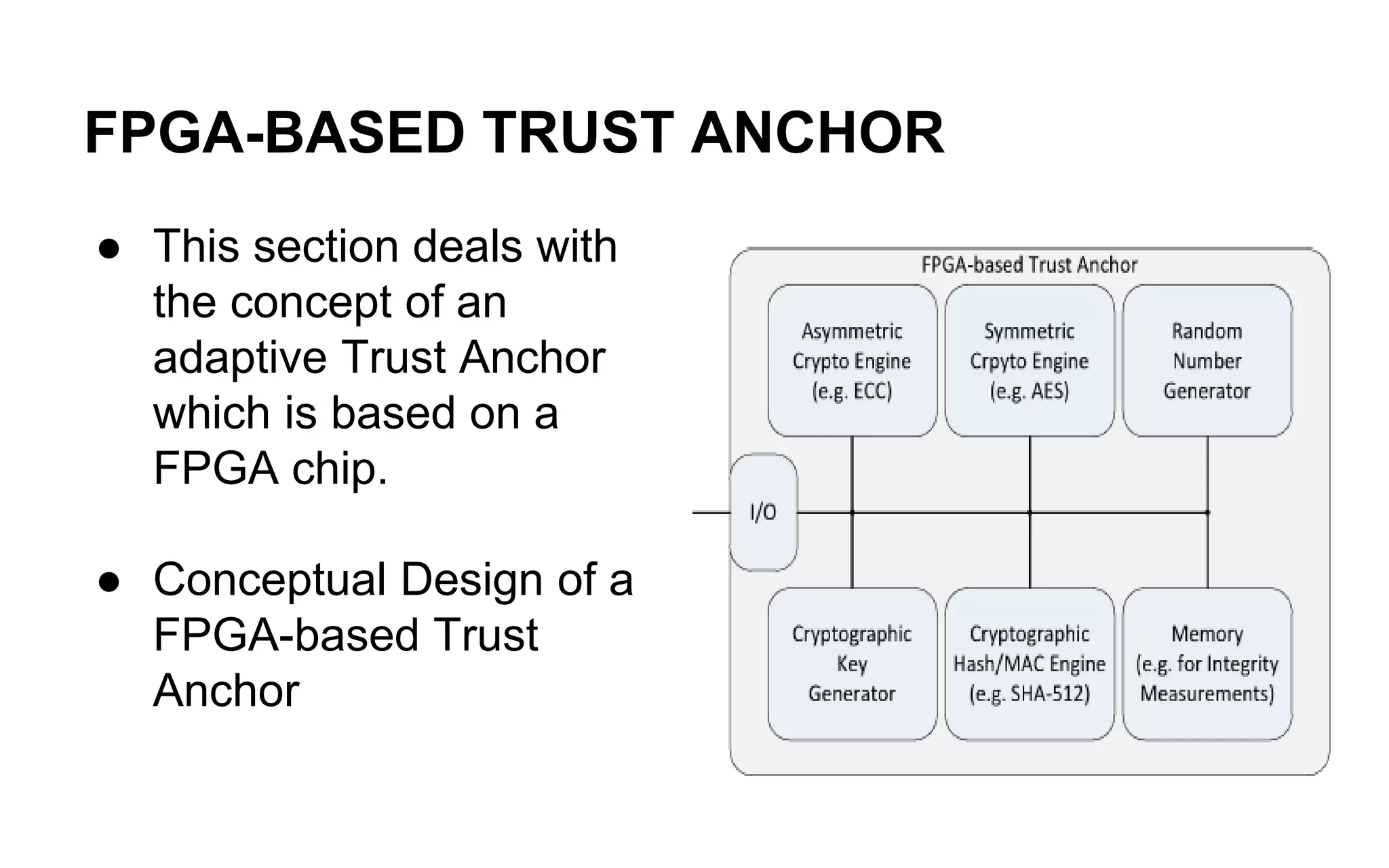
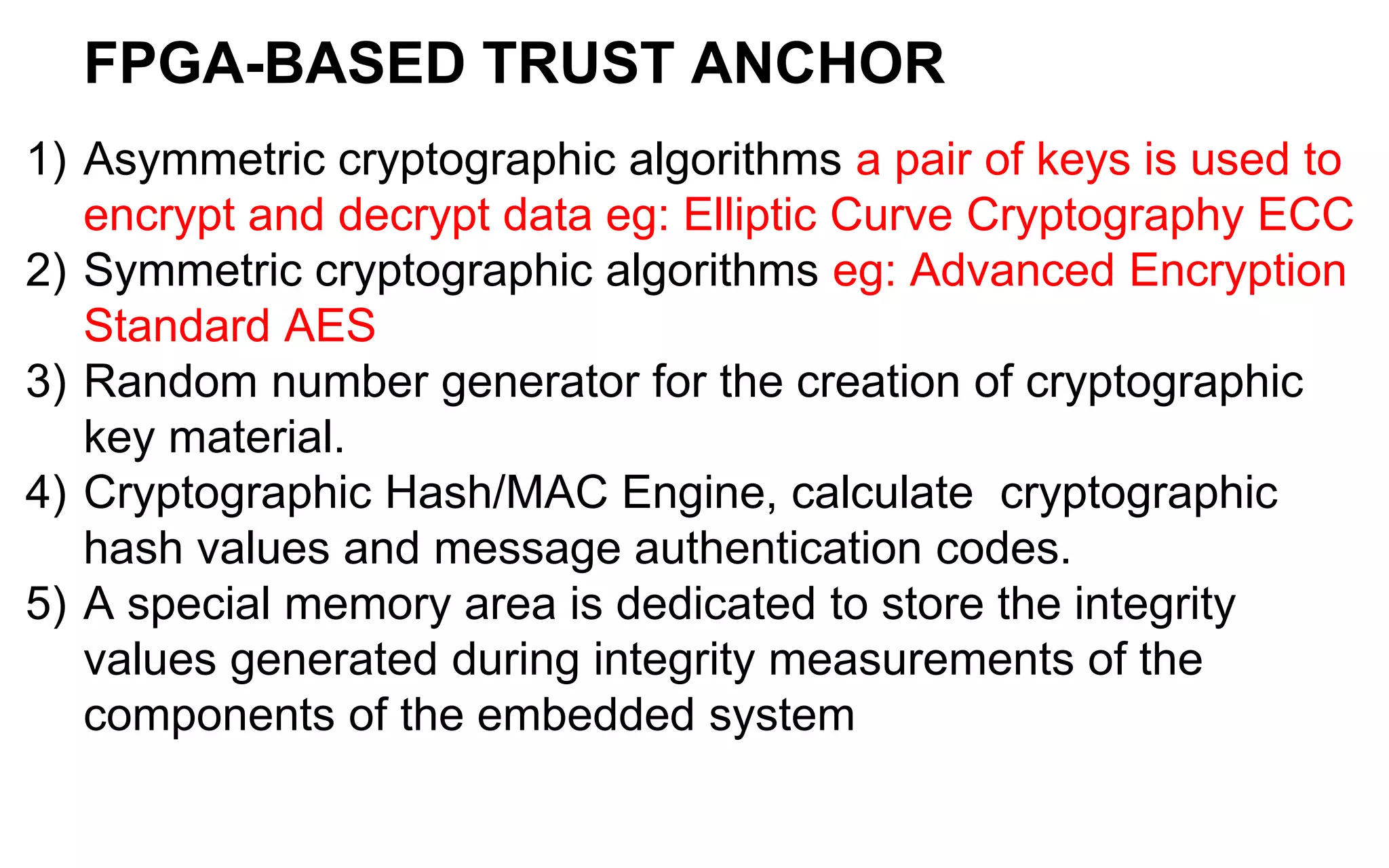
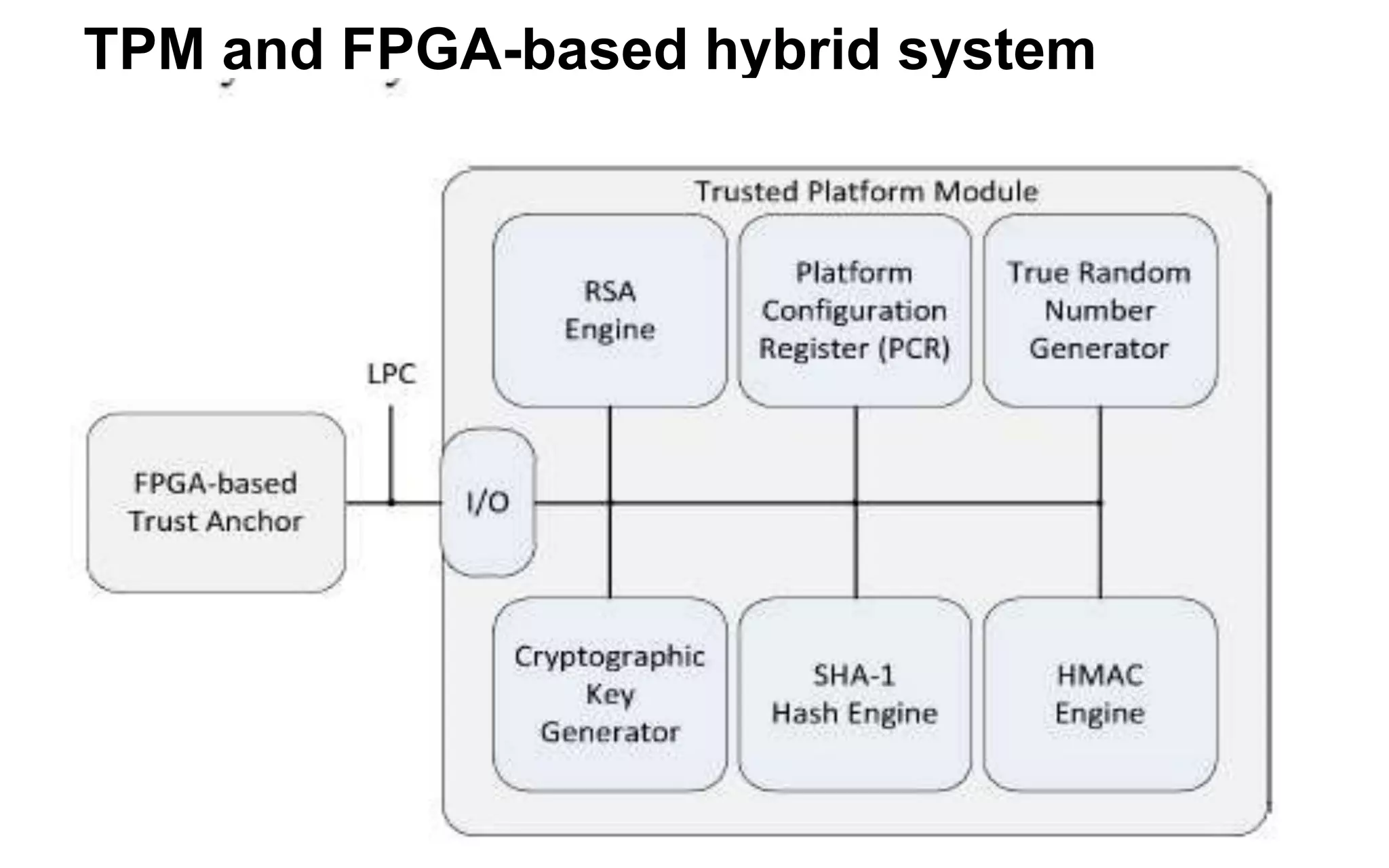
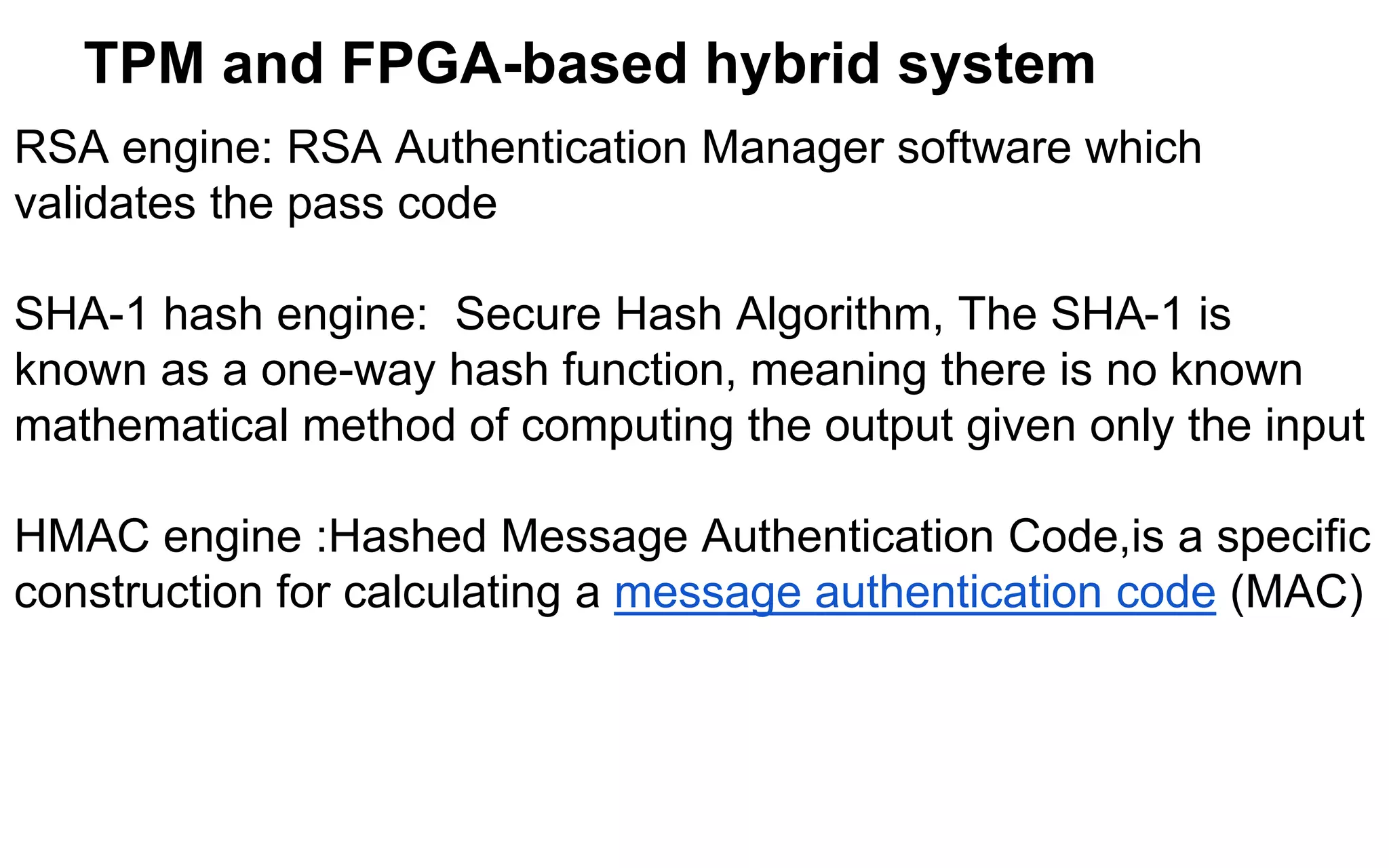
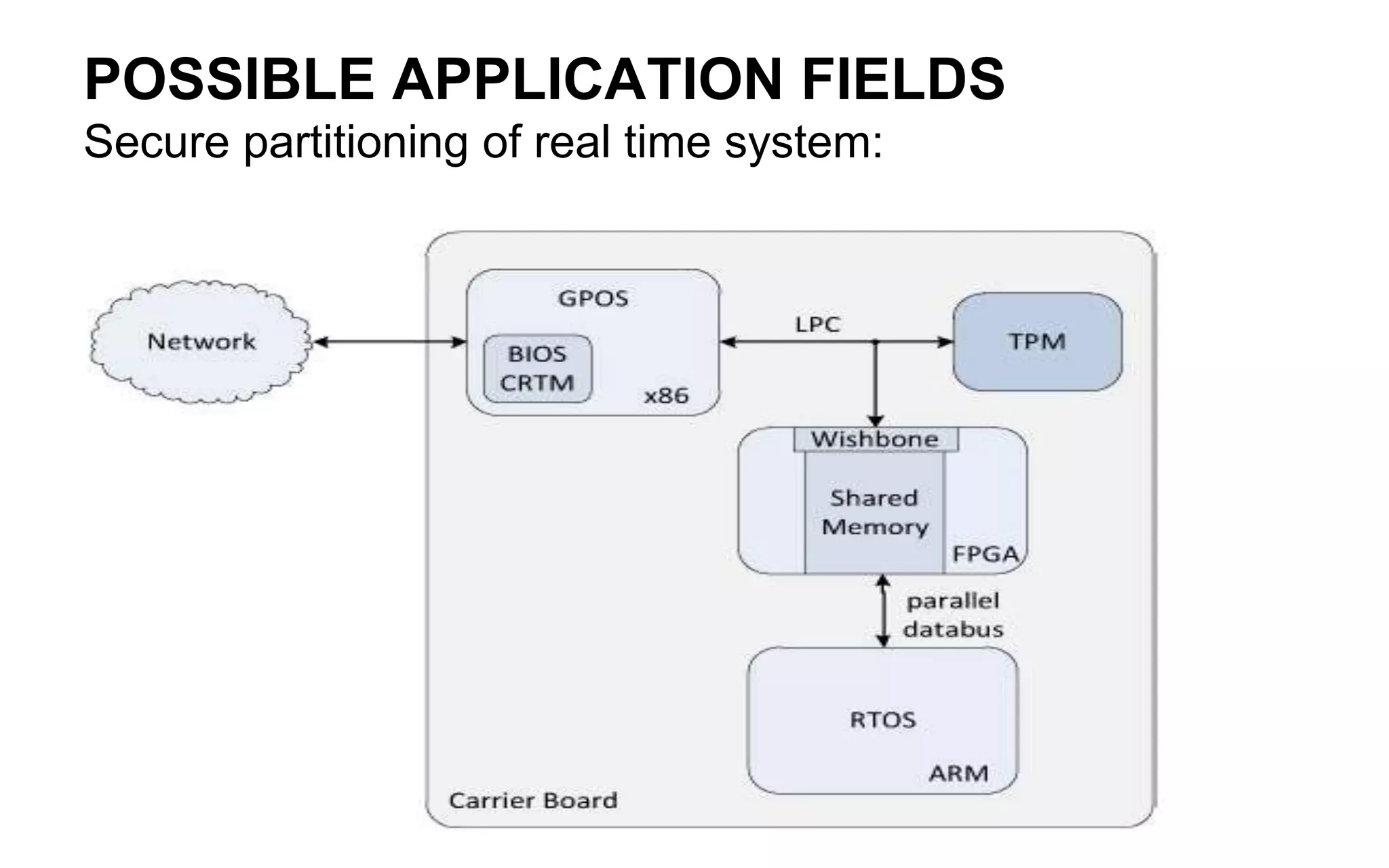
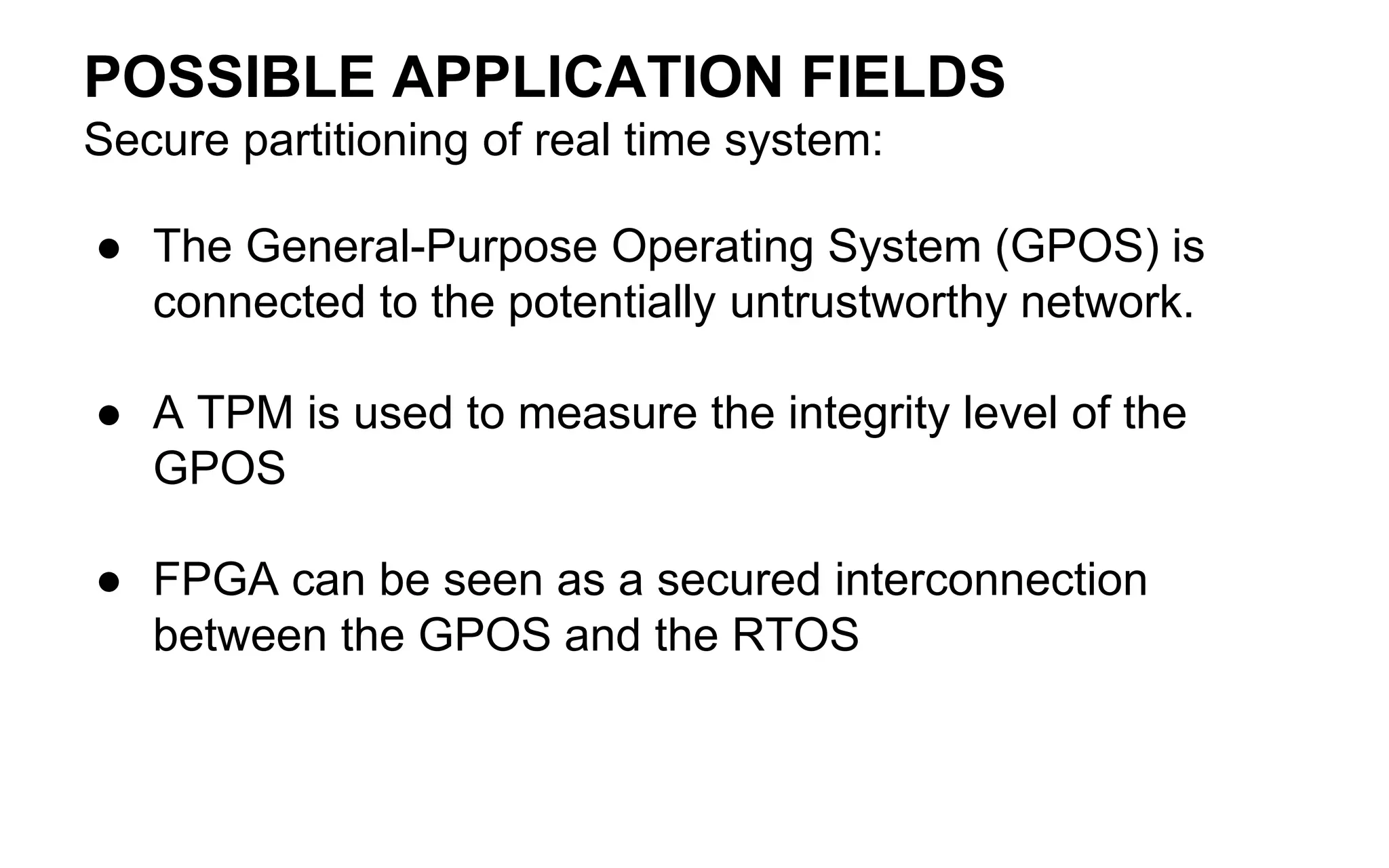
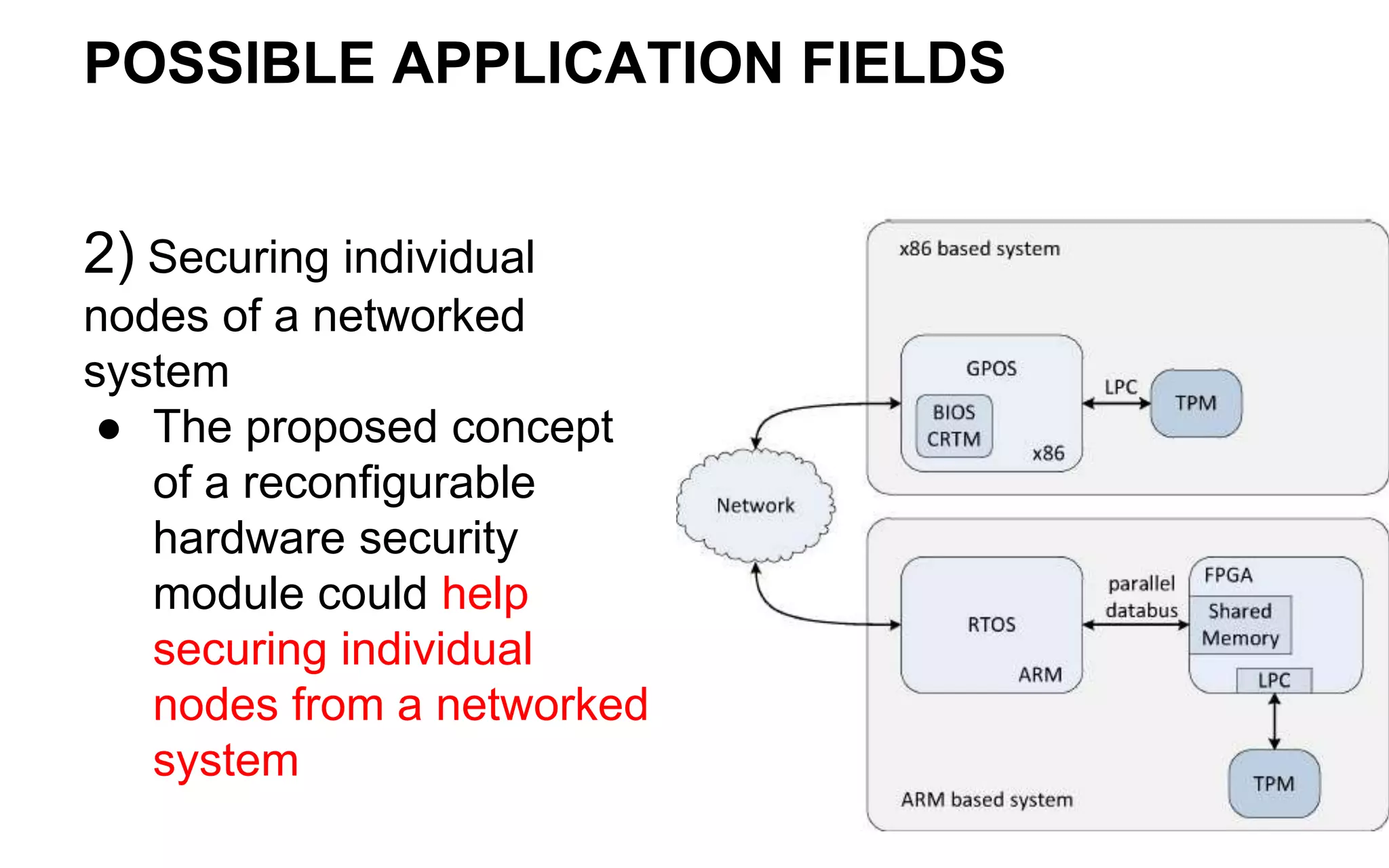
The document discusses the integration of reconfigurable trust mechanisms in embedded computing platforms, highlighting the advantages of FPGA-based trust anchors for cryptographic applications. It outlines the benefits and shortcomings of using FPGAs, including the need for hybrid systems combining FPGAs with Trusted Platform Modules (TPMs) to enhance security. Potential applications include securing real-time systems and individual network nodes, with a focus on ensuring reliability and security in future research.