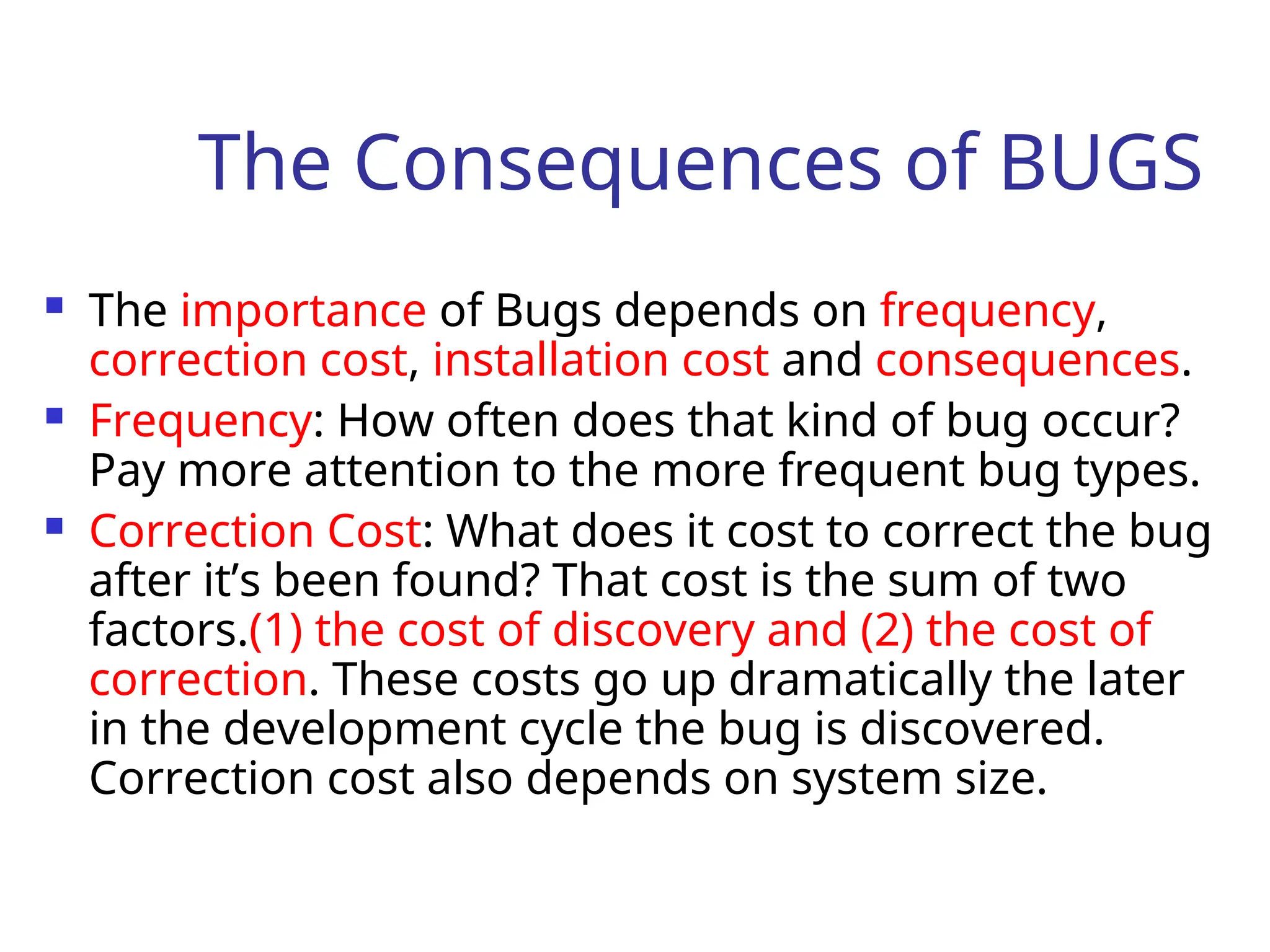
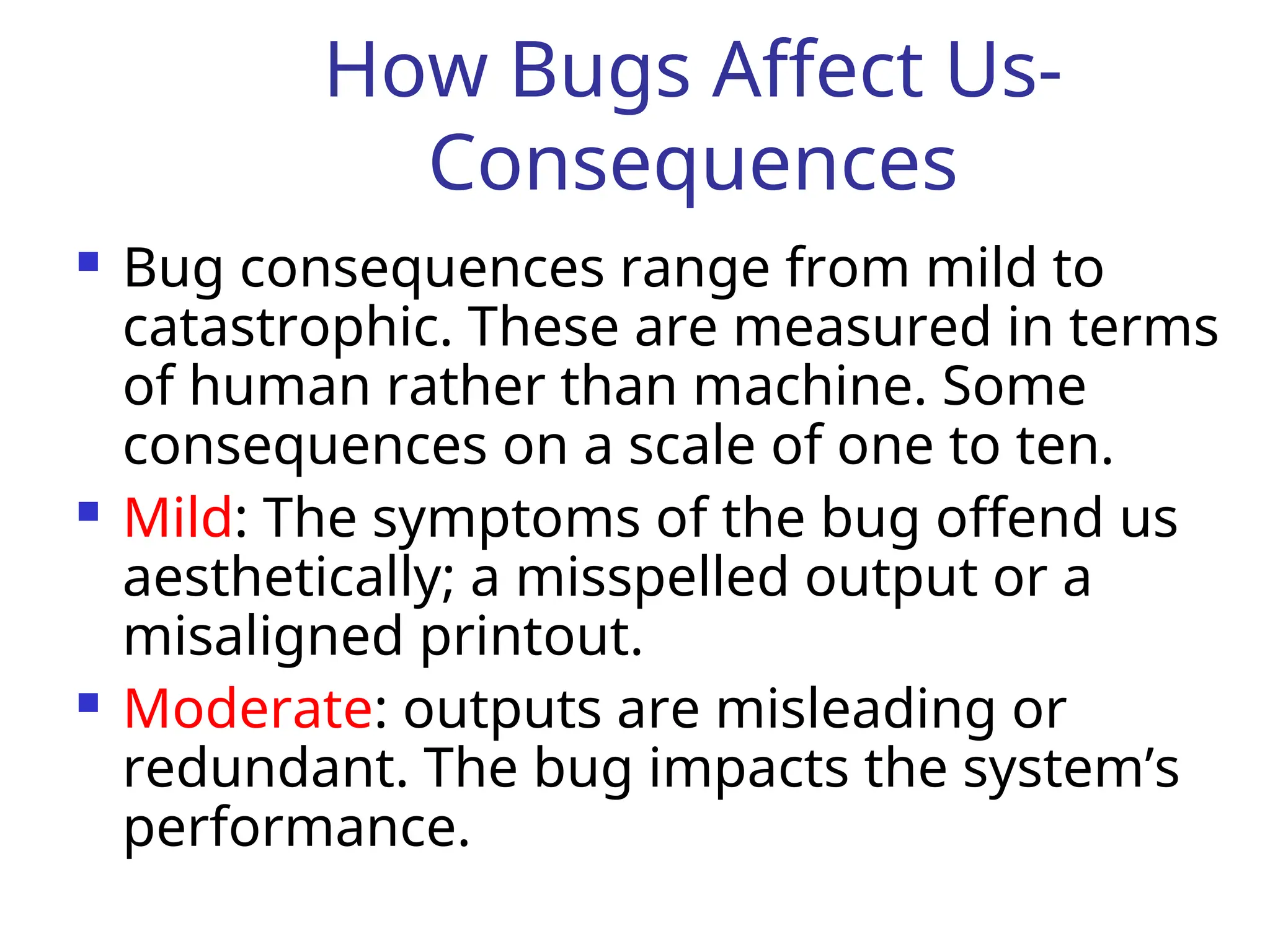
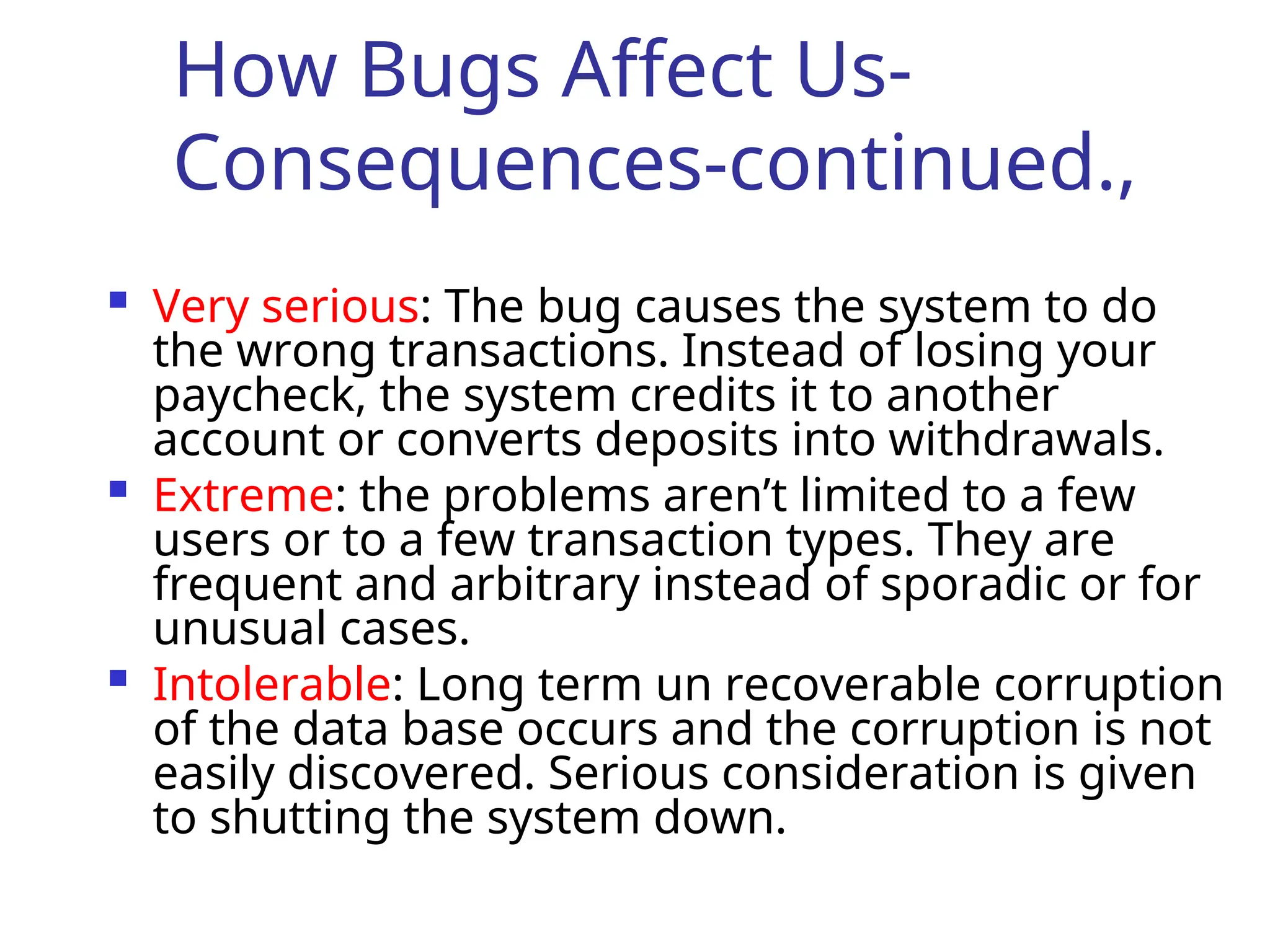
The document outlines the taxonomy of software bugs, detailing their importance based on frequency, correction, installation costs, and consequences. It categorizes bugs into various types, such as functional, structural, data, and coding bugs, and emphasizes the impact of bugs on system performance and user experience. It also discusses strategies for bug detection and prevention, as well as the significance of intervention in addressing bugs throughout the software development process.