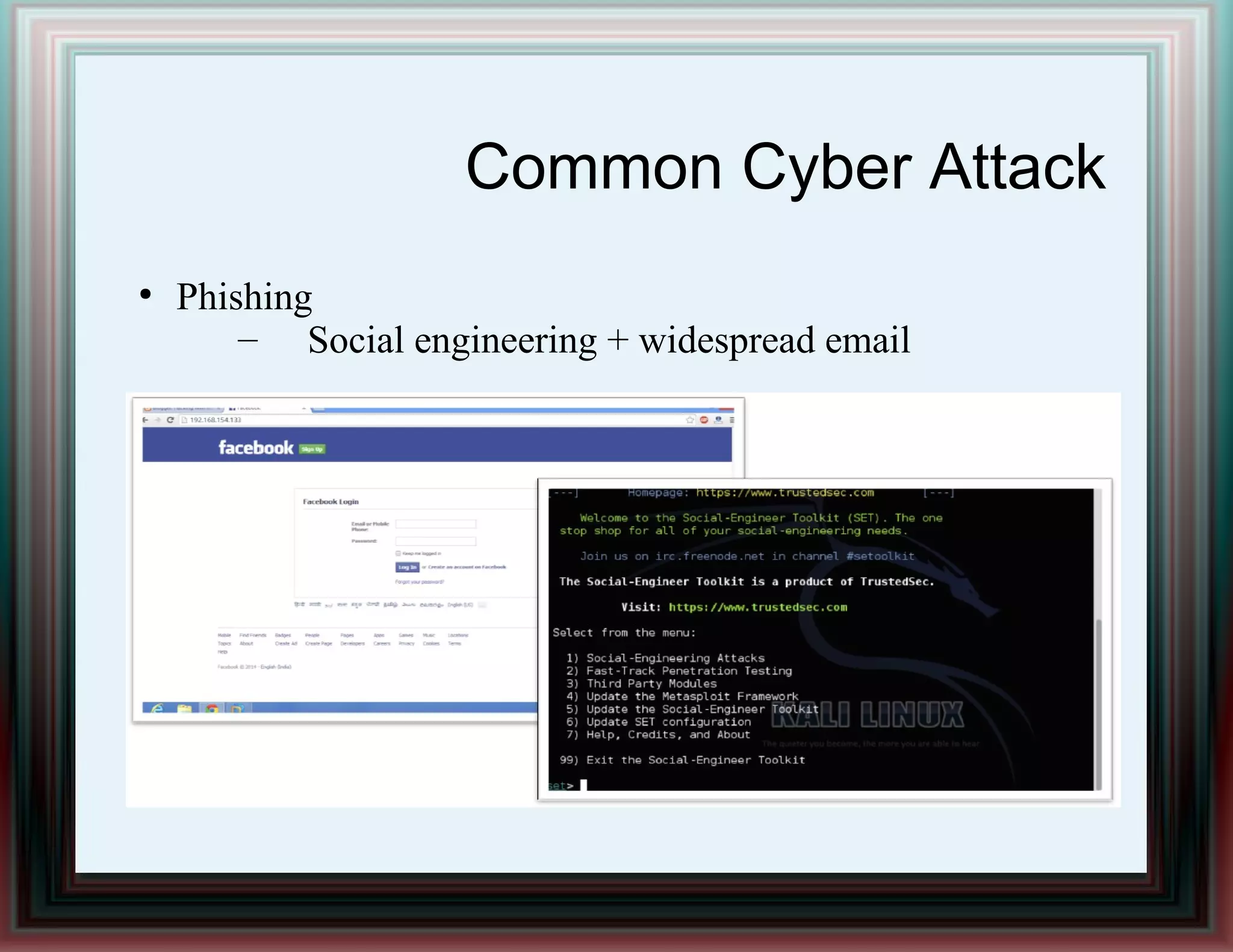
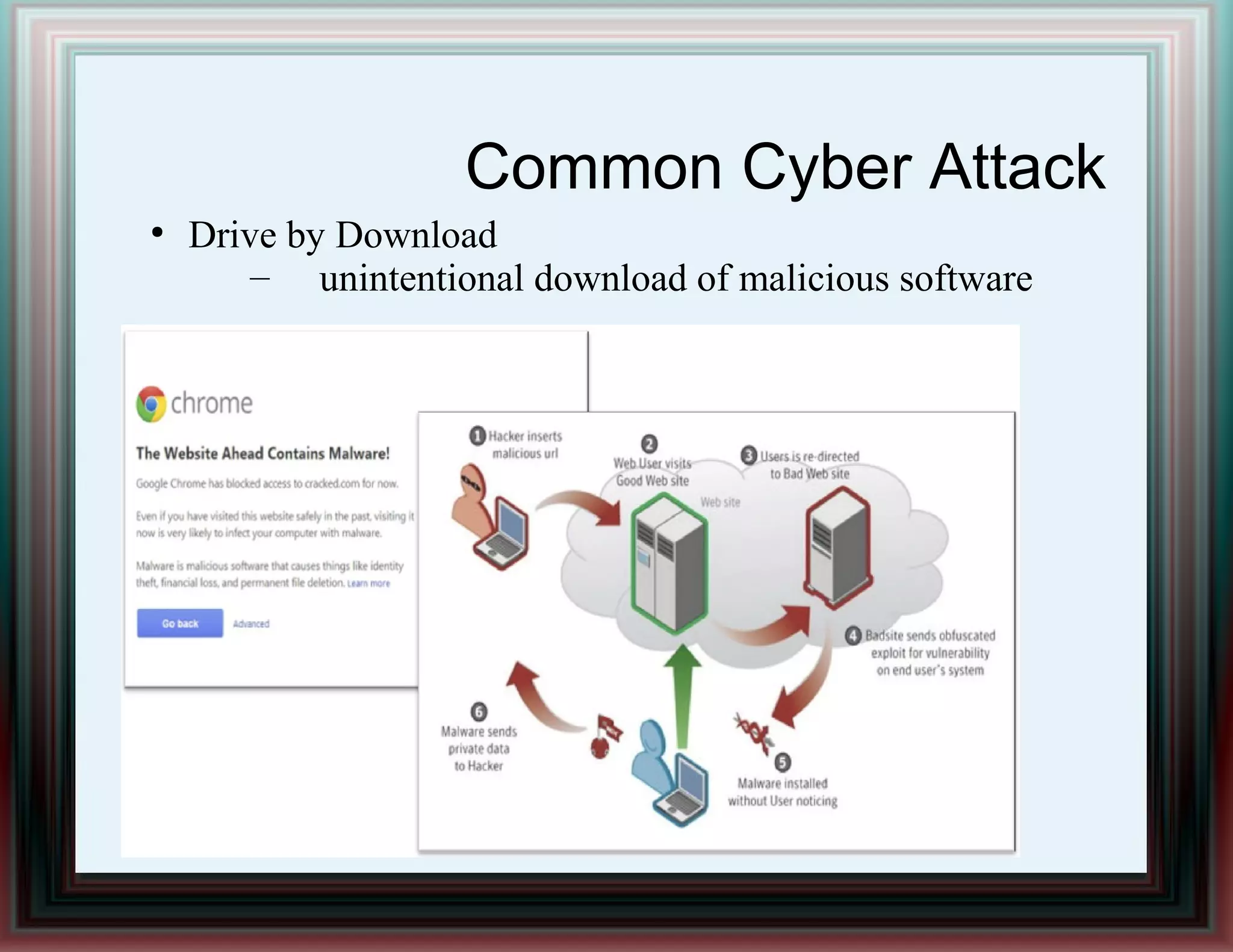
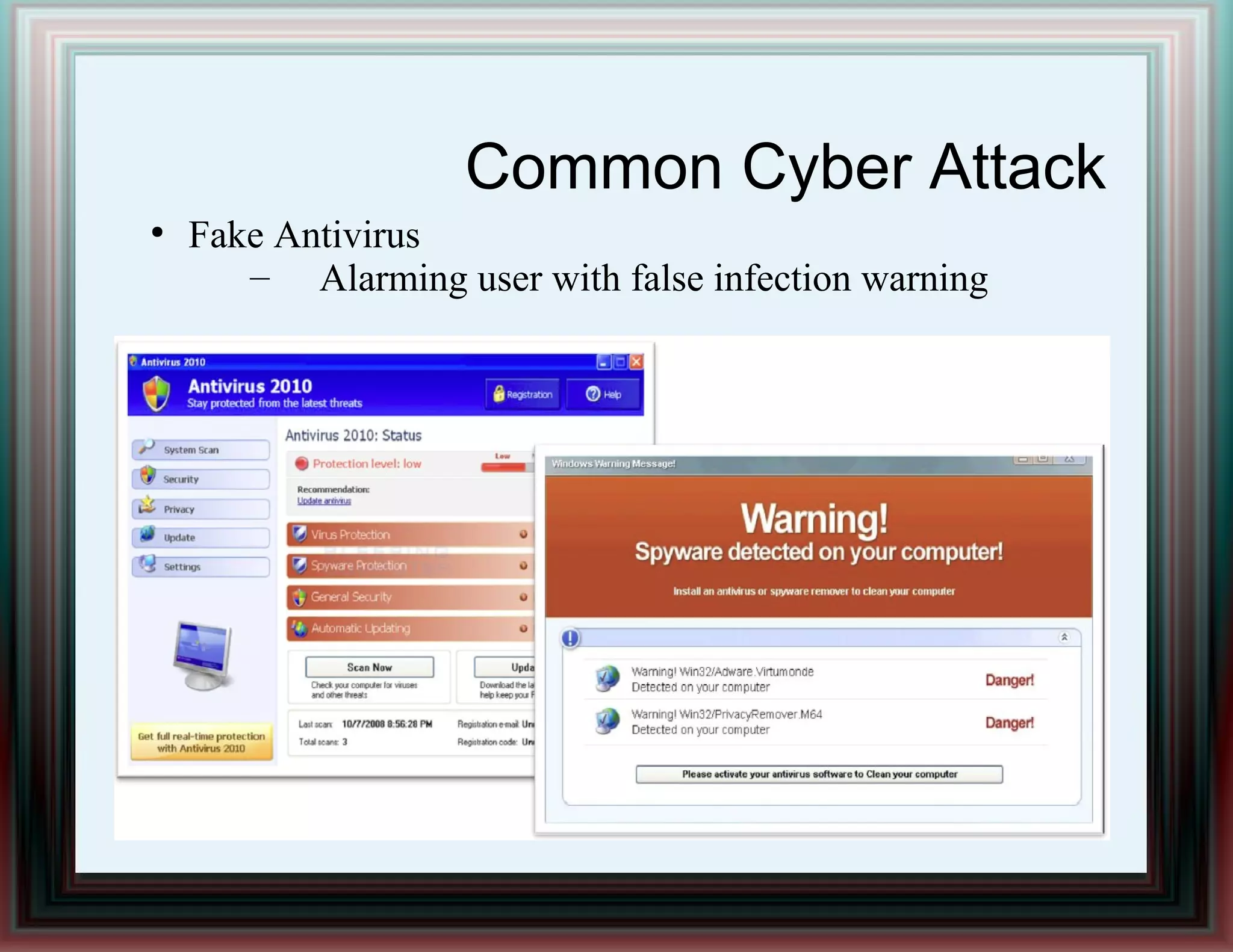
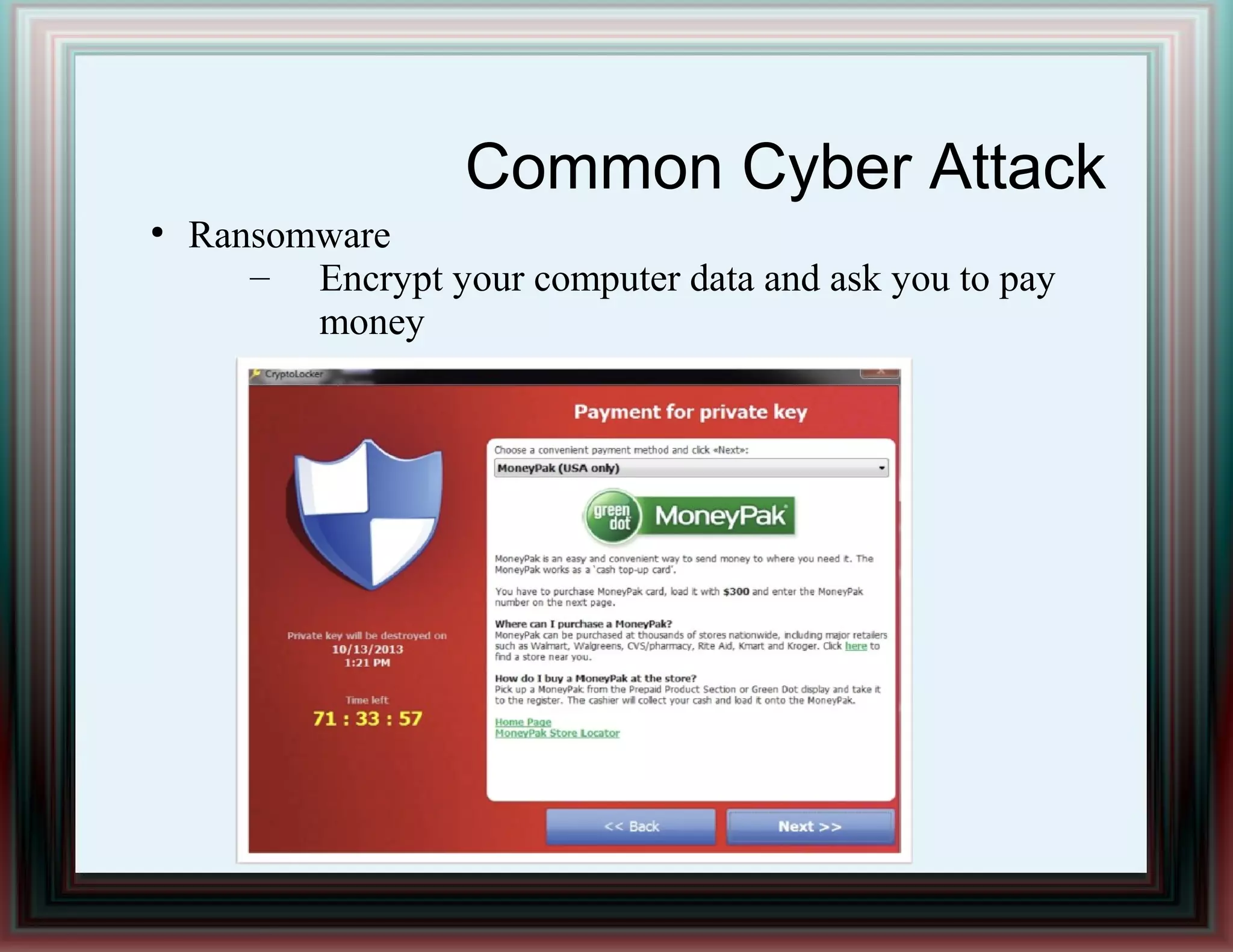
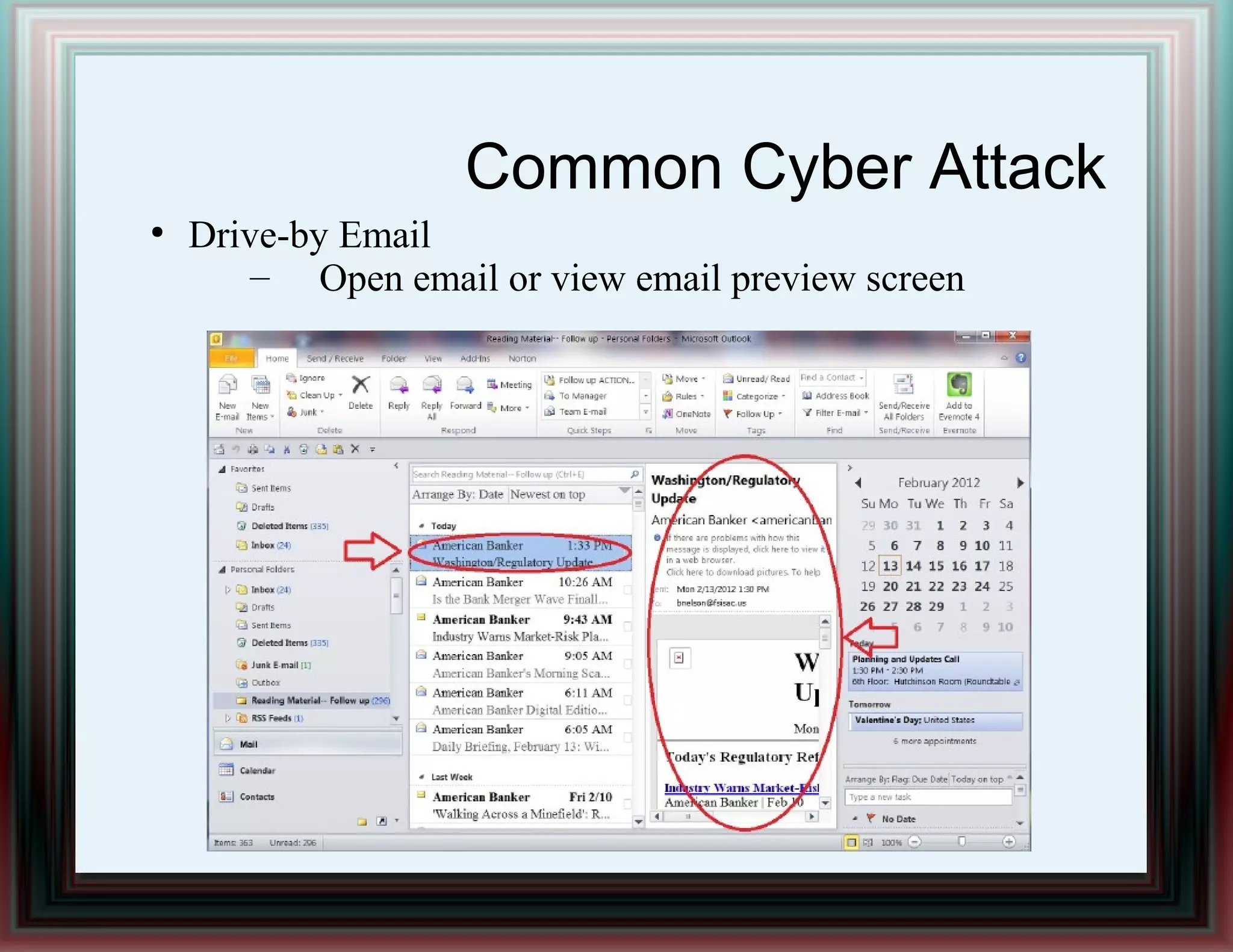
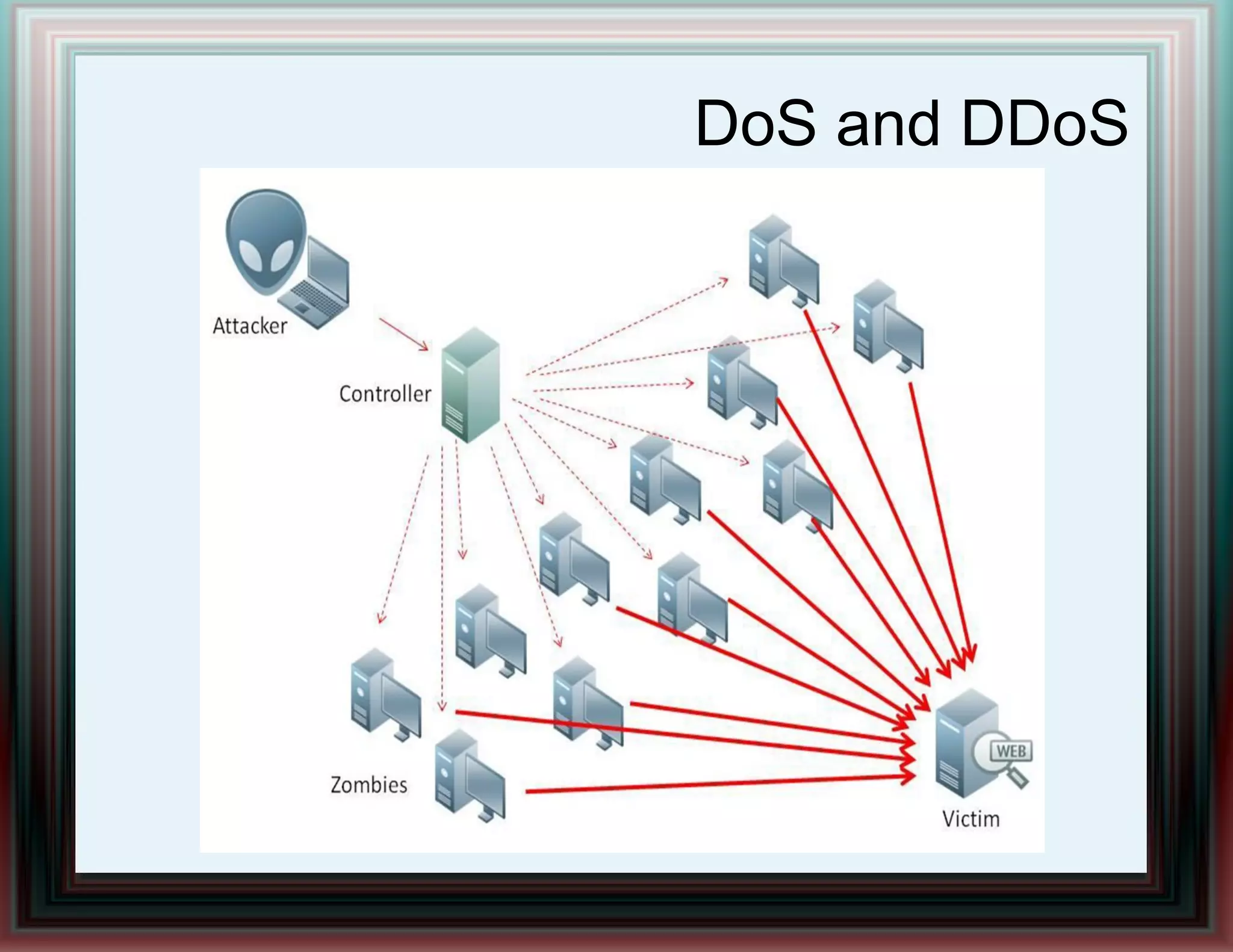
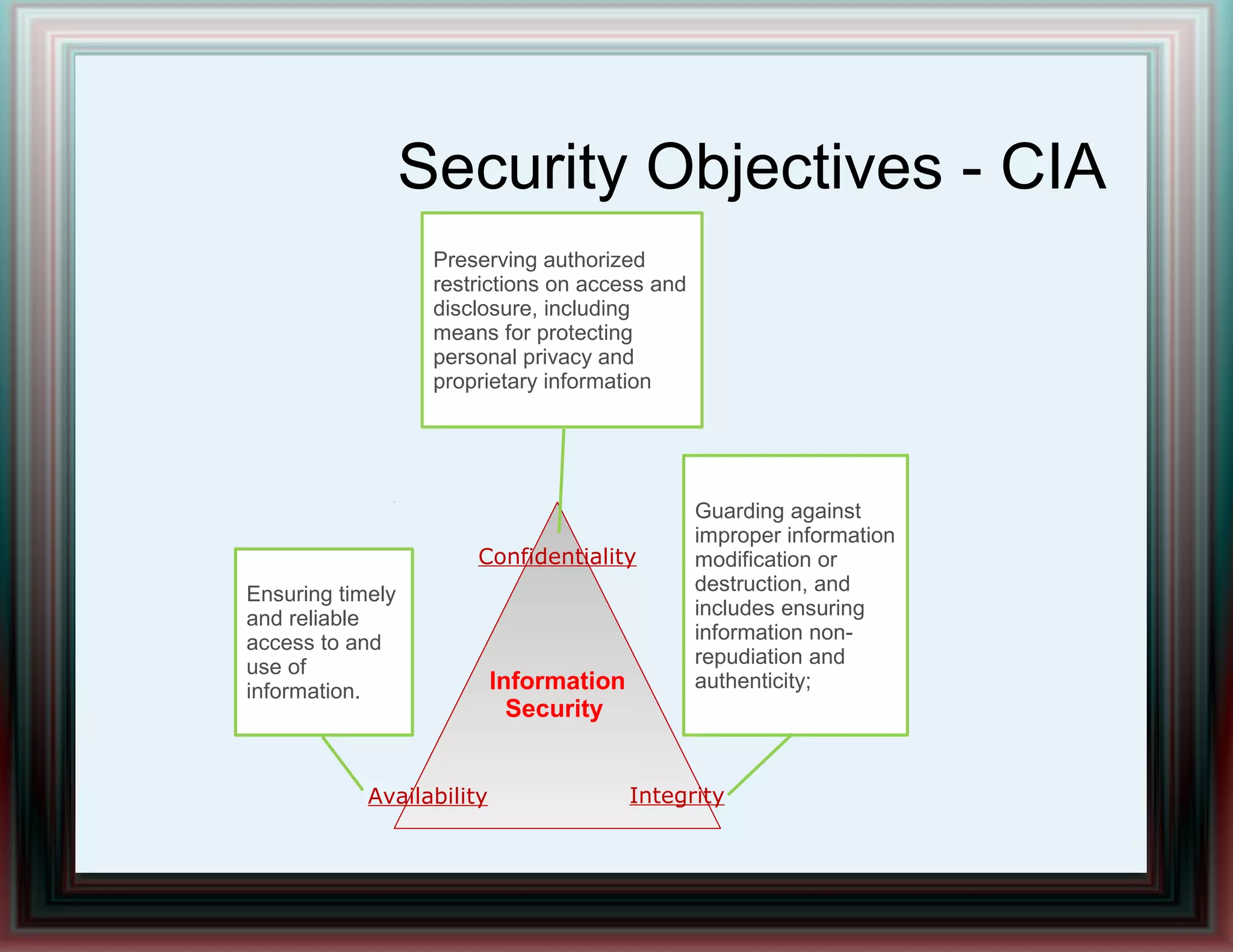
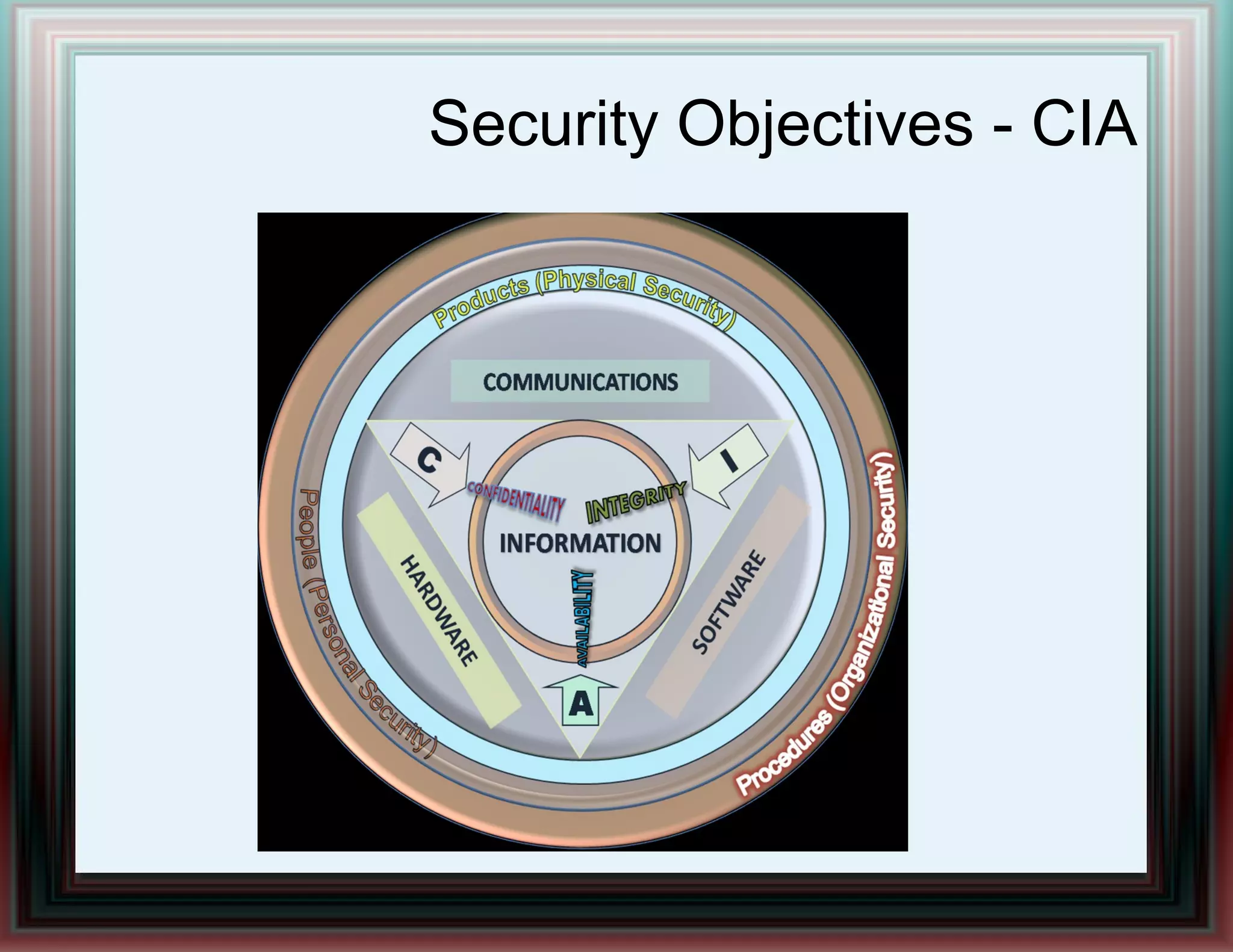
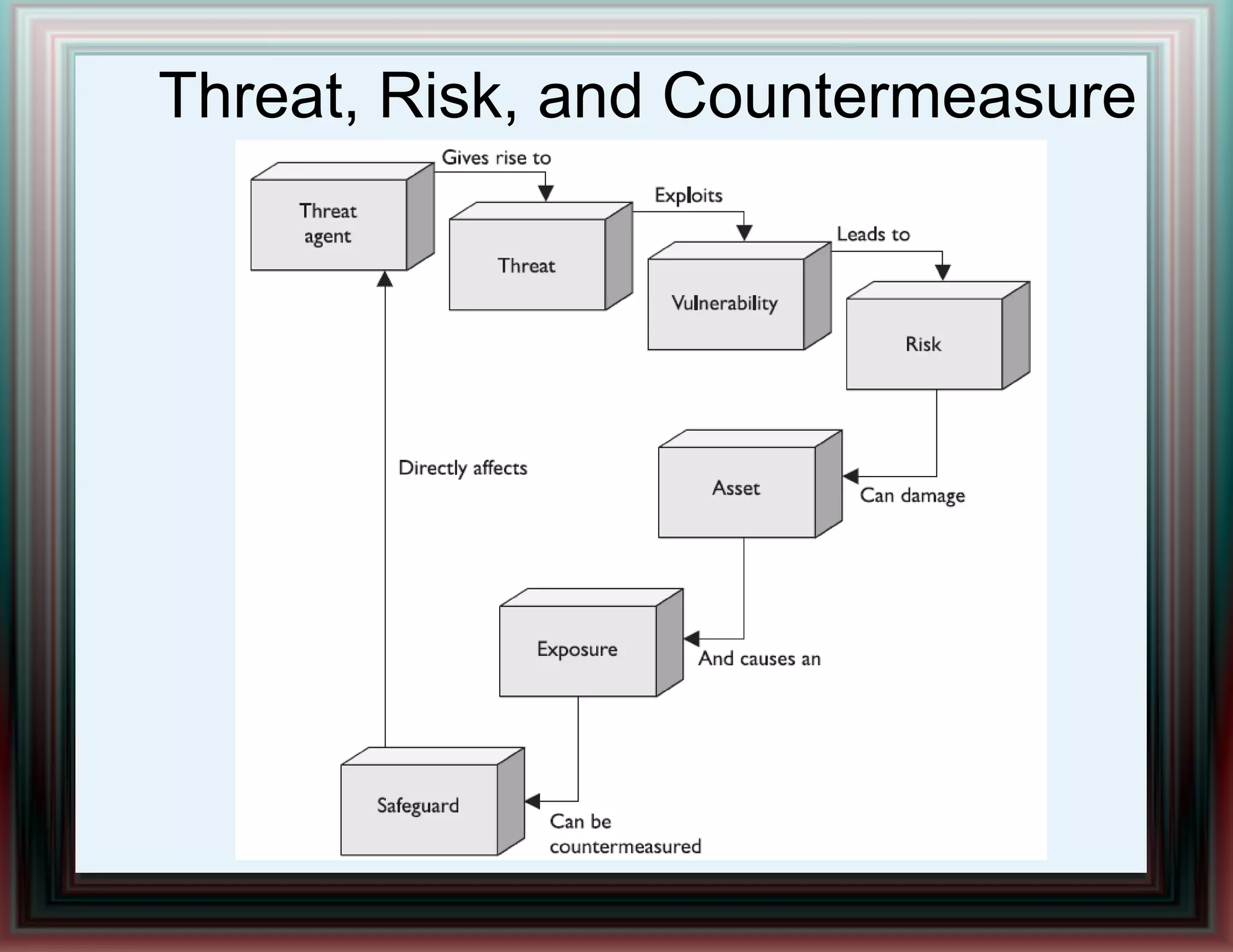
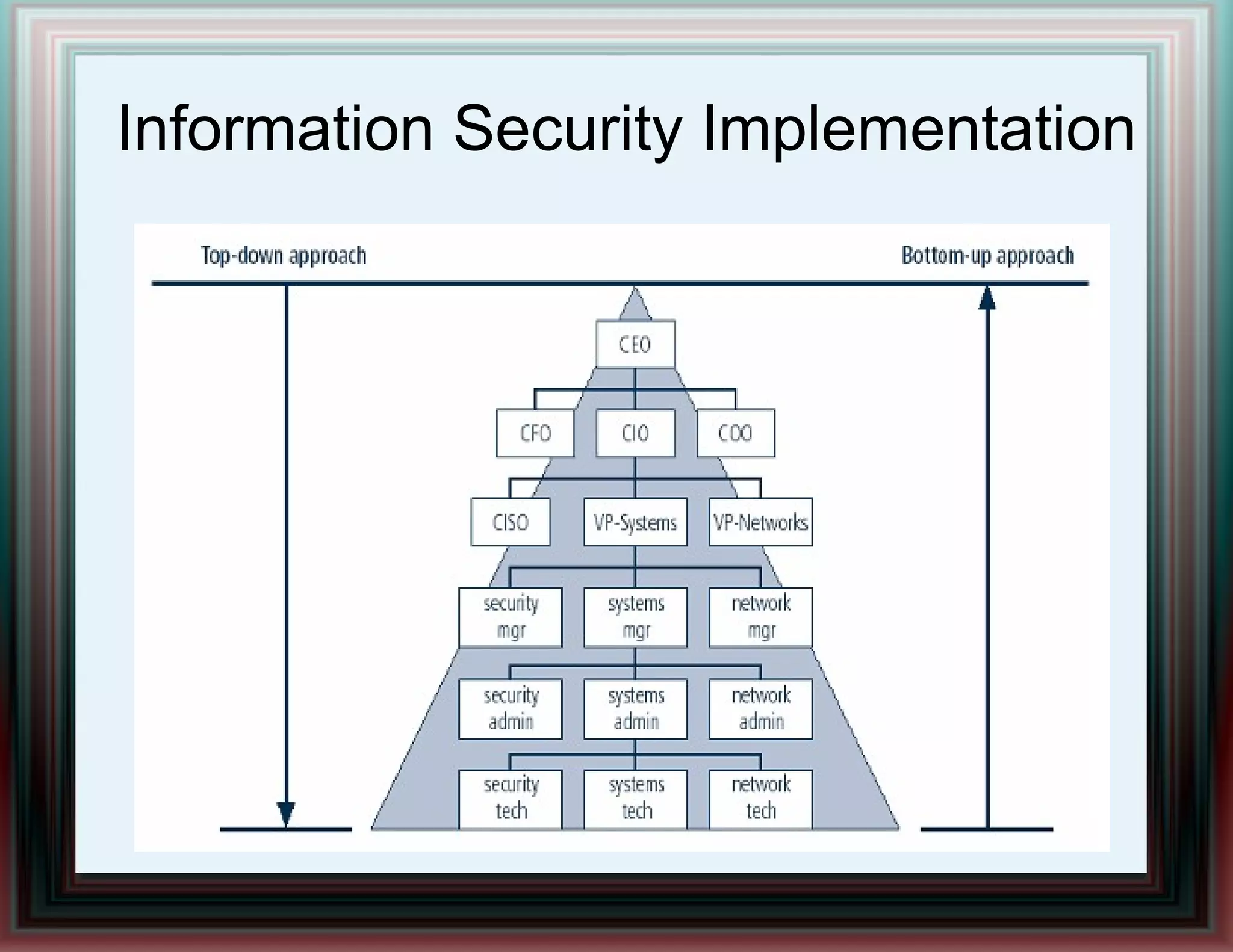
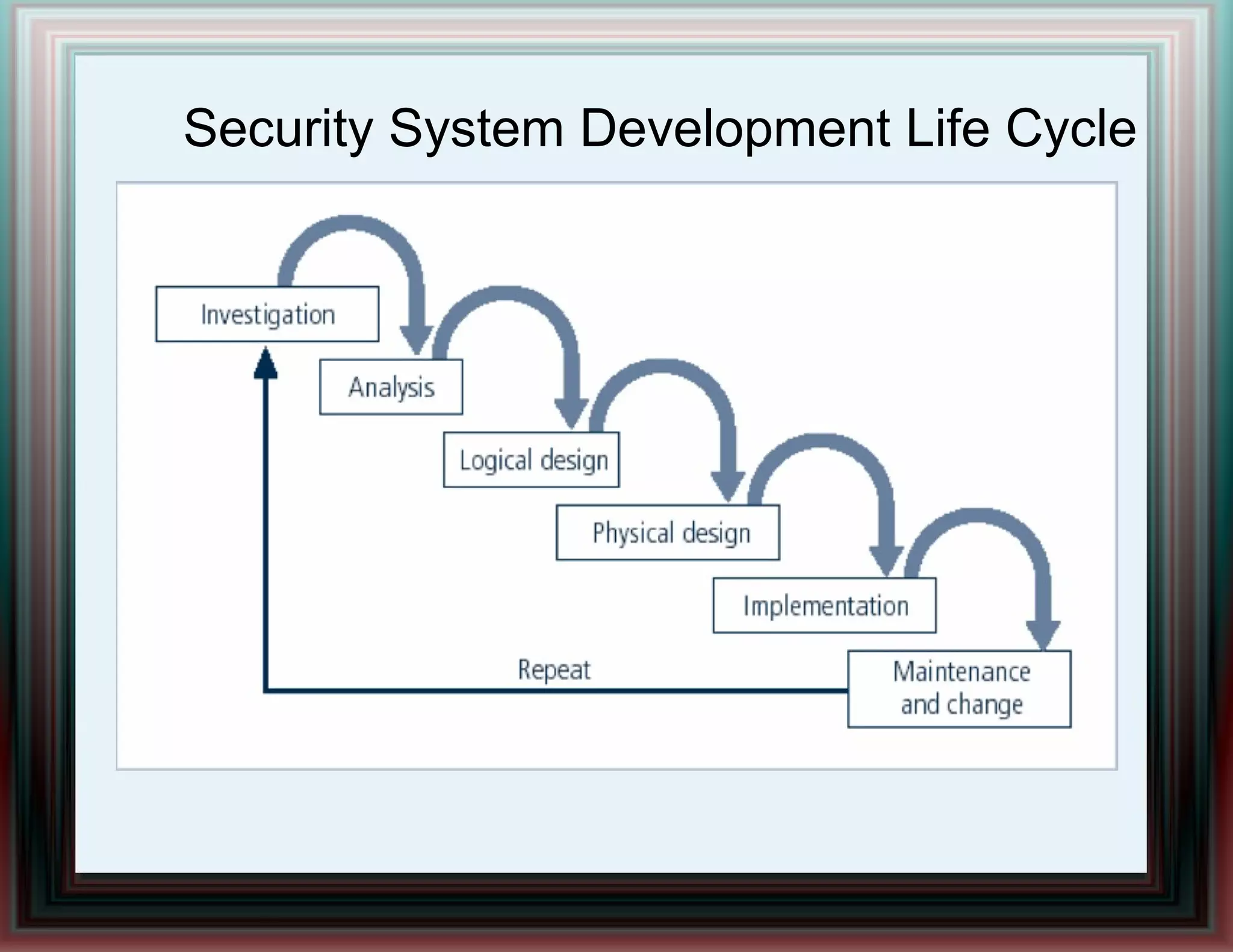
The document provides an overview of information security and risk management, highlighting common cyber attacks such as malware, phishing, and denial-of-service attacks. It emphasizes a layered security approach, including the CIA (Confidentiality, Integrity, Availability) objectives and the importance of risk management practices. Additionally, it outlines the security system development life cycle and the roles of various professionals in maintaining an effective information security program.