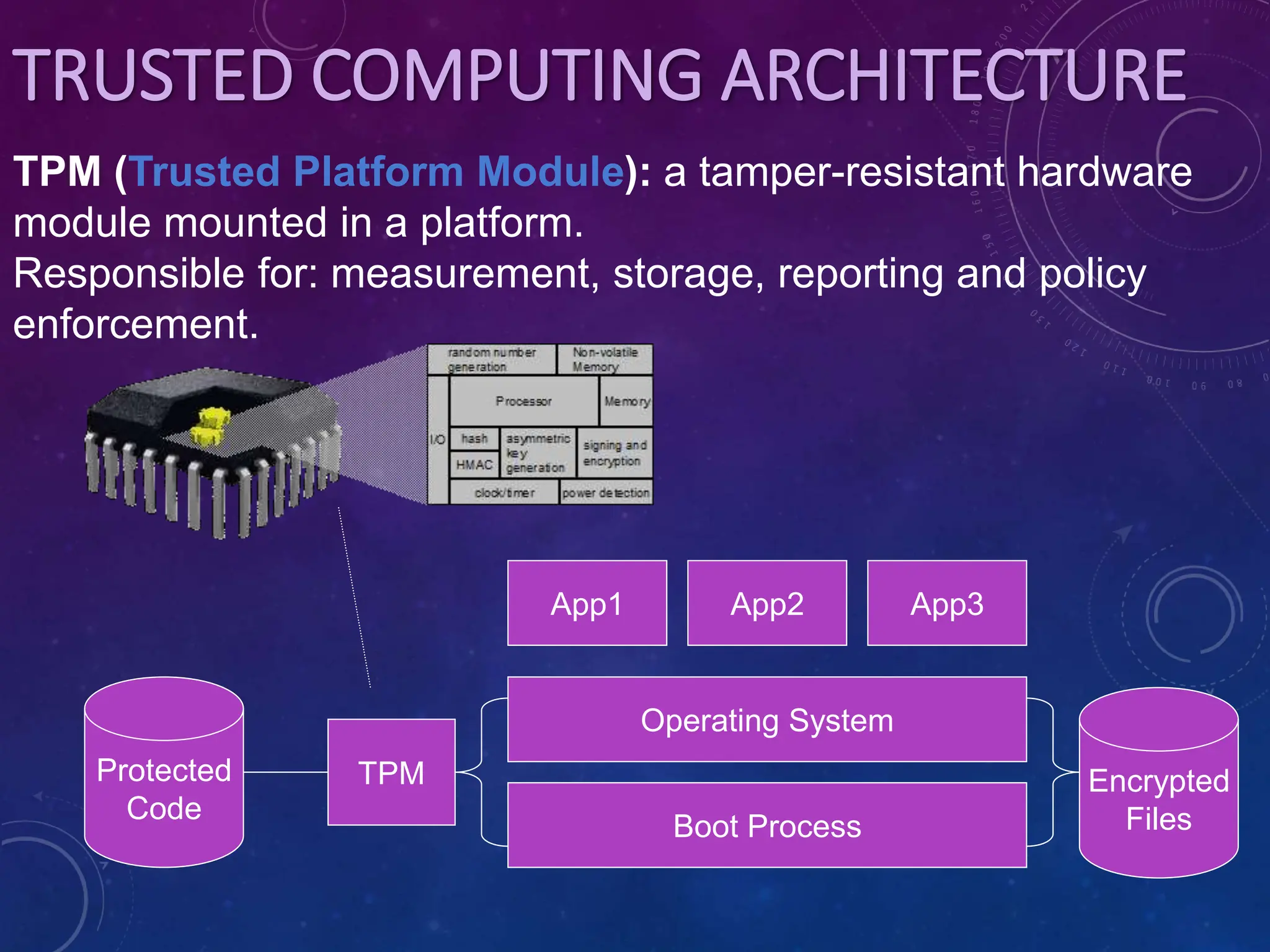
Trusted computing aims to increase security by adding a trusted computing module (TCM) hardware component. The TCM establishes a root of trust and measures the integrity of software during boot. It uses platform configuration registers to verify the system is in a trusted state through mechanisms like sealed storage, memory curtaining, and remote attestation which allows a system to prove its configuration to others. The technology is based on standards from the Trusted Computing Group and aims to address weaknesses of relying solely on software for security.