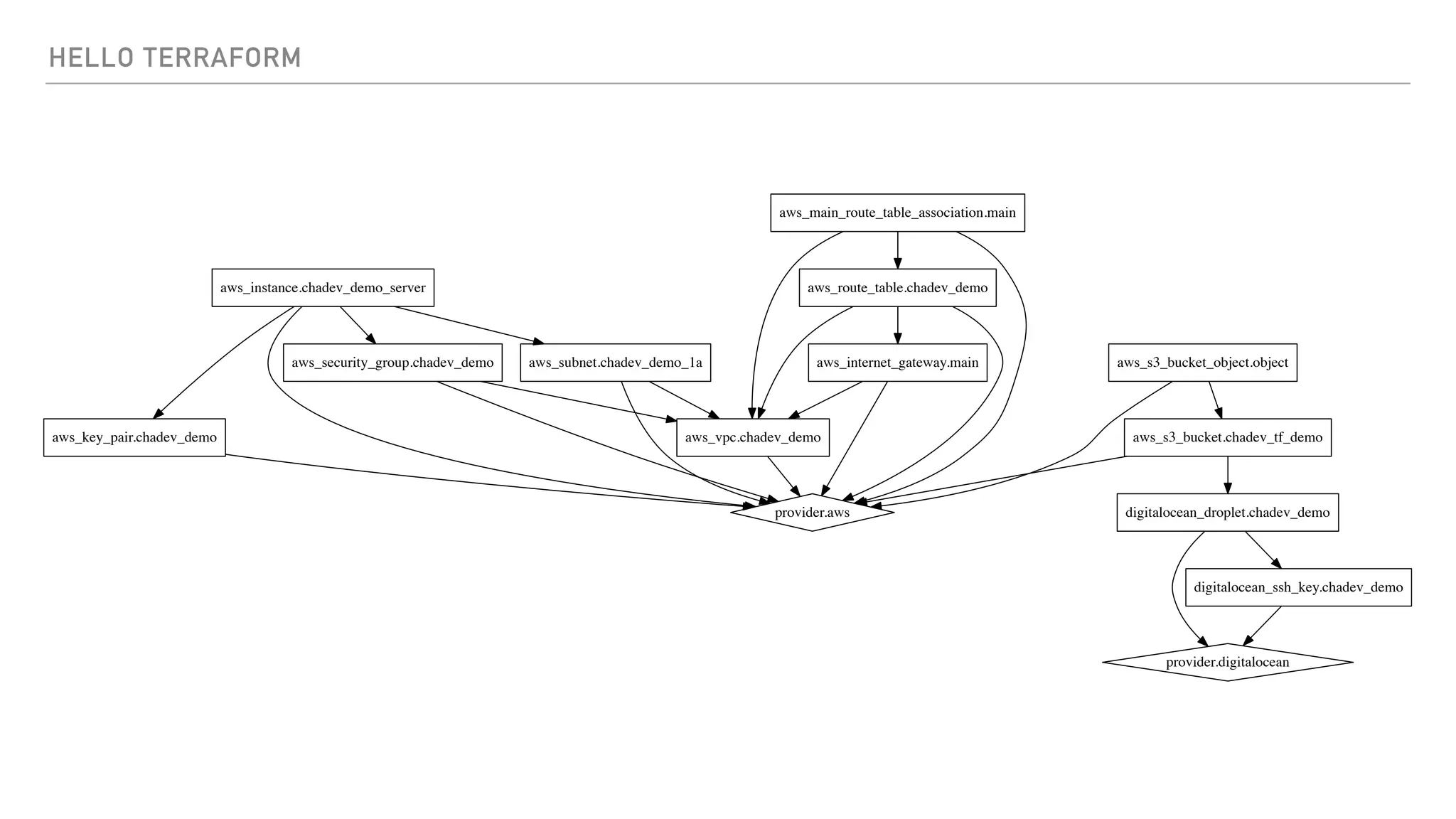
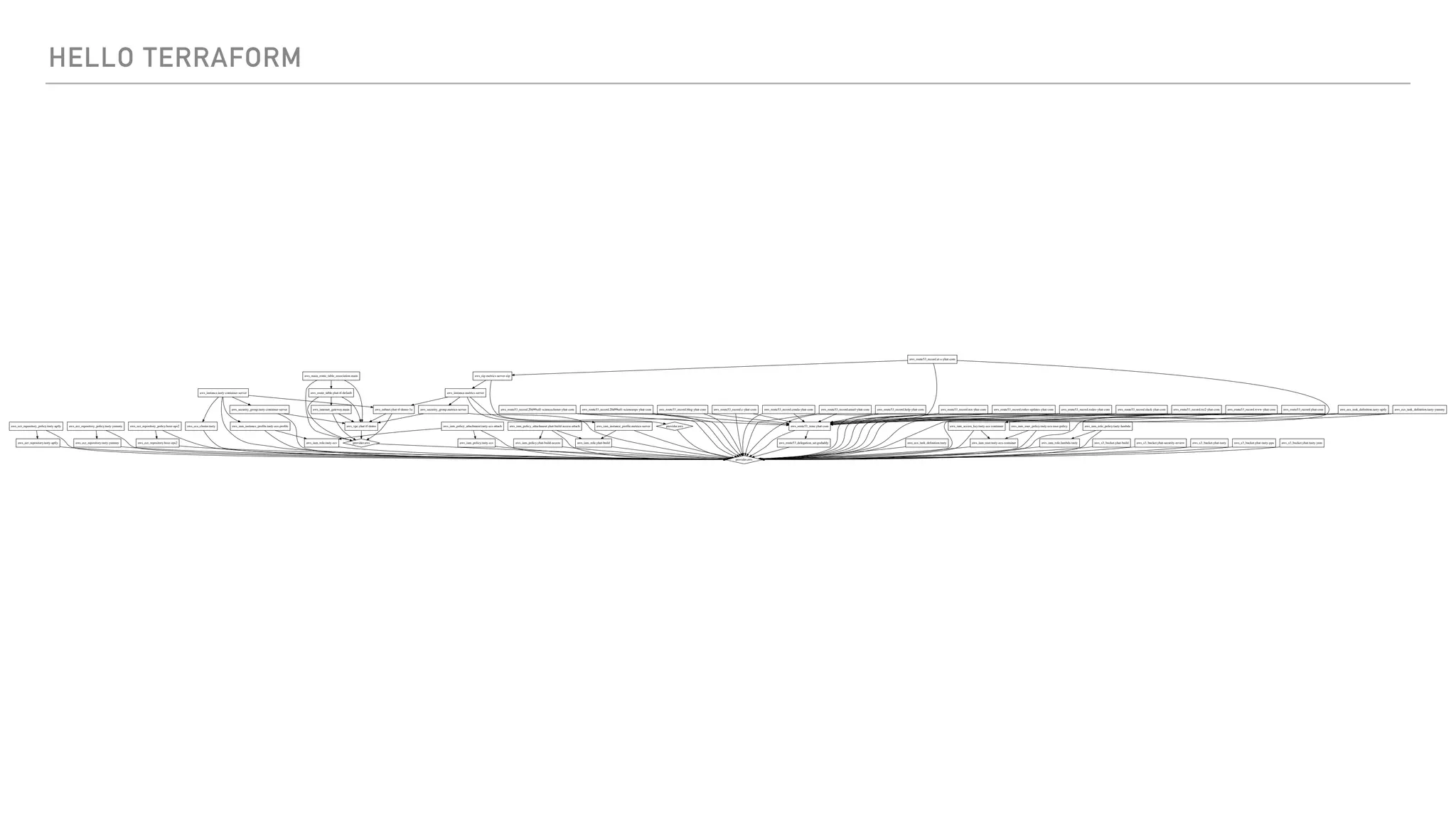
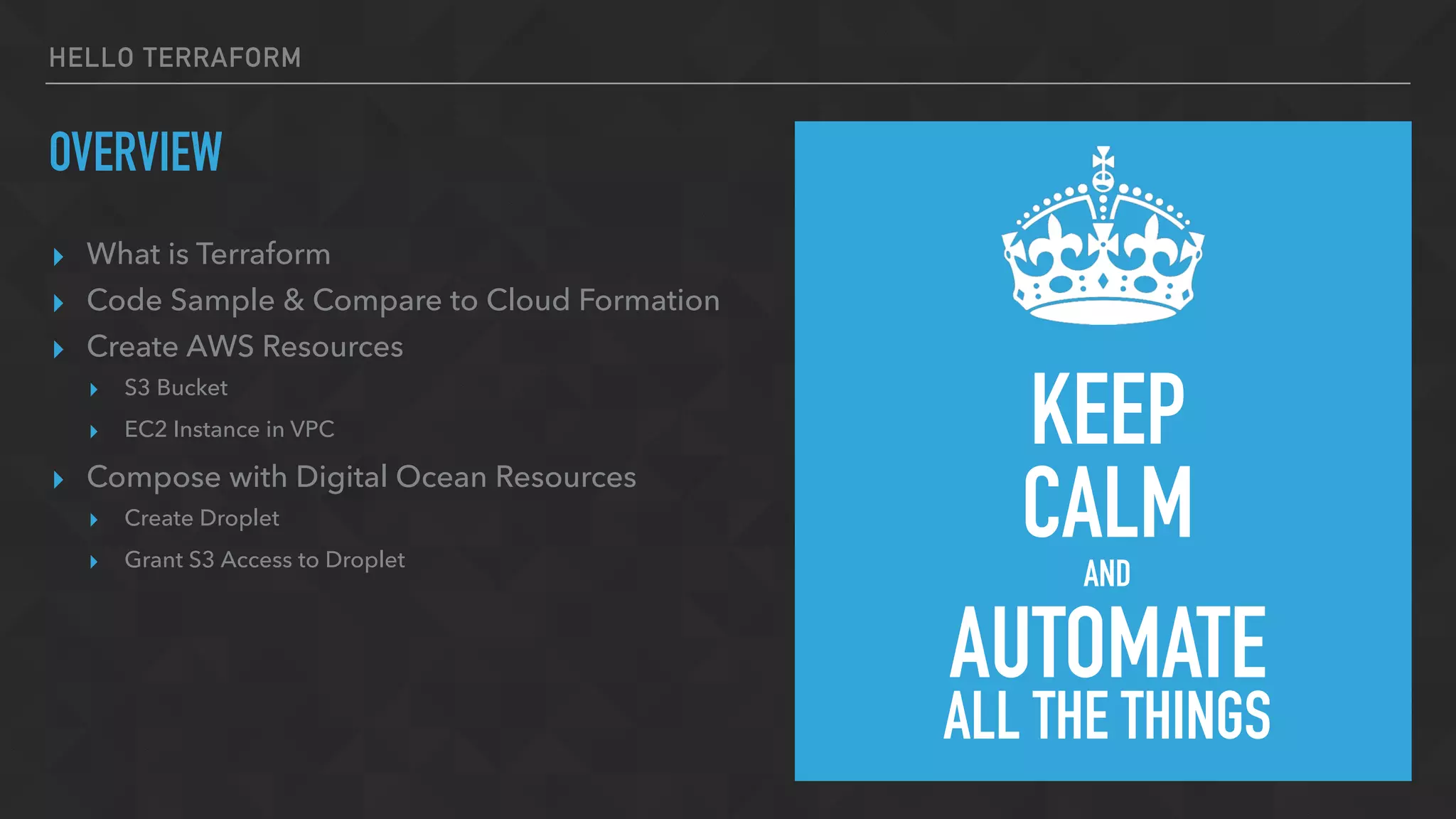
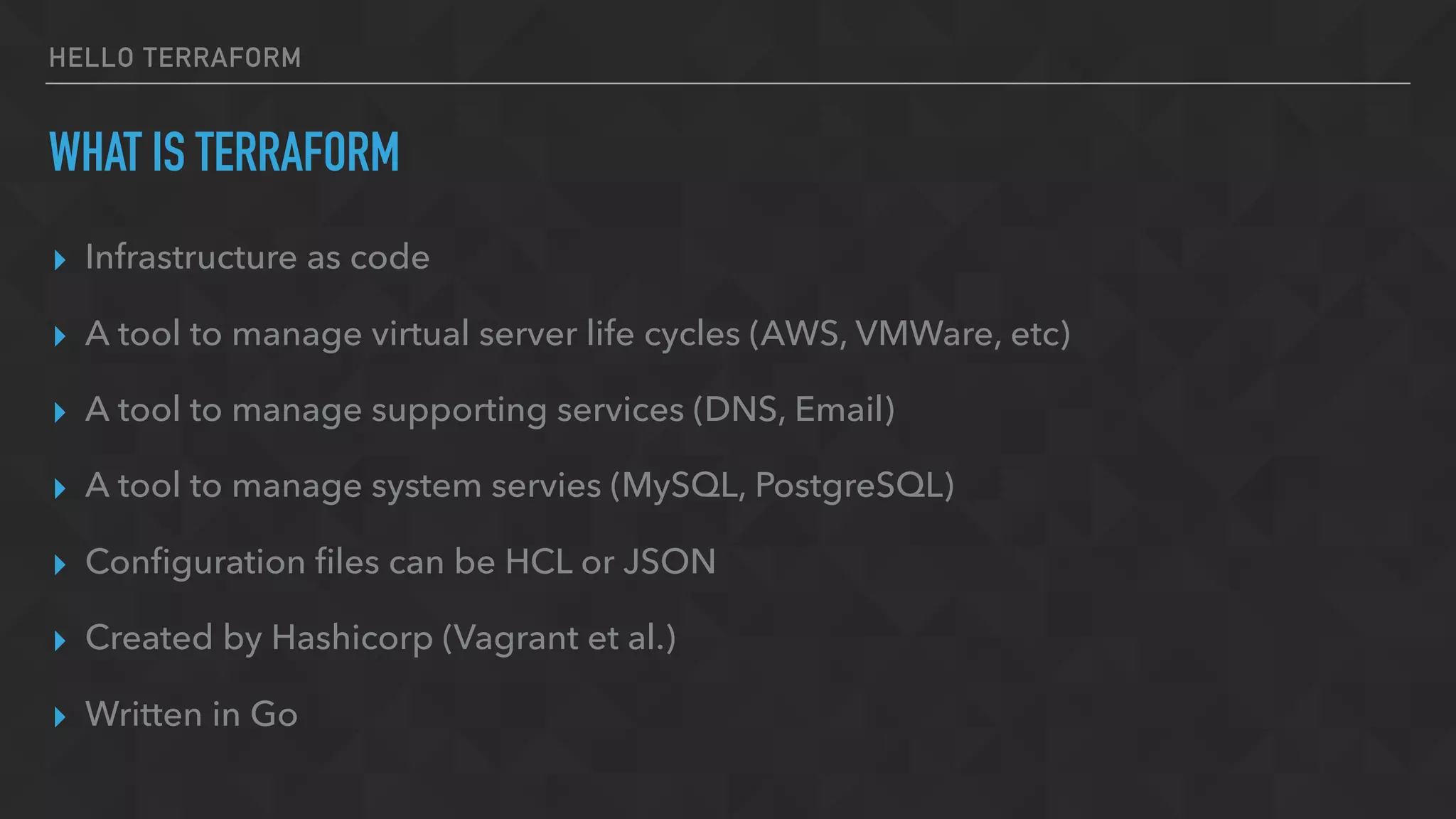
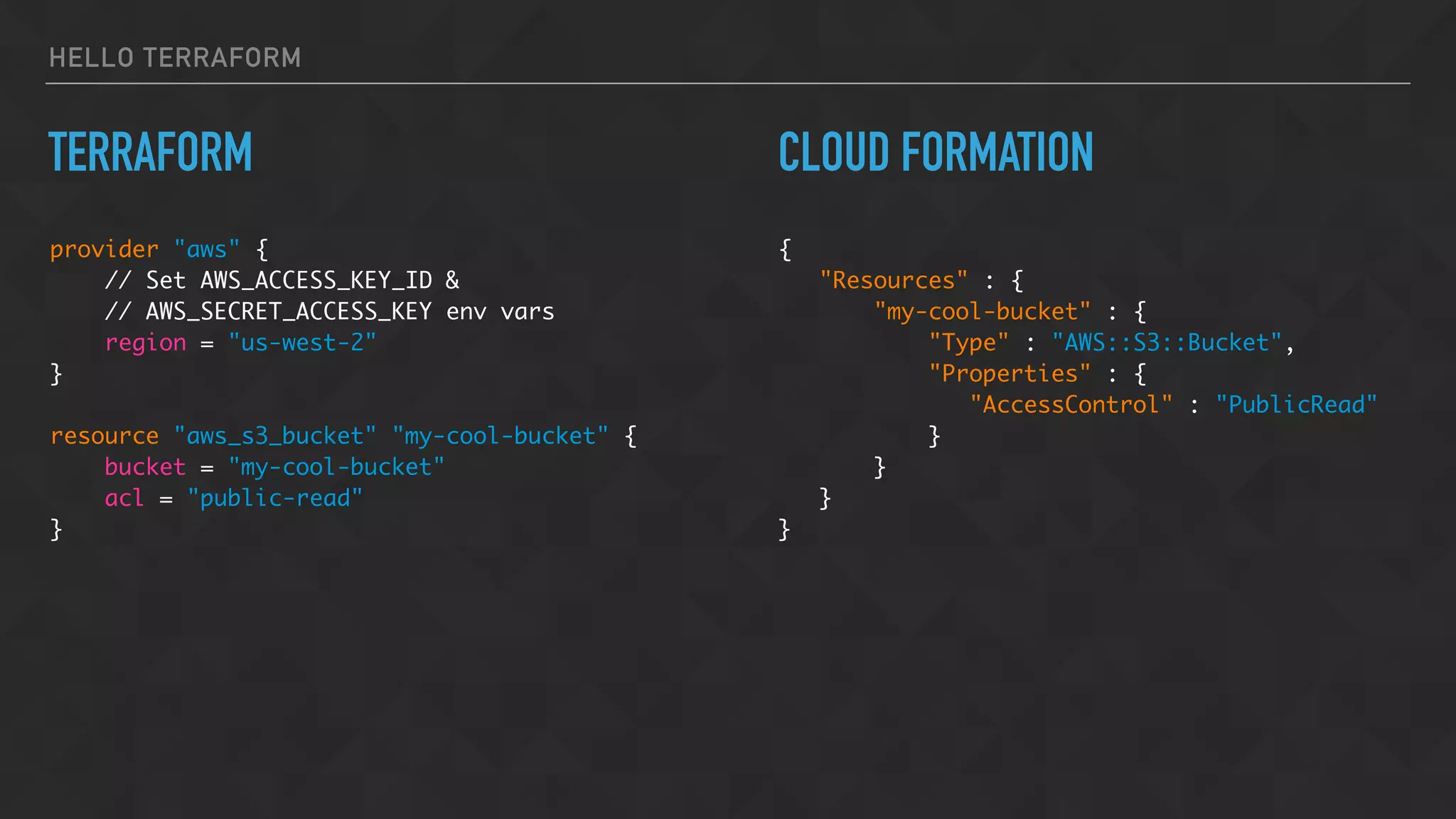
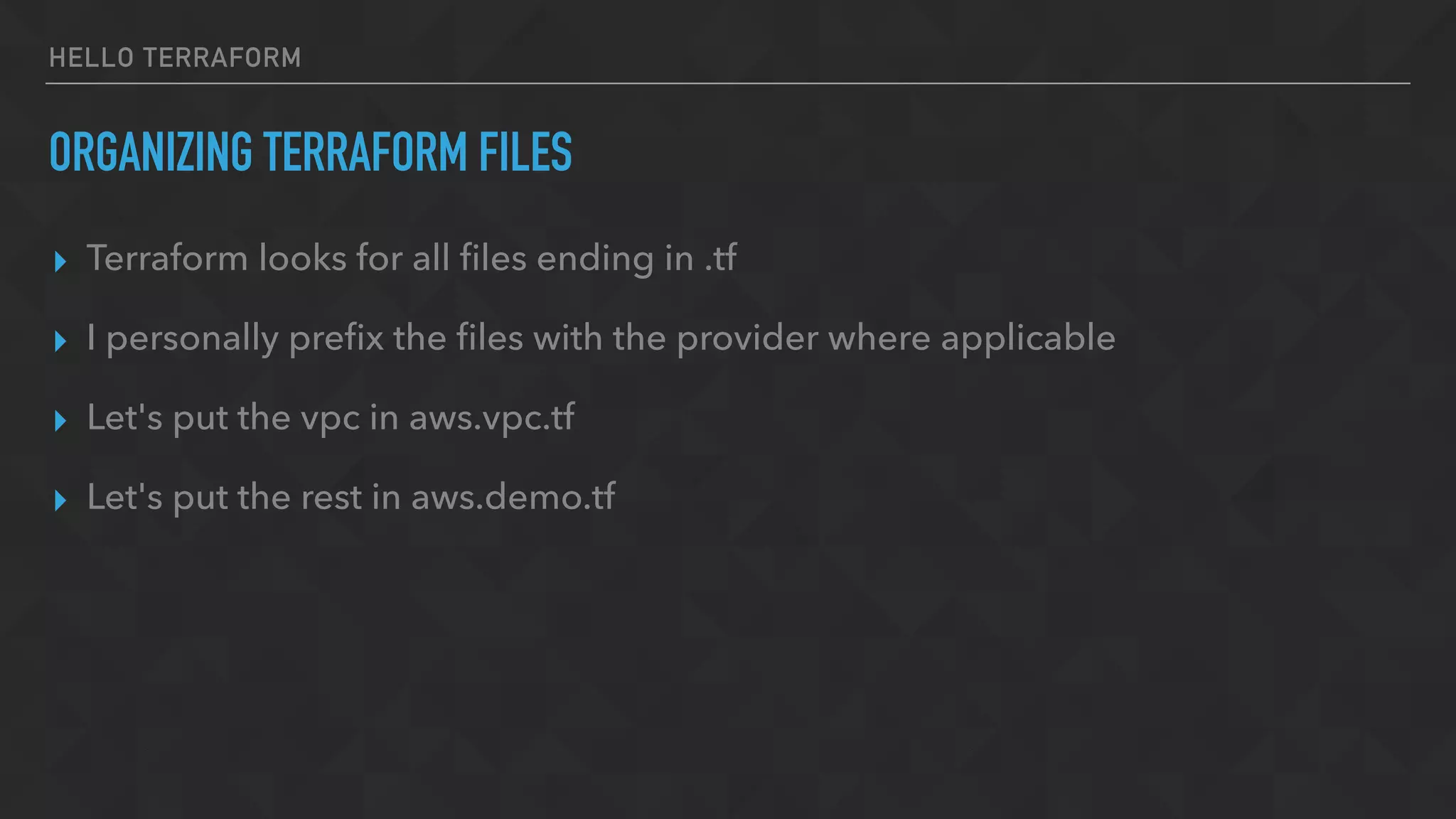
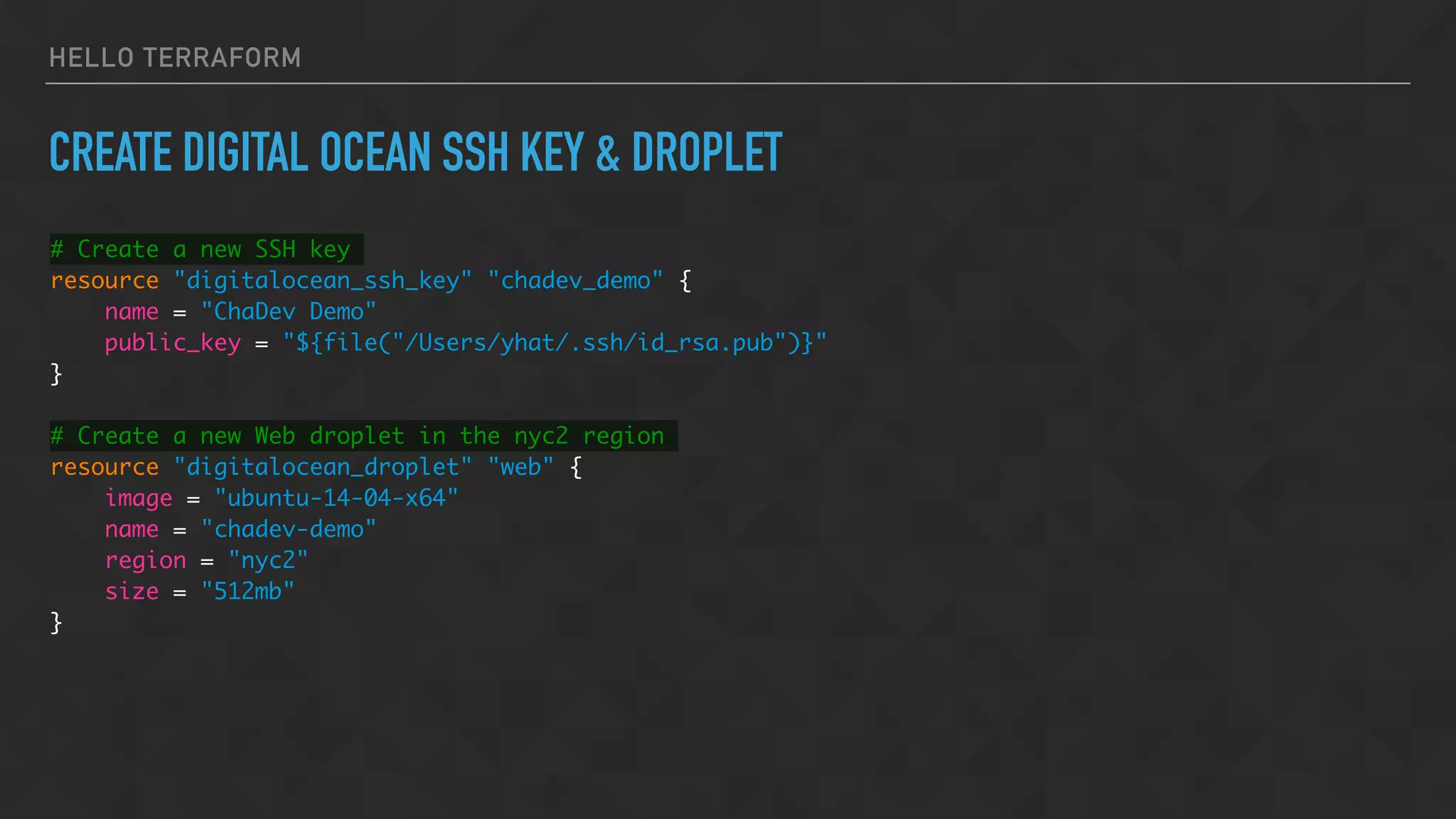
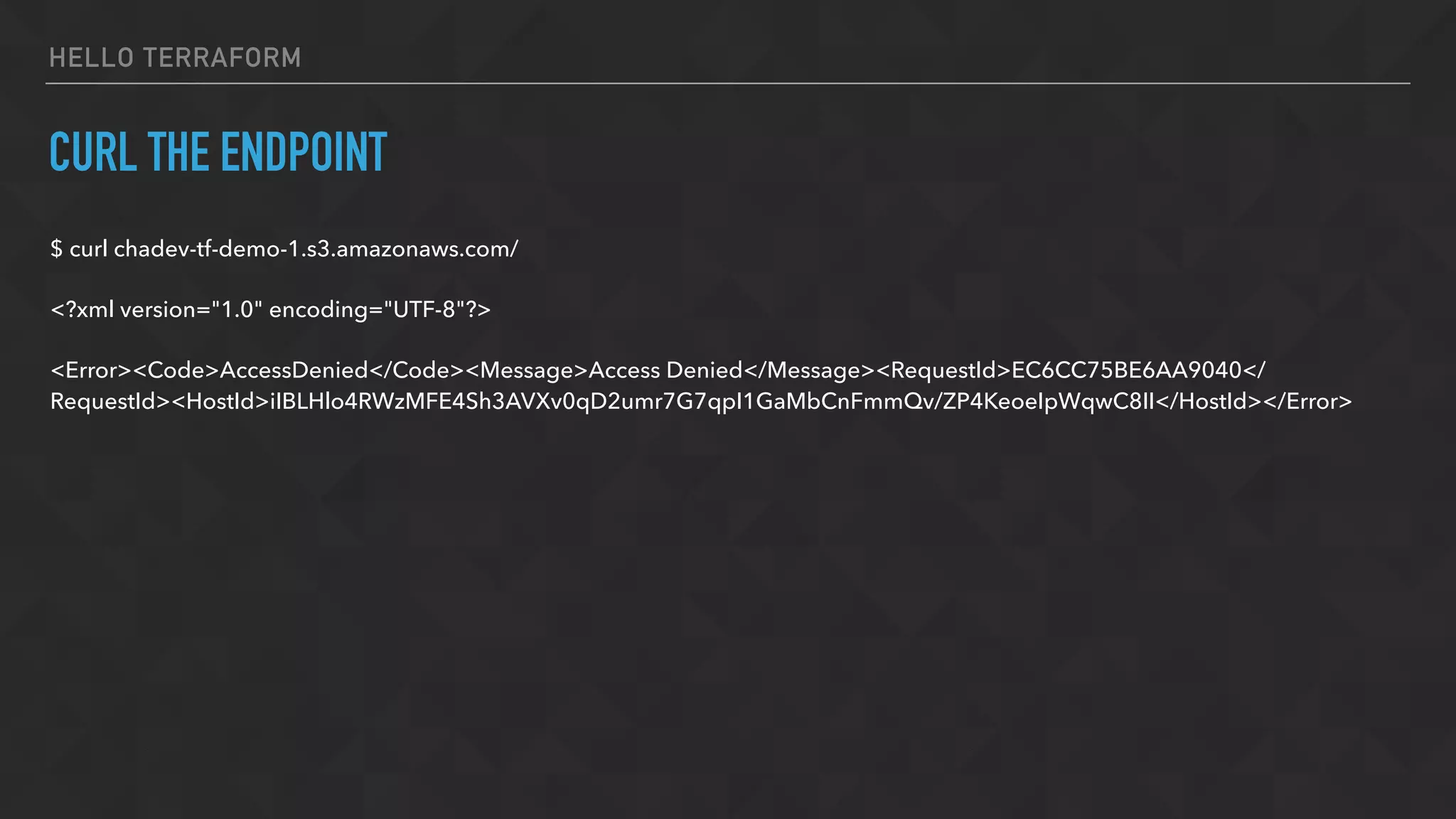
The document provides an overview of Terraform, a tool for managing infrastructure as code, detailing its capabilities in creating and managing AWS resources like S3 buckets and EC2 instances. It includes code samples, configuration examples, and error-handling tips during deployment. Additionally, it discusses organizing Terraform files and integrating with services like DigitalOcean.




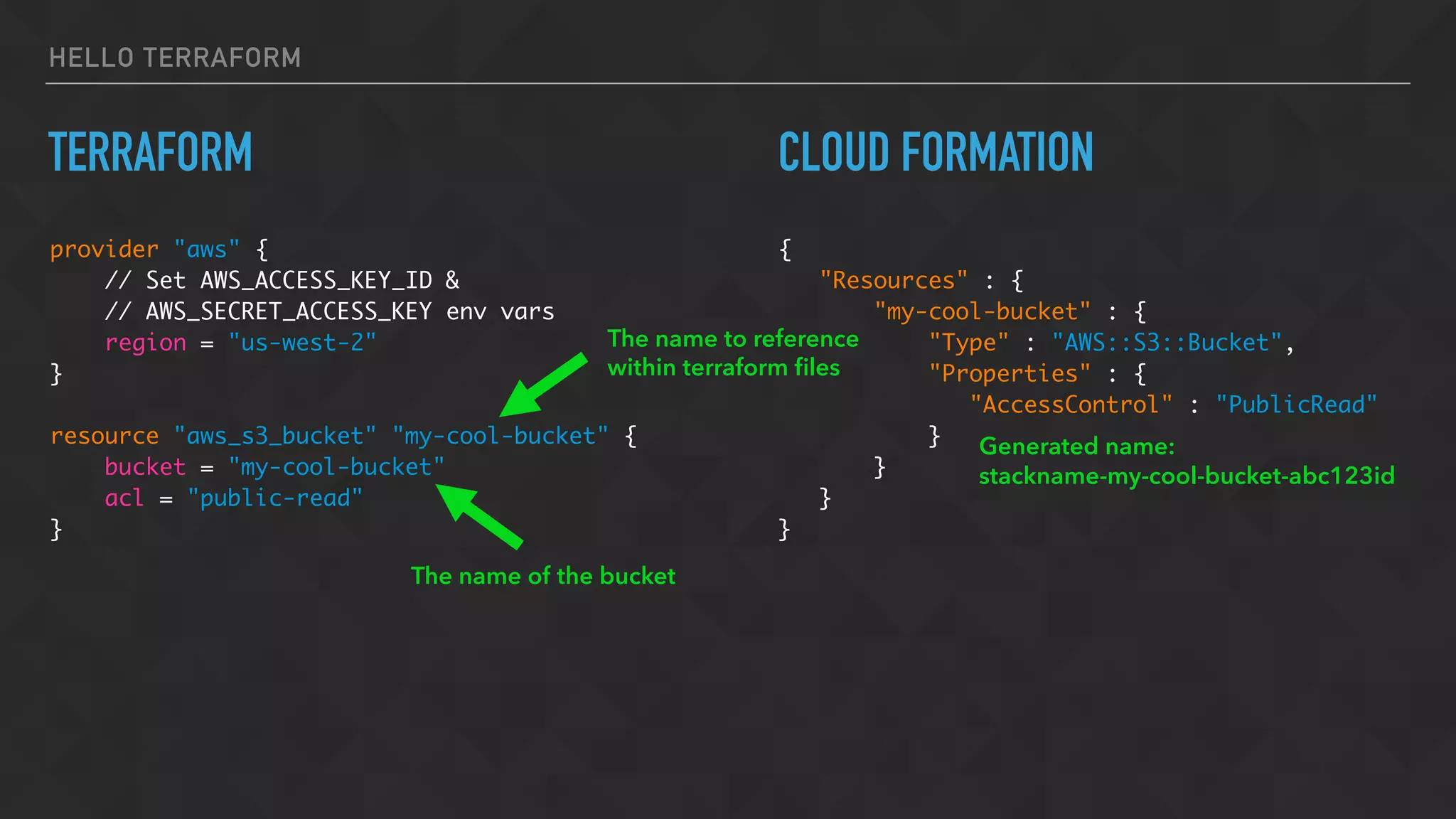

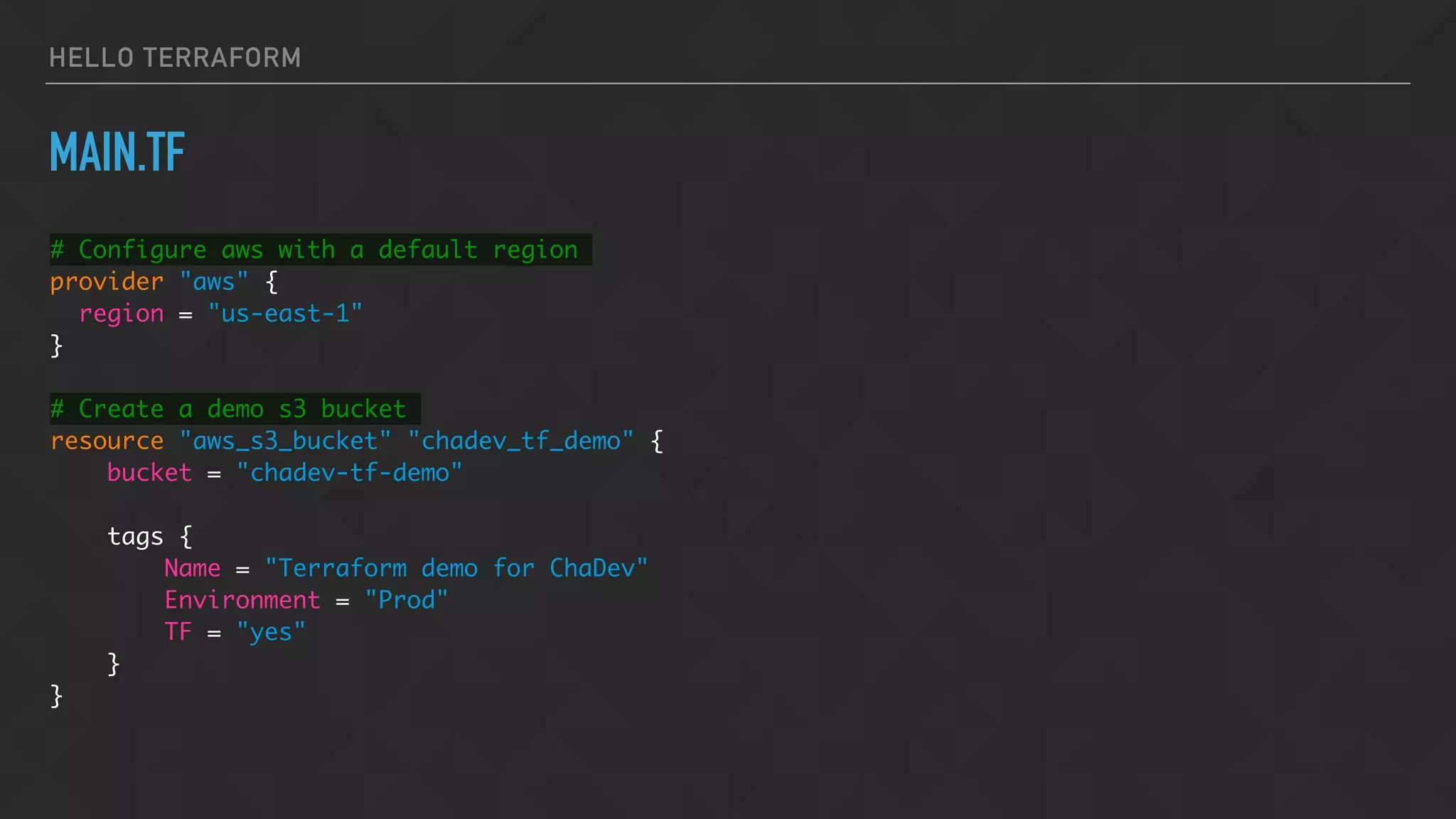
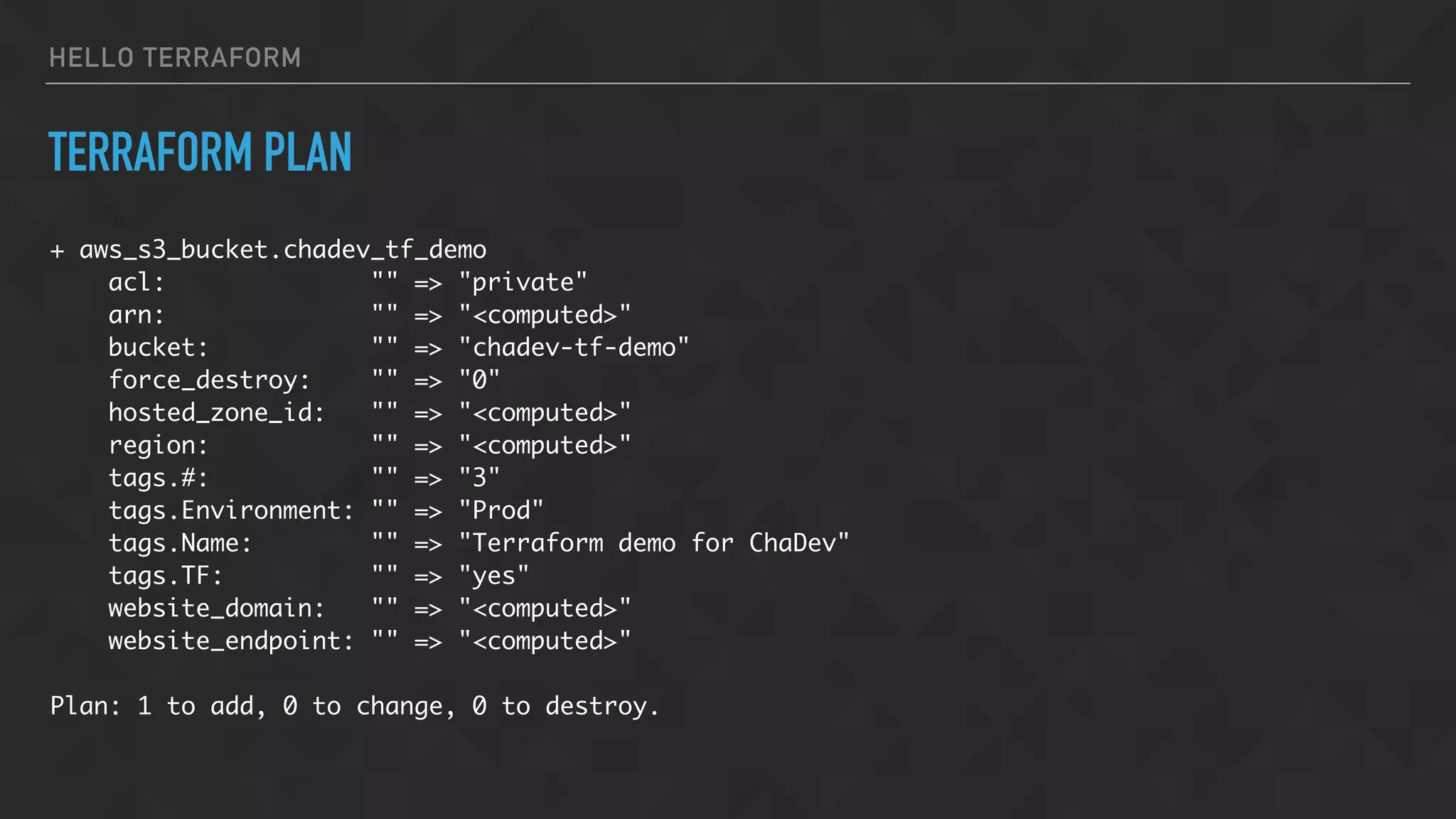
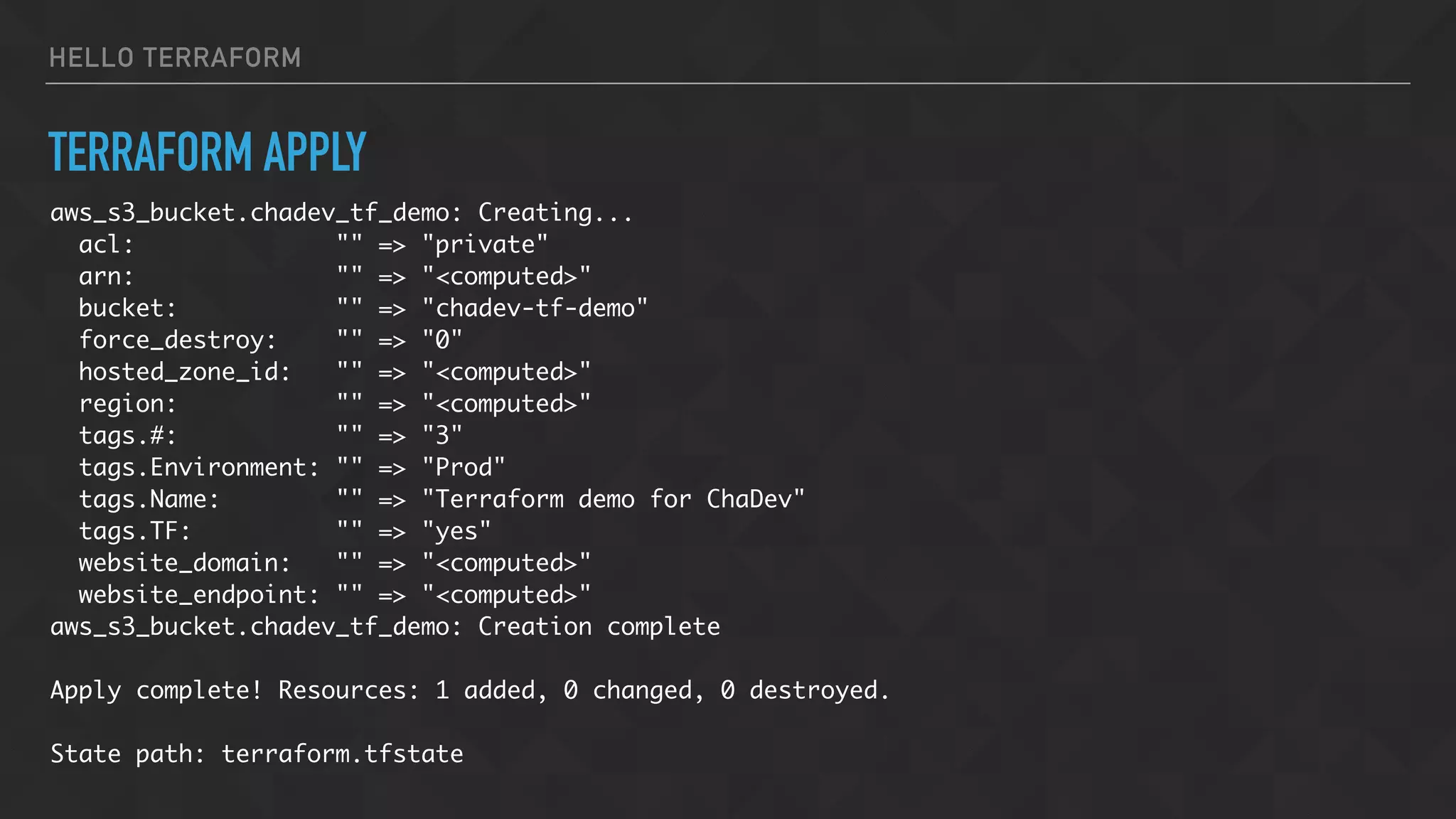
![HELLO TERRAFORM
TERRAFORM STATE
"version": 1,
"serial": 1,
"modules": [
{
"path": [
"root"
],
"outputs": {},
"resources": {
"aws_s3_bucket.chadev_tf_demo": {
"type": "aws_s3_bucket",
"primary": {
"id": "chadev-tf-demo",
"attributes": {
"acl": "private",
"arn": "arn:aws:s3:::chadev-tf-demo",
"bucket": "chadev-tf-demo",
"cors_rule.#": "0",
"force_destroy": "false",
"hosted_zone_id": "Z3AQBSTGFYJSTF",
"id": "chadev-tf-demo",
"policy": "",
"region": "us-east-1",
"tags.#": "3",
"tags.Environment": "Prod",
"tags.Name": "Terraform demo for ChaDev",
"tags.TF": "yes",
"website.#": "0"](https://image.slidesharecdn.com/chadevtf-160930001034/75/Terraform-An-Overview-Introduction-16-2048.jpg)
![HELLO TERRAFORM
TANGENT: USING REMOTE STATE AS A DEPENDENCY
resource "terraform_remote_state" "core" {
backend = "s3"
config {
bucket = "a-tf-state-bucket"
key = "hosted/core.json"
region = "us-east-1"
}
}
resource "aws_route53_record" "my-awesome-subdomain.yhat.com" {
zone_id = "${terraform_remote_state.core.output.yhat-zone-id}"
name = "my-awesome-subdomain.yhat.com"
type = "A"
ttl = "60"
records = [
"${aws_eip.my-elastic-ip.public_ip}"
]
}](https://image.slidesharecdn.com/chadevtf-160930001034/75/Terraform-An-Overview-Introduction-18-2048.jpg)

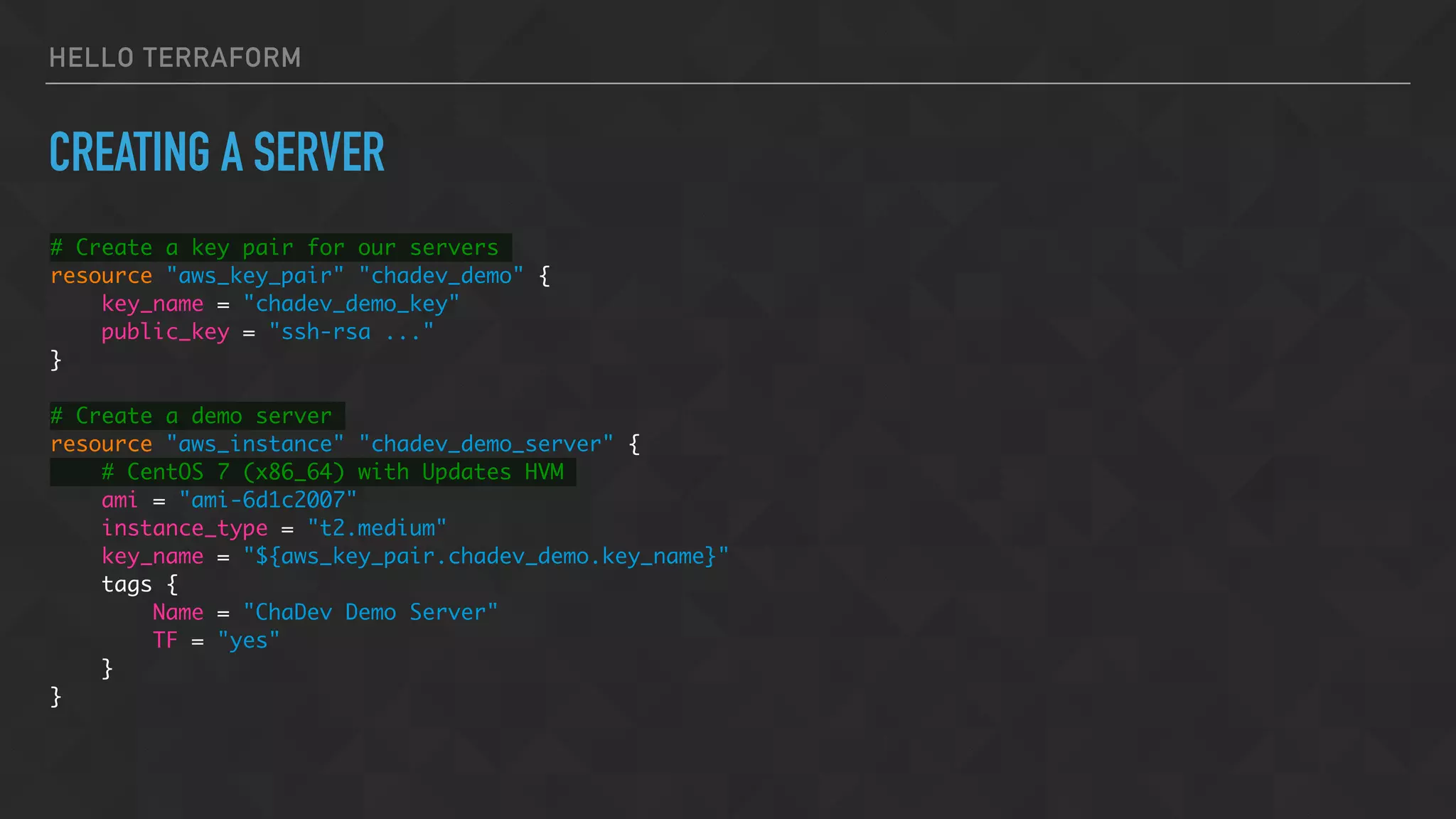

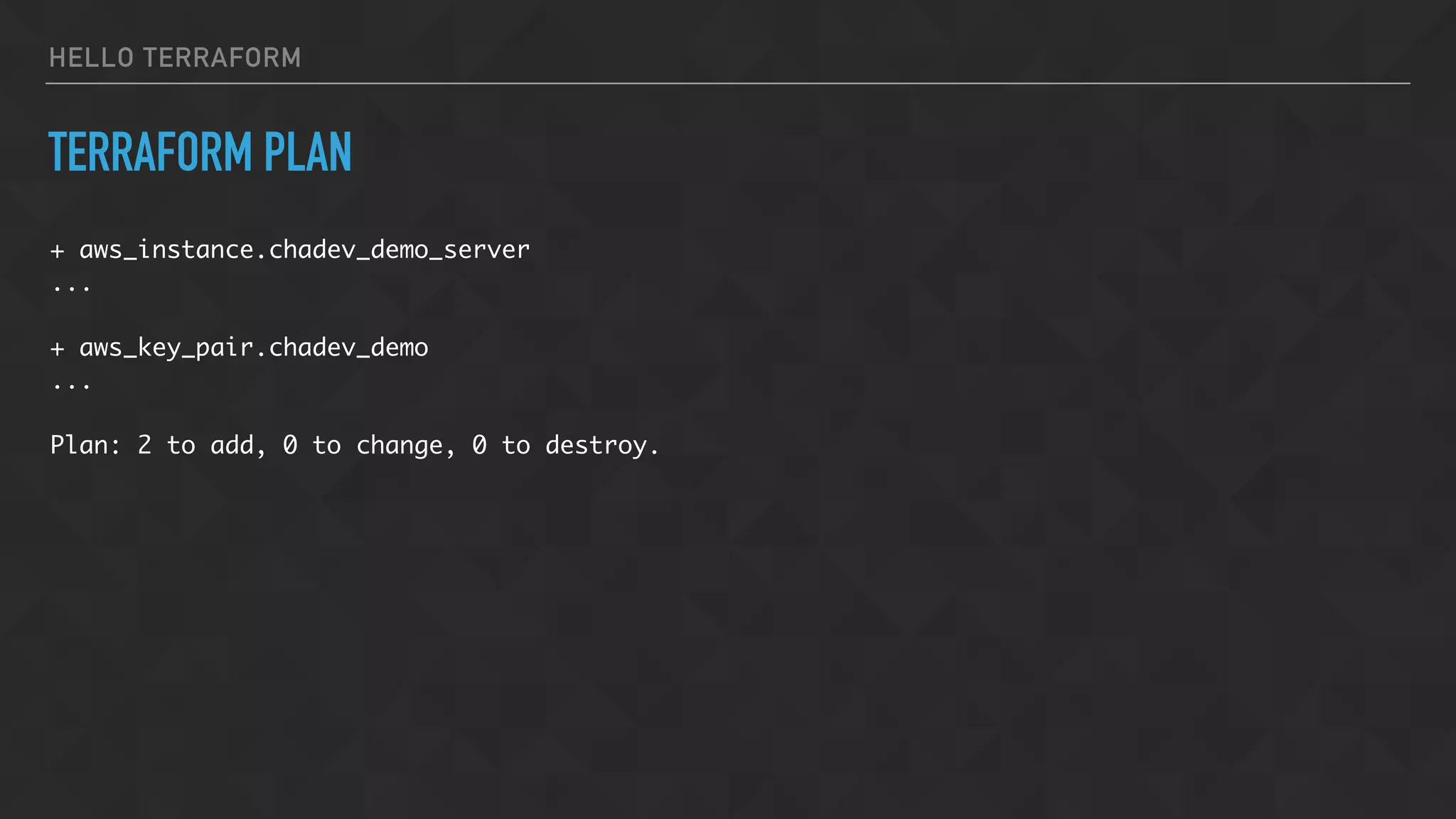
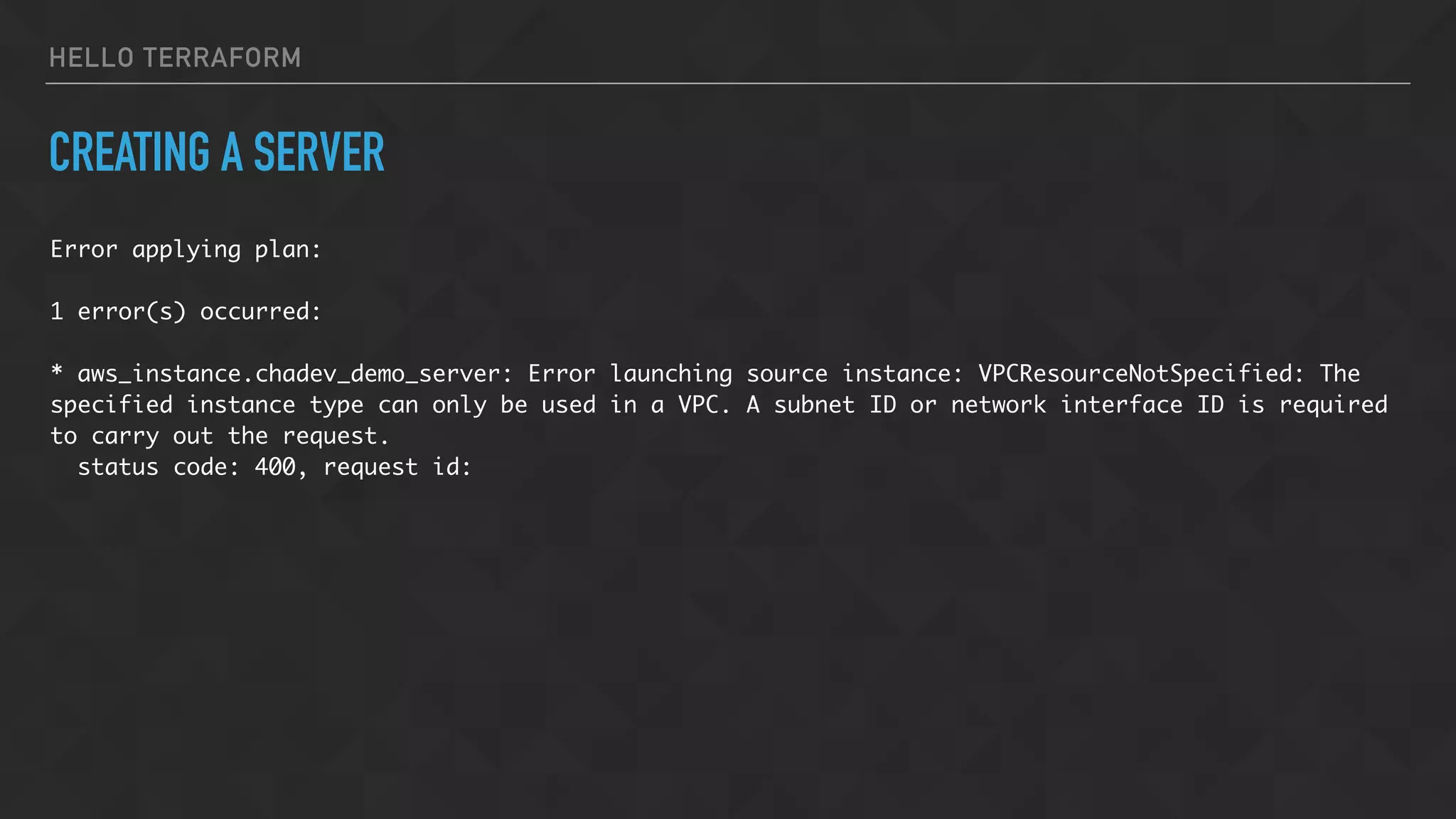

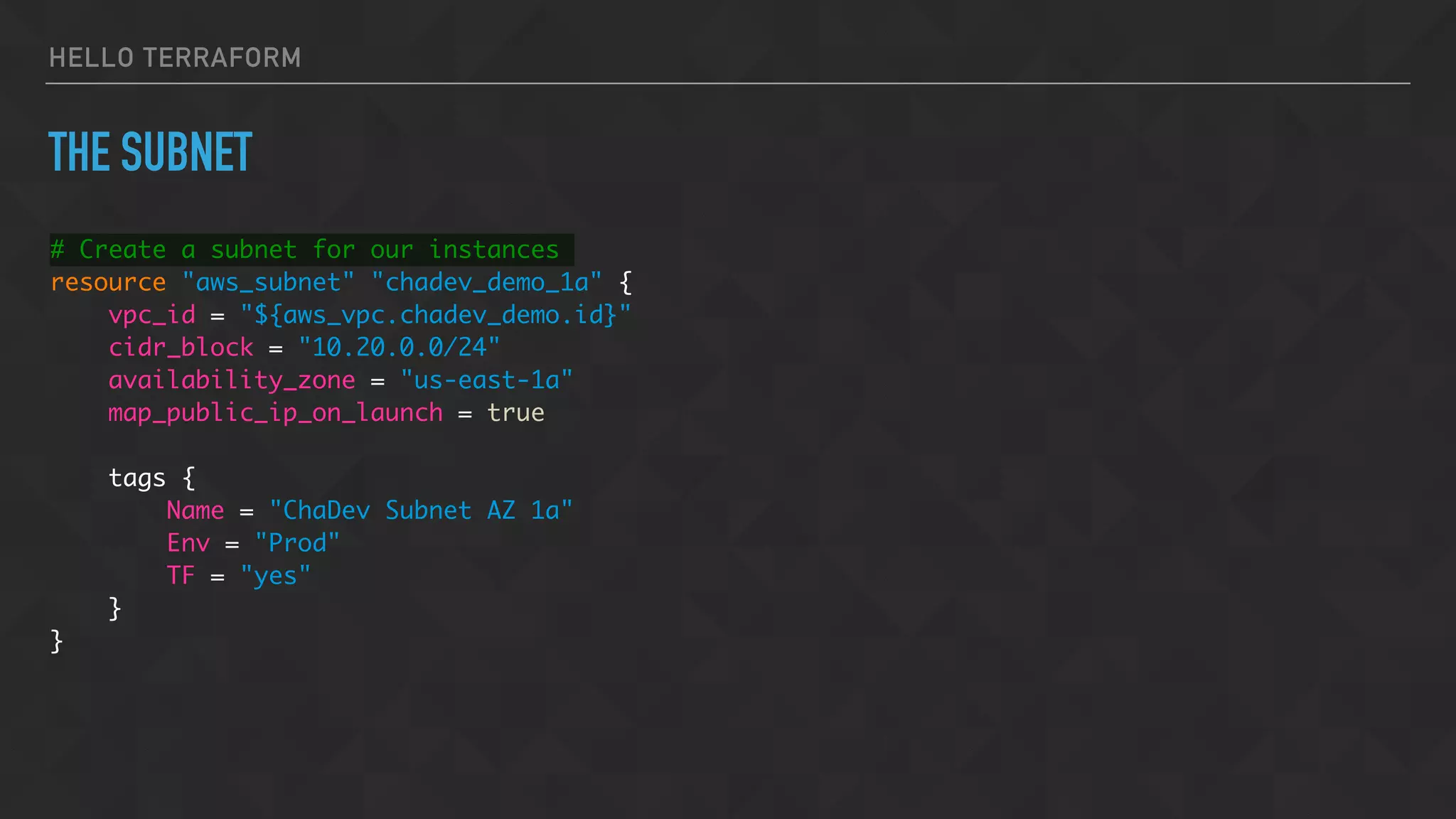
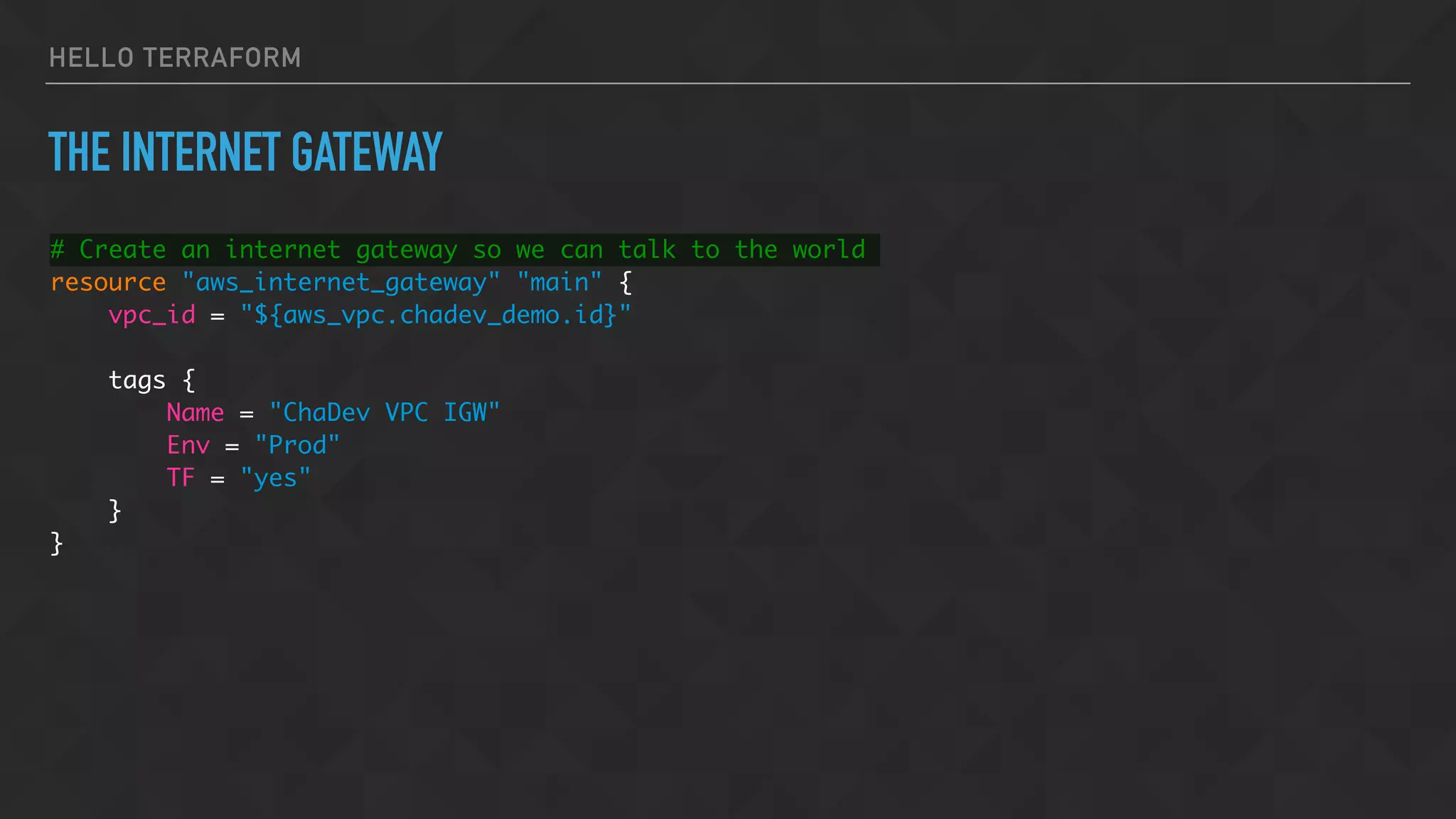
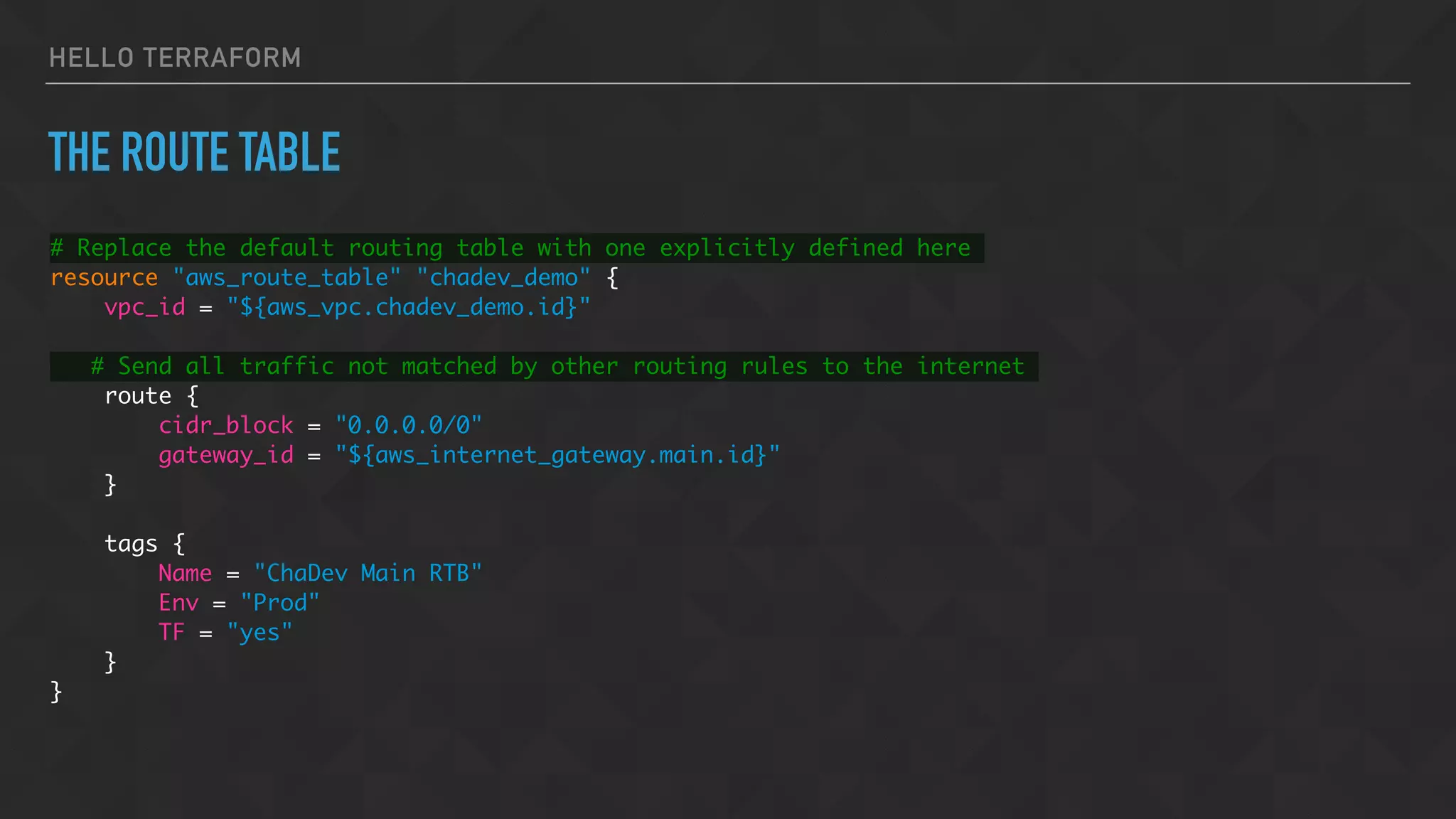
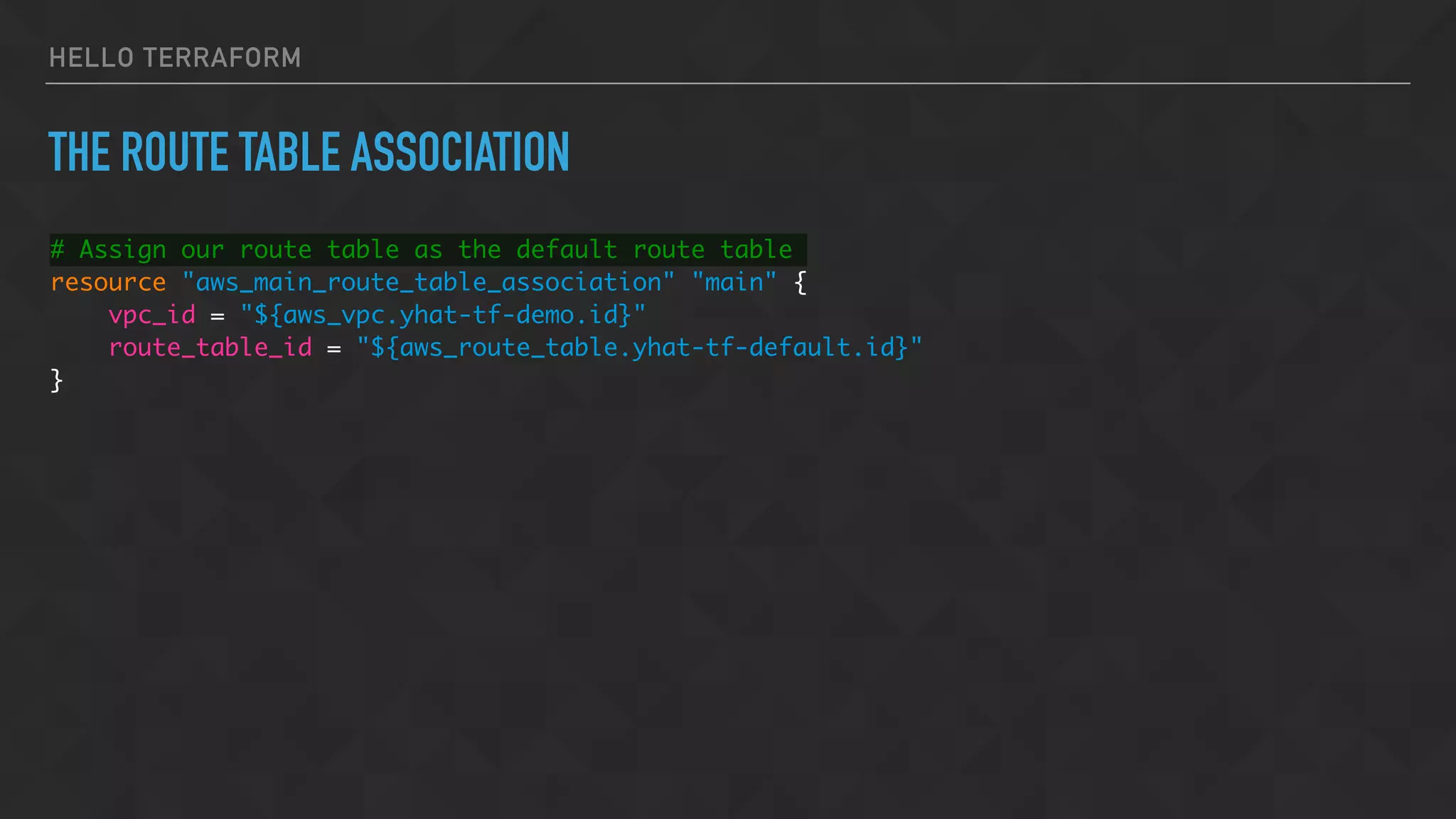


![HELLO TERRAFORM
SPECIFY SUBNET AND SECURITY GROUPS
vpc_security_group_ids = [
"${aws_security_group.chadev_demo.id}",
]
subnet_id = "${aws_subnet.chadev_demo_1a.id}"](https://image.slidesharecdn.com/chadevtf-160930001034/75/Terraform-An-Overview-Introduction-36-2048.jpg)




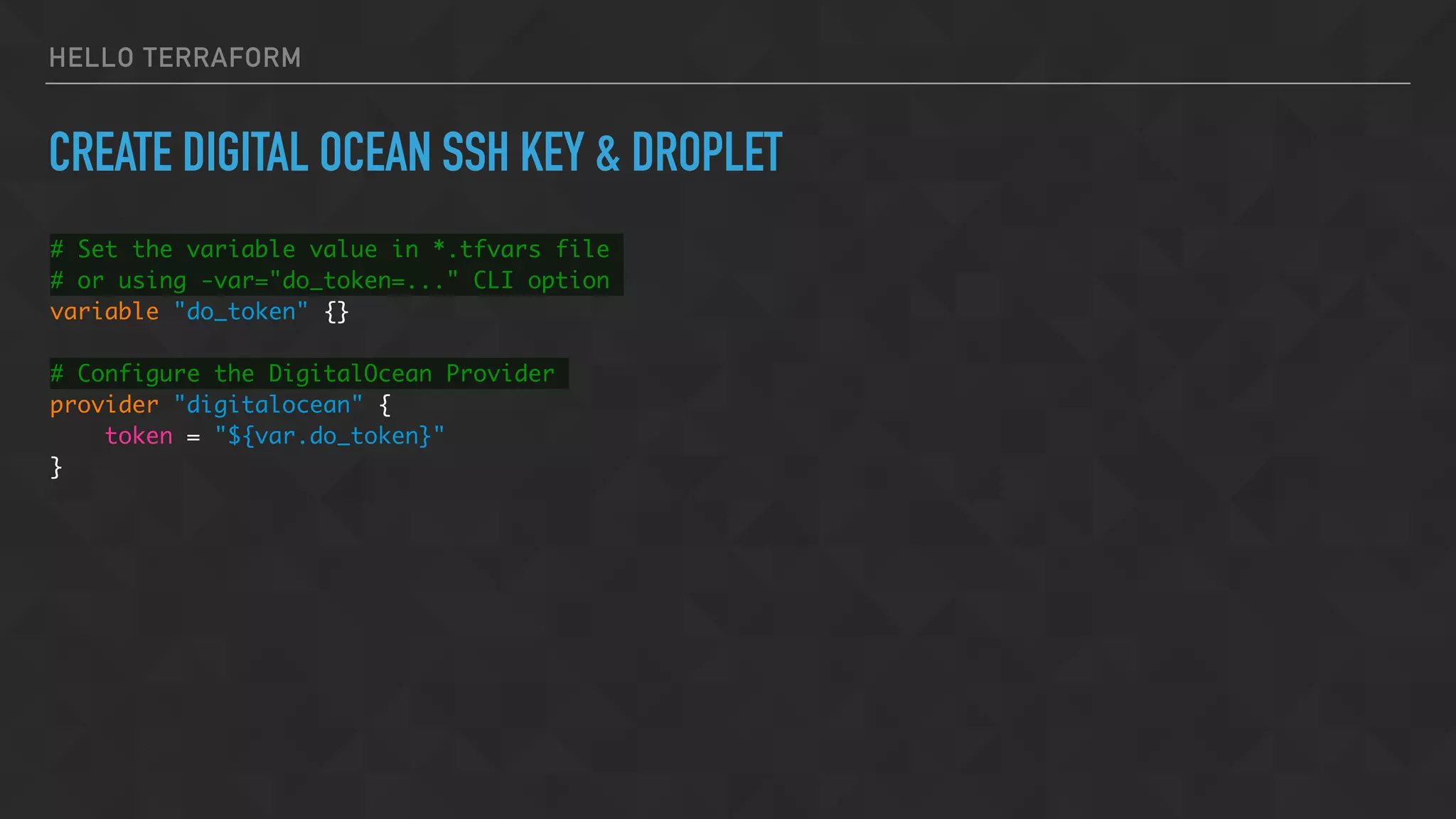
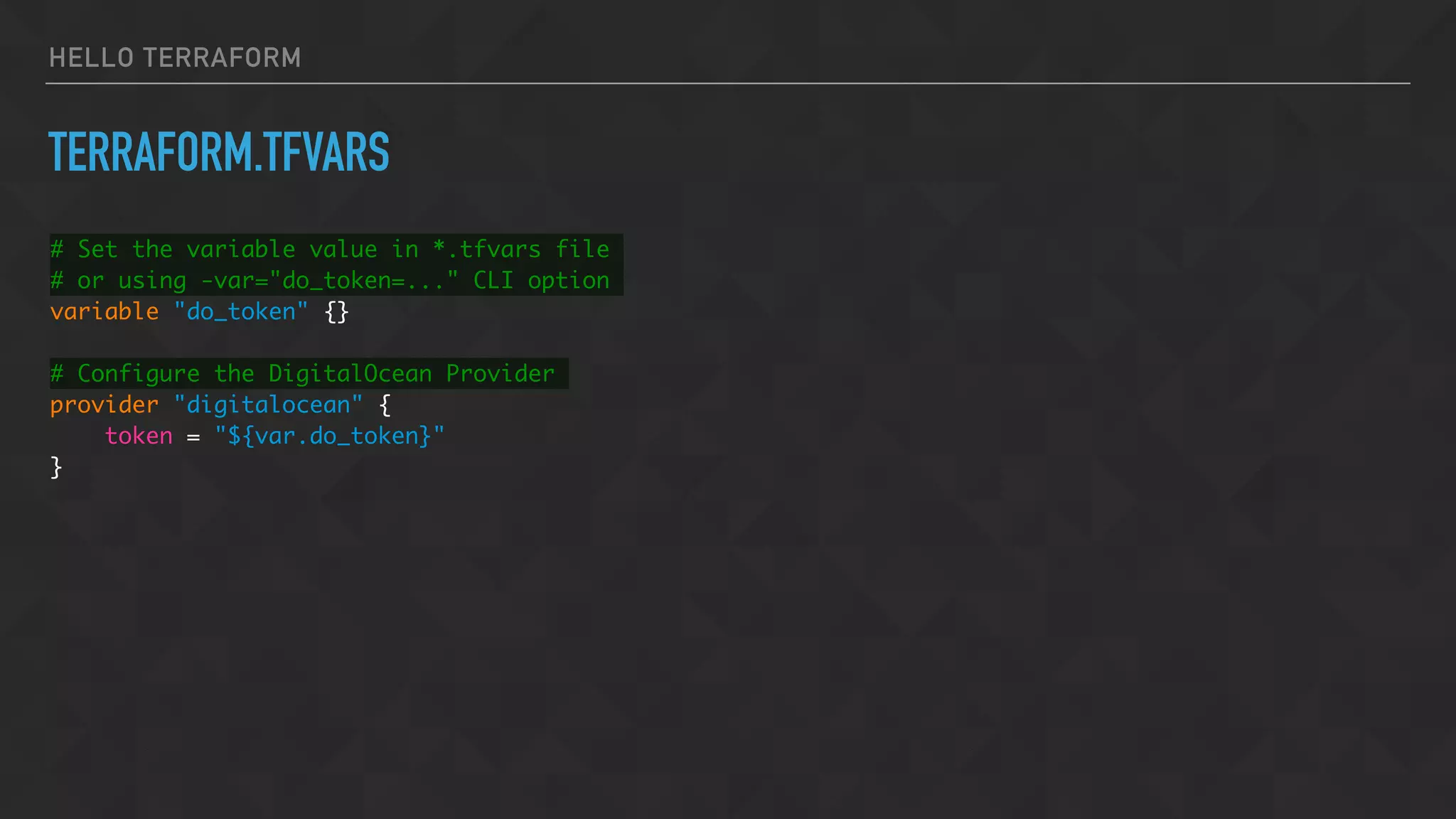
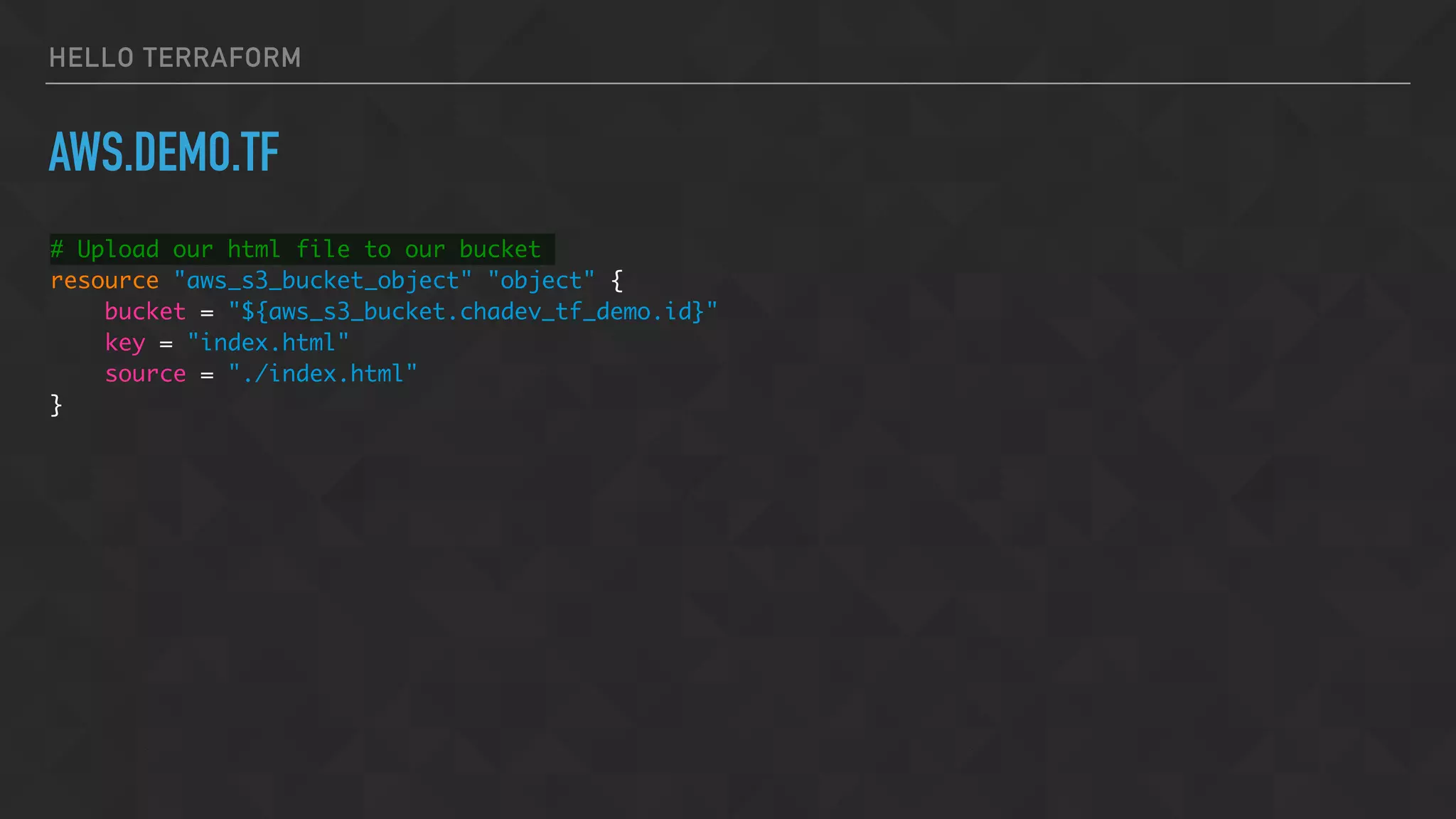
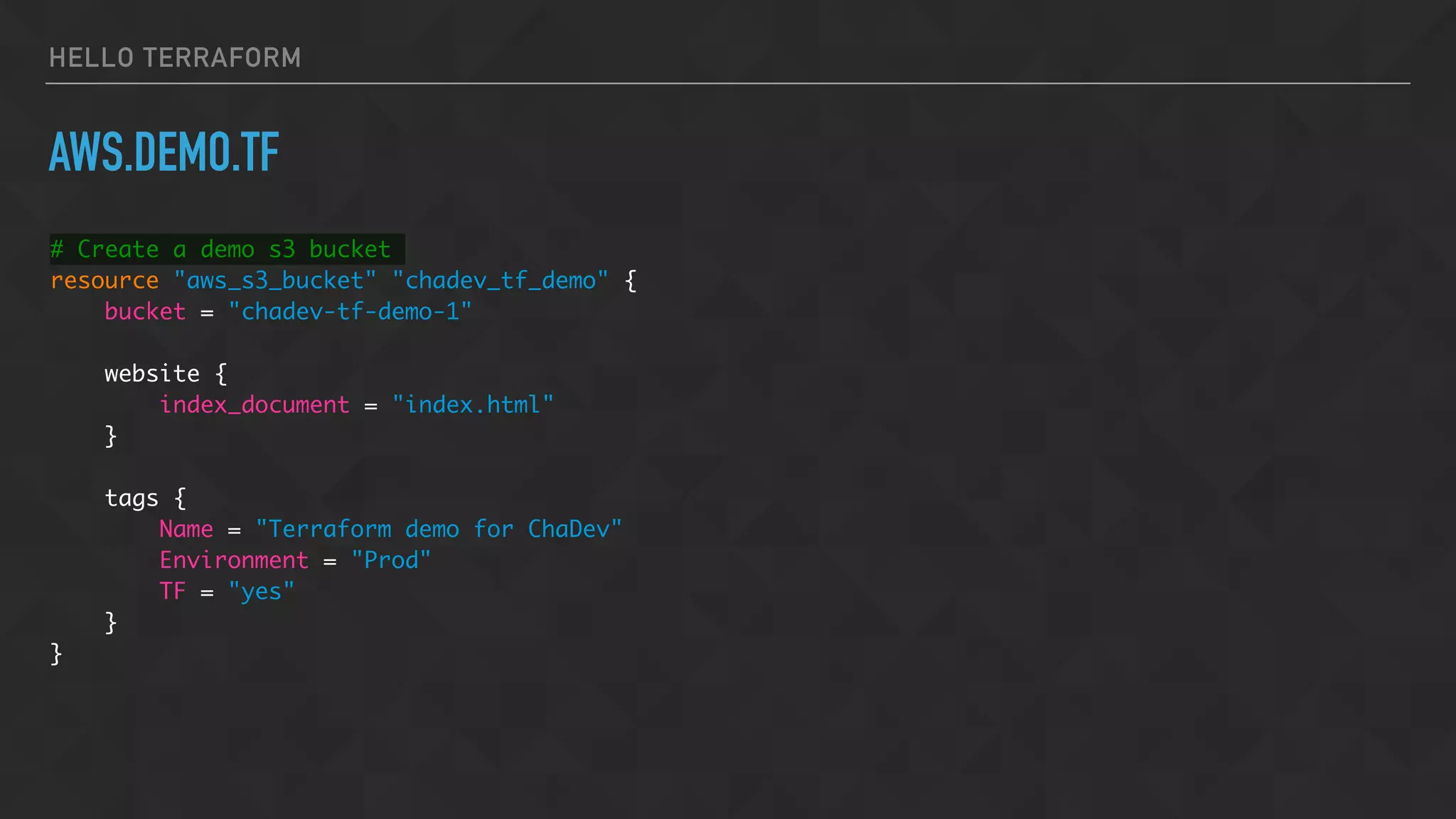
![HELLO TERRAFORM
ALLOW ACCESS FROM DIGITAL OCEAN
policy = <<EOF
{
"Version": "2008-10-17",
"Id": "S3PolicyId1",
"Statement": [
{
"Sid": "IPAllow",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::chadev-tf-demo-1/*",
"arn:aws:s3:::chadev-tf-demo-1"
],
"Condition": {
"IpAddress": {
"aws:SourceIp": "${digitalocean_droplet.chadev_demo.ipv4_address}/32"
}
}
}
]
}
EOF](https://image.slidesharecdn.com/chadevtf-160930001034/75/Terraform-An-Overview-Introduction-49-2048.jpg)