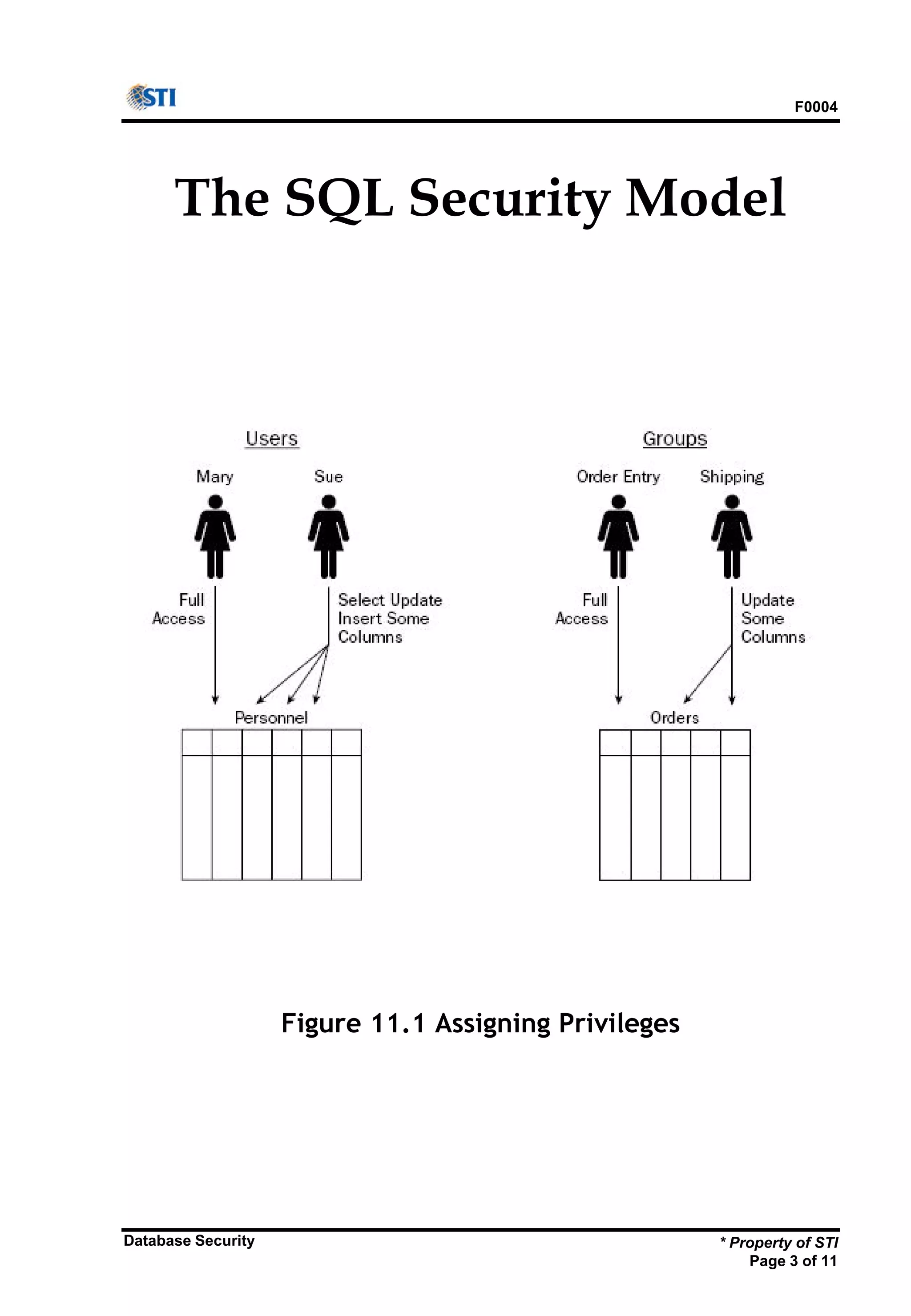
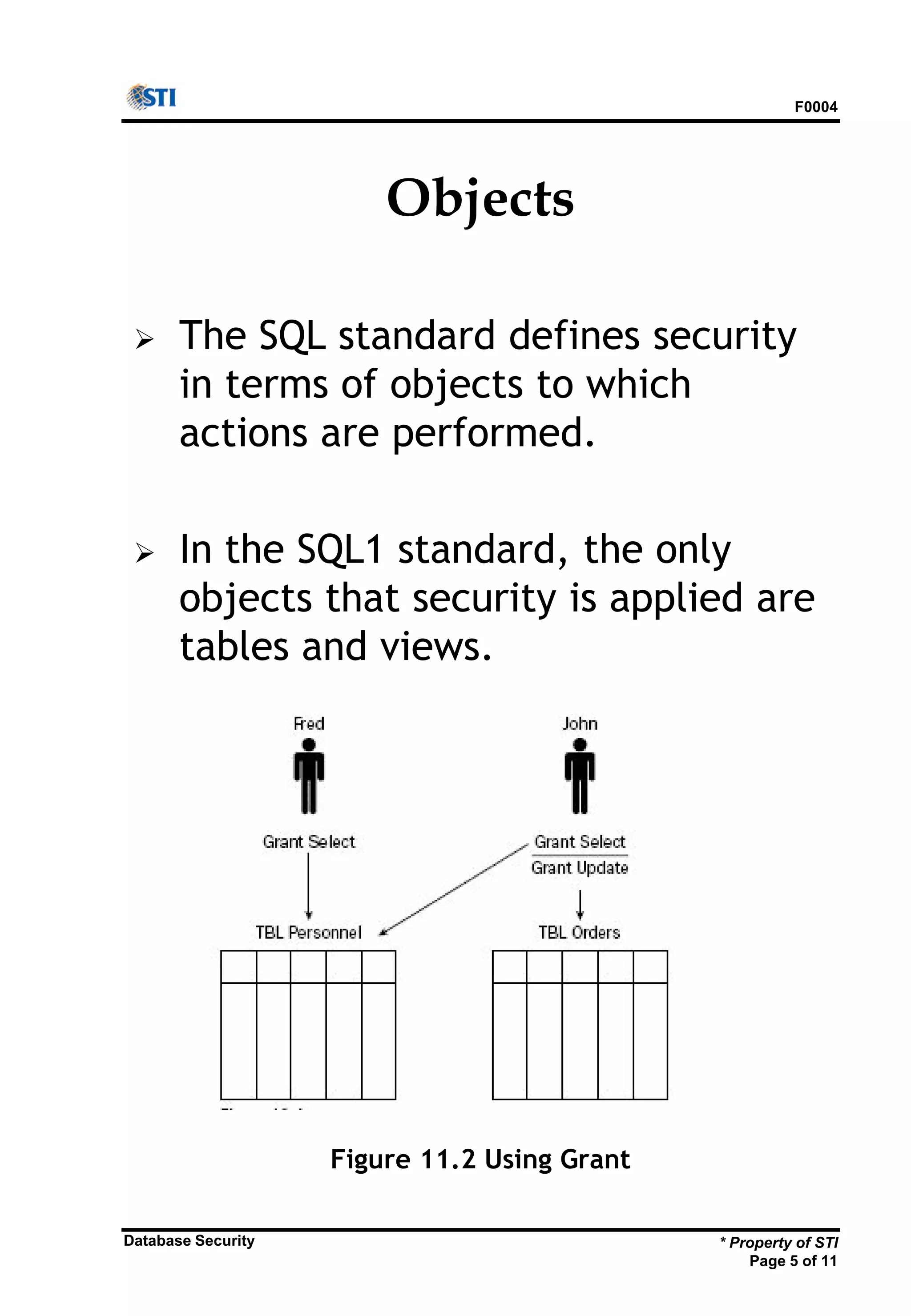
The document outlines key aspects of database security, emphasizing the importance of restricting data access and modifications to qualified users only. It discusses the SQL security model, which includes user IDs, objects involved, and different types of privileges associated with data operations. Additionally, it provides syntax examples for granting and revoking user privileges within various database management systems.





![F0004
* Property of STI
Page 8 of 11
Database Security
Adding Users
Some DBMSs have SQL statements,
extensions to the SQL standard
specific to that DBMS that allow
creating users.
In Oracle the statement is as
follow:
CREATE USER username
IDENTIFIED {BY password |
EXTERNALLY | GLOBALLY AS
external_name}
Options
In Sybase, the syntax is as follow:
GRANT CONNECT TO userid , . . .
[ AT starting-id ]
IDENTIFIED BY password, . . .](https://image.slidesharecdn.com/09ohpslides1-150908153245-lva1-app6891/75/Database-Security-Slide-Handout-8-2048.jpg)
![F0004
* Property of STI
Page 9 of 11
Database Security
Granting Privileges
The basic GRANT statement is used to
grant security privileges on database
objects to specific users or, in some DBMS
implementations, to groups.
The syntax is as follow:
GRANT {
ALL [ PRIVILEGES ],
ALTER,
DELETE,
INSERT,
REFERENCES [ ( column-
name, . . . ) ],
SELECT [ ( column-name, . . . ) ],
UPDATE [ ( column-name, . . . ) ],
}
ON [ owner.]table-name
TO userid , . . .
[ WITH GRANT OPTION ]
[ FROM userid ]](https://image.slidesharecdn.com/09ohpslides1-150908153245-lva1-app6891/75/Database-Security-Slide-Handout-9-2048.jpg)

![F0004
* Property of STI
Page 11 of 11
Database Security
Revoking Privileges
Use the REVOKE statement if you have granted
privileges and later you need to revoke these
privileges.
Syntax 1
REVOKE special-priv , . . . FROM
userid , . . .
special-priv :
CONNECT
Syntax 2
REVOKE table-priv , . . . ON
[ owner.]table-name FROM
userid , . . .
table-priv :
ALL [PRIVILEGES]
| ALTER
| DELETE
| INSERT
| REFERENCES [ ( column-name, . . . ) ]
| SELECT [ ( column-name, . . . ) ]
| UPDATE [ ( column-name, . . . ) ]](https://image.slidesharecdn.com/09ohpslides1-150908153245-lva1-app6891/75/Database-Security-Slide-Handout-11-2048.jpg)