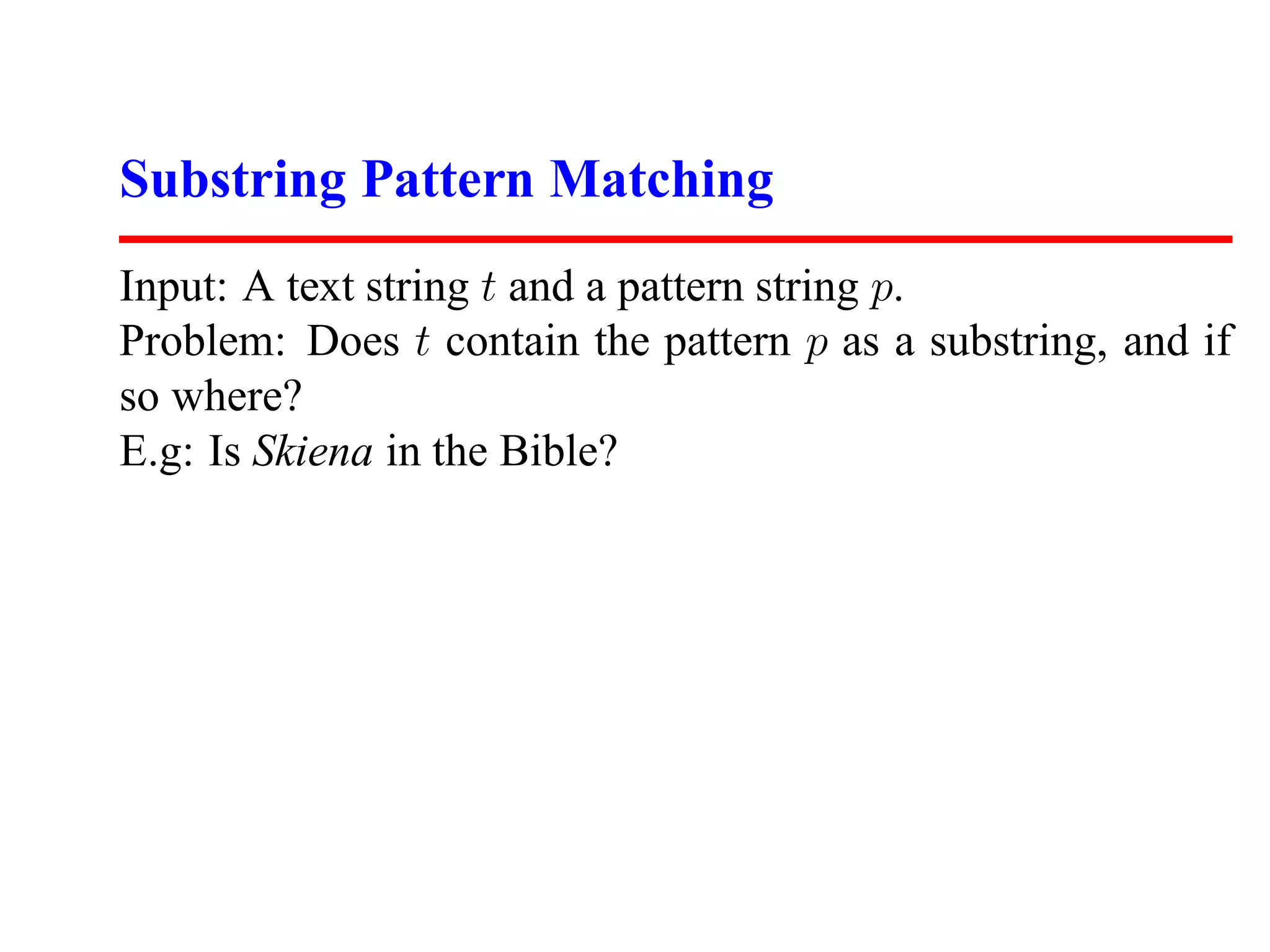
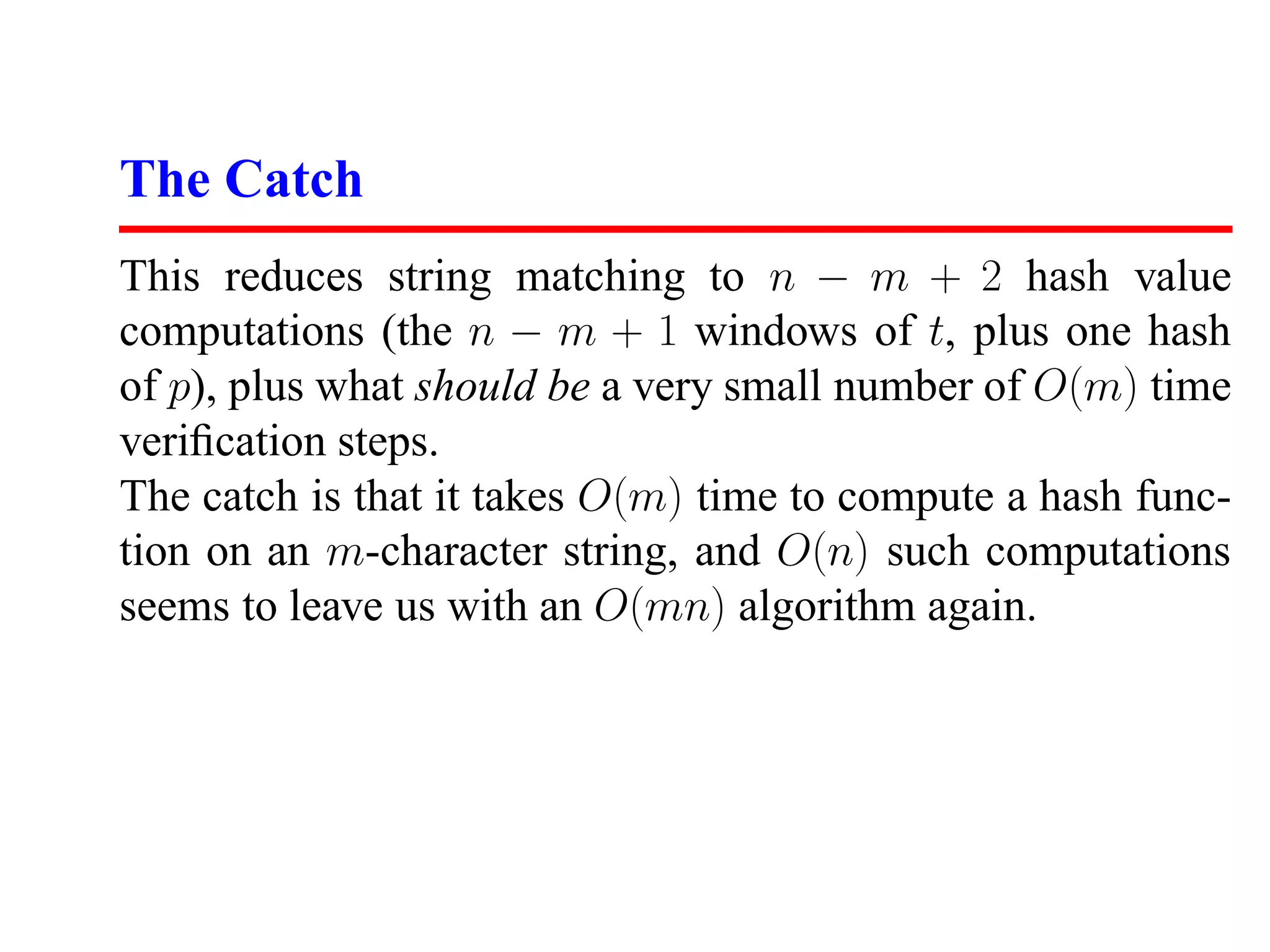
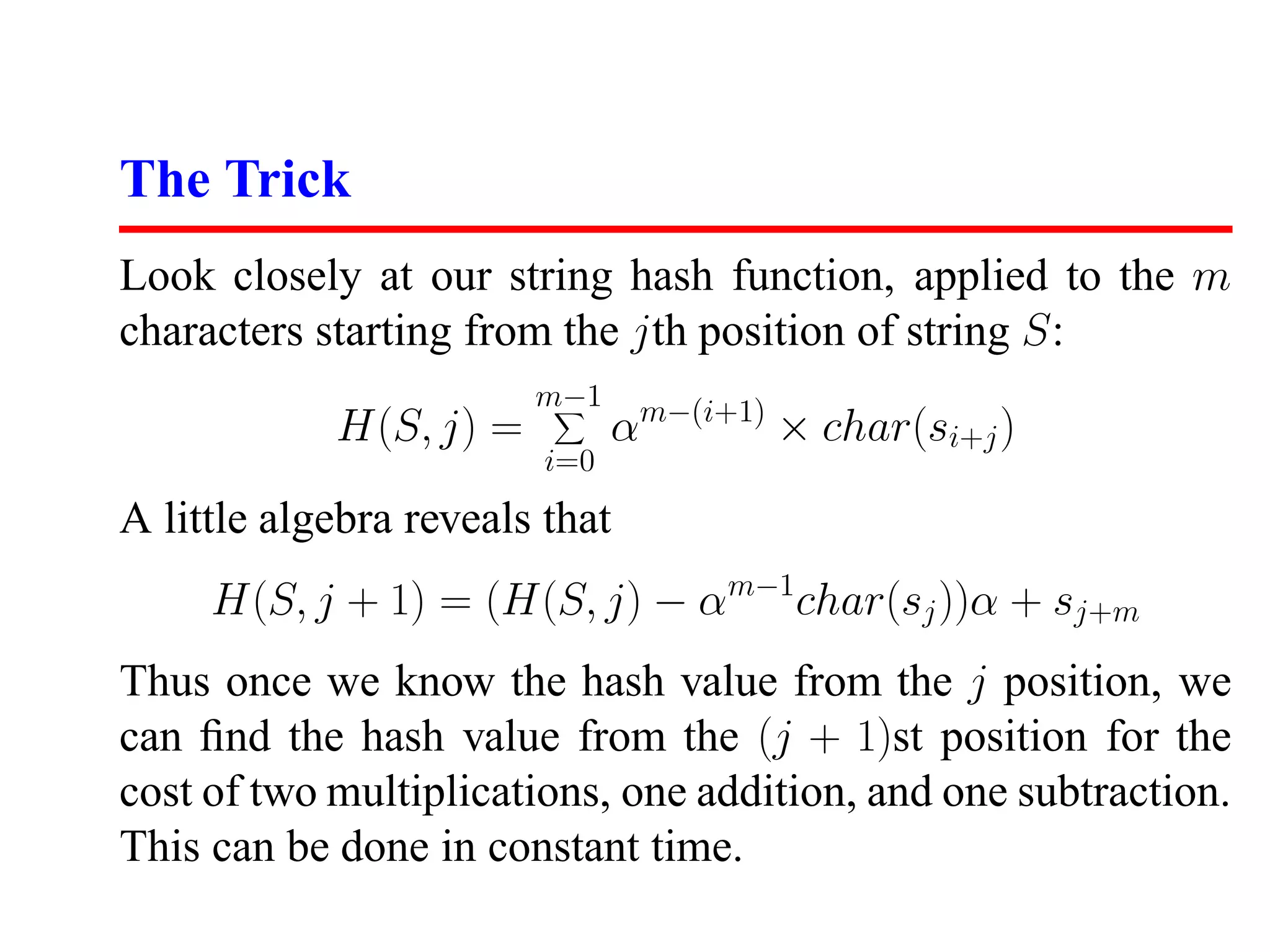
This document discusses hashing and its applications. It begins by describing dictionary operations like search, insert, delete, minimum, maximum, and their implementations using different data structures. It then focuses on hash tables, explaining how they work using hash functions to map keys to array indices. The document discusses collisions, good and bad hash functions, and performance of hash table operations. It also describes how hashing can be used for substring pattern matching and other applications like document fingerprinting.

![Dictionary / Dynamic Set Operations
Perhaps the most important class of data structures maintain
a set of items, indexed by keys.
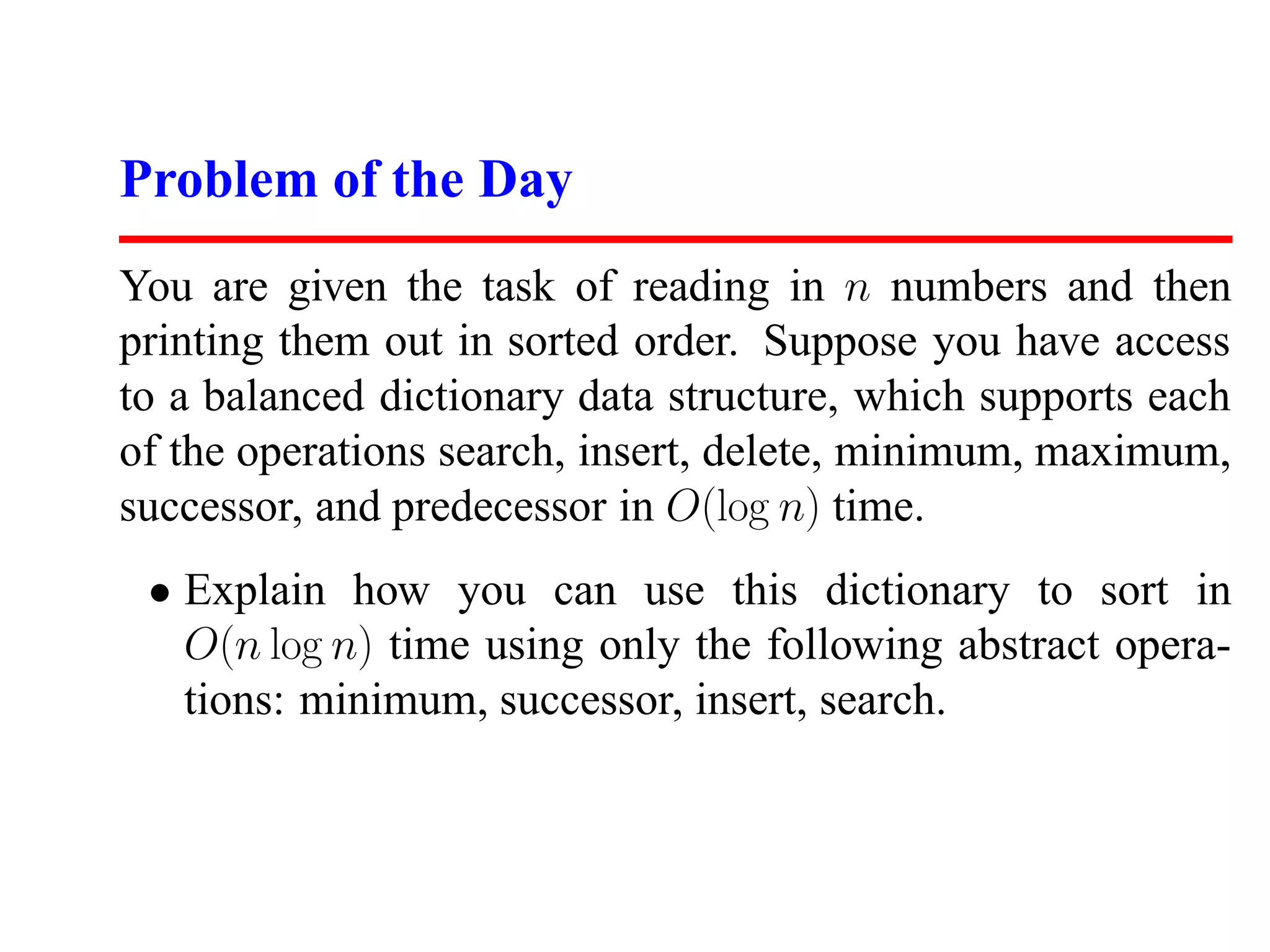
• Search(S,k) – A query that, given a set S and a key value
k, returns a pointer x to an element in S such that key[x]
= k, or nil if no such element belongs to S.
• Insert(S,x) – A modifying operation that augments the set
S with the element x.
• Delete(S,x) – Given a pointer x to an element in the set S,
remove x from S. Observe we are given a pointer to an
element x, not a key value.](https://image.slidesharecdn.com/skienaalgorithm2007lecture06sorting-111212074916-phpapp01/75/Skiena-algorithm-2007-lecture06-sorting-2-2048.jpg)


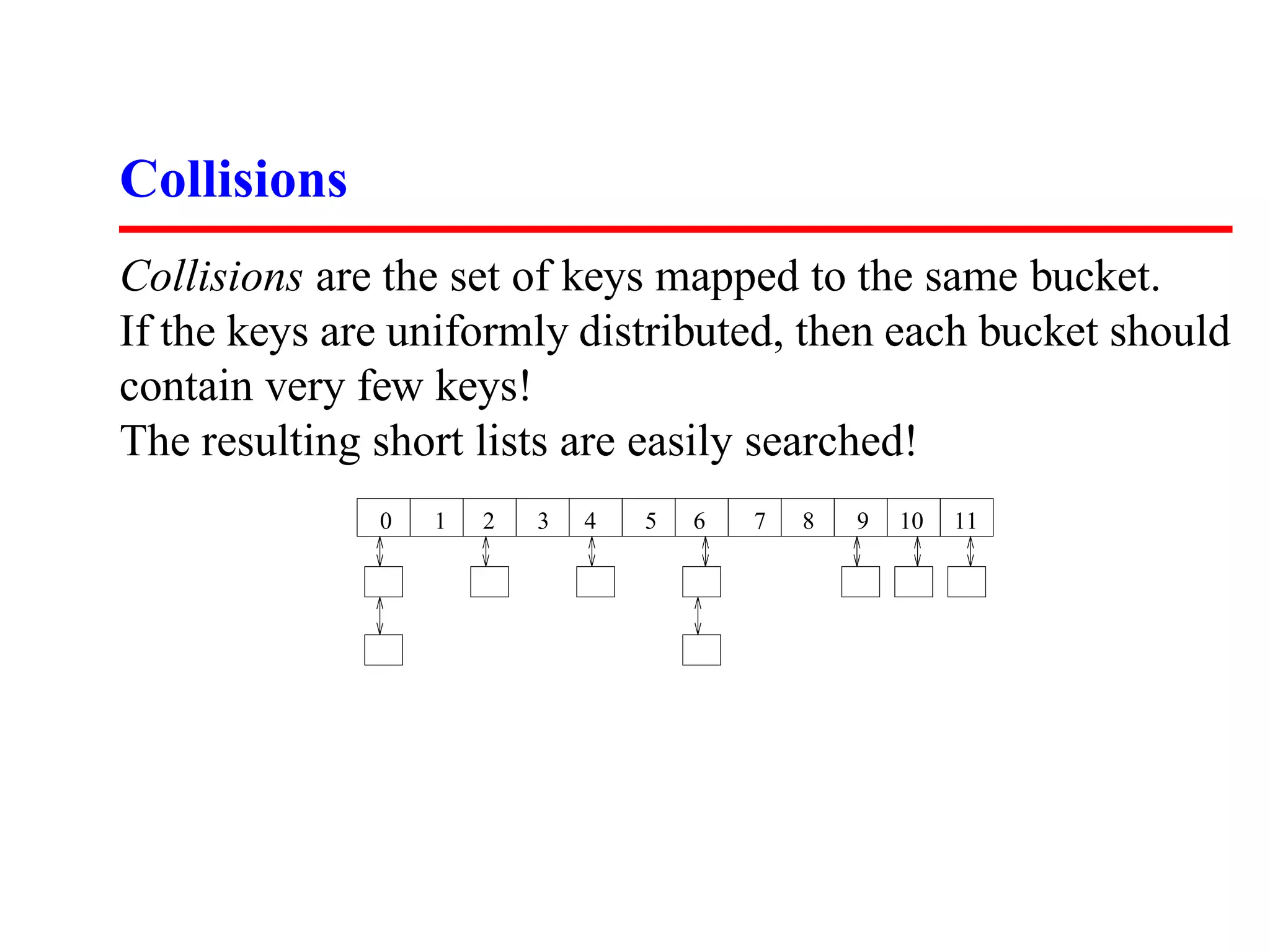
![Hash Functions
It is the job of the hash function to map keys to integers. A
good hash function:
1. Is cheap to evaluate
2. Tends to use all positions from 0 . . . M with uniform
frequency.
The first step is usually to map the key to a big integer, for
example
keylength
h= 128i × char(key[i])
i=0](https://image.slidesharecdn.com/skienaalgorithm2007lecture06sorting-111212074916-phpapp01/75/Skiena-algorithm-2007-lecture06-sorting-8-2048.jpg)