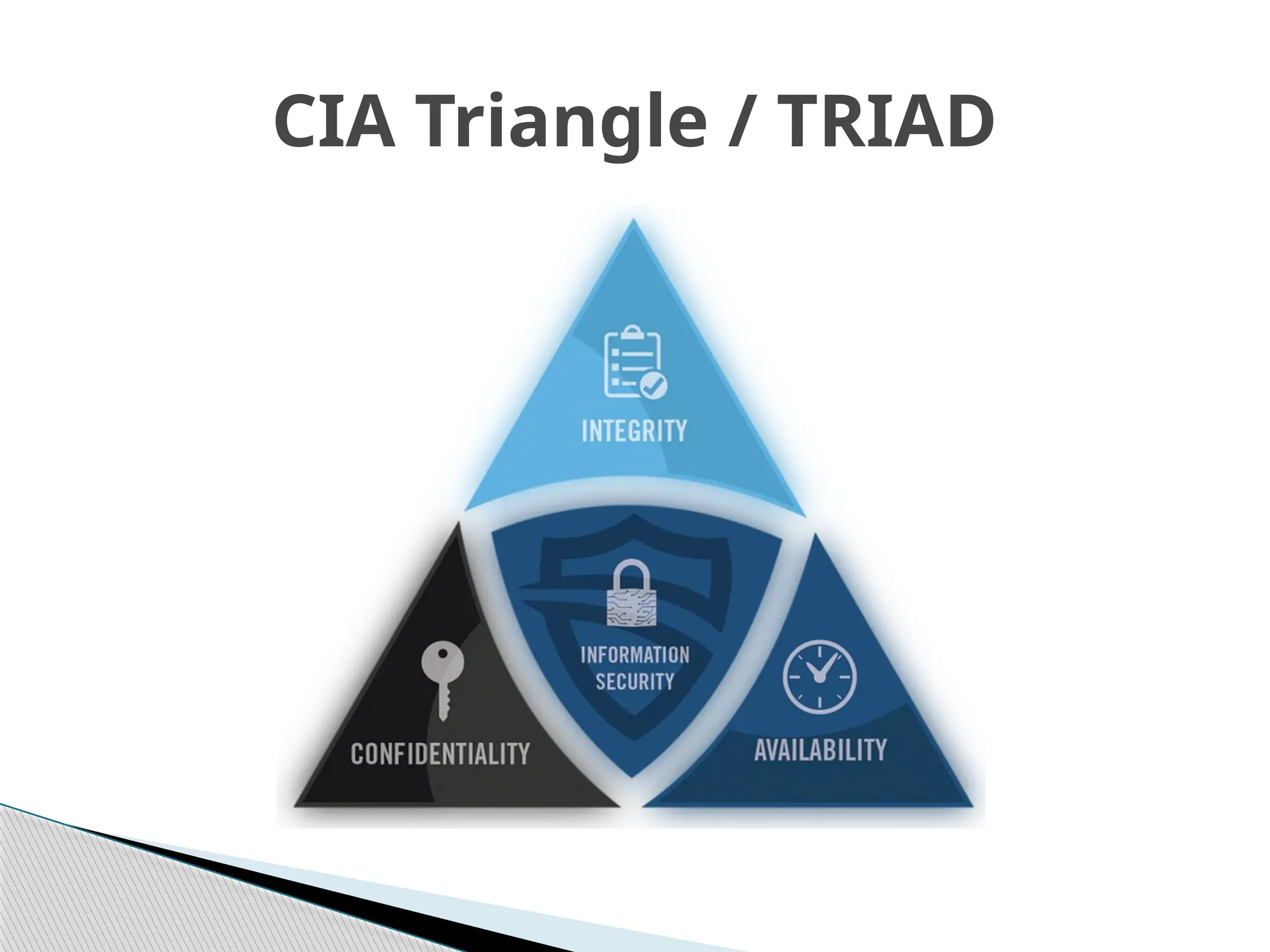
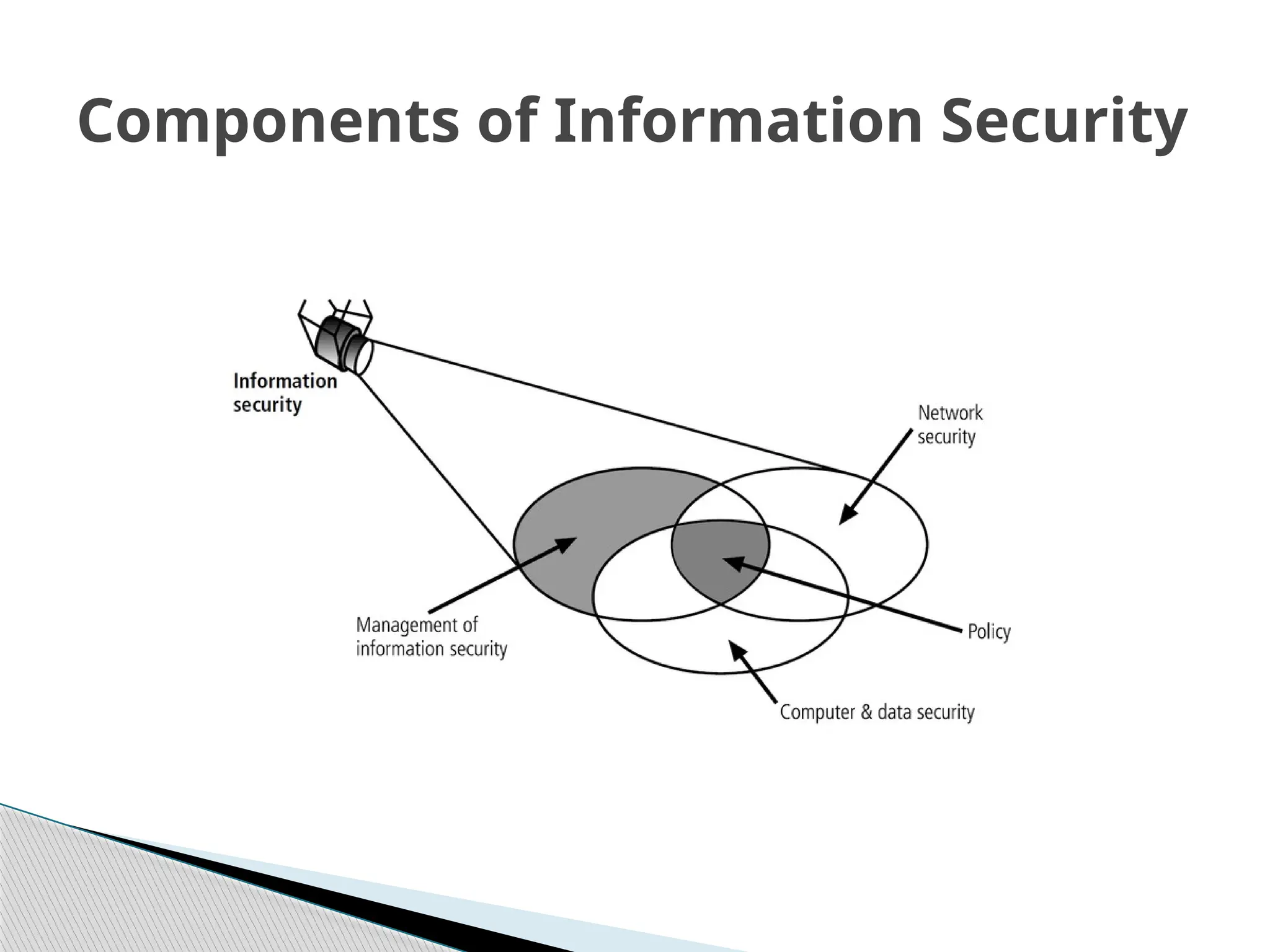
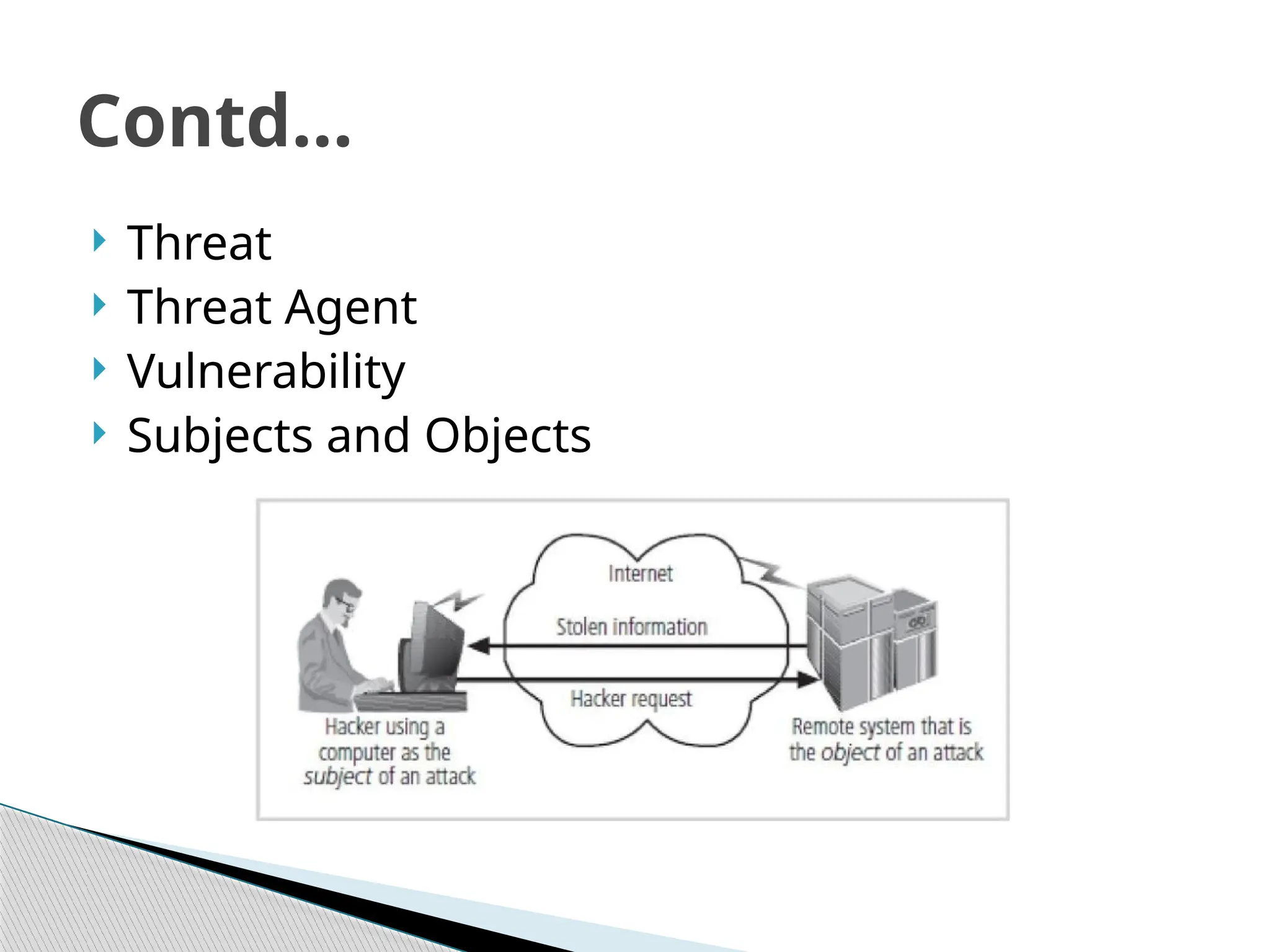
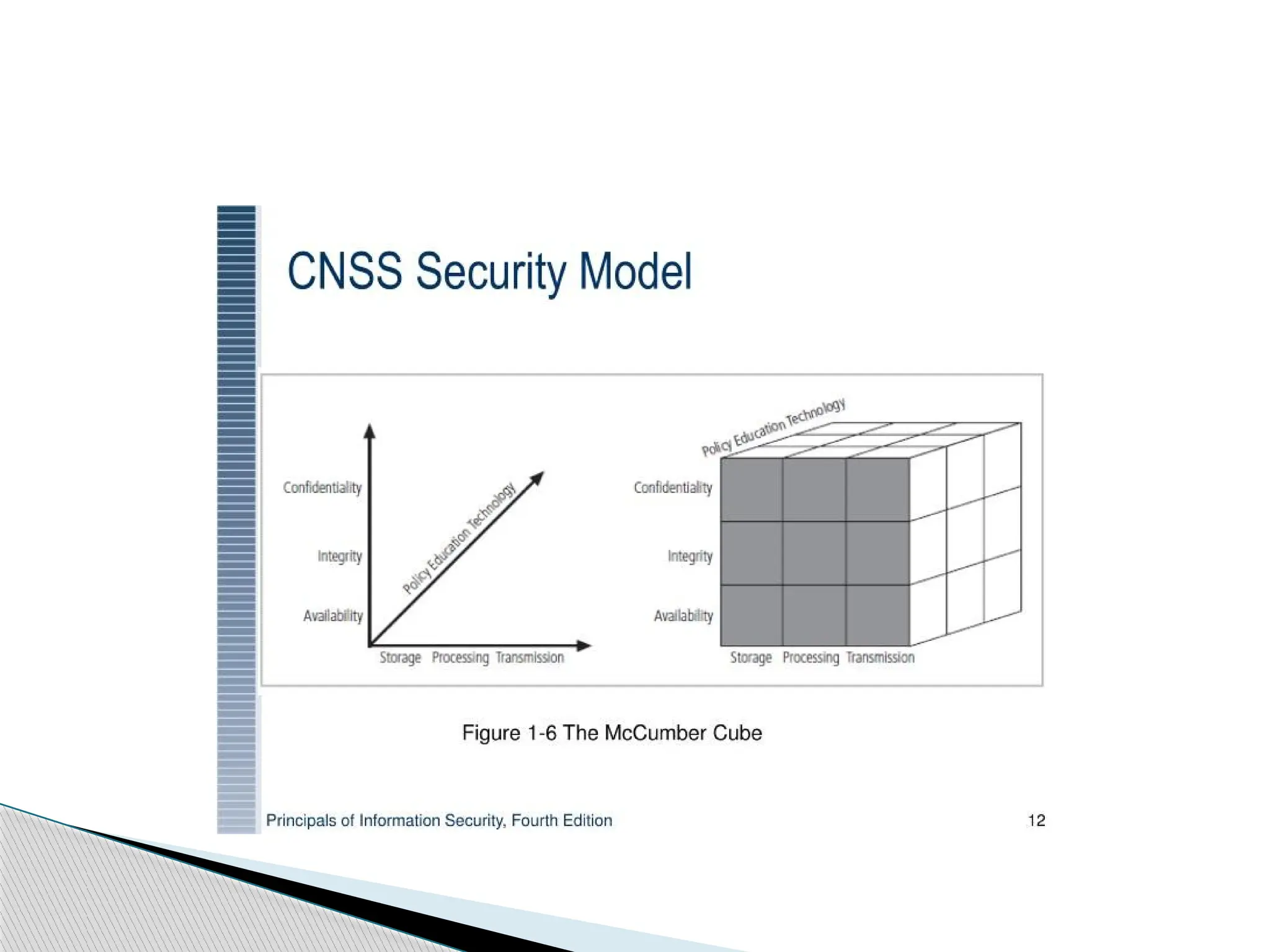
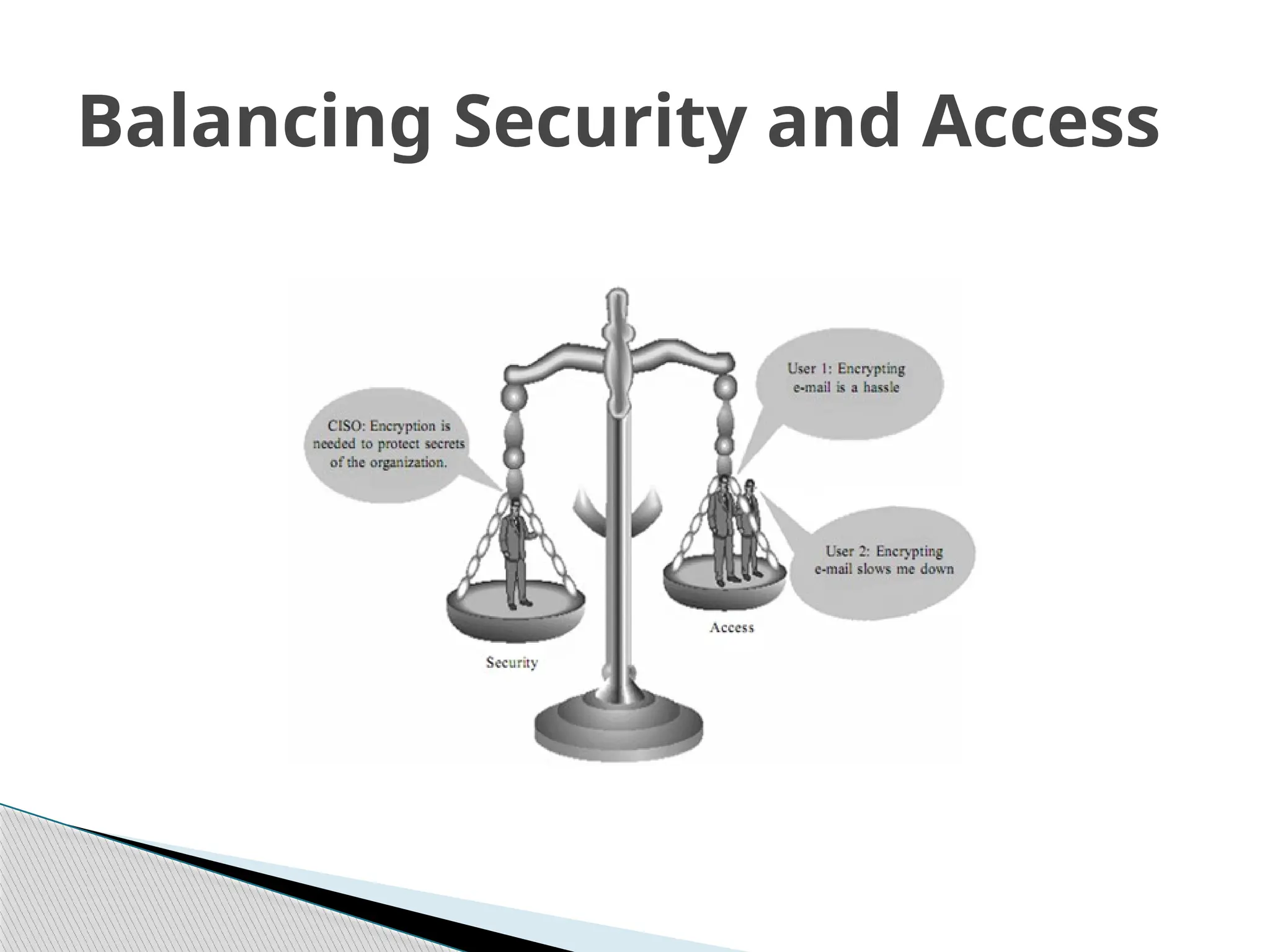
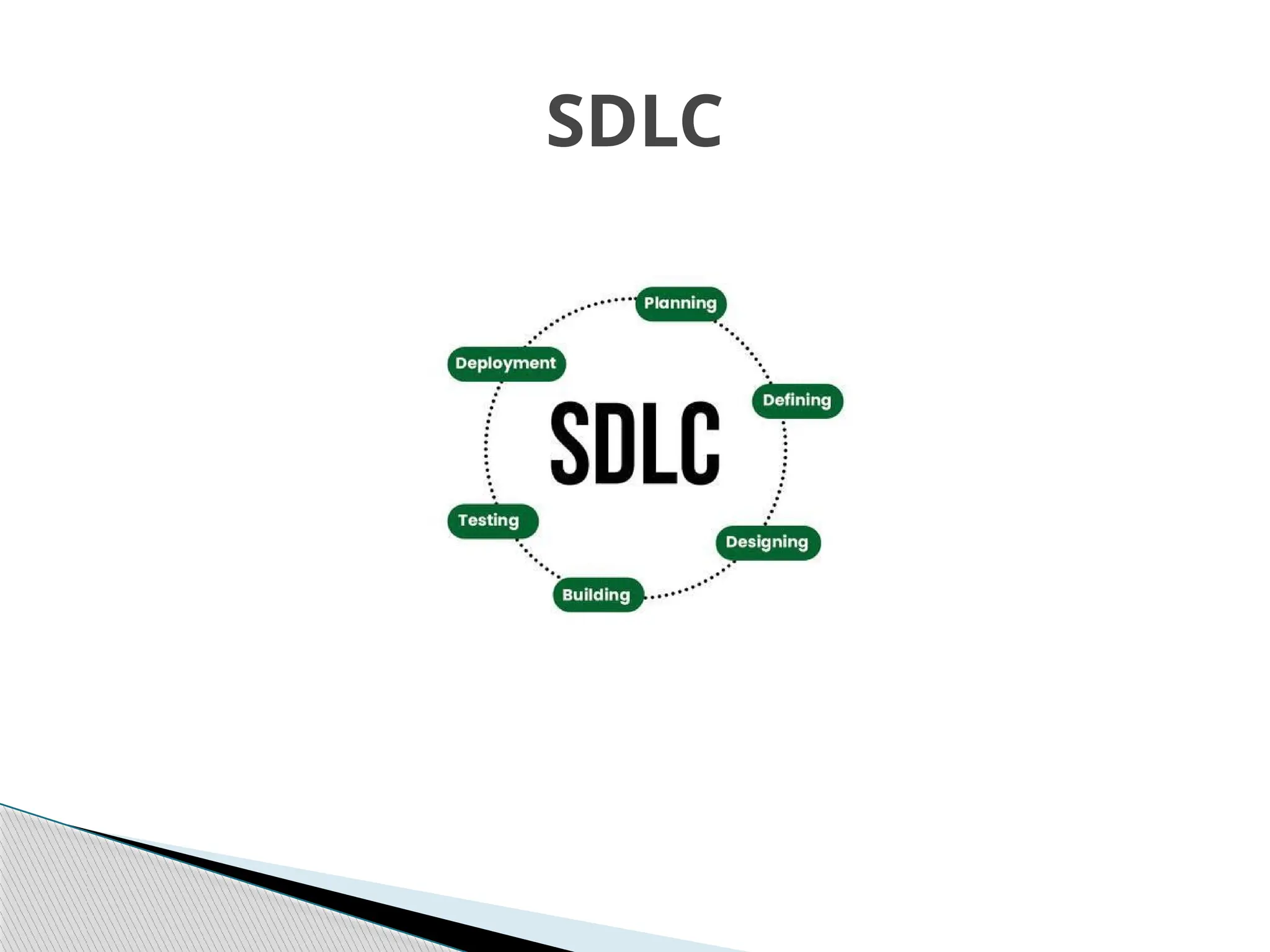
The document outlines the evolution of data and information security, detailing its history from the development of mainframes to the modern-day necessity for layered security systems. It discusses components of security, including physical, personnel, operation, communication, network, and information security, as well as evolving threats and the need for robust policies and training. Key concepts such as the CIA triangle (confidentiality, integrity, availability) and the components of information security are emphasized for organizational protection.