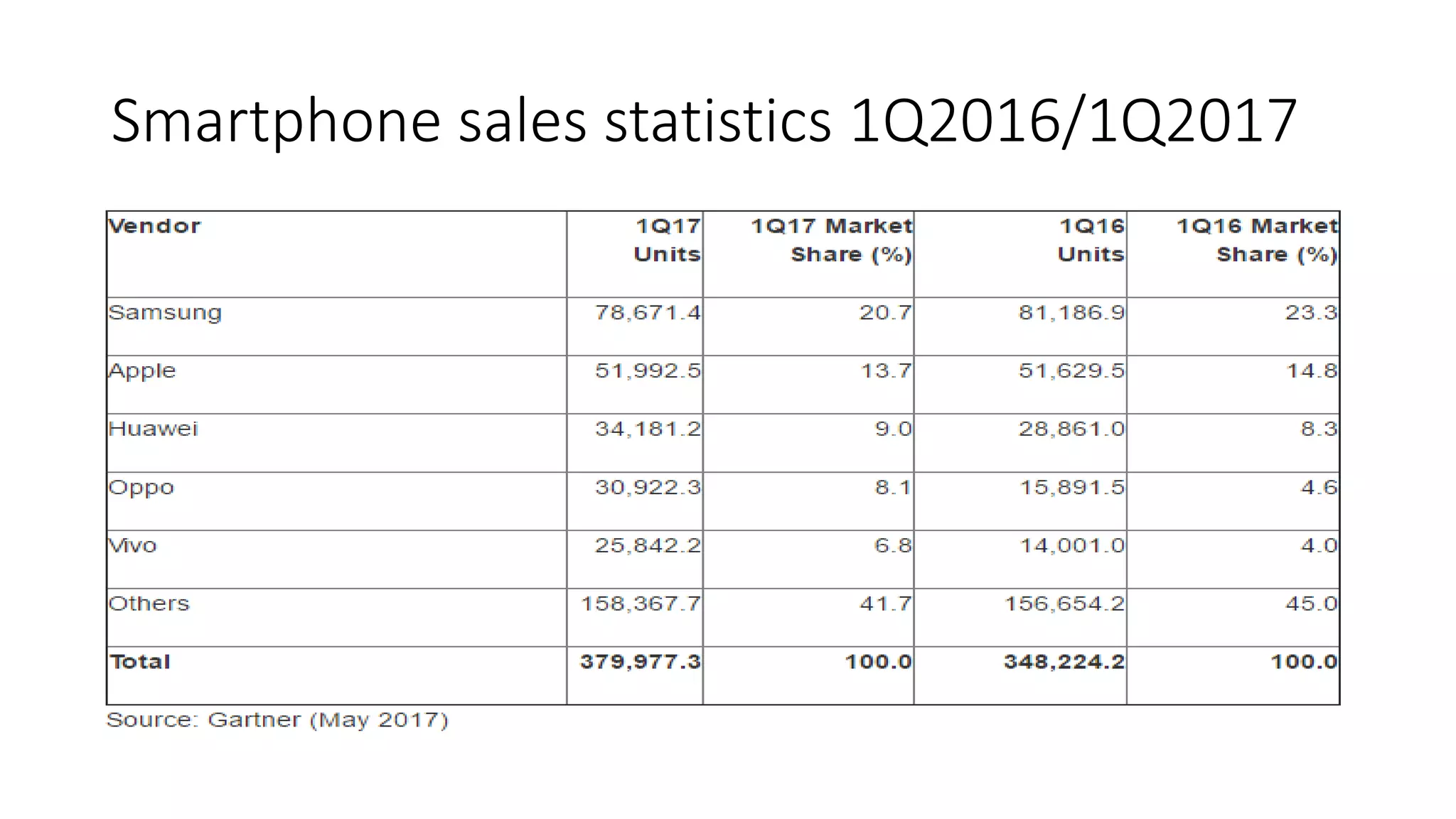
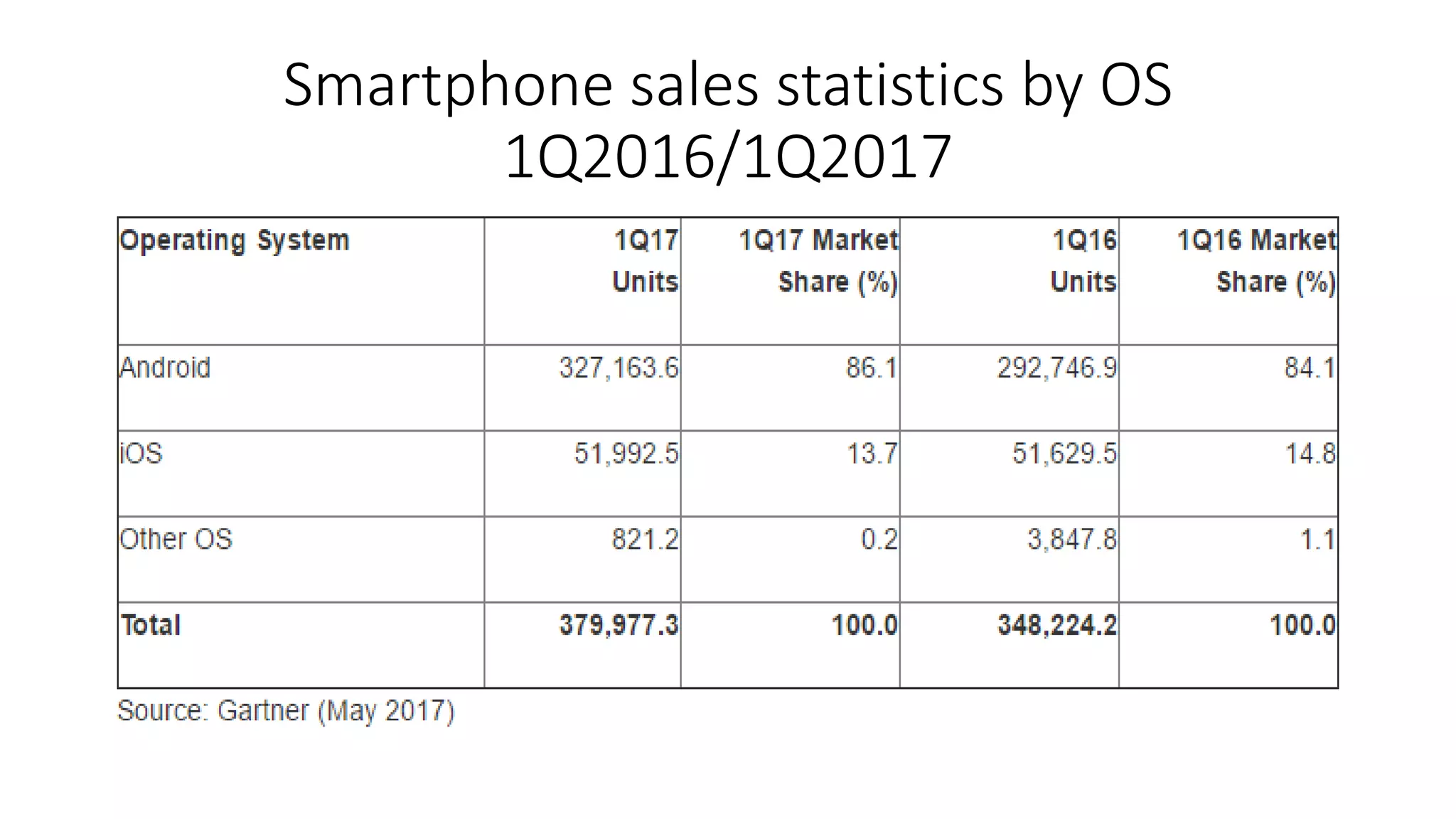
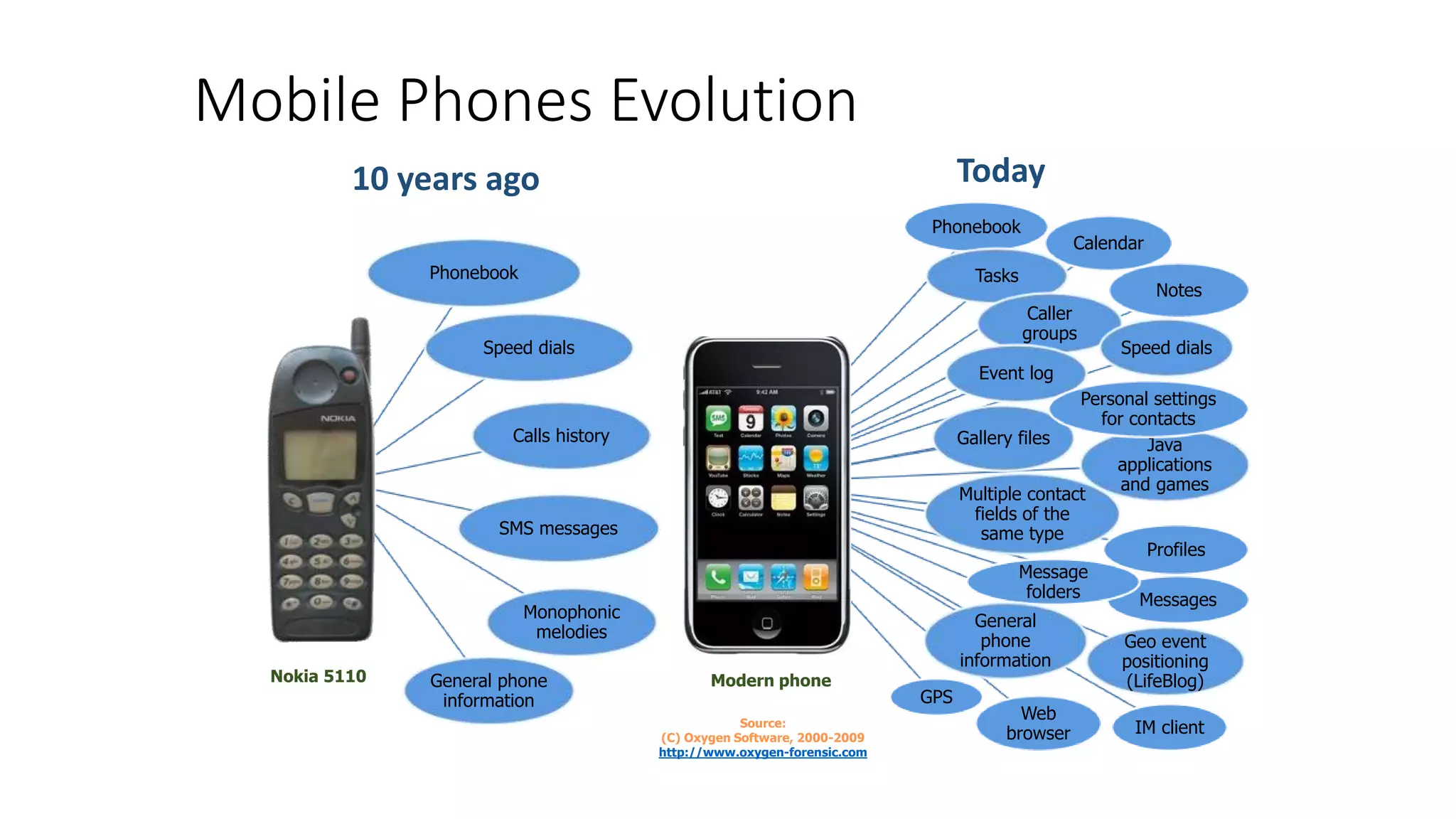
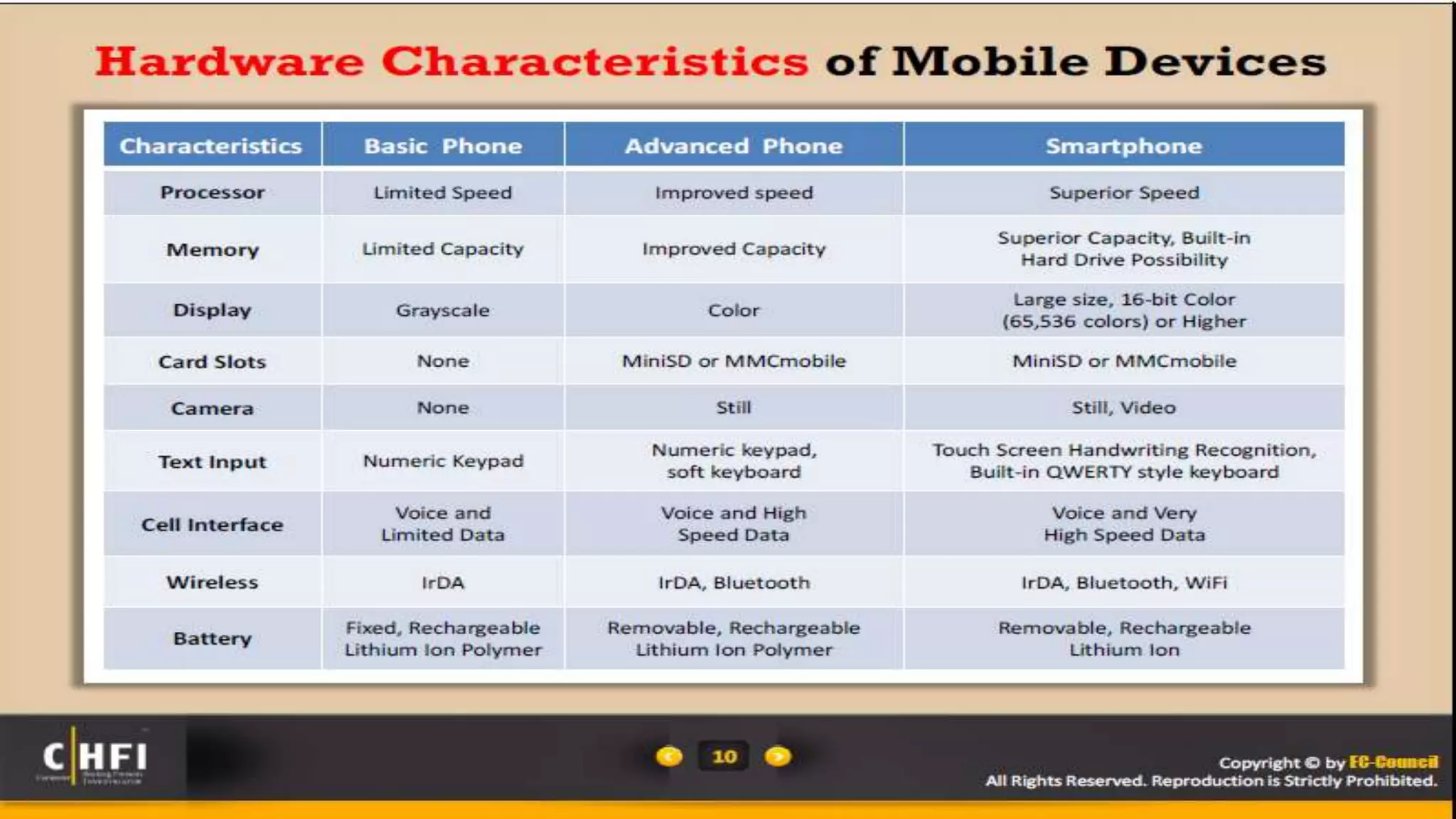
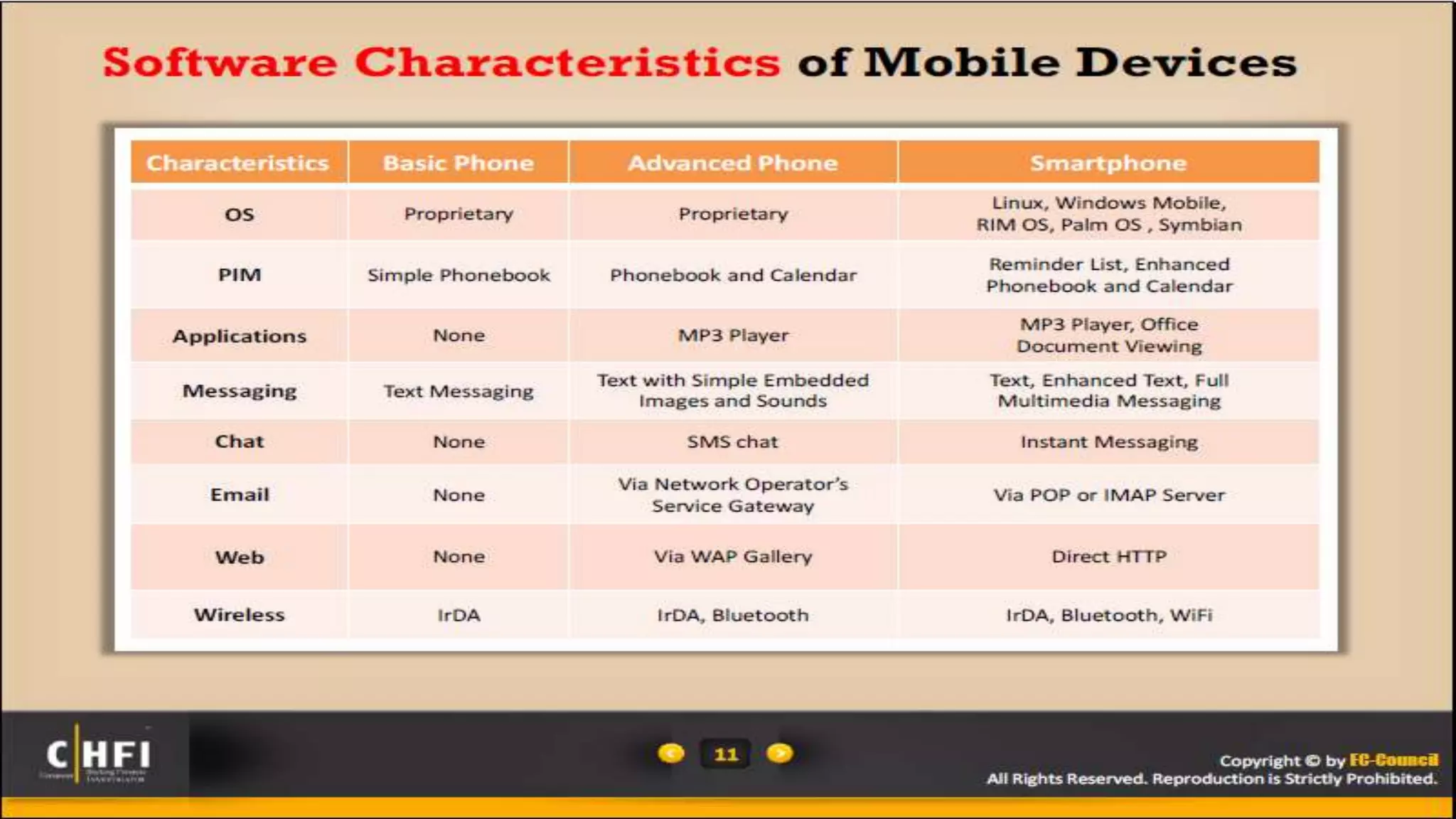
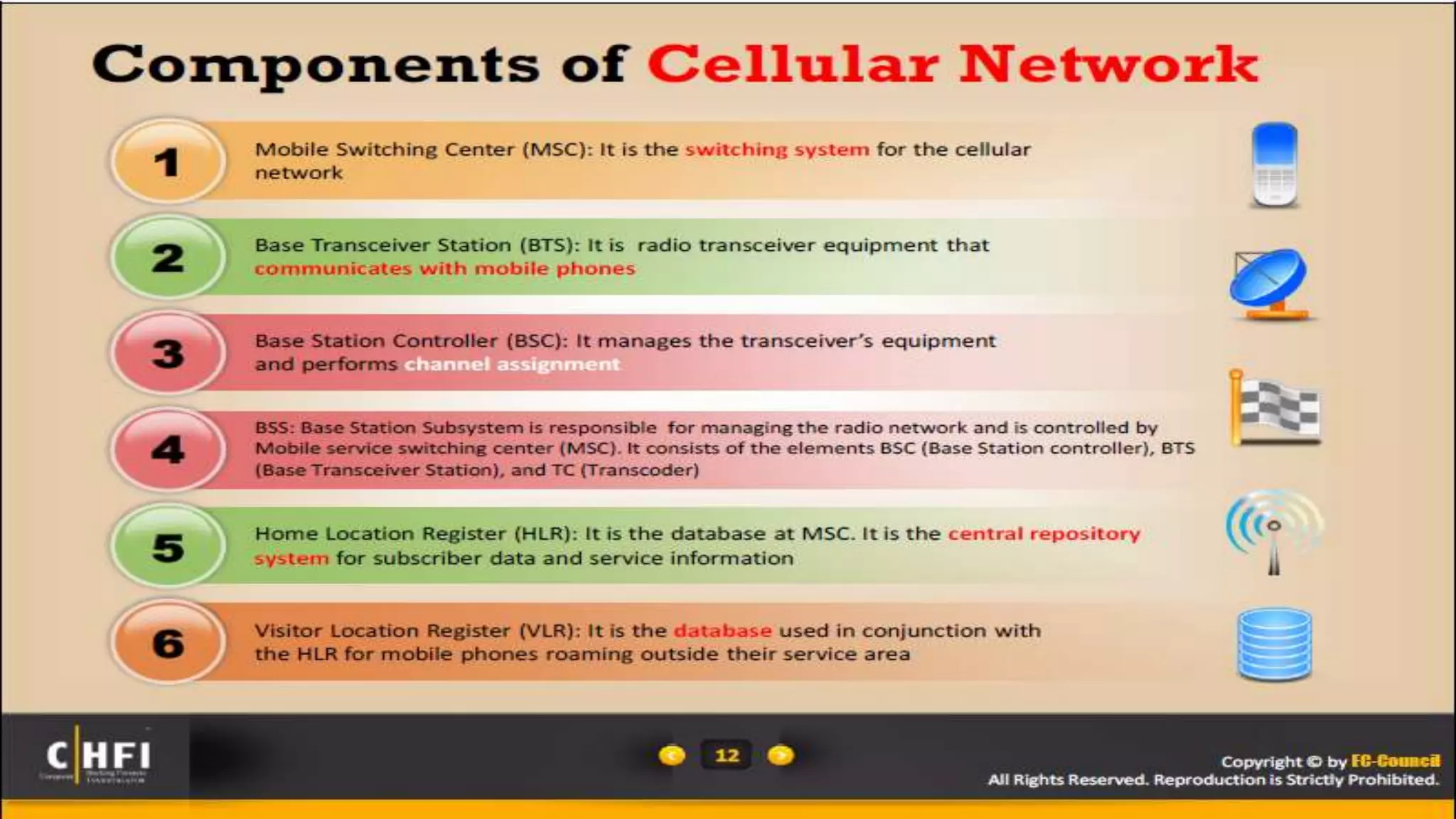
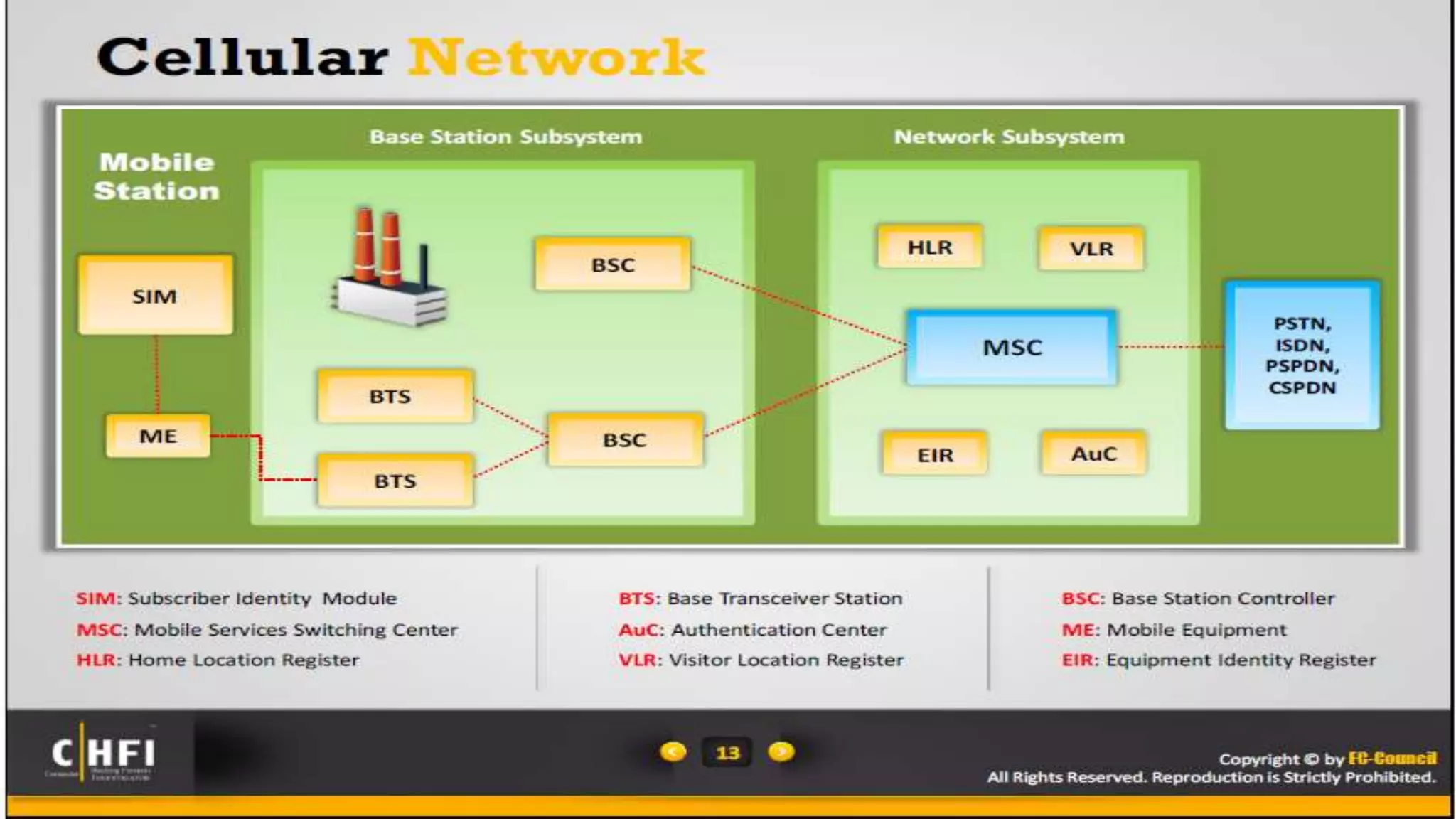
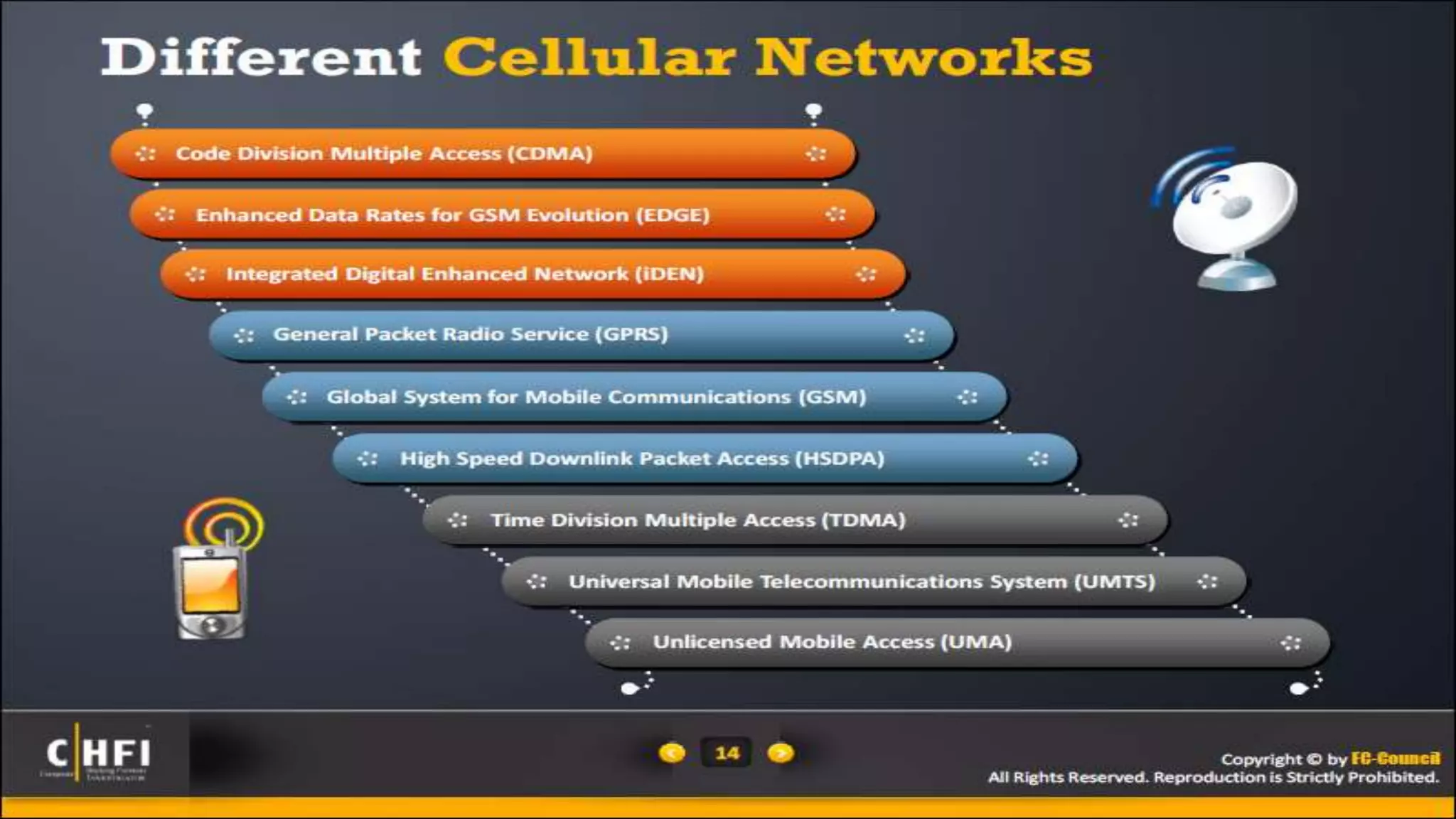
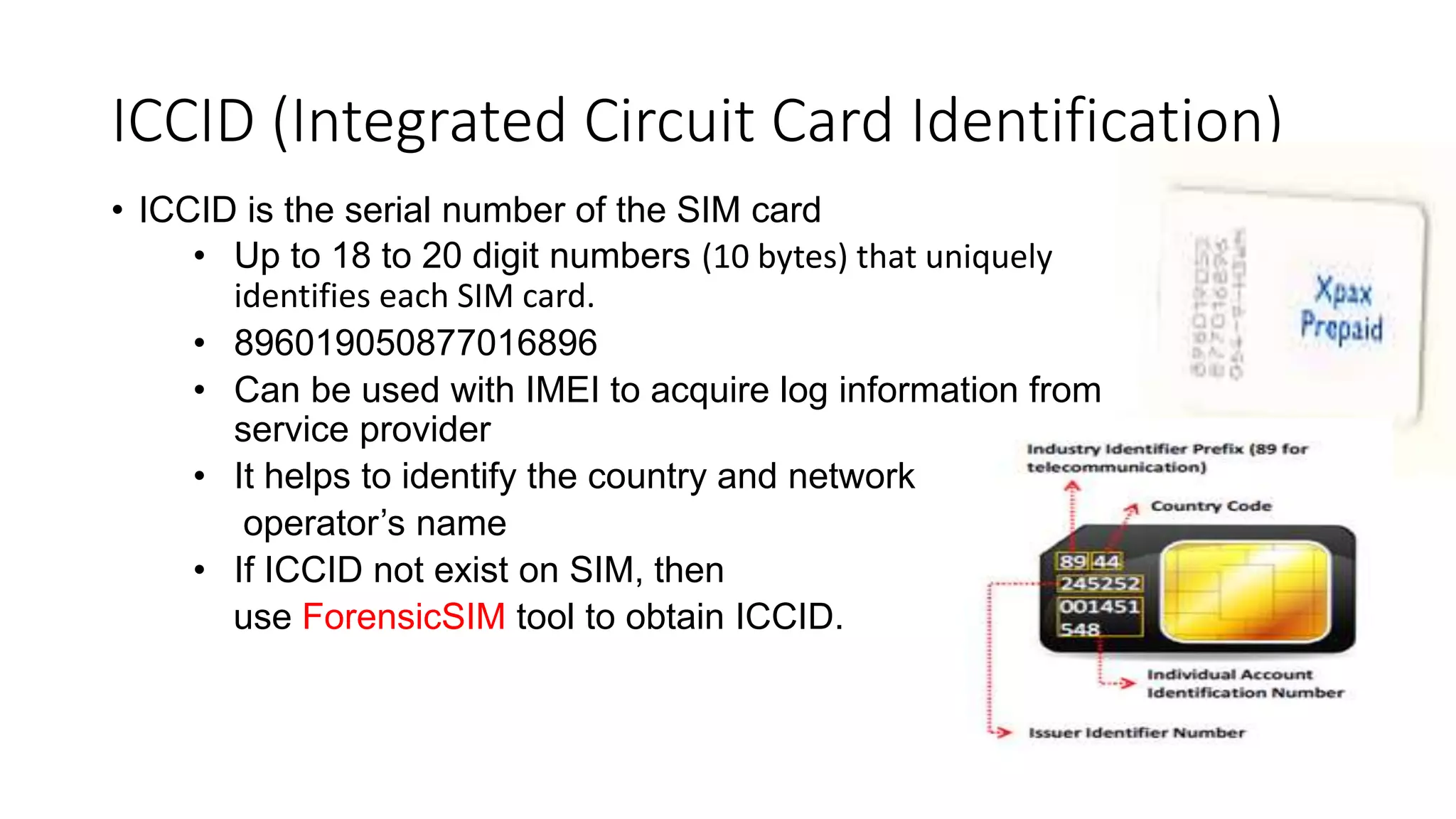
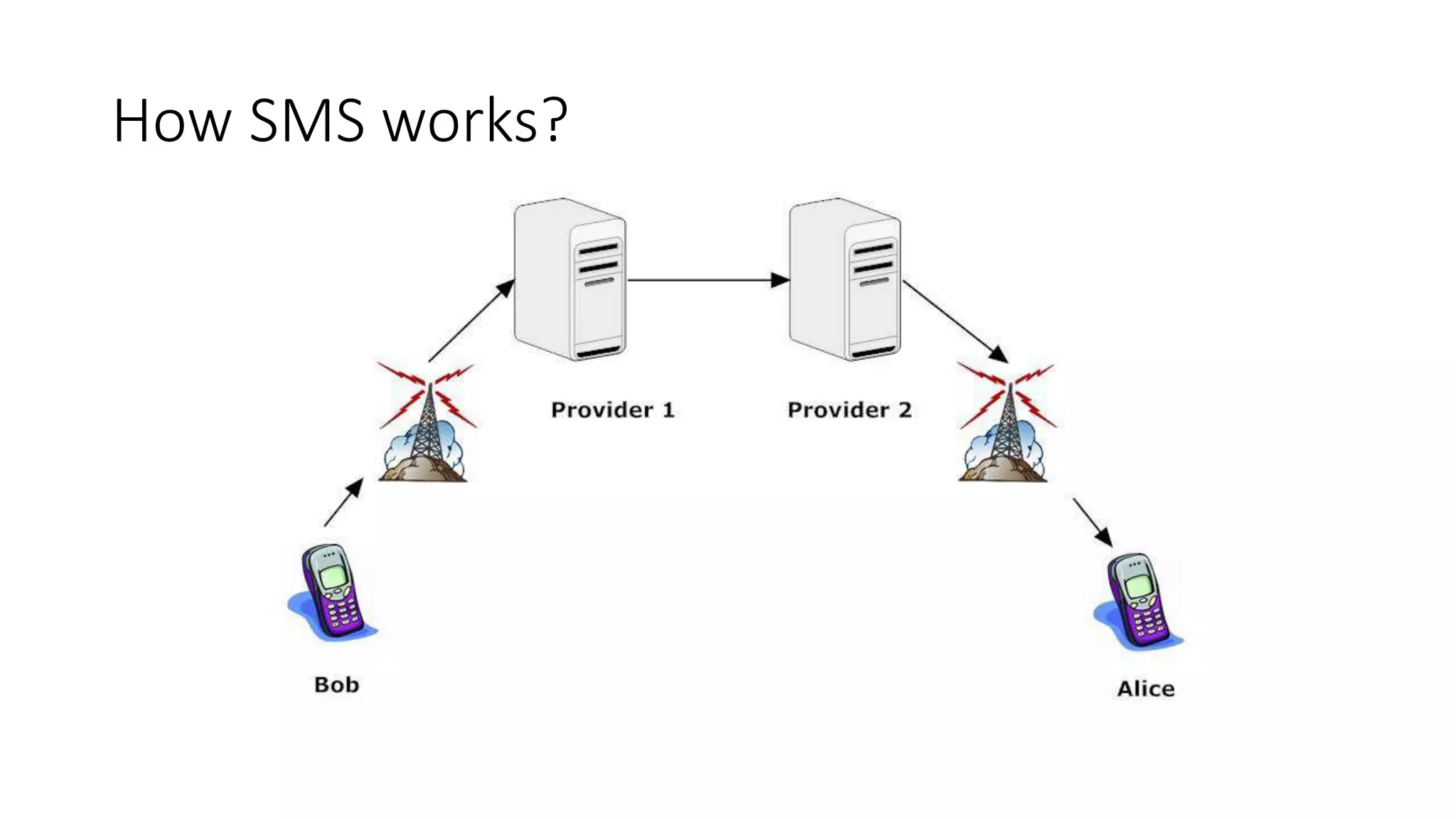
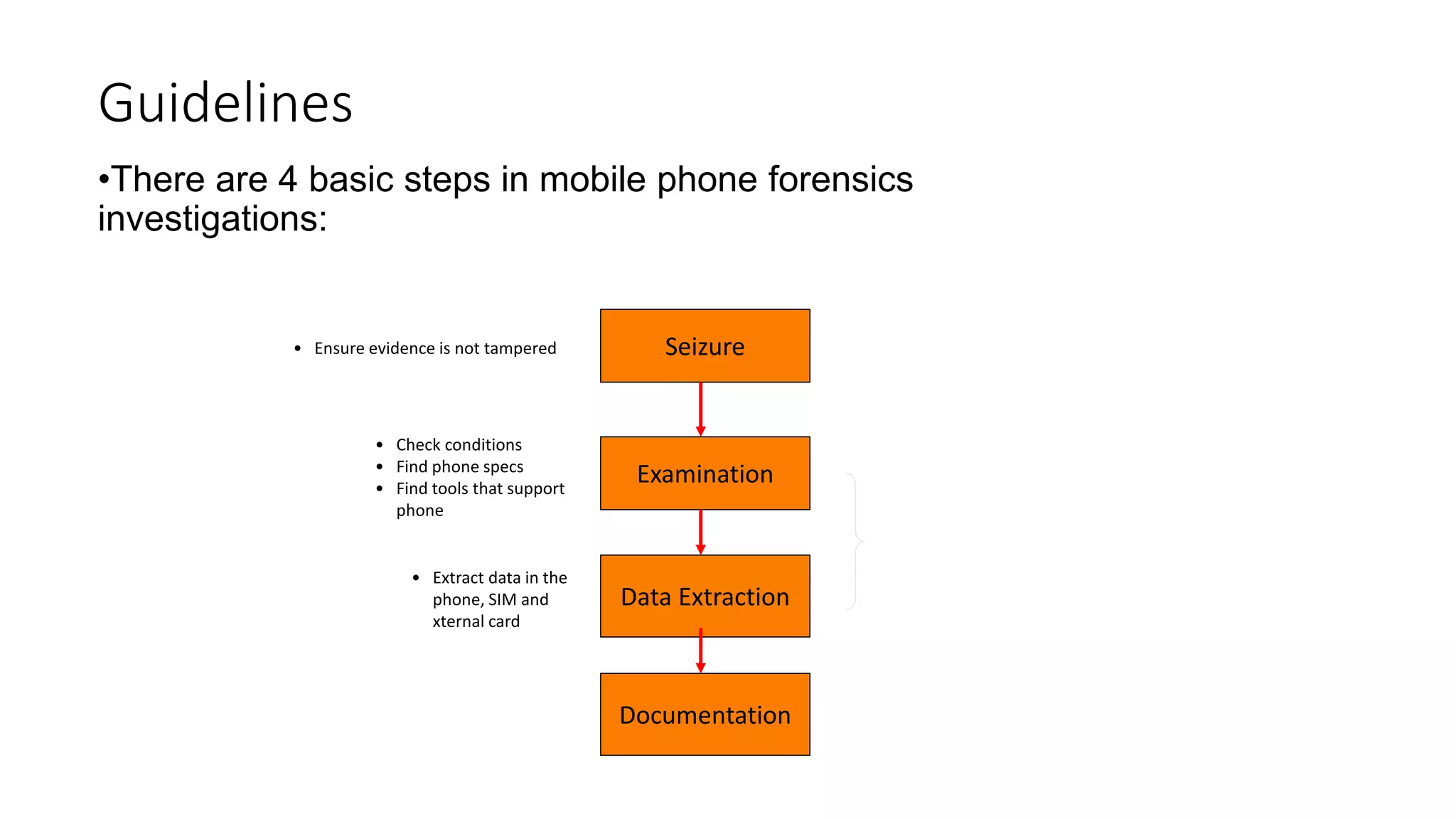
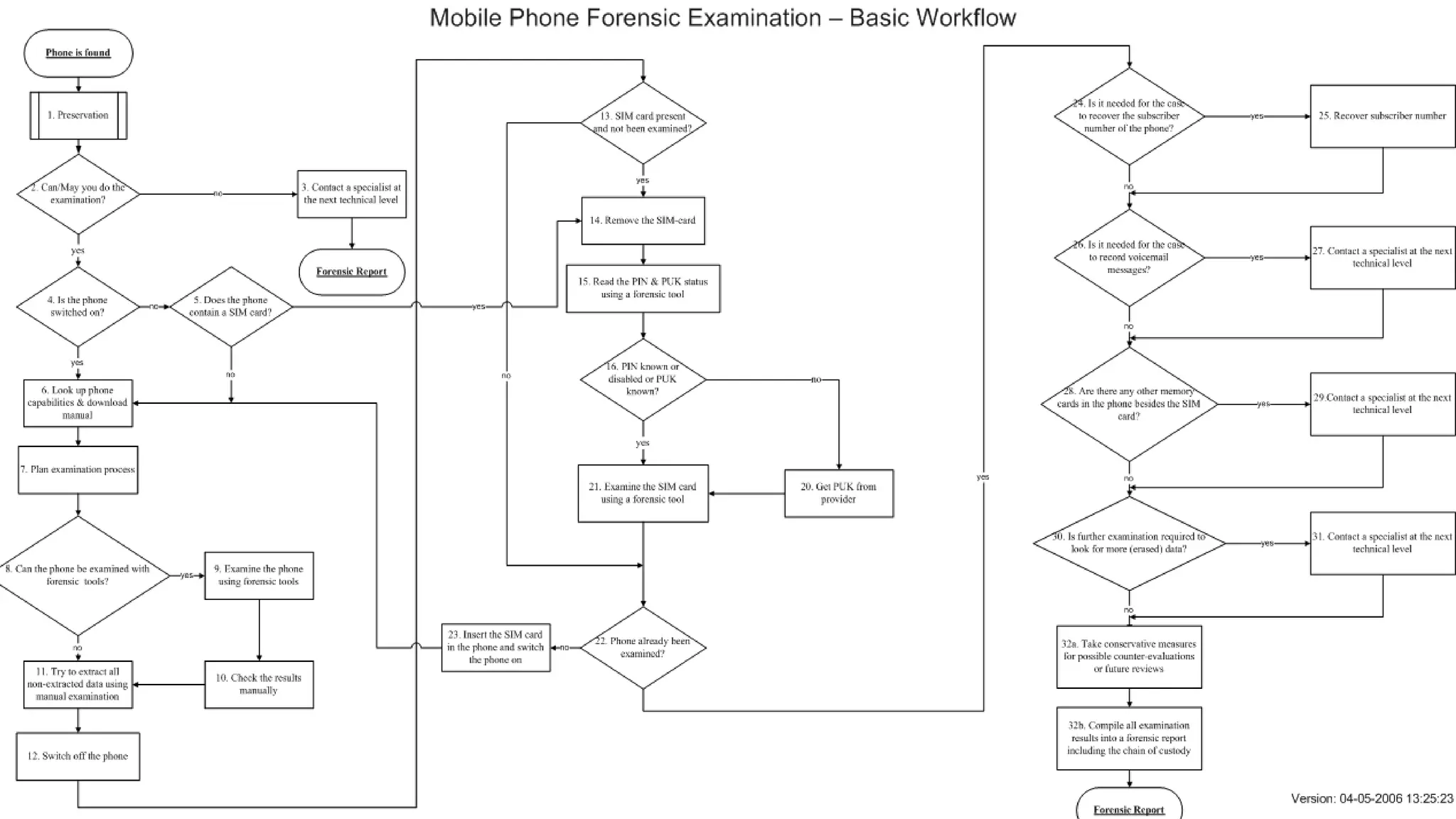
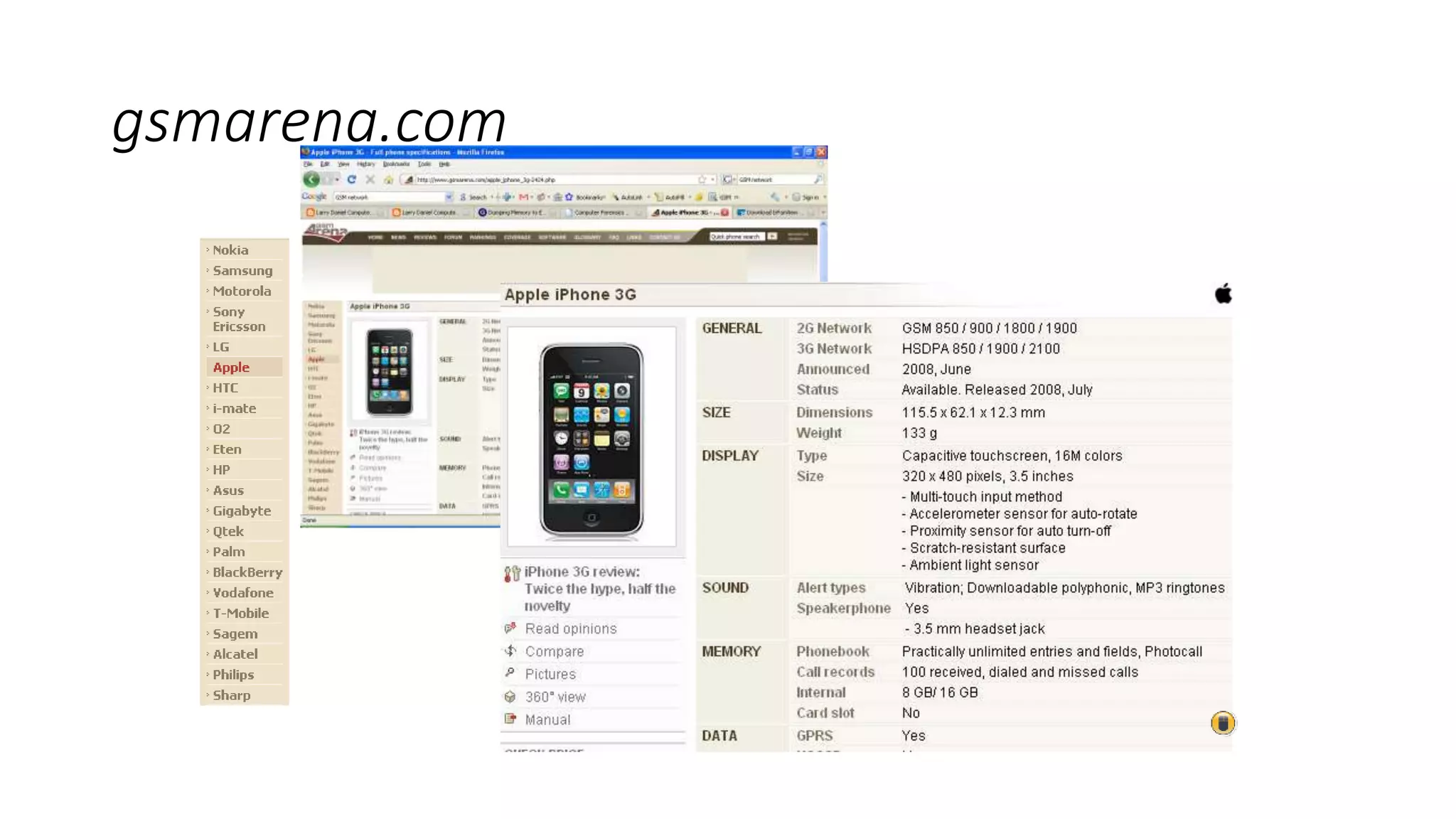
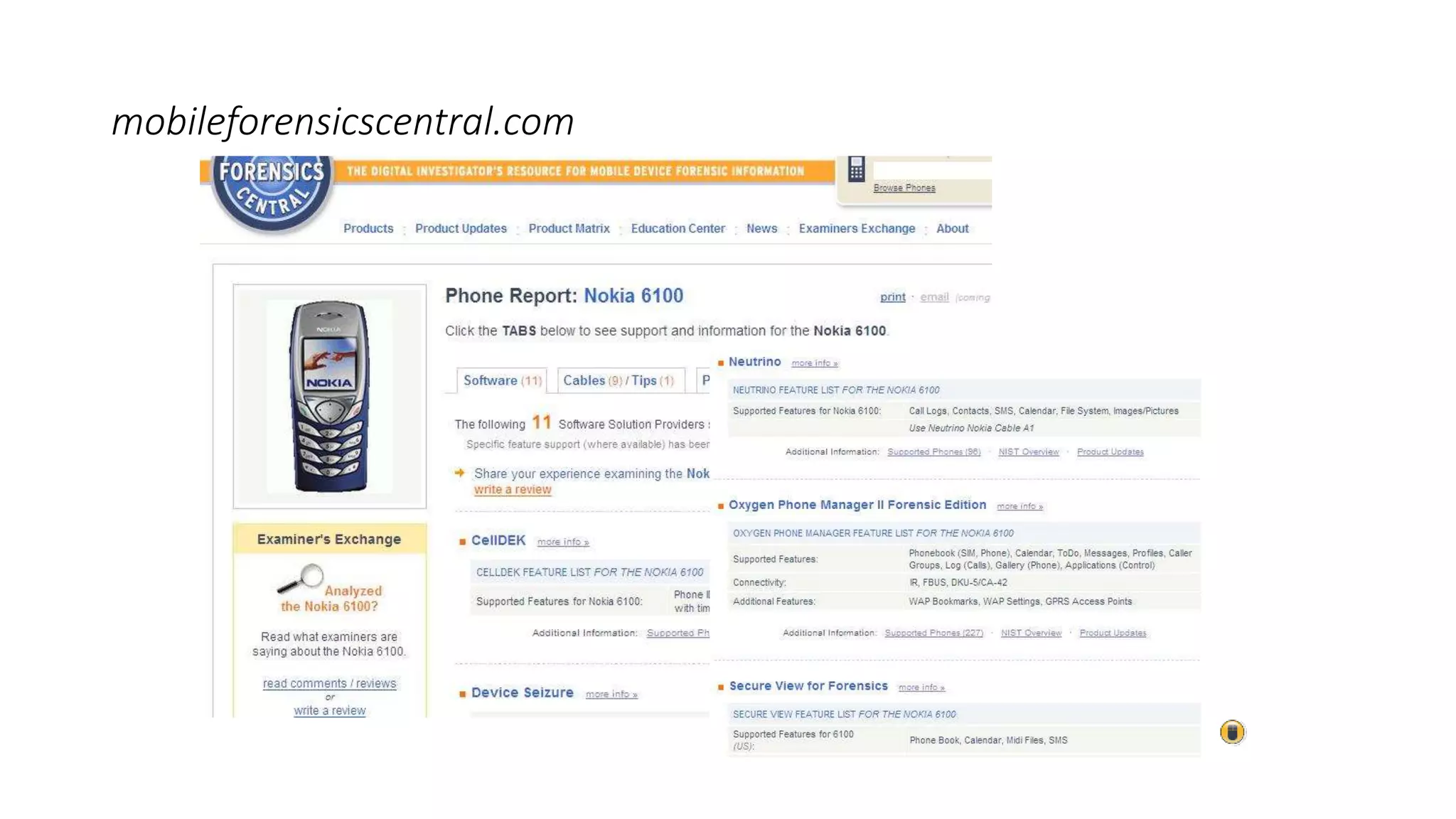
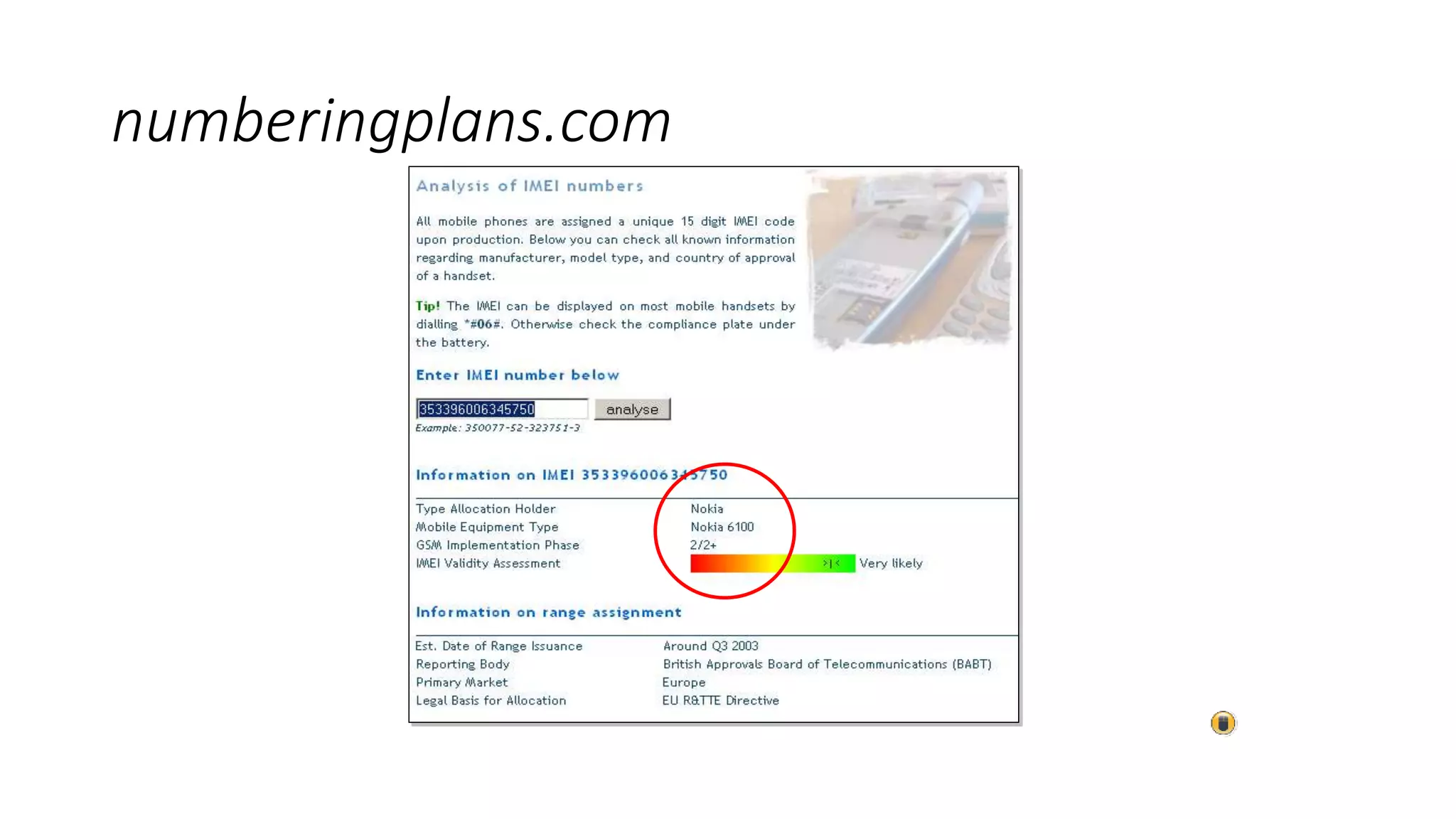
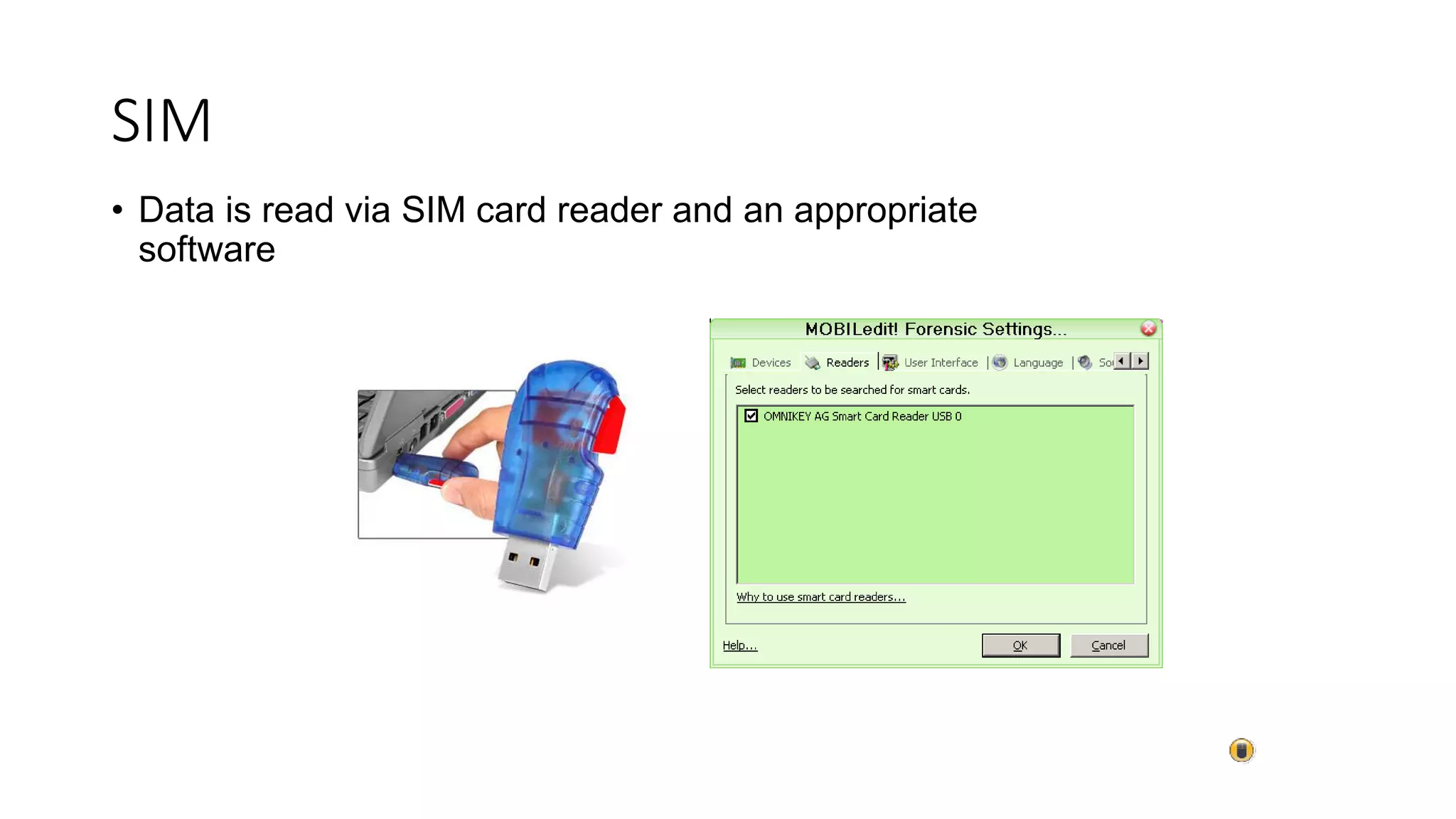
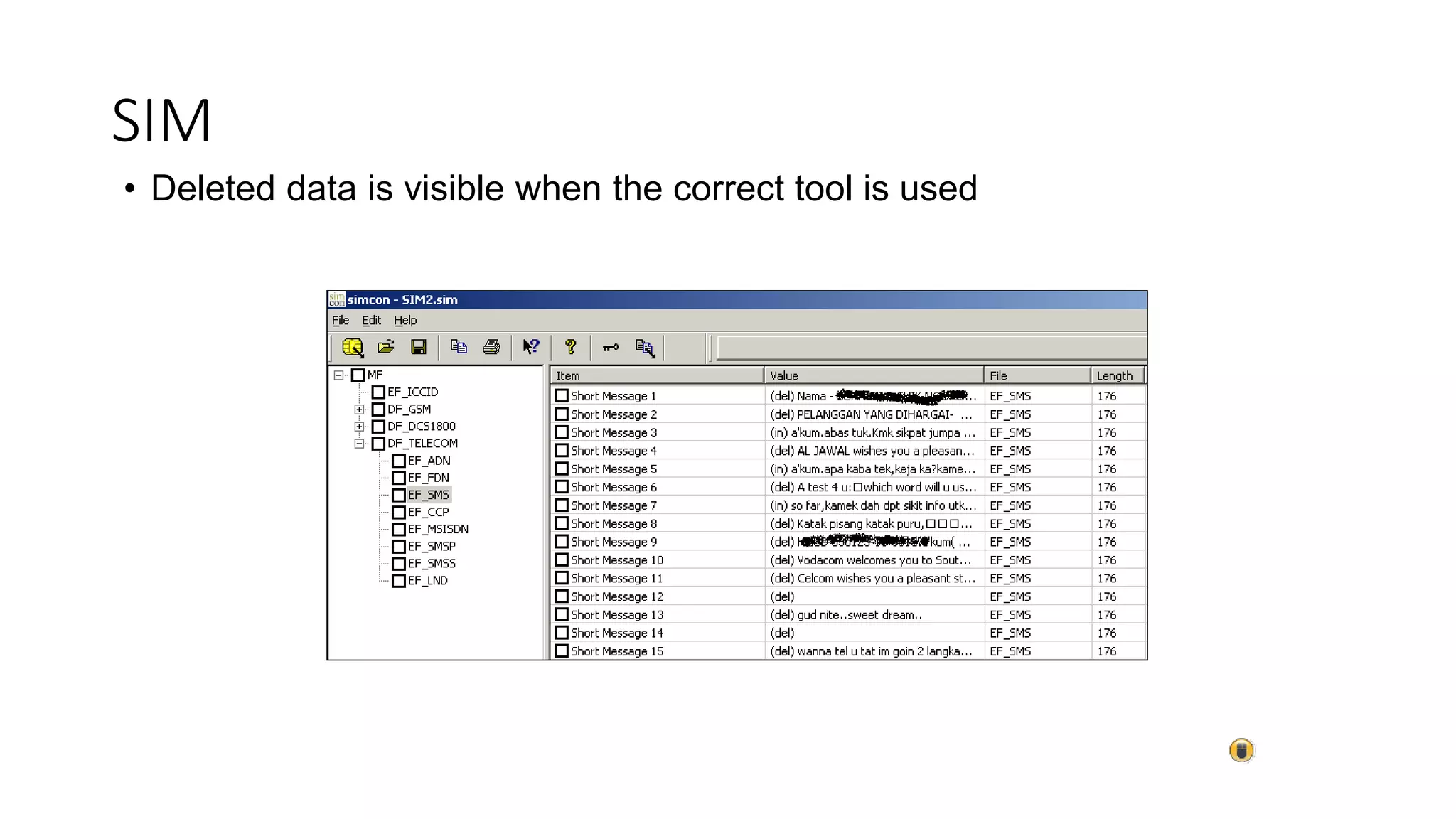
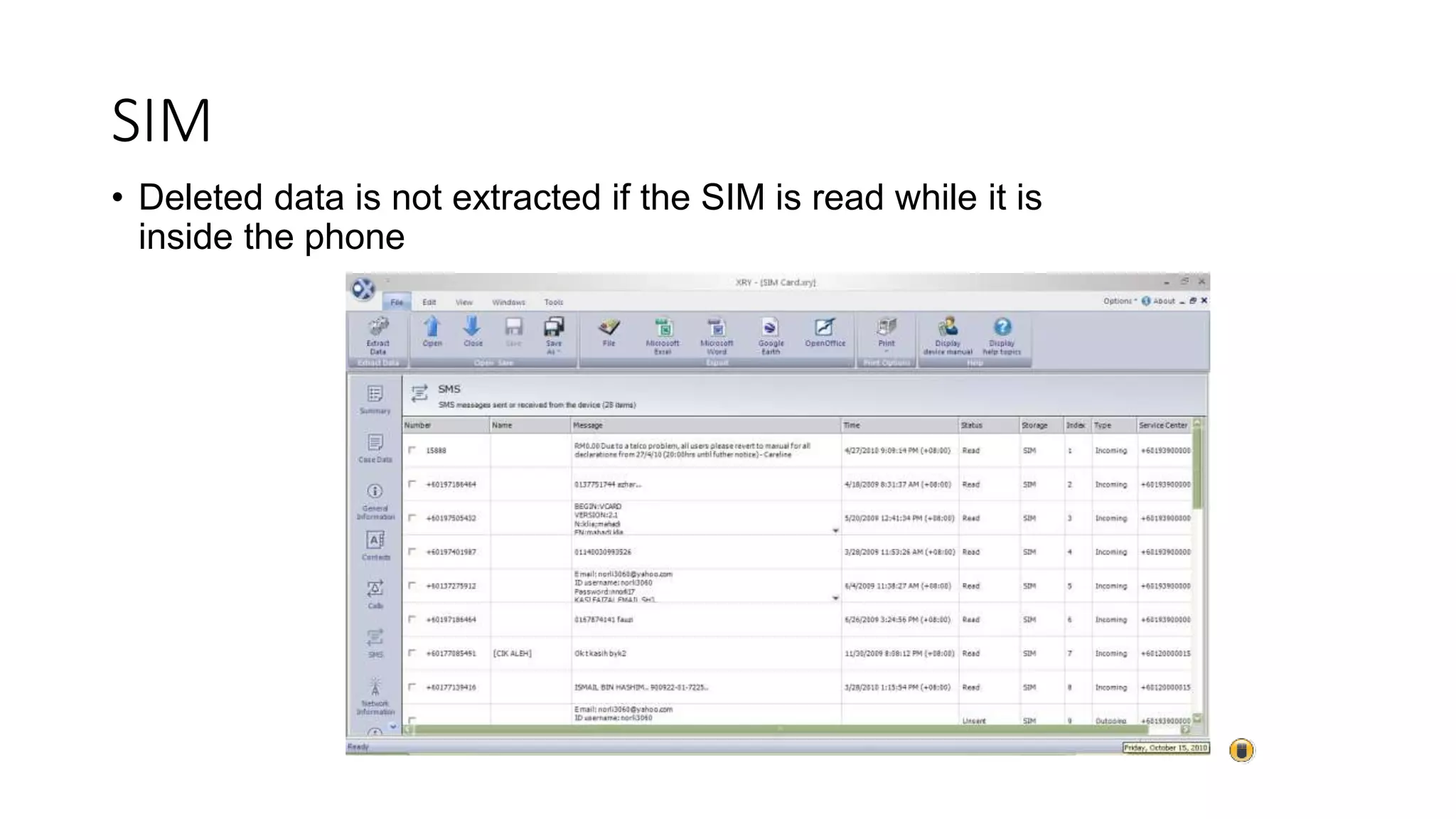
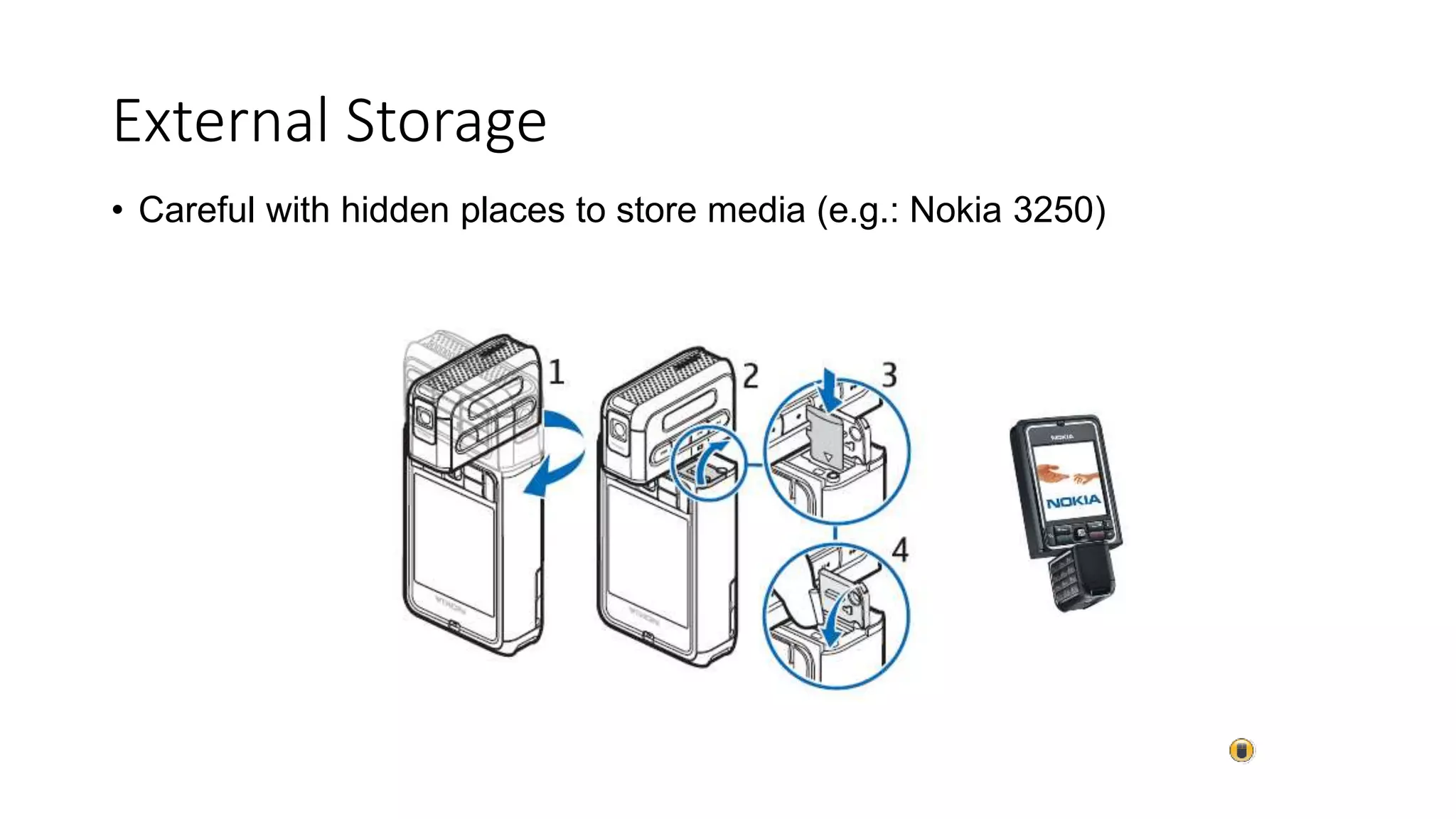
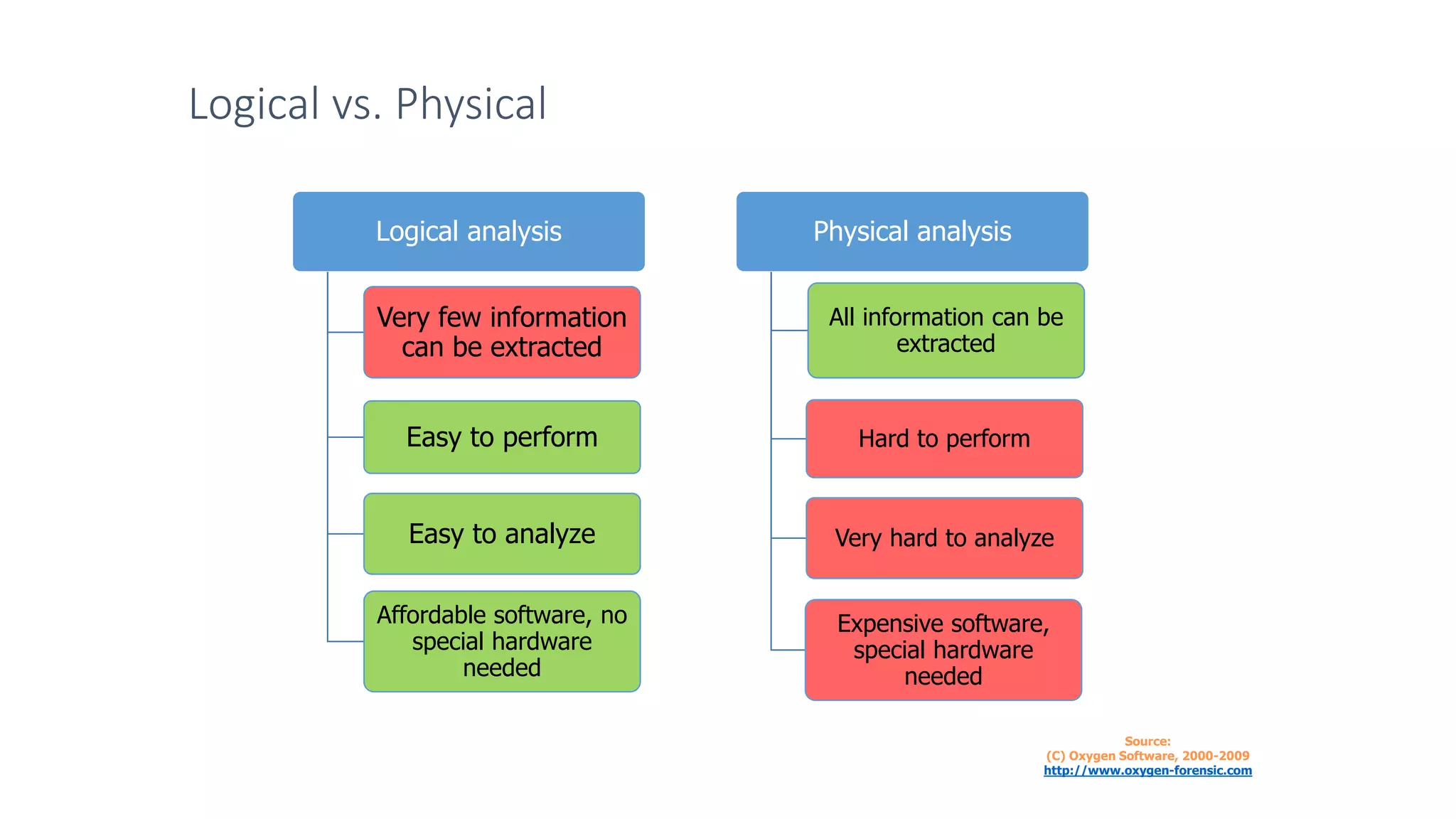
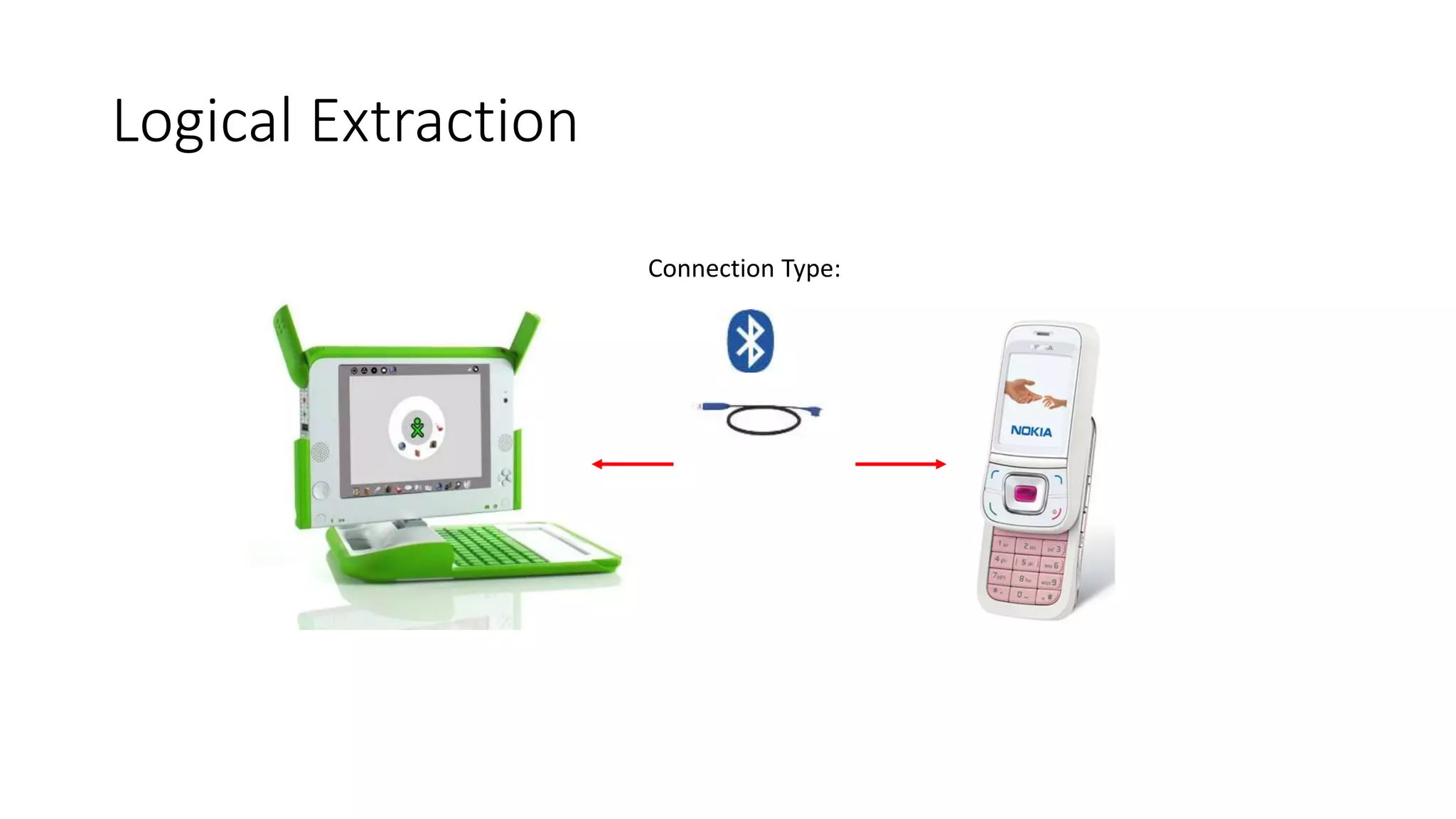
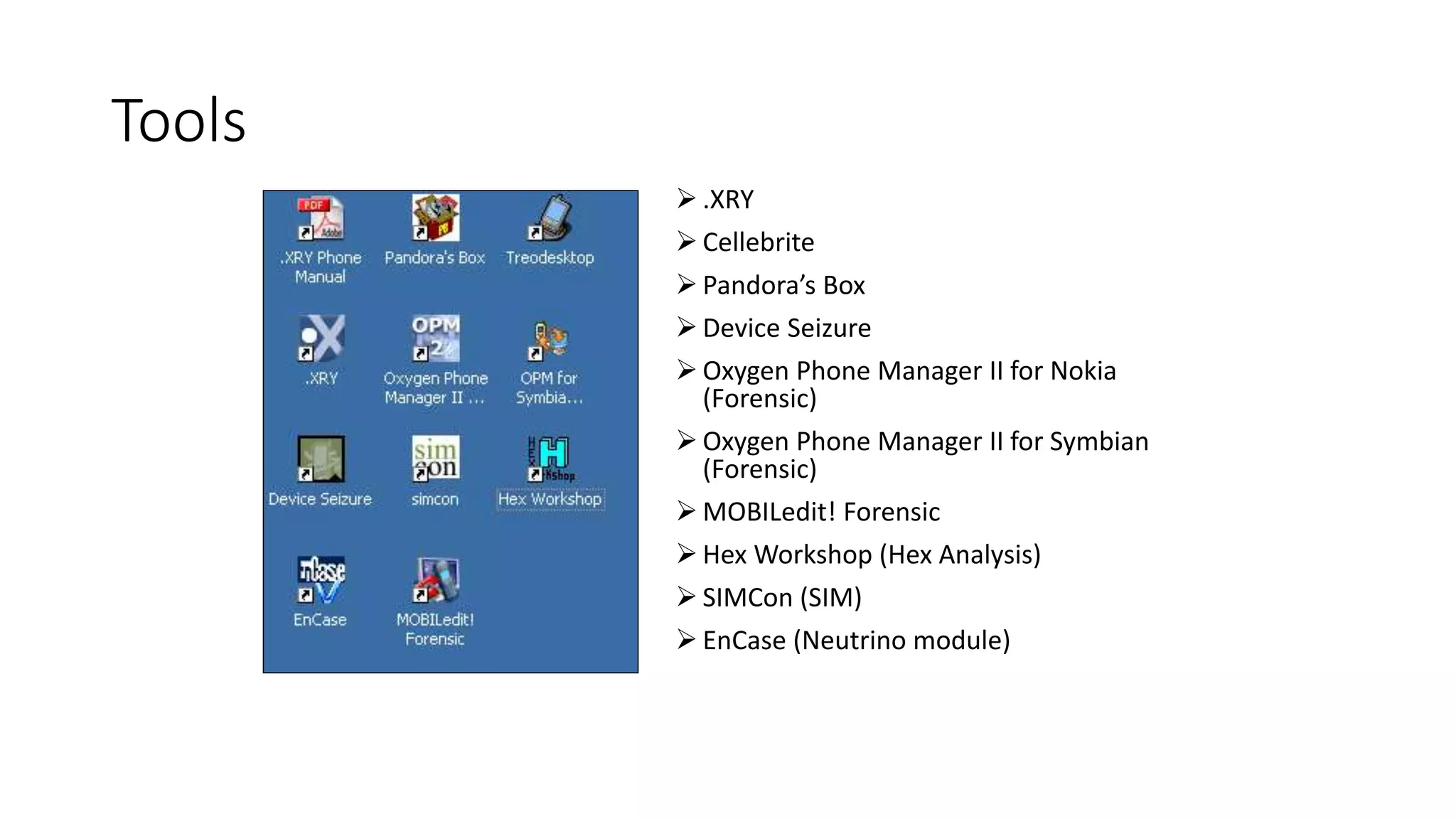
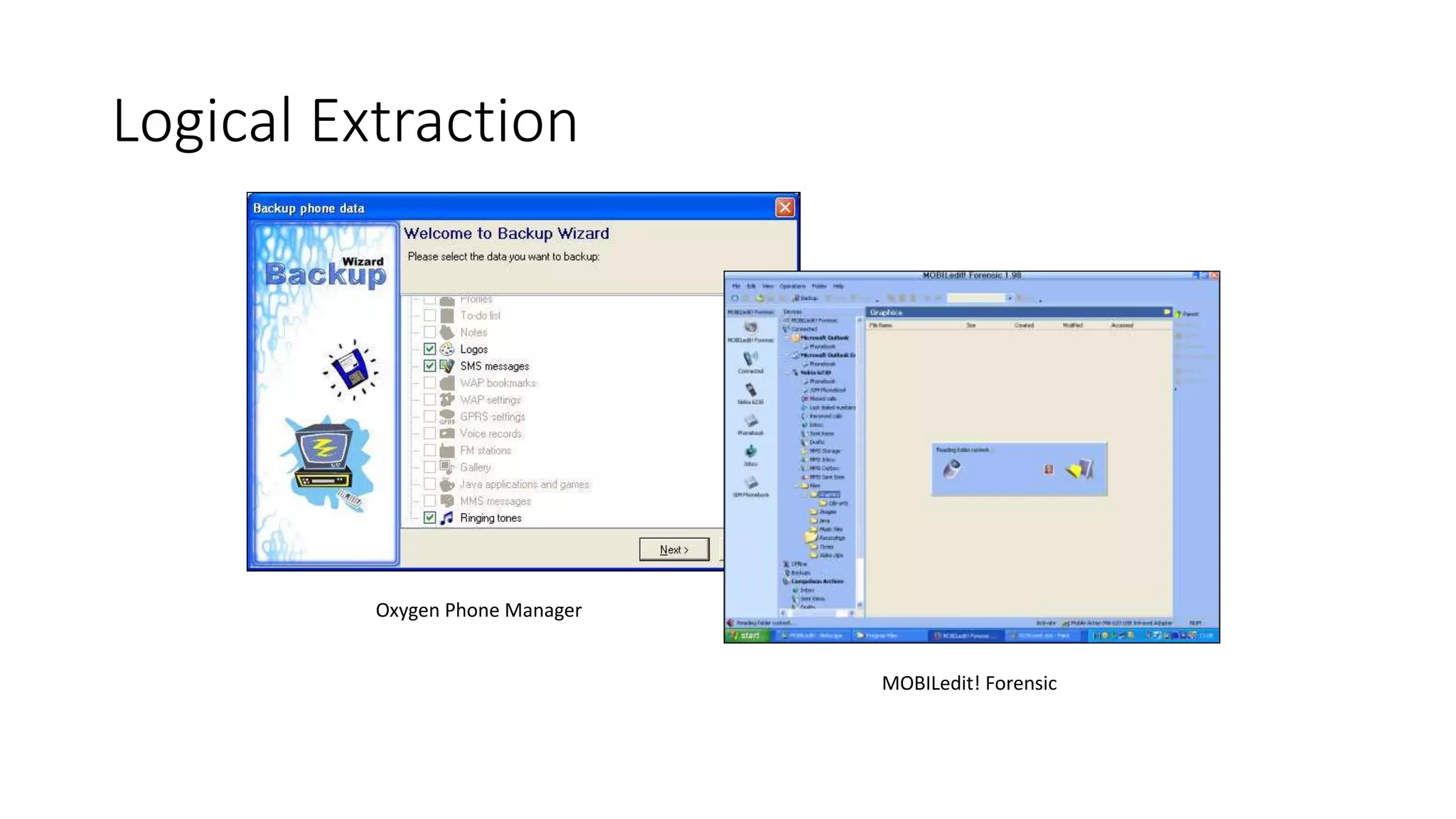
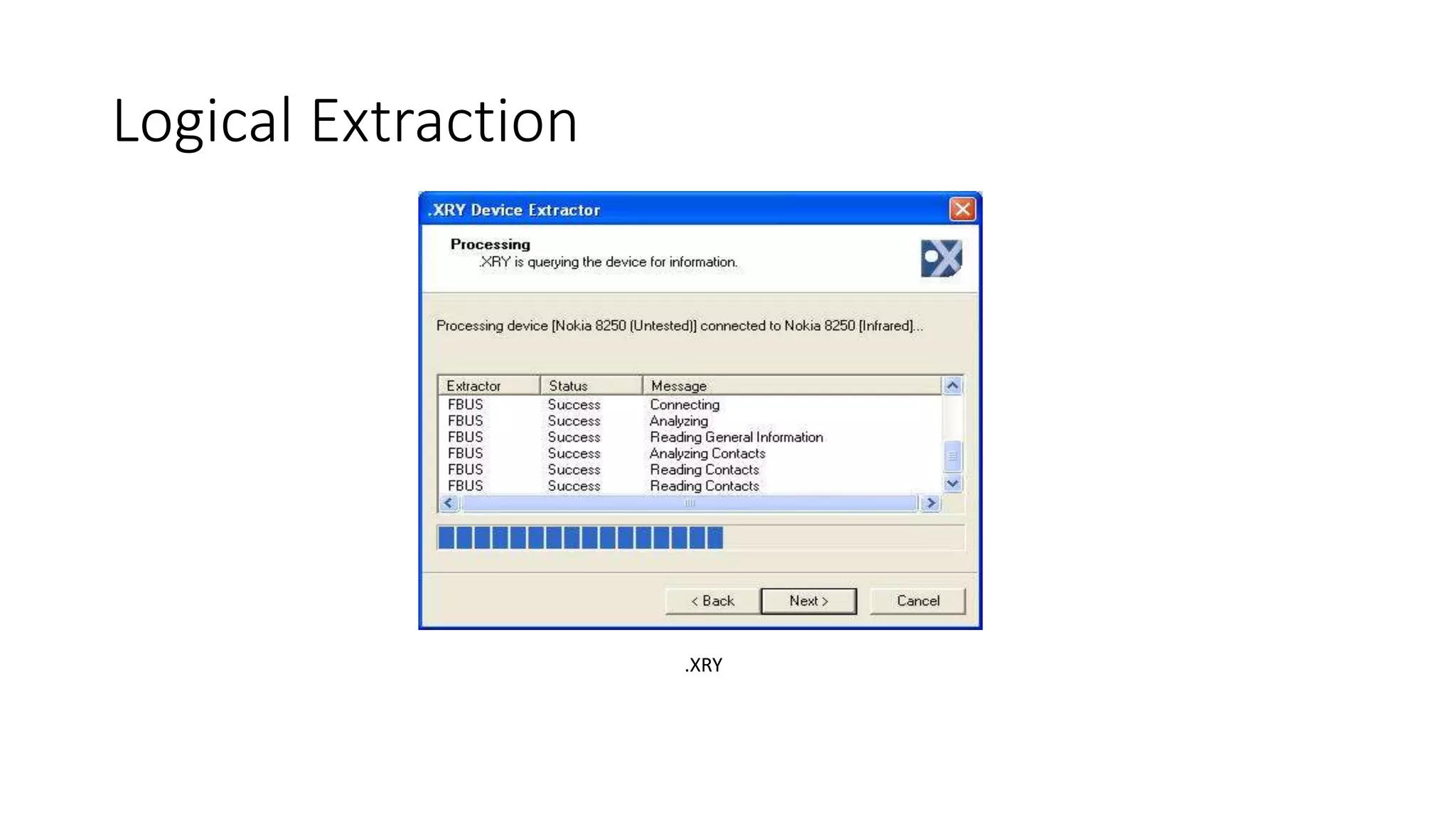
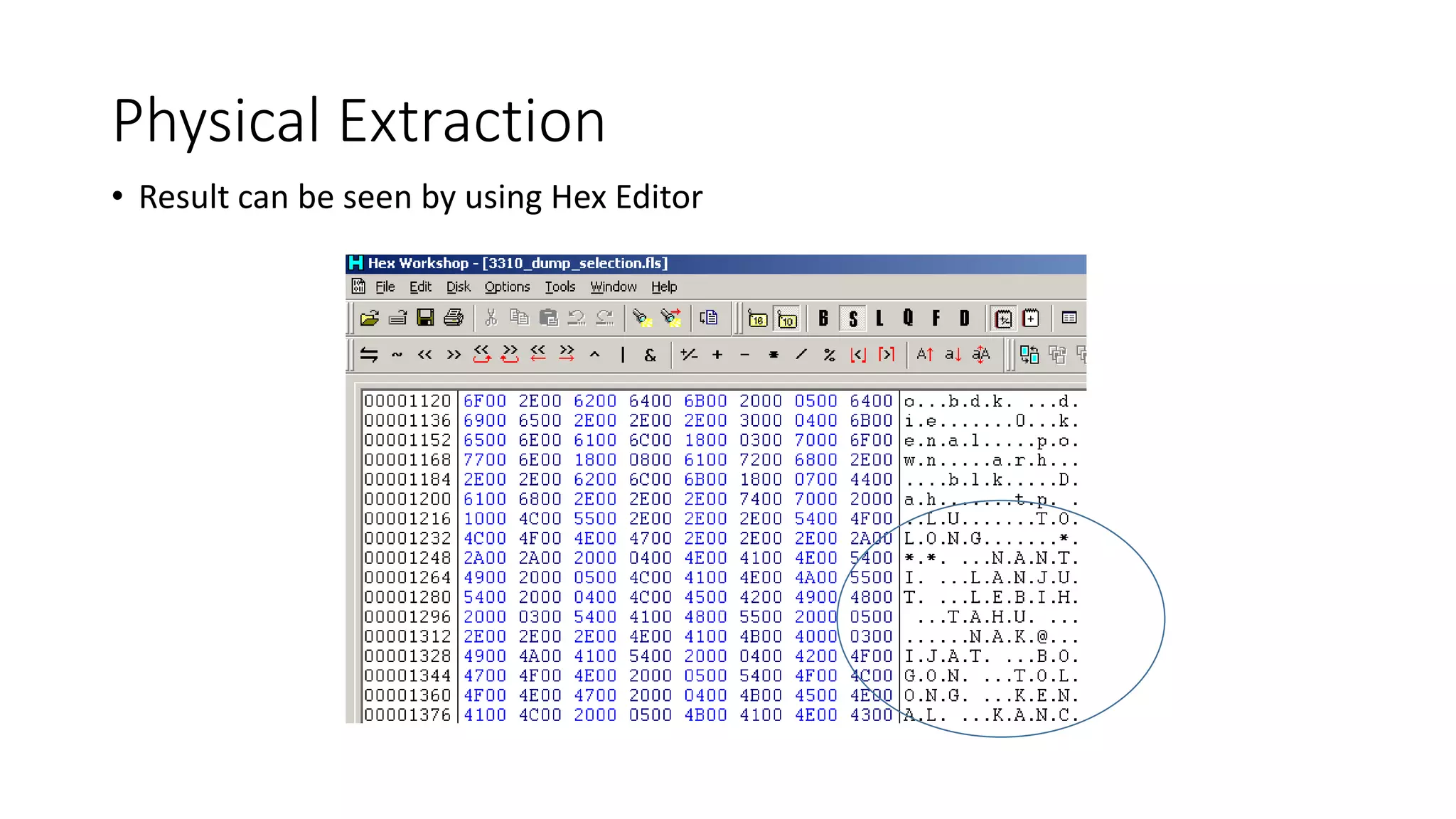
Mr. Islahuddin Jalal presented an introduction to computer forensics focused on mobile phone forensics. The presentation outlined objectives of mobile phone forensics, potential evidence sources like phone memory, SIM card, and external storage. Guidelines for seizure, examination, data extraction, and documentation of mobile phone evidence were discussed. Tools for logical and physical extraction from phone memory, SIM card, and external storage were also presented.