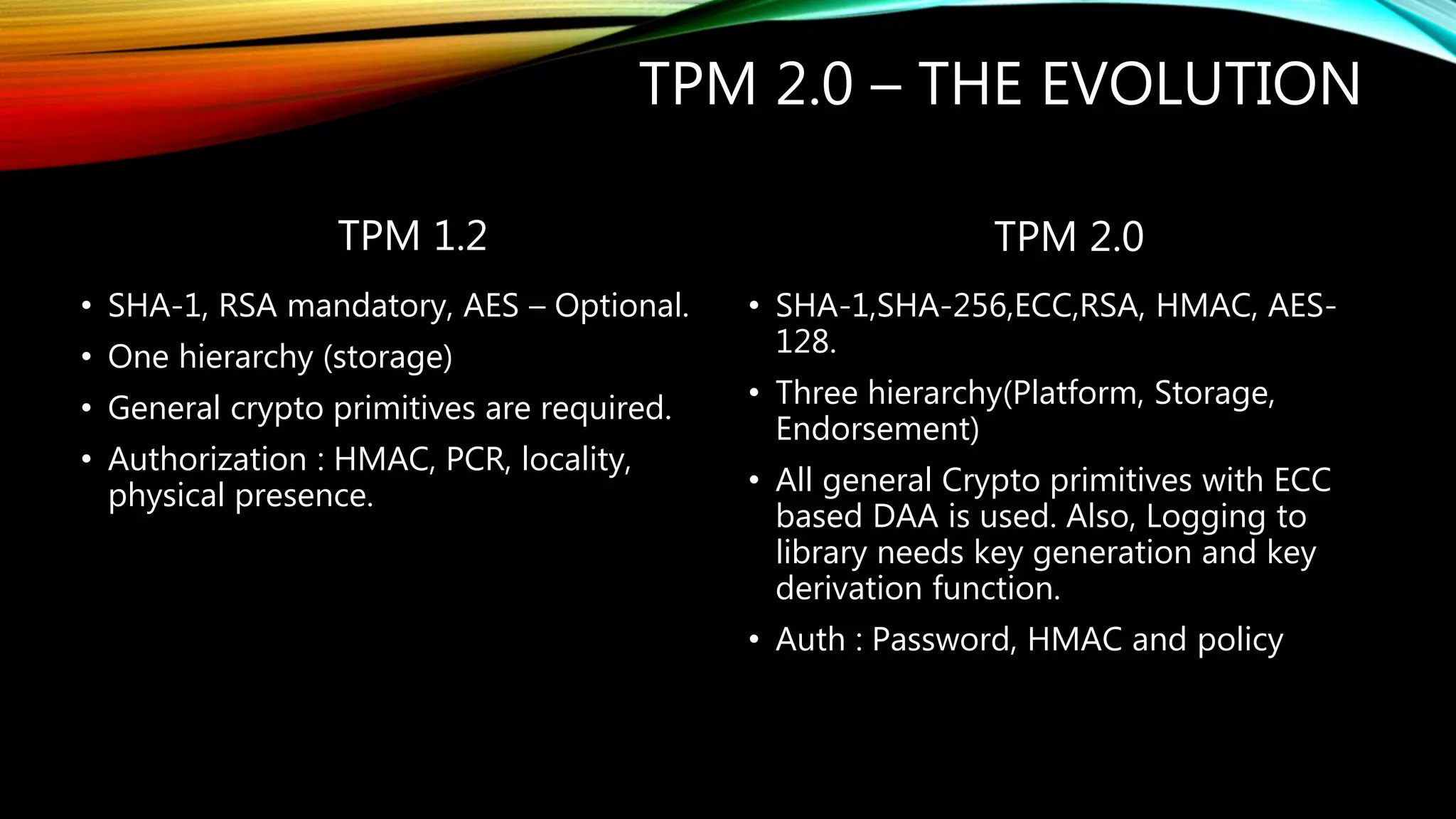
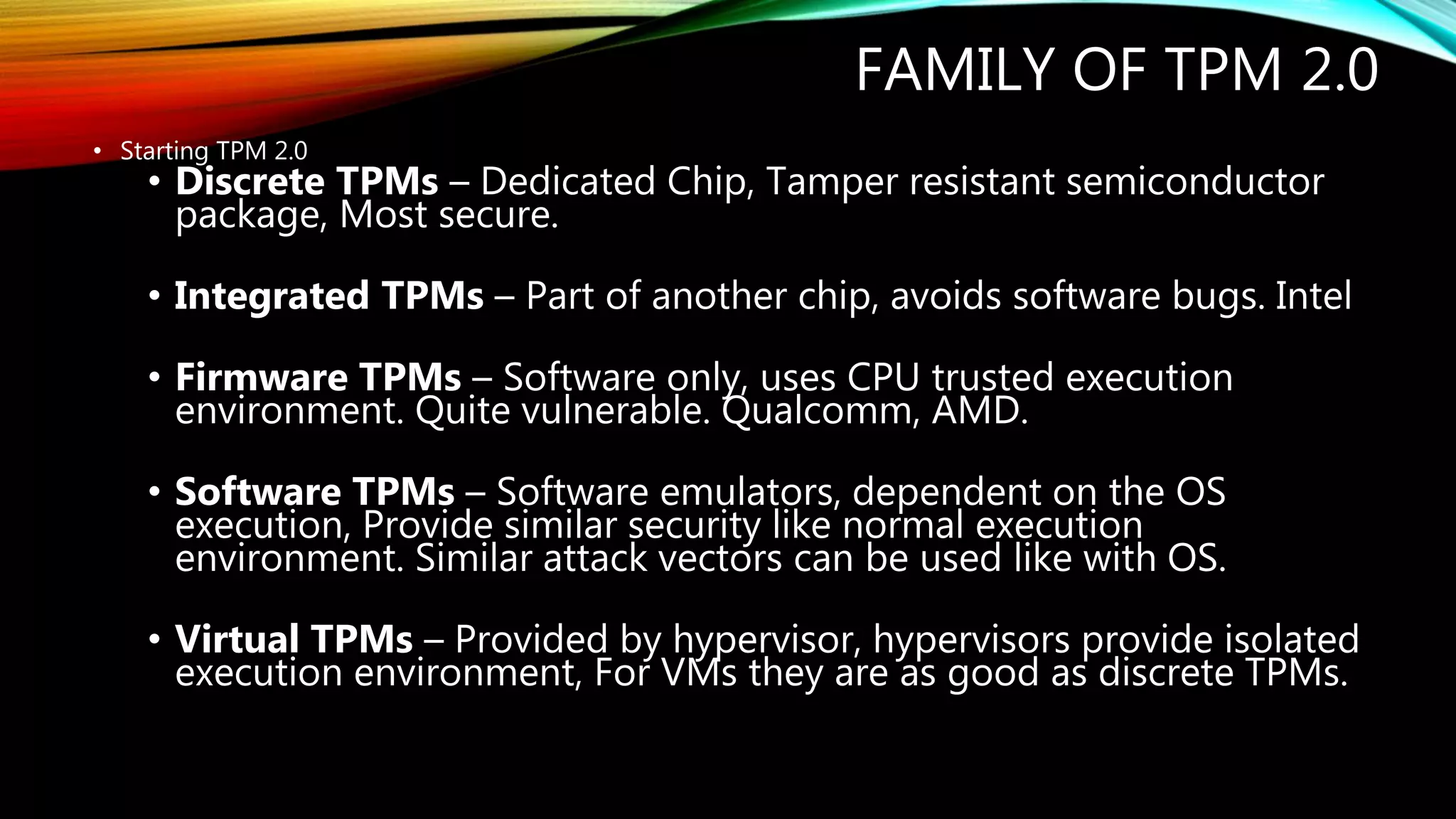
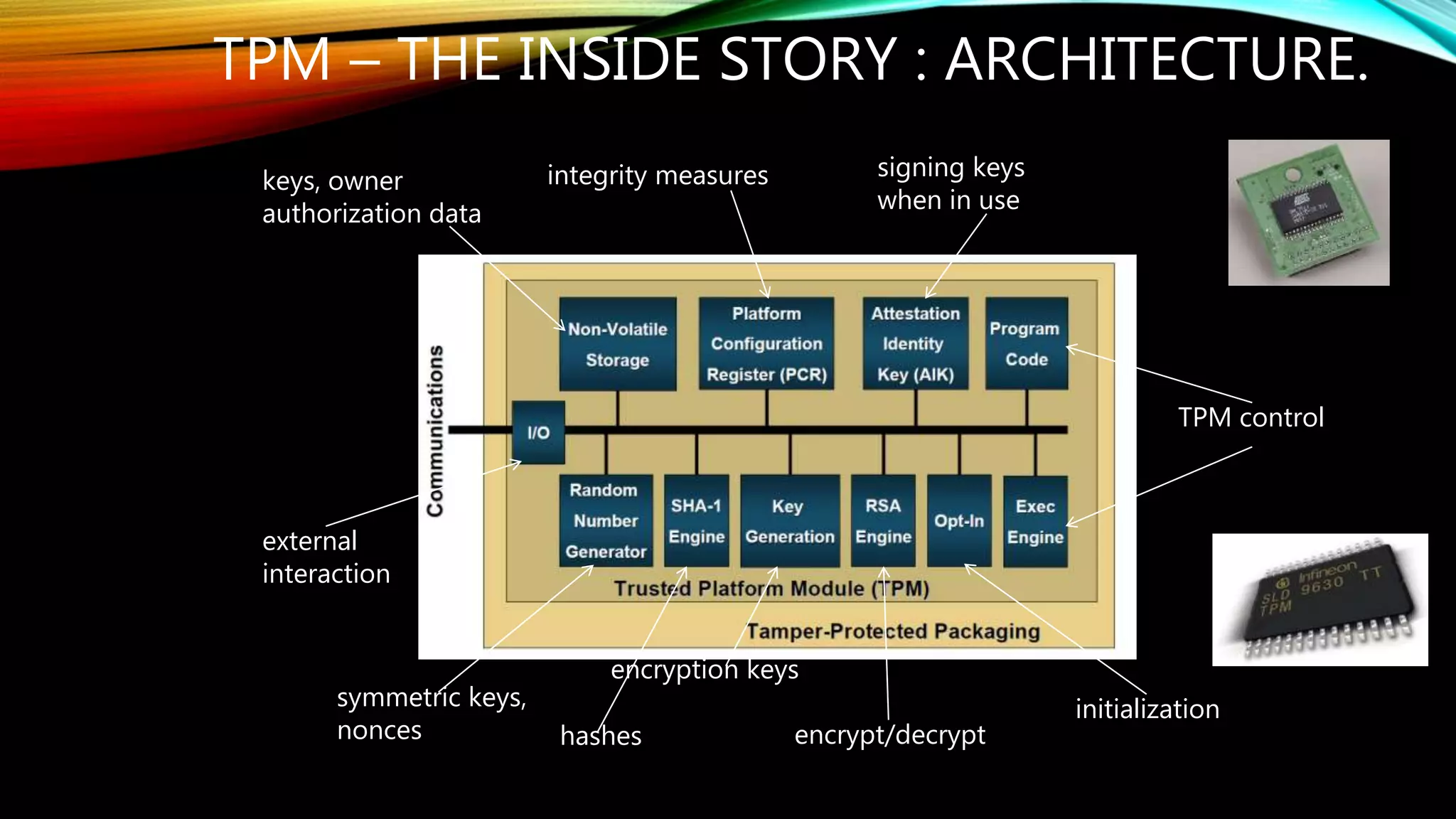
This document provides an overview of Trusted Platform Modules (TPM). It discusses the genesis of TPM, how TPM 1.2 evolved into TPM 2.0 with support for new cryptographic algorithms. It describes the different types of TPM implementations from discrete to software TPMs. The document also outlines some past attacks against TPMs including differential power analysis and extracting secrets. It provides a case study on reset attacks and concludes with the key industry players involved in developing TPM standards over time.