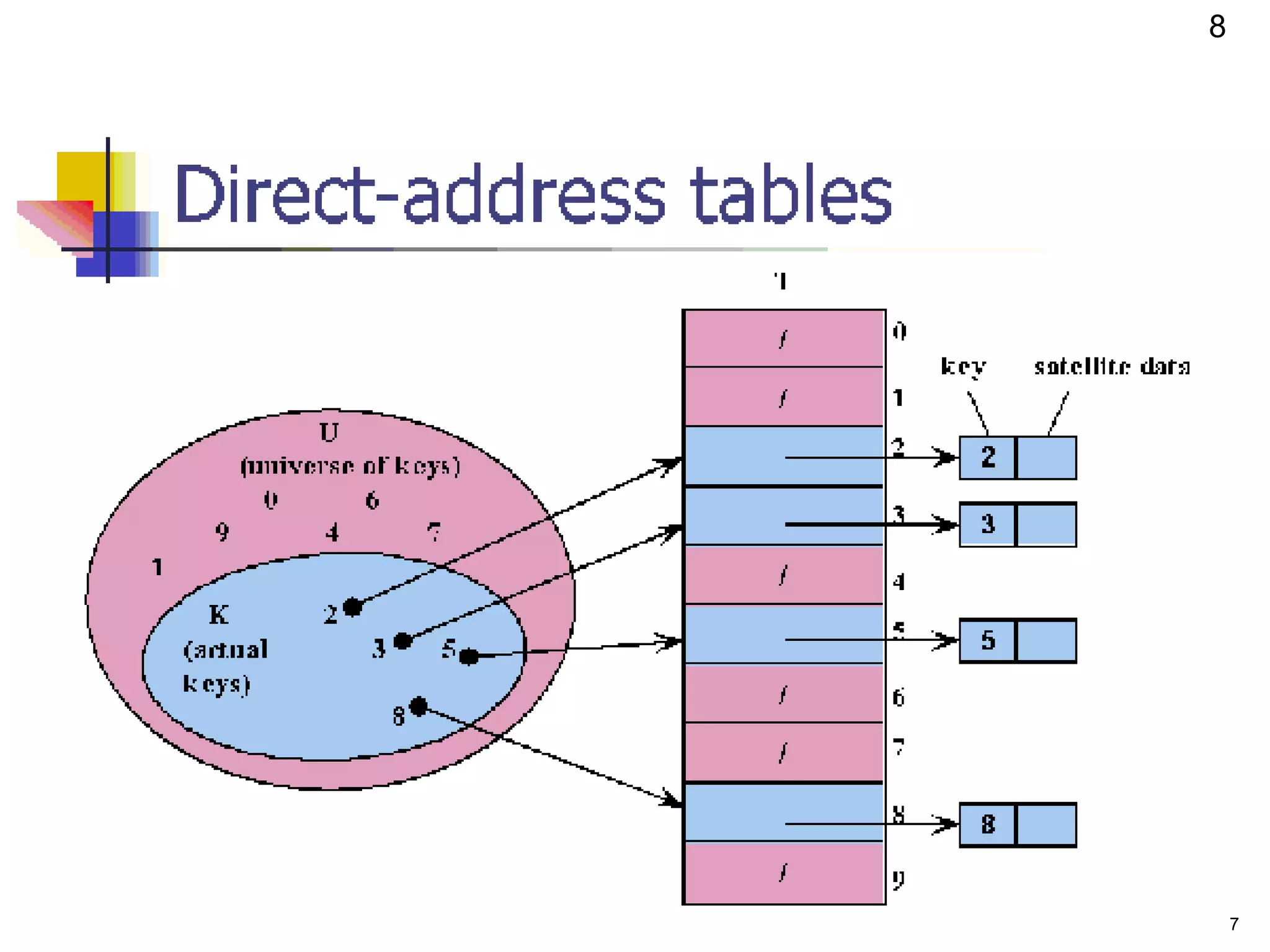
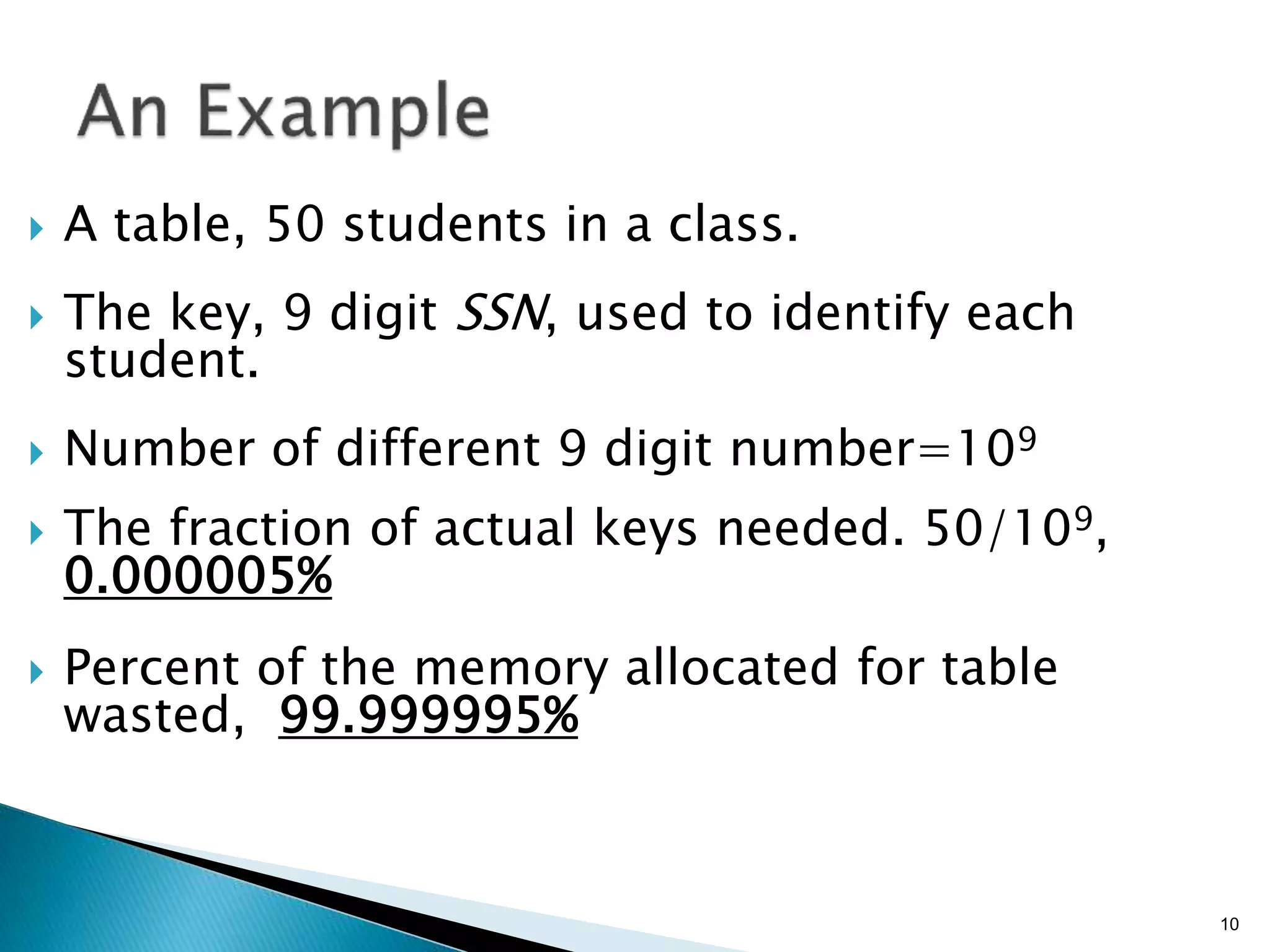
The document discusses hash tables as an efficient data structure for implementing dictionary operations. It describes how hash tables work by using a hash function to map keys to array indices, allowing for fast lookup times of O(1) on average. When collisions occur where two keys map to the same index, techniques like chaining can be used to resolve them. Hash tables are preferable to direct address tables when the key universe is very large relative to the actual number of keys, as they avoid wasting large amounts of memory when most array slots would be empty.



![ Suppose:
◦ The range of keys is 0..m-1
◦ Keys are distinct
The idea:
◦ Set up an array T[0..m-1] in which
T[i] = x if x T and key[x] = i
T[i] = NULL otherwise
◦ This is called a direct-address table
Operations take O(1) time!
6](https://image.slidesharecdn.com/lec-05hashing-140504015411-phpapp01/75/Advance-algorithm-hashing-lec-I-6-2048.jpg)