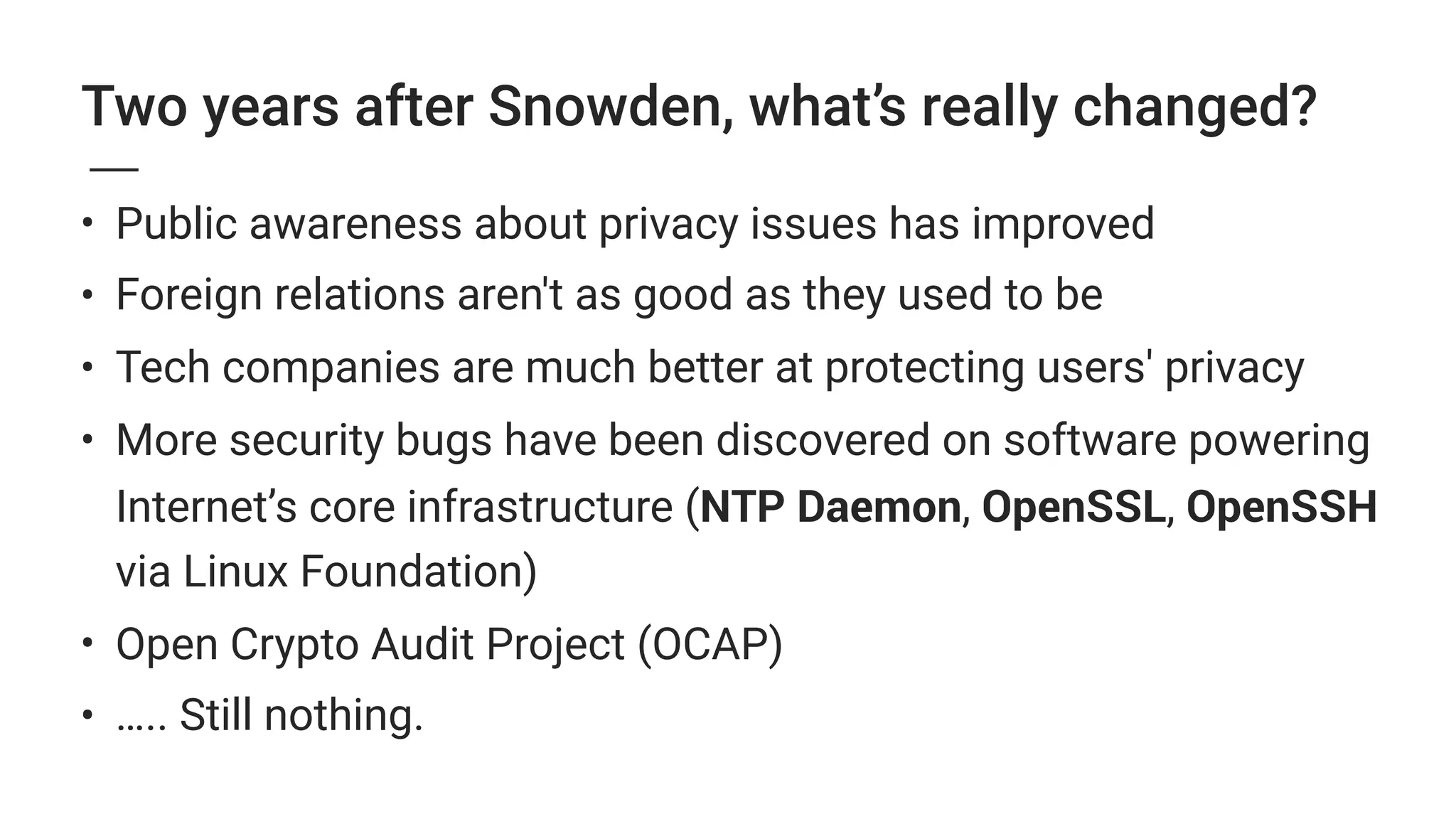
1. Edward Snowden's NSA leaks from 2013 increased public awareness of privacy issues and prompted tech companies to improve privacy protections for users.
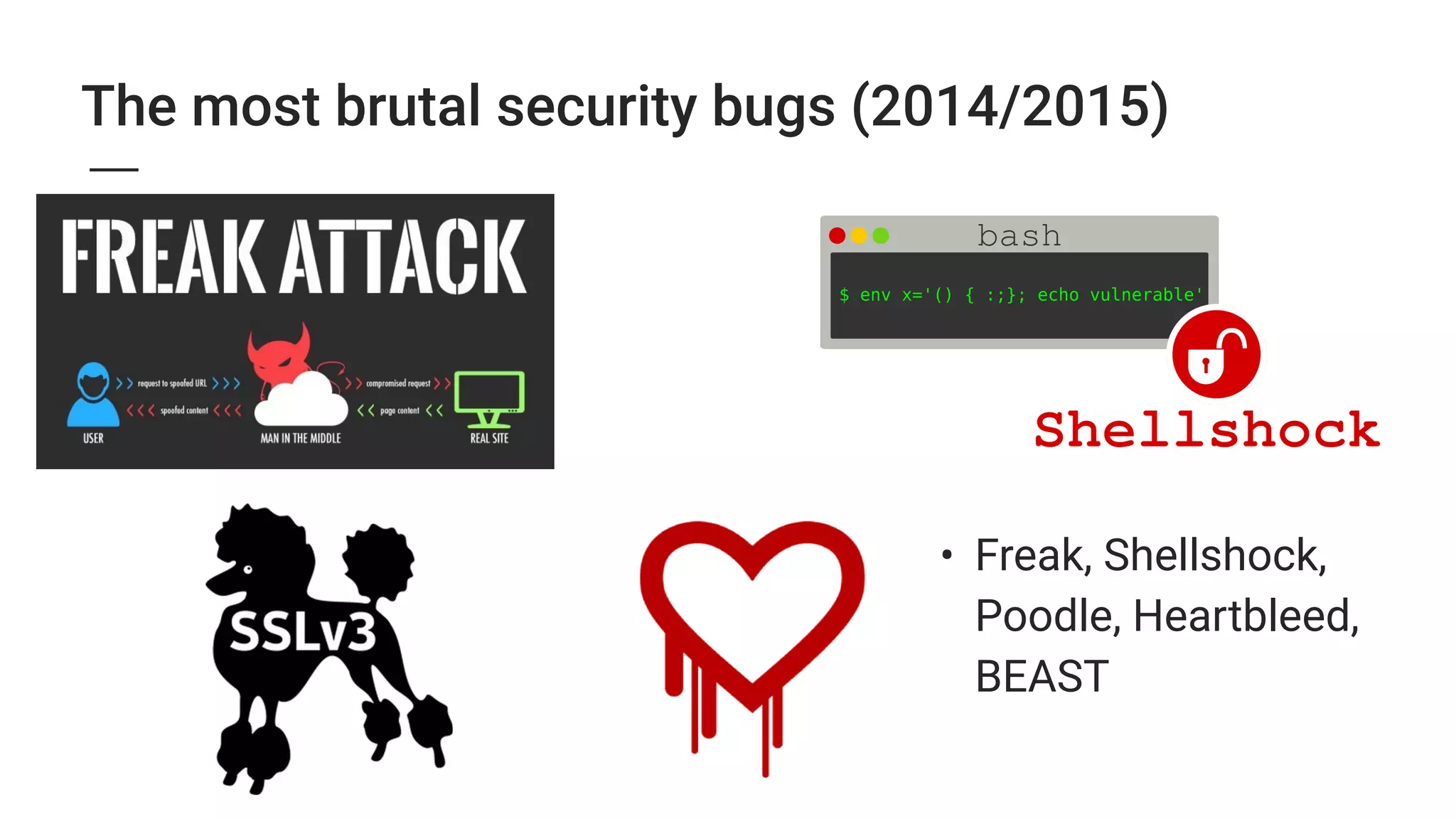
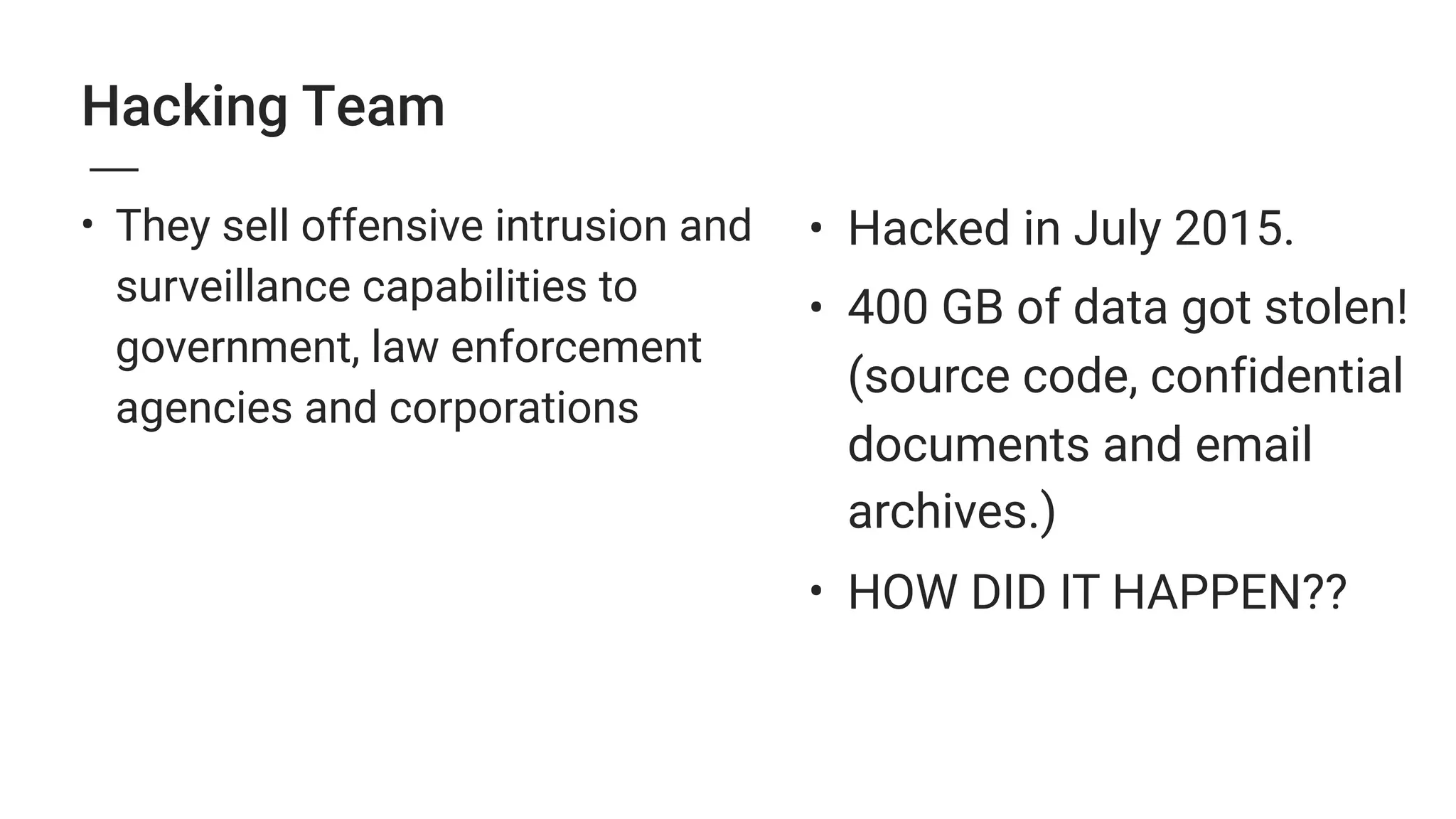
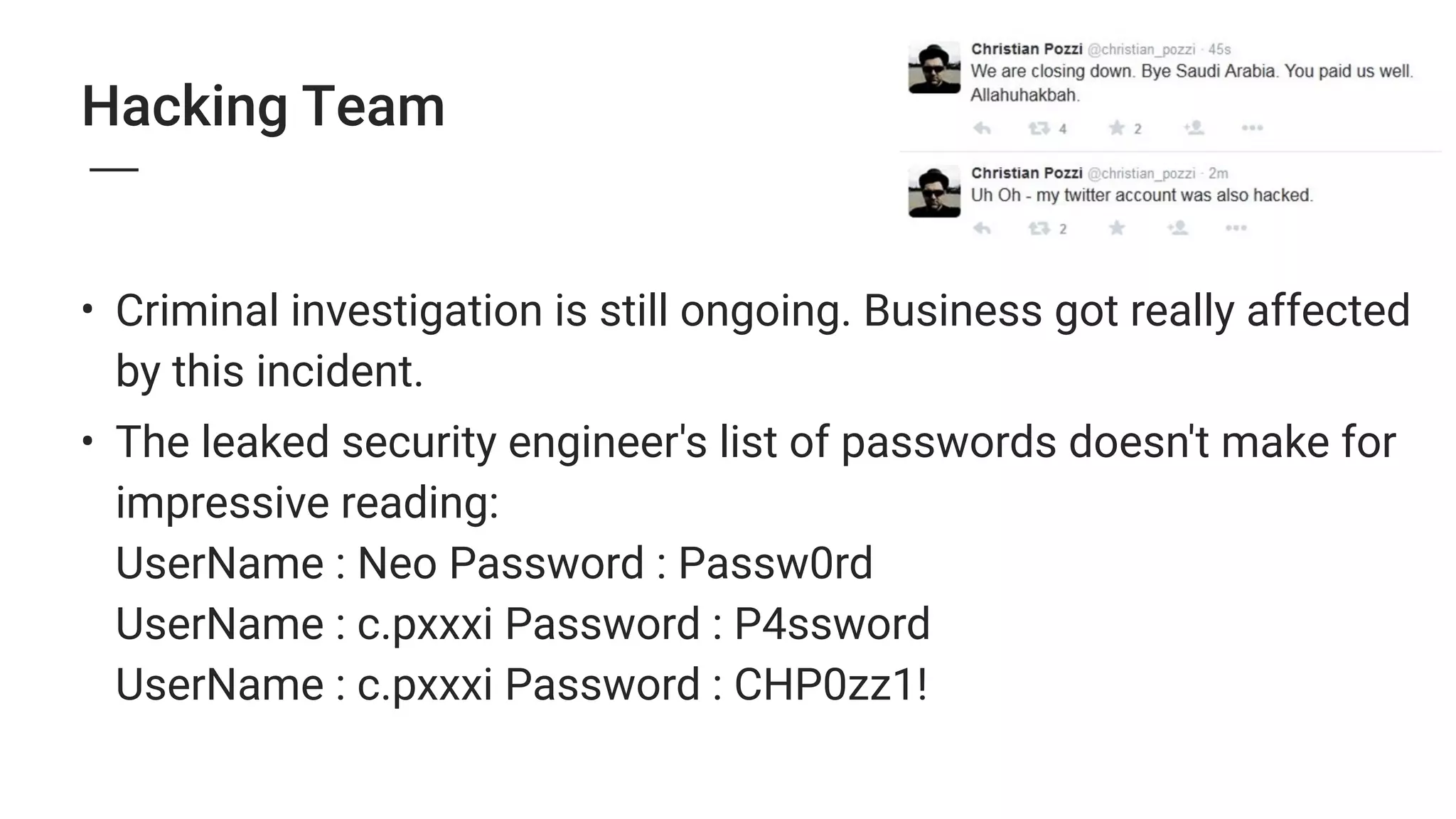
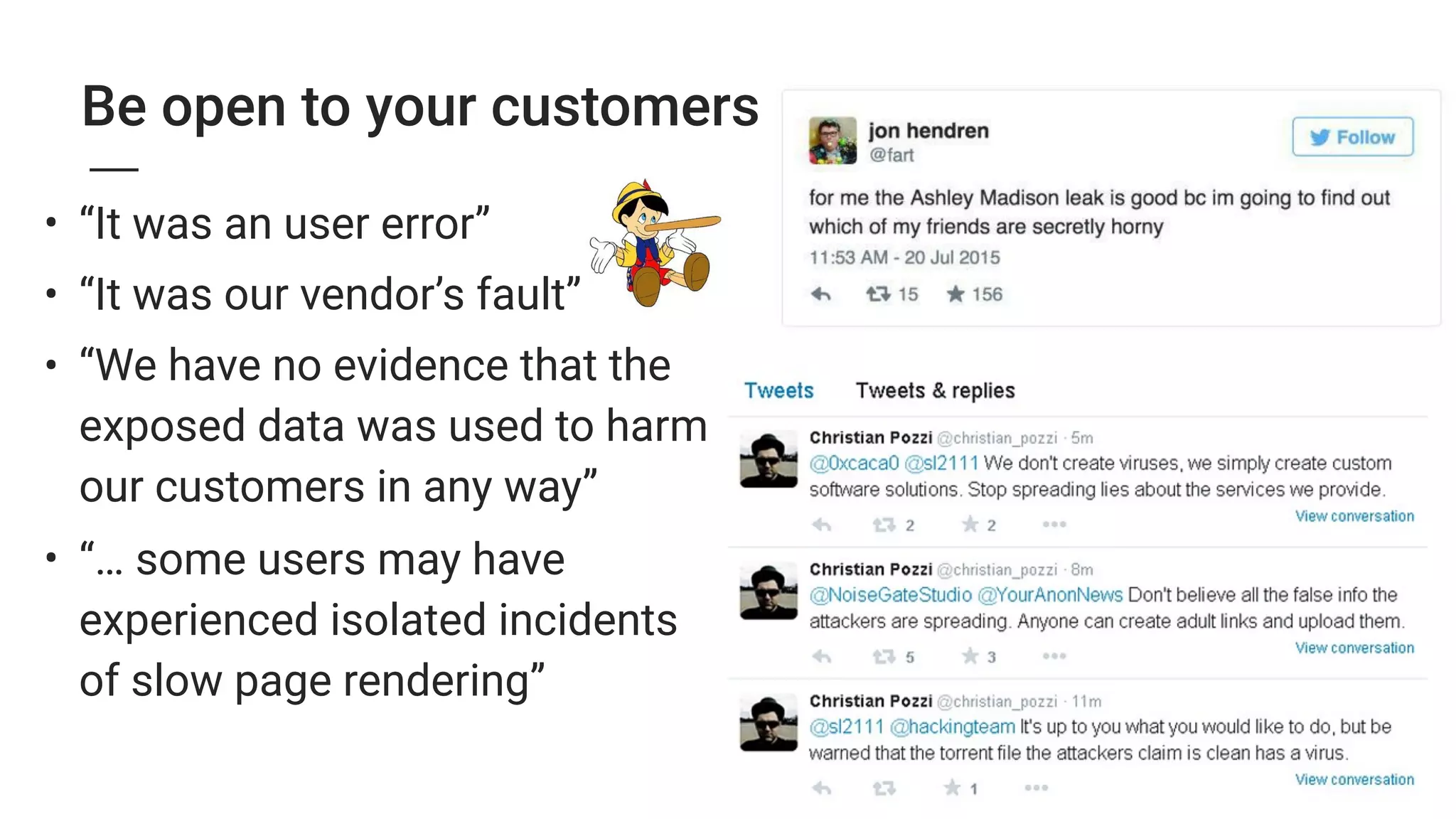
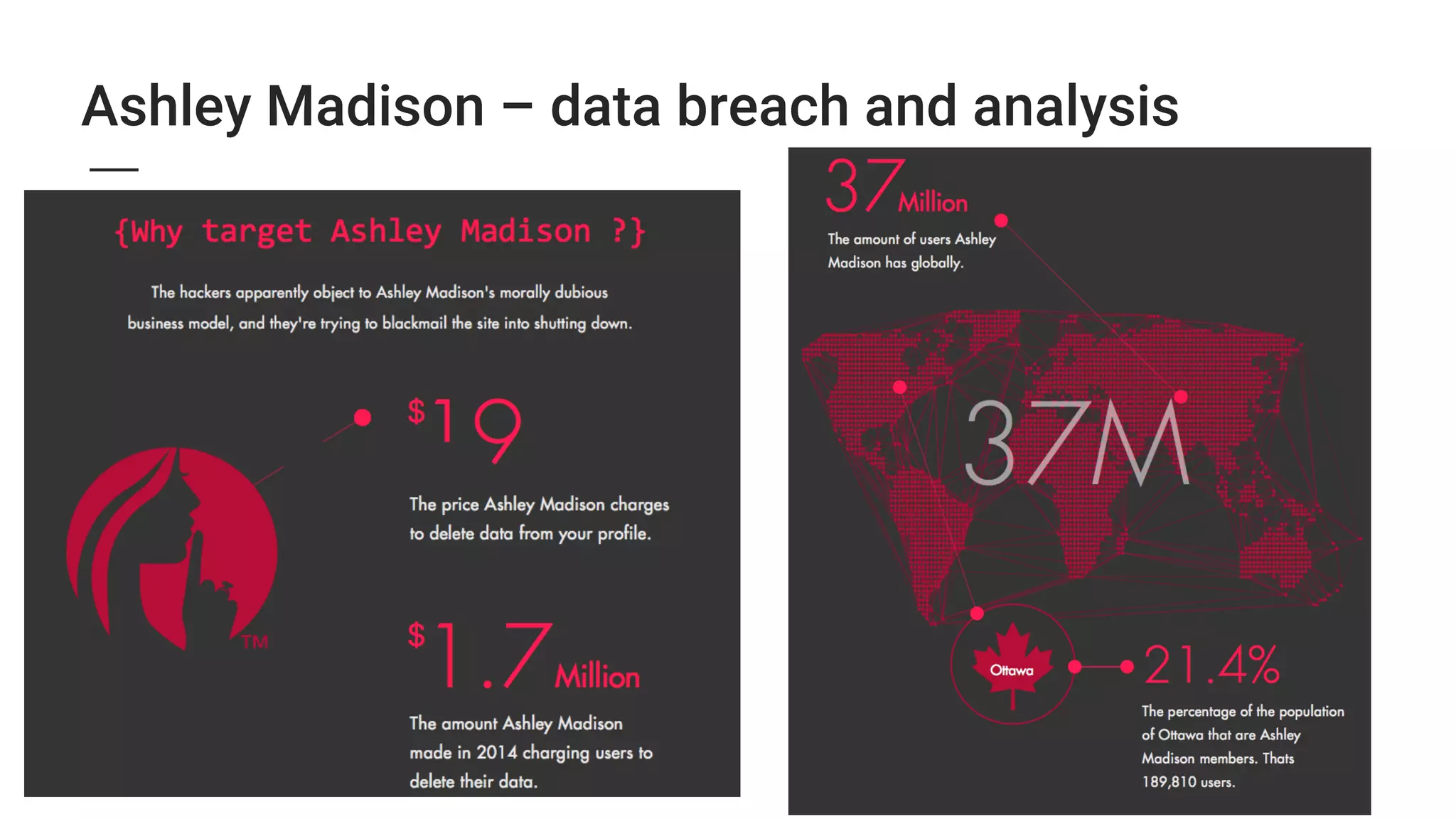
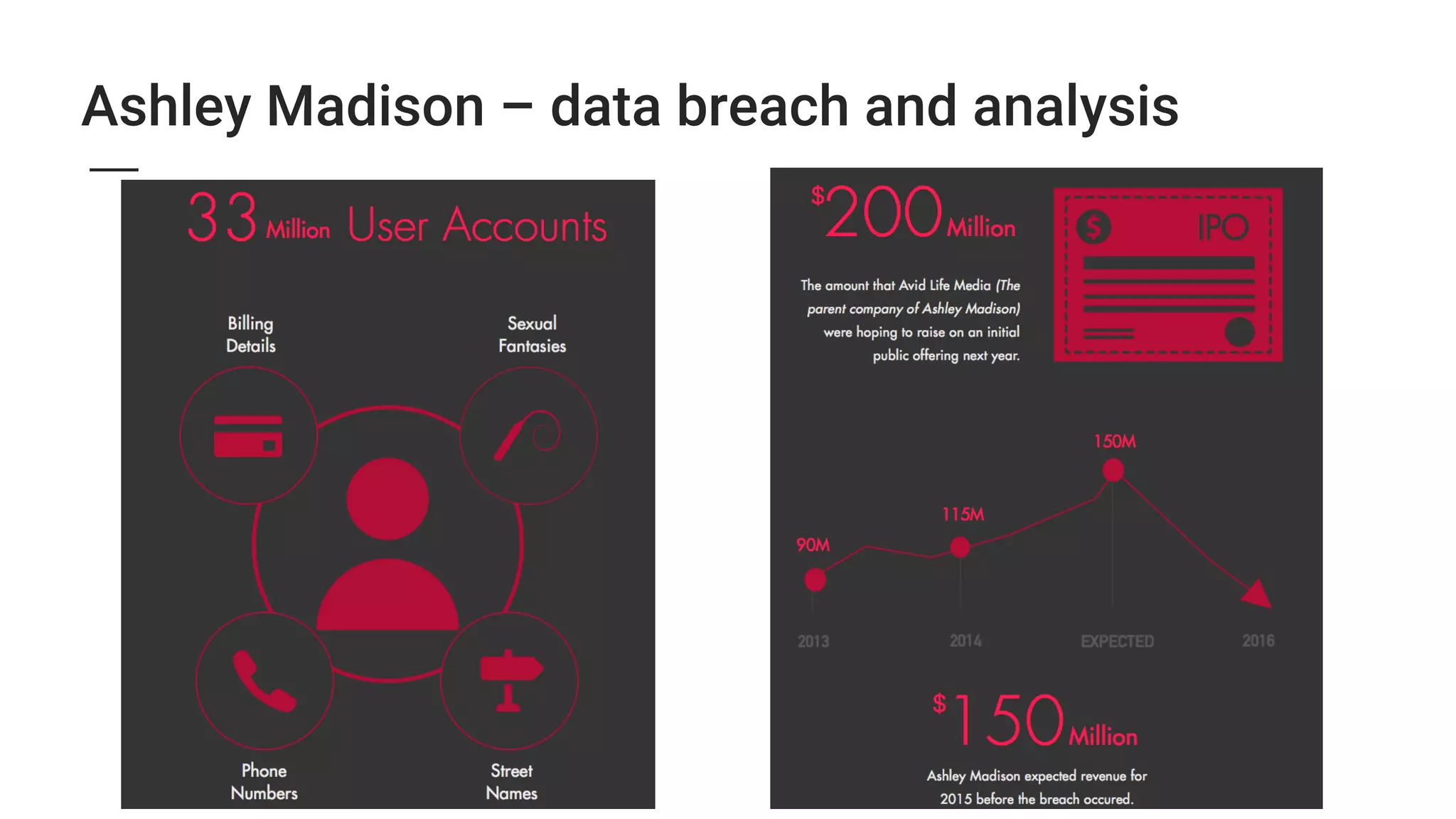
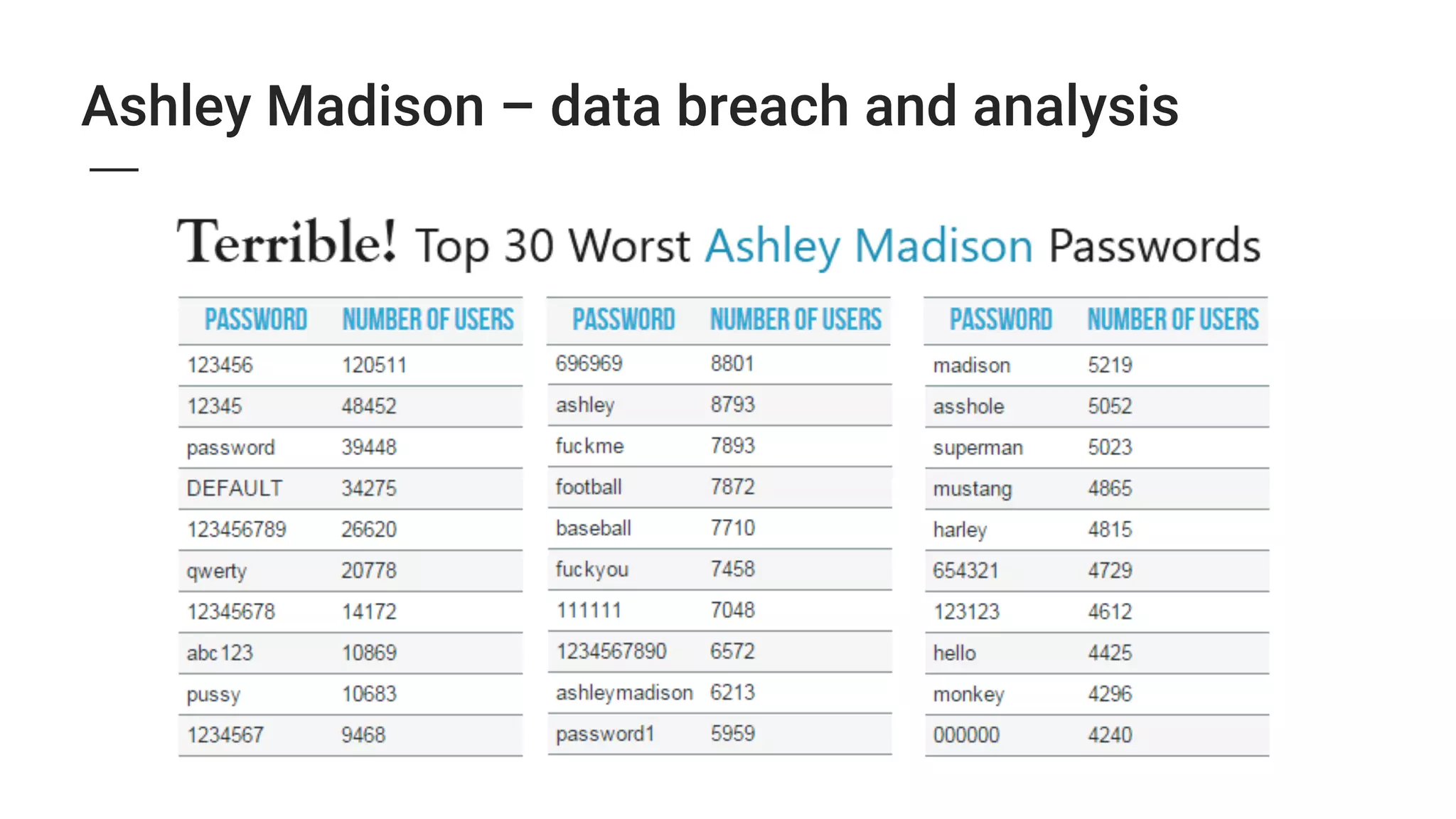
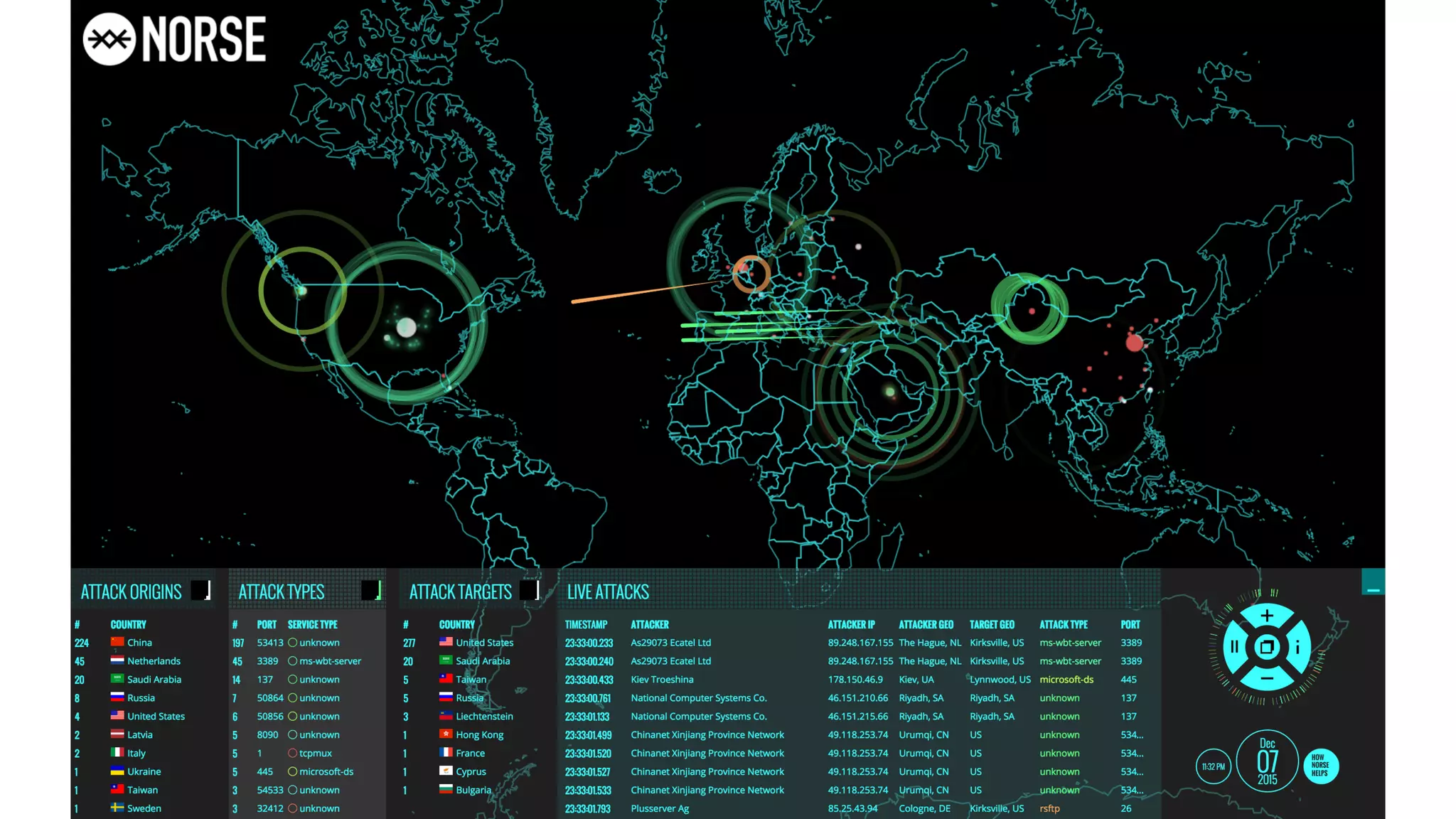
2. Major security breaches in 2014-2015 exposed vulnerabilities like Heartbleed and compromised user data from companies like Ashley Madison, TalkTalk, and VTech.
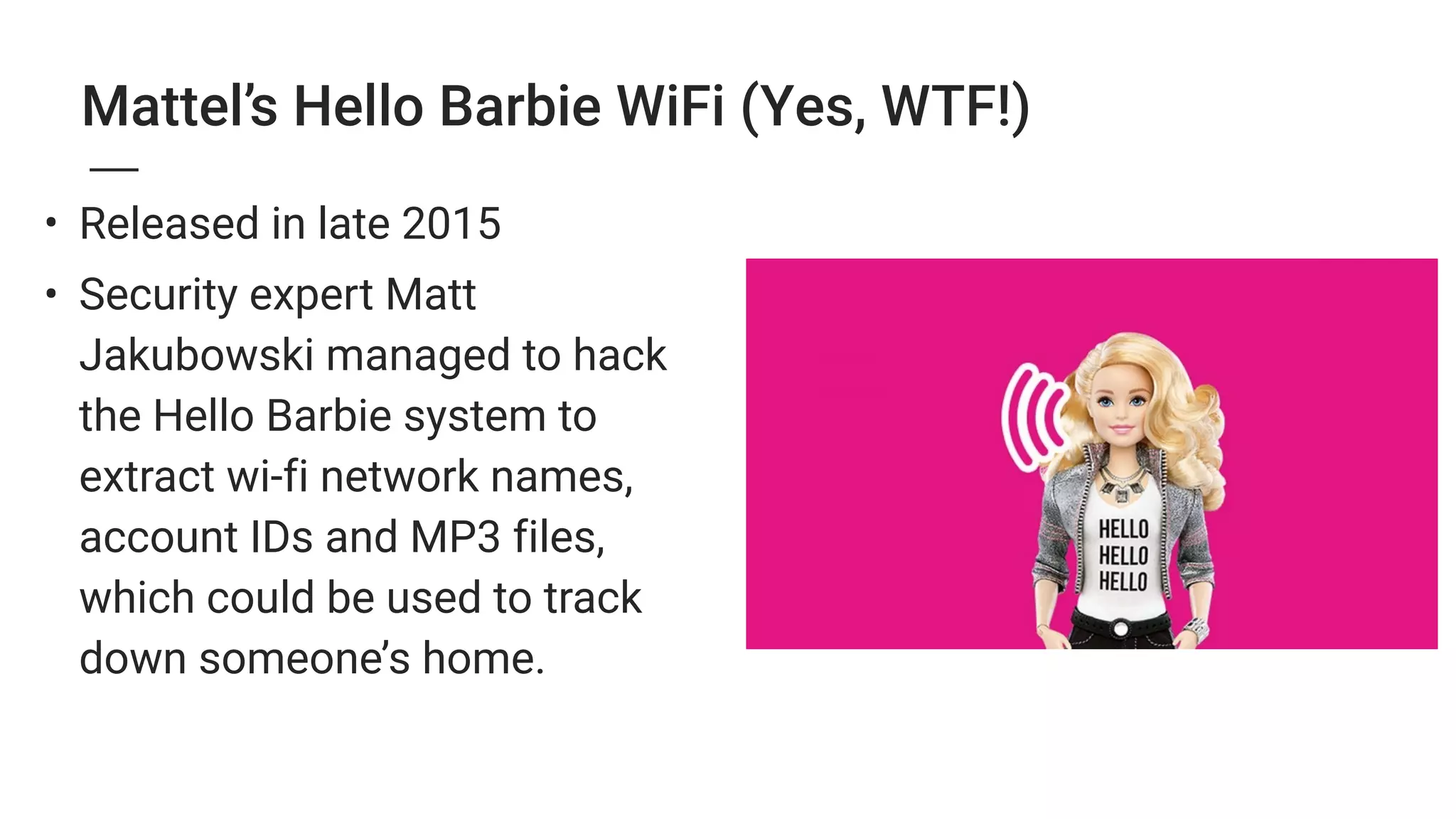
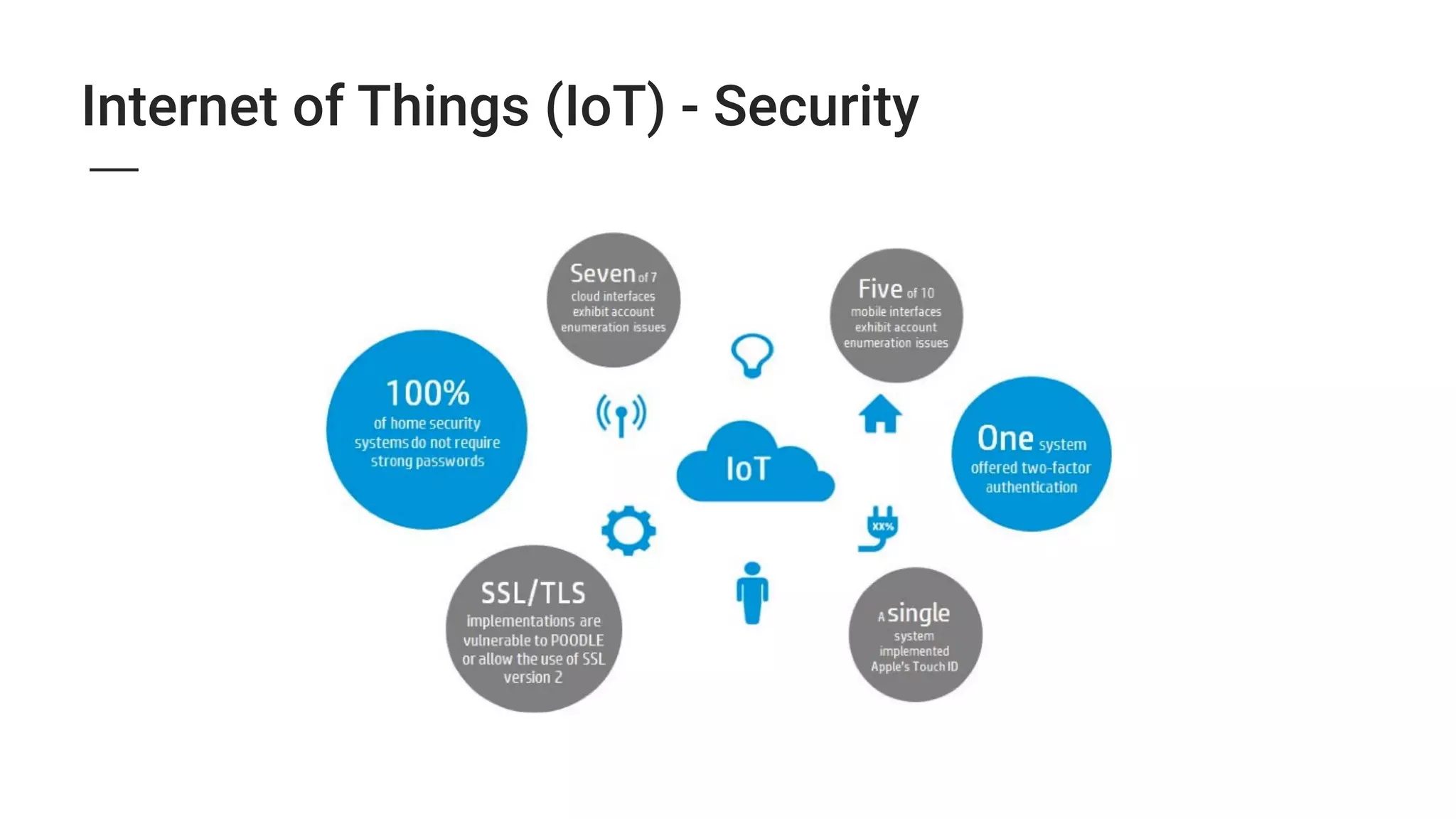
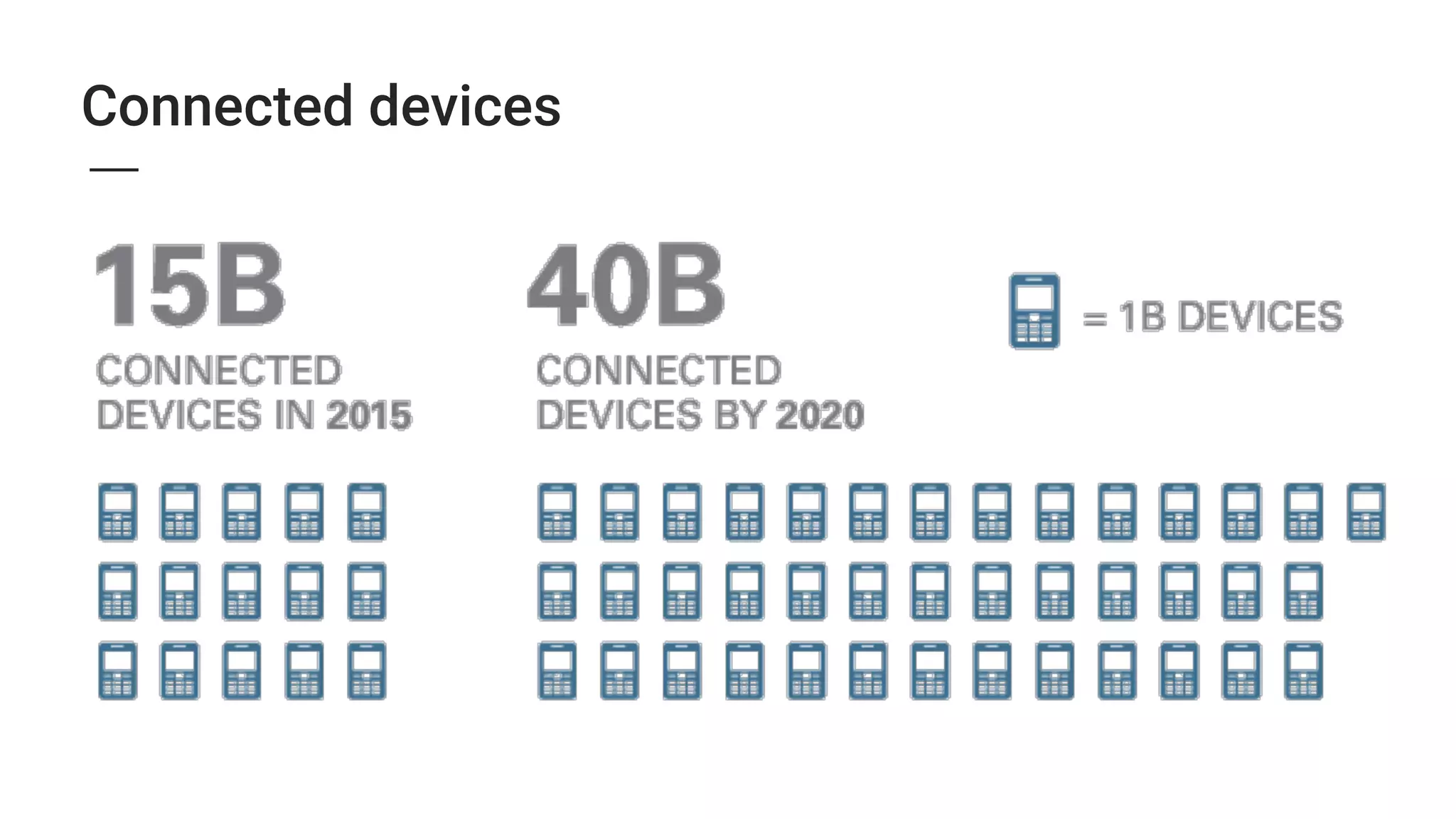
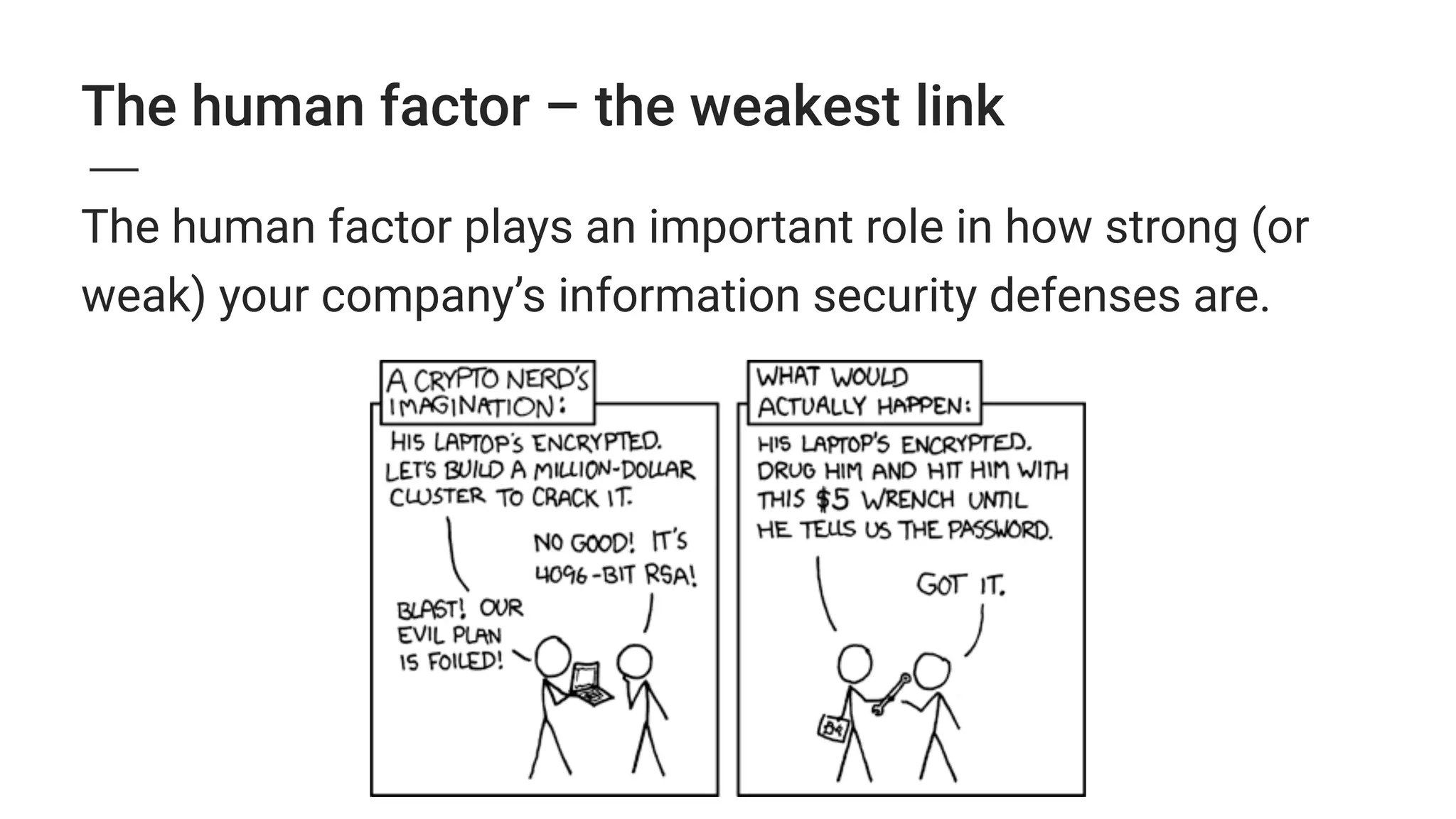
3. The growing Internet of Things introduces new security threats as more devices become connected, and human error remains a major weak point that can undermine other security defenses. Basic security practices like strong unique passwords and two-factor authentication are recommended.