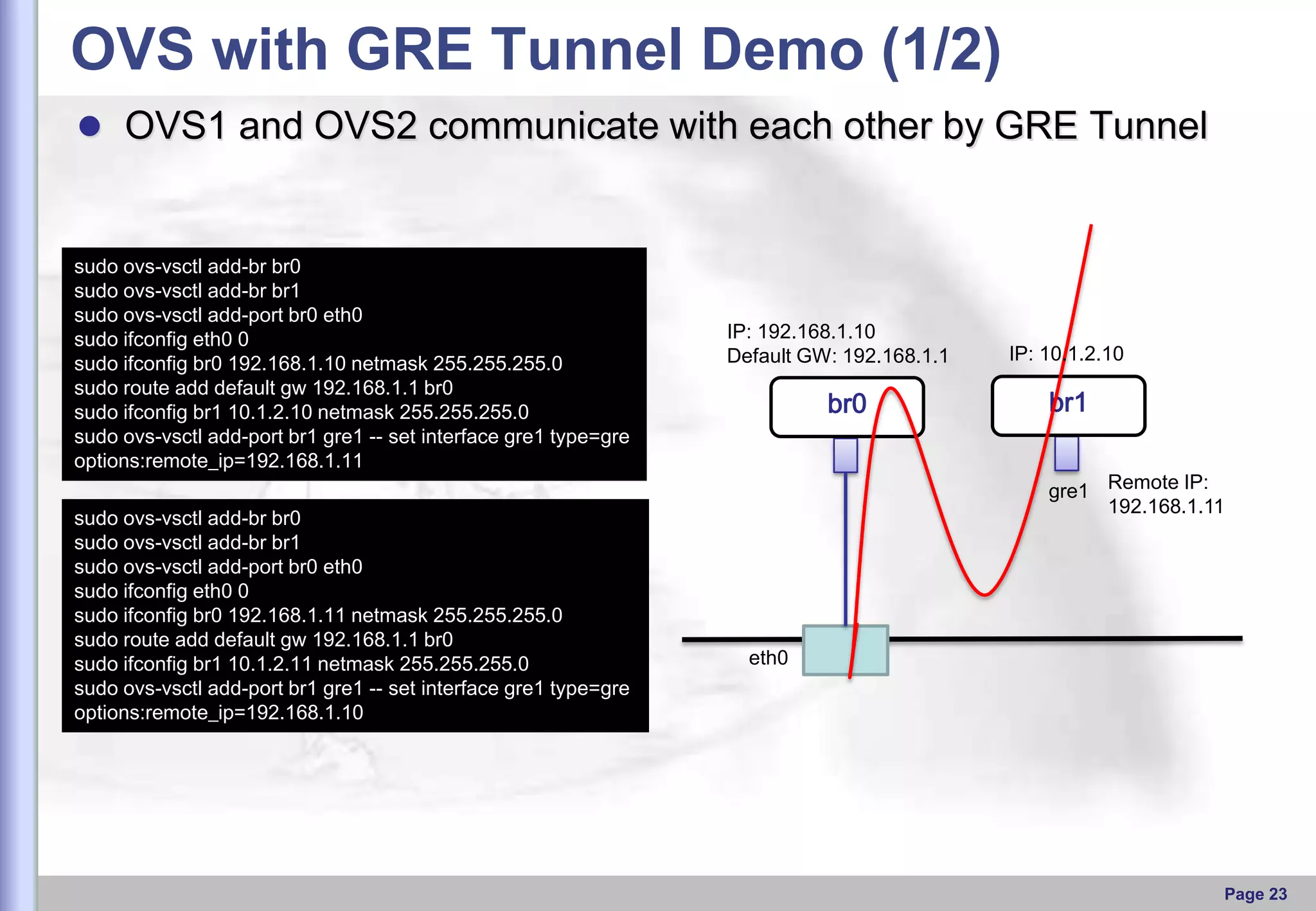
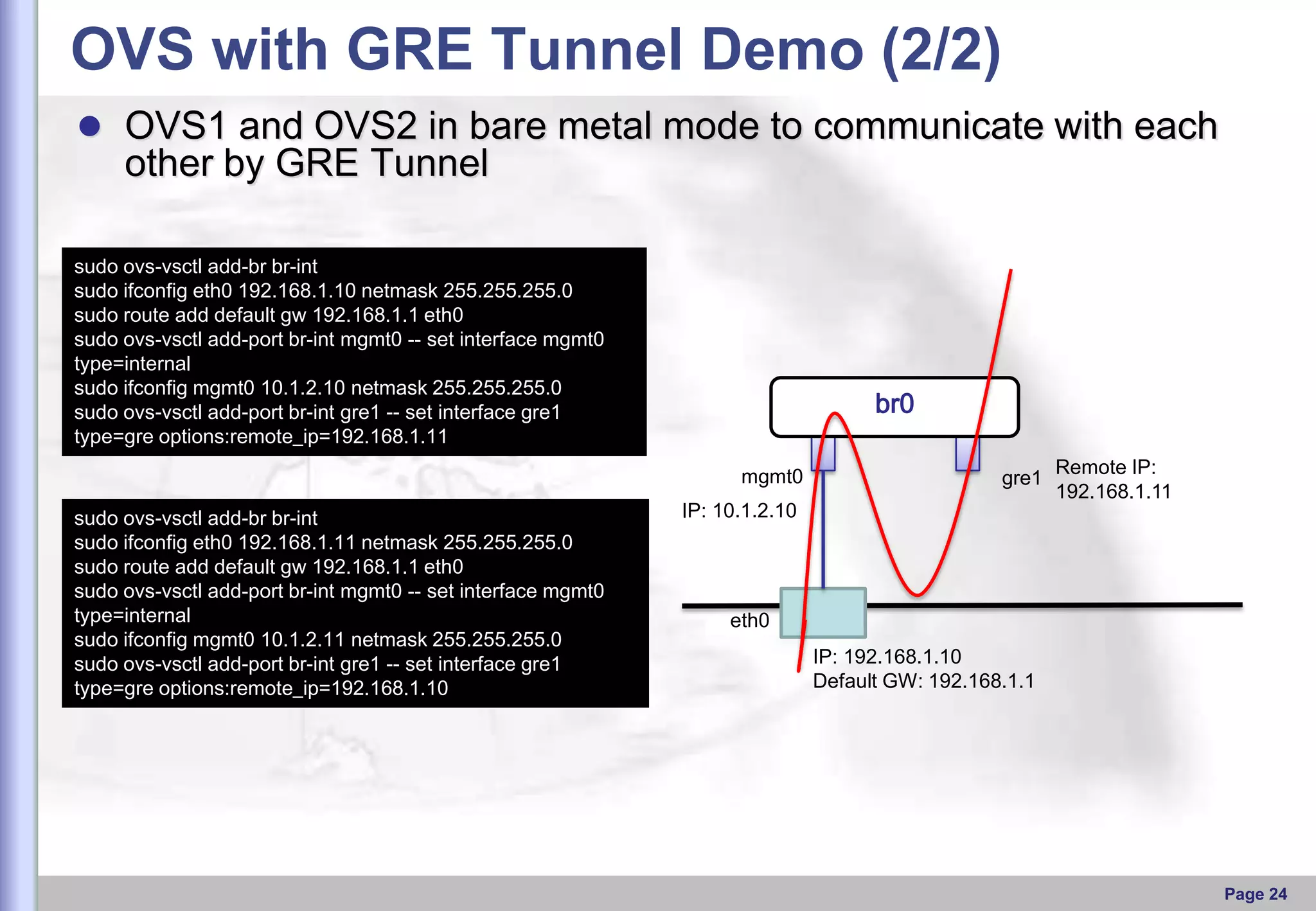
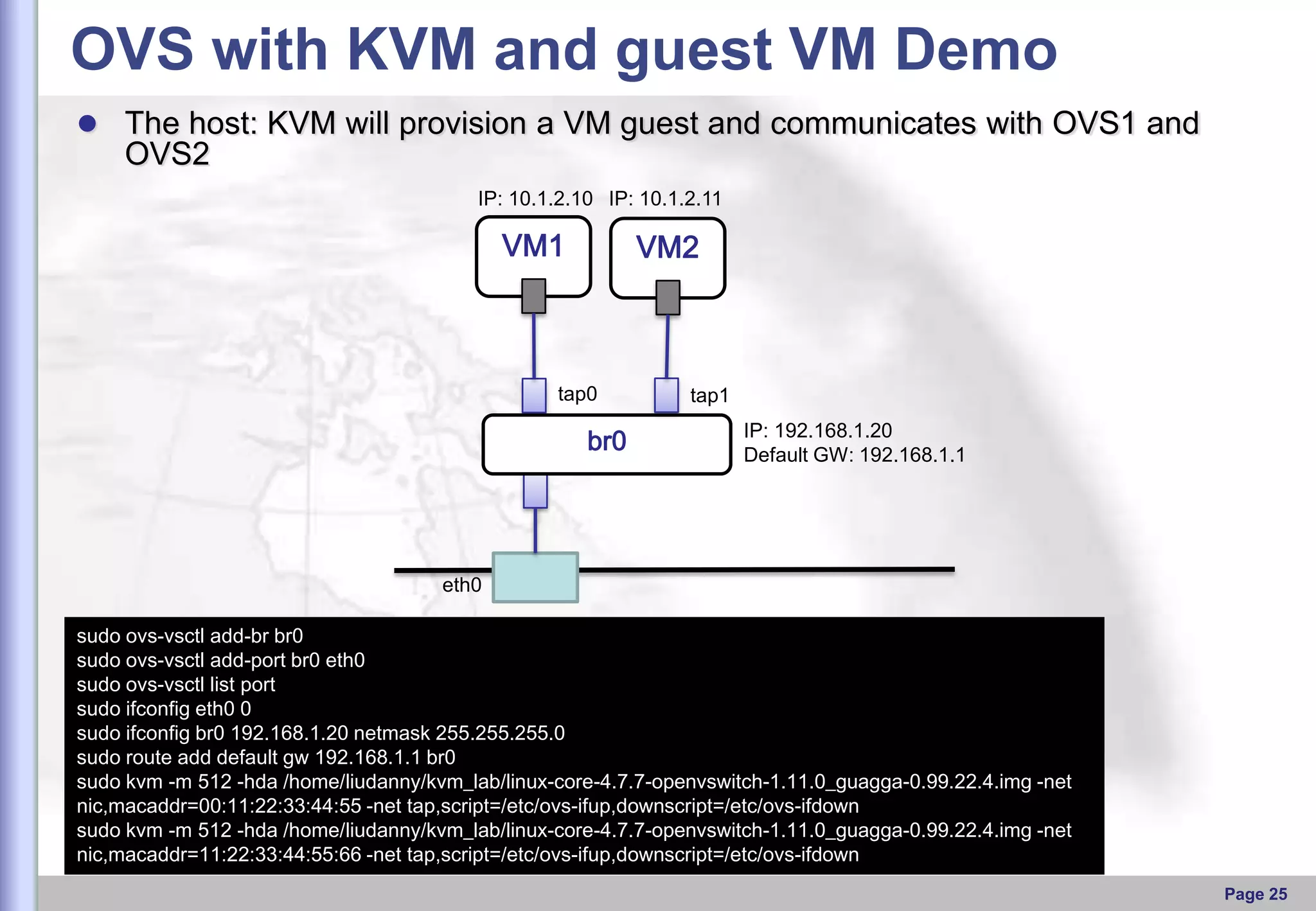
This document provides an overview of Open vSwitch, including what it is, its main components, features, and how it can be used to build virtual network topologies. Open vSwitch is a software-defined networking switch that can be used to create virtual networks and handle network traffic between virtual machines and tunnels. It uses a distributed database, ovsdb-server, and a userspace daemon, ovs-vswitchd, to implement features like virtual switching, tunneling protocols, and OpenFlow support. Examples are provided for using Open vSwitch with KVM virtual machines and GRE tunnels to create virtual network topologies.