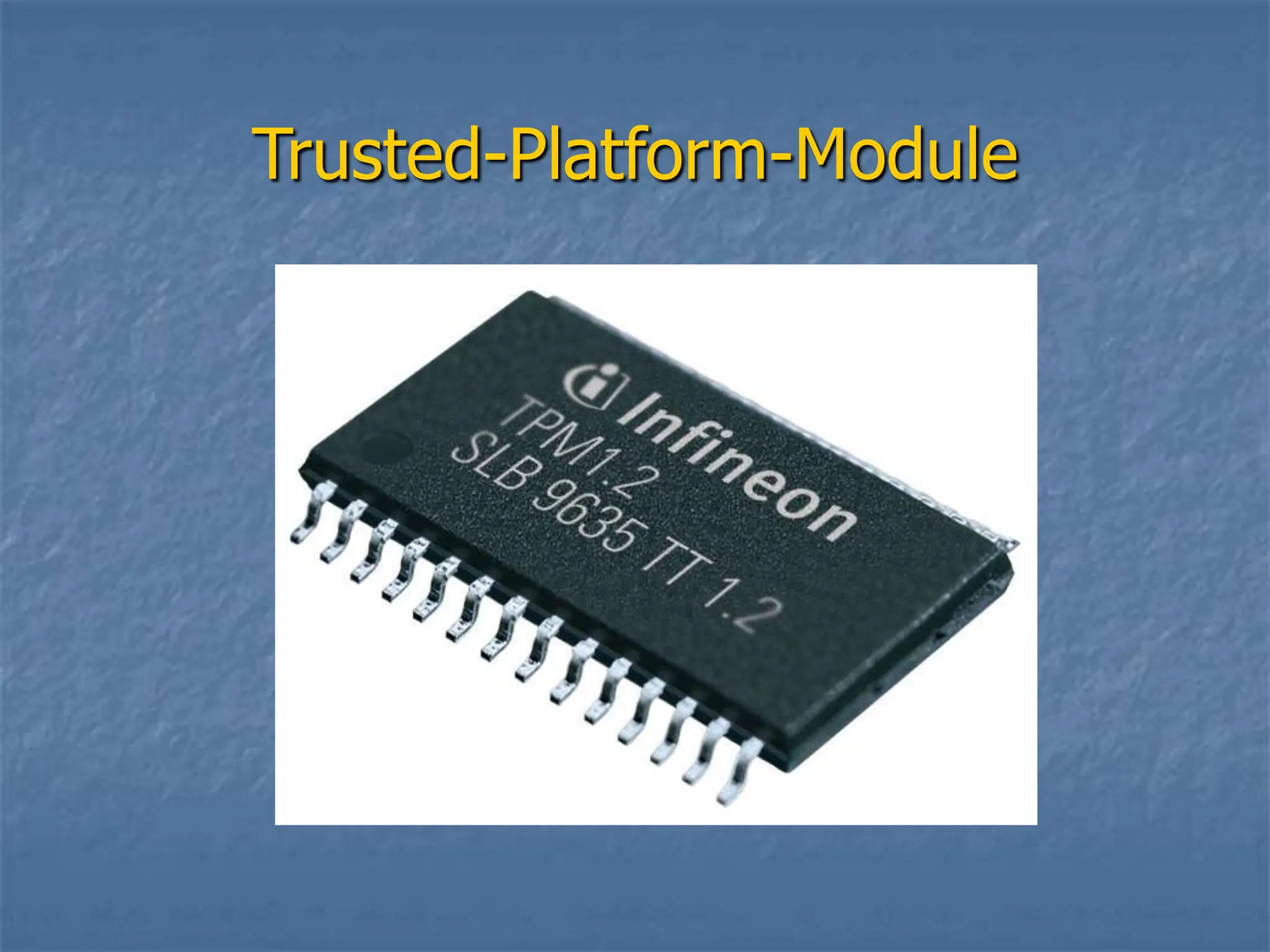
Trusted Computing (TC) uses a Trusted Platform Module (TPM) hardware chip to enable secure computing technologies. The TPM provides hardware-based security features like memory curtaining, sealed storage, and remote attestation to verify the integrity and identity of software. TC aims to make computers trust software creators over users to prevent unauthorized access or software tampering. It is an open industry standard being adopted in operating systems and processors to enhance security for personal and enterprise computing.