This document discusses various aspects of securing Android app development, including:
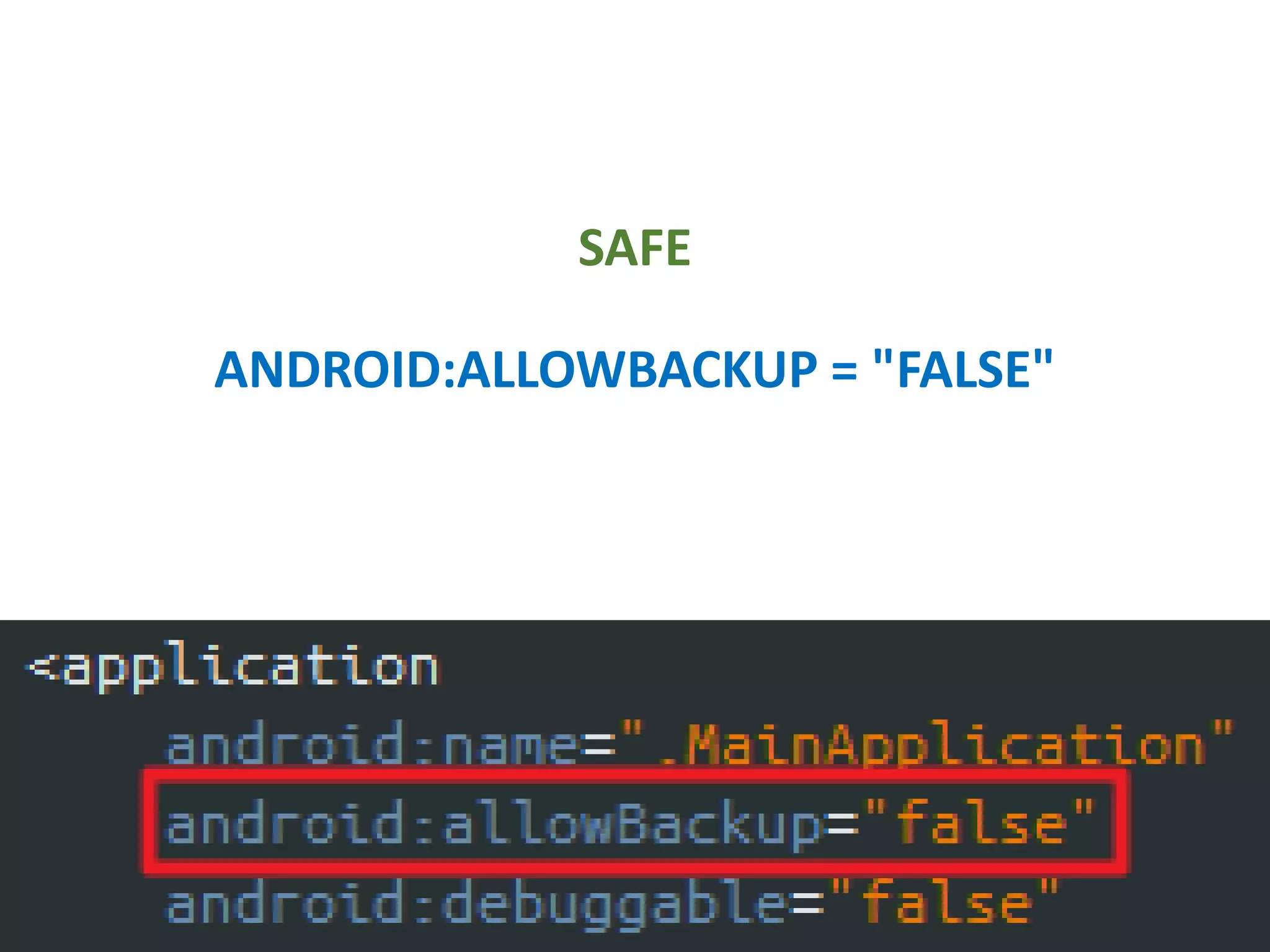
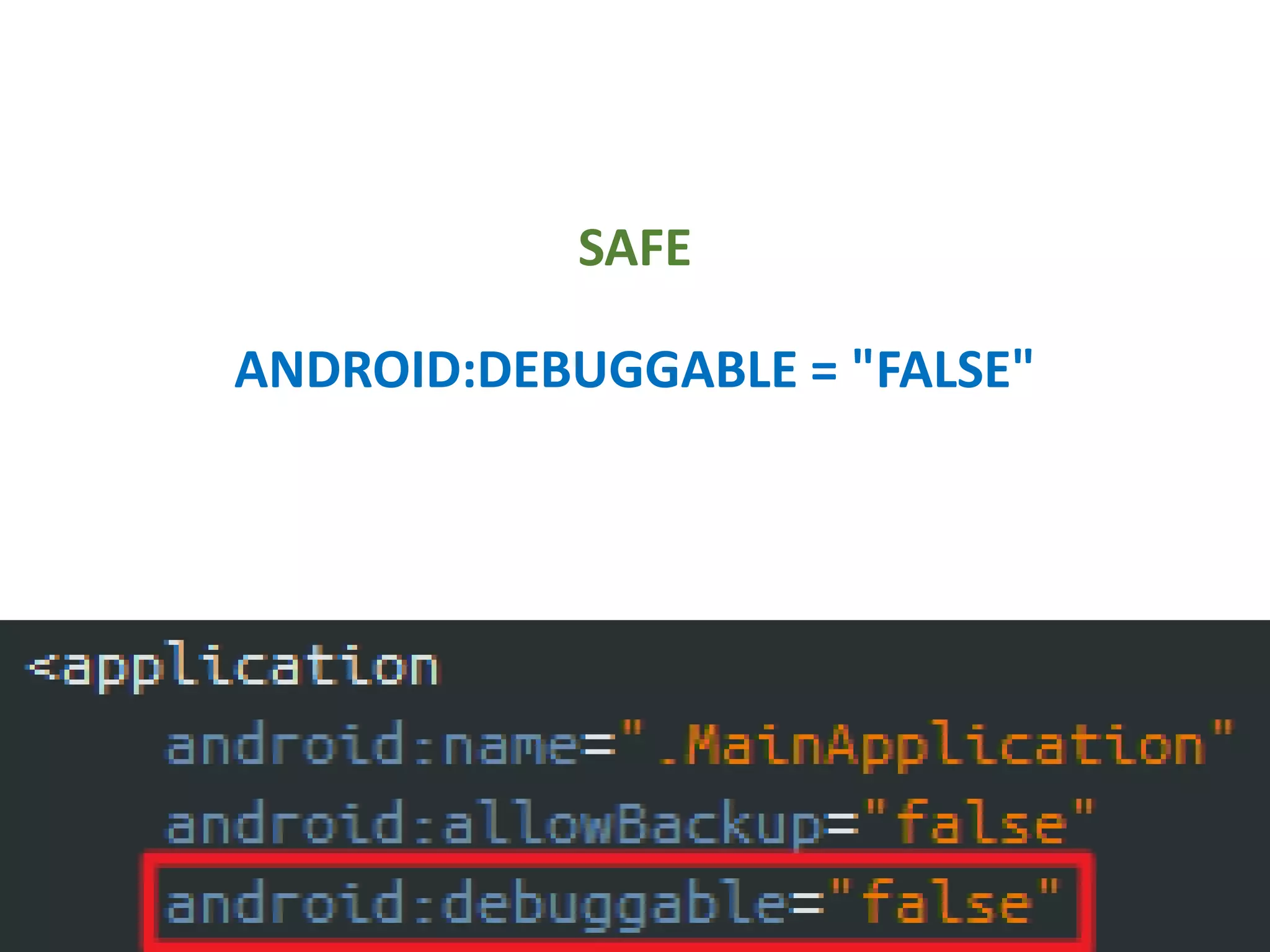
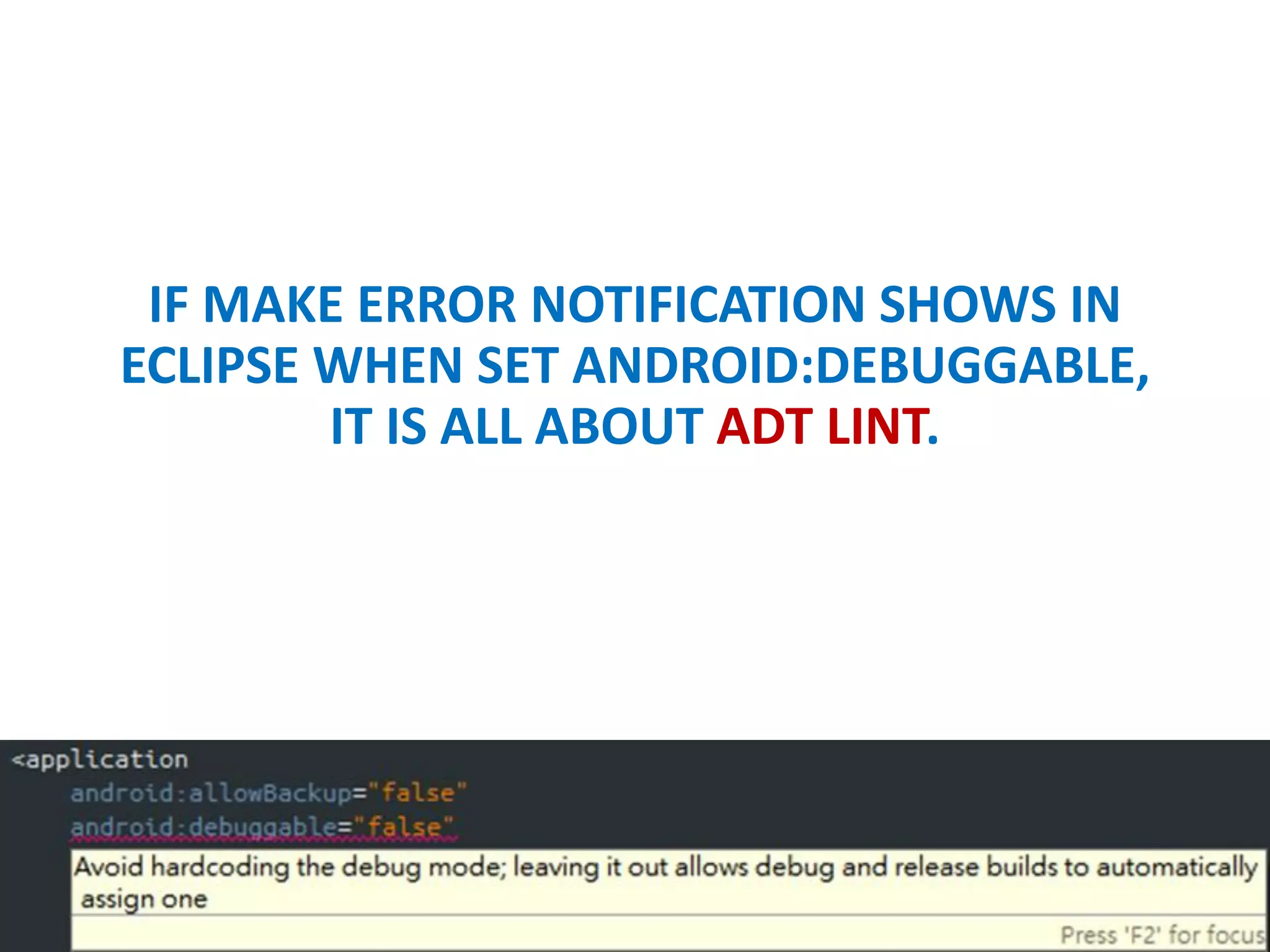
- Setting debuggable and backup permissions to false to prevent unauthorized access.
- Clearing the clipboard when leaving an app to avoid content being copied elsewhere.
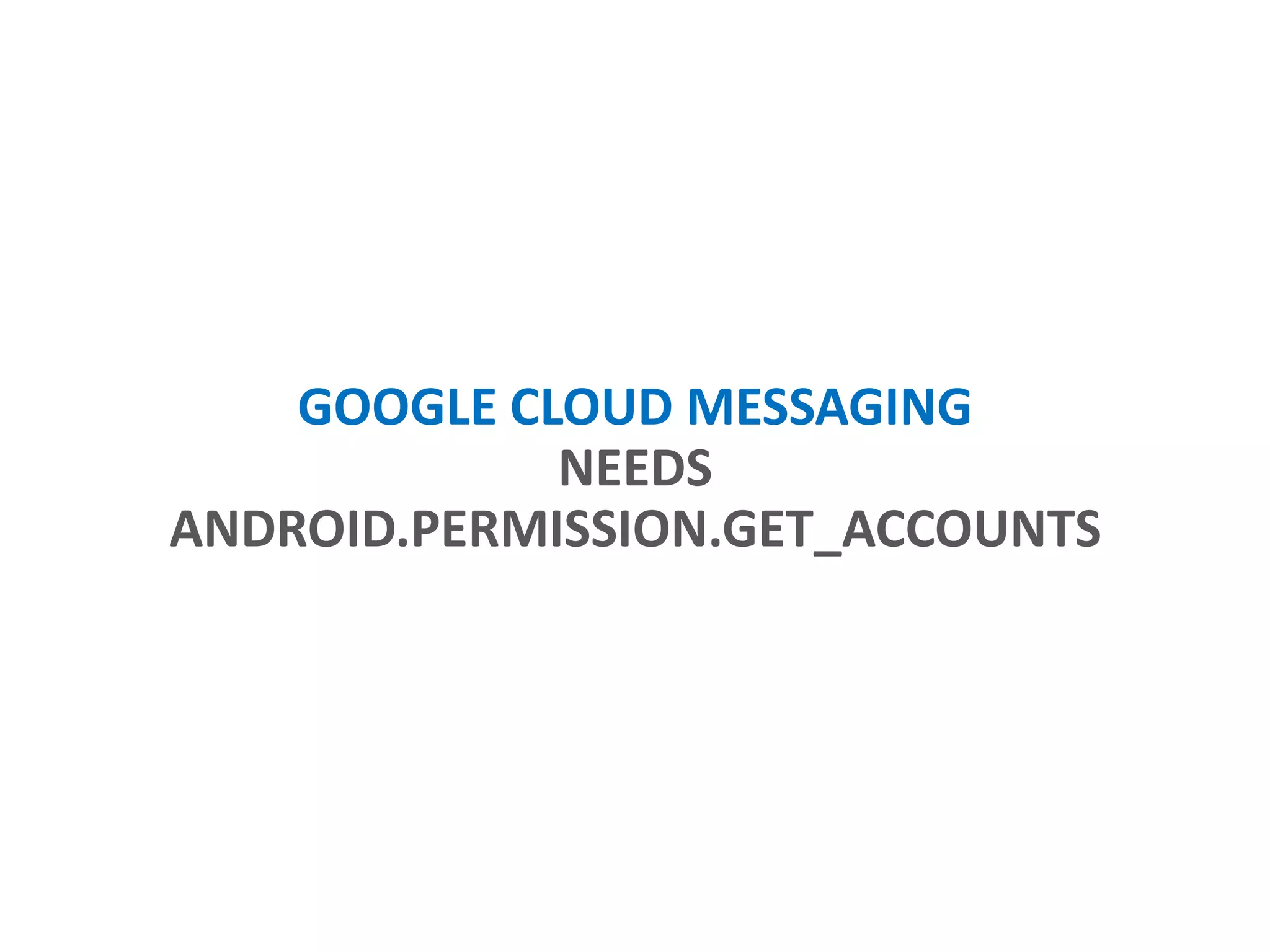
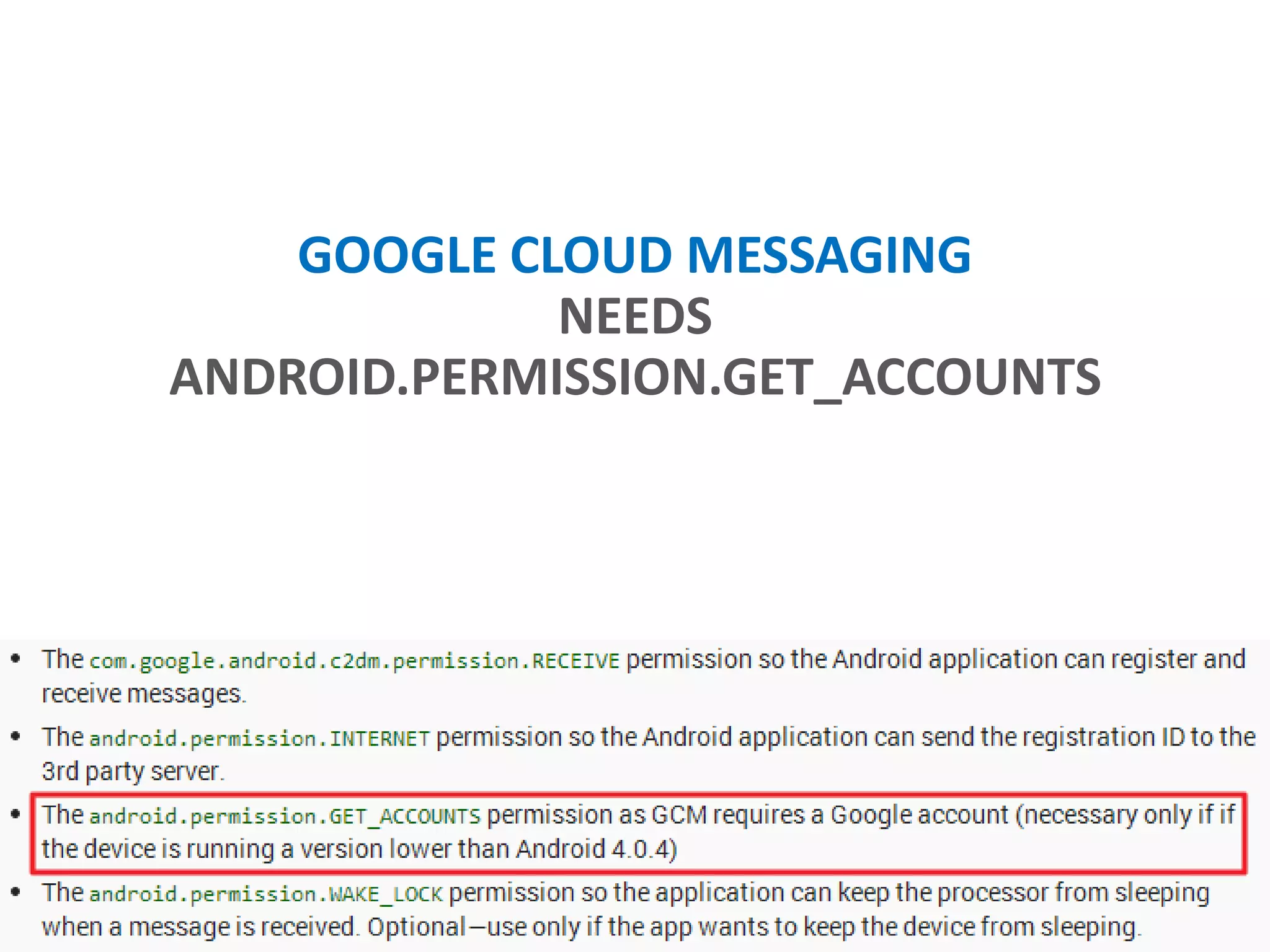
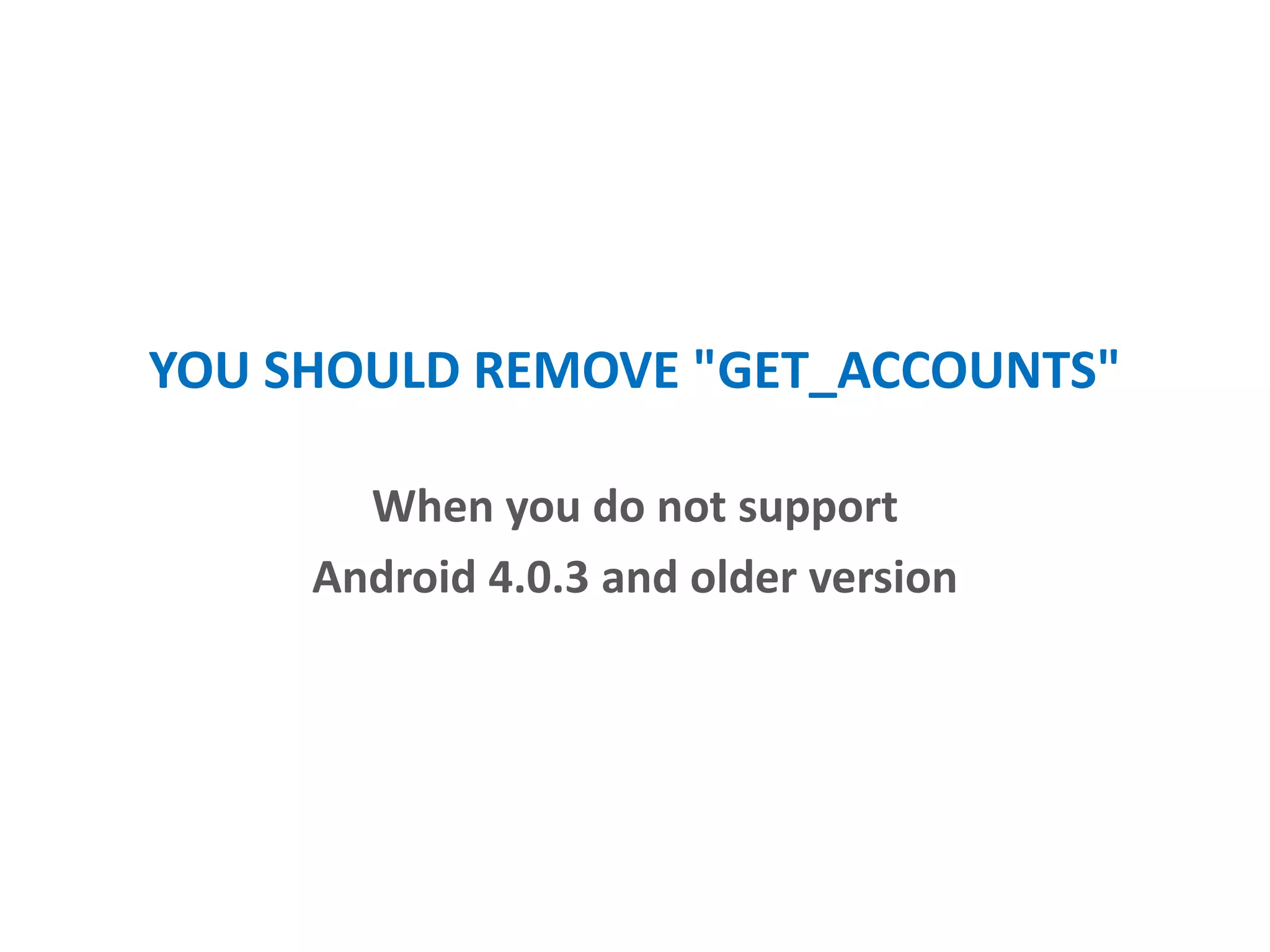
- Only requesting necessary permissions and removing unneeded ones over time.
- Encrypting databases using SQLCipher or the SQLite Encryption Extension.
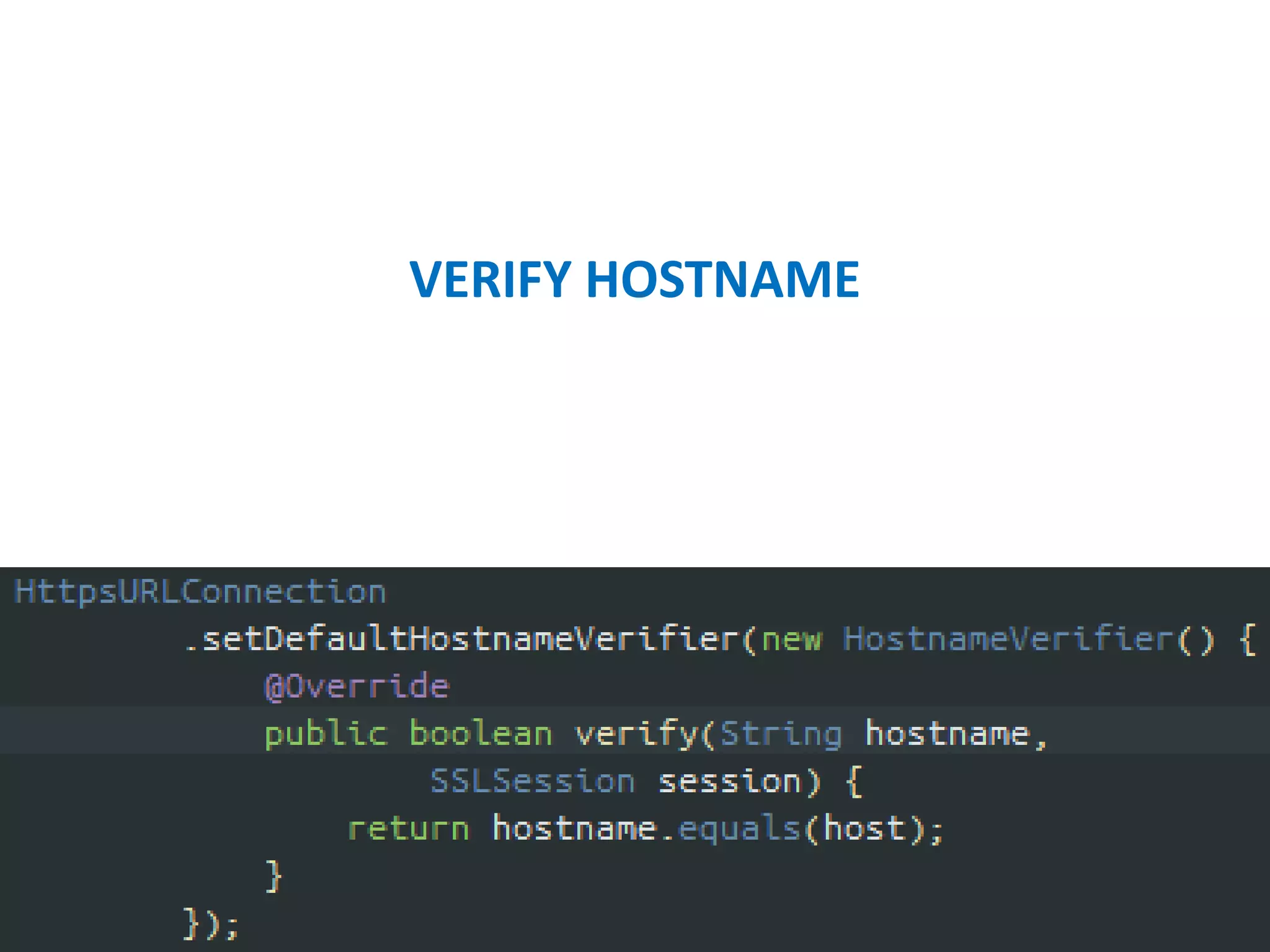
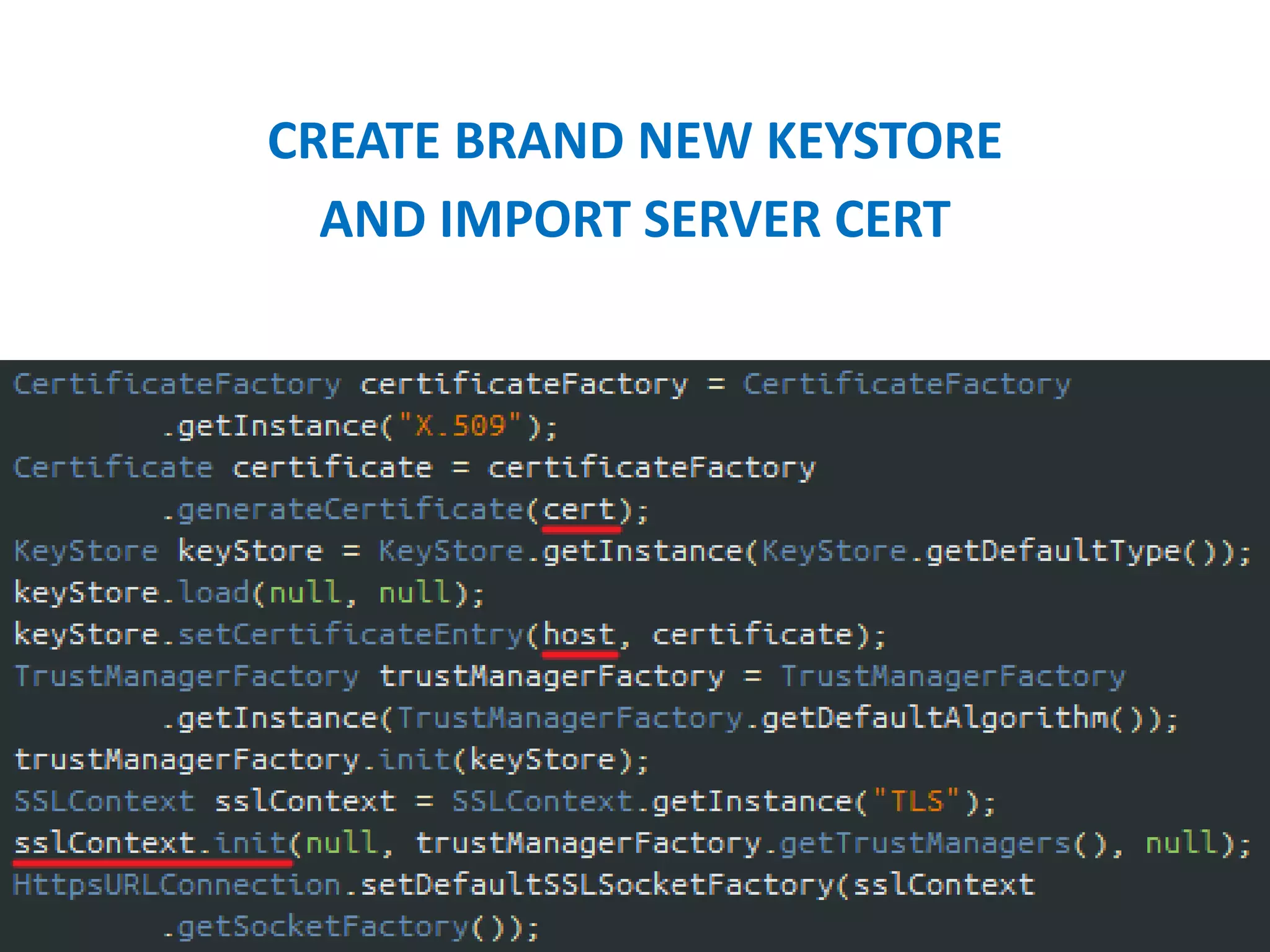
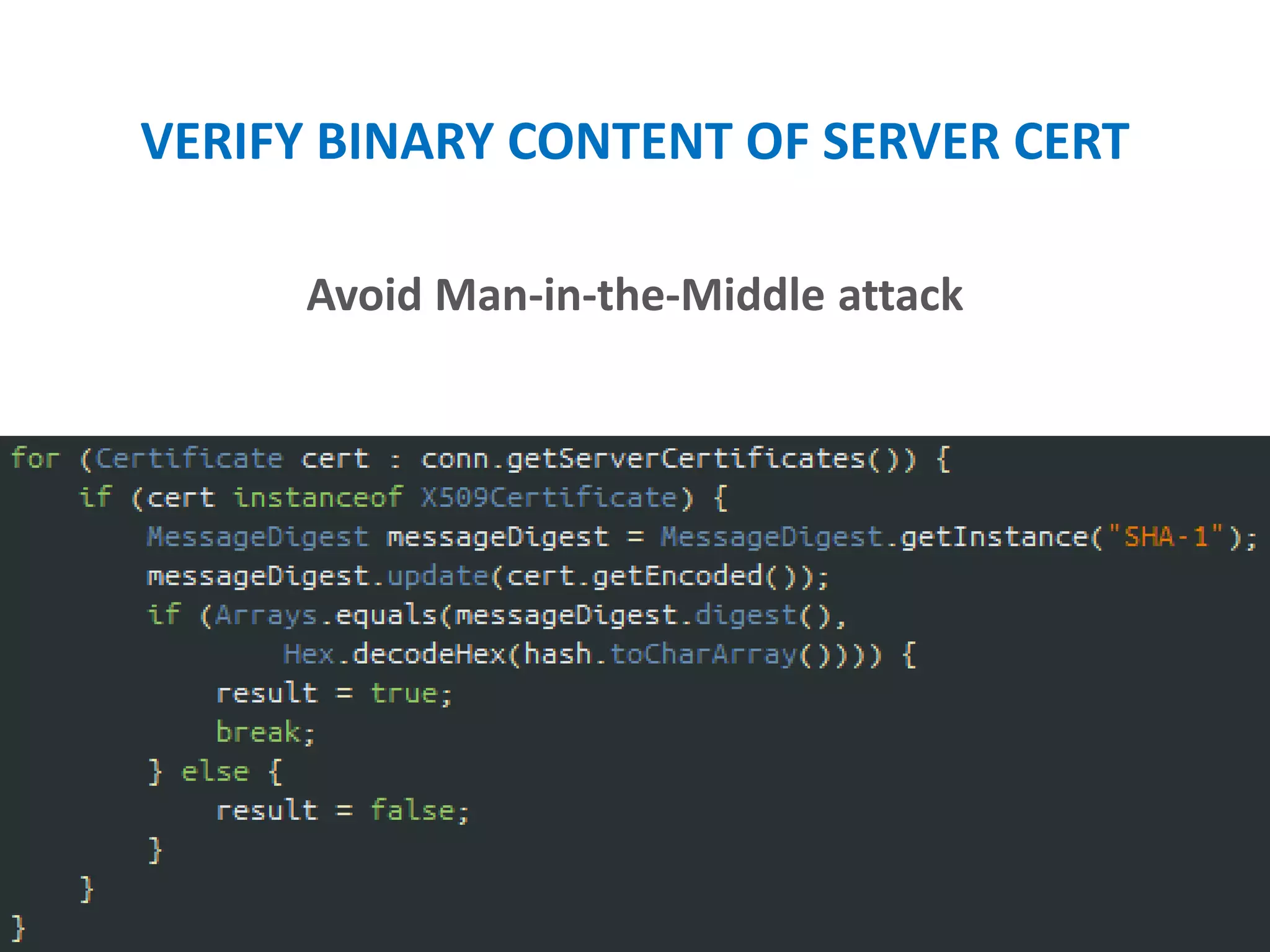
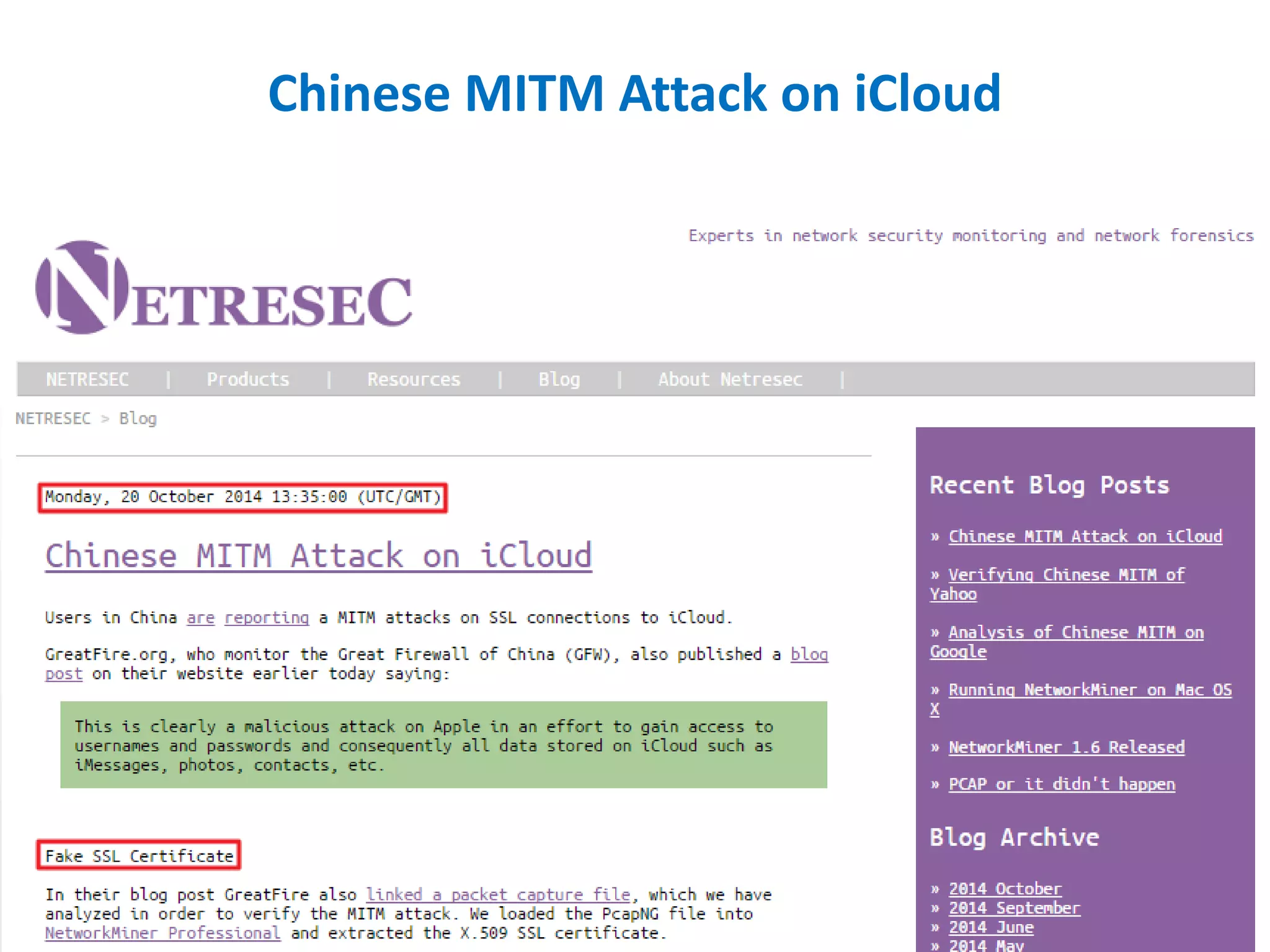
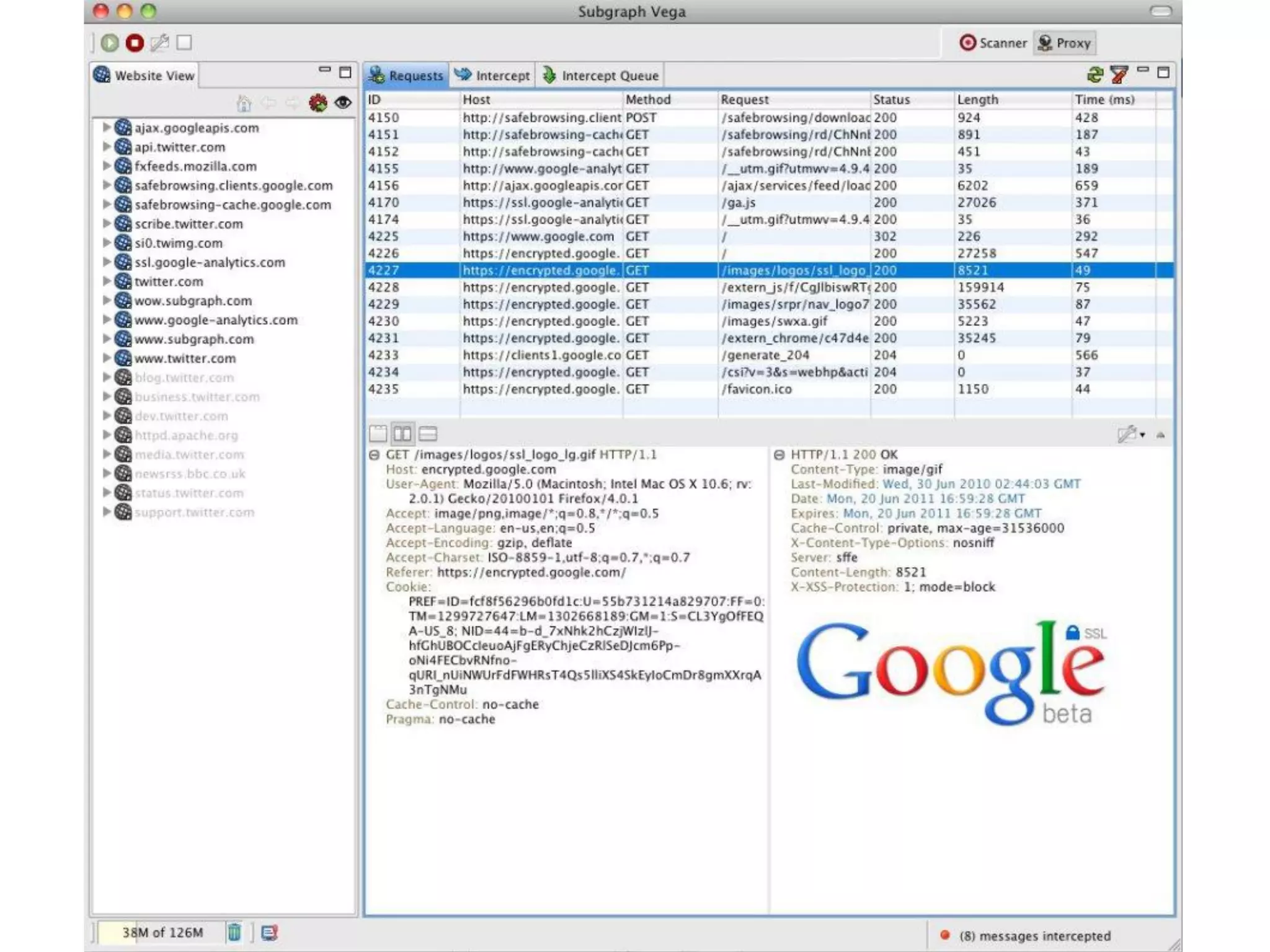
- Verifying SSL certificates and encrypting network traffic using HTTPS.
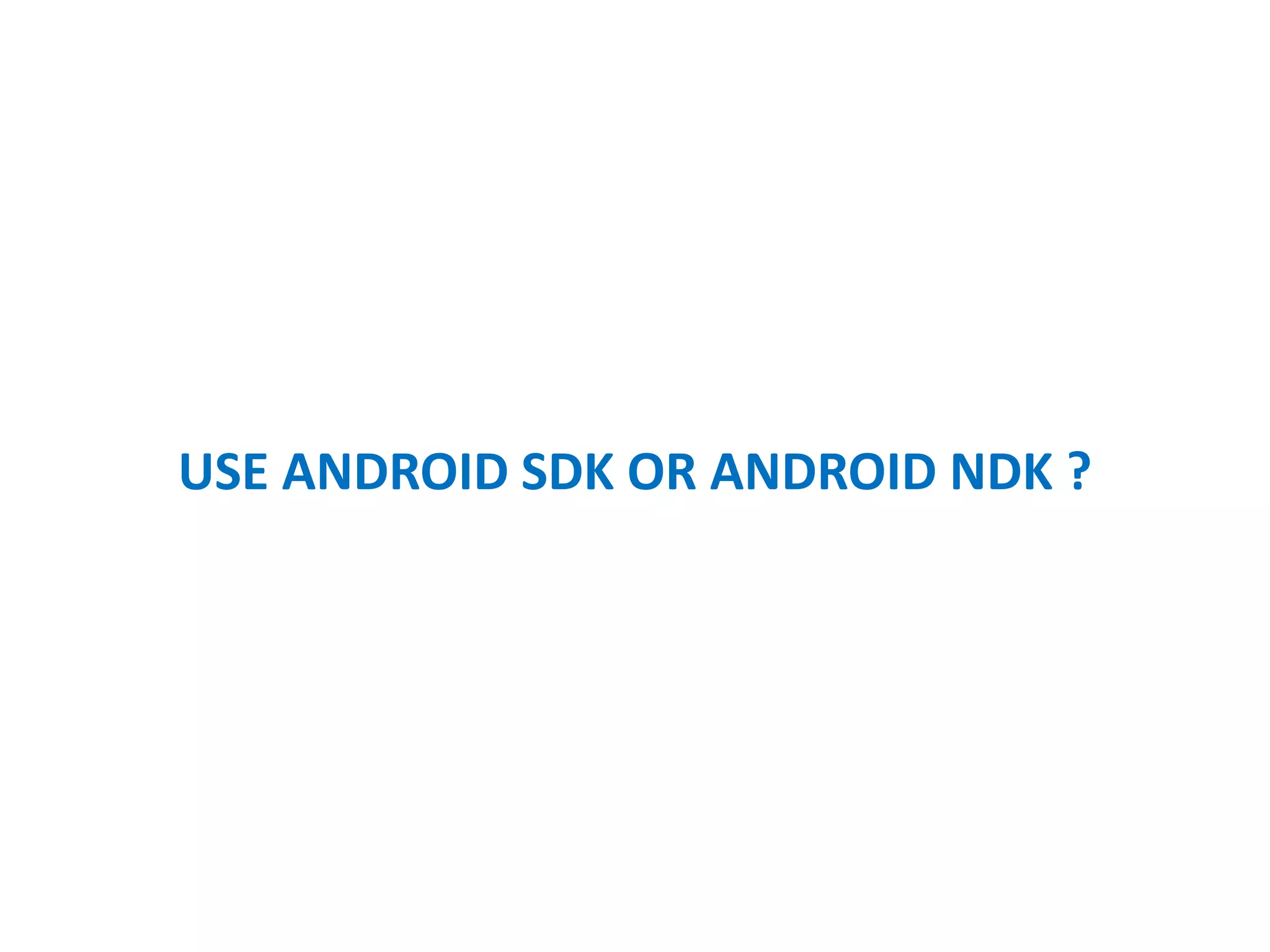
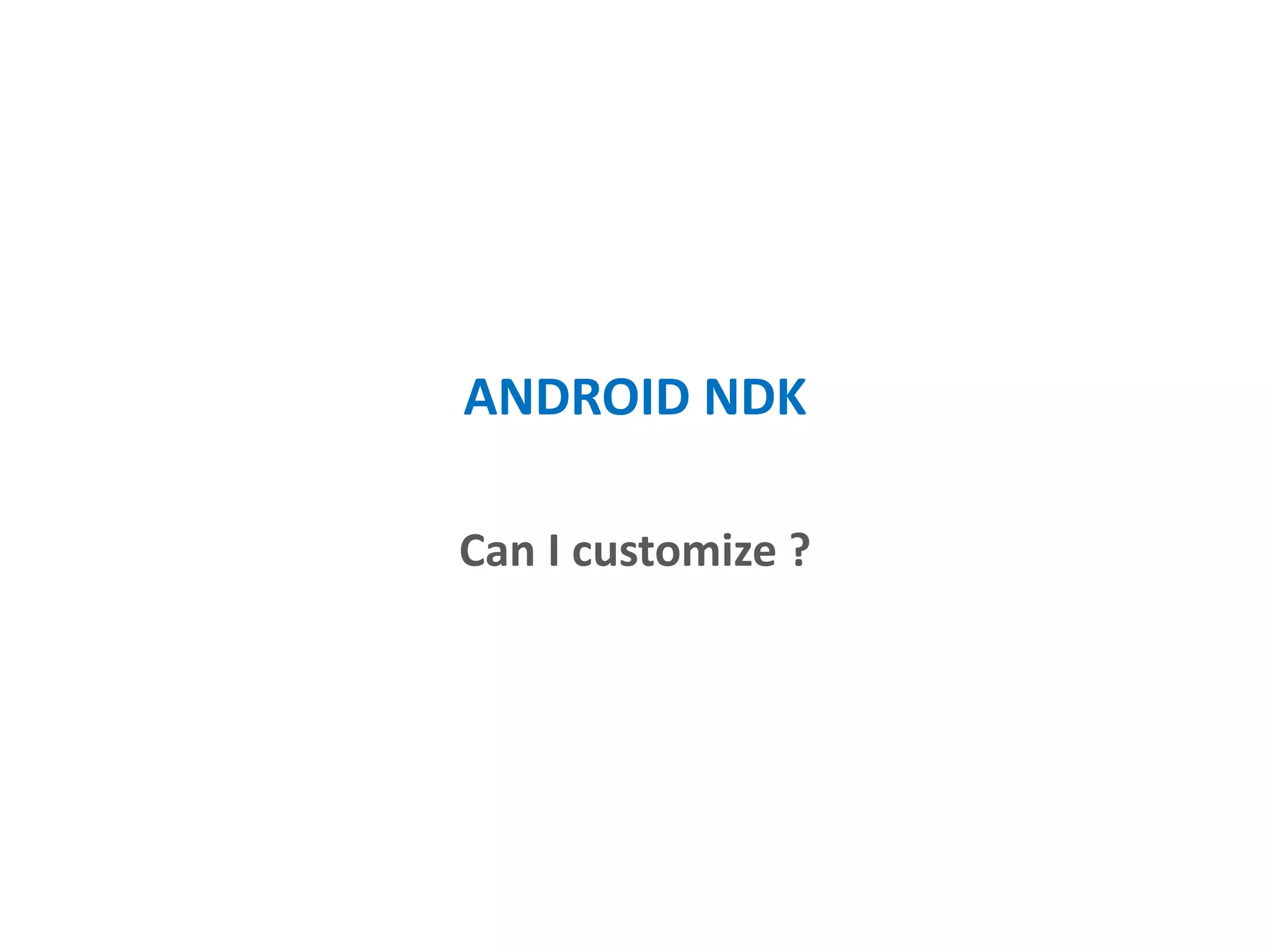
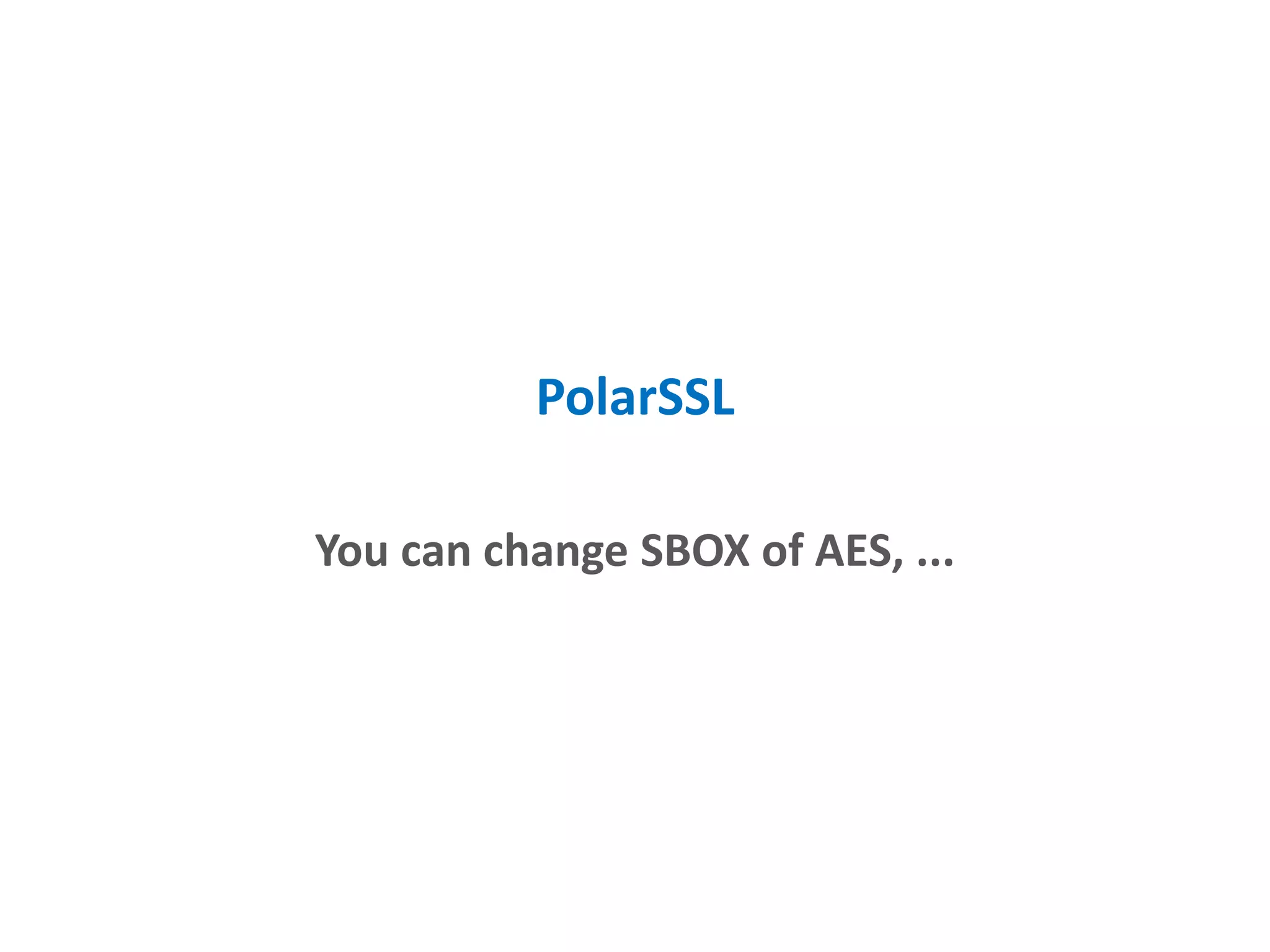
- Performing cryptography in C/C++ via the Android NDK for increased security.
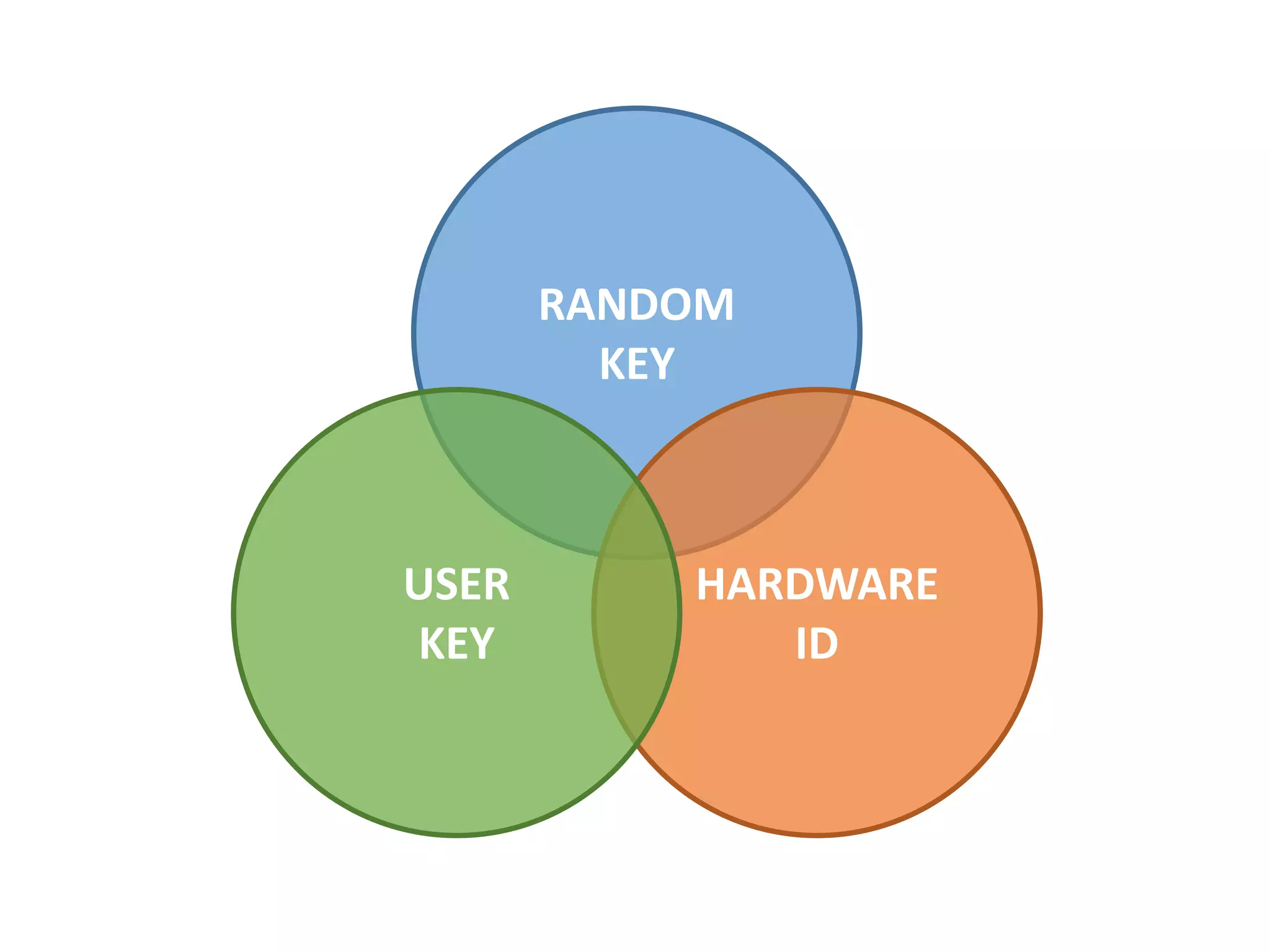
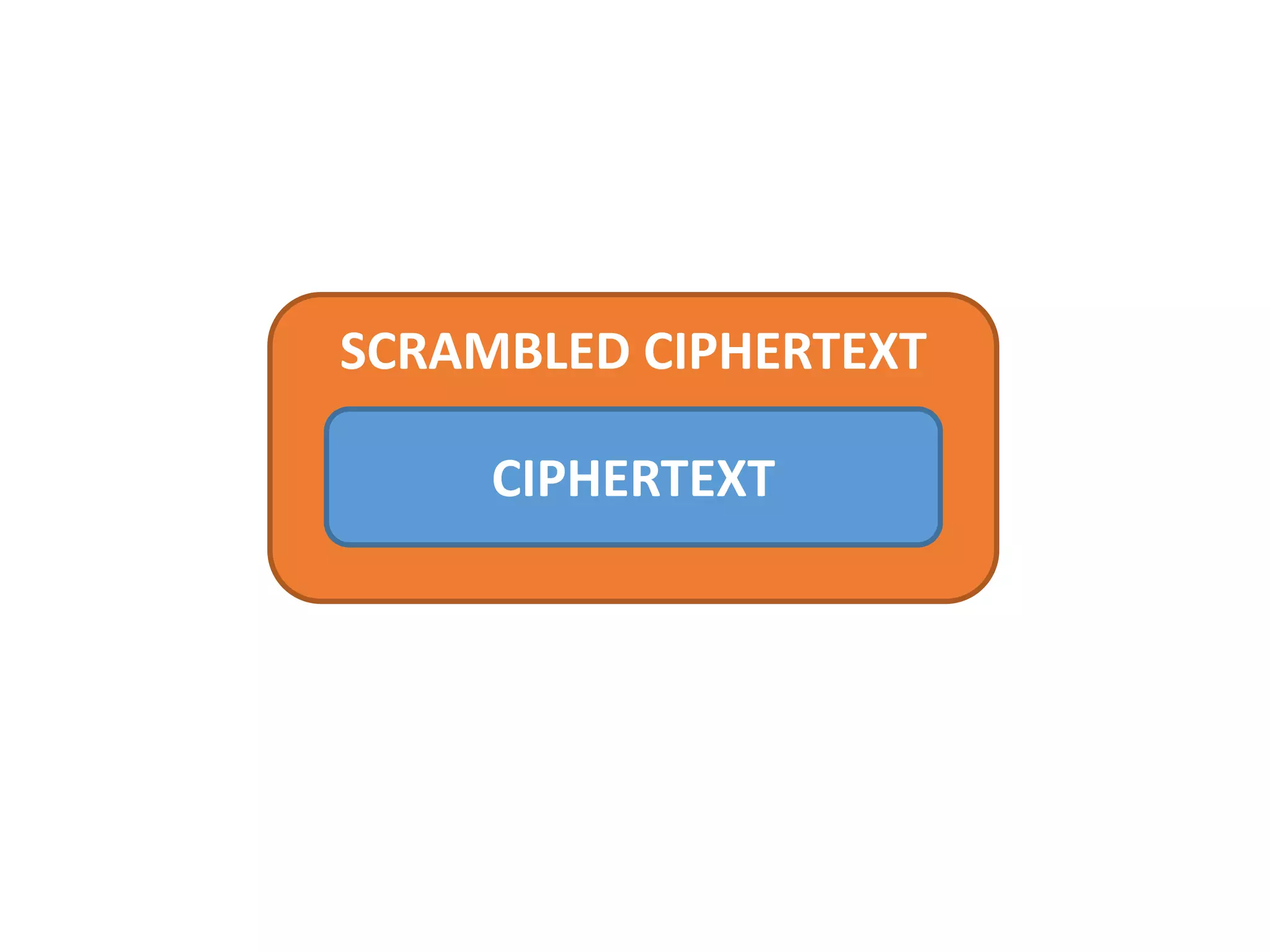
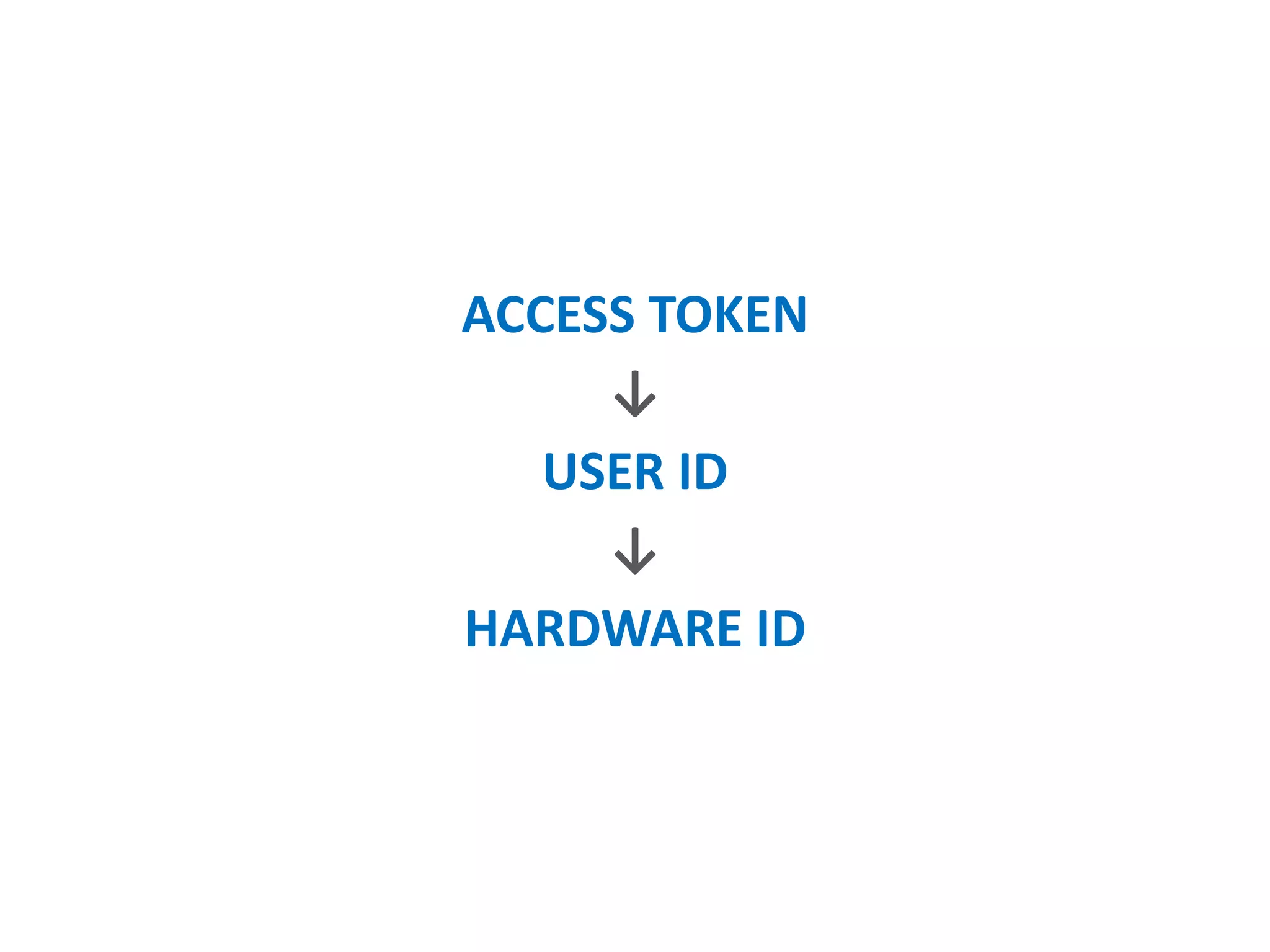
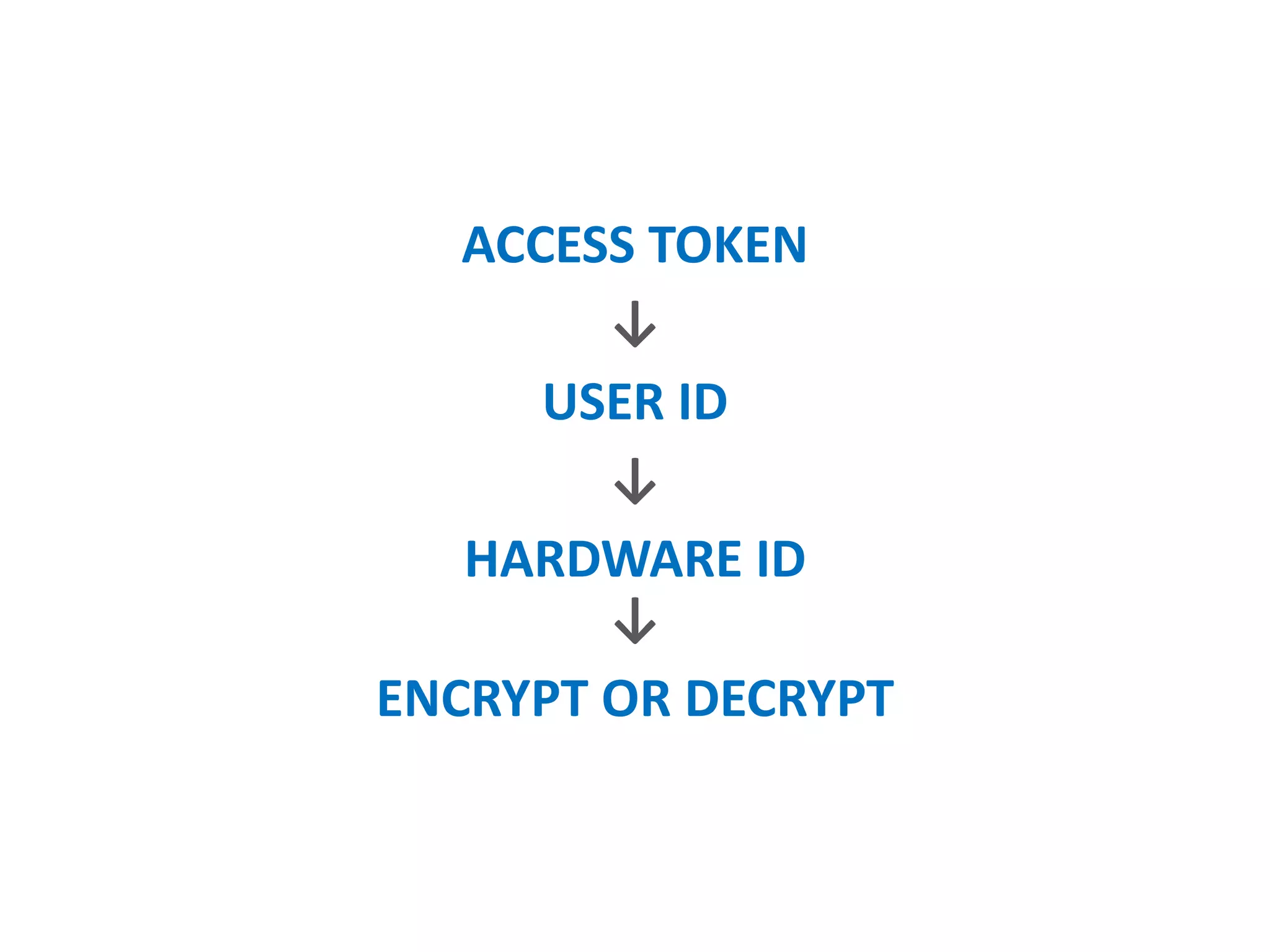
- Generating secure access tokens, passwords, and keys using techniques like hardware IDs and scrambling.
- Validating user input through secure hashing algorithms.






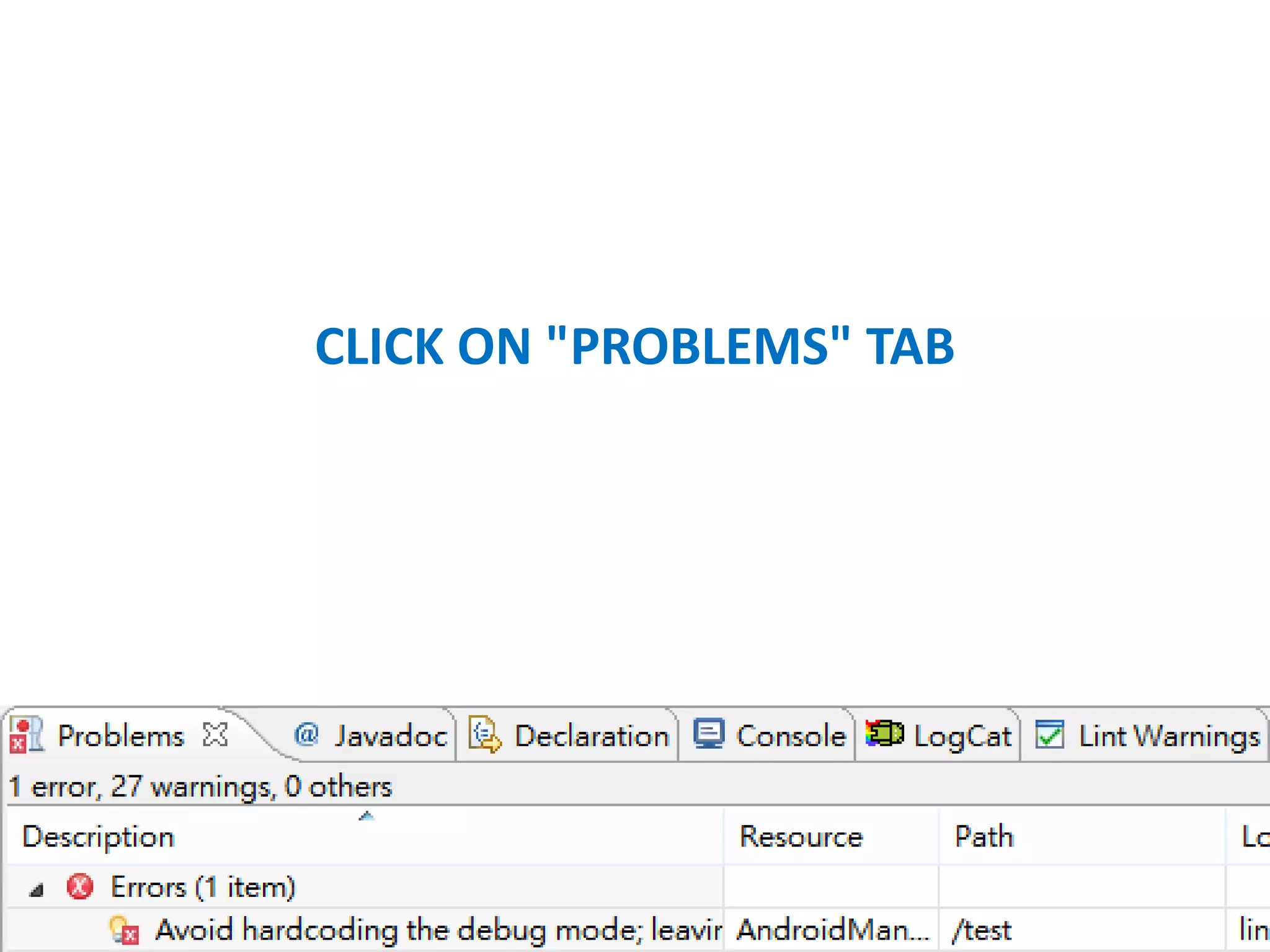
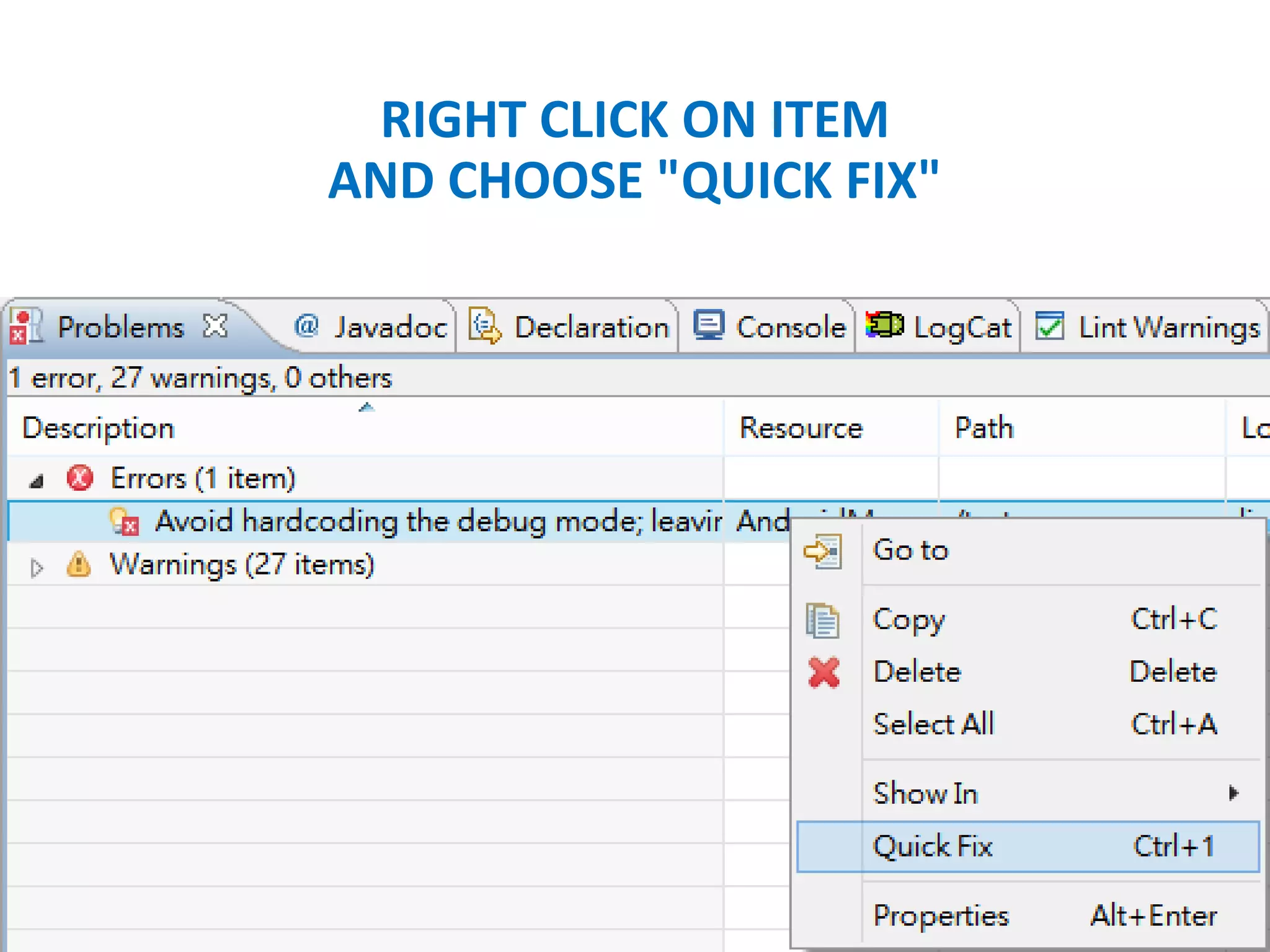
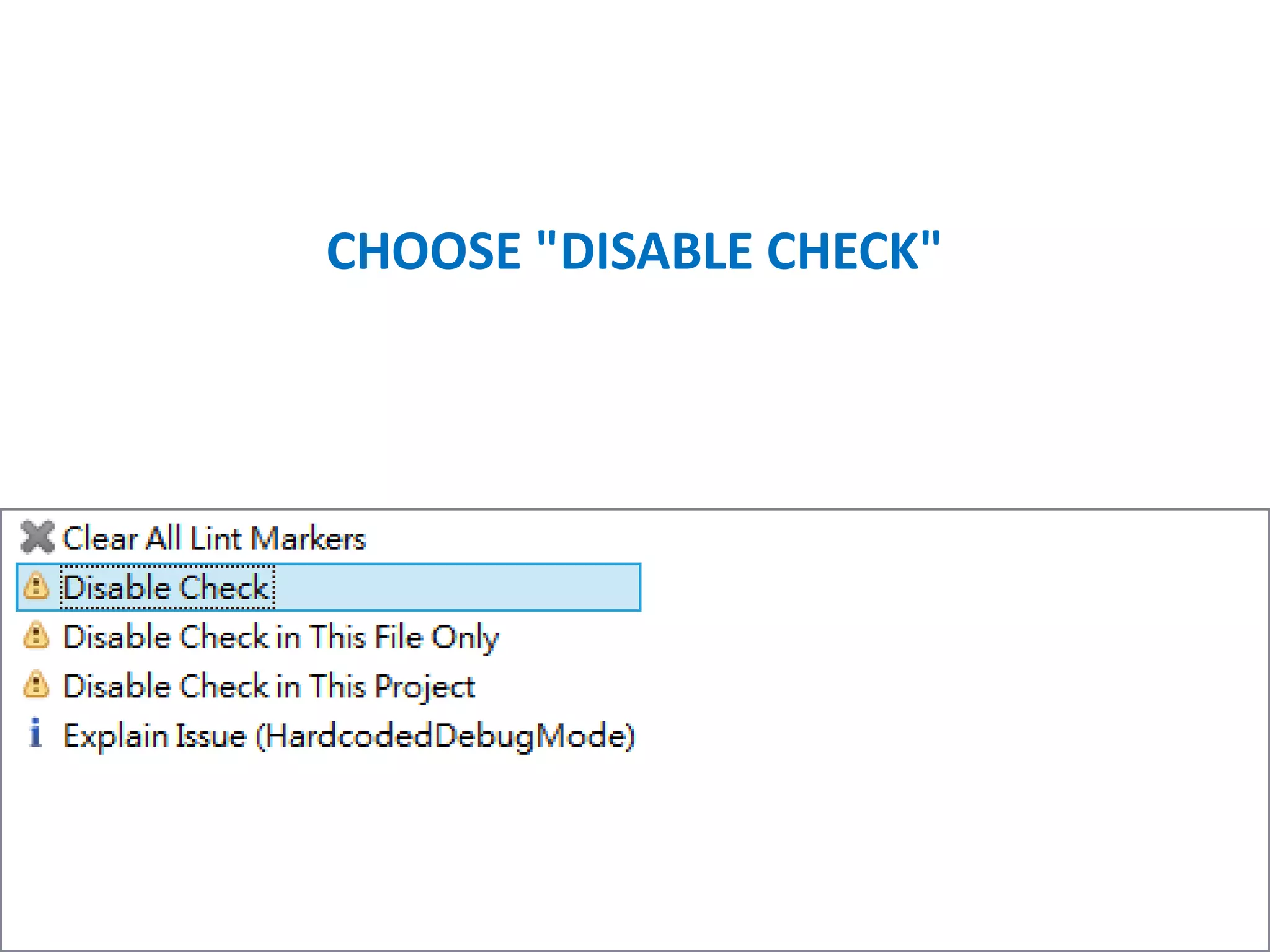

![GETWINDOW().SETFLAGS(LAYOUTPARAMS.FL
AG_SECURE, LAYOUTPARAMS.FLAG_SECURE);
It disable all screen capture (except rooted device)
• [POWER] + [VOL-DWN]
• OEM feature like SAMSUNG / HTC](https://image.slidesharecdn.com/androidsecuritydevelopment-141024153506-conversion-gate01/75/2015-04-24-Updated-Android-Security-Development-Part-1-App-Development-15-2048.jpg)