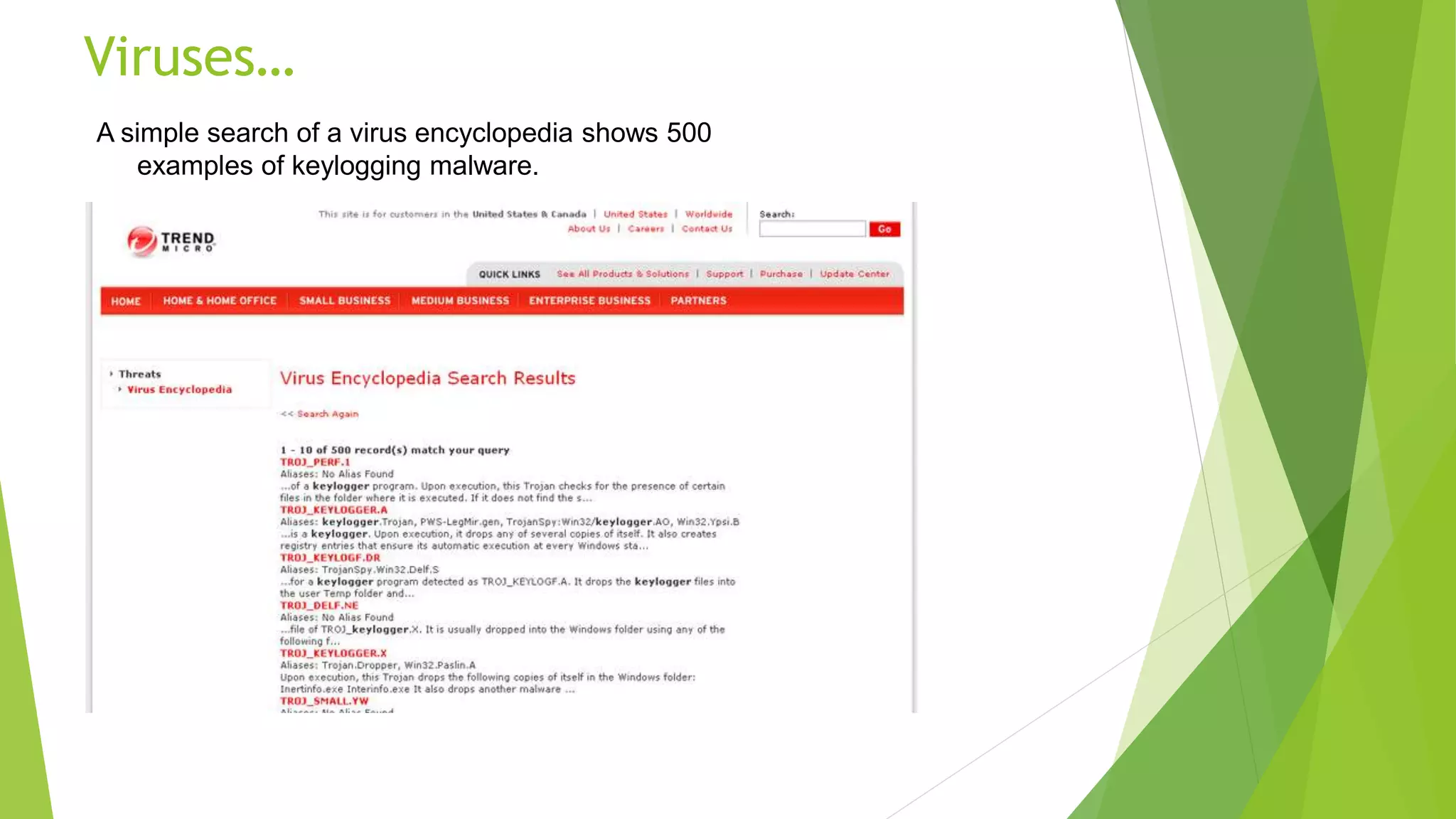
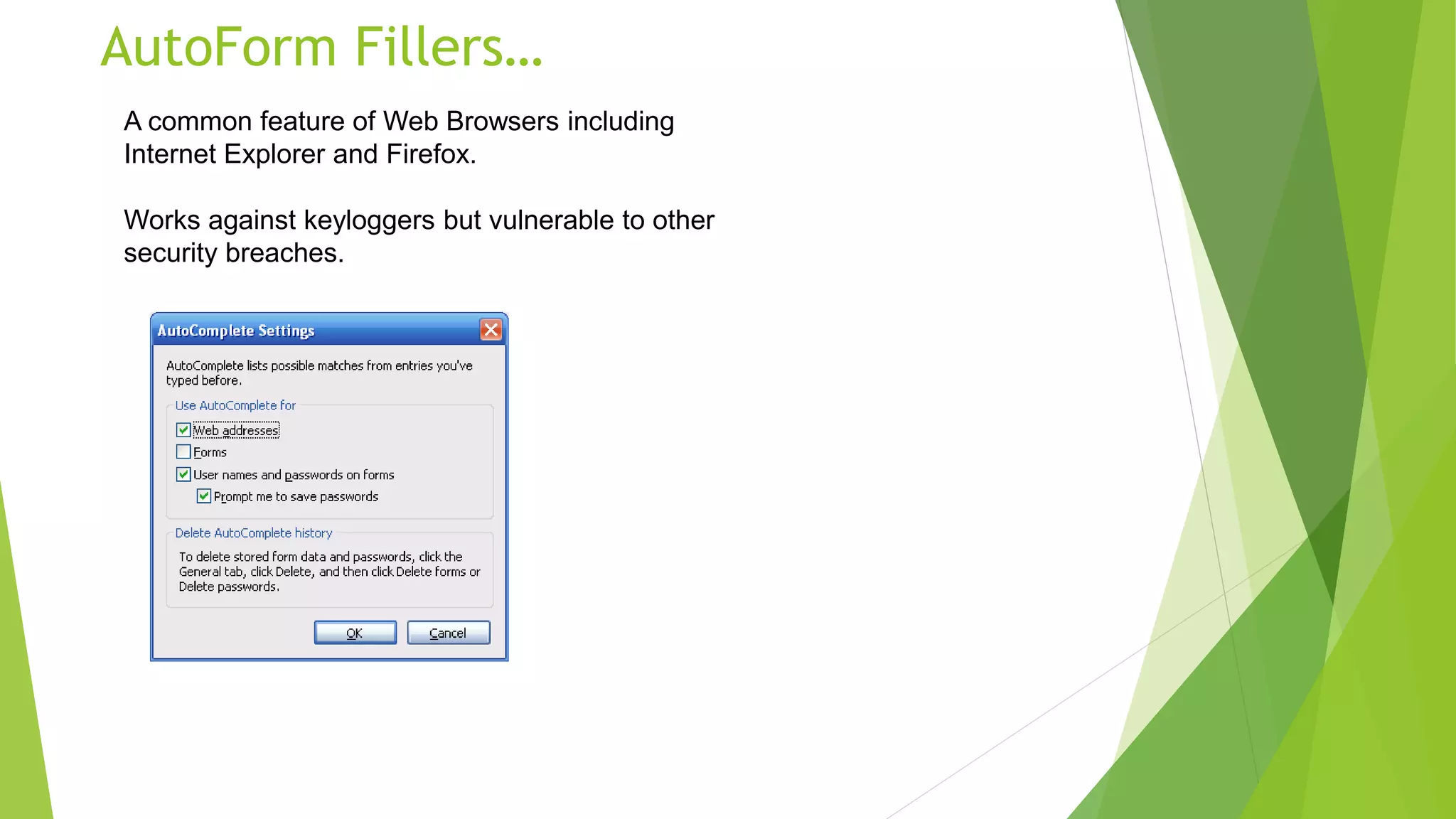
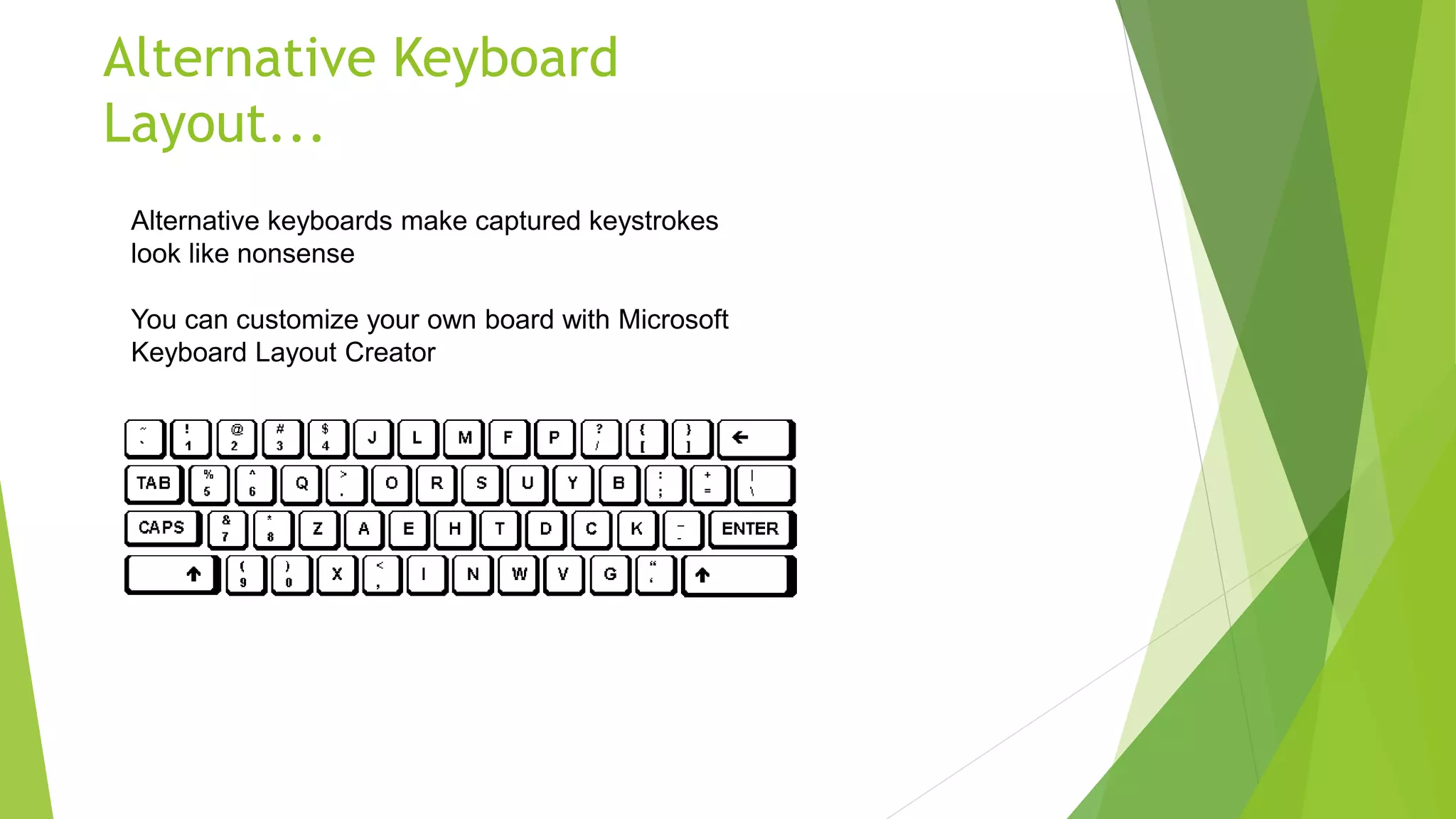
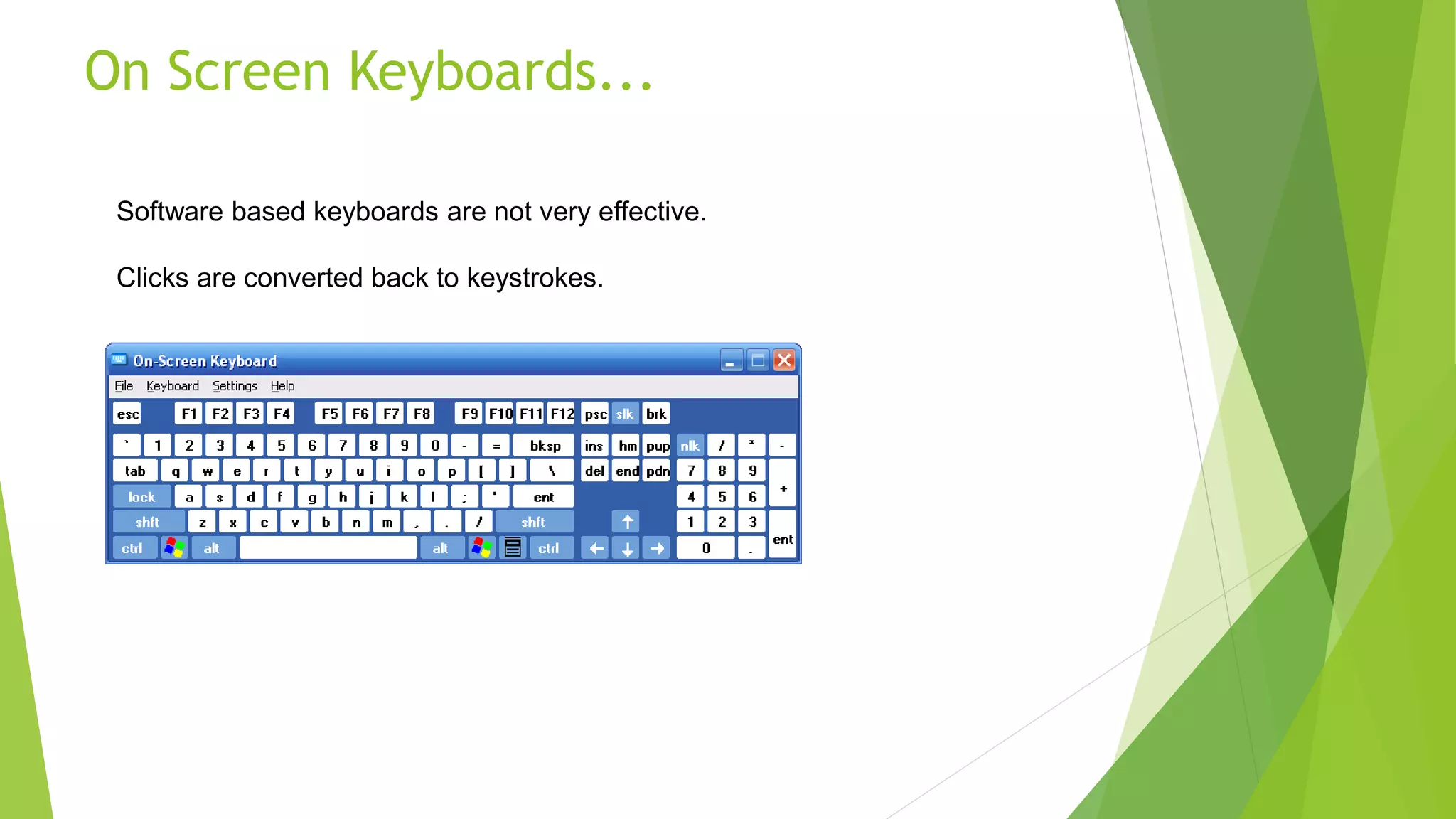
This document discusses password cracking and keyloggers. It defines passwords and describes different types of password attacks like dictionary attacks and brute force attacks. It also lists popular password cracking tools. The document also defines keyloggers and discusses how they can be used legitimately for monitoring or illegally to steal sensitive information. It provides examples of hardware and software keyloggers and describes some methods of preventing keylogger infections like using antivirus software and alternative keyboards.




![What is Password
• String of characters for authentication and log
on computer, web application , software, Files
, network , Mobile phones, and your life
• Comprises:
[a-zA-z, 0-9, symbols , space]](https://image.slidesharecdn.com/cyber-161019183435/75/password-cracking-and-Key-logger-5-2048.jpg)








![Password Cracking Depends on
Attacker's strengths
Attacker's computing resources
Attacker's knowledge
Attacker's mode of access [physical or online]
Strength of the passwords
How often you change your passwords?
How close are the old and new passwords?
How long is your password?
Have you used every possible combination: alphabets, numbers and special characters?
How common are your letters, words, numbers or combination?
Have you used strings followed by numbers or vice versa, instead of mixing them
randomly?](https://image.slidesharecdn.com/cyber-161019183435/75/password-cracking-and-Key-logger-16-2048.jpg)