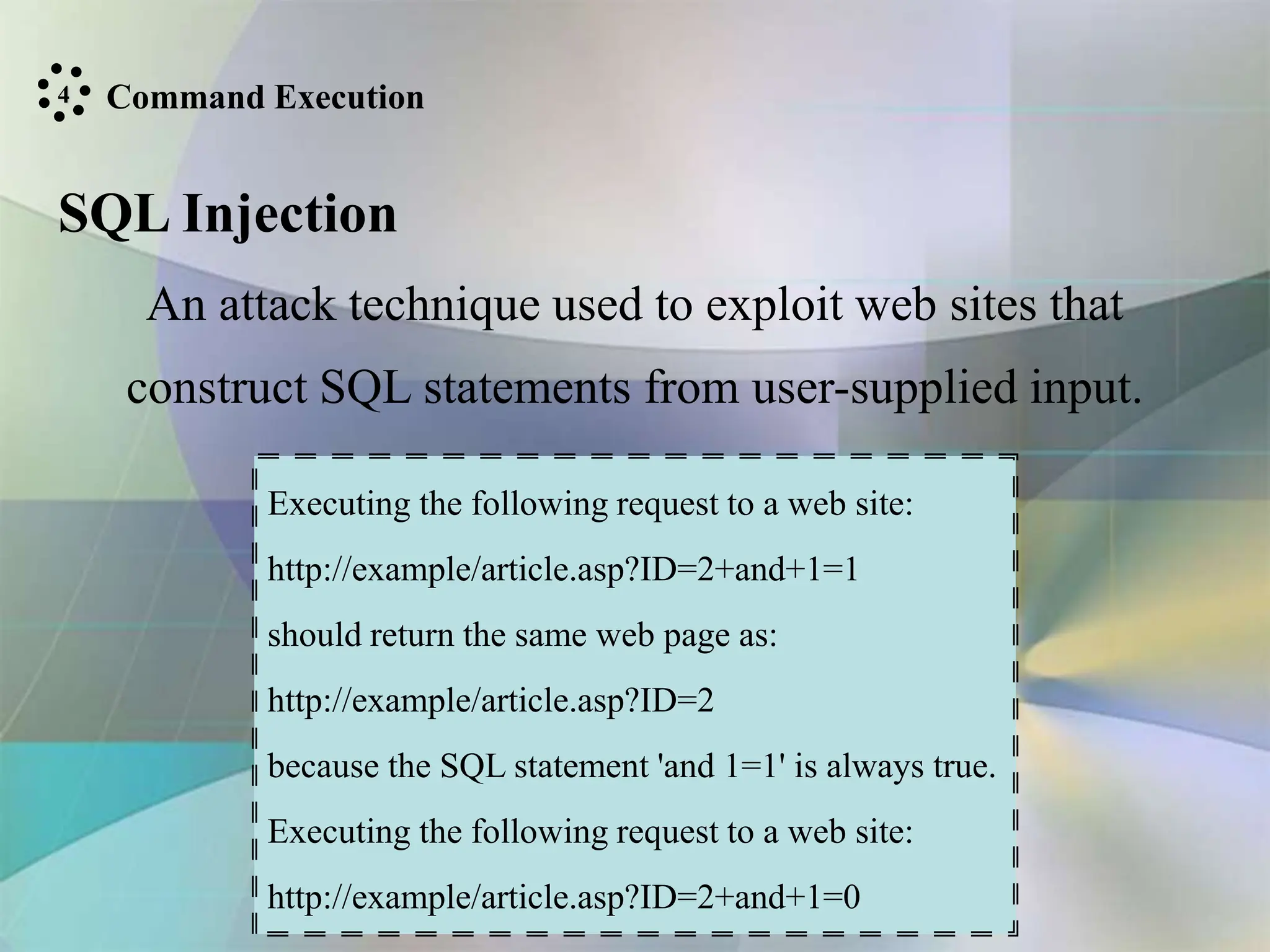
This document provides an overview of web security, defining key terms like the world wide web (WWW), web servers, and web browsers. It discusses web security from the perspectives of users and servers, explaining they expect secure and private communications. The document outlines common web site attacks like threats to information integrity and confidentiality from modification or eavesdropping. It also covers attacks on web site accessibility through denial of service and on authentication through impersonation. Finally, it categorizes some classes of attacks on authentication, authorization, clients, and command execution like SQL injection and cross-site scripting.