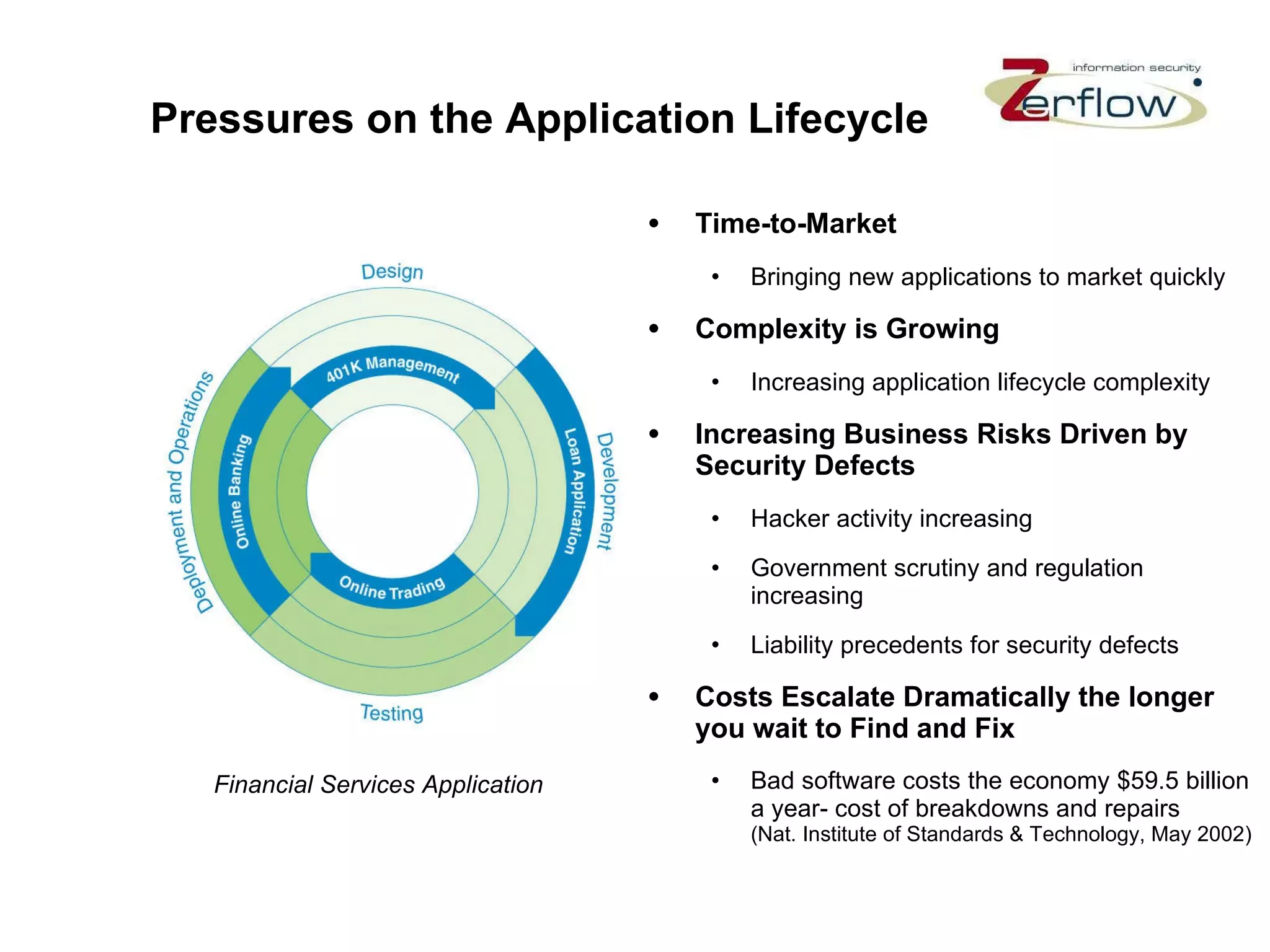
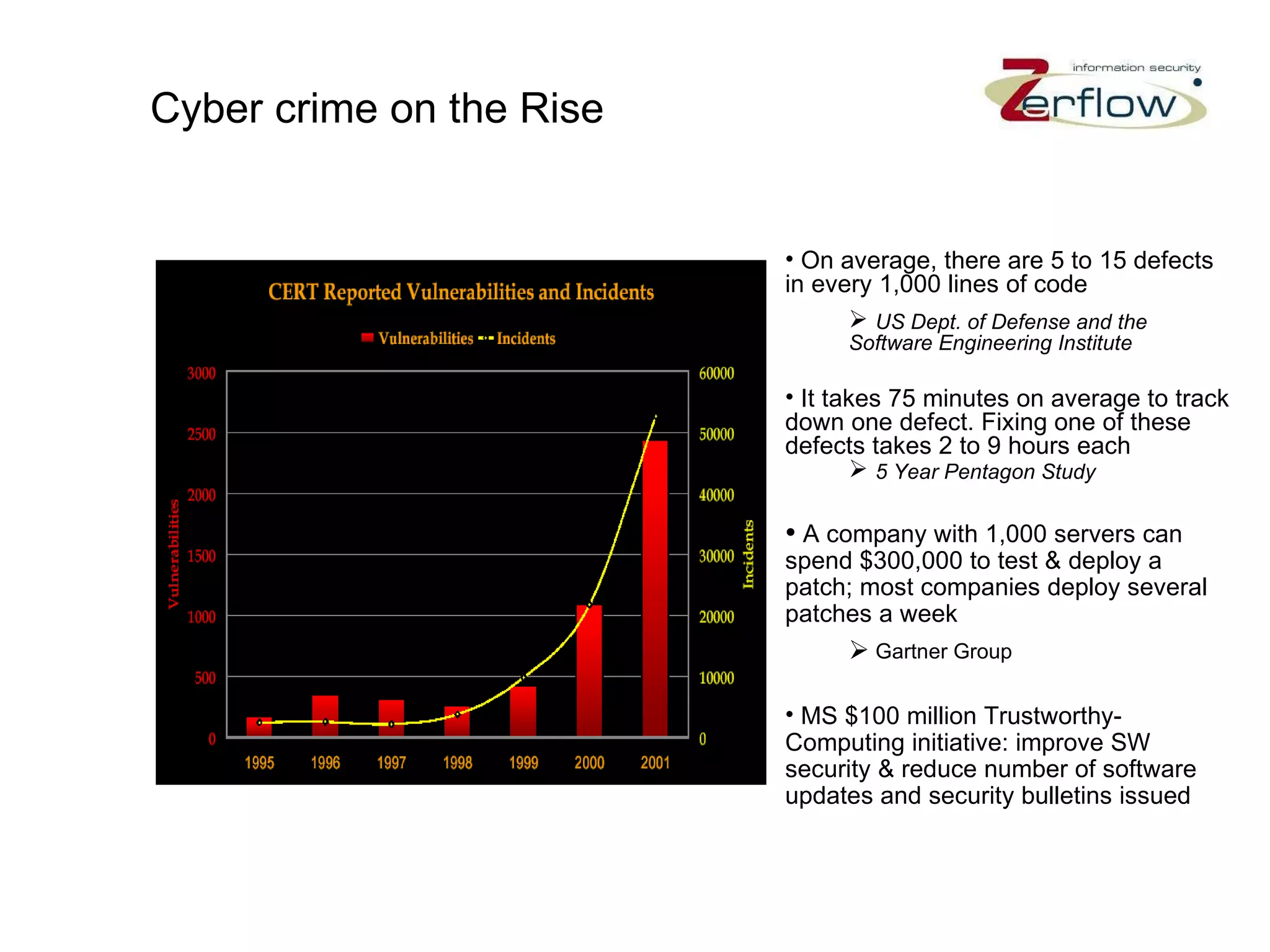
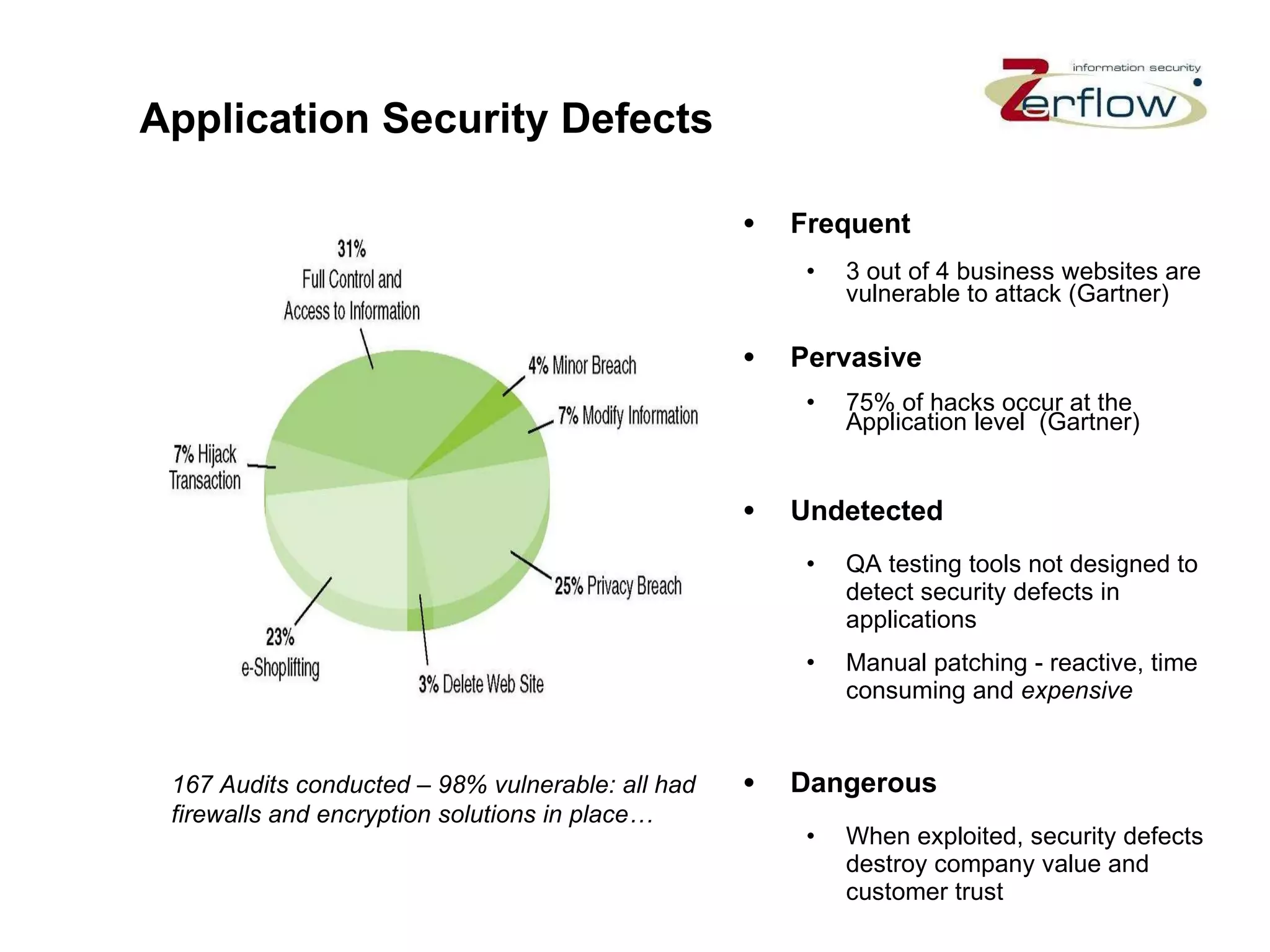
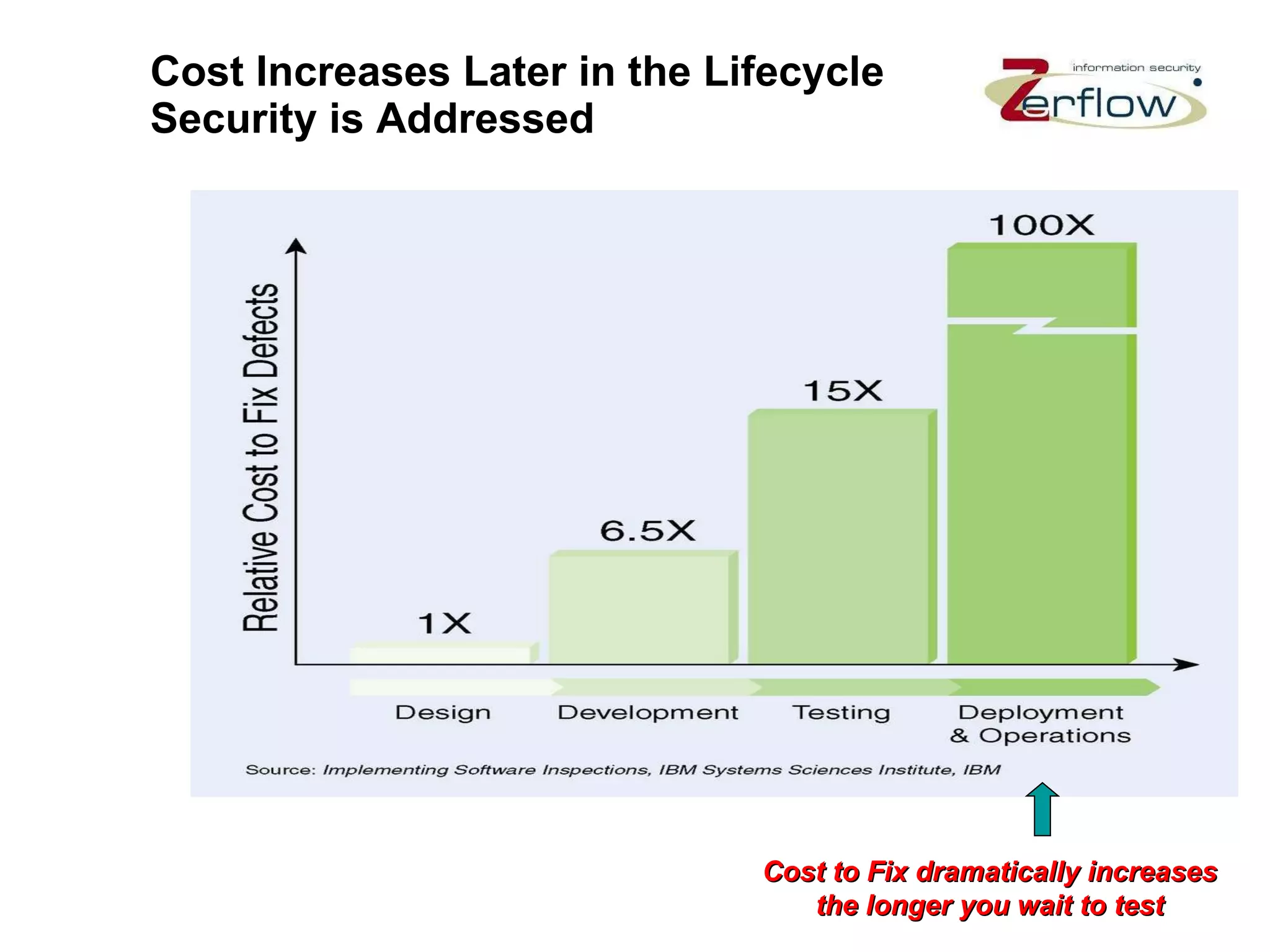
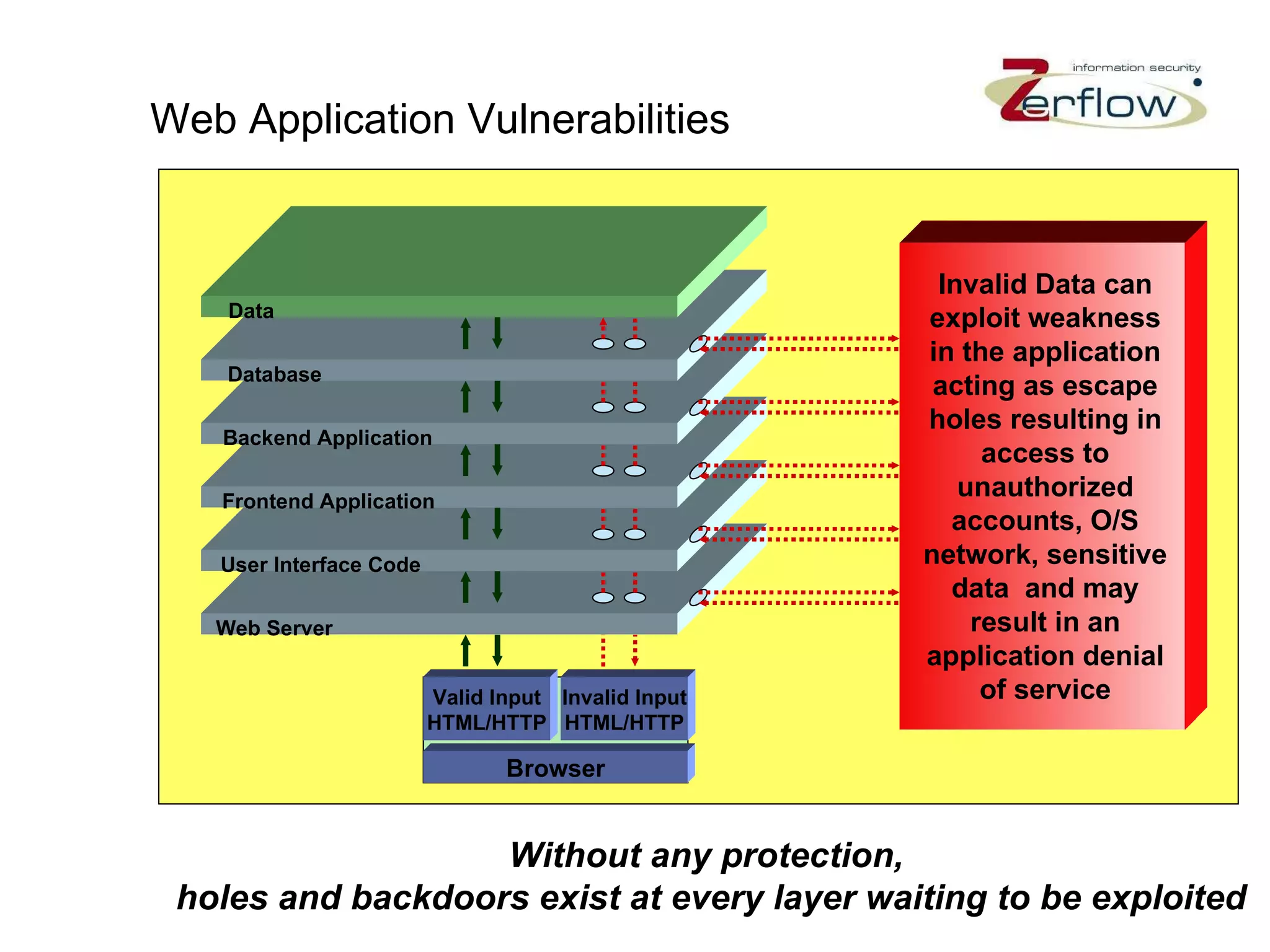
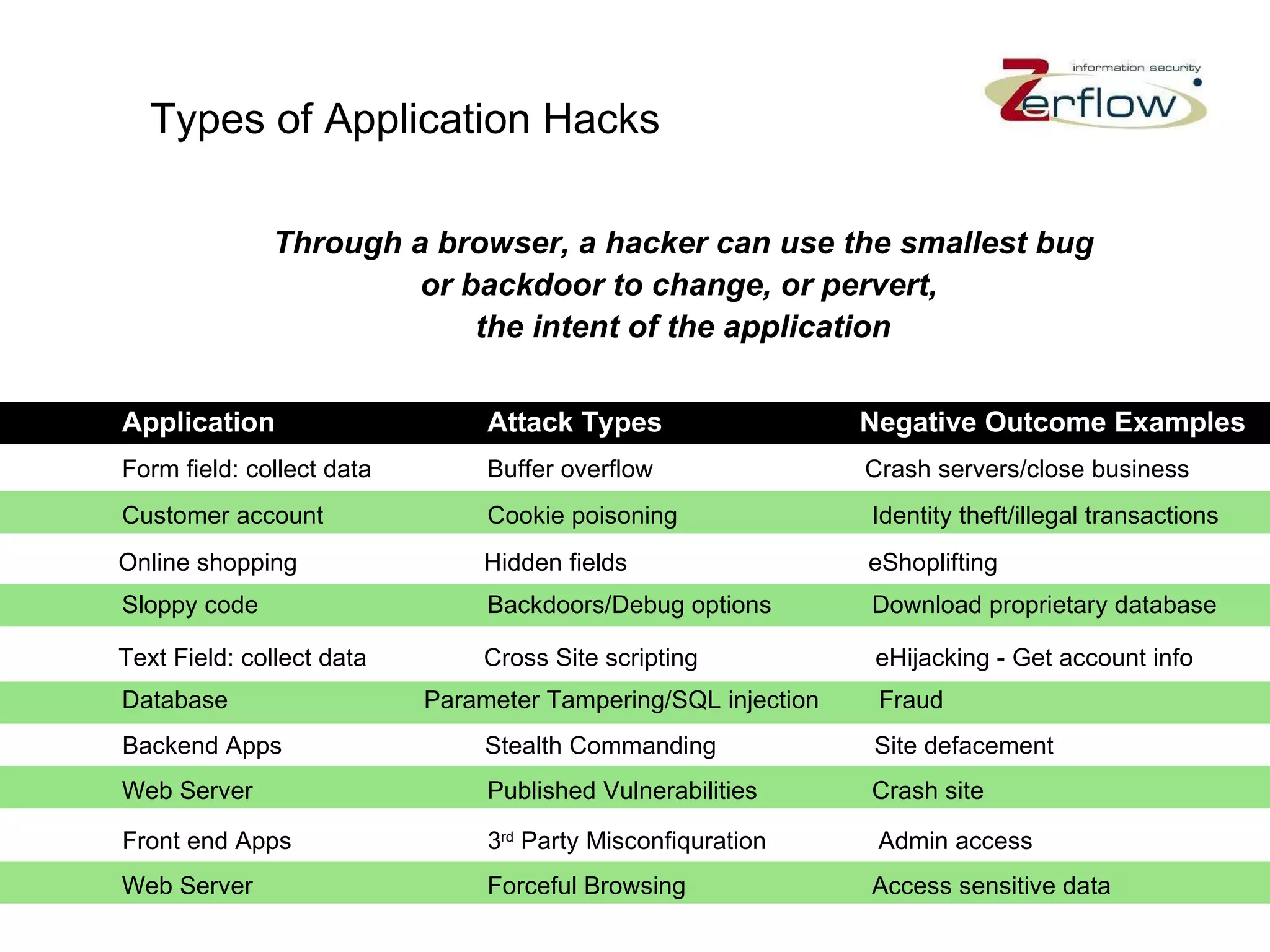
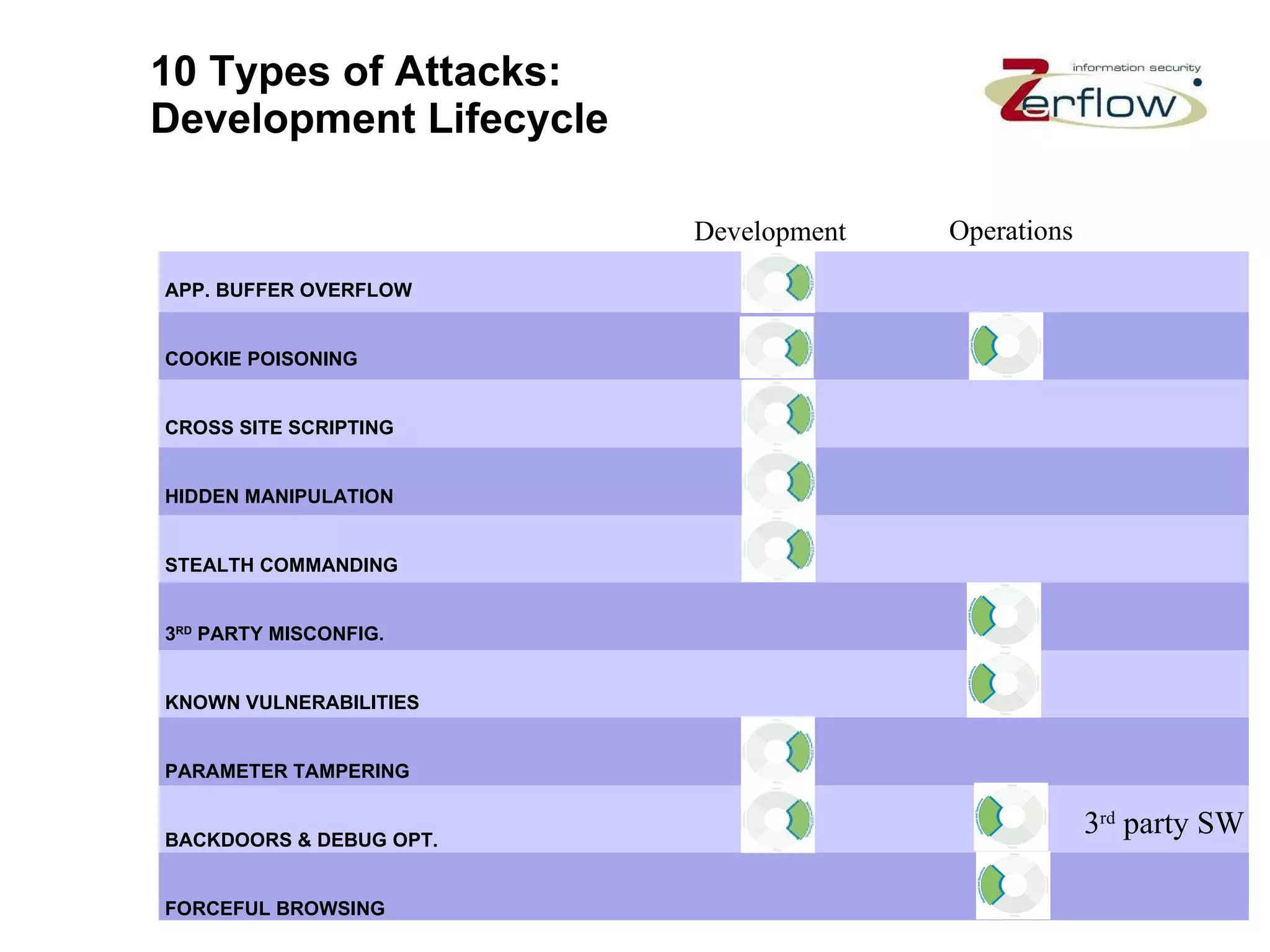
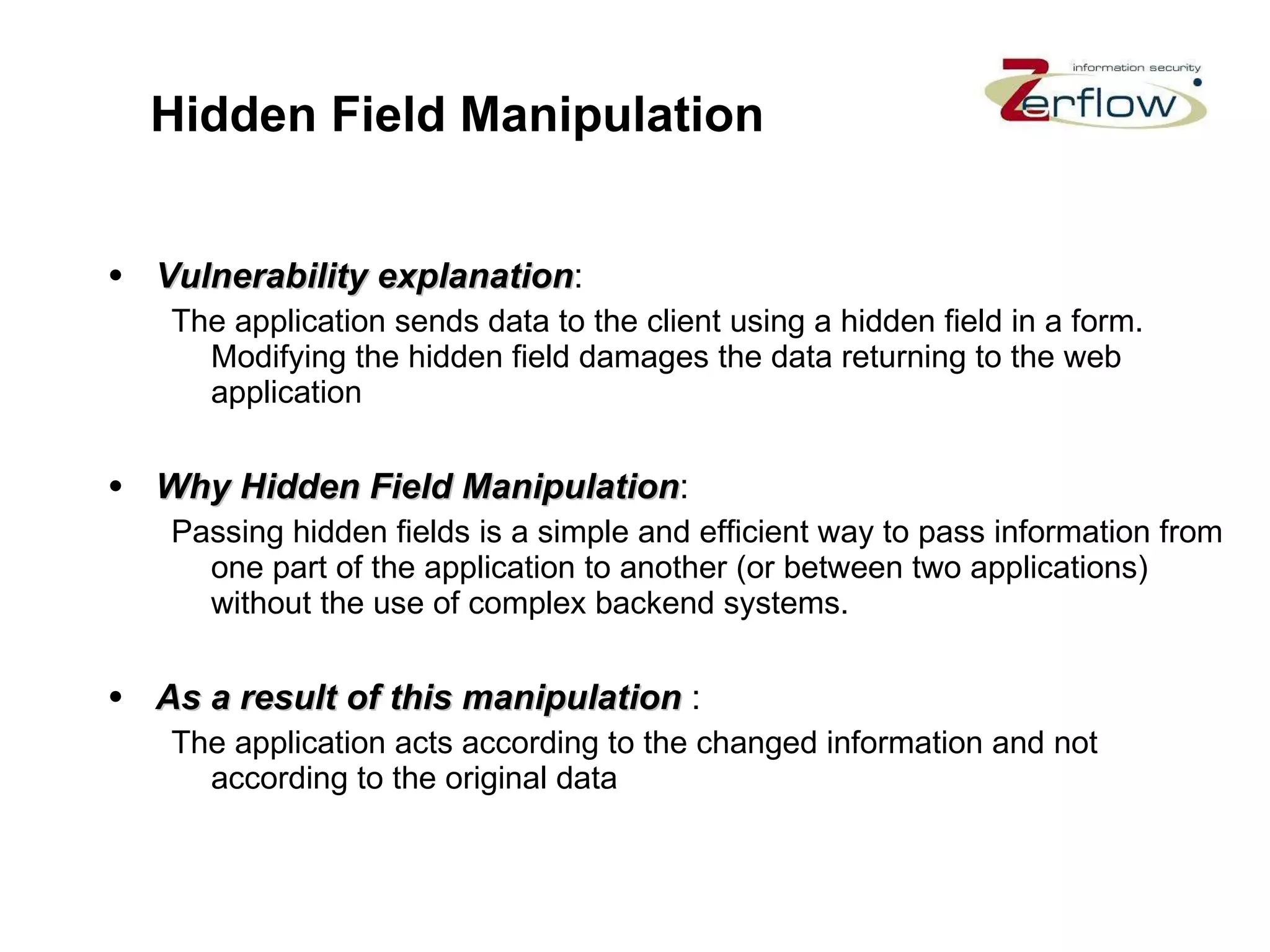
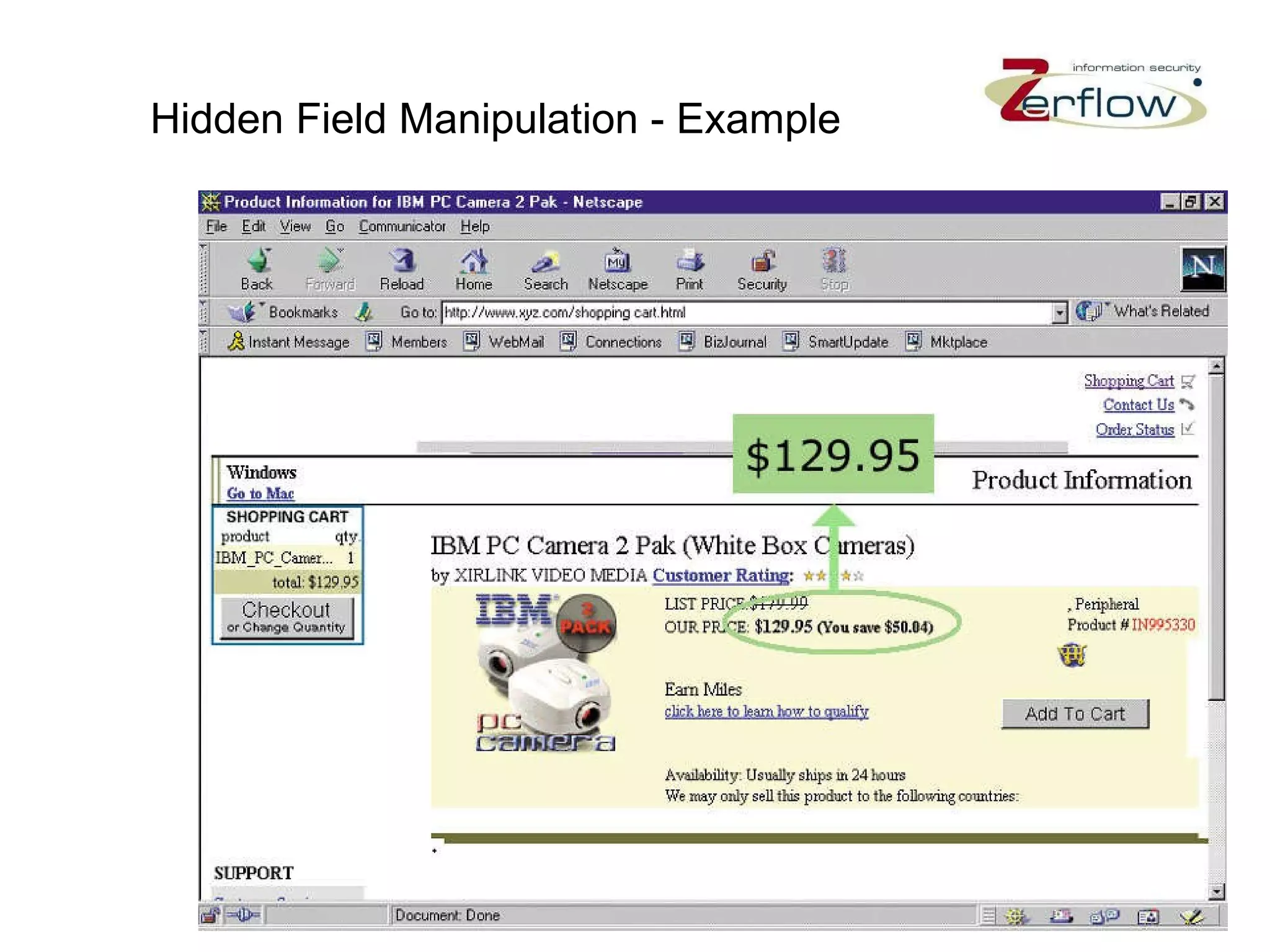
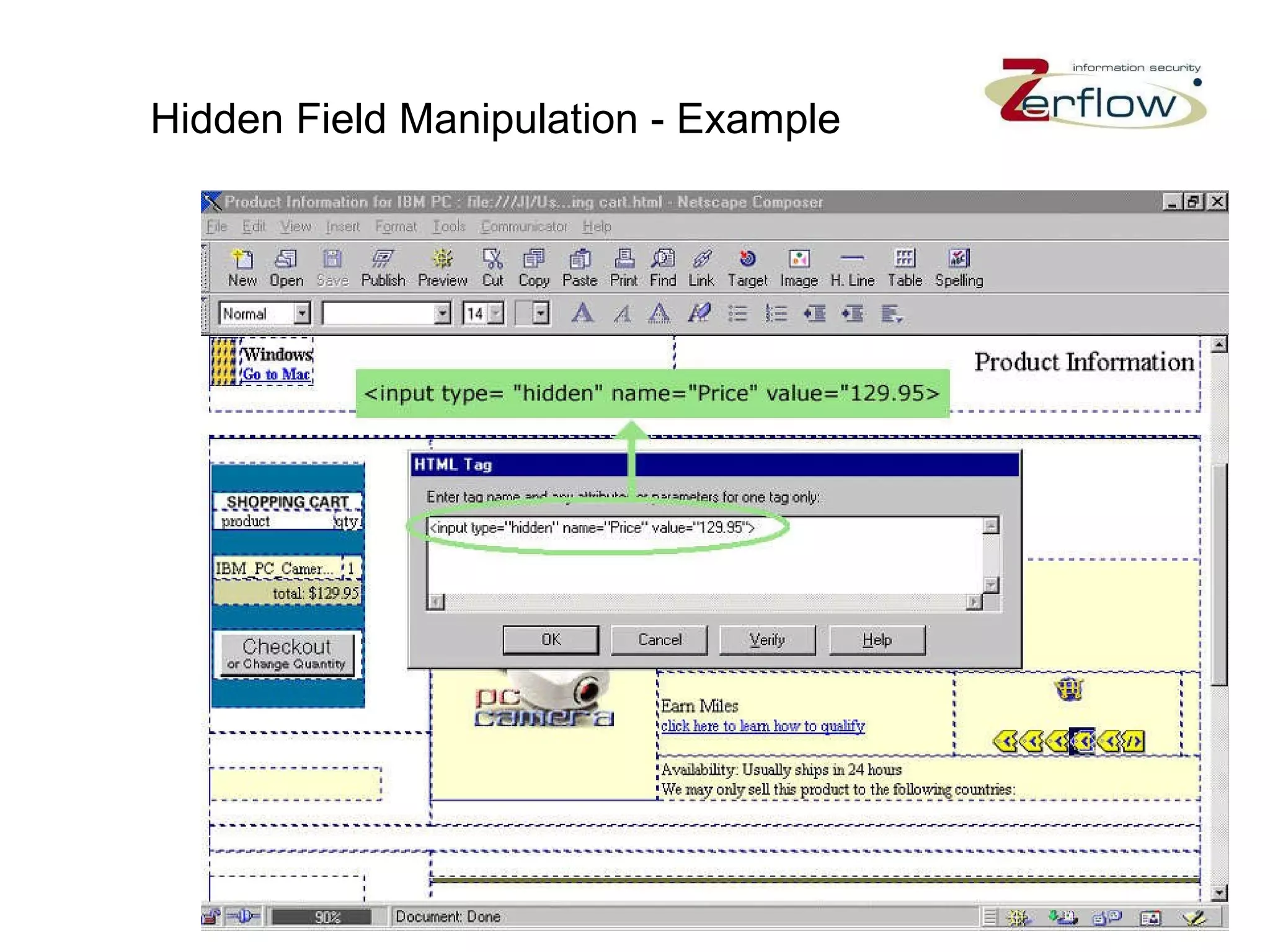
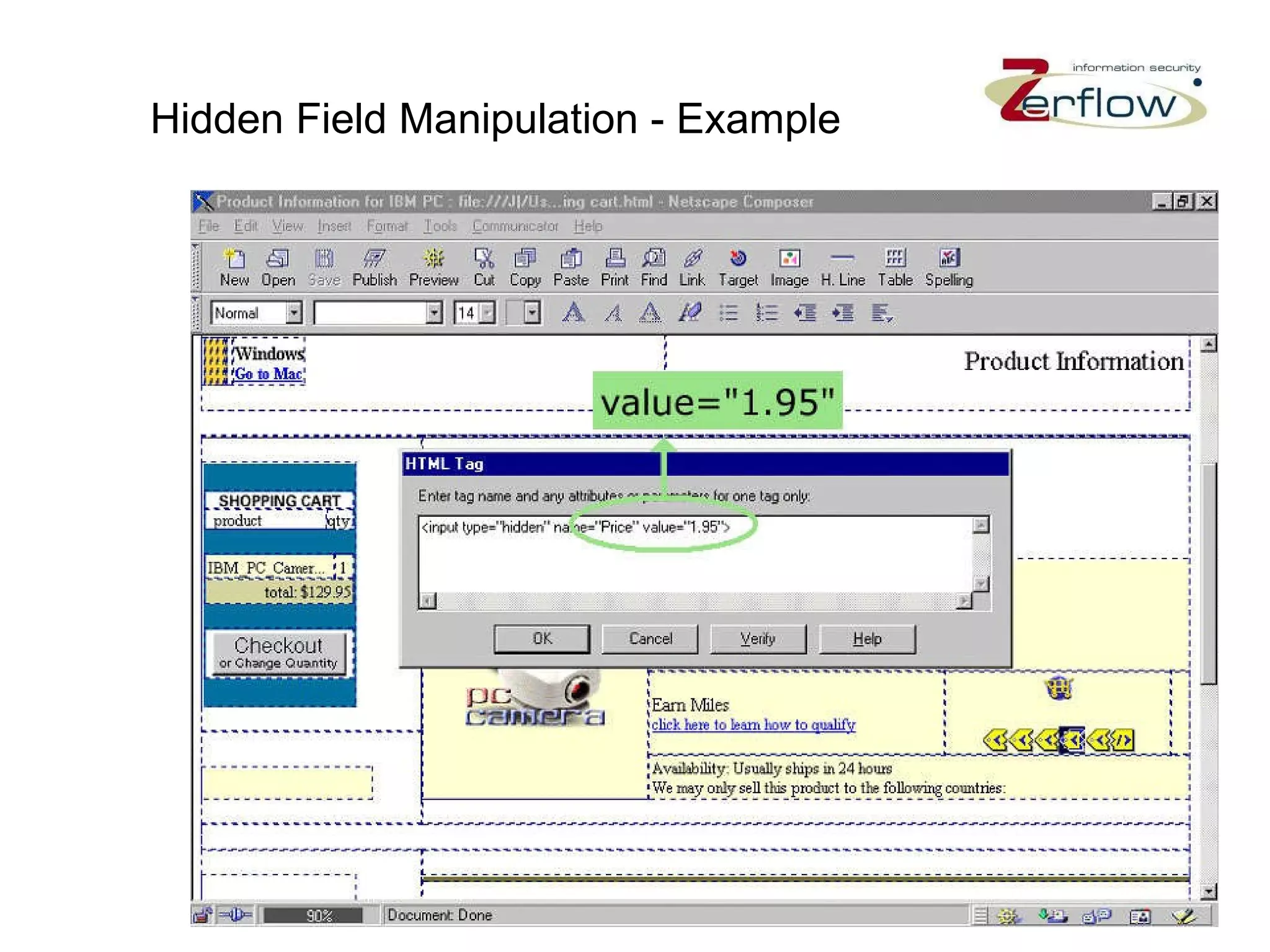
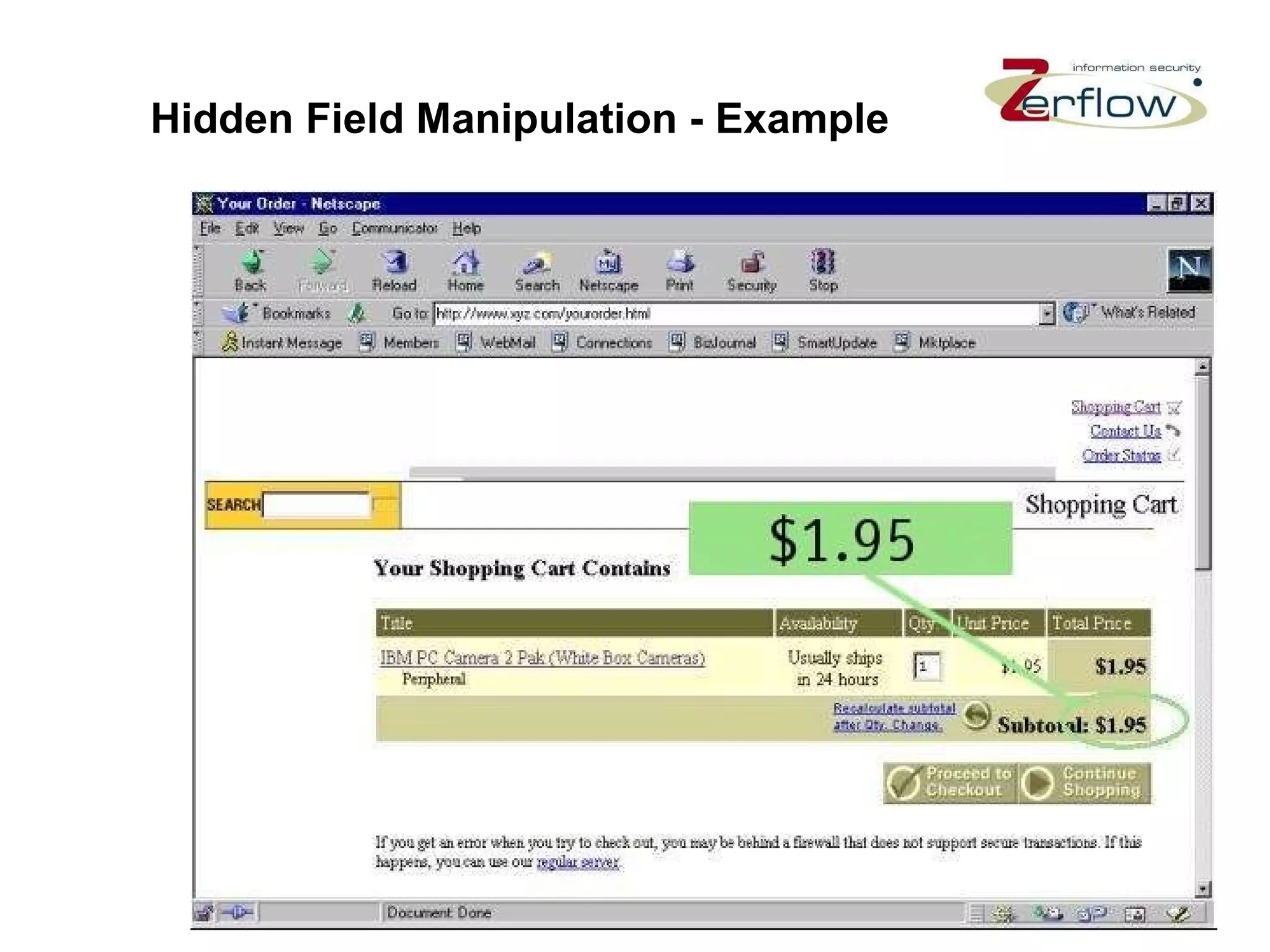
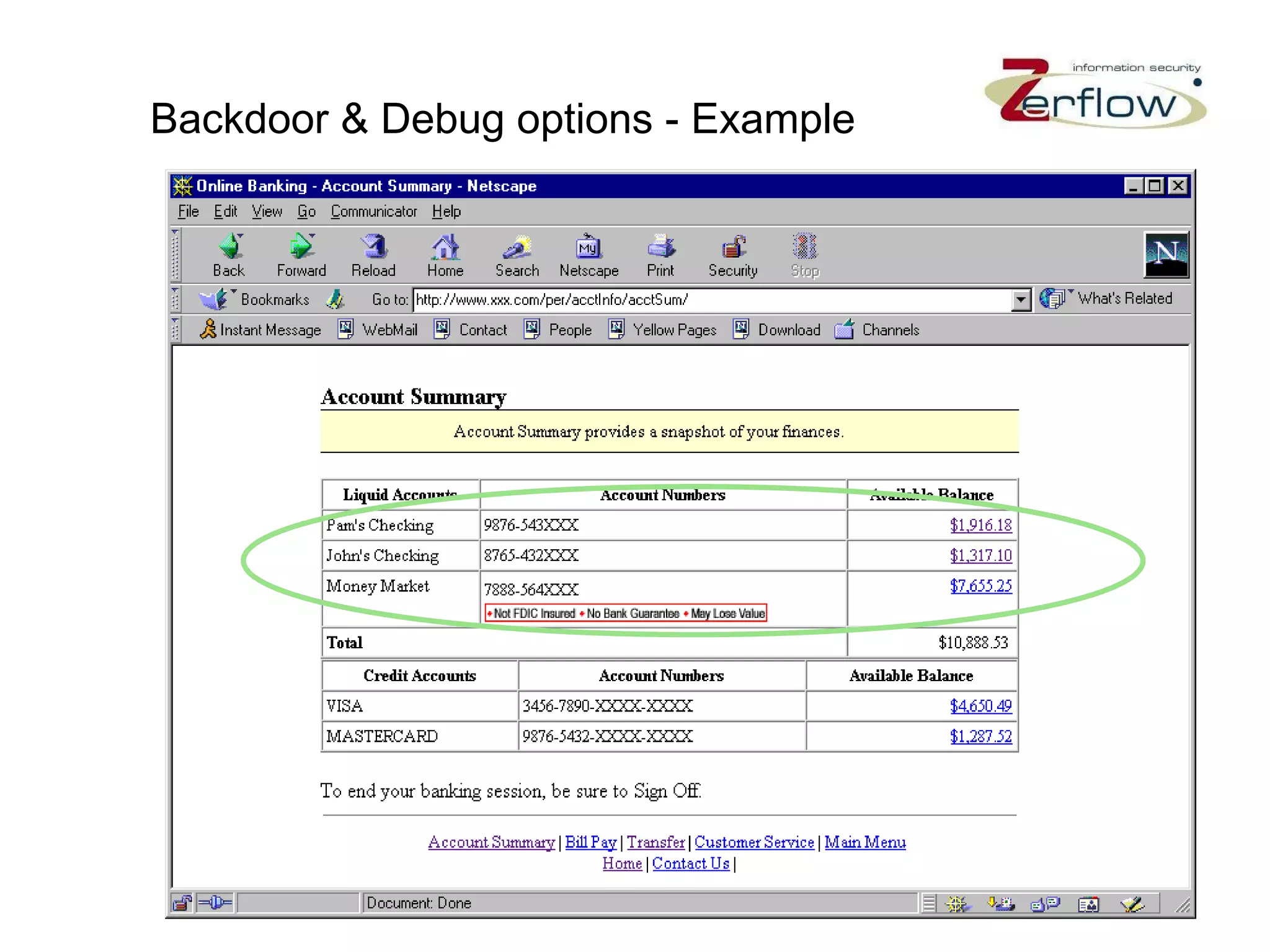
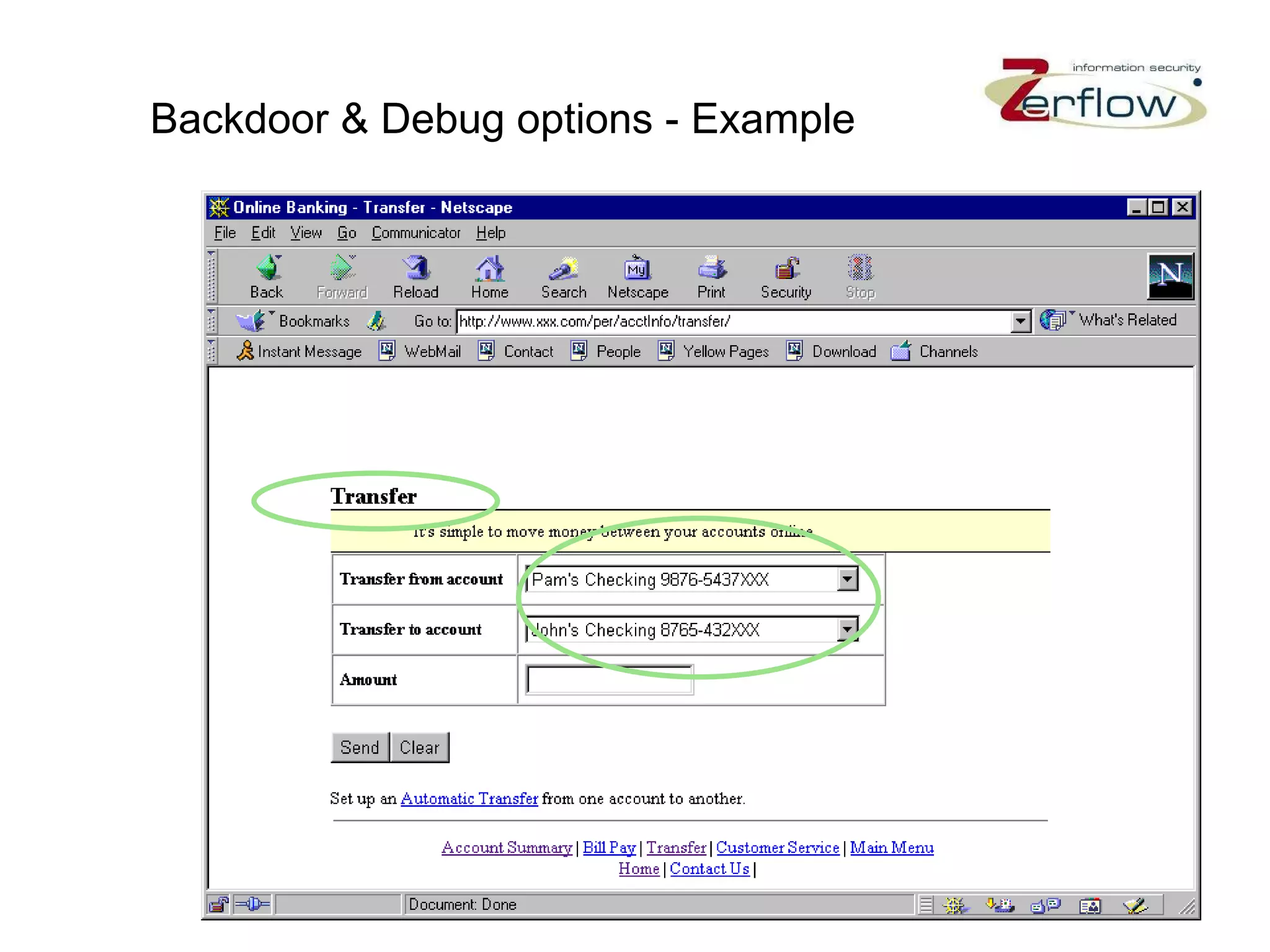
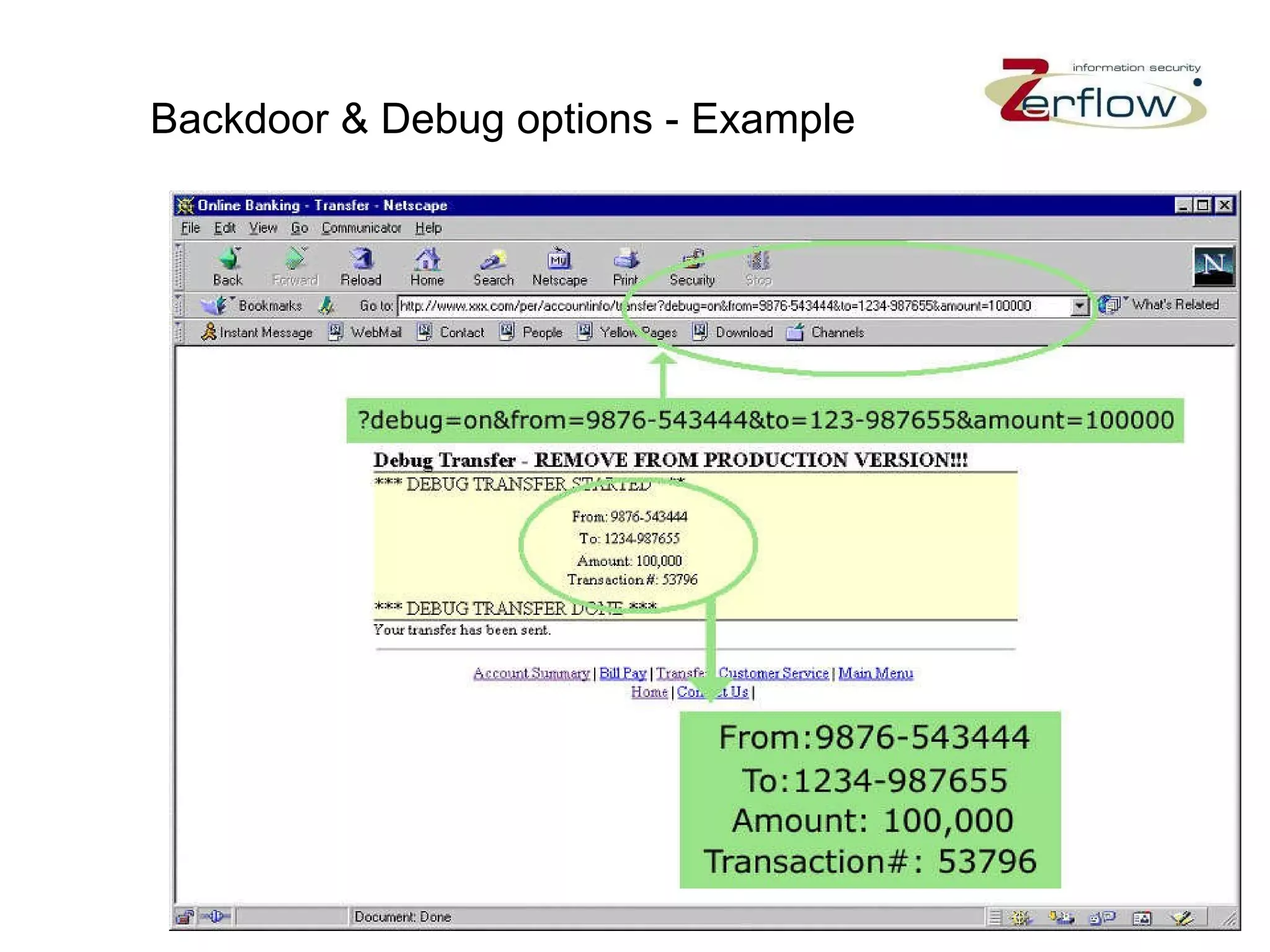
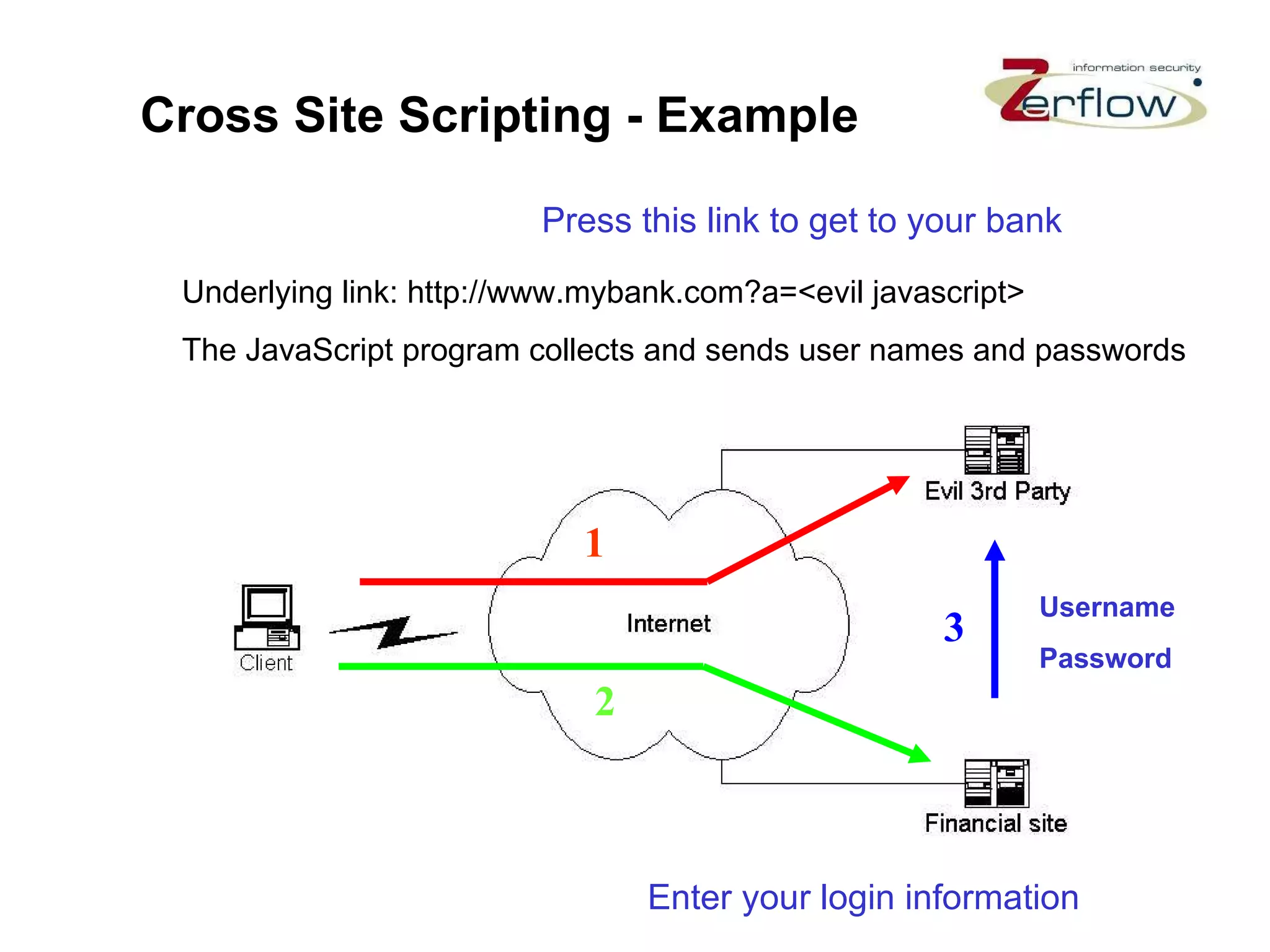
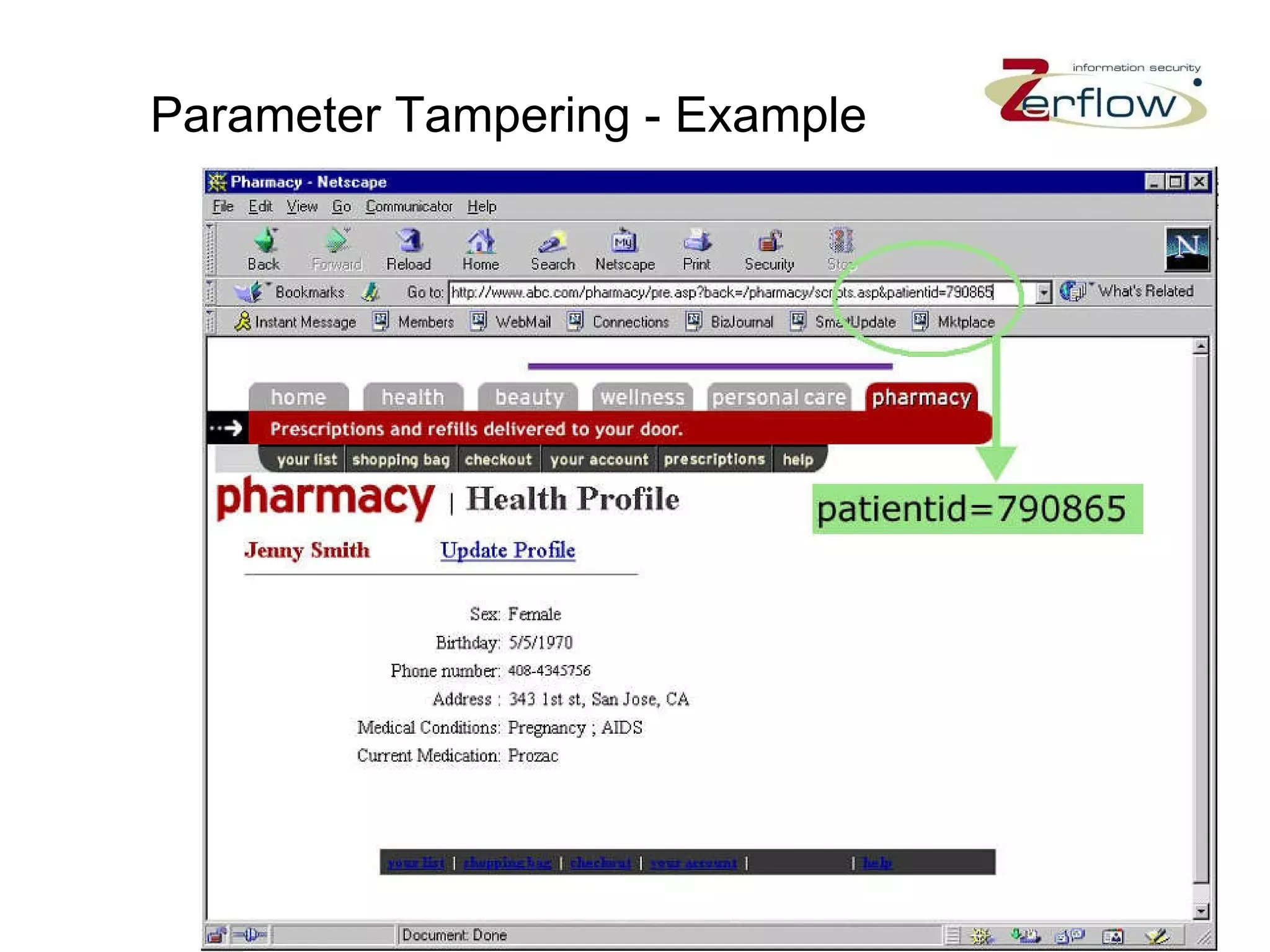
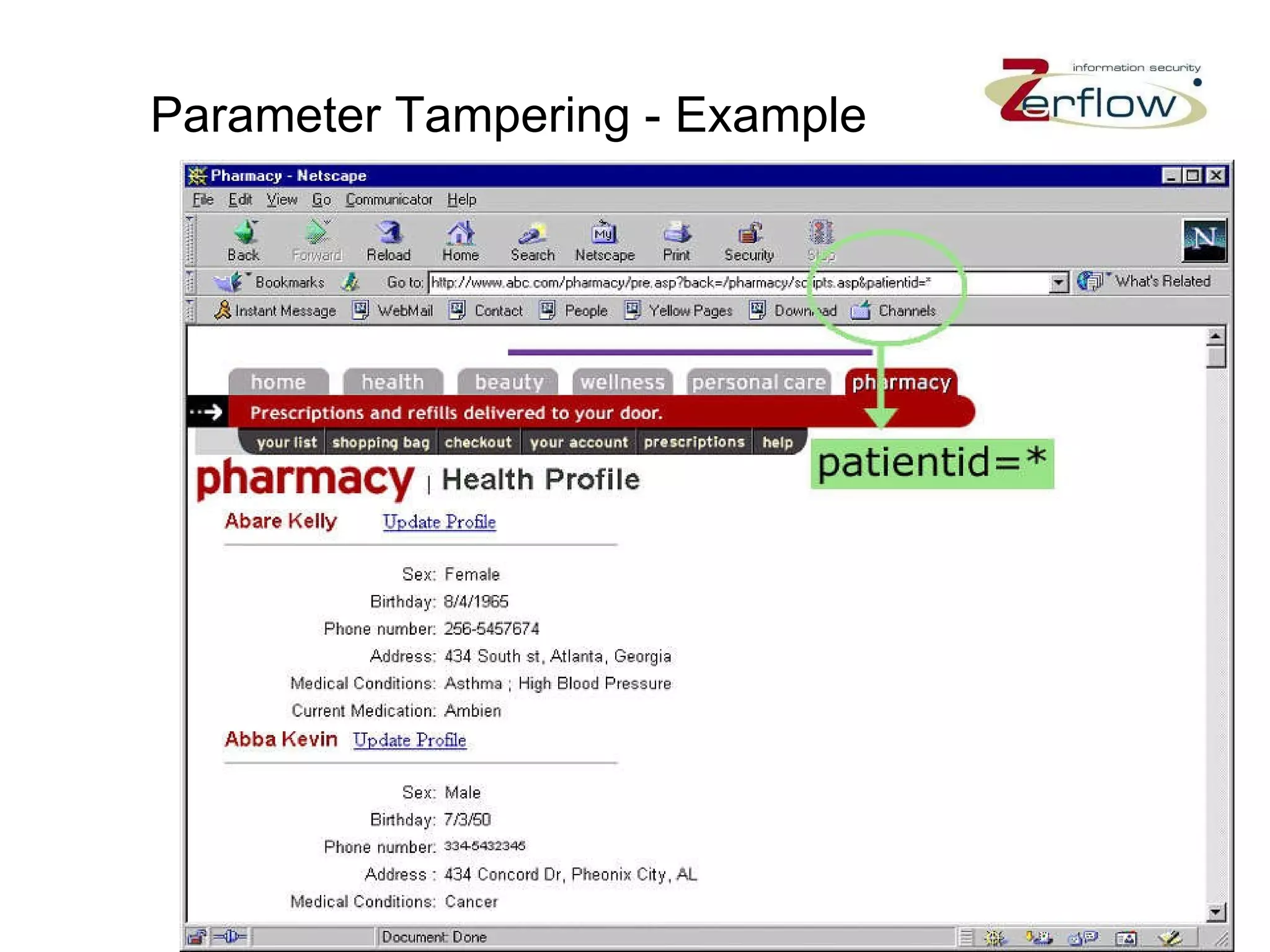
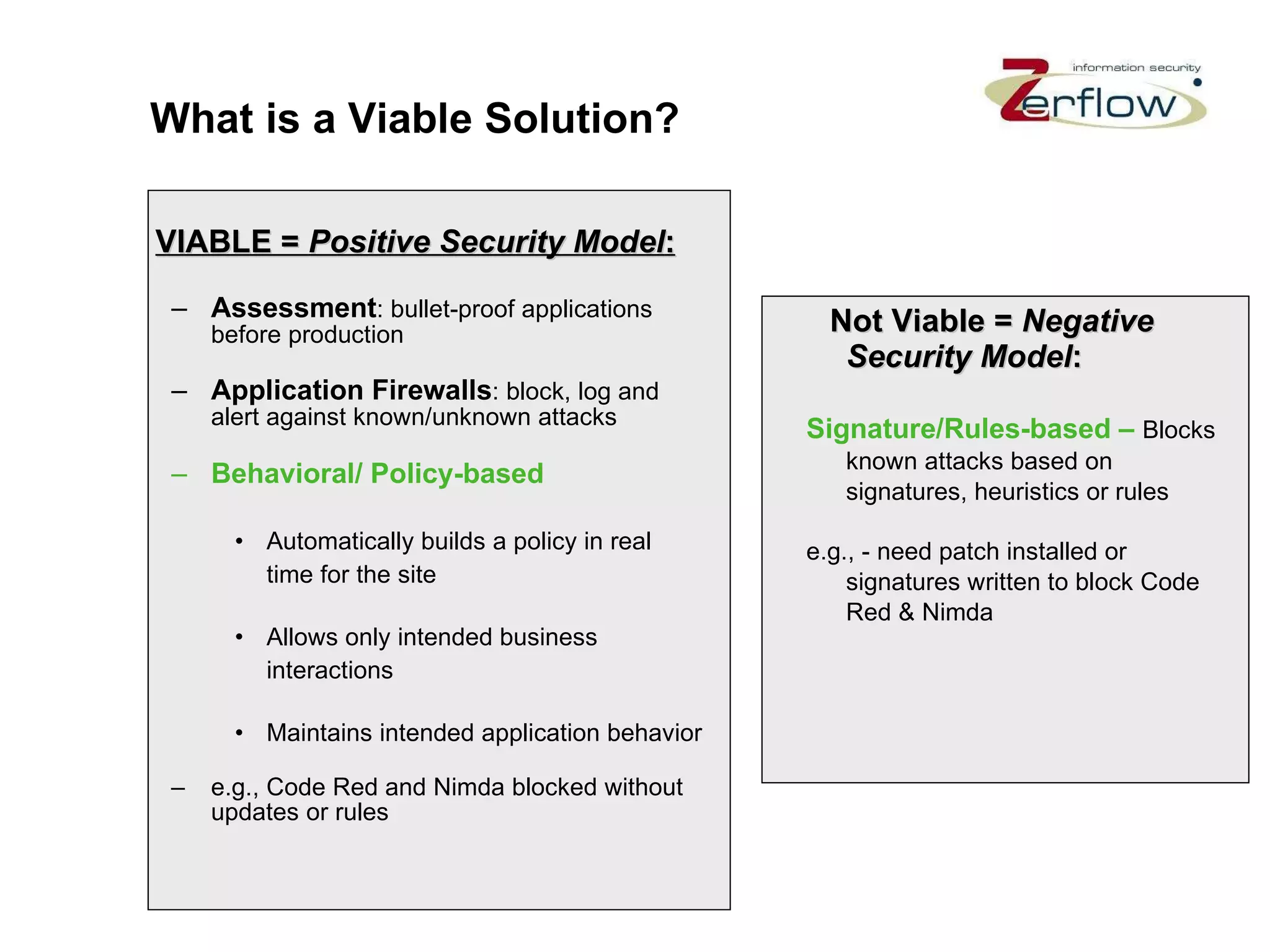
The document discusses web application security vulnerabilities and provides examples of common attacks like hidden field manipulation, backdoors and debug options, cross-site scripting, and parameter tampering. It notes that application security defects are frequent, pervasive, and often go undetected. Later in the lifecycle, vulnerabilities become much more costly to fix. The document advocates for positive security models like application firewalls that can automatically learn and enforce intended application behavior to block both known and unknown attacks.