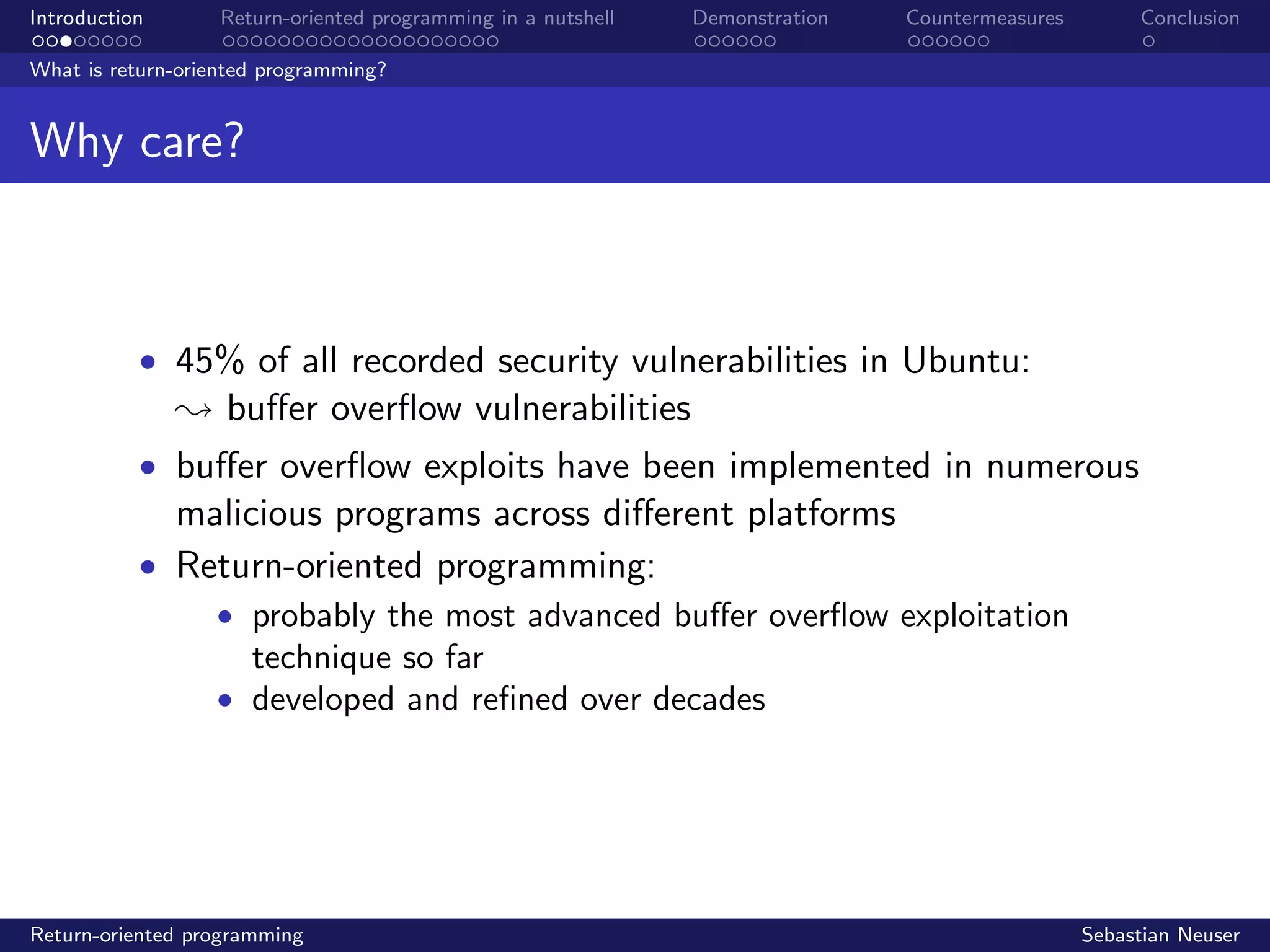
The document discusses return-oriented programming (ROP), an advanced exploitation technique used to leverage buffer overflow vulnerabilities by chaining short instruction sequences known as 'gadgets' to perform arbitrary computations. It provides a historical background of ROP, examples of its uses in computer worms, and various countermeasures to mitigate such vulnerabilities. Additionally, it includes a demonstration of a ROP compiler, ropgadget, which helps identify available gadgets within a binary.






![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
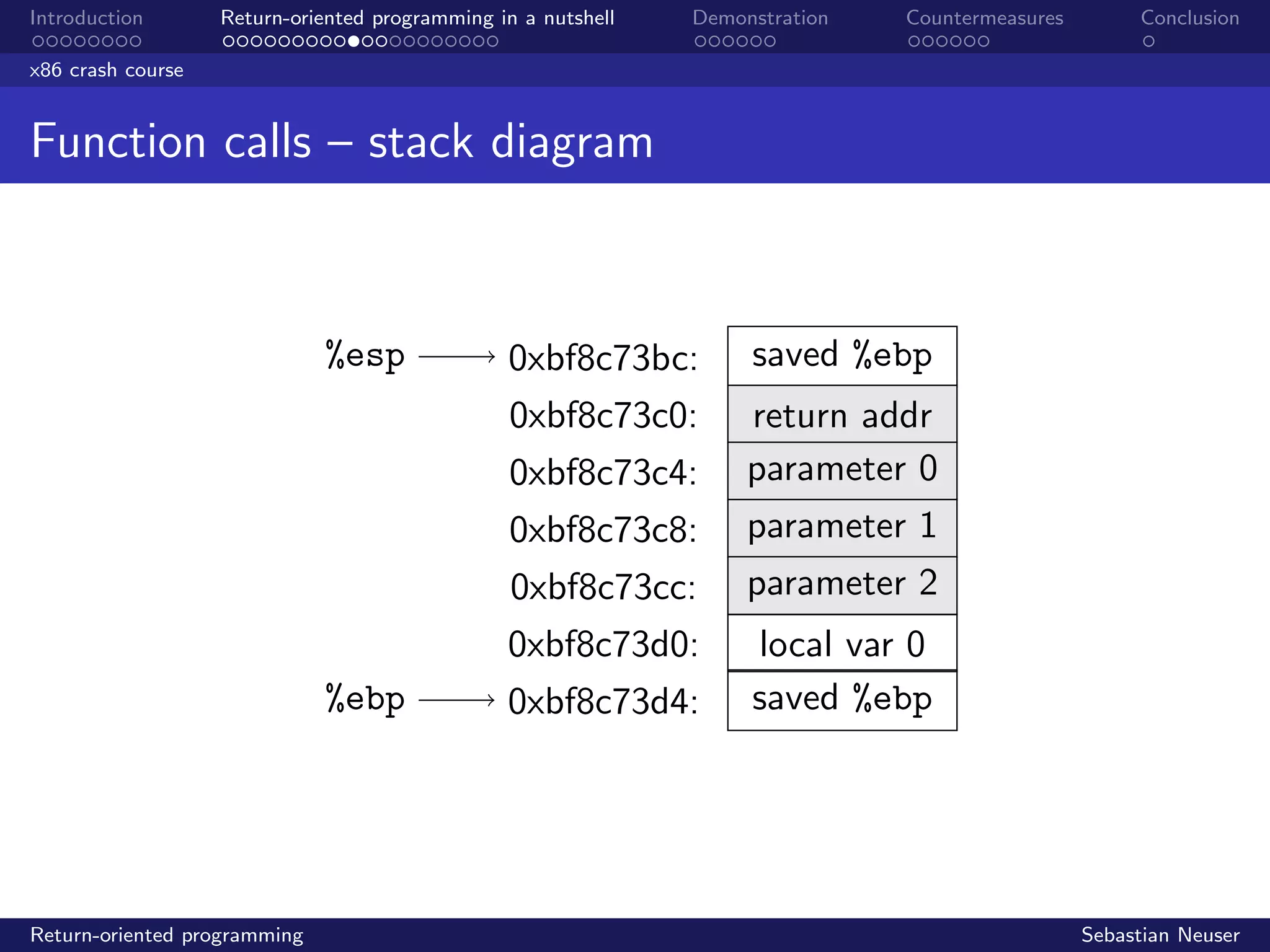
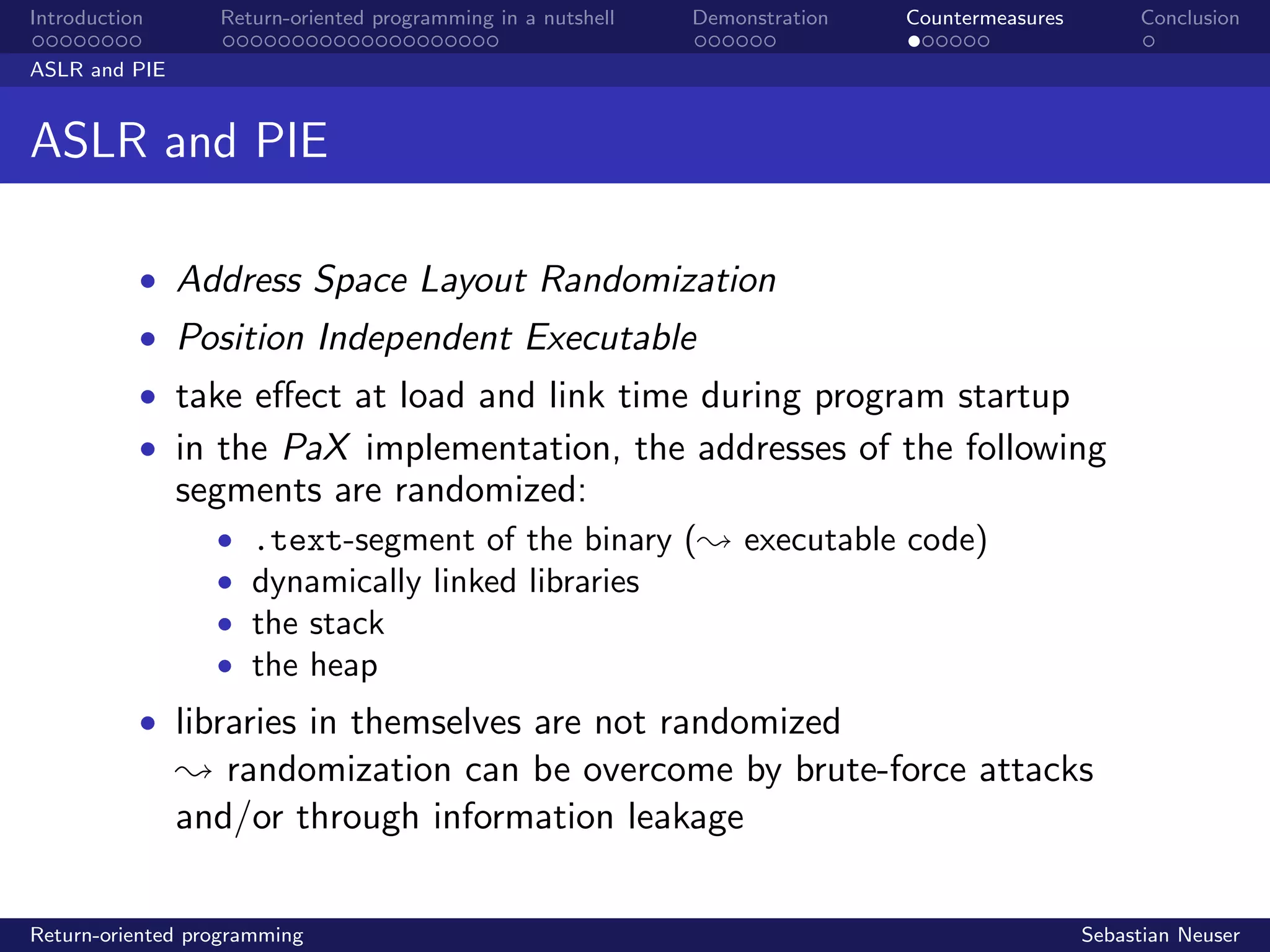
Stack buffer overflow
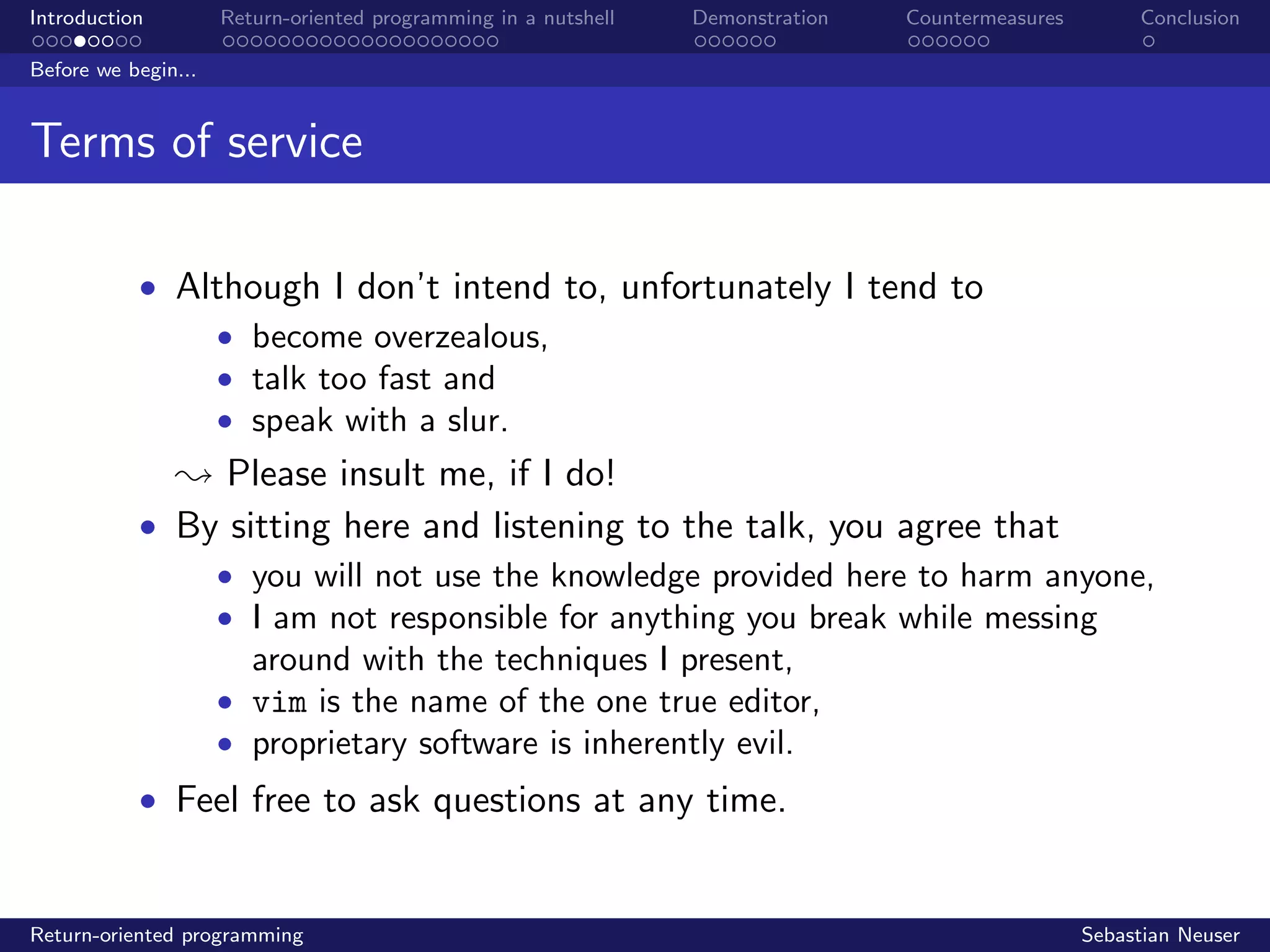
Before...
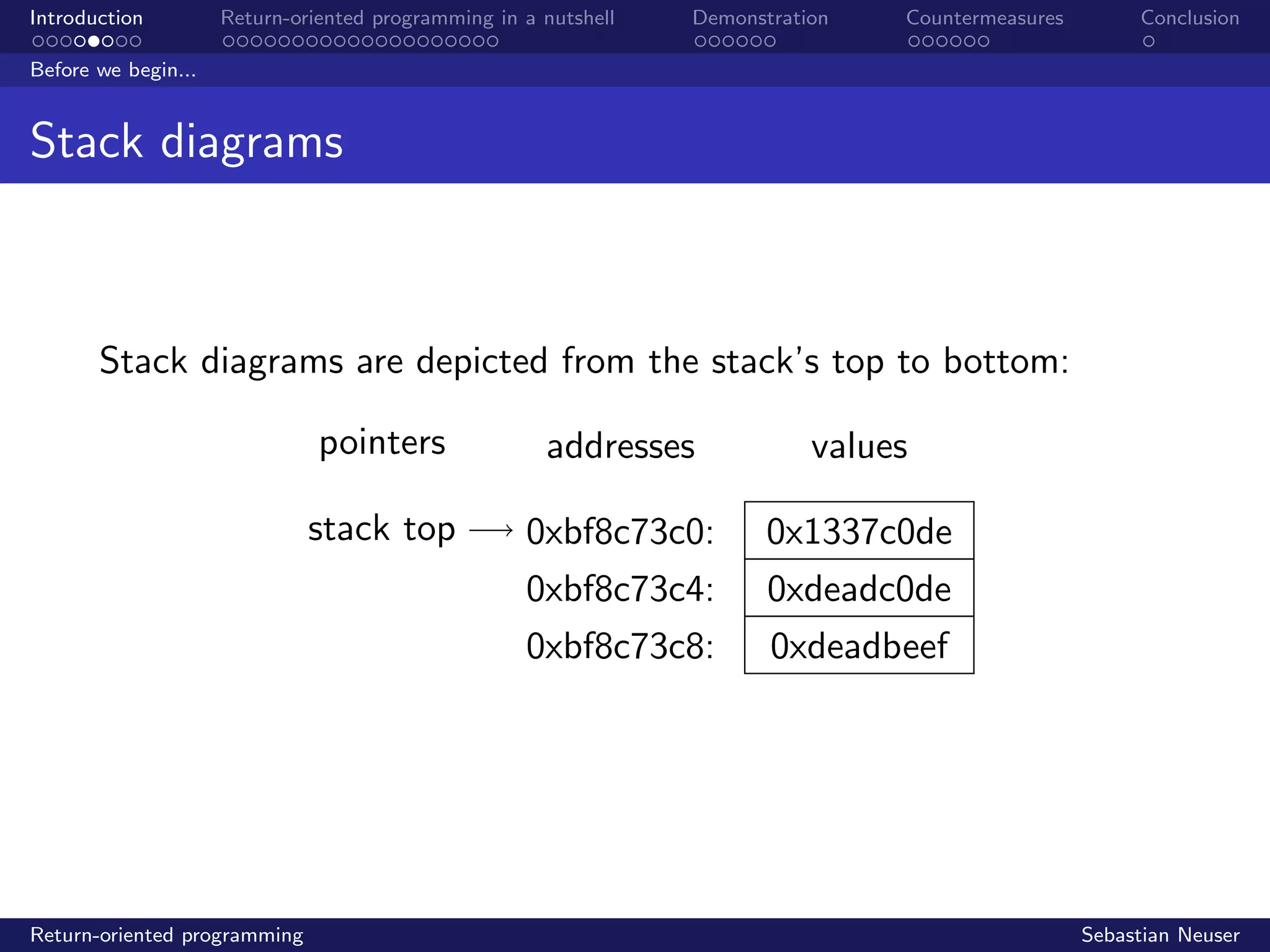
%esp
%ebp
0xbffff8b4:
0xbffff8b8:
0xbffff8bc:
...
0xbffff93c:
0xbffff940:
0xbffff944:
buffer[0]
buffer[1]
. . .
local var 1
local var 0
saved %ebp
return addr
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-26-2048.jpg)
![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
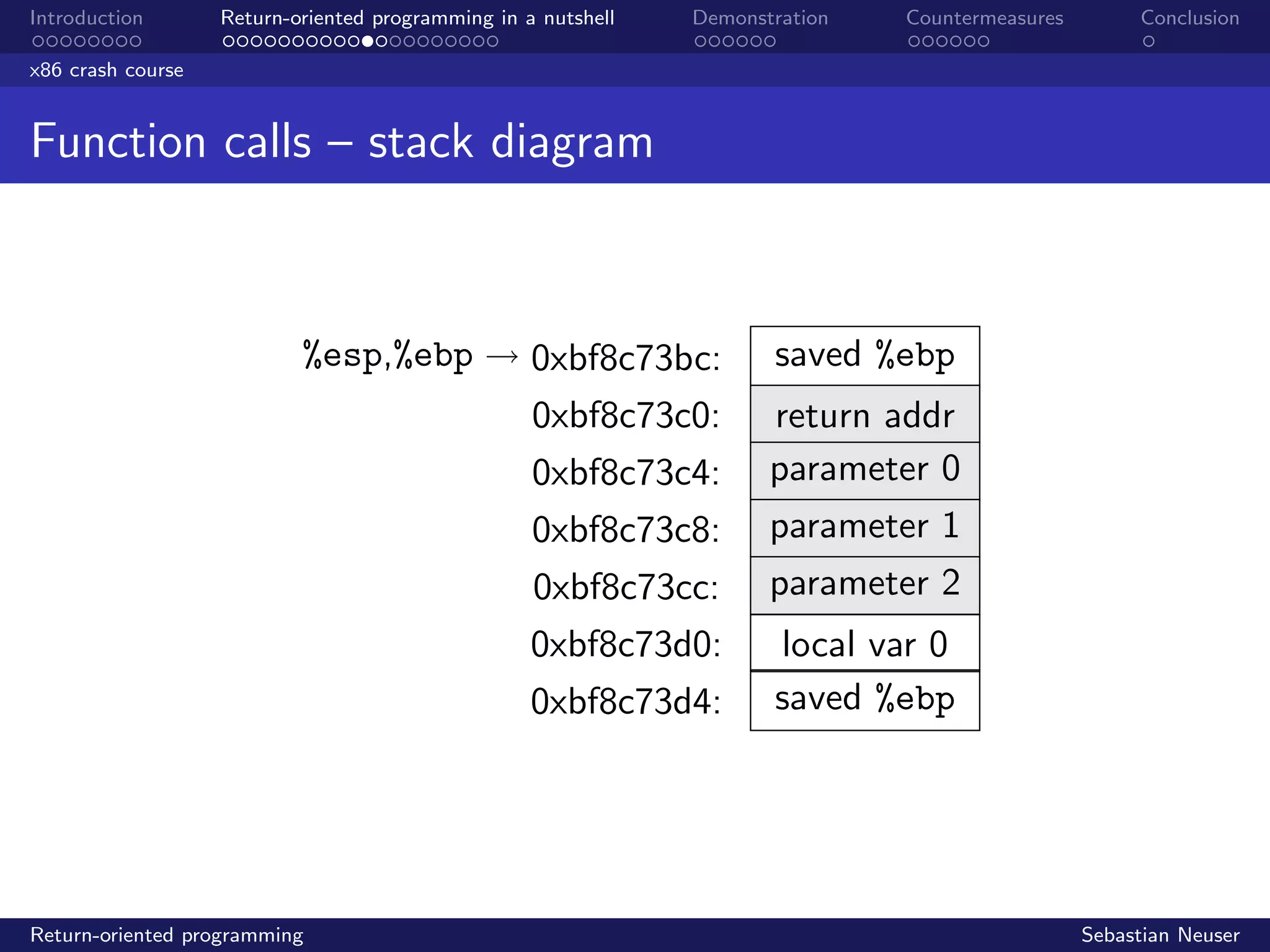
Stack buffer overflow
Meanwhile...
%esp
%ebp
0xbffff8b4:
0xbffff8b8:
0xbffff8bc:
...
0xbffff93c:
0xbffff940:
0xbffff944:
buffer[0]
buffer[1]
. . .
local var 1
local var 0
saved %ebp
return addr
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-27-2048.jpg)
![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
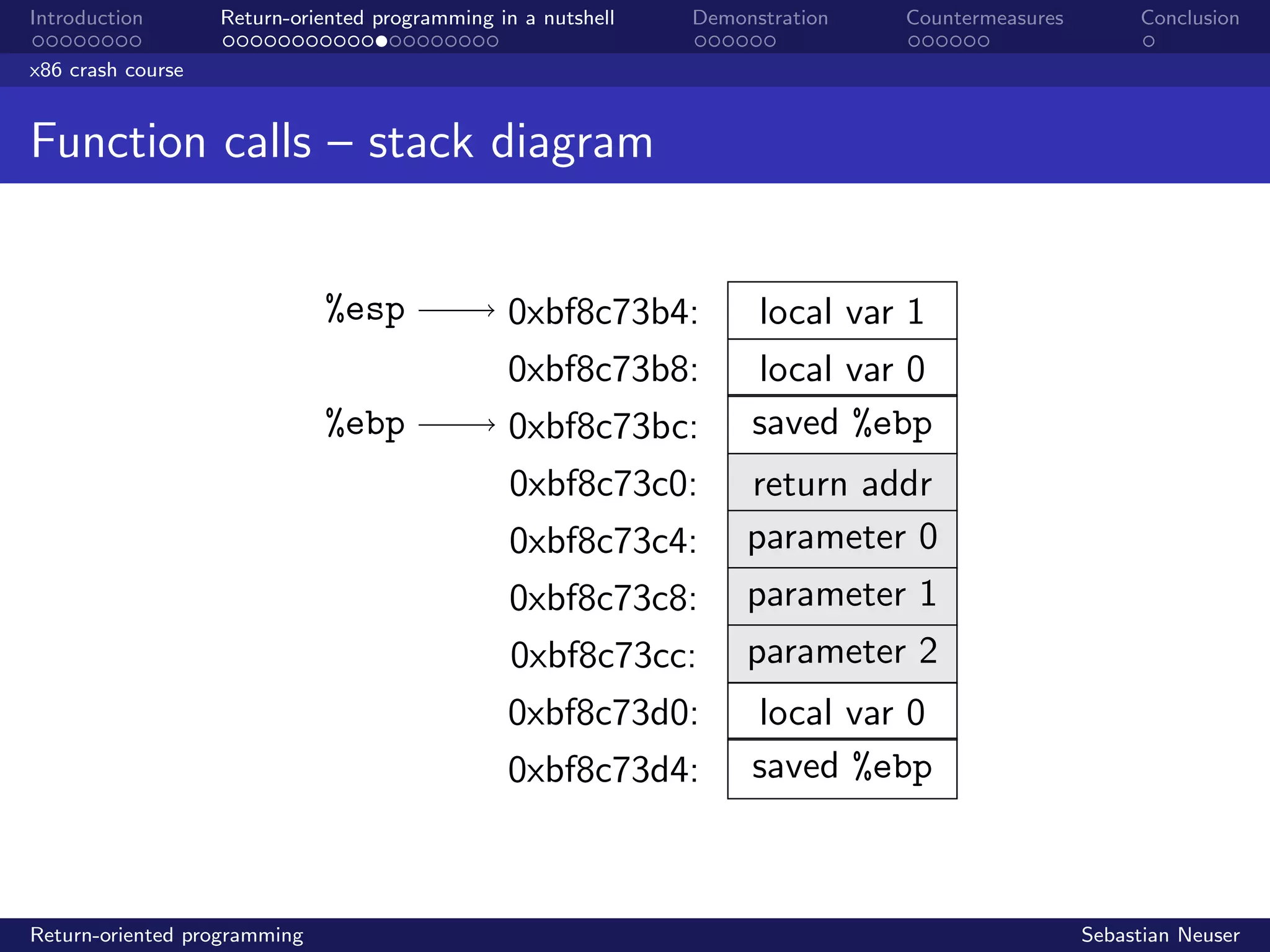
Stack buffer overflow
Meanwhile...
%esp
%ebp
0xbffff8b4:
0xbffff8b8:
0xbffff8bc:
...
0xbffff93c:
0xbffff940:
0xbffff944:
buffer[0]
buffer[1]
. . .
local var 1
local var 0
saved %ebp
return addr
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-28-2048.jpg)
![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
Stack buffer overflow
Meanwhile...
%esp
%ebp
0xbffff8b4:
0xbffff8b8:
0xbffff8bc:
...
0xbffff93c:
0xbffff940:
0xbffff944:
buffer[0]
buffer[1]
. . .
local var 1
local var 0
saved %ebp
return addr
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-29-2048.jpg)
![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
Stack buffer overflow
Meanwhile...
%esp
%ebp
0xbffff8b4:
0xbffff8b8:
0xbffff8bc:
...
0xbffff93c:
0xbffff940:
0xbffff944:
buffer[0]
buffer[1]
. . .
local var 1
local var 0
saved %ebp
return addr
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-30-2048.jpg)
![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
Stack buffer overflow
Boom!
%esp
%ebp
0xbffff8b4:
0xbffff8b8:
0xbffff8bc:
...
0xbffff93c:
0xbffff940:
0xbffff944:
buffer[0]
buffer[1]
. . .
local var 1
local var 0
saved %ebp
return addr
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-31-2048.jpg)

![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
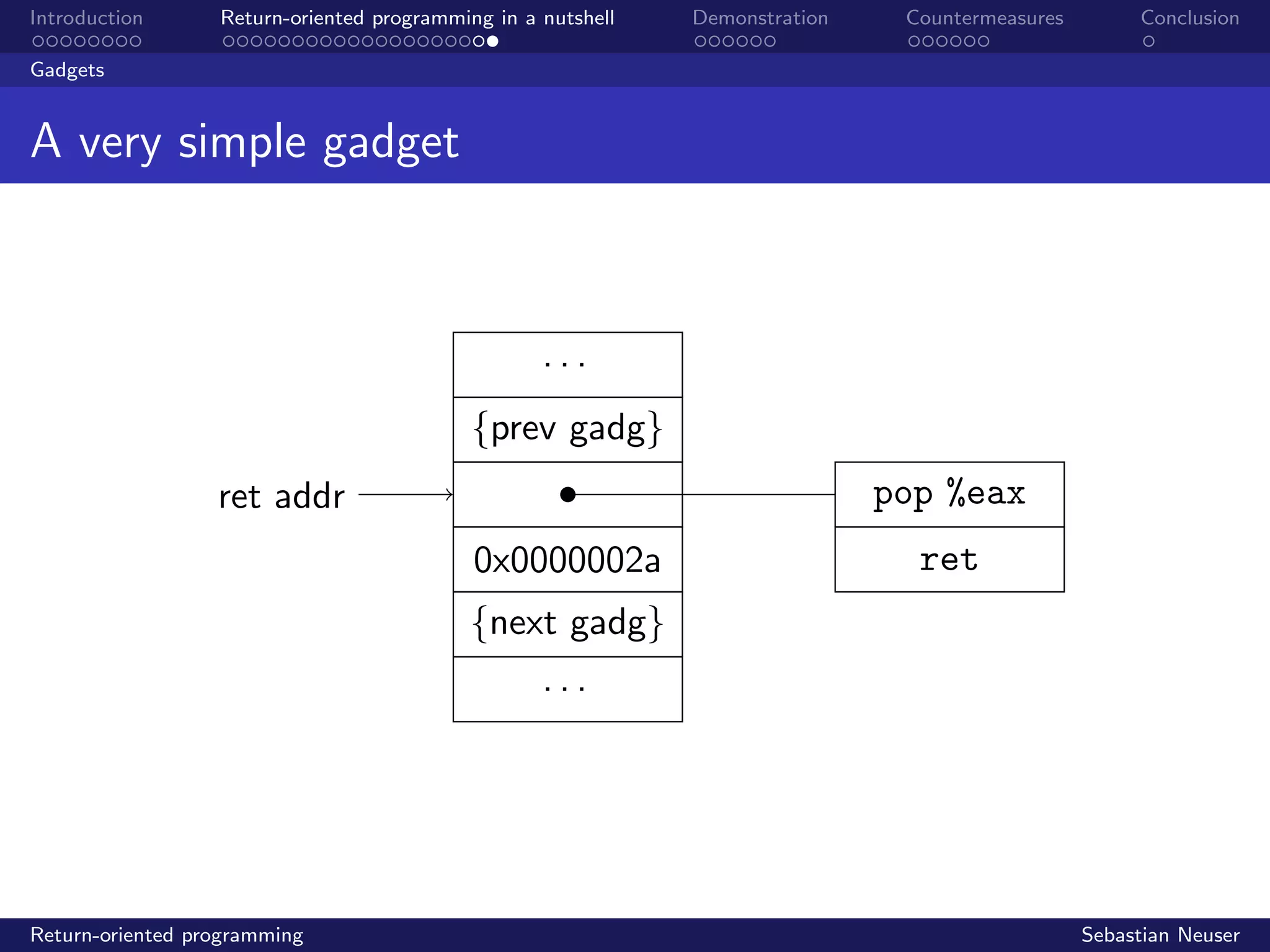
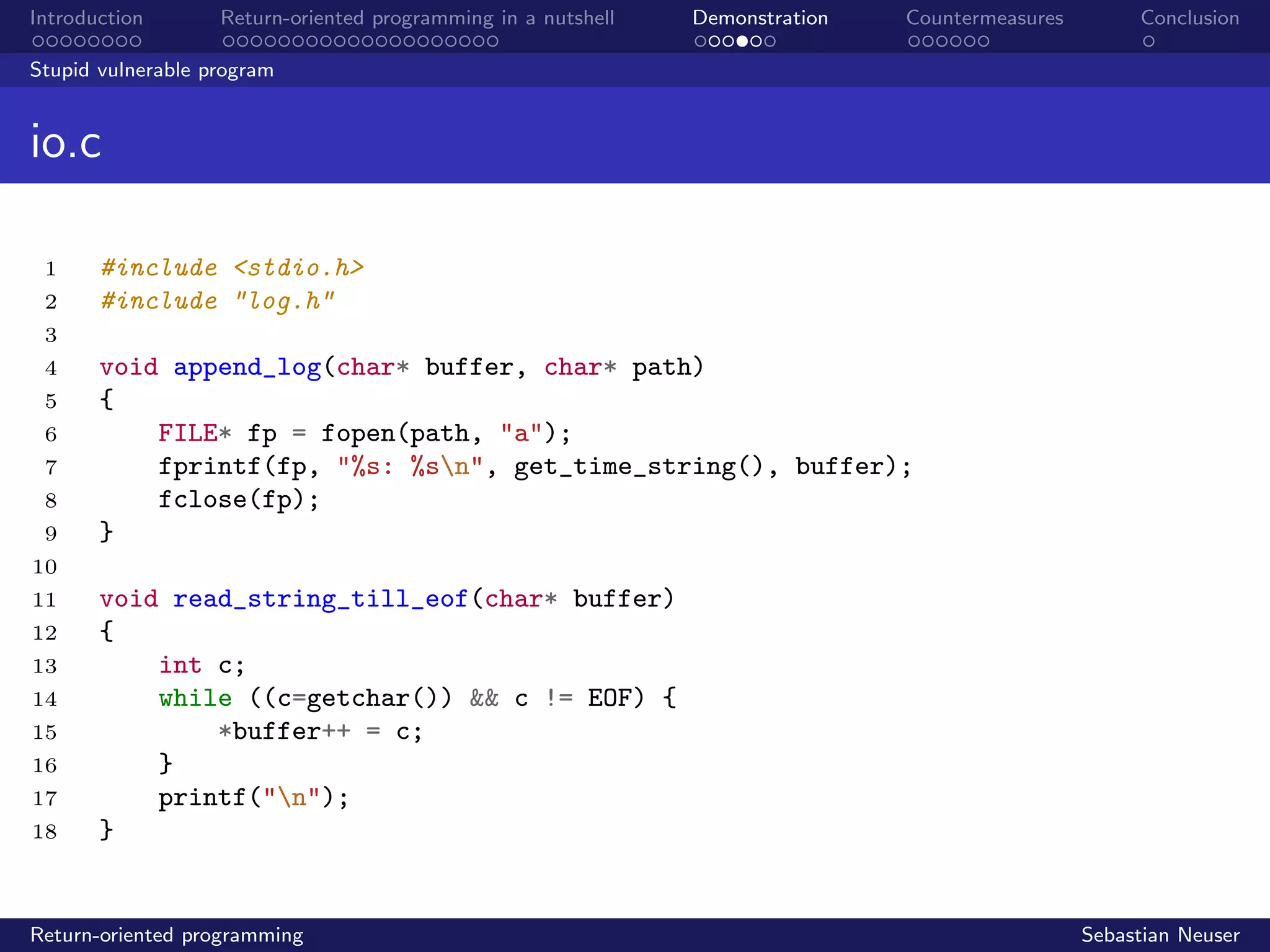
Stupid vulnerable program
log.h
1 //// io.c ////
2
3 // Appends the buffer to the log-file specified by the path
4 void append_log(char* buffer, char* path);
5
6 // Reads an input string to the buffer until EOF is read
7 void read_string_till_eof(char* buffer);
8
9
10
11 //// util.c ////
12
13 // Checks the program arguments
14 void check_args(int count, char* vector[]);
15
16 // Returns a string that describes the current timestamp
17 char* get_time_string(void);
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-36-2048.jpg)
![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
Stupid vulnerable program
log.c
1 #include <string.h>
2 #include "log.h"
3
4 int main(int argc, char* argv[])
5 {
6 check_args(argc, argv);
7
8 char buffer[512];
9 char logfile_path[32];
10
11 strcpy(logfile_path, argv[1]);
12 if (!strcasestr(logfile_path, ".log"))
13 strcat(logfile_path, ".log");
14
15 read_string_till_eof(buffer);
16 append_log(buffer, logfile_path);
17 return 0;
18 }
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-37-2048.jpg)
![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
Stupid vulnerable program
util.c
1 #include <stdio.h>
2 #include <stdlib.h>
3 #include <string.h>
4 #include <time.h>
5
6 void check_args(int count, char* vector[])
7 {
8 if (count != 2) {
9 printf("Usage: log <log file>n");
10 exit(0);
11 }
12 }
13
14 char* get_time_string(void)
15 {
16 time_t timestamp = time(NULL);
17 char* time_string = ctime(×tamp);
18 time_string[strlen(time_string)-1] = ’0’;
19 return time_string;
20 }
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-39-2048.jpg)


![Introduction Return-oriented programming in a nutshell Demonstration Countermeasures Conclusion
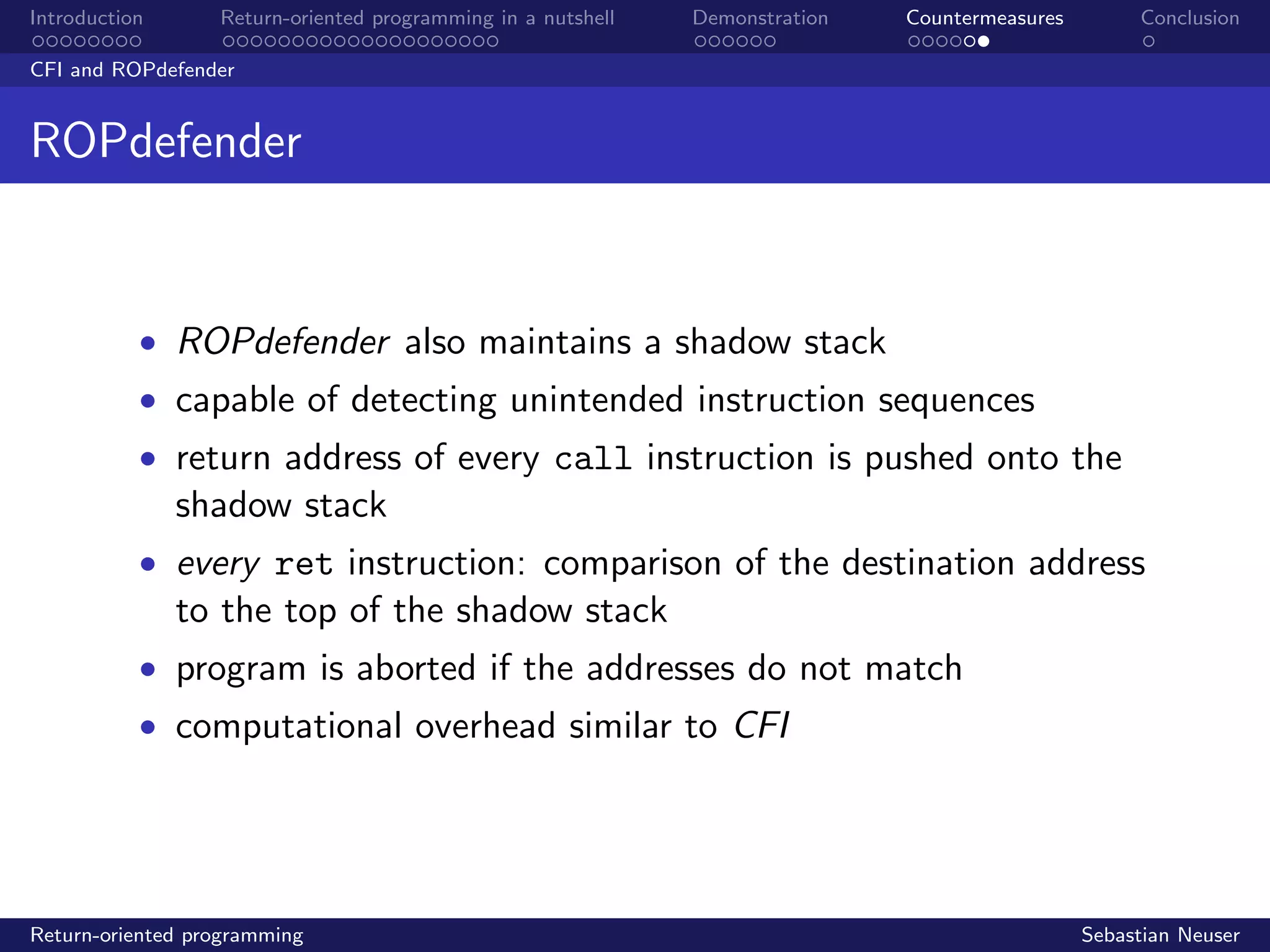
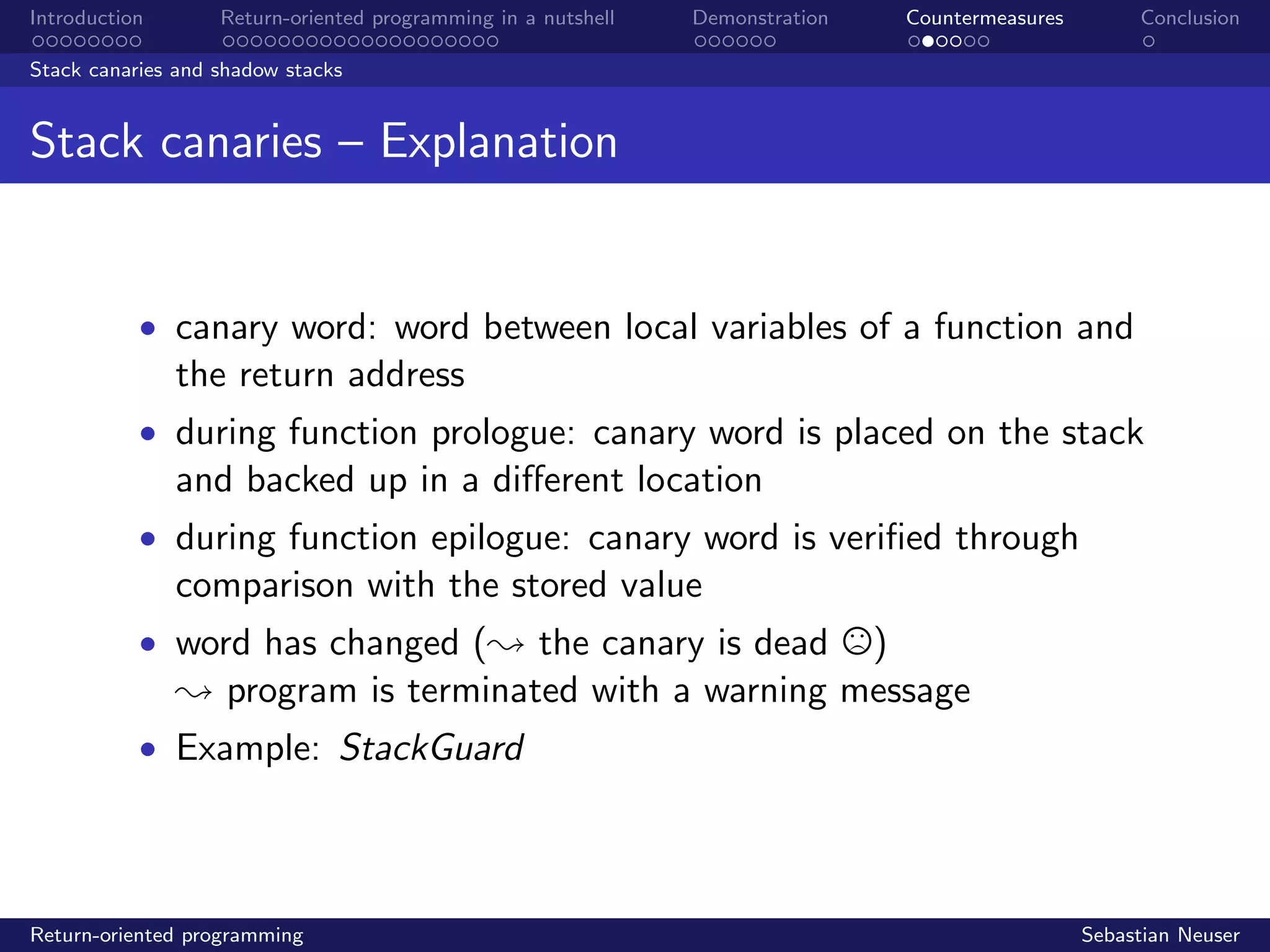
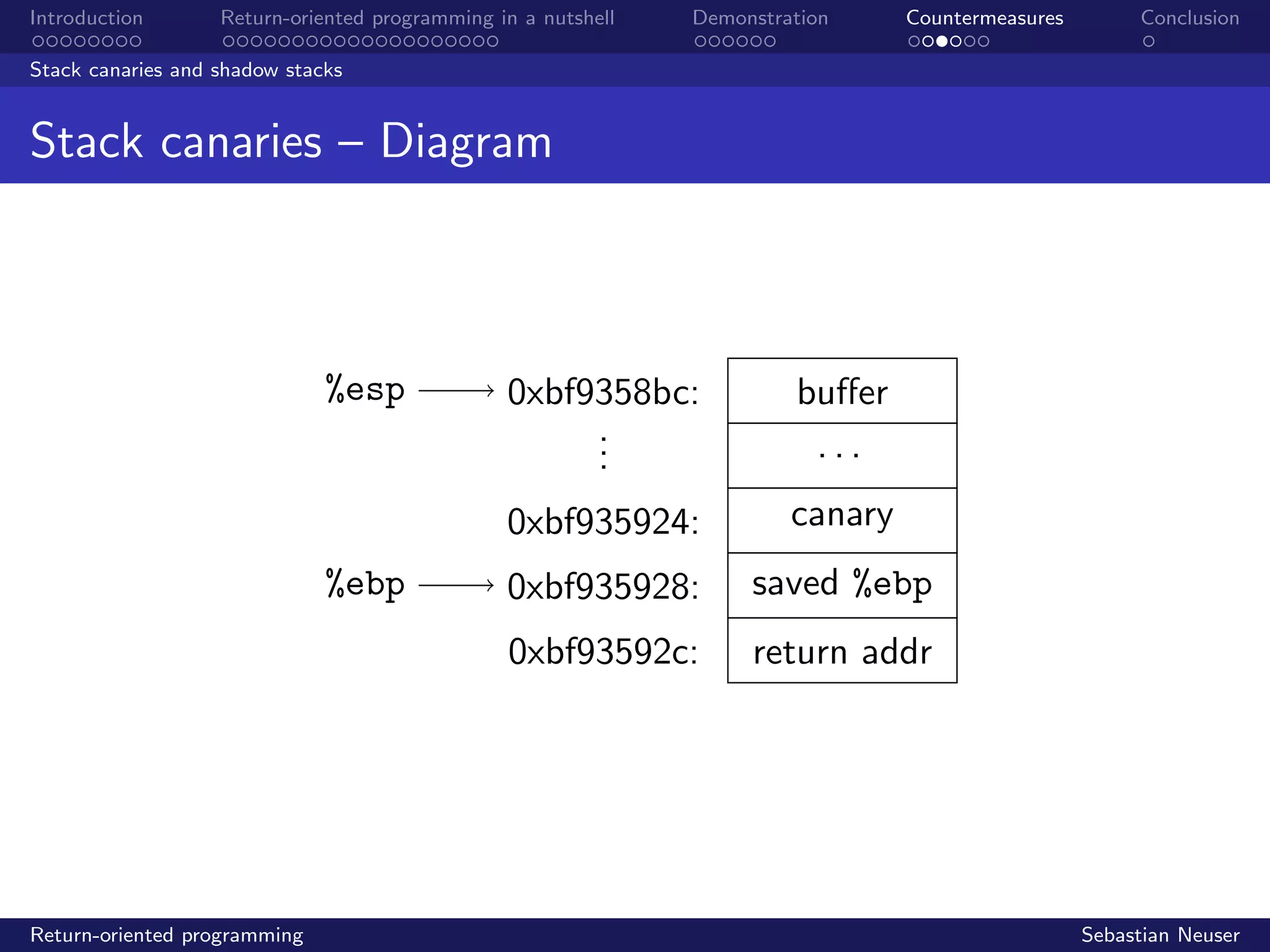
CFI and ROPdefender
Control Flow Integrity
• control flow graph maps all function calls
• function prologues and epilogues are modified at runtime
• targets of call and ret instructions are correlated with the
anticipated control flow in the graph
• opcodes do not match ; program is aborted
• significant computational overhead with a factor typically in
the range of [1.5, 3.5]
Return-oriented programming Sebastian Neuser](https://image.slidesharecdn.com/hagglreturn-orientedprogramming-140508132847-phpapp01/75/Return-oriented-programming-46-2048.jpg)