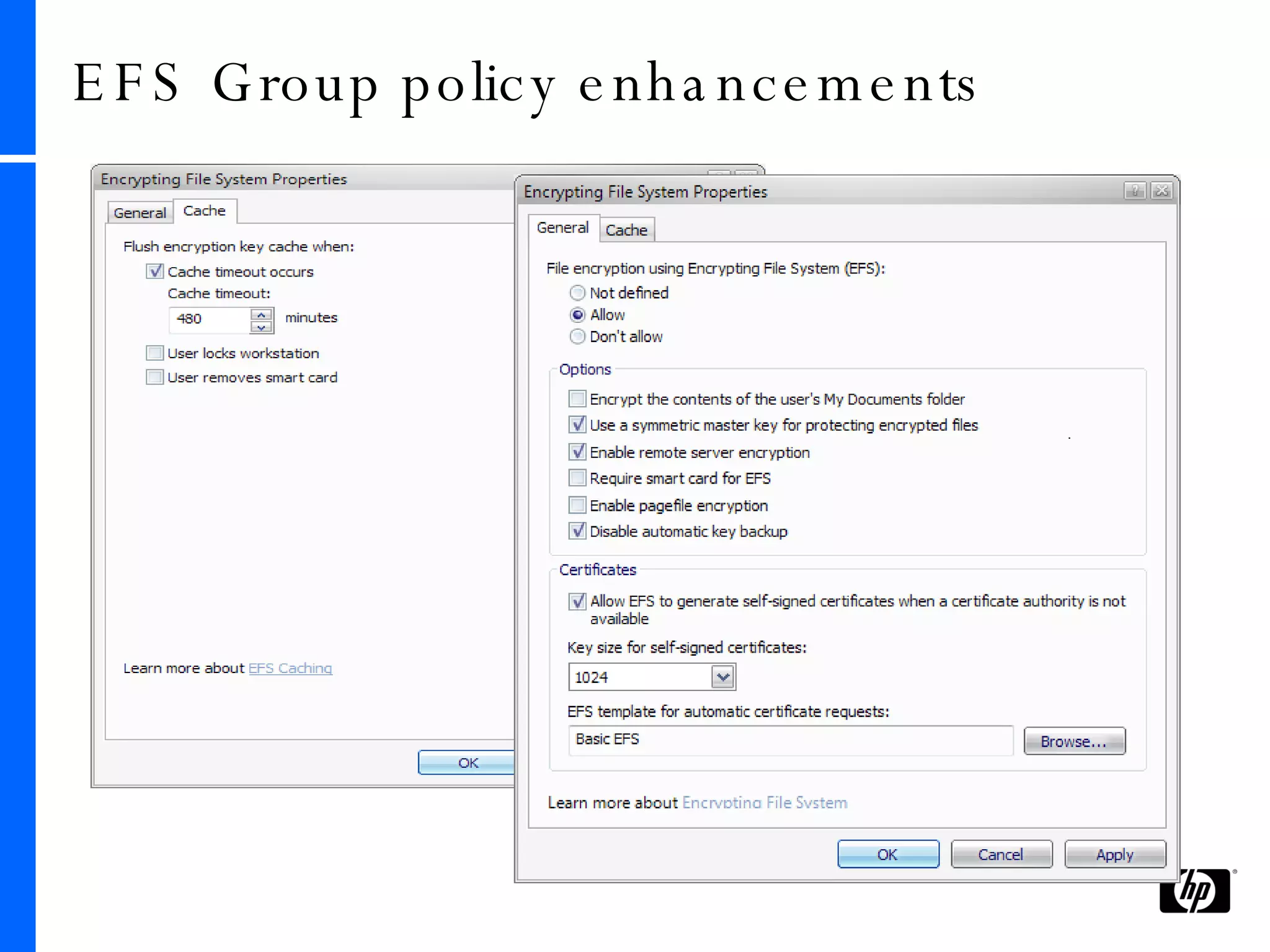
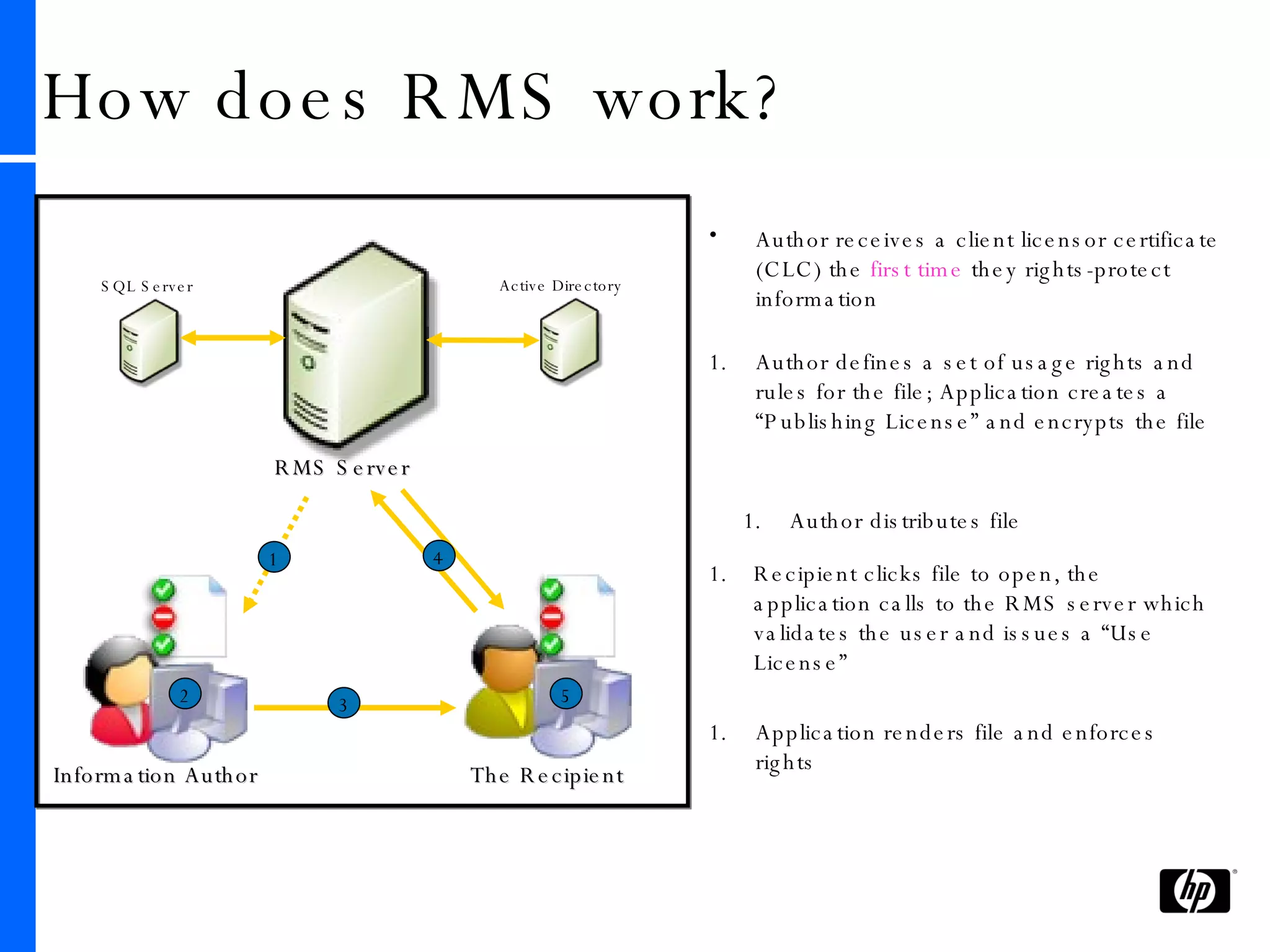
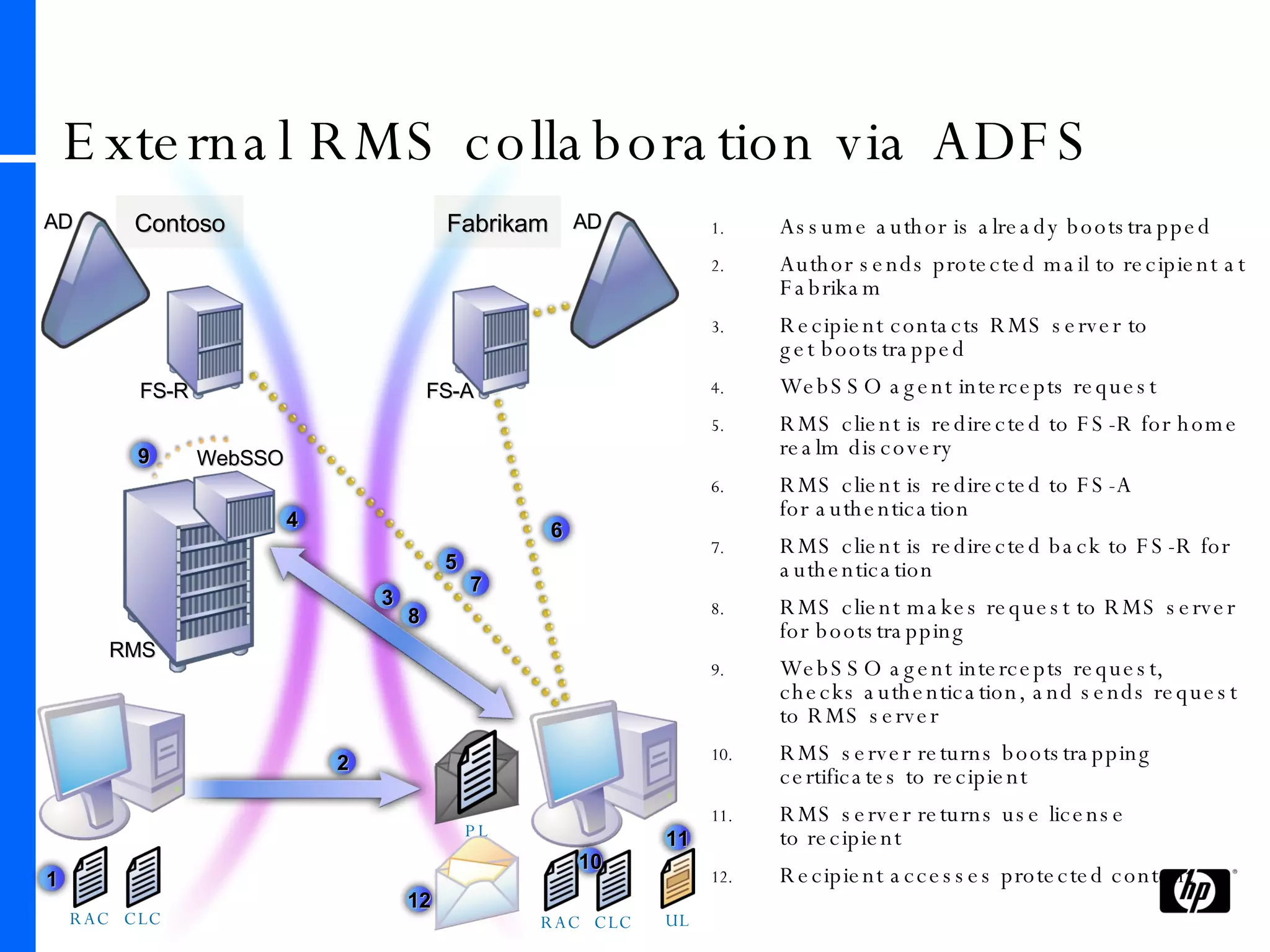
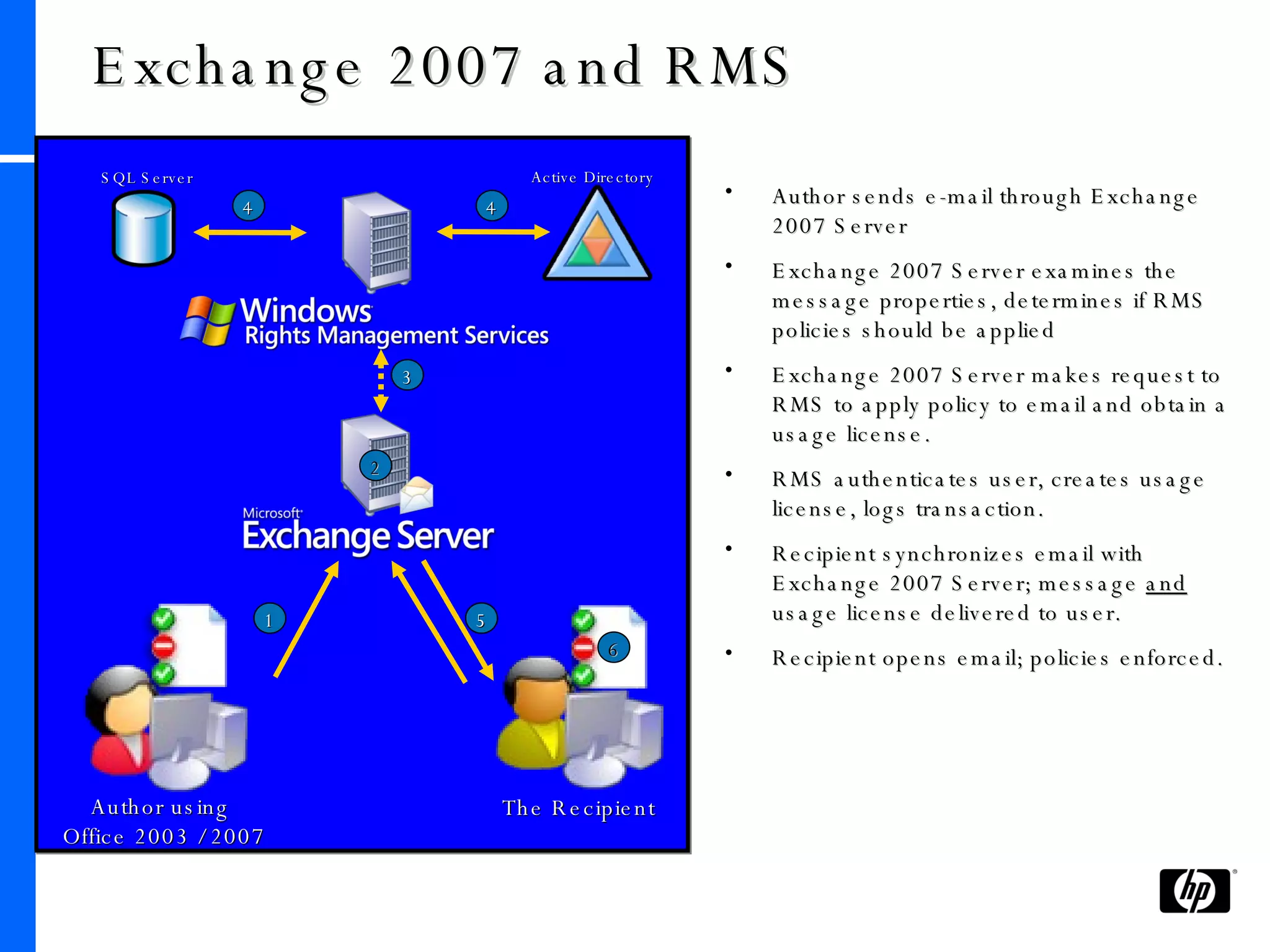
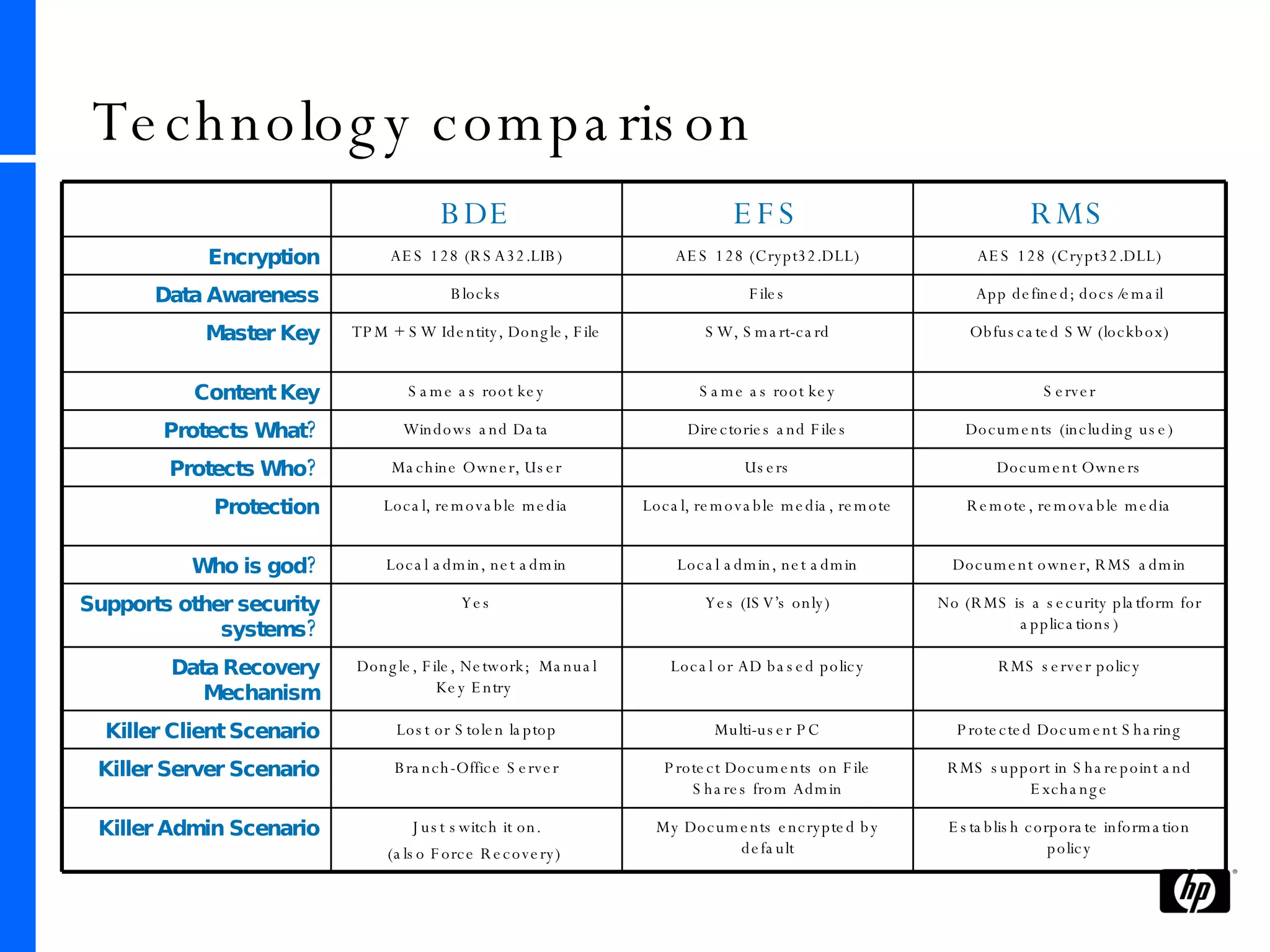
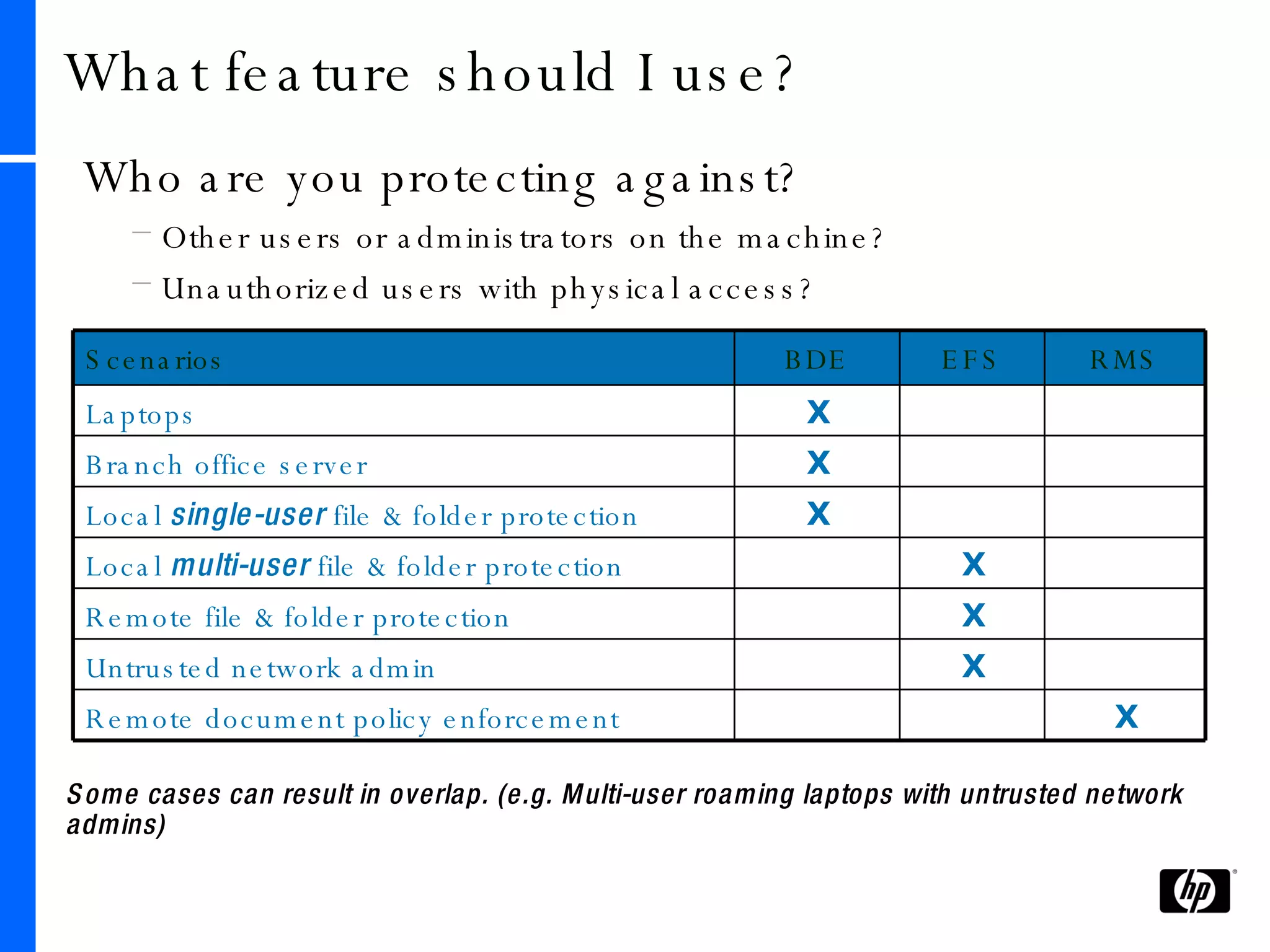
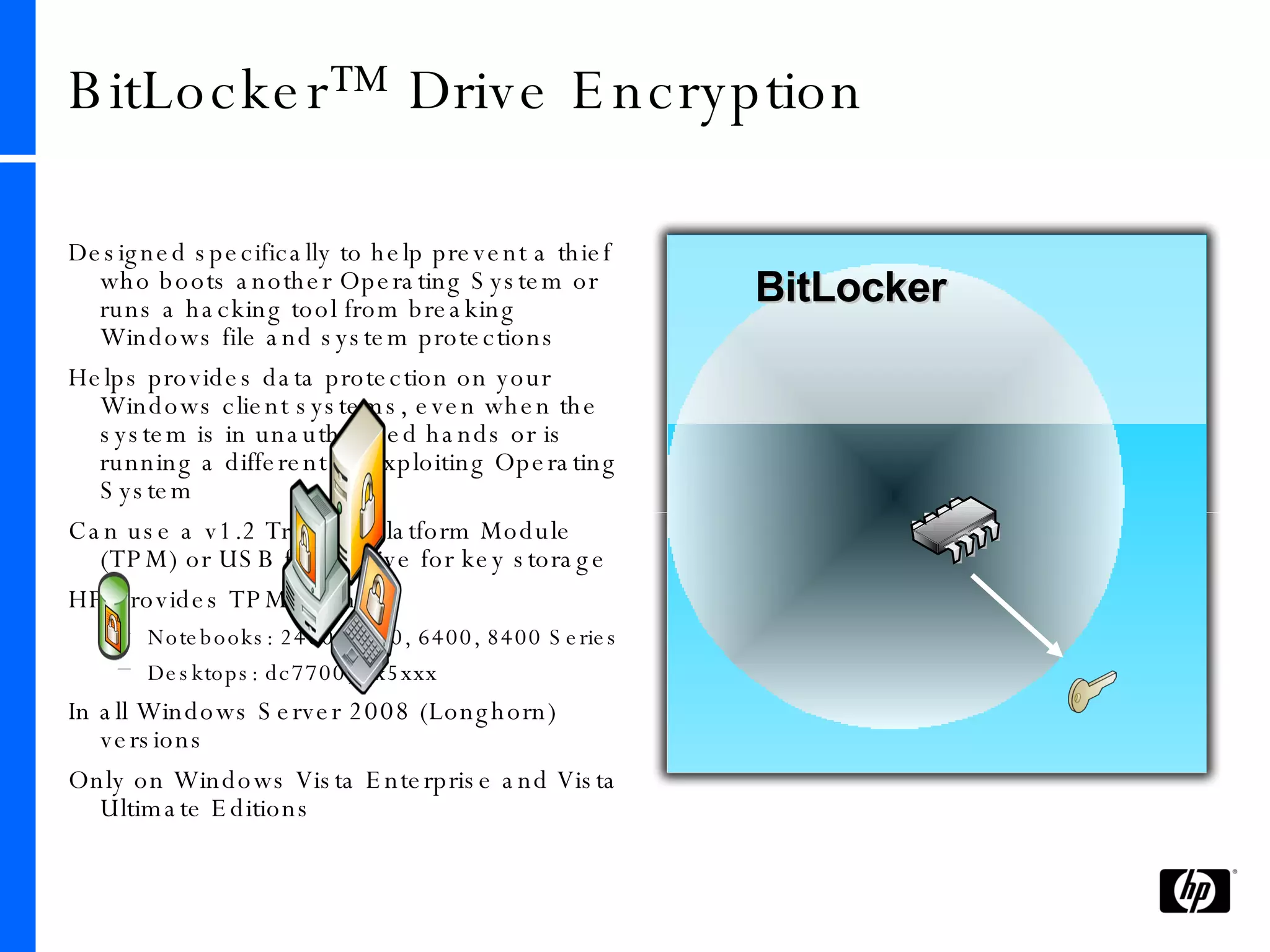
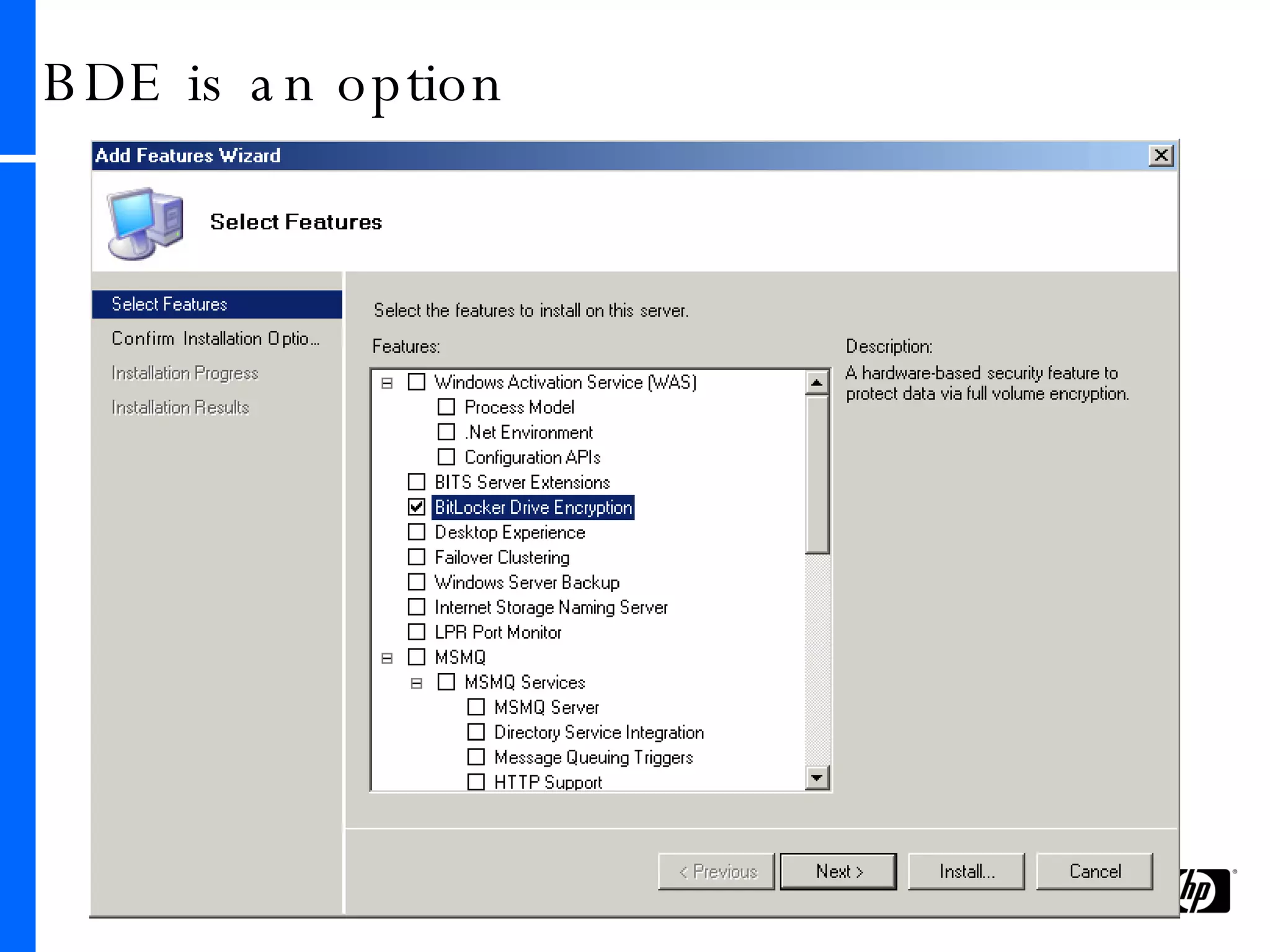
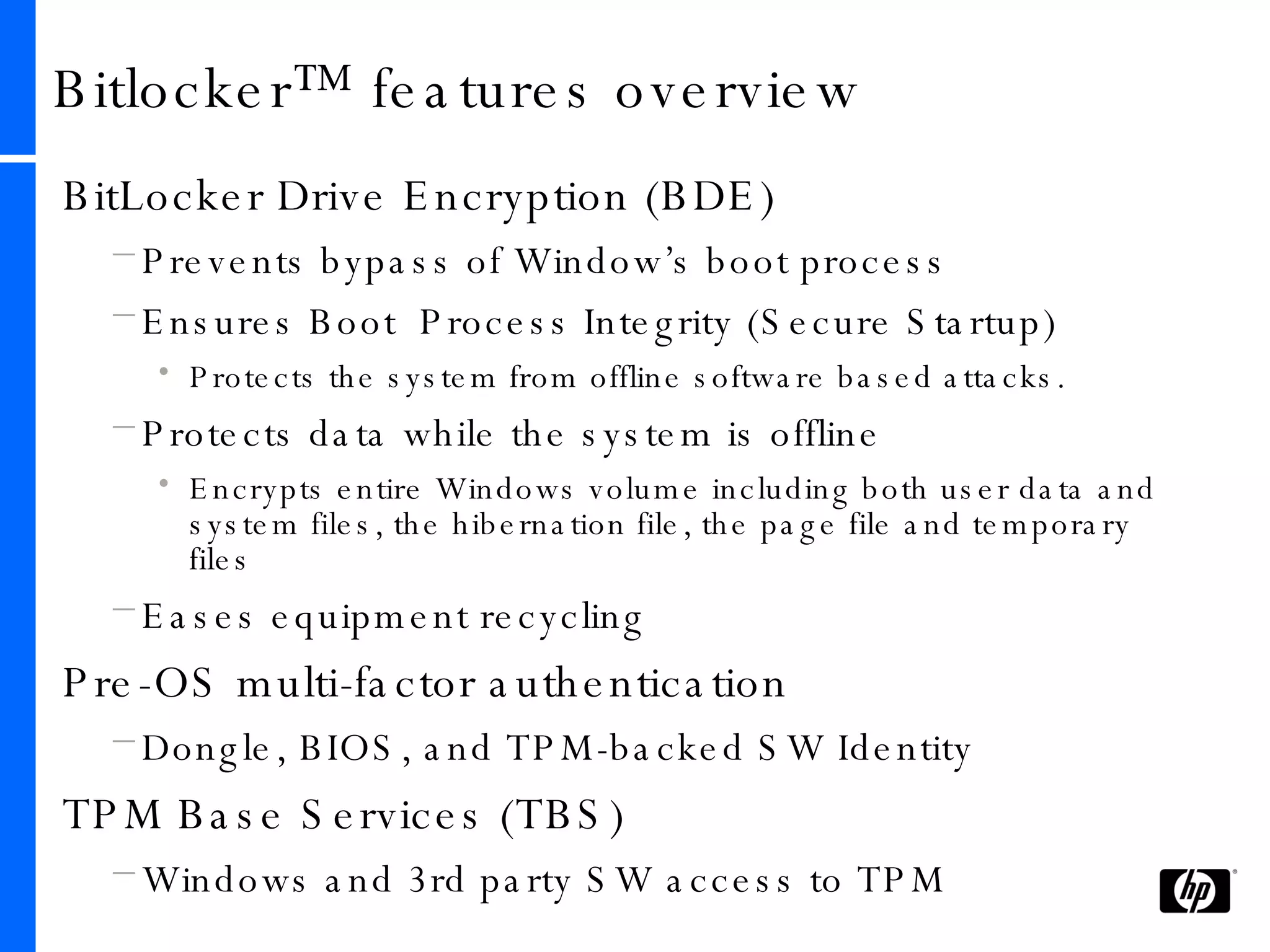
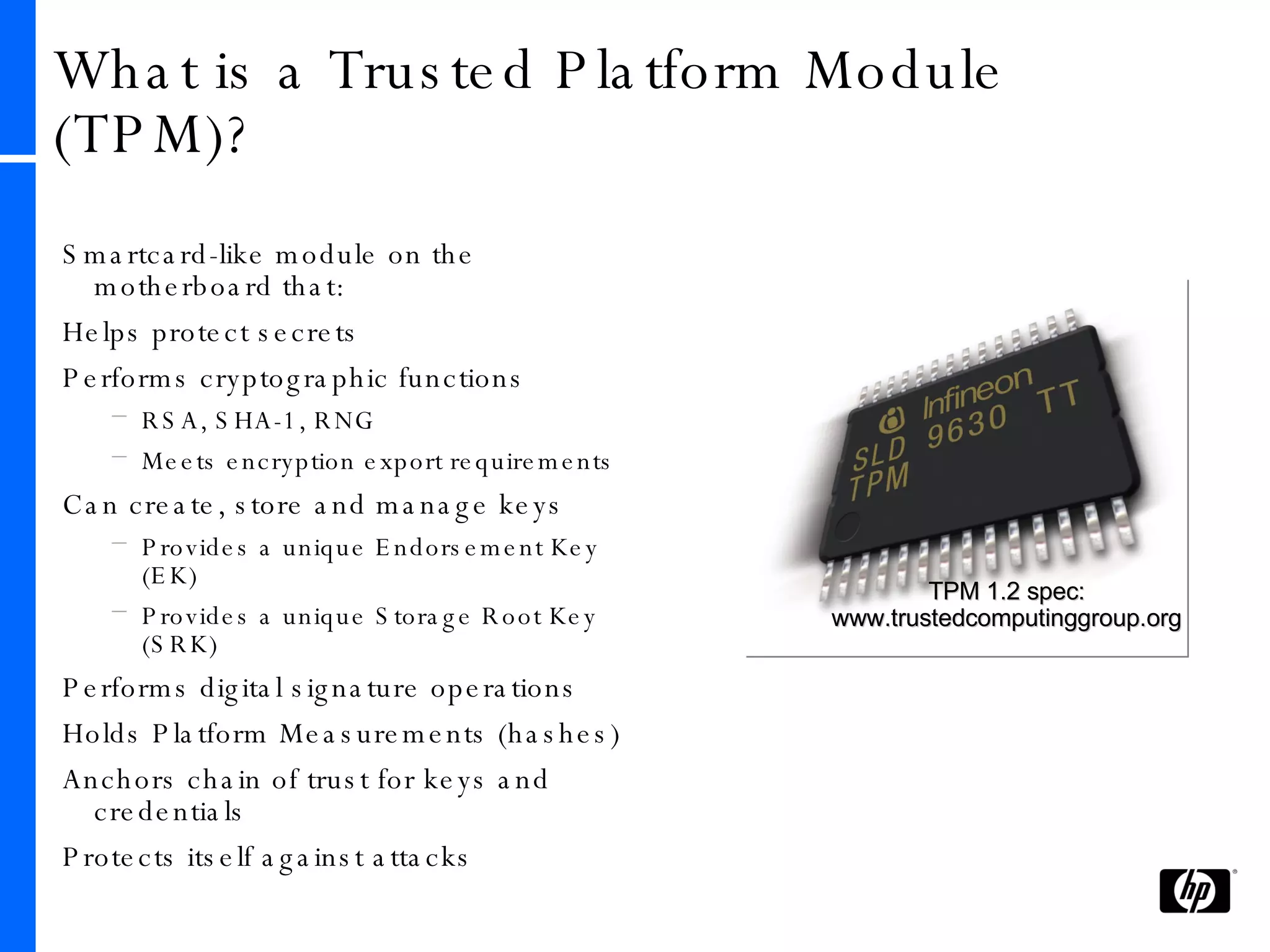
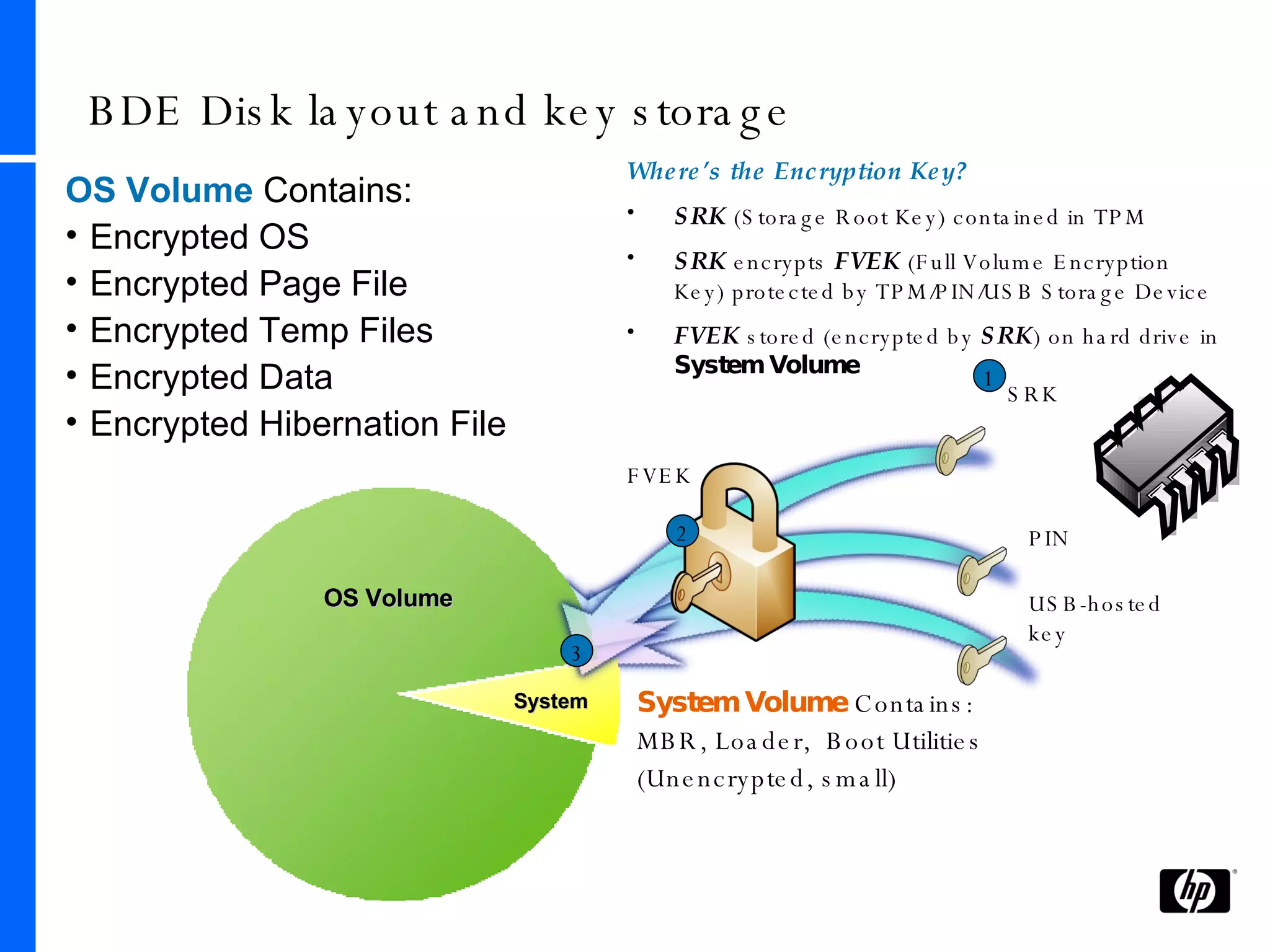
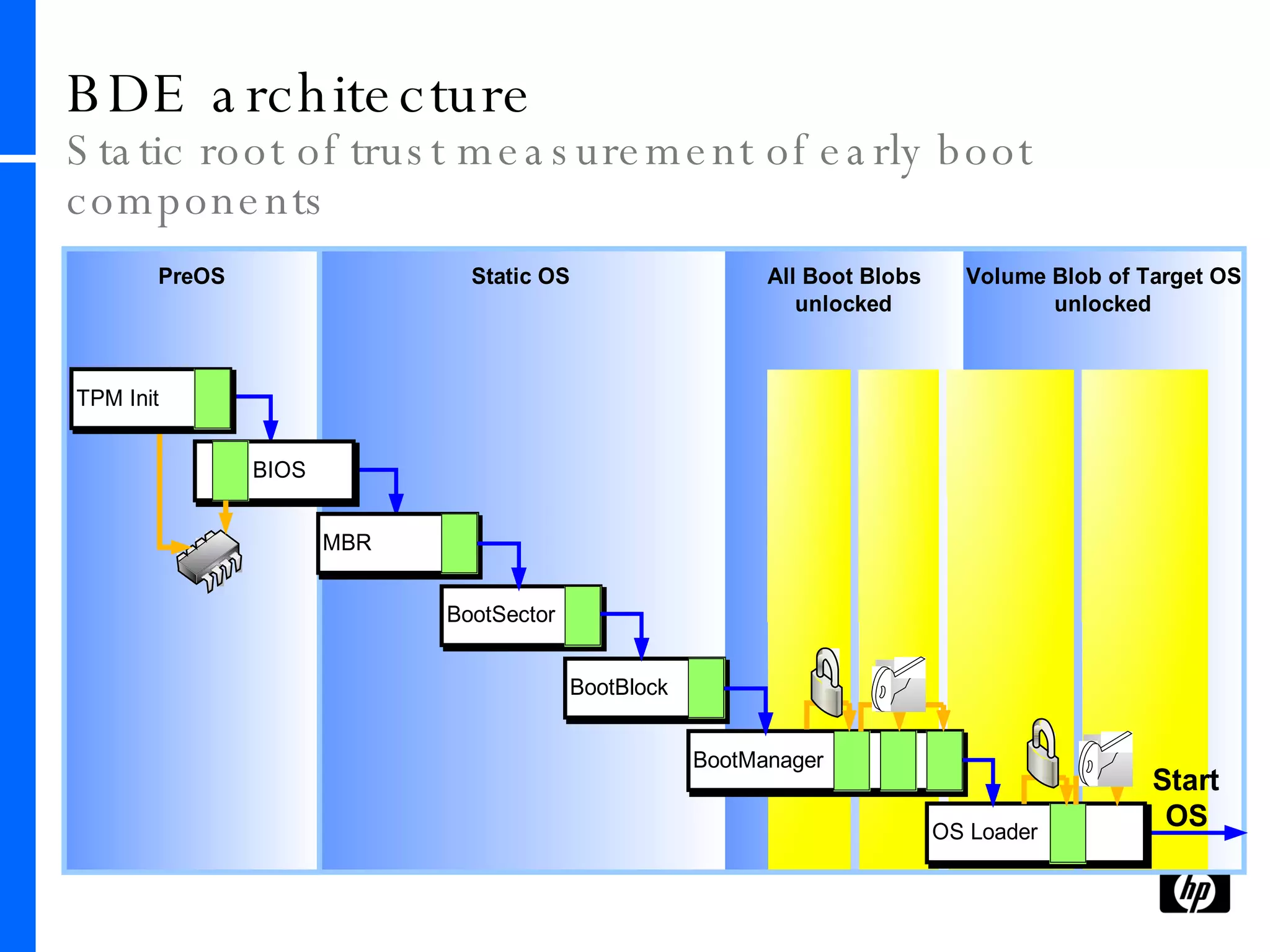
This document provides an overview and comparison of Microsoft's data protection solutions: BitLocker Drive Encryption (BDE), Encrypting File System (EFS), and Rights Management Services (RMS). BDE encrypts the entire hard drive to protect data when a device is lost or stolen. EFS encrypts individual files and folders on a system and when files are shared remotely. RMS allows document owners to control usage rights and enforce policies when content is distributed externally.











![EFS with remote files Client side encryption Local EFS encryption [Keys and certificates live on the client] Client connects to remote server share SMB protocol No need to enable Trust For Delegation Encrypted file sent to server File Share](https://image.slidesharecdn.com/microsoftdataprotectionsolutions-090424210142-phpapp01/75/Microsoft-Data-Protection-Solutions-21-2048.jpg)