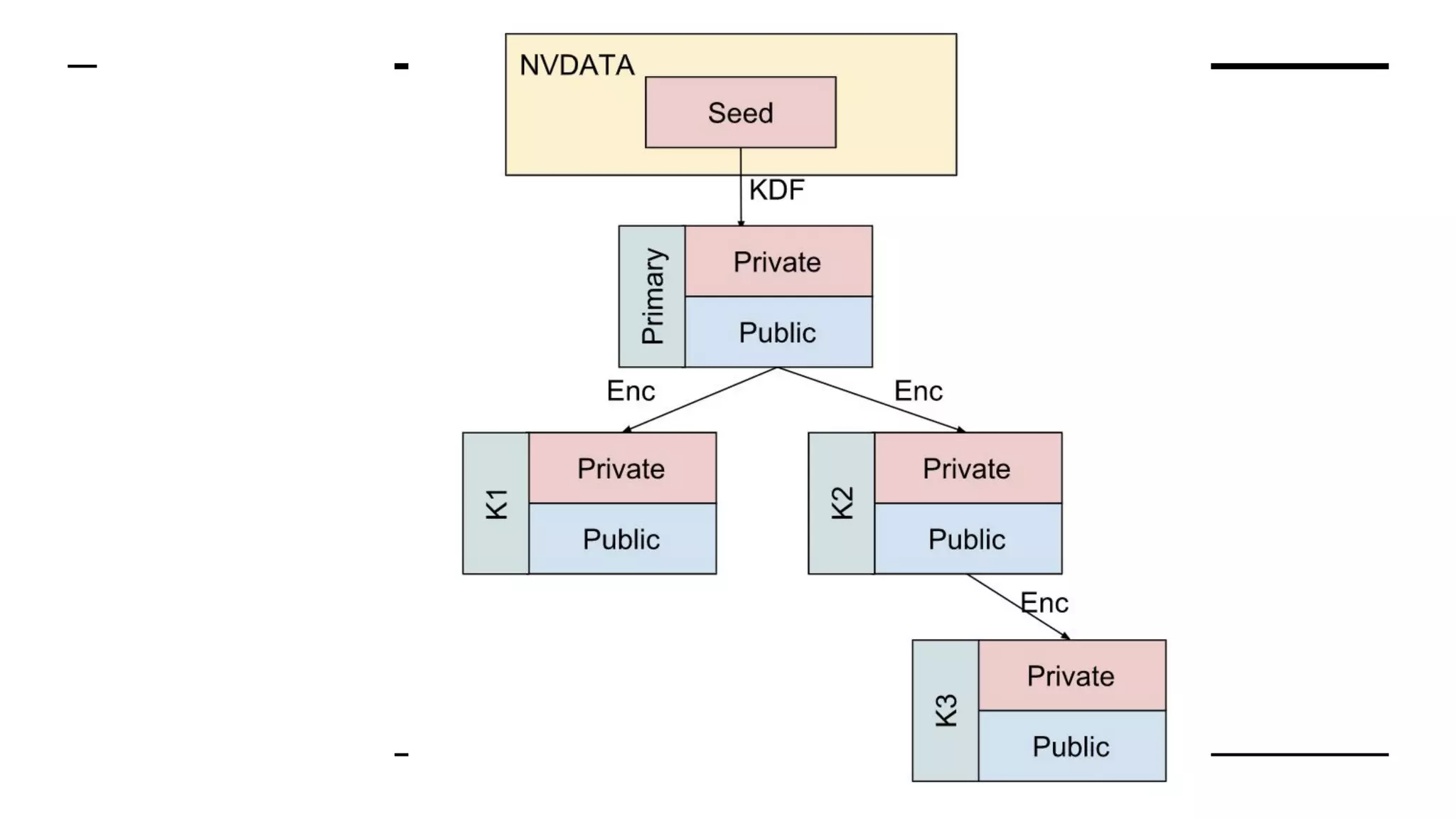
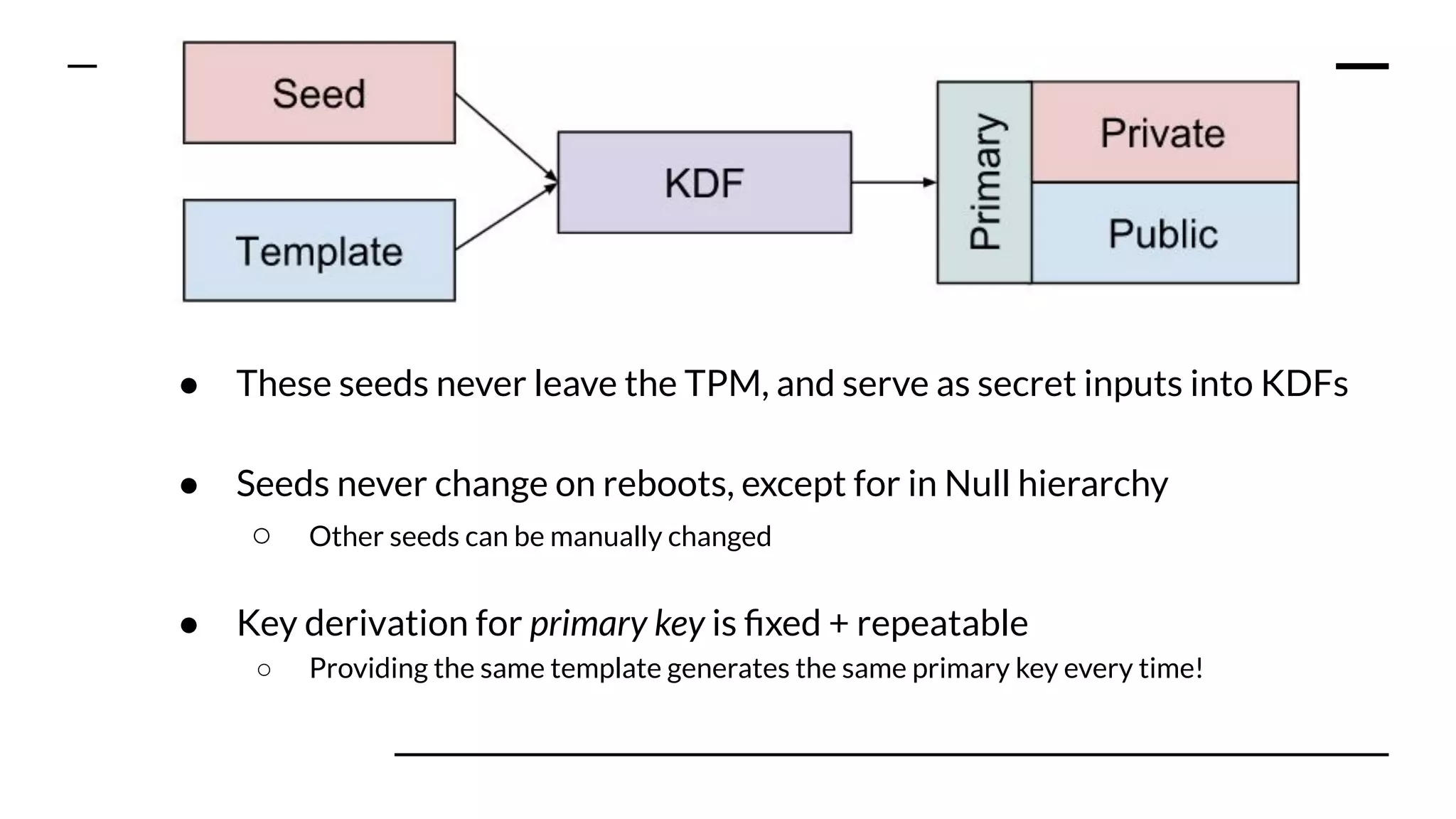
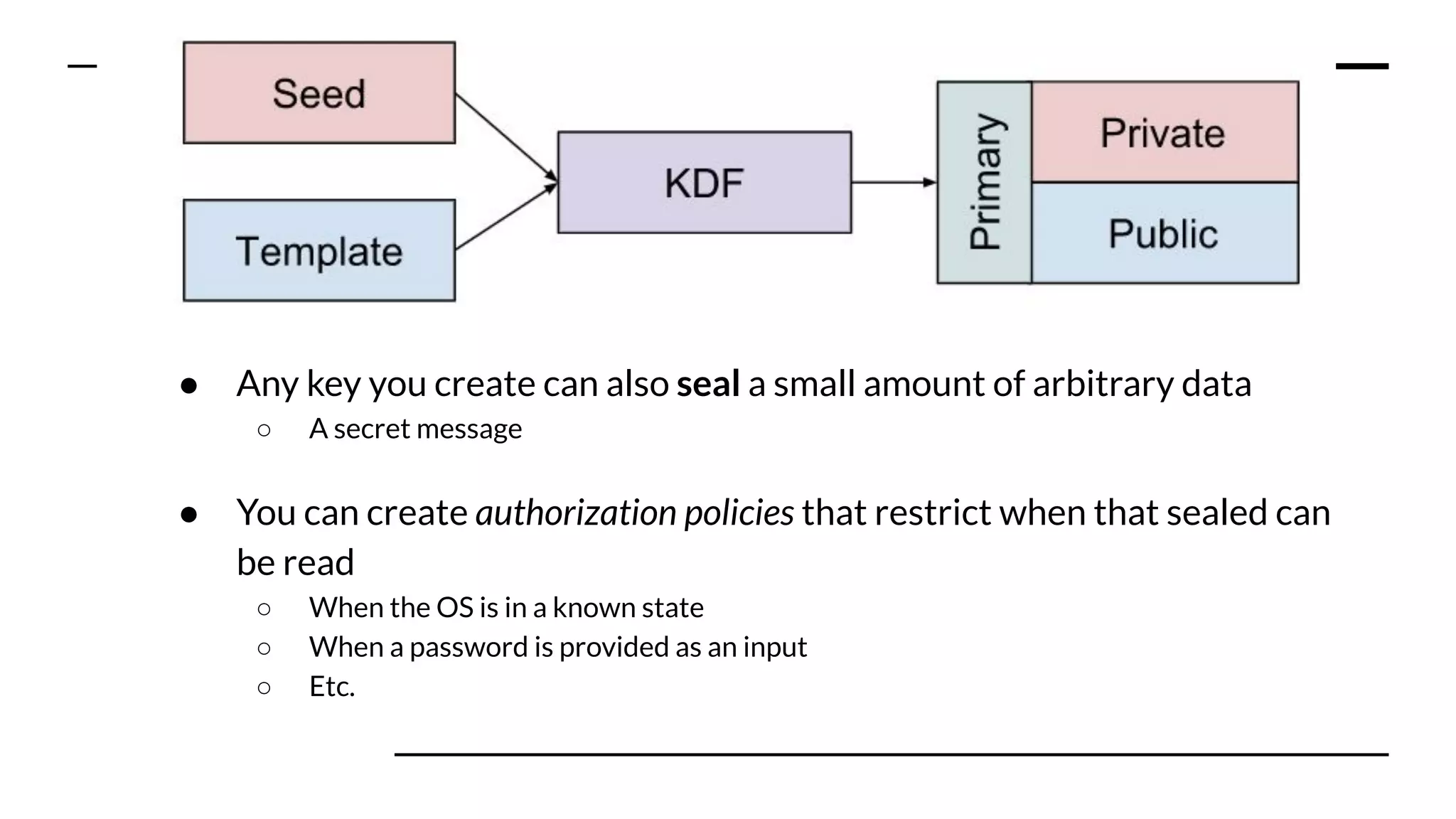
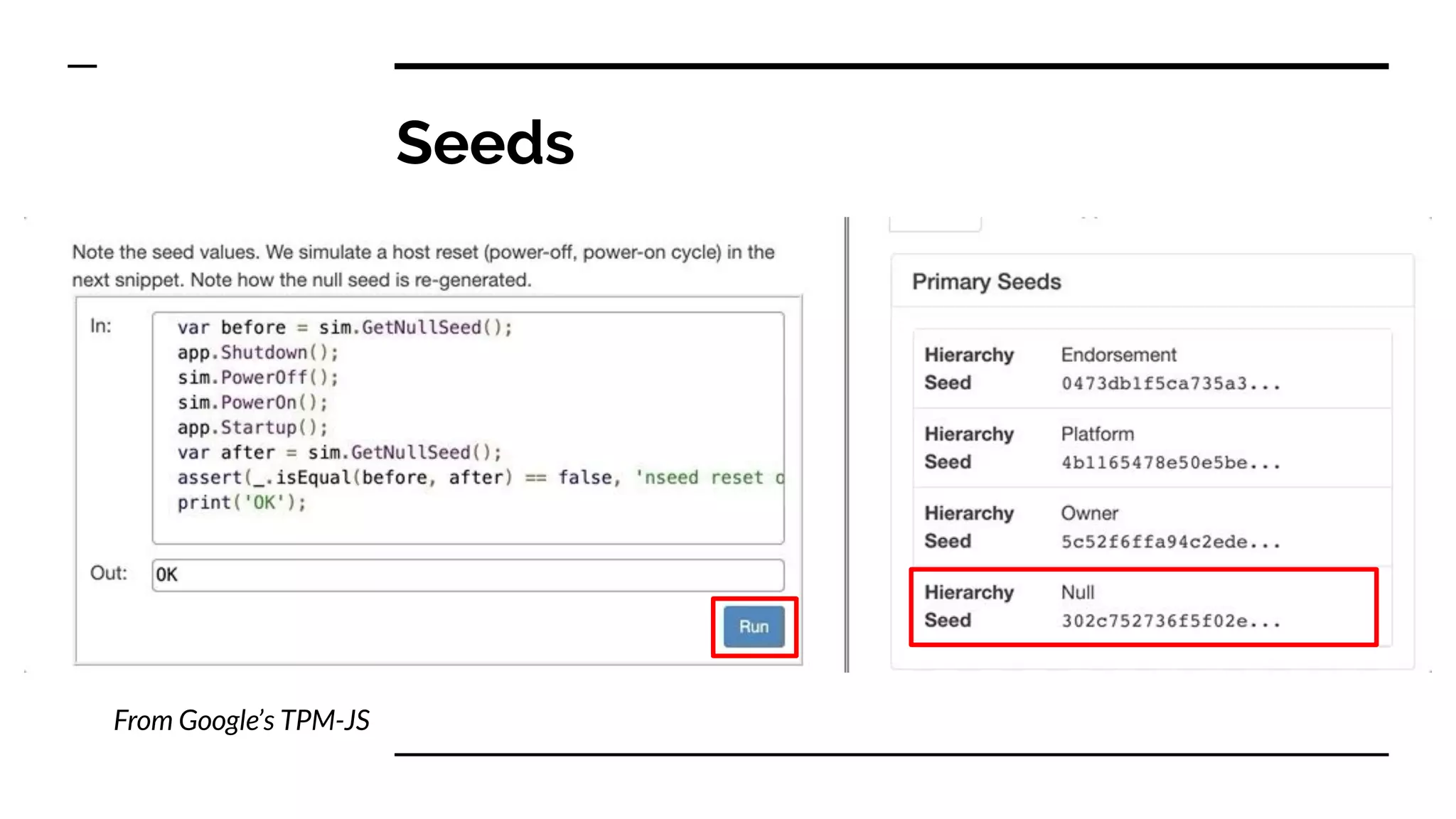
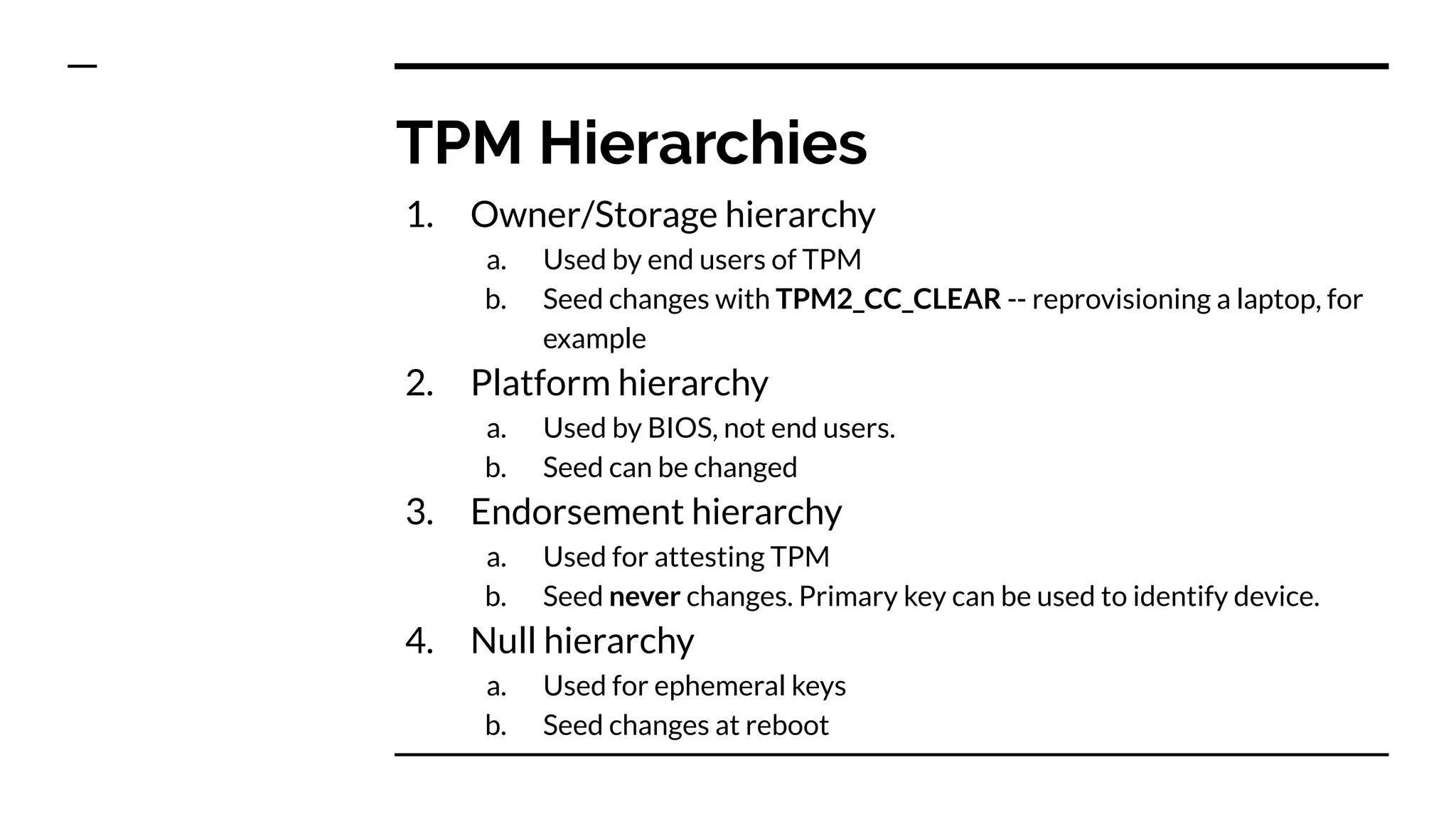
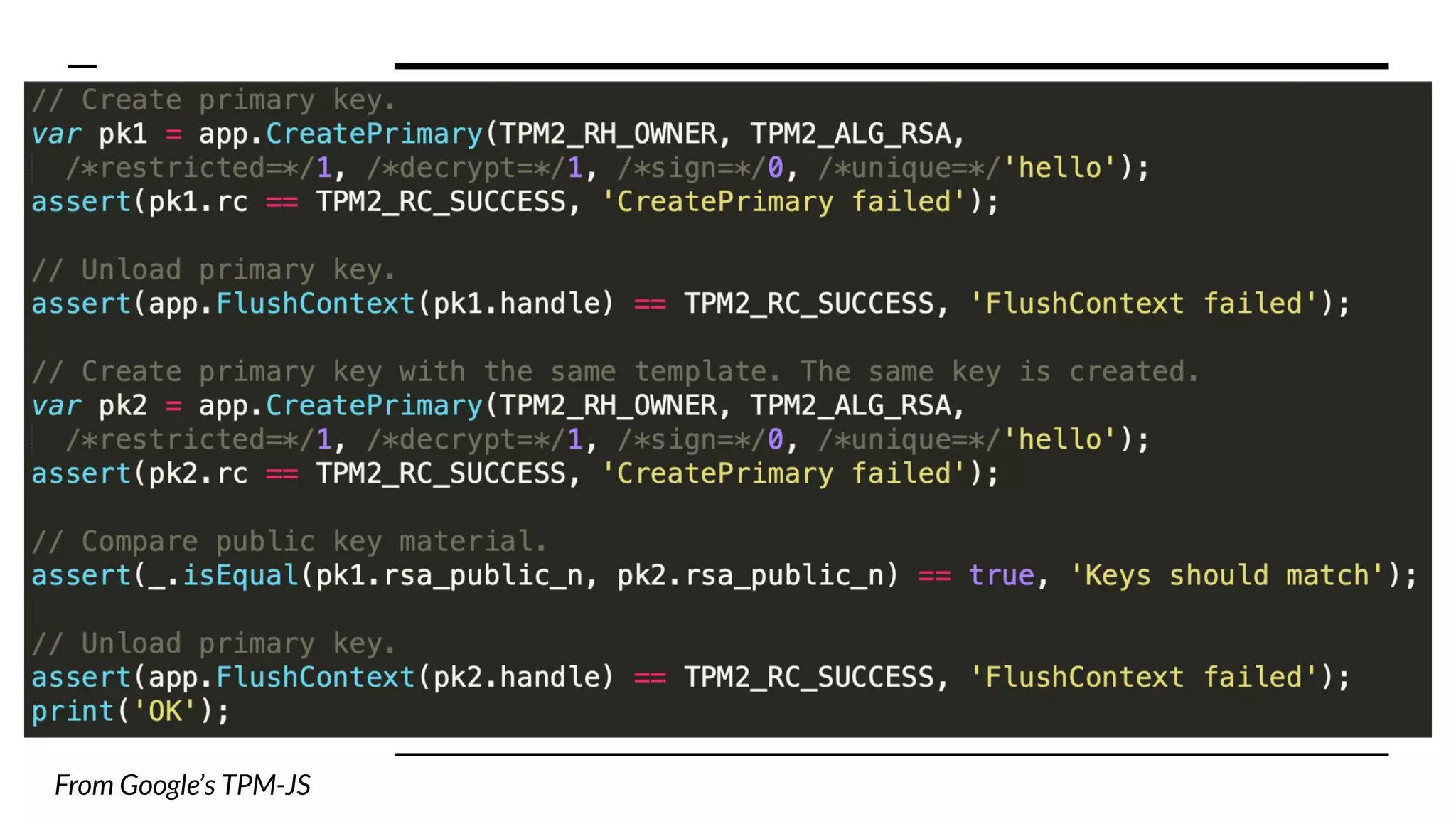
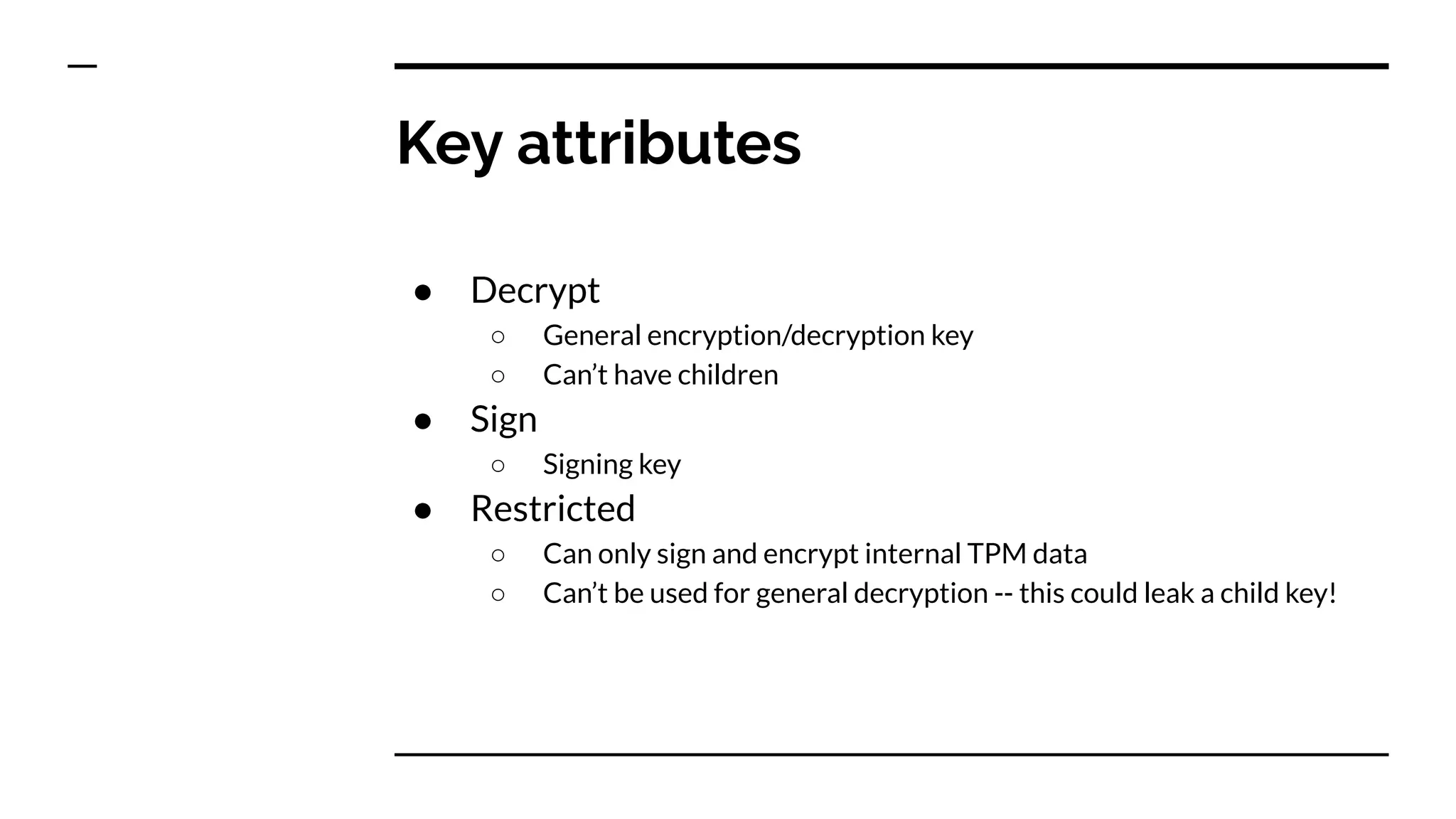
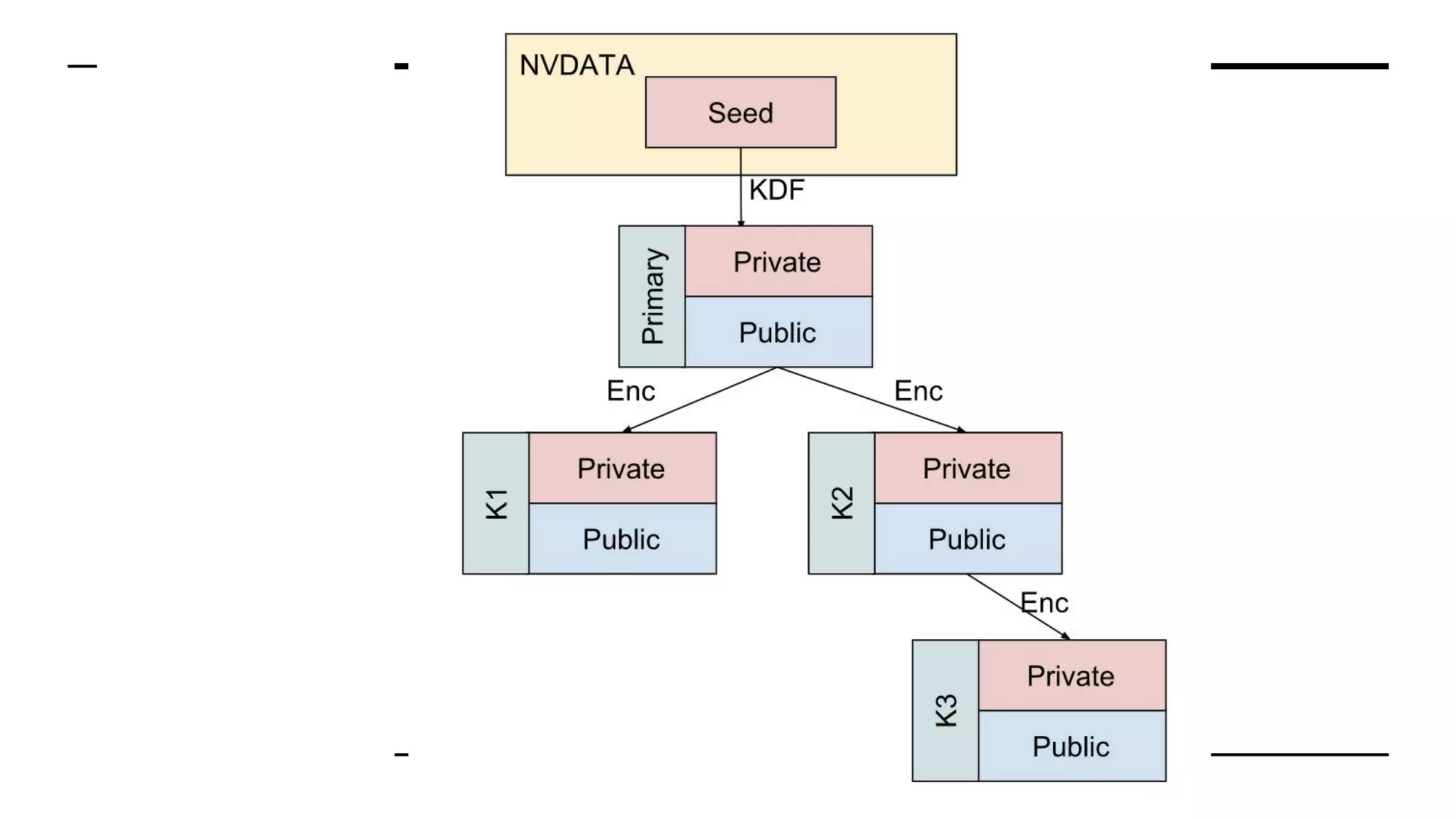
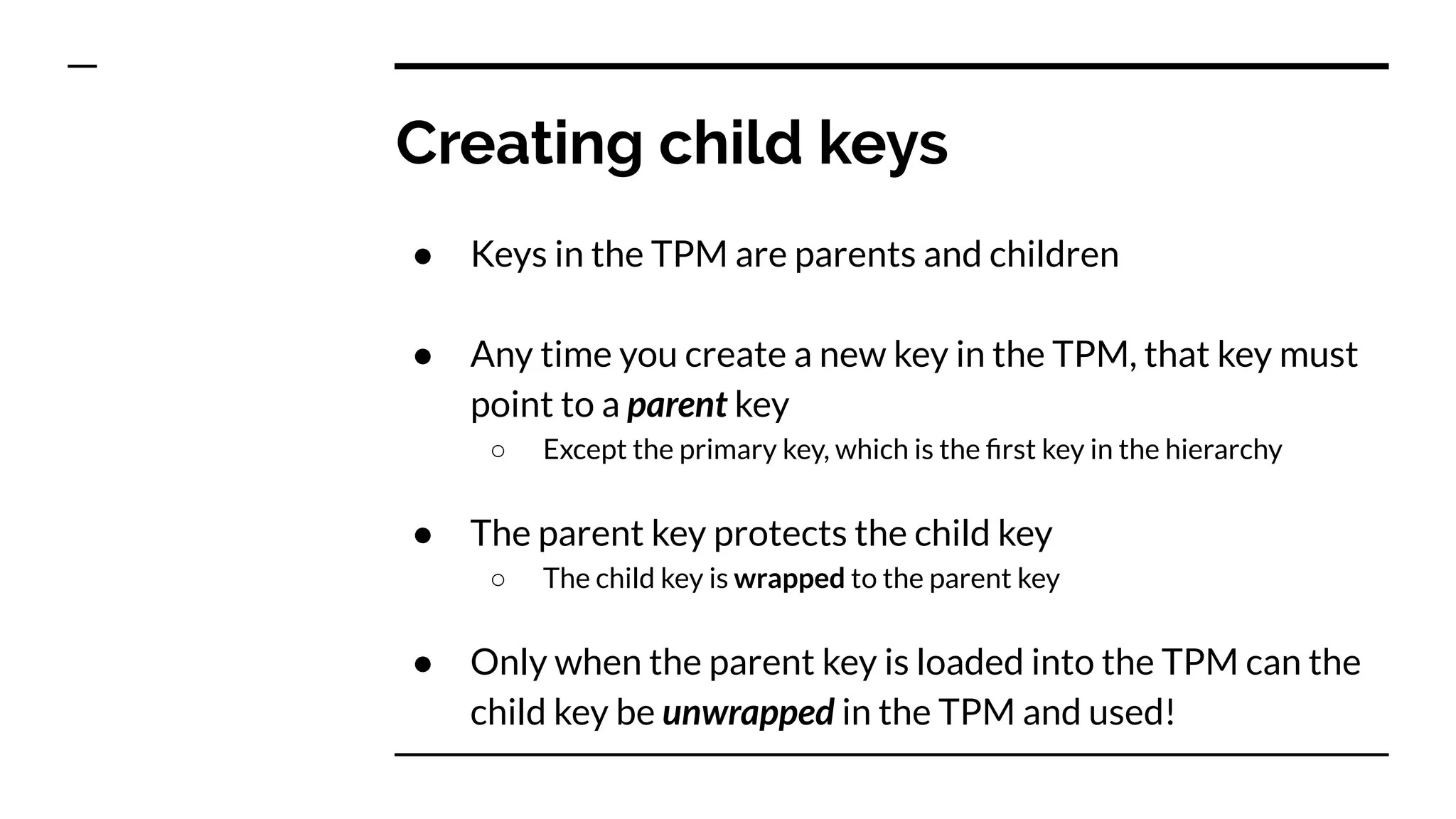
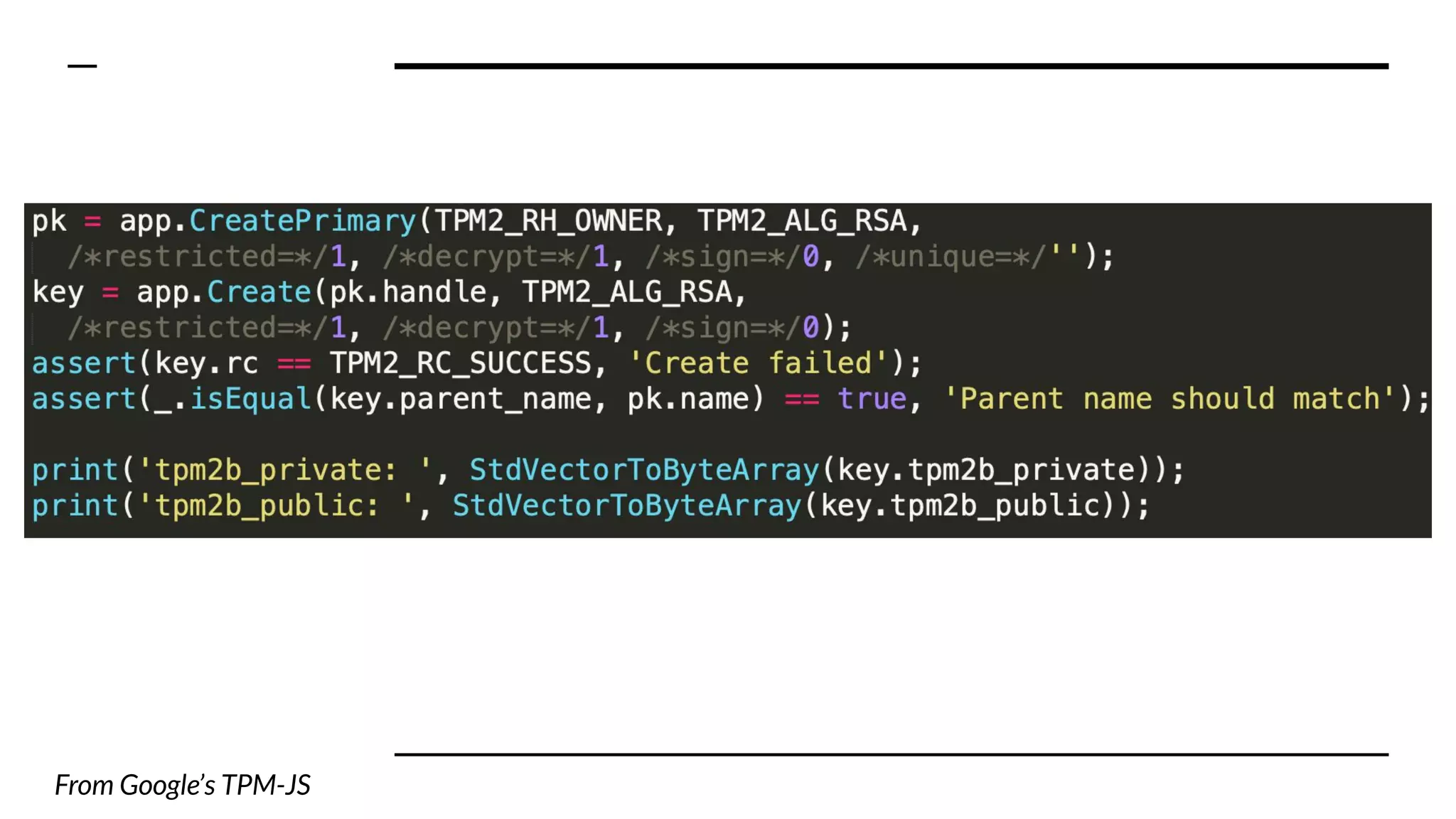
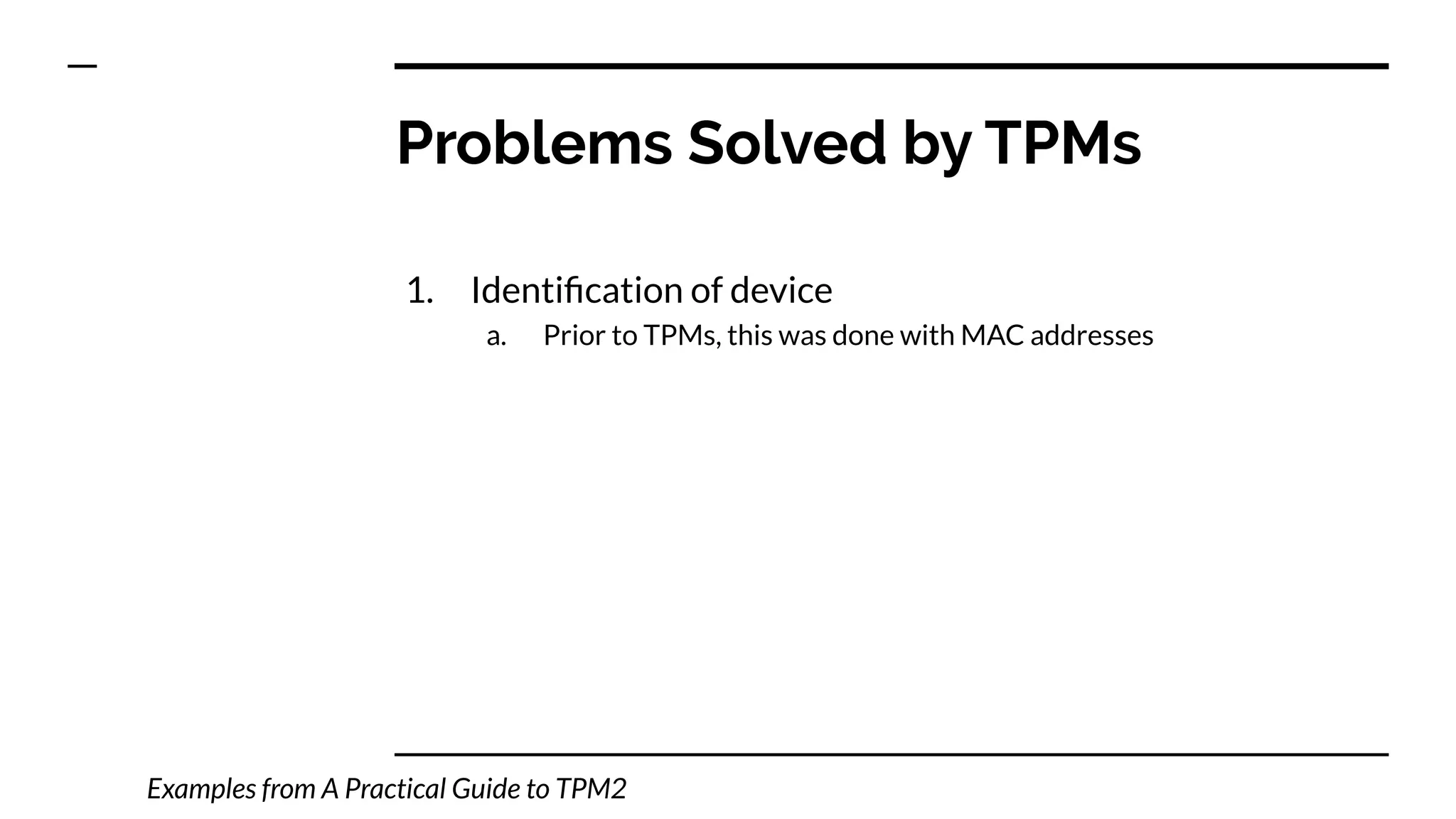
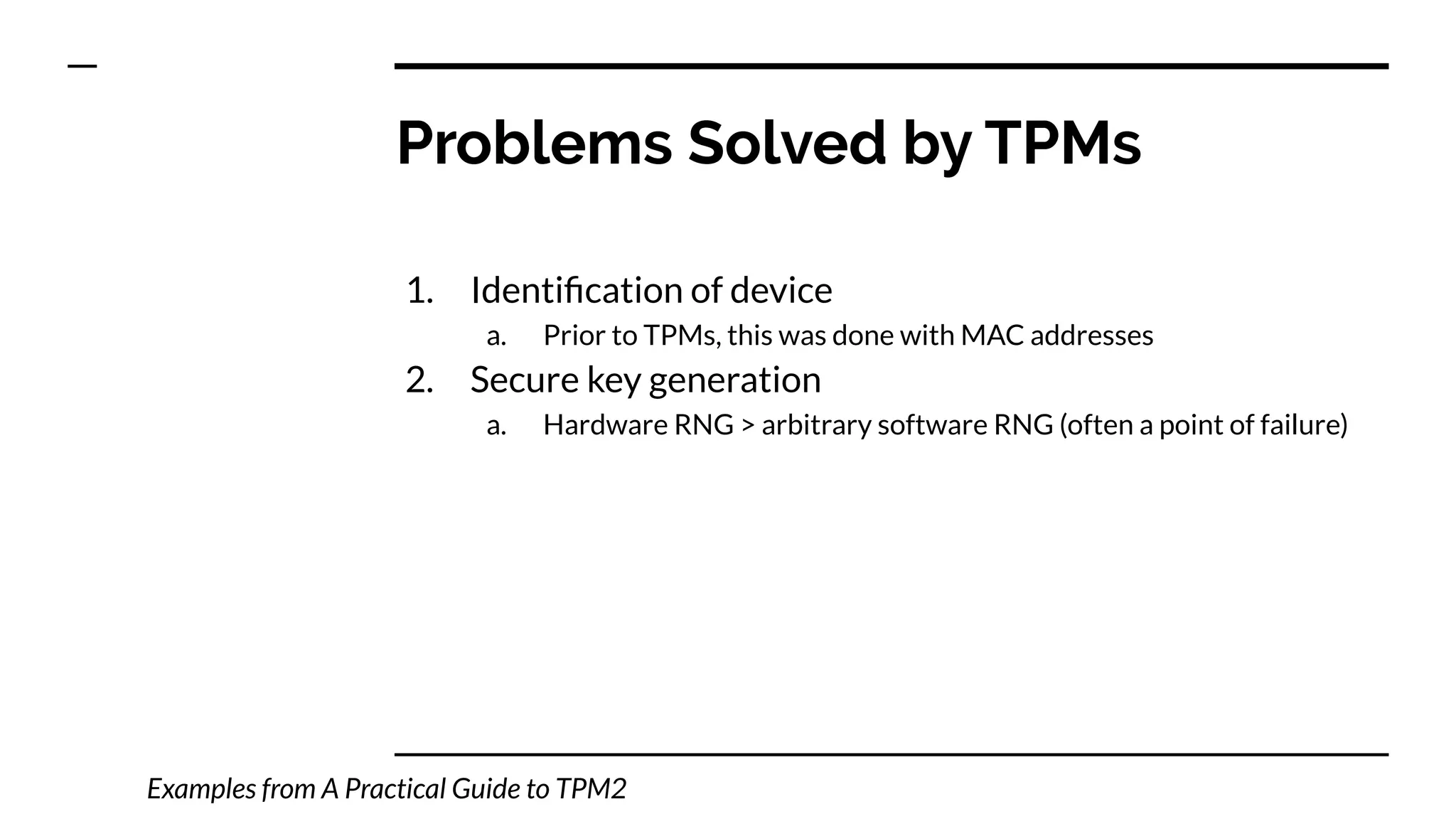
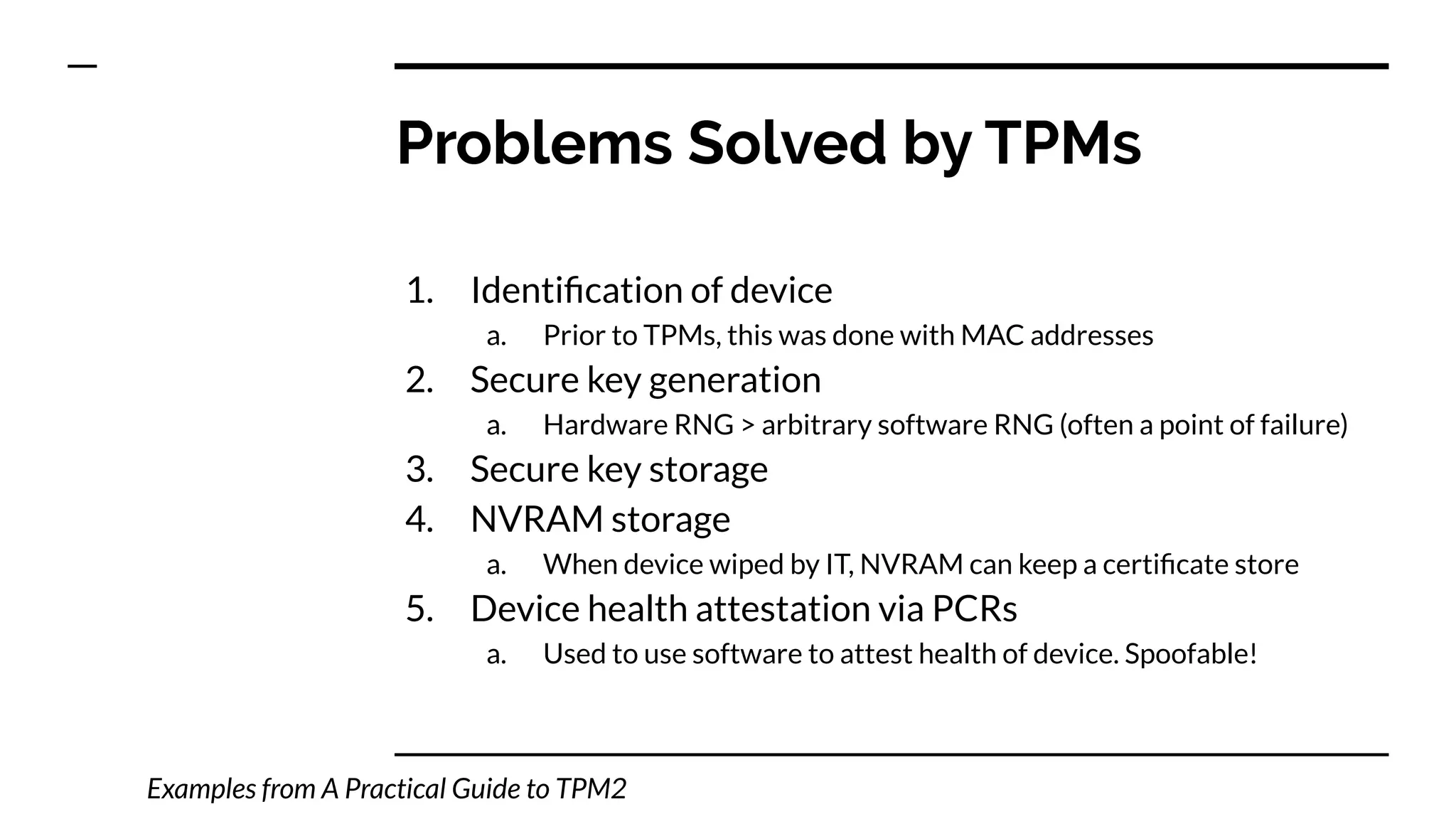
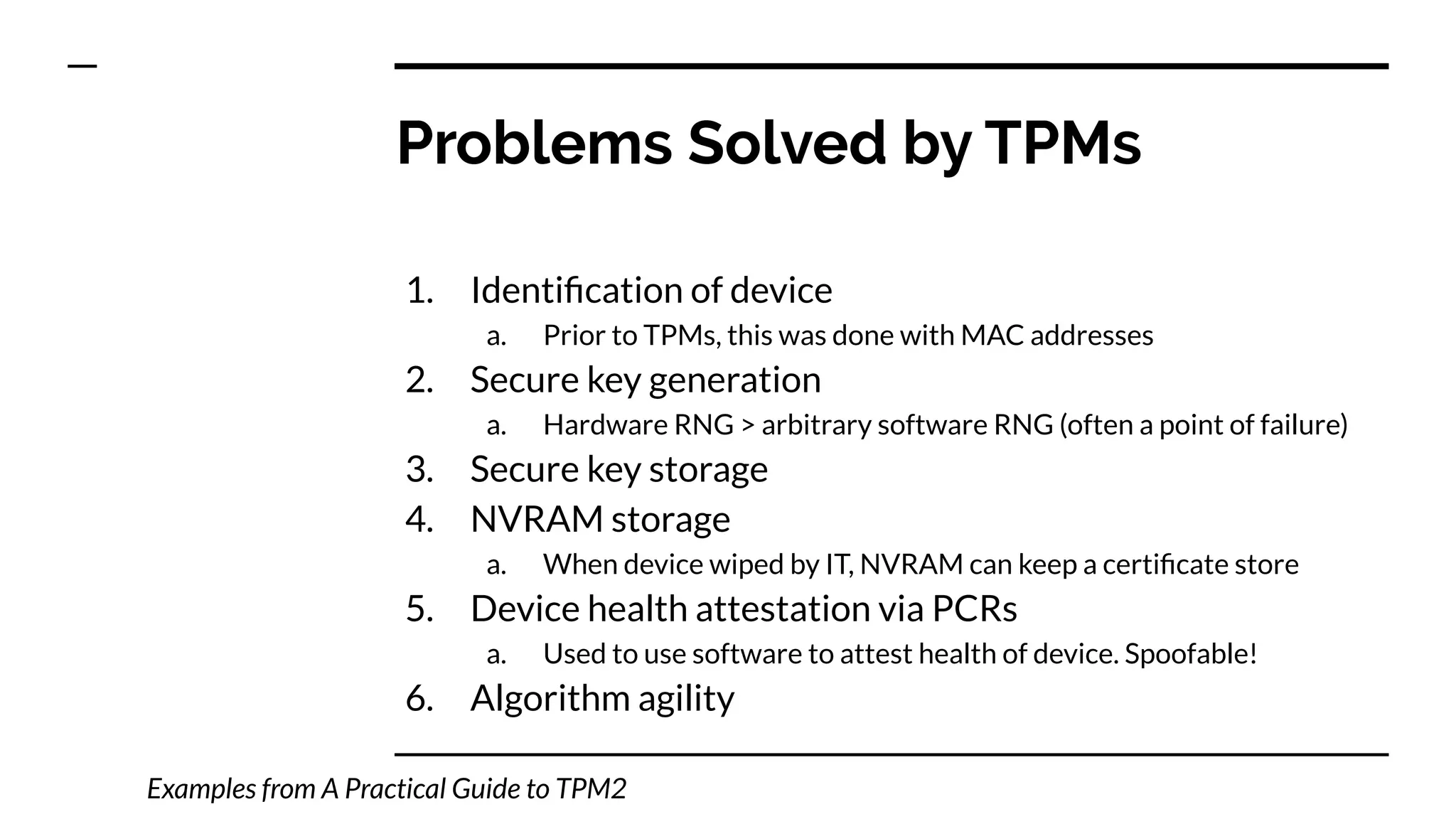
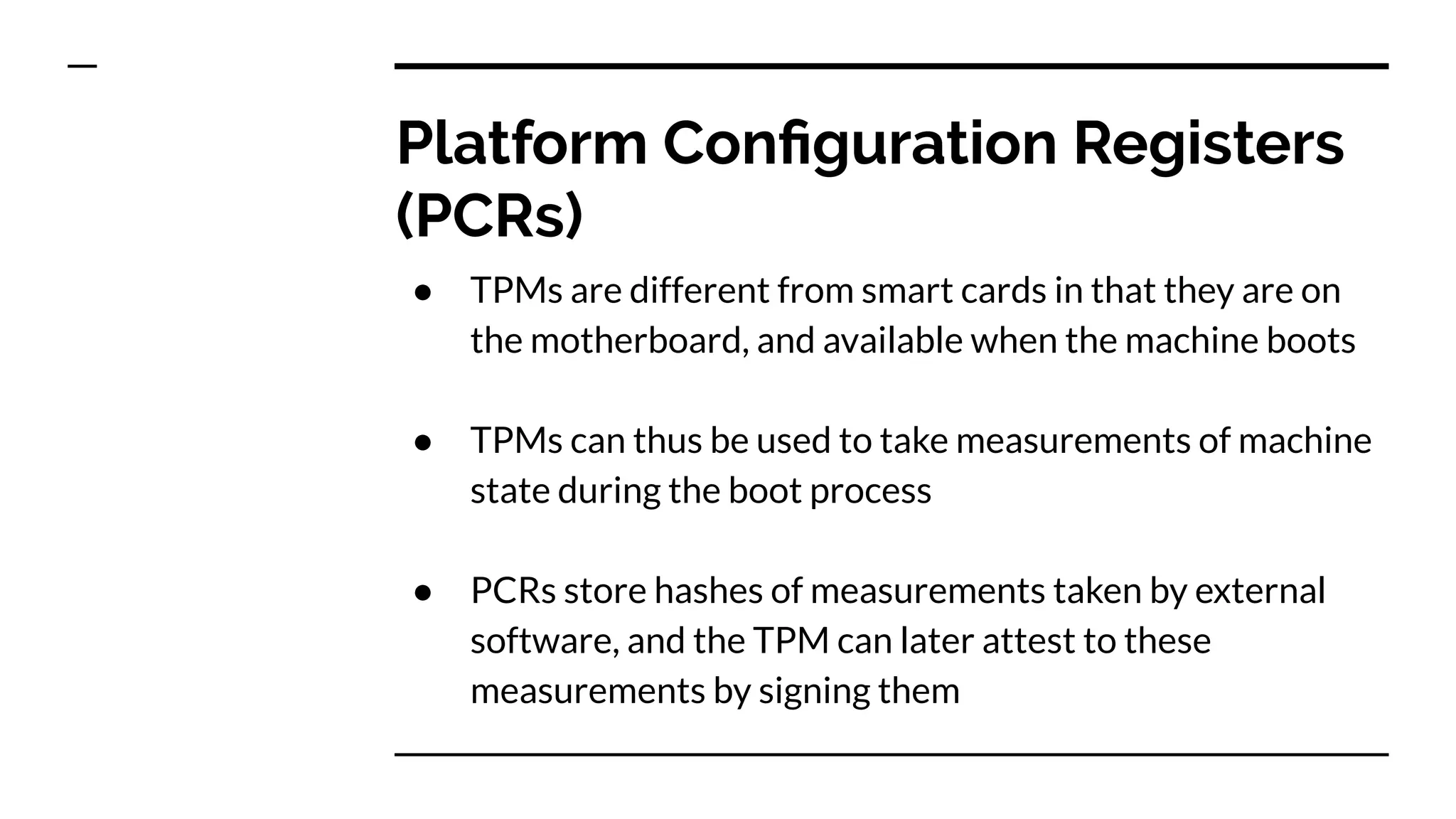
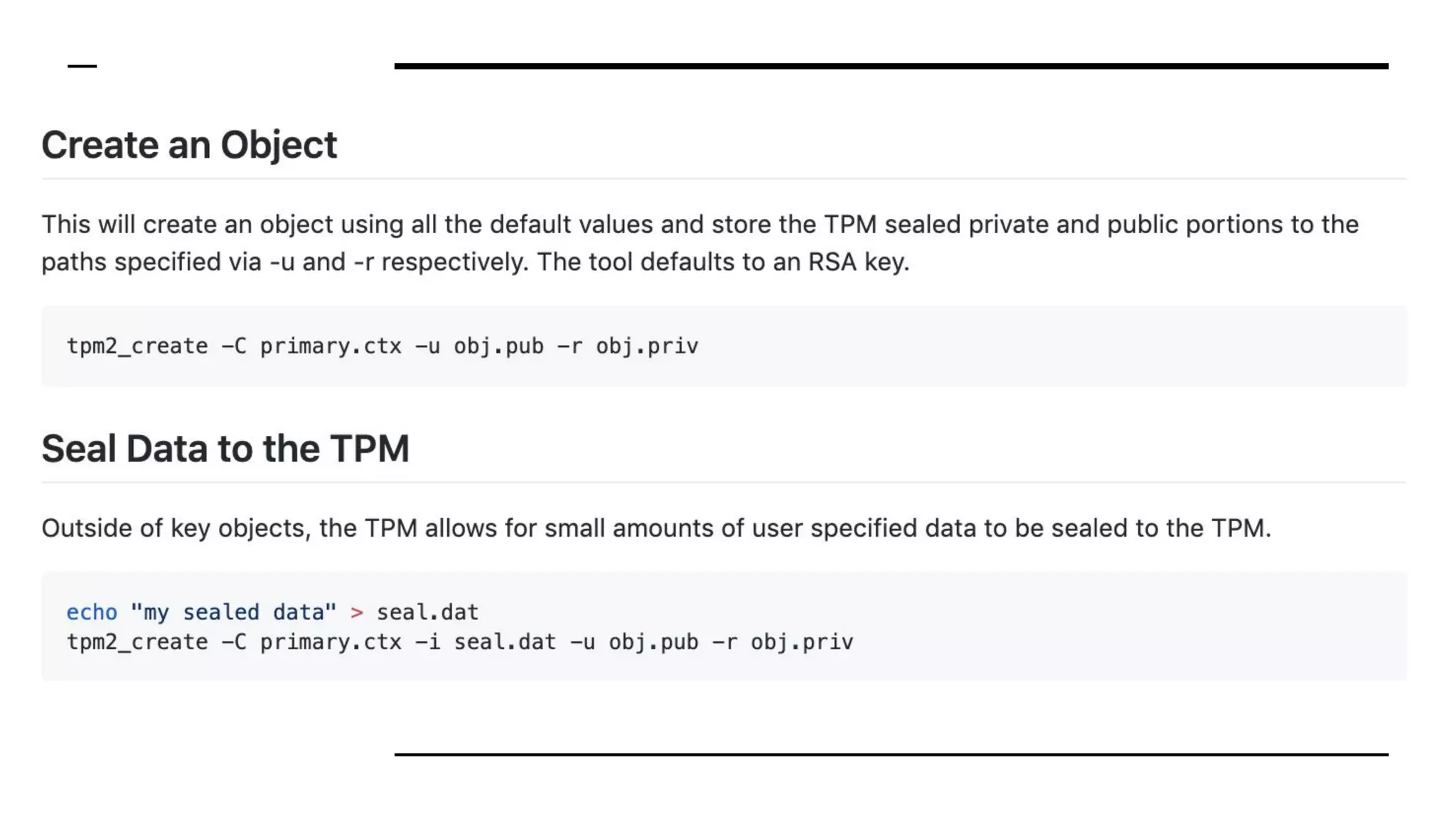
This document summarizes information from a presentation on practical Trusted Platform Module (TPM) programming. It discusses TPM hierarchies, keys, and the problems TPMs help solve such as secure device identification, key generation and storage, device health attestation, and algorithm agility. It provides examples from the resource "A Practical Guide to TPM 2.0" and the TPM simulator tool "tpm2_tools".