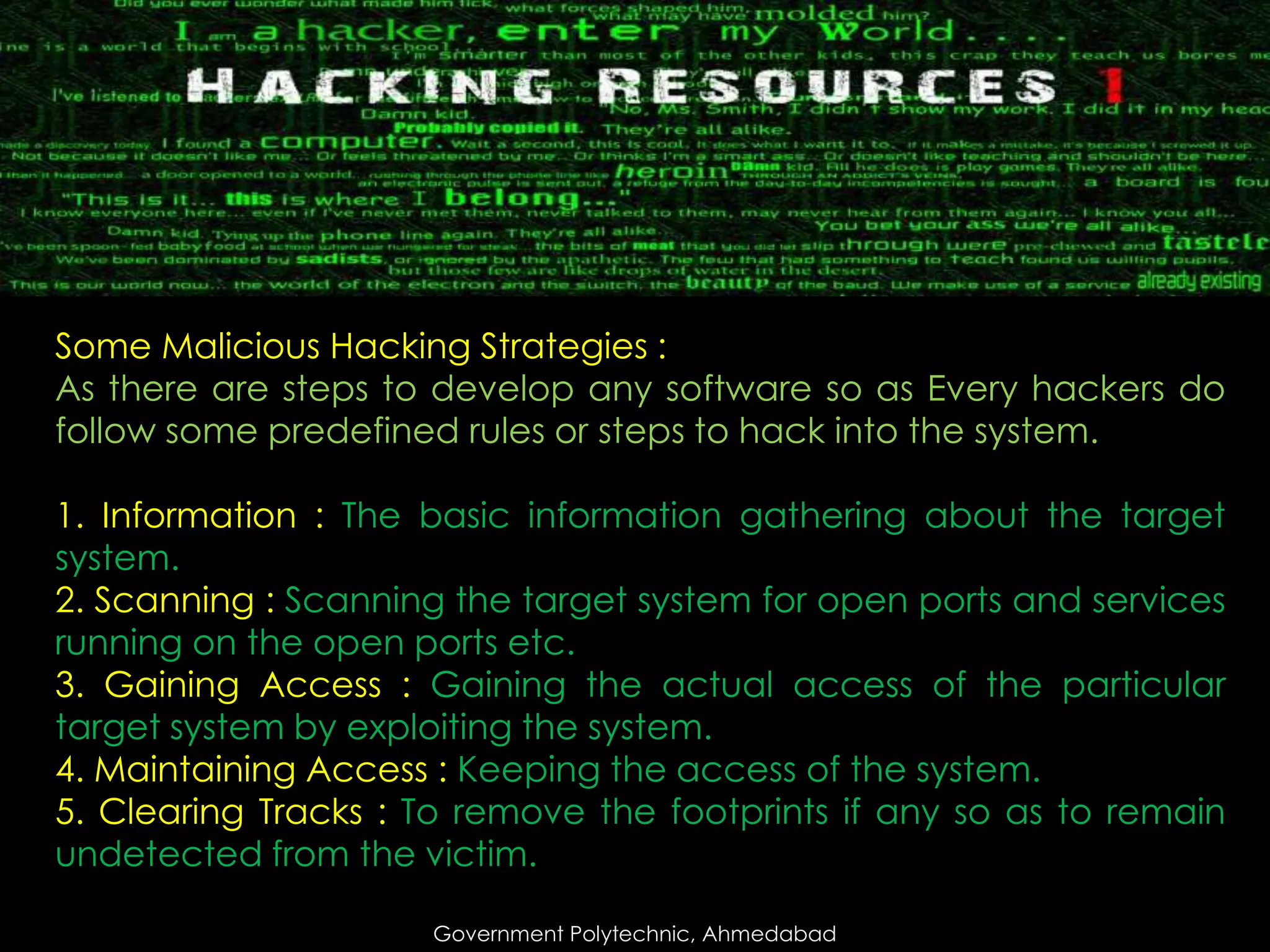
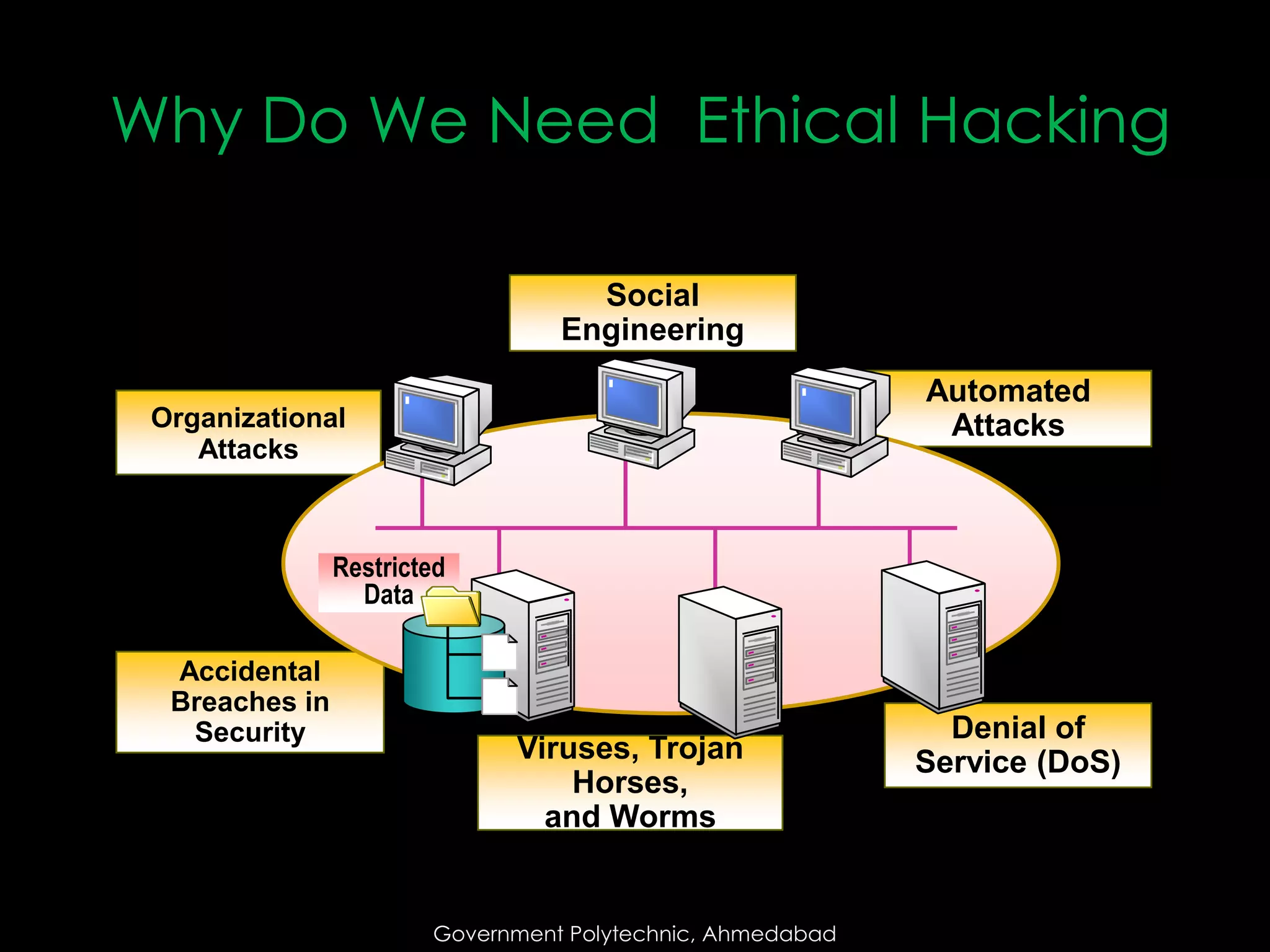
The document outlines different types of hackers, including white hats (ethical hackers), grey hats (hybrids), black hats (malicious hackers), phreakers, script kiddies, and hacktivists. It discusses the stages of malicious hacking and the importance of ethical hacking, emphasizing the need for security professionals to prevent attacks. It also highlights the skills and training required to become an ethical hacker and the job opportunities available in this field.